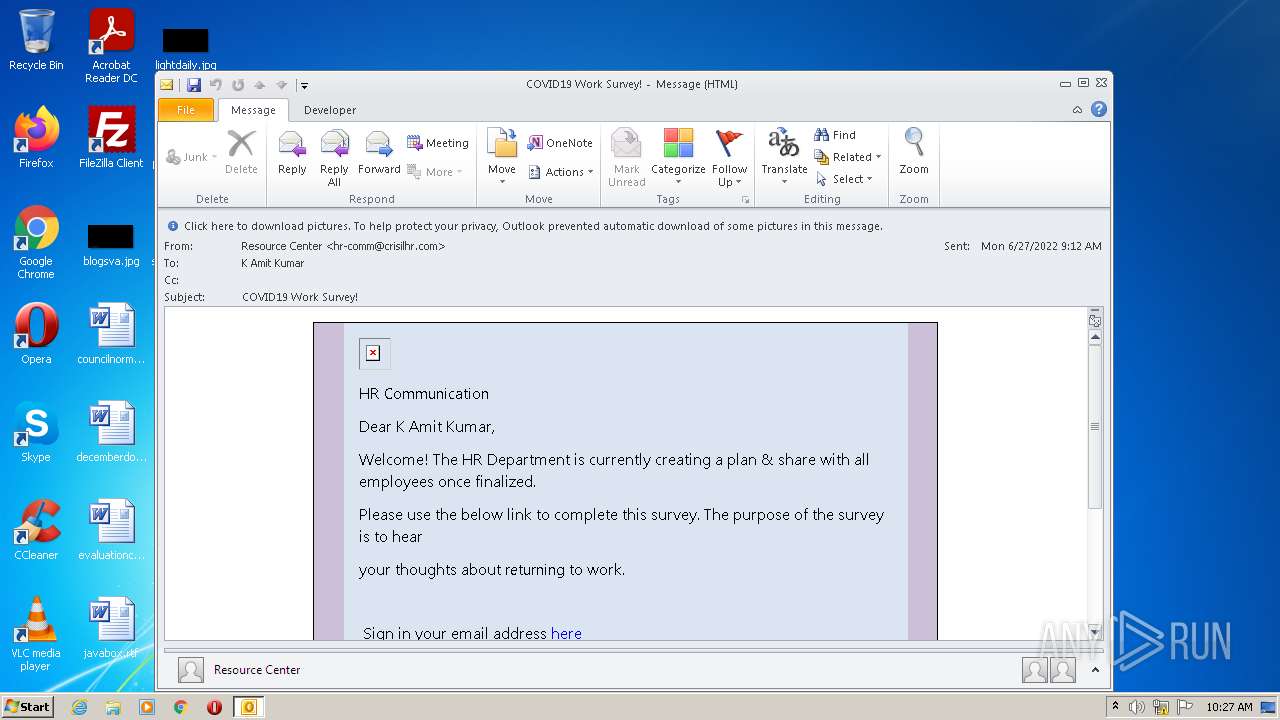
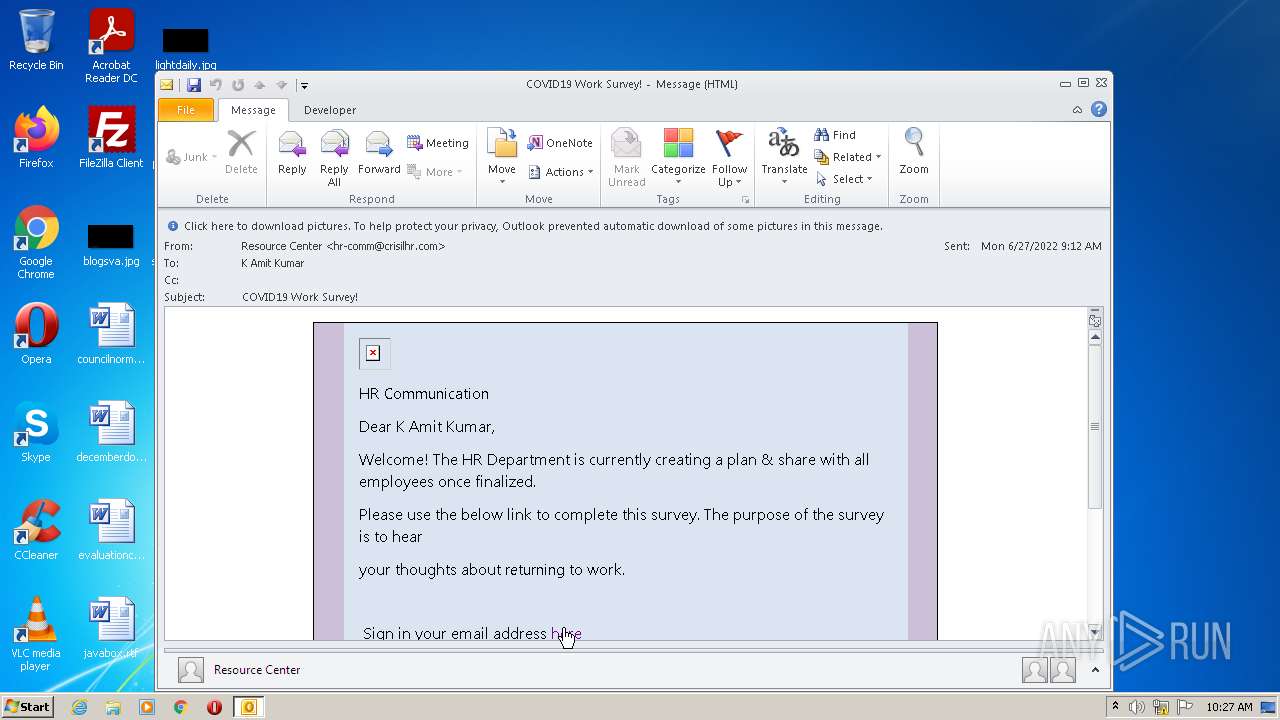
| File name: | COVID19 Work Survey!.msg |
| Full analysis: | https://app.any.run/tasks/b833c95c-26b4-4d0c-b729-ae45b48657d4 |
| Verdict: | Malicious activity |
| Analysis date: | June 27, 2022, 09:27:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | EE6DD0F2D6E898F9FFFA946CF423FA10 |
| SHA1: | 645553C0B249FE8026FD2BF5A0AA7C3142536984 |
| SHA256: | 631CD9F9C43A2DE9FD7A3DF81F8E005B028127F81A7A3A41A8E52DE9CF56232D |
| SSDEEP: | 768:dlI3TeBss3fXeCgSKDM0FZuWgJUUWsKtW2K3fXqRYLRqxM:DDCOyZuDPWVWlI2q |
MALICIOUS
Unusual execution from Microsoft Office
- OUTLOOK.EXE (PID: 1000)
SUSPICIOUS
Starts Internet Explorer
- OUTLOOK.EXE (PID: 1000)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3996)
INFO
Checks supported languages
- OUTLOOK.EXE (PID: 1000)
- iexplore.exe (PID: 3996)
- iexplore.exe (PID: 836)
Reads the computer name
- OUTLOOK.EXE (PID: 1000)
- iexplore.exe (PID: 3996)
- iexplore.exe (PID: 836)
Searches for installed software
- OUTLOOK.EXE (PID: 1000)
Creates files in the user directory
- OUTLOOK.EXE (PID: 1000)
Reads settings of System Certificates
- iexplore.exe (PID: 3996)
- iexplore.exe (PID: 836)
Application launched itself
- iexplore.exe (PID: 836)
Changes internet zones settings
- iexplore.exe (PID: 836)
Checks Windows Trust Settings
- iexplore.exe (PID: 836)
- iexplore.exe (PID: 3996)
Reads internet explorer settings
- iexplore.exe (PID: 3996)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 1000)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
40
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
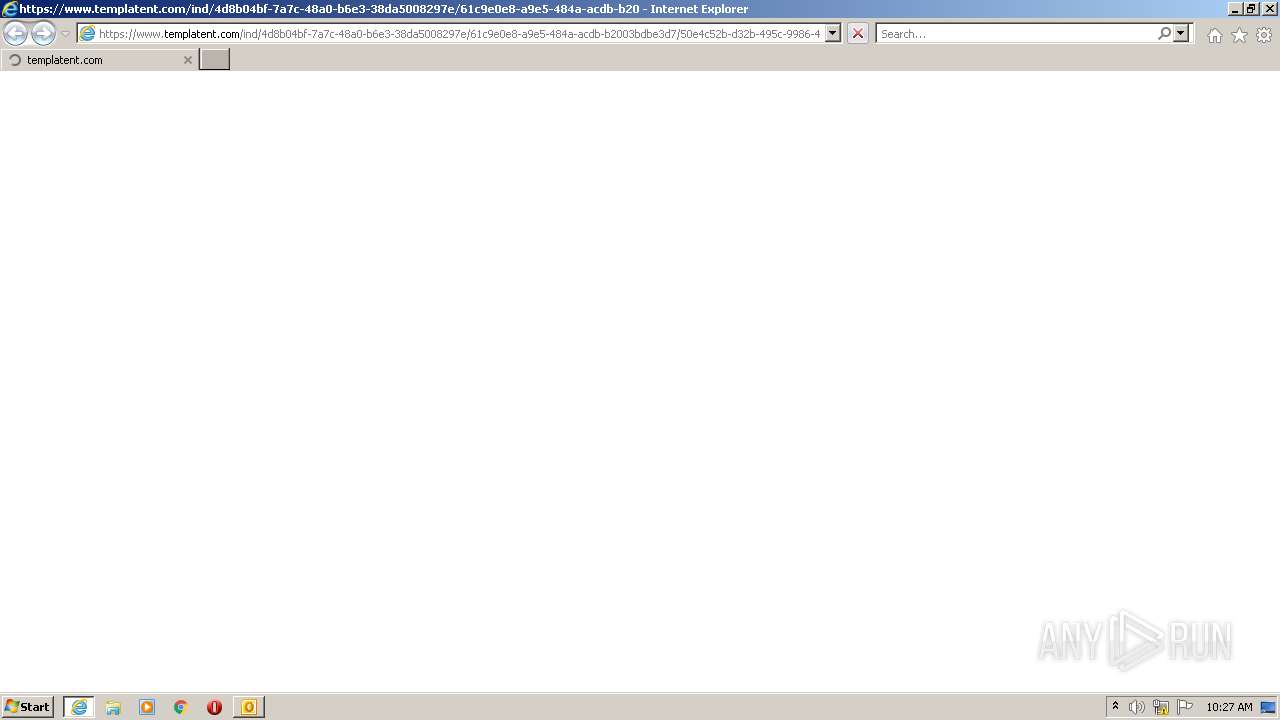
| 836 | "C:\Program Files\Internet Explorer\iexplore.exe" https://www.templatent.com/ind/4d8b04bf-7a7c-48a0-b6e3-38da5008297e/61c9e0e8-a9e5-484a-acdb-b2003bdbe3d7/50e4c52b-d32b-495c-9986-4f32616c57eb/landing?id=bXp1ZjUyUnliaGtGMDVDNXZnRzlwSVpsRmxVdkt5TXJoamJoYkxrWldLU1Zra1lvZVo2WVBVYkRYeDdOVkVRL0NSWms1WG5FWnZKVUp6UlVvazBPeThIZFpQaWNTM2lUMURVOGdYTU9ja0o0UUVKZDRuT0lGN01lOGhNTGhBSlB6RVBVNENDNUNVZ201UVlLa0ppOXk4MVJZdEwzNlVHOXR1WXdPbHN4bzRkY3g2RENYYUMxWVE4dS9xbFJUV091L3ZNWXJDOXpaNTRMUnpRTE50UW9tbks5eU5TVmc4dnVPdGs5bG1HTDdjMmtRUS9PUWNCenljL1pid09SdTVWVkpJYVVOejFOL0oxd1NvWTF5cGpPUDRjcHVNaDBjZjI3b0RPR204UGdRRyttMWs5d0VJNHp6cHAzZ3RNNlVZSkZkU21SL2p1QW1uYitrV0lQNDJTVXpnPT0 | C:\Program Files\Internet Explorer\iexplore.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1000 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\Desktop\COVID19 Work Survey!.msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 3996 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:836 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
14 636
Read events
13 938
Write events
678
Delete events
20
Modification events
| (PID) Process: | (1000) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (1000) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (1000) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (1000) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (1000) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (1000) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (1000) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (1000) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (1000) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (1000) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
0
Suspicious files
5
Text files
13
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1000 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR94F3.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1000 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst | — | |
MD5:— | SHA256:— | |||
| 1000 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 1000 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 1000 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\{3E7451A9-3A2F-4322-BABD-62D008E4B424}\{1C306CB1-771E-4B4B-A902-86E897877F5B}.png | image | |
MD5:4C61C12EDBC453D7AE184976E95258E1 | SHA256:296526F9A716C1AA91BA5D6F69F0EB92FDF79C2CB2CFCF0CEB22B7CCBC27035F | |||
| 1000 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_RssRule_2_7C0E32BD98333344B72465337C884139.dat | xml | |
MD5:D8B37ED0410FB241C283F72B76987F18 | SHA256:31E68049F6B7F21511E70CD7F2D95B9CF1354CF54603E8F47C1FC40F40B7A114 | |||
| 836 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | der | |
MD5:— | SHA256:— | |||
| 836 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:— | SHA256:— | |||
| 836 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 1000 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_Calendar_2_03380599F938C242A5C83F2B5ABAEB88.dat | xml | |
MD5:B21ED3BD946332FF6EBC41A87776C6BB | SHA256:B1AAC4E817CD10670B785EF8E5523C4A883F44138E50486987DC73054A46F6F4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
19
DNS requests
11
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1000 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
3996 | iexplore.exe | GET | 200 | 41.63.96.128:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?9dfc310853302a4f | ZA | compressed | 4.70 Kb | whitelisted |
836 | iexplore.exe | GET | 200 | 41.63.96.128:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?0313db5469b36e55 | ZA | compressed | 4.70 Kb | whitelisted |
836 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
3996 | iexplore.exe | GET | 200 | 13.107.40.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBQN1VoiX40jVOMldh7uDThi9DqeewQU1cFnOsKjnfR3UltZEjgp5lVou6UCEzMANPAzk2JZiyvmkdgAAAA08DM%3D | US | der | 1.74 Kb | whitelisted |
3996 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEALnkXH7gCHpP%2BLZg4NMUMA%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3996 | iexplore.exe | 13.107.227.45:443 | www.templatent.com | Microsoft Corporation | US | suspicious |
3996 | iexplore.exe | 41.63.96.128:80 | ctldl.windowsupdate.com | Limelight Networks, Inc. | ZA | suspicious |
836 | iexplore.exe | 41.63.96.128:80 | ctldl.windowsupdate.com | Limelight Networks, Inc. | ZA | suspicious |
836 | iexplore.exe | 131.253.33.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
836 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3996 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1000 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
836 | iexplore.exe | 13.107.22.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
836 | iexplore.exe | 152.199.19.161:443 | r20swj13mr.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3996 | iexplore.exe | 13.107.219.45:443 | www.templatent.com | Microsoft Corporation | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
www.templatent.com |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
oneocsp.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |