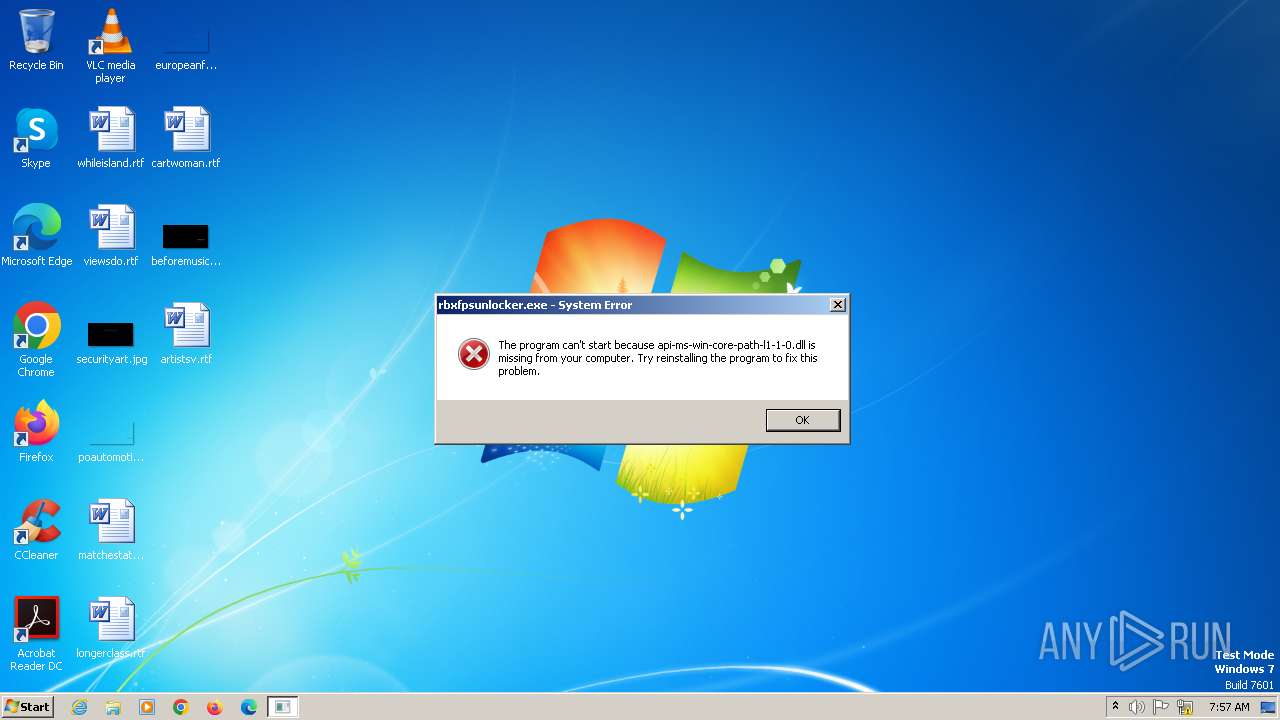
| File name: | rbxfpsunlocker.exe |
| Full analysis: | https://app.any.run/tasks/10b2da04-171e-40e9-9493-47cf24401378 |
| Verdict: | Malicious activity |
| Analysis date: | October 29, 2023, 07:57:08 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | 559E4B863C9736D6DD81B67A1C7C51E9 |
| SHA1: | 351CD63B60A1F570EFC1A4D662A8D22C3A4D3C0E |
| SHA256: | 6314F6518CD5779E9BA758702432180DE55F69E2963601D77A57799569332FFB |
| SSDEEP: | 98304:3jsVP1nzPnvEAEZGPBzJx7WQizOMAu8PHieEM1SBkyZiJYfpx7AHHWWmOOei8yRS:KOjcYfzPuB6ERaql+X7aCrMO |
MALICIOUS
Loads dropped or rewritten executable
- rbxfpsunlocker.exe (PID: 1584)
Drops the executable file immediately after the start
- rbxfpsunlocker.exe (PID: 2536)
SUSPICIOUS
The process drops C-runtime libraries
- rbxfpsunlocker.exe (PID: 2536)
Application launched itself
- rbxfpsunlocker.exe (PID: 2536)
Loads Python modules
- rbxfpsunlocker.exe (PID: 1584)
Process drops legitimate windows executable
- rbxfpsunlocker.exe (PID: 2536)
INFO
Checks supported languages
- rbxfpsunlocker.exe (PID: 2536)
- rbxfpsunlocker.exe (PID: 1584)
Reads the computer name
- rbxfpsunlocker.exe (PID: 2536)
Create files in a temporary directory
- rbxfpsunlocker.exe (PID: 2536)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2023:09:10 07:15:27+02:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.32 |
| CodeSize: | 165888 |
| InitializedDataSize: | 154112 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xafa0 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
Total processes
32
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1584 | "C:\Users\admin\AppData\Local\Temp\rbxfpsunlocker.exe" | C:\Users\admin\AppData\Local\Temp\rbxfpsunlocker.exe | — | rbxfpsunlocker.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2536 | "C:\Users\admin\AppData\Local\Temp\rbxfpsunlocker.exe" | C:\Users\admin\AppData\Local\Temp\rbxfpsunlocker.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
14
Read events
14
Write events
0
Delete events
0
Modification events
Executable files
89
Suspicious files
6
Text files
16
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2536 | rbxfpsunlocker.exe | C:\Users\admin\AppData\Local\Temp\_MEI25362\Crypto\Cipher\_pkcs1_decode.pyd | executable | |
MD5:3EFFD59CD95B6706C1F2DD661AA943FC | SHA256:4C29950A9EDEDBBC24A813F8178723F049A529605EF6D35F16C7955768AACE9E | |||
| 2536 | rbxfpsunlocker.exe | C:\Users\admin\AppData\Local\Temp\_MEI25362\Crypto\Cipher\_chacha20.pyd | executable | |
MD5:ED1BBDC7CC945DA2D1F5A914987EB885 | SHA256:1EECE2F714DC1F520D0608F9F71E692F5B269930603F8AFC330118EA38F16005 | |||
| 2536 | rbxfpsunlocker.exe | C:\Users\admin\AppData\Local\Temp\_MEI25362\Crypto\Cipher\_ARC4.pyd | executable | |
MD5:D9F2264898AAAA9EF6152A1414883D0F | SHA256:836CBA3B83B00427430FE6E1C4E45790616BC85C57DBD6E6D5B6930A9745B715 | |||
| 2536 | rbxfpsunlocker.exe | C:\Users\admin\AppData\Local\Temp\_MEI25362\Crypto\Cipher\_raw_aesni.pyd | executable | |
MD5:DCD2F68680E2FB83E9FEFA18C7B4B3E0 | SHA256:D63F63985356B7D2E0E61E7968720FB72DC6B57D73BED4F337E372918078F946 | |||
| 2536 | rbxfpsunlocker.exe | C:\Users\admin\AppData\Local\Temp\_MEI25362\Crypto\Cipher\_raw_aes.pyd | executable | |
MD5:671100B821EB357CEB5A4C5FF86BC31A | SHA256:803E46354CDAB4AF6FF289E98DE9C56B5B08E3E9AD5F235D5A282005FA9F2D50 | |||
| 2536 | rbxfpsunlocker.exe | C:\Users\admin\AppData\Local\Temp\_MEI25362\Crypto\Cipher\_raw_arc2.pyd | executable | |
MD5:3F5FD606893B3DE6116D4A185E713CA3 | SHA256:0898CDE5FCCFA86E2423CDF627A3745B1F59BB30DFEF0DD9423926D4167F9F82 | |||
| 2536 | rbxfpsunlocker.exe | C:\Users\admin\AppData\Local\Temp\_MEI25362\Crypto\Cipher\_raw_ecb.pyd | executable | |
MD5:F94726F6B584647142EA6D5818B0349D | SHA256:B98297FD093E8AF7FCA2628C23A9916E767540C3C6FA8894394B5B97FFEC3174 | |||
| 2536 | rbxfpsunlocker.exe | C:\Users\admin\AppData\Local\Temp\_MEI25362\Crypto\Cipher\_raw_ctr.pyd | executable | |
MD5:D67F83D1482D9600AC012868FB49D16E | SHA256:AA463CD4D0B4BBD4159650D66C11A699B23775BF92455FB58A2206B932A65FEC | |||
| 2536 | rbxfpsunlocker.exe | C:\Users\admin\AppData\Local\Temp\_MEI25362\Crypto\Cipher\_raw_eksblowfish.pyd | executable | |
MD5:E5021B9925A53B20946C93B5BF686647 | SHA256:87922D0EE99AF46080AFD4BAA2F96219FA195731C0745FCB9C7789338ECC778F | |||
| 2536 | rbxfpsunlocker.exe | C:\Users\admin\AppData\Local\Temp\_MEI25362\Crypto\Cipher\_raw_cfb.pyd | executable | |
MD5:FF64FD41B794E0EF76A9EEAE1835863C | SHA256:5D2D1A5F79B44F36AC87D9C6D886404D9BE35D1667C4B2EB8AAB59FB77BF8BAC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
6
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1956 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
324 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |