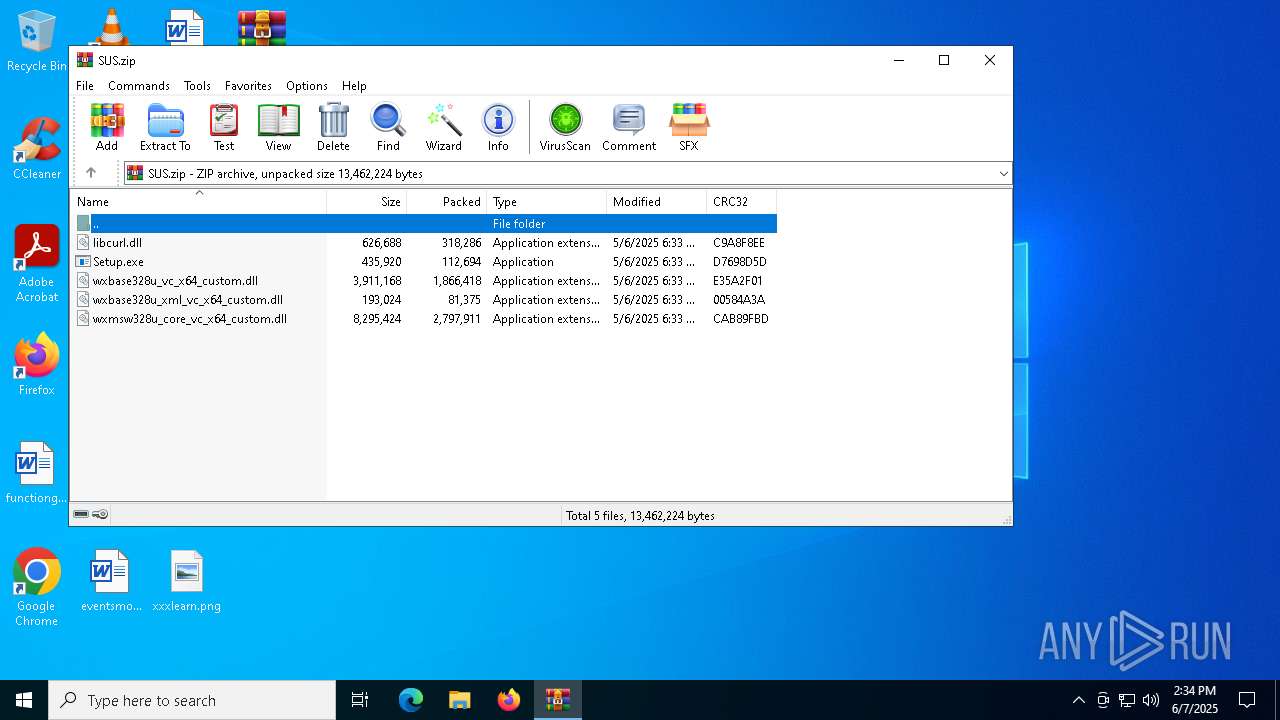
| File name: | SUS.zip |
| Full analysis: | https://app.any.run/tasks/6b554f6f-dad2-4812-b367-a2f07e0c2600 |
| Verdict: | Malicious activity |
| Analysis date: | June 07, 2025, 14:34:07 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | D1F5E079A4B95DAF51791975C4C661E3 |
| SHA1: | C33A28A50BCF97CC10419AC0A4C70A159A07C600 |
| SHA256: | 62D8AA0AFCFF53529D09D7E79E7CB1DD1836C0087ACAF8880142C1338CDF4FA6 |
| SSDEEP: | 98304:ycq1PWjBxl+D5PUvPPG2JFKnn8X4PkctdH3p+lZES0krkmMjLoRusifBxsIv8lGA:wXCh5tJJtDK4 |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 3968)
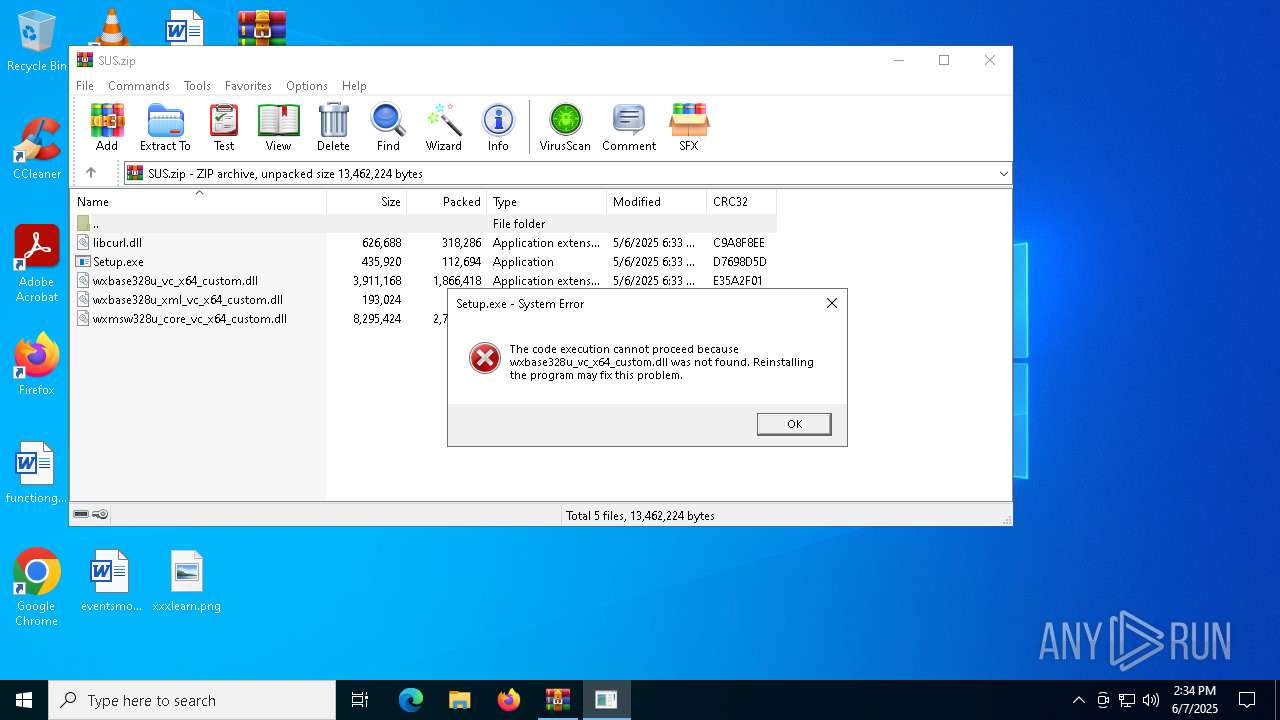
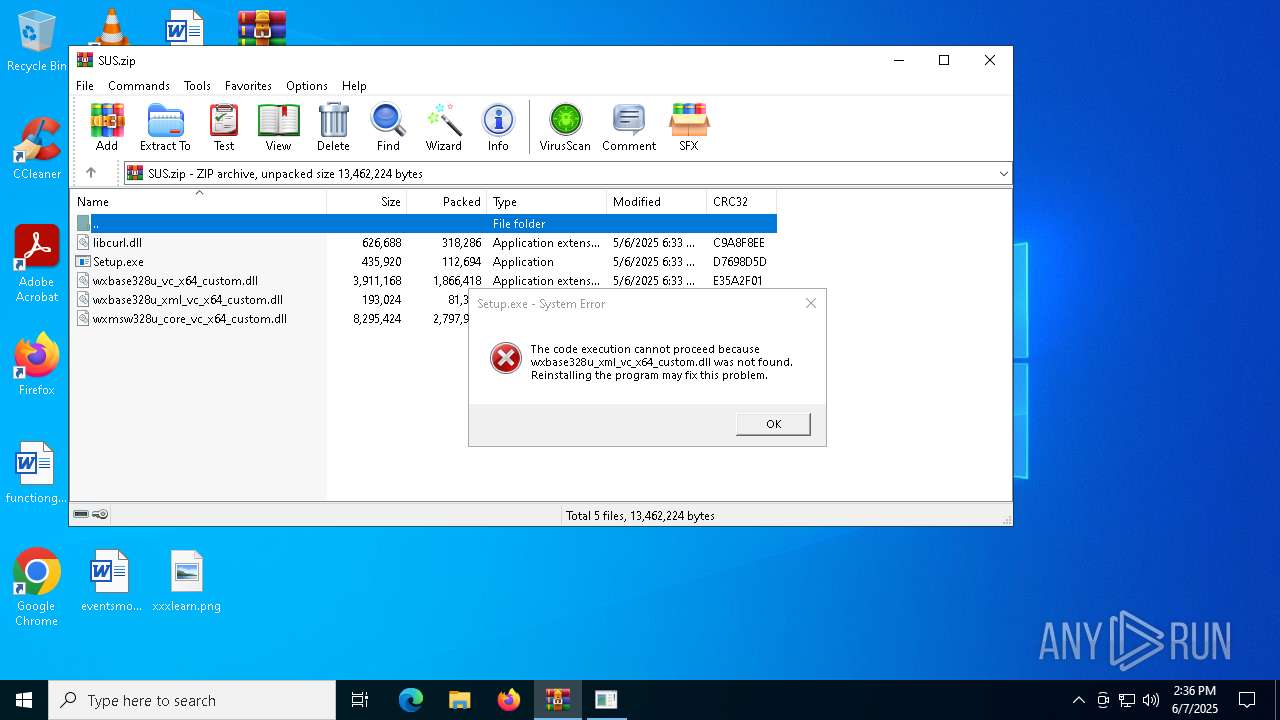
Executing a file with an untrusted certificate
- Setup.exe (PID: 632)
- Setup.exe (PID: 3124)
SUSPICIOUS
Executing commands from a ".bat" file
- WinRAR.exe (PID: 3968)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 3968)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3968)
INFO
Manual execution by a user
- Setup.exe (PID: 3124)
- Setup.exe (PID: 632)
The sample compiled with english language support
- WinRAR.exe (PID: 3968)
Checks proxy server information
- slui.exe (PID: 1812)
Reads the software policy settings
- slui.exe (PID: 1812)
Create files in a temporary directory
- MpCmdRun.exe (PID: 8164)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3968)
Reads the computer name
- MpCmdRun.exe (PID: 8164)
Checks supported languages
- MpCmdRun.exe (PID: 8164)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:05:06 13:33:40 |
| ZipCRC: | 0xc9a8f8ee |
| ZipCompressedSize: | 318286 |
| ZipUncompressedSize: | 626688 |
| ZipFileName: | libcurl.dll |
Total processes
131
Monitored processes
7
Malicious processes
0
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 632 | "C:\Users\admin\Desktop\Setup.exe" | C:\Users\admin\Desktop\Setup.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: StackBuilder for PostgreSQL Version: 4.2.2 Modules
| |||||||||||||||
| 1812 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3124 | "C:\Users\admin\Desktop\Setup.exe" | C:\Users\admin\Desktop\Setup.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: StackBuilder for PostgreSQL Exit code: 3221226540 Version: 4.2.2 Modules
| |||||||||||||||
| 3968 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\SUS.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 5352 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8076 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR3968.30512\Rar$Scan137494.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
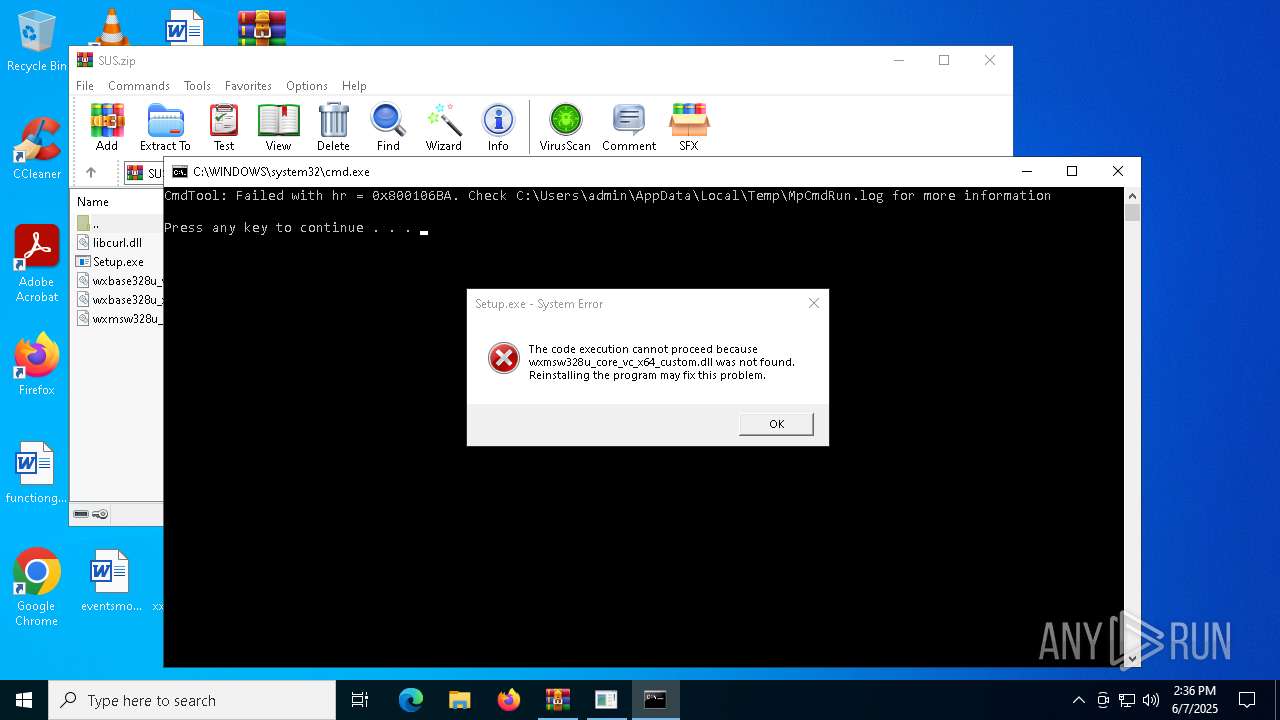
| 8164 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR3968.30512" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 971
Read events
4 960
Write events
11
Delete events
0
Modification events
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\SUS.zip | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList |
| Operation: | write | Name: | ArcSort |
Value: 32 | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList |
| Operation: | write | Name: | ArcSort |
Value: 0 | |||
Executable files
5
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 8164 | MpCmdRun.exe | C:\Users\admin\AppData\Local\Temp\MpCmdRun.log | text | |
MD5:71585F928D831C17BD57DFBBF2D8AAF7 | SHA256:3C121989CAE7D61E457A2441070DF7C75C6850336731ECB273FB9B115EC02BDC | |||
| 3968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR3968.30512\Rar$Scan137494.bat | text | |
MD5:D0090AB2C7ABACBE9927178B4BA9F79E | SHA256:05EFC6BCA6FA72A3F620B0321CAF4EA8492BEB2092A3CE903B9B230A279F6657 | |||
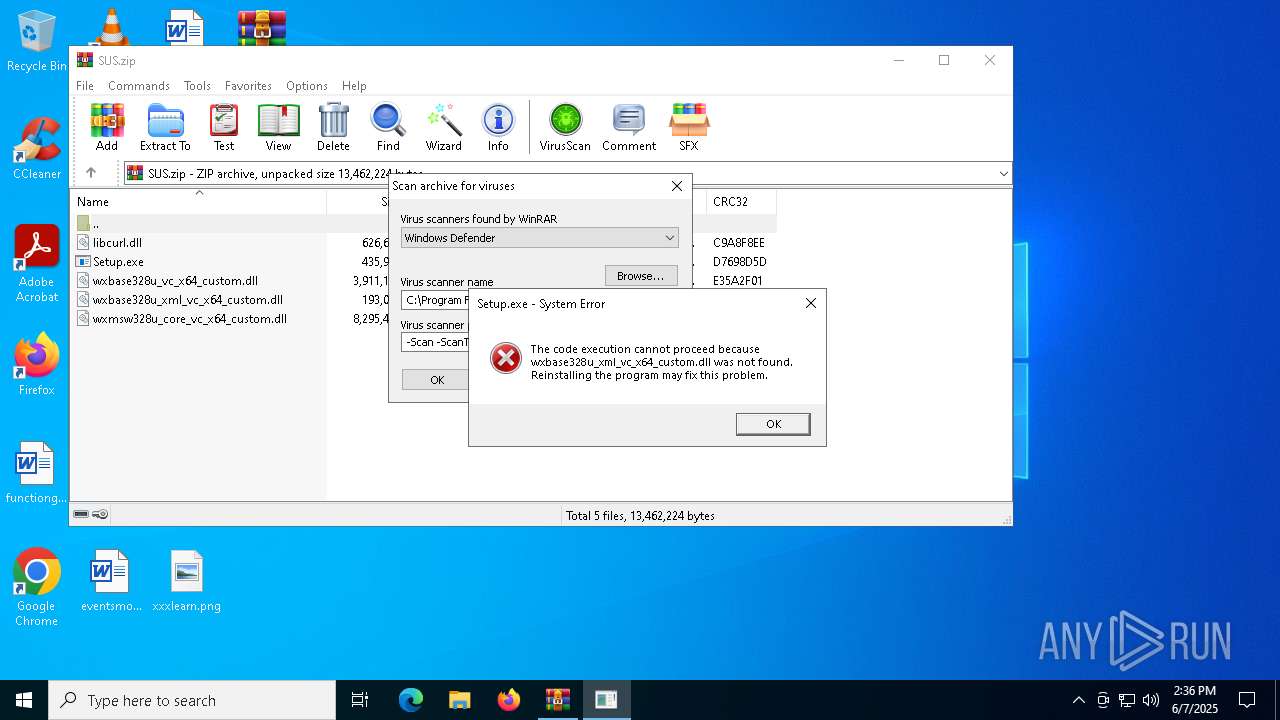
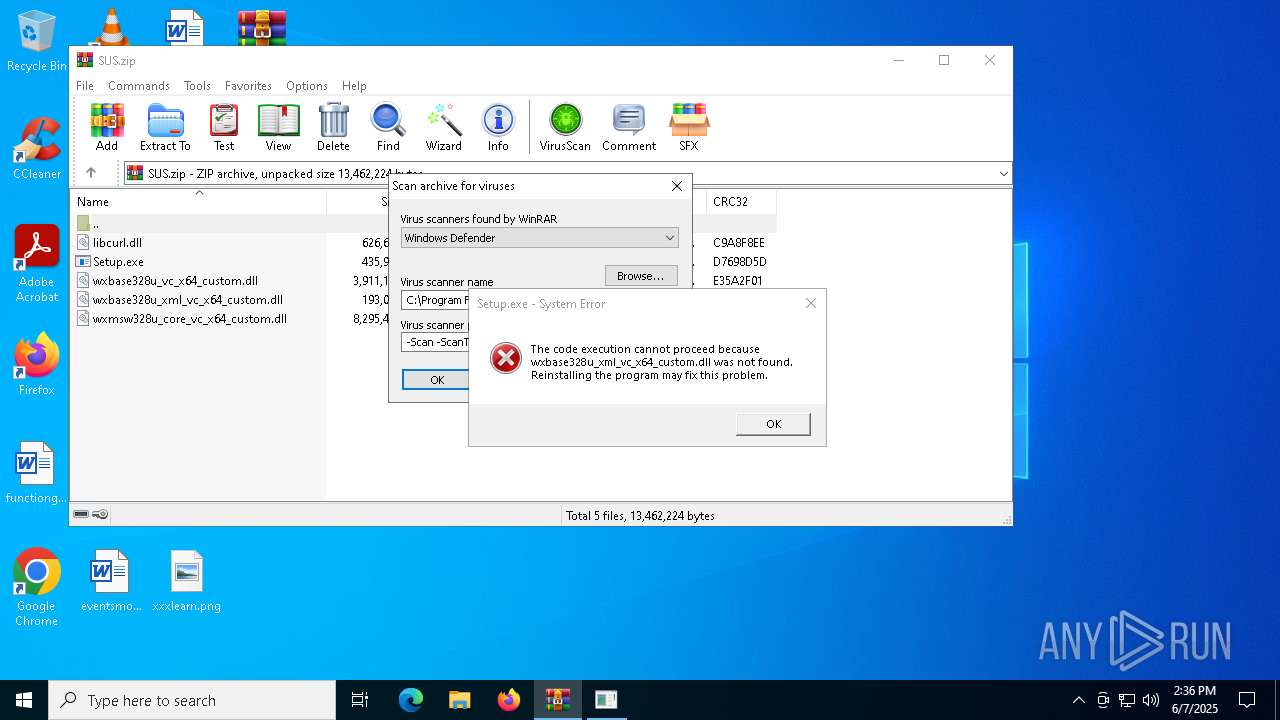
| 3968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR3968.30512\SUS.zip\Setup.exe | executable | |
MD5:B55441ECBFA5105DC2AA3BBBE33914F2 | SHA256:BA42A73F1CA561A2E633EE9979D7885CB8DE4ABBE4BA55F49B15B972BCB35405 | |||
| 3968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR3968.30512\SUS.zip\wxbase328u_xml_vc_x64_custom.dll | executable | |
MD5:75F4EDF61CF30C3EE1B38D8C9D450EBC | SHA256:DC43A3150F9C792C01EF9A2F4FE136415445B7874C0AC04C66FCC1A8AAC65D7D | |||
| 3968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR3968.30512\SUS.zip\libcurl.dll | executable | |
MD5:7117DD2E531577D023B9CF1D5BB113F1 | SHA256:8010DF3966B136395959F938B34F3AC125E09C61971B06E7D55FC4835D11590F | |||
| 3968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR3968.30512\SUS.zip\wxbase328u_vc_x64_custom.dll | executable | |
MD5:E00CFE72967DF9F730058D97AA51026C | SHA256:43E9C21955277B99734960070D02A94EF00F943D35C2B5931BAF75D28105F787 | |||
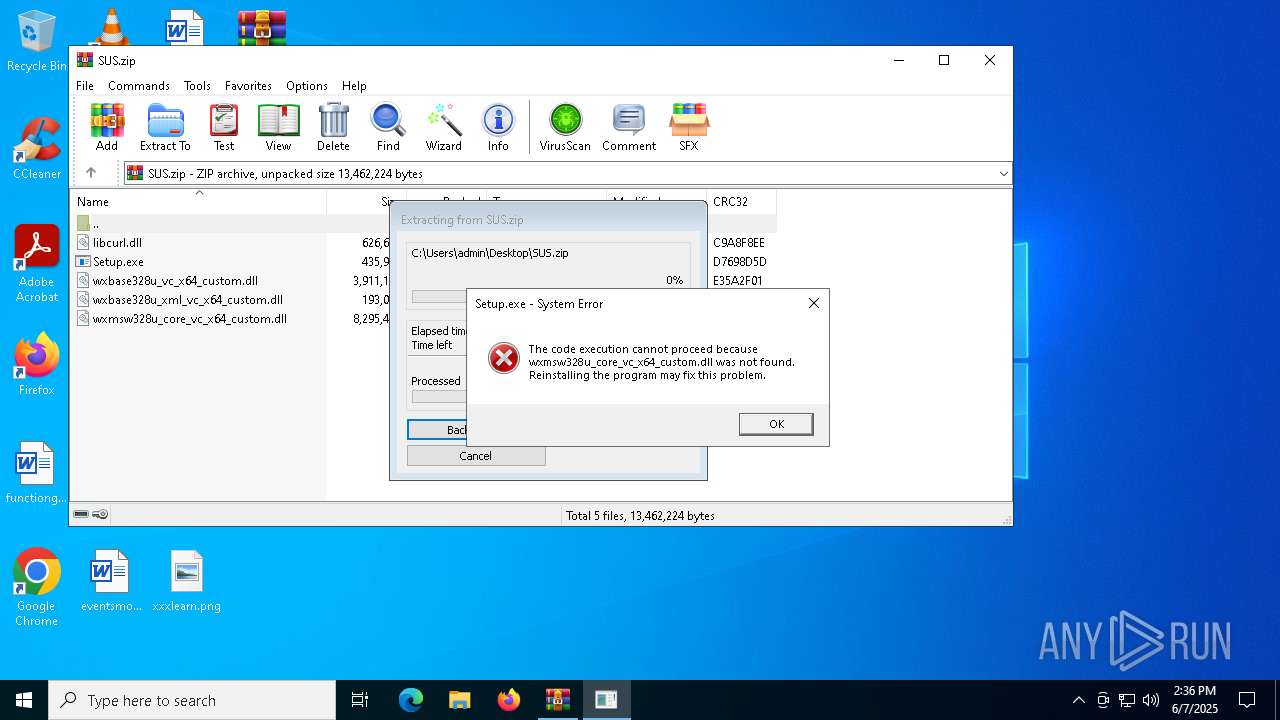
| 3968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR3968.30512\SUS.zip\wxmsw328u_core_vc_x64_custom.dll | executable | |
MD5:34808B658C1E2A0A06A526F503666642 | SHA256:0545358C18E5E8F1CA01D0C5B6EA6E2B6AC2A21ADB034C3D94813C1CA3EA2A27 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
23
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
864 | svchost.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6132 | RUXIMICS.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
864 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6132 | RUXIMICS.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6132 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
864 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
864 | svchost.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6132 | RUXIMICS.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
864 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
864 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |