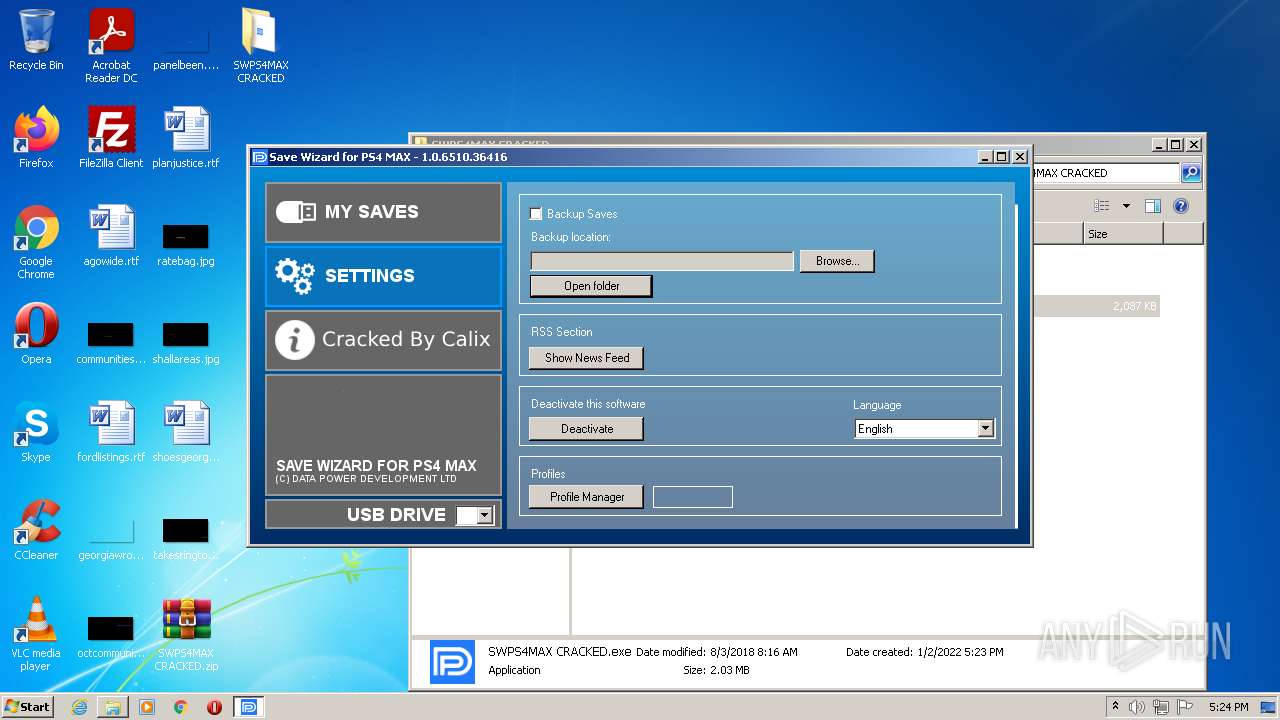
| File name: | SWPS4MAX CRACKED.zip |
| Full analysis: | https://app.any.run/tasks/ae6f8581-667c-472d-be30-fff57320ac63 |
| Verdict: | Malicious activity |
| Analysis date: | January 02, 2022, 17:23:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 5DF513AA3611A7410EB00FAC75FBAFF8 |
| SHA1: | 469DBD51D2E7DDD5A73D515A0DBEFFE0CBAECDAD |
| SHA256: | 6311D08123F4D9B95FFD7F6083BBB16C8FE4DCF24D72291E976DDEE245102420 |
| SSDEEP: | 49152:3HpyqemW663O5+xj1xfx5Tj8z91cyx9IXGToSuraJTh5R3KxTPnTtxbd0rDK:3HoveG1txS91pxCGT9JF5MTPnZxEDK |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3712)
Application was dropped or rewritten from another process
- SWPS4MAX CRACKED.exe (PID: 3544)
- SWPS4MAX CRACKED.exe (PID: 2652)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 3636)
- SWPS4MAX CRACKED.exe (PID: 3544)
- SWPS4MAX CRACKED.exe (PID: 2652)
Reads the computer name
- WinRAR.exe (PID: 3636)
- SWPS4MAX CRACKED.exe (PID: 3544)
- SWPS4MAX CRACKED.exe (PID: 2652)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3636)
Reads Environment values
- SWPS4MAX CRACKED.exe (PID: 3544)
- SWPS4MAX CRACKED.exe (PID: 2652)
Starts Internet Explorer
- SWPS4MAX CRACKED.exe (PID: 2652)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3344)
INFO
Manual execution by user
- SWPS4MAX CRACKED.exe (PID: 3544)
- SWPS4MAX CRACKED.exe (PID: 2652)
Checks supported languages
- explorer.exe (PID: 1512)
- iexplore.exe (PID: 1872)
- iexplore.exe (PID: 3344)
Reads the computer name
- explorer.exe (PID: 1512)
- iexplore.exe (PID: 1872)
- iexplore.exe (PID: 3344)
Application launched itself
- iexplore.exe (PID: 1872)
Drops Coronavirus (possible) decoy
- iexplore.exe (PID: 3344)
Changes internet zones settings
- iexplore.exe (PID: 1872)
Reads the date of Windows installation
- iexplore.exe (PID: 1872)
Checks Windows Trust Settings
- iexplore.exe (PID: 3344)
Reads settings of System Certificates
- iexplore.exe (PID: 3344)
Reads internet explorer settings
- iexplore.exe (PID: 3344)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | SWPS4MAX CRACKED.exe |
|---|---|
| ZipUncompressedSize: | 2137088 |
| ZipCompressedSize: | 1190386 |
| ZipCRC: | 0x3c0dfa61 |
| ZipModifyDate: | 2018:08:03 08:16:10 |
| ZipCompression: | Deflated |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
45
Monitored processes
7
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1512 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | SWPS4MAX CRACKED.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
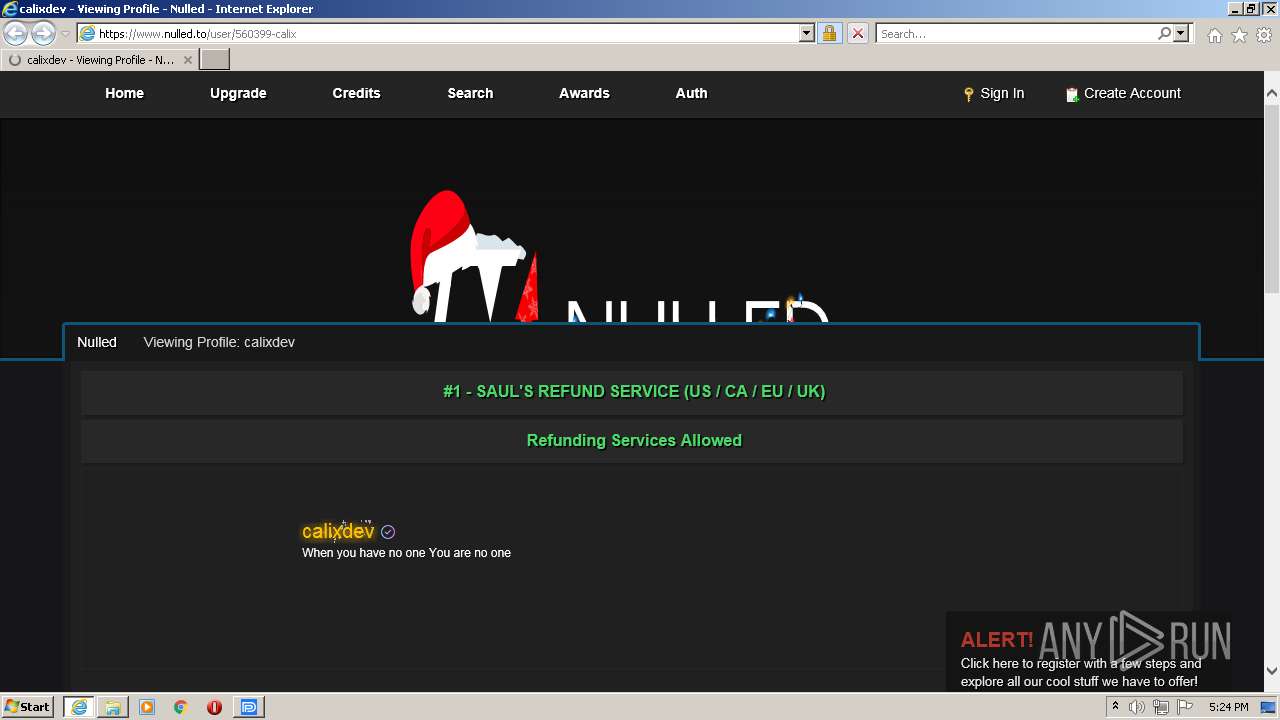
| 1872 | "C:\Program Files\Internet Explorer\iexplore.exe" https://www.nulled.to/user/560399-calix | C:\Program Files\Internet Explorer\iexplore.exe | — | SWPS4MAX CRACKED.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
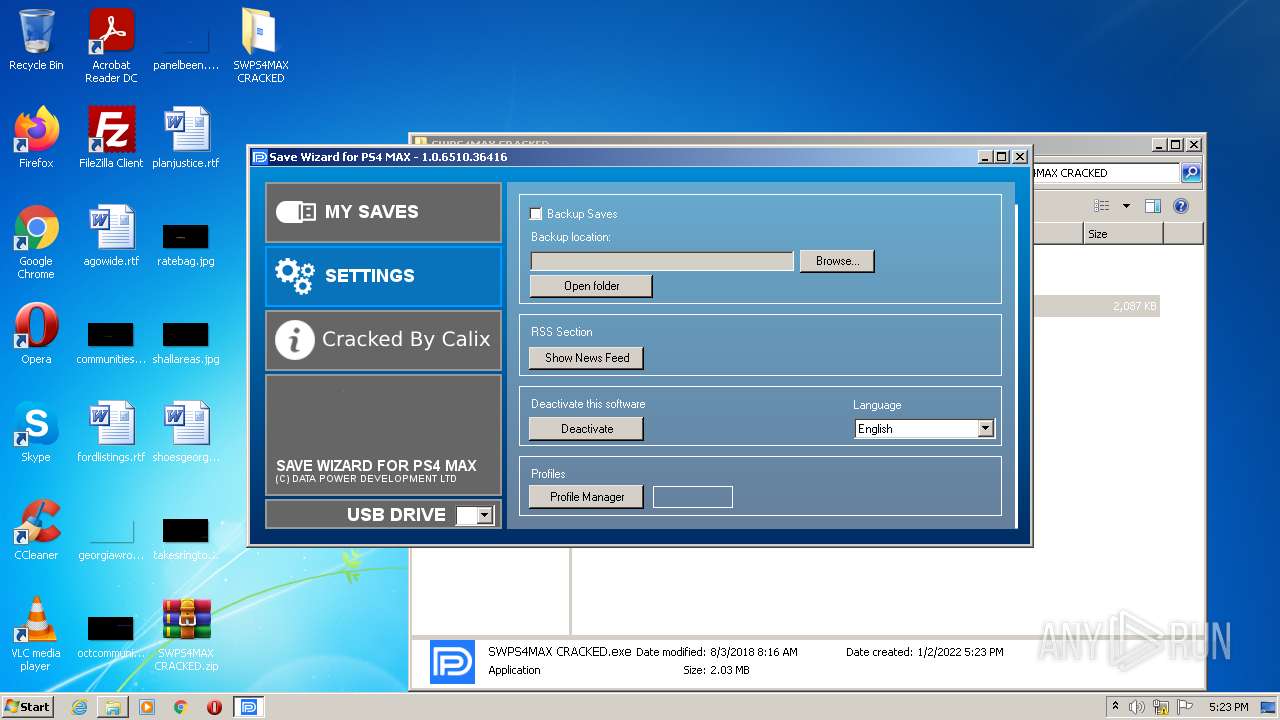
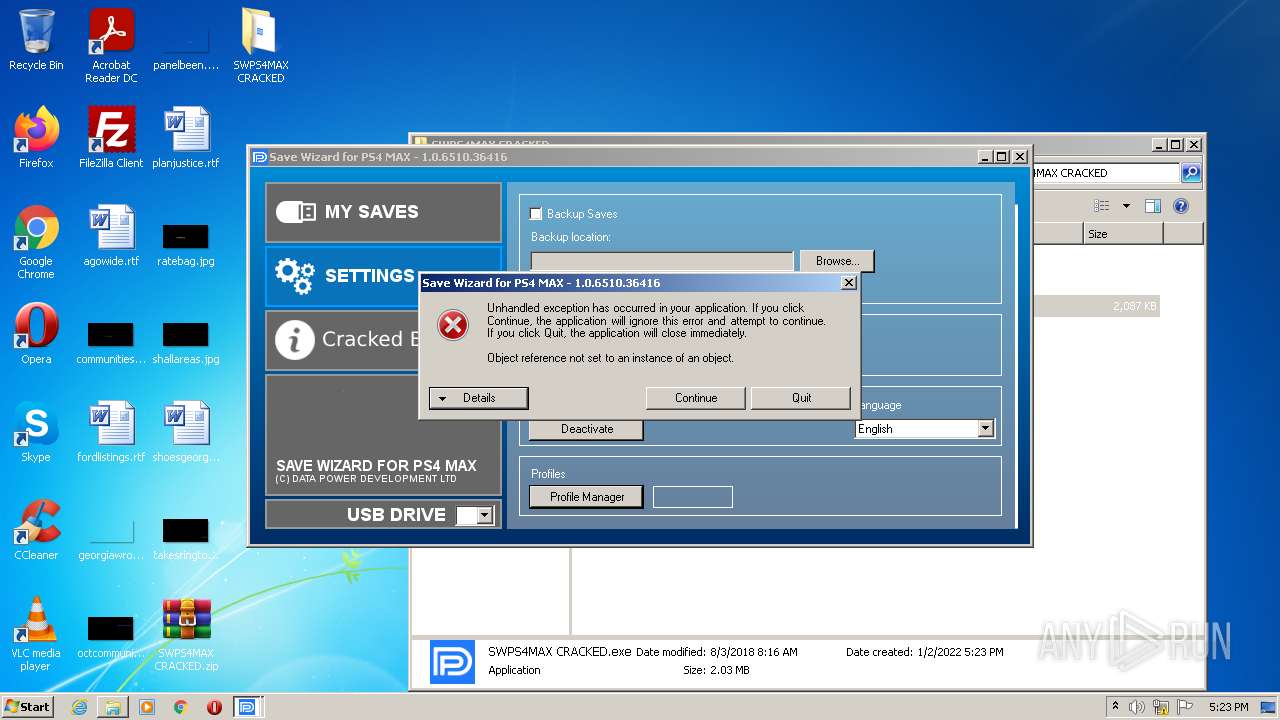
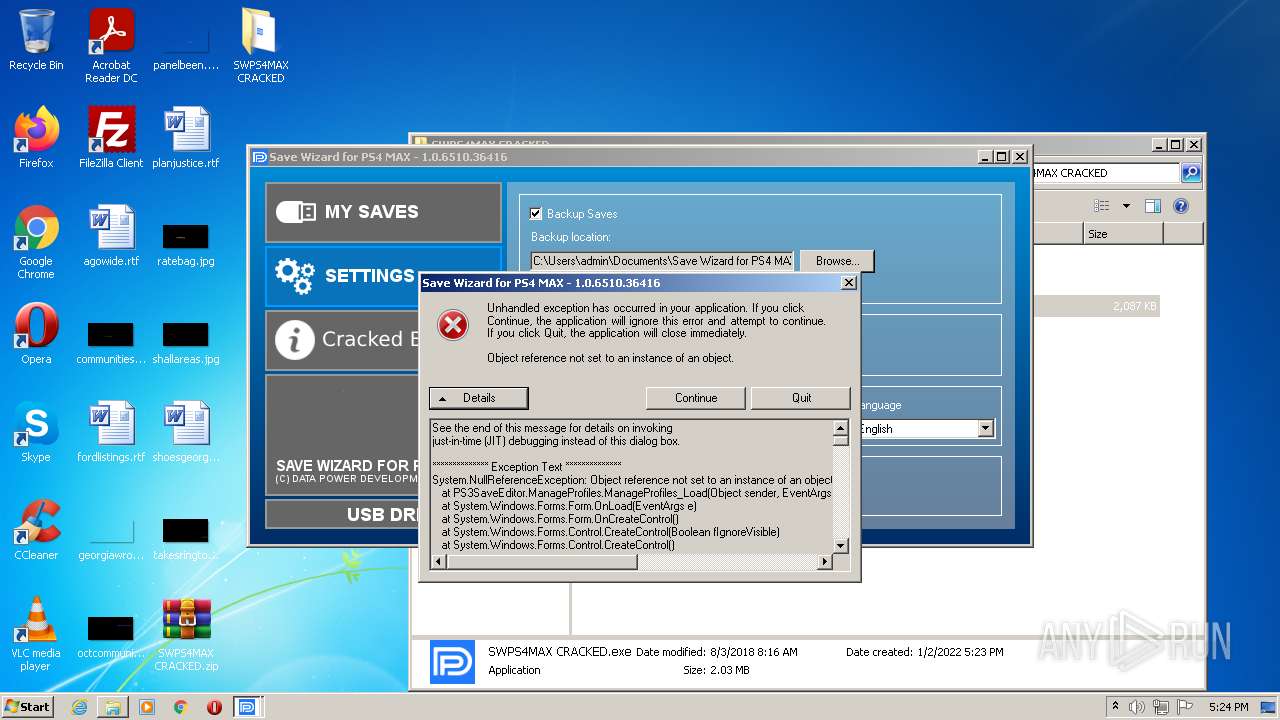
| 2652 | "C:\Users\admin\Desktop\SWPS4MAX CRACKED\SWPS4MAX CRACKED.exe" | C:\Users\admin\Desktop\SWPS4MAX CRACKED\SWPS4MAX CRACKED.exe | Explorer.EXE | ||||||||||||
User: admin Company: Datapower Integrity Level: MEDIUM Description: Save Wizard for PS4 MAX Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3344 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1872 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3544 | "C:\Users\admin\Desktop\SWPS4MAX CRACKED\SWPS4MAX CRACKED.exe" | C:\Users\admin\Desktop\SWPS4MAX CRACKED\SWPS4MAX CRACKED.exe | Explorer.EXE | ||||||||||||
User: admin Company: Datapower Integrity Level: MEDIUM Description: Save Wizard for PS4 MAX Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3636 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\SWPS4MAX CRACKED.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3712 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe2_ Global\UsGthrCtrlFltPipeMssGthrPipe2 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
Total events
11 867
Read events
11 758
Write events
108
Delete events
1
Modification events
| (PID) Process: | (3636) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3636) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3636) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3636) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3636) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3636) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\SWPS4MAX CRACKED.zip | |||
| (PID) Process: | (3636) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3636) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3636) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3636) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
3
Suspicious files
10
Text files
85
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3636 | WinRAR.exe | C:\Users\admin\Desktop\SWPS4MAX CRACKED\zh-Hans\SaveWizard.resources.dll | executable | |
MD5:— | SHA256:— | |||
| 3344 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:— | SHA256:— | |||
| 3344 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | der | |
MD5:— | SHA256:— | |||
| 3636 | WinRAR.exe | C:\Users\admin\Desktop\SWPS4MAX CRACKED\zh-Hant\SaveWizard.resources.dll | executable | |
MD5:— | SHA256:— | |||
| 3344 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\560399-calix[1].htm | html | |
MD5:— | SHA256:— | |||
| 3344 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3636 | WinRAR.exe | C:\Users\admin\Desktop\SWPS4MAX CRACKED\SWPS4MAX CRACKED.exe | executable | |
MD5:378E6C74038795994120B1F2F50B9FE4 | SHA256:132AE685763C5B96D3647C2B4FABB35A6C124C419BDF3212F5D1831A6904A533 | |||
| 3344 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
| 3344 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\ipb.lang[1].js | text | |
MD5:97861C0947576766E7892E6DB8466794 | SHA256:2069288F5210231977491F1B4E14AFE9C89EFFDA2E48E7CDF903B9801EECB3CA | |||
| 3344 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\api[1].js | text | |
MD5:6C6281C15CBC981BC05942BAC40BCD7E | SHA256:0D3118E306C6A26F1D2EFCB698984E6922C5E7E155C94A84760E36E5592A3C11 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
36
DNS requests
16
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3544 | SWPS4MAX CRACKED.exe | POST | — | 14.136.218.90:8082 | http://ps4ws2.savewizard.net:8082/ps4auth | HK | — | — | suspicious |
3344 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
3344 | iexplore.exe | GET | 200 | 143.204.101.124:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | US | der | 1.51 Kb | whitelisted |
3344 | iexplore.exe | GET | 200 | 13.107.4.50:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?aa193ce07d465549 | US | compressed | 4.70 Kb | whitelisted |
2652 | SWPS4MAX CRACKED.exe | GET | 200 | 14.136.218.90:8082 | http://ps4ws3.savewizard.net:8082/ps4/rss?token= | HK | binary | 40 b | suspicious |
3344 | iexplore.exe | GET | 200 | 143.204.101.195:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
3344 | iexplore.exe | GET | 200 | 52.222.206.35:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwZ%2FlFeFh%2Bisd96yUzJbvJmLVg0%3D | US | der | 1.39 Kb | shared |
3344 | iexplore.exe | GET | 200 | 13.107.4.50:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?7e41c166691fc69e | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3544 | SWPS4MAX CRACKED.exe | 14.136.218.90:8082 | ps4ws2.savewizard.net | HK Broadband Network Ltd. | HK | suspicious |
2652 | SWPS4MAX CRACKED.exe | 14.136.218.90:8082 | ps4ws2.savewizard.net | HK Broadband Network Ltd. | HK | suspicious |
3344 | iexplore.exe | 104.26.6.150:443 | www.nulled.to | Cloudflare Inc | US | malicious |
3344 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3344 | iexplore.exe | 104.16.19.94:443 | cdnjs.cloudflare.com | Cloudflare Inc | US | suspicious |
3344 | iexplore.exe | 104.26.7.150:443 | www.nulled.to | Cloudflare Inc | US | suspicious |
3344 | iexplore.exe | 52.222.206.35:80 | ocsp.rootca1.amazontrust.com | Amazon.com, Inc. | US | whitelisted |
3344 | iexplore.exe | 13.107.4.50:80 | ctldl.windowsupdate.com | Microsoft Corporation | US | whitelisted |
3344 | iexplore.exe | 143.204.101.195:80 | o.ss2.us | — | US | unknown |
3344 | iexplore.exe | 143.204.101.124:80 | ocsp.rootg2.amazontrust.com | — | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ps4ws2.savewizard.net |
| suspicious |
ps4ws3.savewizard.net |
| suspicious |
www.nulled.to |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
cdnjs.cloudflare.com |
| whitelisted |
media.nulled.to |
| unknown |
static.nulled.to |
| unknown |
www.google.com |
| malicious |
shoppy.gg |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3544 | SWPS4MAX CRACKED.exe | Potential Corporate Privacy Violation | ET POLICY Outgoing Basic Auth Base64 HTTP Password detected unencrypted |
— | — | Potentially Bad Traffic | ET DNS Query for .to TLD |
— | — | Potentially Bad Traffic | ET DNS Query for .to TLD |
— | — | Potentially Bad Traffic | ET DNS Query for .to TLD |