| File name: | lino |
| Full analysis: | https://app.any.run/tasks/be1a822a-48e8-45a1-be0c-ce3fc77c1c2c |
| Verdict: | Malicious activity |
| Analysis date: | April 10, 2024, 01:58:10 |
| OS: | Ubuntu 22.04.2 |
| Tags: | |
| MIME: | application/x-executable |
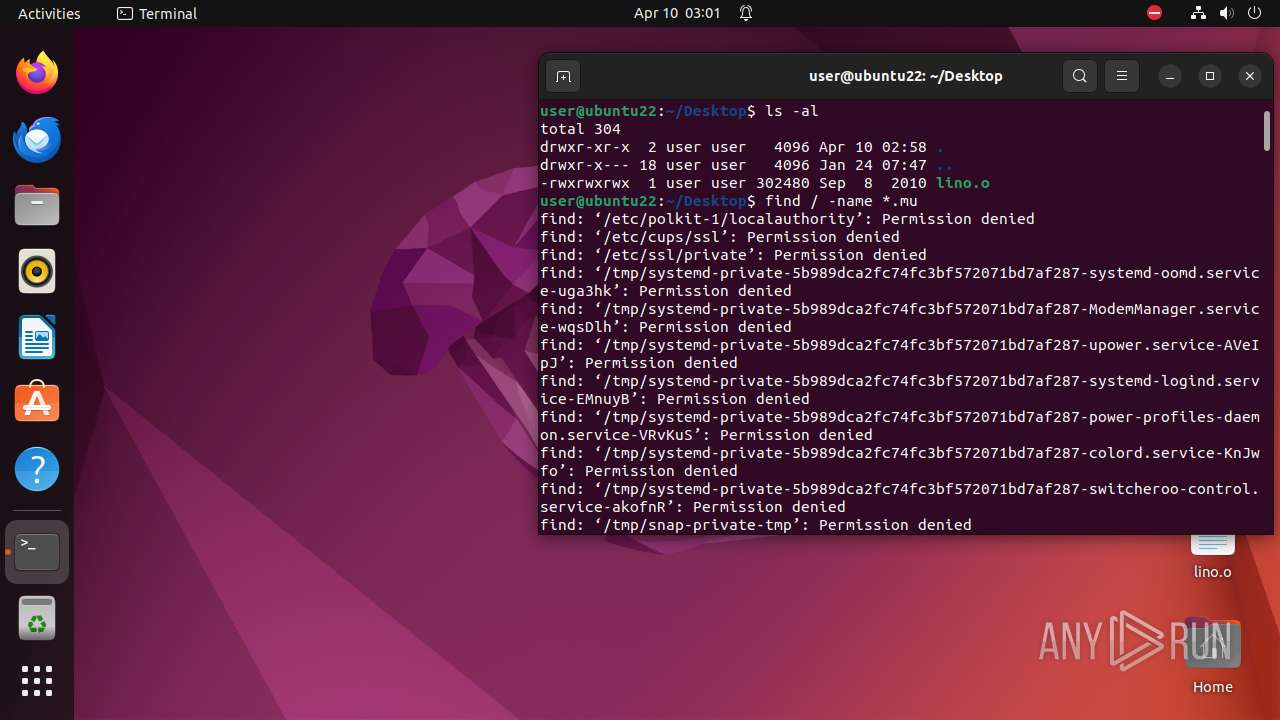
| File info: | ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 2.6.9, stripped |
| MD5: | F1CF940F9E64EDBD21F30249926C7E03 |
| SHA1: | 8F6840D7B6B43D37293FC37C1636132B5934876B |
| SHA256: | 6302ACDFCE30CEC5E9167FF7905800A6220C7DDA495C0AAE1F4594C7263A29B2 |
| SSDEEP: | 3072:oGPAKSoJIdU7EJqkLB97r6KFozsBjVuMjgTw5AIpxmdqPmm9DnSyoWE7lzre559K:oGPAKS7XVgTaAIekx9DnroWEV8B9e5d |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executes commands using command-line interpreter
- bash (PID: 9266)
- lino.o (PID: 9271)
- lino.o (PID: 9281)
- gnome-terminal-server (PID: 9307)
Checks the system hardware (BIOS, baseboard, CPU, etc.)
- sh (PID: 9287)
Modifies file or directory owner
- sudo (PID: 9260)
Modify startup scripts of the system services
- lino.o (PID: 9271)
Writes to Systemd service files (likely for persistence achievement)
- lino.o (PID: 9264)
Changes time attribute to hide new files or make changes to the existing one
- sh (PID: 9289)
- sh (PID: 9282)
Gets information about currently running processes
- sh (PID: 9293)
Reads information about logins, logouts, and login attempts
- bash (PID: 9325)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .o | | | ELF Executable and Linkable format (generic) (49.8) |
|---|
EXIF
EXE
| CPUArchitecture: | 64 bit |
|---|---|
| CPUByteOrder: | Little endian |
| ObjectFileType: | Executable file |
| CPUType: | AMD x86-64 |
Total processes
278
Monitored processes
58
Malicious processes
0
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 9259 | /bin/sh -c "sudo chown user \"/home/user/Desktop/lino\.o\" && chmod +x \"/home/user/Desktop/lino\.o\" && DISPLAY=:0 sudo -i \"/home/user/Desktop/lino\.o\" " | /bin/sh | — | any-guest-agent |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 9260 | sudo chown user /home/user/Desktop/lino.o | /usr/bin/sudo | — | sh |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 9261 | chown user /home/user/Desktop/lino.o | /usr/bin/chown | — | sudo |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 9262 | chmod +x /home/user/Desktop/lino.o | /usr/bin/chmod | — | sh |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 9263 | sudo -i /home/user/Desktop/lino.o | /usr/bin/sudo | — | sh |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 9264 | /home/user/Desktop/lino.o | /home/user/Desktop/lino.o | — | sudo |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 9265 | /usr/bin/locale-check C.UTF-8 | /usr/bin/locale-check | — | lino.o |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 9266 | -bash --login -c \/home\/user\/Desktop\/lino\.o | /usr/bin/bash | — | lino.o |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 9267 | sh -c "cat /usr/etc/debuginfod/*\.urls 2>/dev/null" | /usr/bin/sh | — | bash |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 9268 | tr \n " " | /usr/bin/tr | — | bash |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 9271 | lino.o | /usr/lib/systemd/system/rc.local.service | — | |
MD5:— | SHA256:— | |||
| 9271 | lino.o | /etc/rc.local | — | |
MD5:— | SHA256:— | |||
| 9281 | lino.o | /etc/.netsc.conf | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
16
DNS requests
9
Threats
221
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 204 | 91.189.91.97:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | unknown |
— | — | GET | 204 | 91.189.91.97:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 91.189.91.97:80 | connectivity-check.ubuntu.com | Canonical Group Limited | US | unknown |
— | — | 185.125.190.48:80 | connectivity-check.ubuntu.com | Canonical Group Limited | GB | unknown |
— | — | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 91.195.240.94:443 | update.microsoft-setting.com | — | — | unknown |
— | — | 185.125.188.54:443 | api.snapcraft.io | Canonical Group Limited | GB | unknown |
— | — | 185.125.188.58:443 | api.snapcraft.io | Canonical Group Limited | GB | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
update.microsoft-setting.com |
| unknown |
97.100.168.192.in-addr.arpa |
| unknown |
connectivity-check.ubuntu.com |
| unknown |
api.snapcraft.io |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | A Network Trojan was detected | ET MALWARE DNS Query to Earth Krahang APT Domain (update .microsoft-setting .com) |
— | — | A Network Trojan was detected | ET MALWARE Suspected DinodasRAT Related Activity (UDP) |
— | — | A Network Trojan was detected | ET MALWARE Linux/Dinodas RAT CnC Checkin - UDP |
— | — | A Network Trojan was detected | ET MALWARE Suspected DinodasRAT Related Activity (UDP) |
— | — | A Network Trojan was detected | ET MALWARE Linux/Dinodas RAT CnC Checkin - UDP |
— | — | A Network Trojan was detected | ET MALWARE Suspected DinodasRAT Related Activity (UDP) |
— | — | A Network Trojan was detected | ET MALWARE Linux/Dinodas RAT CnC Checkin - UDP |
— | — | A Network Trojan was detected | ET MALWARE Suspected DinodasRAT Related Activity (UDP) |
— | — | A Network Trojan was detected | ET MALWARE Linux/Dinodas RAT CnC Checkin - UDP |
— | — | A Network Trojan was detected | ET MALWARE Suspected DinodasRAT Related Activity (UDP) |