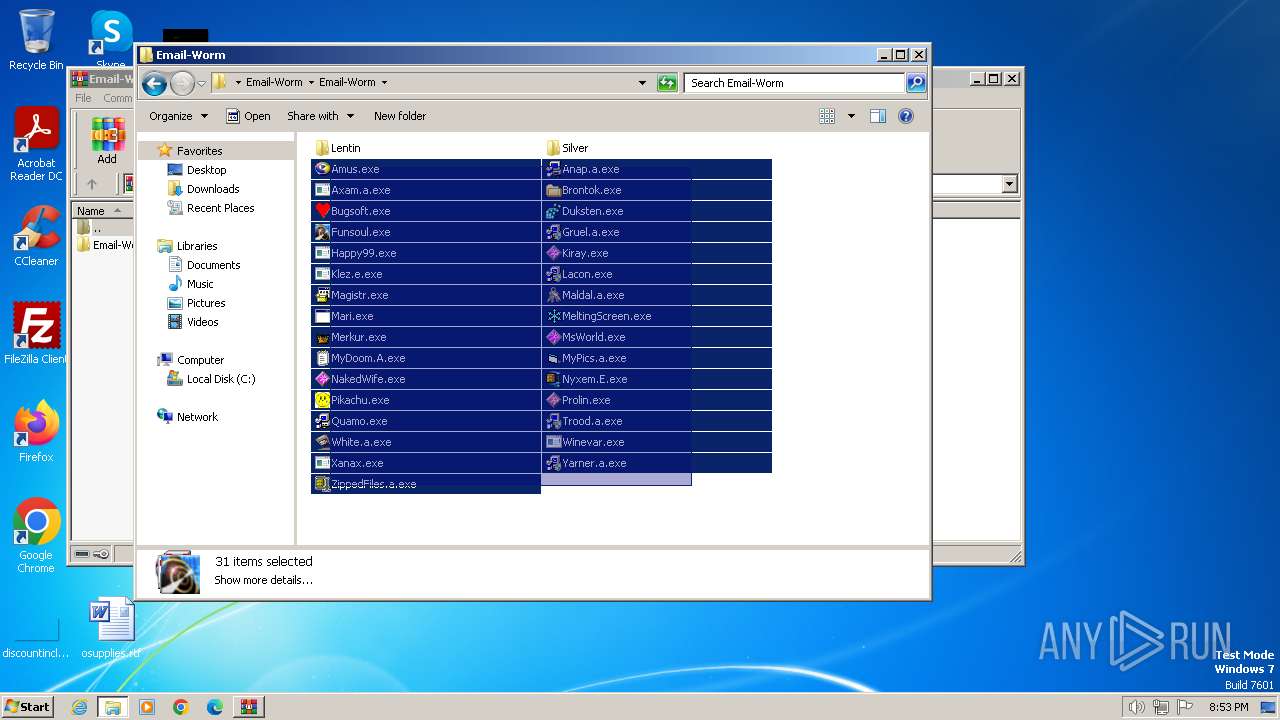
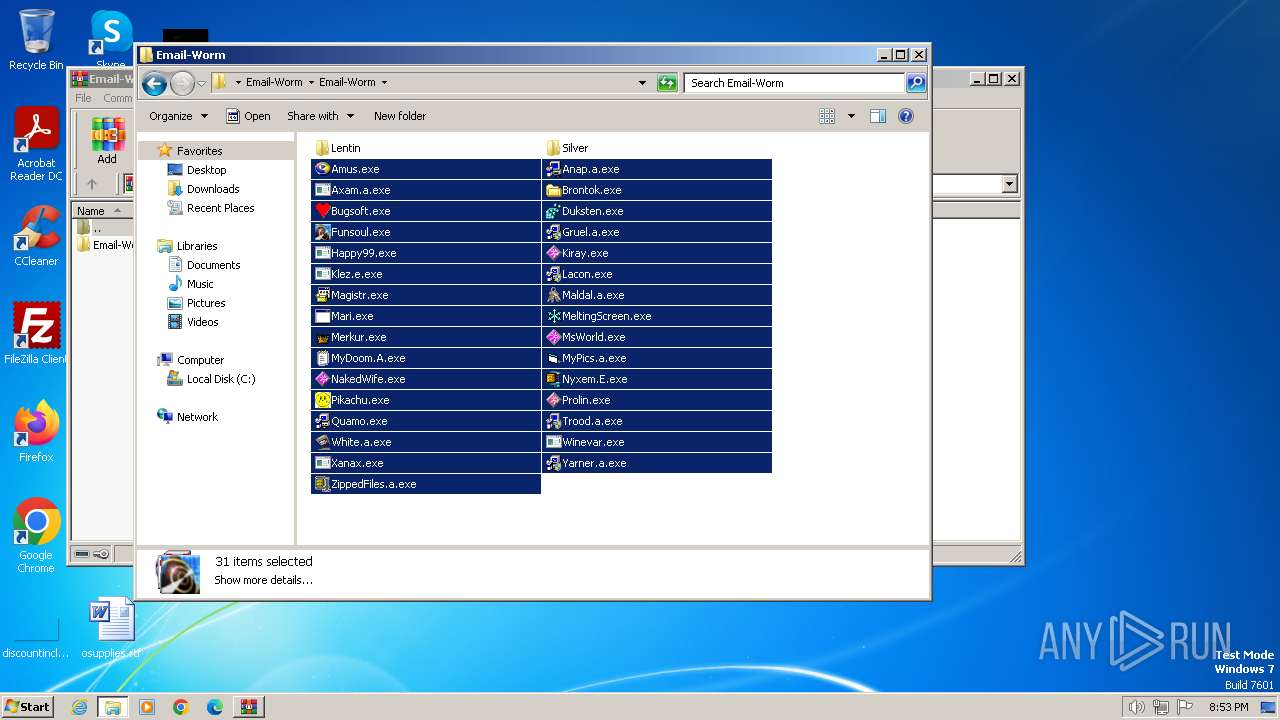
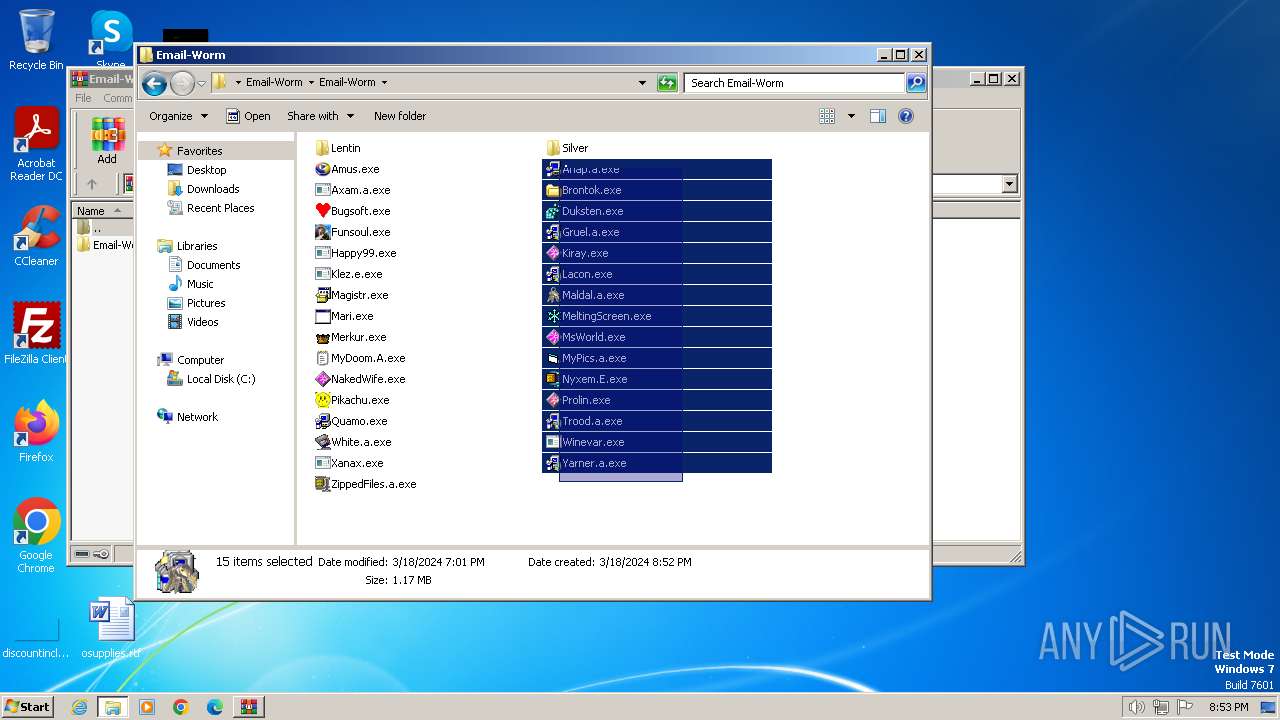
| File name: | Email-Worm.zip |
| Full analysis: | https://app.any.run/tasks/32c8e078-b9c8-469f-8820-d5ce3d5eeff6 |
| Verdict: | Malicious activity |
| Analysis date: | March 18, 2024, 20:51:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v4.5 to extract, compression method=deflate |
| MD5: | F5A7CF4053708EF7AE4C1E9E5310F197 |
| SHA1: | 2DFD07394626D00F433F41C0464A60D97A1ED95F |
| SHA256: | 63278688C6F335CEAD87F9E130766CC2075B9CA8D9DCA375150DDAE2D5884CB3 |
| SSDEEP: | 98304:gRSHMzxkBu/aSNeXpO+QiTUPNgMVT0fkCRzYVRLg1BoSoSpRMQd+Z+n1qVTGfaID:XaVgMrajCvY |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3500)
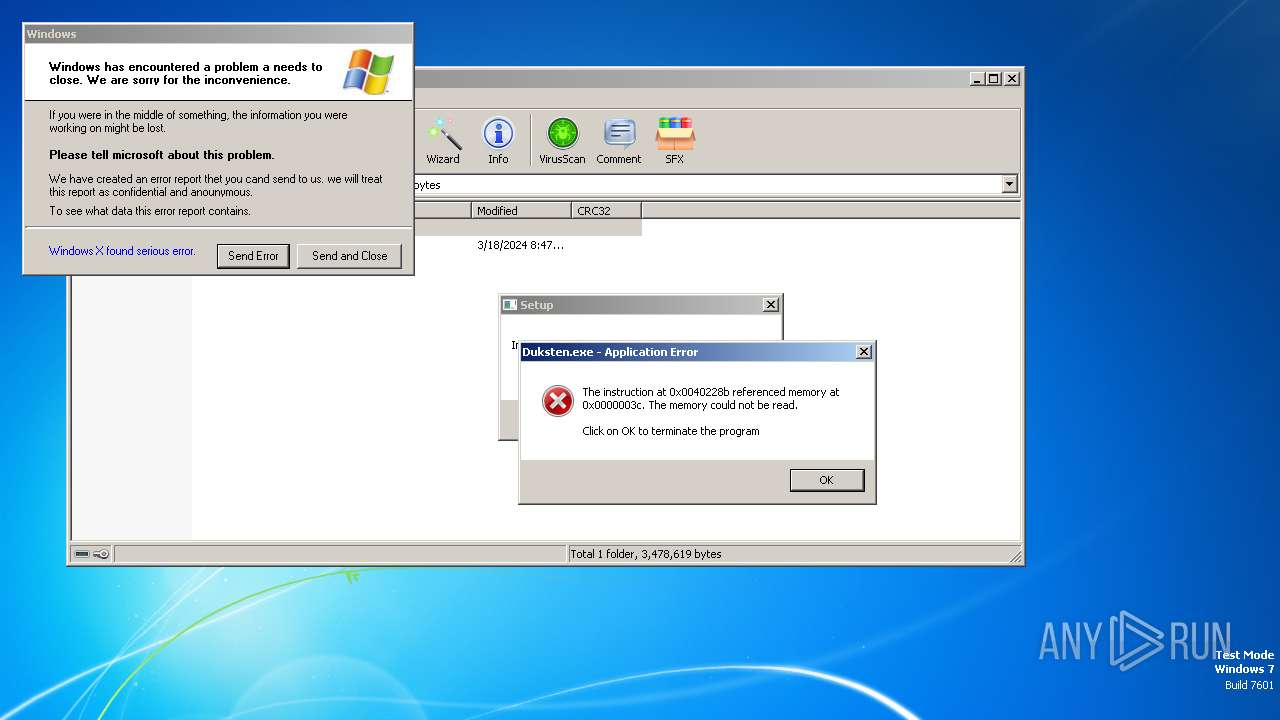
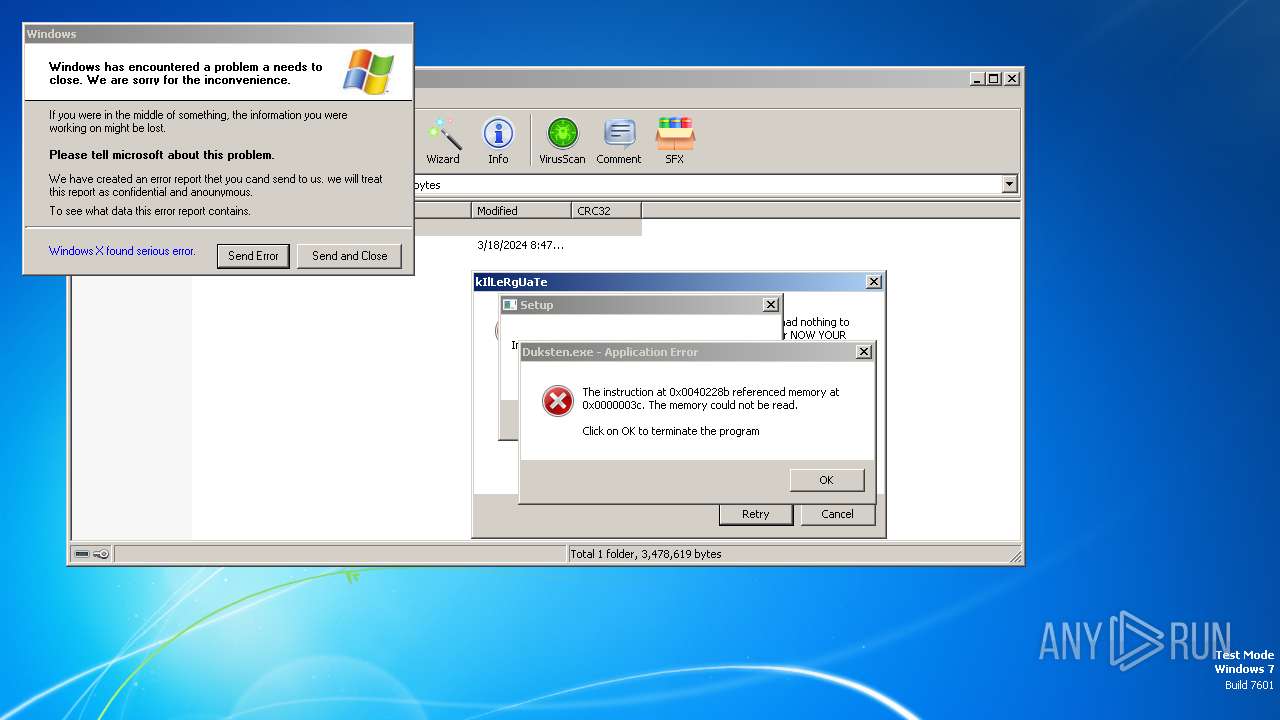
- Duksten.exe (PID: 2096)
- Brontok.exe (PID: 680)
- Gruel.a.exe (PID: 3028)
- Lacon.exe (PID: 1728)
- Prolin.exe (PID: 2828)
- Yarner.a.exe (PID: 3264)
- Winevar.exe (PID: 1172)
- smss.exe (PID: 1040)
- Maldal.a.exe (PID: 1780)
Changes the autorun value in the registry
- Duksten.exe (PID: 2096)
- Brontok.exe (PID: 680)
- Gruel.a.exe (PID: 3028)
- Lacon.exe (PID: 1728)
- Yarner.a.exe (PID: 3264)
- smss.exe (PID: 1040)
- winlogon.exe (PID: 2444)
Modify registry editing tools (regedit)
- Brontok.exe (PID: 680)
- smss.exe (PID: 1040)
- winlogon.exe (PID: 2444)
Changes appearance of the Explorer extensions
- Brontok.exe (PID: 680)
- smss.exe (PID: 1040)
- winlogon.exe (PID: 2444)
Disables the Find the Start menu
- Gruel.a.exe (PID: 3028)
Creates a writable file in the system directory
- Duksten.exe (PID: 2096)
- Lacon.exe (PID: 1728)
- Maldal.a.exe (PID: 1780)
- Winevar.exe (PID: 1172)
- smss.exe (PID: 1040)
Changes the login/logoff helper path in the registry
- Brontok.exe (PID: 680)
- smss.exe (PID: 1040)
- winlogon.exe (PID: 2444)
Disables the Run the Start menu
- Gruel.a.exe (PID: 3028)
Create files in the Startup directory
- Lacon.exe (PID: 1728)
- smss.exe (PID: 1040)
Actions looks like stealing of personal data
- Lacon.exe (PID: 1728)
SUSPICIOUS
Creates/Modifies COM task schedule object
- Gruel.a.exe (PID: 3028)
Executable content was dropped or overwritten
- Duksten.exe (PID: 2096)
- Brontok.exe (PID: 680)
- Gruel.a.exe (PID: 3028)
- Lacon.exe (PID: 1728)
- Maldal.a.exe (PID: 1780)
- Prolin.exe (PID: 2828)
- Winevar.exe (PID: 1172)
- Yarner.a.exe (PID: 3264)
- smss.exe (PID: 1040)
Drops a file with a rarely used extension (PIF)
- Brontok.exe (PID: 680)
- Winevar.exe (PID: 1172)
- smss.exe (PID: 1040)
The process creates files with name similar to system file names
- Brontok.exe (PID: 680)
- Gruel.a.exe (PID: 3028)
- Duksten.exe (PID: 2096)
Creates file in the systems drive root
- Gruel.a.exe (PID: 3028)
- Prolin.exe (PID: 2828)
- MsWorld.exe (PID: 924)
Starts a Microsoft application from unusual location
- Trood.a.exe (PID: 2736)
Reads the Internet Settings
- WIN68D2.pif (PID: 2612)
Starts application with an unusual extension
- Winevar.exe (PID: 1172)
Starts itself from another location
- Winevar.exe (PID: 1172)
- smss.exe (PID: 1040)
- Brontok.exe (PID: 680)
Reads security settings of Internet Explorer
- WIN68D2.pif (PID: 2612)
Process drops legitimate windows executable
- Yarner.a.exe (PID: 3264)
- Duksten.exe (PID: 2096)
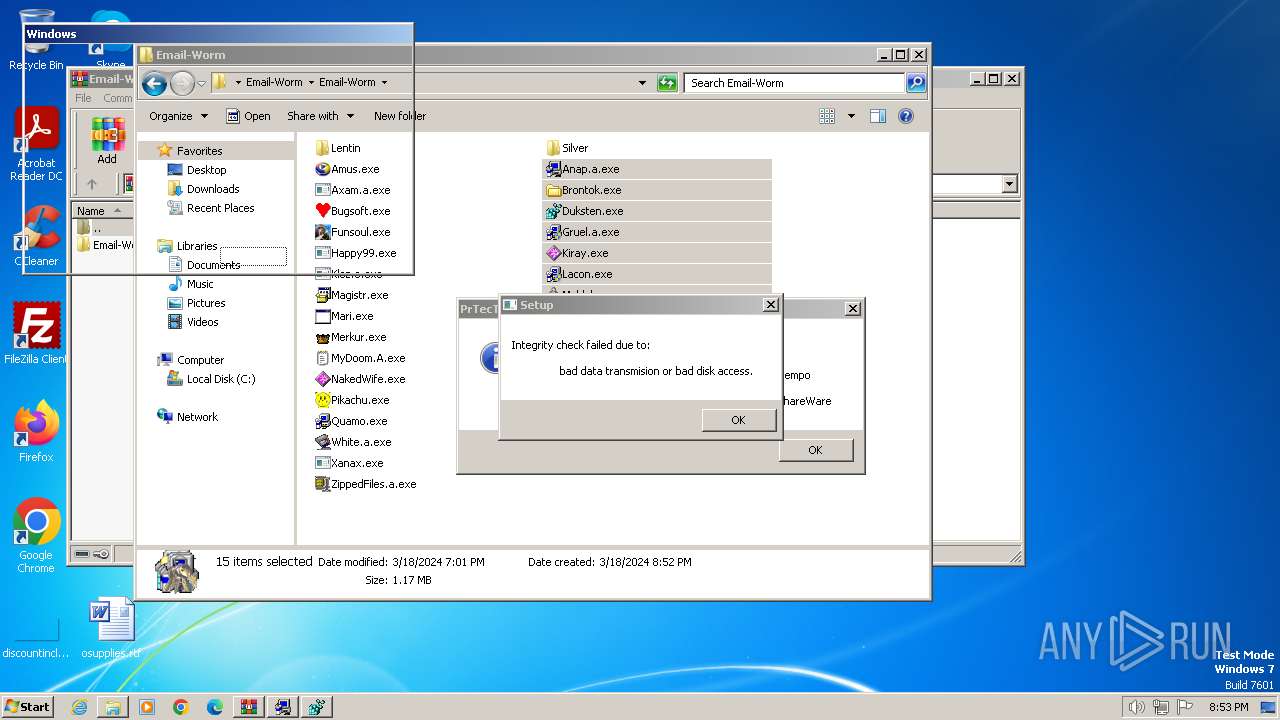
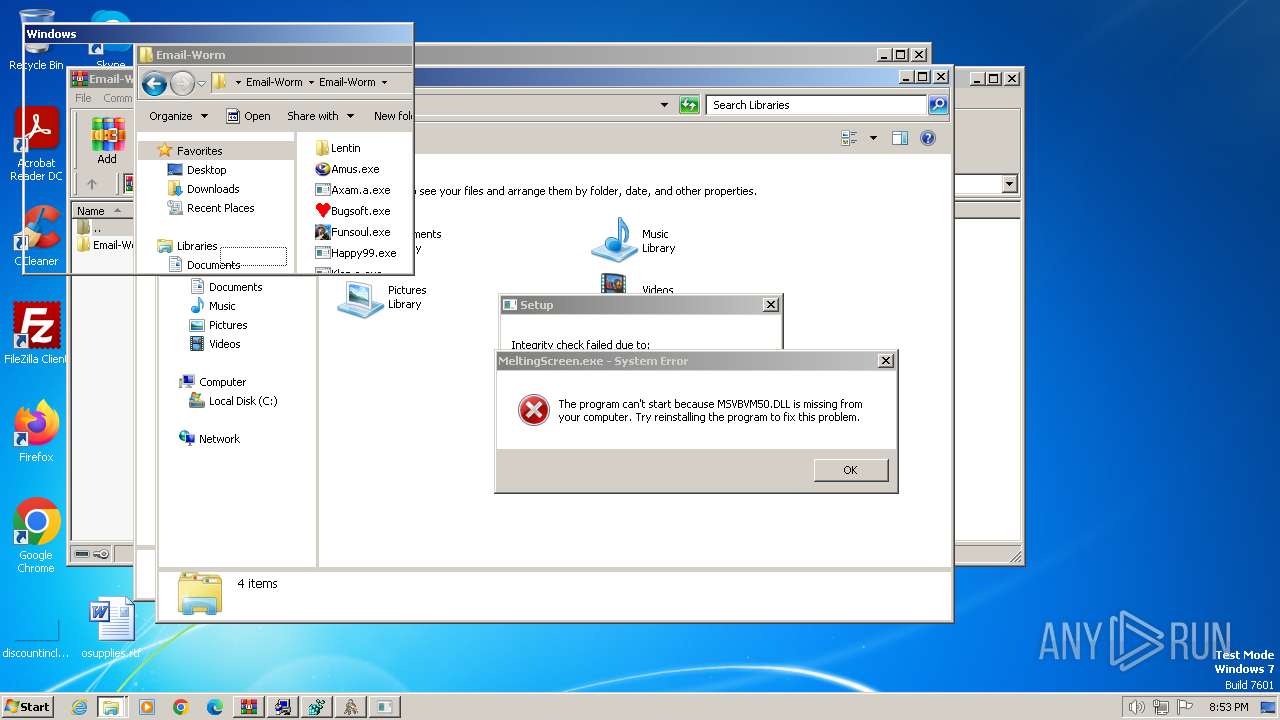
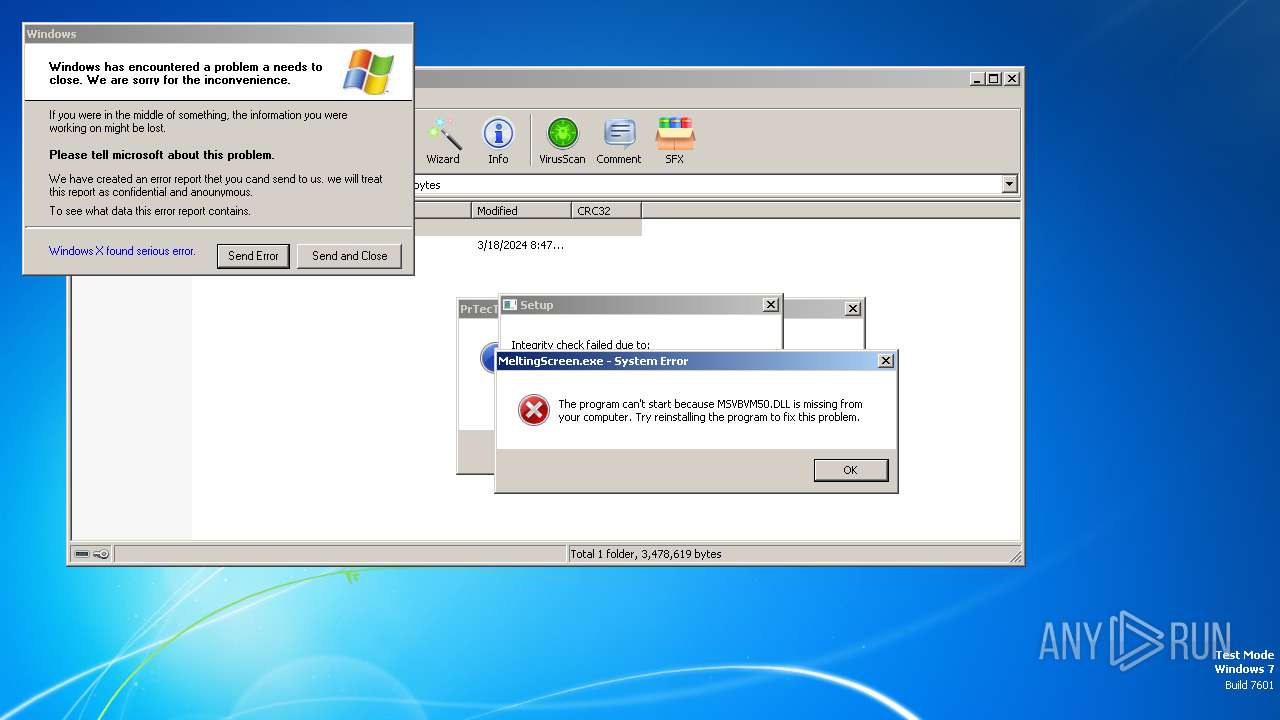
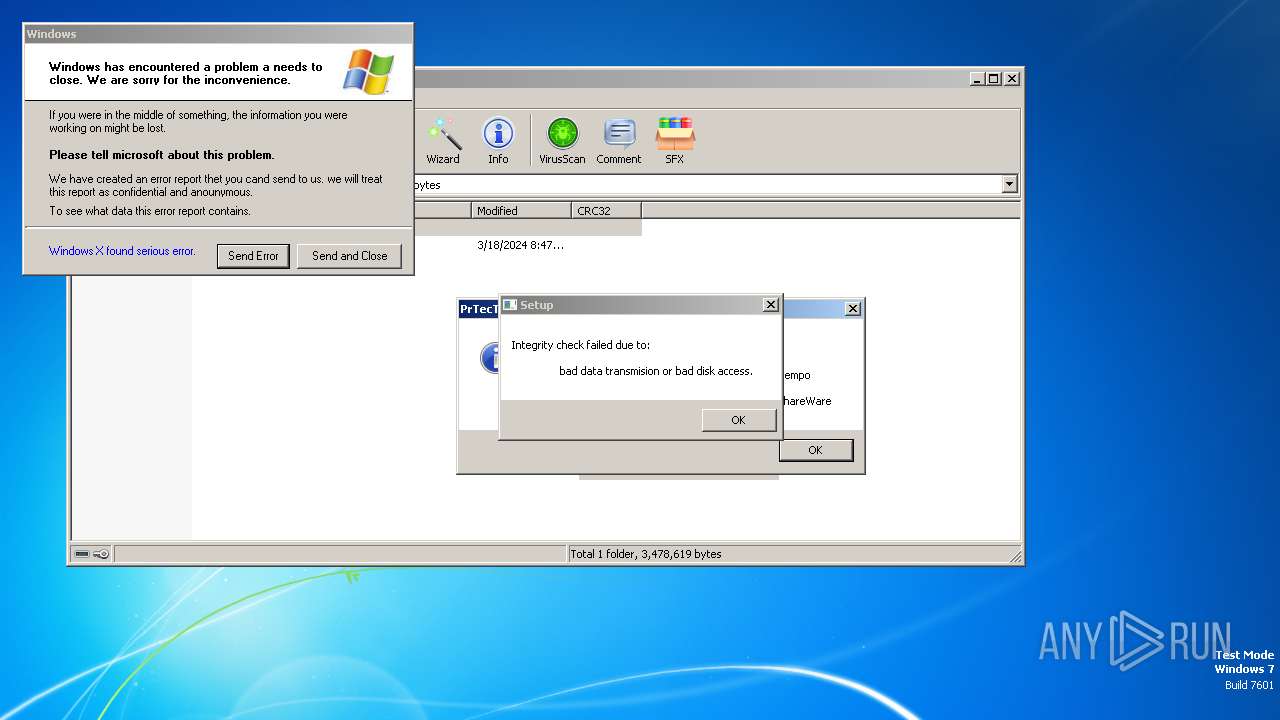
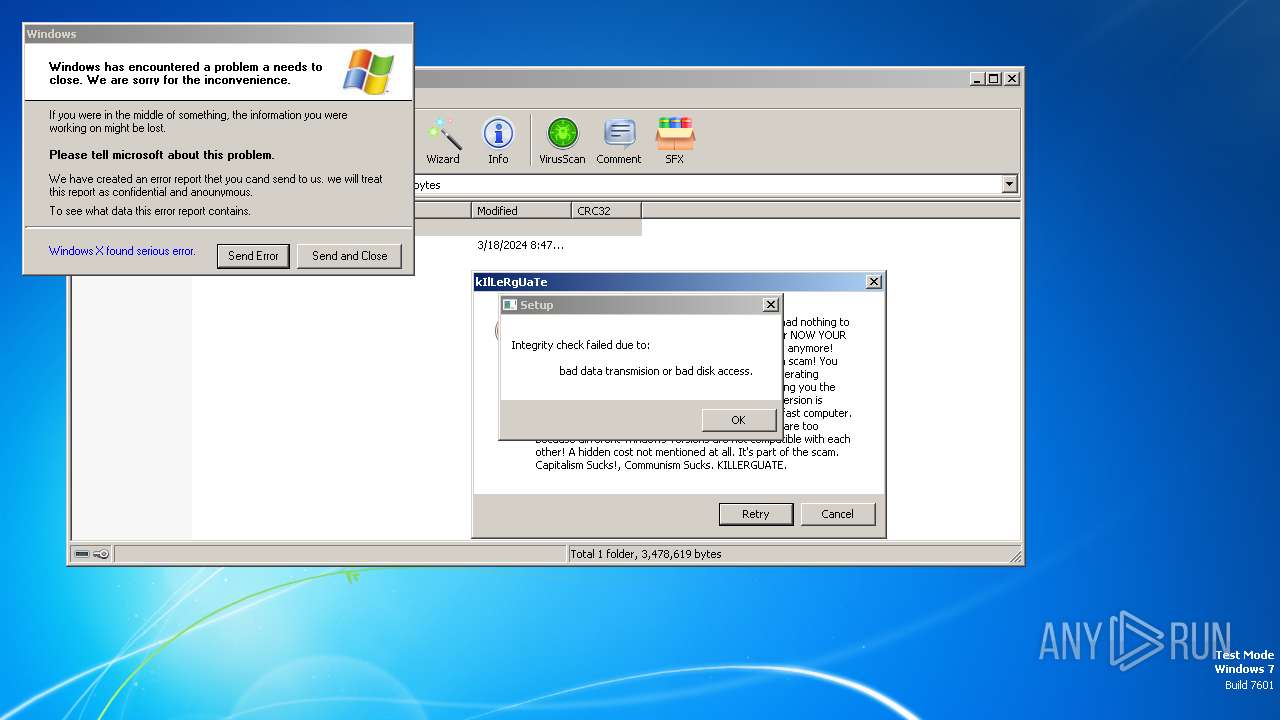
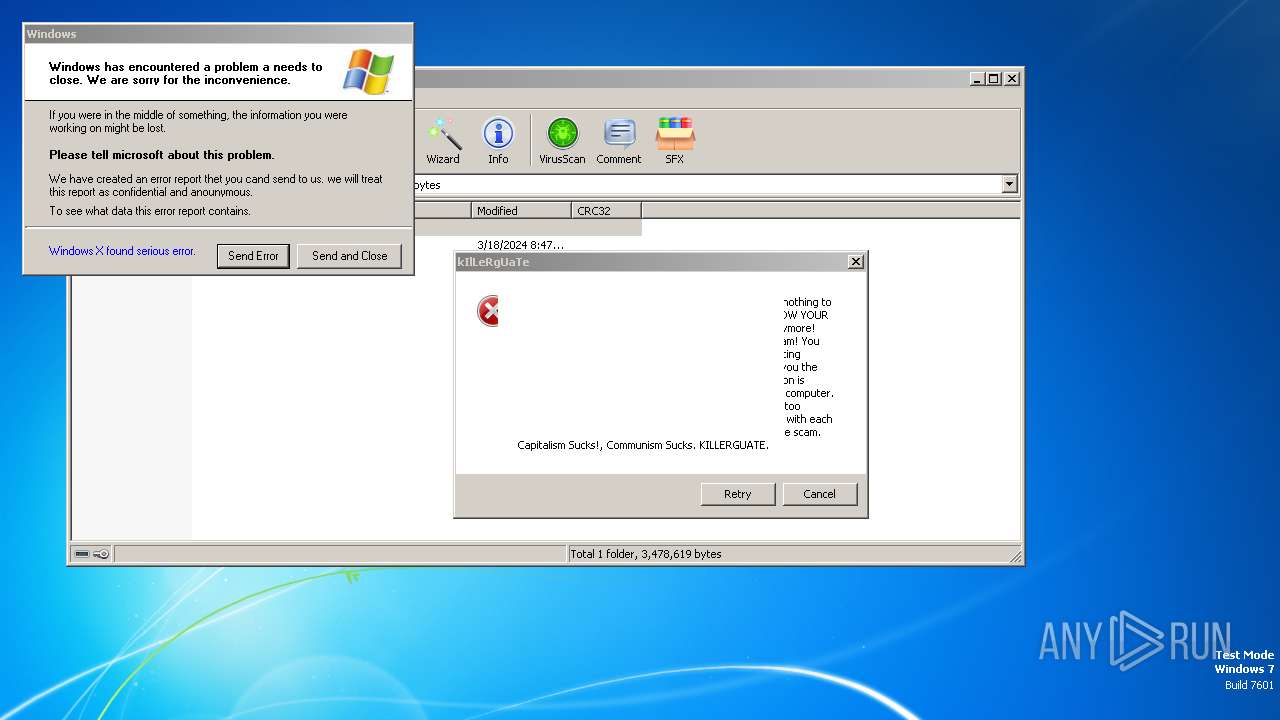
Executes application which crashes
- Duksten.exe (PID: 2096)
INFO
Checks supported languages
- Anap.a.exe (PID: 2244)
- Brontok.exe (PID: 680)
- Duksten.exe (PID: 2096)
- Gruel.a.exe (PID: 3028)
- Lacon.exe (PID: 1728)
- Kiray.exe (PID: 3088)
- Maldal.a.exe (PID: 1780)
- MsWorld.exe (PID: 924)
- Winevar.exe (PID: 1172)
- Yarner.a.exe (PID: 3264)
- Prolin.exe (PID: 2828)
- WIN68D2.pif (PID: 2612)
- winlogon.exe (PID: 2444)
- smss.exe (PID: 1040)
- Gruel.a.exe (PID: 292)
- services.exe (PID: 1092)
- lsass.exe (PID: 1740)
Manual execution by a user
- Anap.a.exe (PID: 2244)
- Brontok.exe (PID: 680)
- Duksten.exe (PID: 2096)
- Gruel.a.exe (PID: 3028)
- Lacon.exe (PID: 1728)
- Kiray.exe (PID: 3088)
- Maldal.a.exe (PID: 1780)
- MeltingScreen.exe (PID: 2020)
- MsWorld.exe (PID: 924)
- MyPics.a.exe (PID: 2308)
- Nyxem.E.exe (PID: 2616)
- Trood.a.exe (PID: 2736)
- Winevar.exe (PID: 1172)
- Yarner.a.exe (PID: 3264)
- Prolin.exe (PID: 2828)
Reads the machine GUID from the registry
- Brontok.exe (PID: 680)
- Kiray.exe (PID: 3088)
- Gruel.a.exe (PID: 3028)
- MsWorld.exe (PID: 924)
- Lacon.exe (PID: 1728)
- Maldal.a.exe (PID: 1780)
- Prolin.exe (PID: 2828)
- WIN68D2.pif (PID: 2612)
- Yarner.a.exe (PID: 3264)
- smss.exe (PID: 1040)
- winlogon.exe (PID: 2444)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3500)
Create files in a temporary directory
- Brontok.exe (PID: 680)
- Gruel.a.exe (PID: 3028)
- Kiray.exe (PID: 3088)
- Maldal.a.exe (PID: 1780)
- MsWorld.exe (PID: 924)
- Prolin.exe (PID: 2828)
- winlogon.exe (PID: 2444)
- smss.exe (PID: 1040)
Reads the computer name
- Brontok.exe (PID: 680)
- Kiray.exe (PID: 3088)
- Lacon.exe (PID: 1728)
- MsWorld.exe (PID: 924)
- Prolin.exe (PID: 2828)
- Winevar.exe (PID: 1172)
- Yarner.a.exe (PID: 3264)
- WIN68D2.pif (PID: 2612)
- winlogon.exe (PID: 2444)
- smss.exe (PID: 1040)
Creates files or folders in the user directory
- Brontok.exe (PID: 680)
- Lacon.exe (PID: 1728)
- smss.exe (PID: 1040)
Checks proxy server information
- WIN68D2.pif (PID: 2612)
Reads the Internet Settings
- explorer.exe (PID: 3688)
Reads security settings of Internet Explorer
- explorer.exe (PID: 3688)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 45 |
|---|---|
| ZipBitFlag: | 0x0800 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:03:18 20:47:46 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | 2 |
| ZipUncompressedSize: | - |
| ZipFileName: | Email-Worm/ |
Total processes
102
Monitored processes
33
Malicious processes
9
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | C:\Windows\system32\WerFault.exe -u -p 2096 -s 8 | C:\Windows\System32\WerFault.exe | — | Duksten.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 3221226091 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 292 | "C:\Users\admin\Desktop\Email-Worm\Email-Worm\Gruel.a.exe" C:\Windows\eksplorasi.pif | C:\Users\admin\Desktop\Email-Worm\Email-Worm\Gruel.a.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Integrity Level: HIGH Exit code: 1073807364 Version: 1.00 Modules
| |||||||||||||||
| 332 | C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE -Embedding | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Outlook Exit code: 3221226091 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 680 | "C:\Users\admin\Desktop\Email-Worm\Email-Worm\Brontok.exe" | C:\Users\admin\Desktop\Email-Worm\Email-Worm\Brontok.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 924 | "C:\Users\admin\Desktop\Email-Worm\Email-Worm\MsWorld.exe" | C:\Users\admin\Desktop\Email-Worm\Email-Worm\MsWorld.exe | explorer.exe | ||||||||||||
User: admin Company: Macromedia, Inc. Integrity Level: HIGH Description: Flash Player 5.0 r30 Exit code: 0 Version: 5.00 Modules
| |||||||||||||||
| 1040 | C:\Users\admin\AppData\Local\smss.exe | C:\Users\admin\AppData\Local\smss.exe | Brontok.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1073807364 Modules
| |||||||||||||||
| 1092 | C:\Users\admin\AppData\Local\services.exe | C:\Users\admin\AppData\Local\services.exe | — | smss.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 3221226091 Modules
| |||||||||||||||
| 1172 | "C:\Users\admin\Desktop\Email-Worm\Email-Worm\Winevar.exe" | C:\Users\admin\Desktop\Email-Worm\Email-Worm\Winevar.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1384 | C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE -Embedding | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Outlook Exit code: 3221226091 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 1728 | "C:\Users\admin\Desktop\Email-Worm\Email-Worm\Lacon.exe" | C:\Users\admin\Desktop\Email-Worm\Email-Worm\Lacon.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1073807364 Version: 1.00 Modules
| |||||||||||||||
Total events
6 965
Read events
6 864
Write events
97
Delete events
4
Modification events
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Email-Worm.zip | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
687
Suspicious files
4
Text files
2
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3500 | WinRAR.exe | C:\Users\admin\Desktop\Email-Worm\Email-Worm\Happy99.exe | executable | |
MD5:02DD0EAA9649A11E55FA5467FA4B8EF8 | SHA256:4EBE3E1AF5E147C580ECCE052FE7D7D0219D5E5A2F5E6D8A7F7291735923DB18 | |||
| 3500 | WinRAR.exe | C:\Users\admin\Desktop\Email-Worm\Email-Worm\MeltingScreen.exe | executable | |
MD5:4784E42C3B15D1A141A5E0C8ABC1205C | SHA256:9D355E4F9A51536B05269F696B304859155985957BA95EB575F3F38C599D913C | |||
| 3500 | WinRAR.exe | C:\Users\admin\Desktop\Email-Worm\Email-Worm\Duksten.exe | executable | |
MD5:900EBFF3E658825F828AB95B30FAD2E7 | SHA256:CAEC6E664B3CFF5717DD2EFEA8DCD8715ABDCFE7F611456BE7009771F22A8F50 | |||
| 3500 | WinRAR.exe | C:\Users\admin\Desktop\Email-Worm\Email-Worm\Axam.a.exe | executable | |
MD5:0FBF8022619BA56C545B20D172BF3B87 | SHA256:4AE7D63EC497143C2ACDE1BA79F1D9EED80086A420B6F0A07B1E2917DA0A6C74 | |||
| 3500 | WinRAR.exe | C:\Users\admin\Desktop\Email-Worm\Email-Worm\Funsoul.exe | executable | |
MD5:A13A4DB860D743A088EF7AB9BACB4DDA | SHA256:69EE59CEE5A1D39739D935701CFA917F75787B29E0B9BDA9ADA9E2642ADE434C | |||
| 3500 | WinRAR.exe | C:\Users\admin\Desktop\Email-Worm\Email-Worm\Lacon.exe | executable | |
MD5:CB0F7B3FD927CF0D0BA36302E6F9AF86 | SHA256:9B3F73A12A793D1648F3209E1E3F10BBB548B1EC21D53B8AC060B7B95AE4EF1F | |||
| 3500 | WinRAR.exe | C:\Users\admin\Desktop\Email-Worm\Email-Worm\Prolin.exe | executable | |
MD5:65EEB8A0FCE412D7F236F8348357D1C0 | SHA256:DB0C7E3029FB2A048E7A3E74C9CBF3E8BCEC06288B5EAFAC5AAE678D8663BFFC | |||
| 3500 | WinRAR.exe | C:\Users\admin\Desktop\Email-Worm\Email-Worm\Winevar.exe | executable | |
MD5:E79D0B1A342712EA9B96104086149D65 | SHA256:E68EBECD17BB8E91079BD4FE9BD24059A2BC007B4BAAC477127EDA7C5D5C6706 | |||
| 3500 | WinRAR.exe | C:\Users\admin\Desktop\Email-Worm\Email-Worm\Quamo.exe | executable | |
MD5:A1F722324492FDA51077449EC2DB2827 | SHA256:FC2CED1D89845DCFAE55B6E854CD0E622FDF98BAEEB4A67A60852ECD1212F93B | |||
| 3500 | WinRAR.exe | C:\Users\admin\Desktop\Email-Worm\Email-Worm\Klez.e.exe | executable | |
MD5:F2DB87B351770E5995E9FCAAD47D9591 | SHA256:3113FA9A3CF00ED423A2C686A2FFB19586F6A047747DE65A93436A7DCA8FCFA7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
5
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.symantec.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Duksten.exe | Error - |
Duksten.exe | RtlWerpReportException failed with status code :-1073741823. Will try to launch the process directly |
Duksten.exe |