analyze malware
- Huge database of samples and IOCs
- Custom VM setup
- Unlimited submissions
- Interactive approach
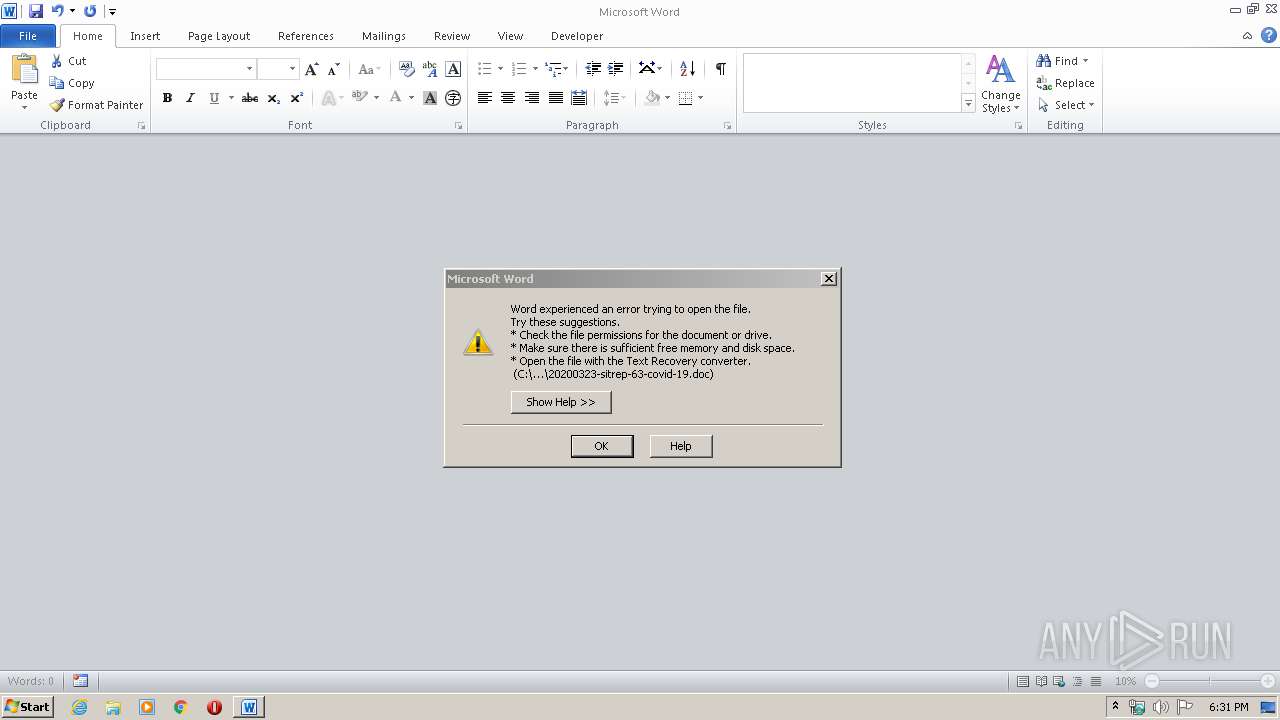
| File name: | 20200323-sitrep-63-covid-19.doc |
| Full analysis: | https://app.any.run/tasks/f21666da-26cf-4463-a390-c720ede4bf6f |
| Verdict: | Malicious activity |
| Analysis date: | March 30, 2020, 17:31:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/rtf |
| File info: | Rich Text Format data, version 1, unknown character set |
| MD5: | 994A67D5D6341173AD95BC6F5D795FD0 |
| SHA1: | FA84EE006B205F105DF40DD2ABCF238653F8CEF0 |
| SHA256: | 62D38F19E67013CE7B2A84CB17362C77E2F13134EE3F8743CBADDE818483E617 |
| SSDEEP: | 12288:iIwhGKVNiBgY3SkPCfxEbYvEFqvn1wMVBk3oRoVDAUMn47f43:EhGfW9IYsFqvnyL3C6/WSY |
MALICIOUS
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 3952)
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 3952)
Executable content was dropped or overwritten
- WINWORD.EXE (PID: 3952)
Application was dropped or rewritten from another process
- svchost.exe (PID: 3680)
SUSPICIOUS
Creates executable files which already exist in Windows
- WINWORD.EXE (PID: 3952)
Starts Microsoft Office Application
- WINWORD.EXE (PID: 3952)
Application launched itself
- WINWORD.EXE (PID: 3952)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 4092)
- cmd.exe (PID: 3392)
INFO
Drops Coronavirus (possible) decoy
- WINWORD.EXE (PID: 3952)
Creates files in the user directory
- WINWORD.EXE (PID: 3952)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3952)
- WINWORD.EXE (PID: 3340)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rtf | | | Rich Text Format (100) |
|---|
Total processes
44
Monitored processes
7
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 3952 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\20200323-sitrep-63-covid-19.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 | ||||
| 3680 | C:\Users\admin\AppData\Local\Temp\..\svchost.exe | C:\Users\admin\AppData\Local\svchost.exe | WINWORD.EXE | |
User: admin Integrity Level: MEDIUM Description: eda2 Version: 1.0.0.0 | ||||
| 4092 | cmd.exe /c reg delete "HKCU\Software\Microsoft\Office\14.0\Word\Resiliency" /F | C:\Windows\system32\cmd.exe | — | WINWORD.EXE |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) | ||||
| 3392 | cmd.exe /c reg delete "HKCU\Software\Microsoft\Office\12.0\Word\Resiliency" /F | C:\Windows\system32\cmd.exe | — | WINWORD.EXE |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) | ||||
| 3340 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" "C:\Users\admin\AppData\Local\Temp\20200323-sitrep-63-covid-19.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WINWORD.EXE |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 14.0.6024.1000 | ||||
| 2124 | reg delete "HKCU\Software\Microsoft\Office\14.0\Word\Resiliency" /F | C:\Windows\system32\reg.exe | — | cmd.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 3180 | reg delete "HKCU\Software\Microsoft\Office\12.0\Word\Resiliency" /F | C:\Windows\system32\reg.exe | — | cmd.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
Total events
2 008
Read events
1 262
Write events
0
Delete events
0
Modification events
Executable files
1
Suspicious files
4
Text files
0
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3952 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR6C01.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3340 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR77E7.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3952 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{01B594BB-03A4-4822-B99C-8771D4C48963}.tmp | binary | |
MD5:46648FBC9AD57EB02E9215A90DECB119 | SHA256:2A4050534BF4C6BE94025C38C5E2BFA20CF75D1E4171BB3DA74097DDFEFAE642 | |||
| 3952 | WINWORD.EXE | C:\Users\admin\AppData\Local\svchost.exe | executable | |
MD5:6700A8204081A1CC2F27D371E921983D | SHA256:2779863A173FF975148CB3156EE593CB5719A0AB238EA7C9E0B0CA3B5A4A9326 | |||
| 3952 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$200323-sitrep-63-covid-19.doc | pgc | |
MD5:85A86763B9E1452416CCD566A250EECB | SHA256:B4BF957D9A164EA7643FA3C5A322D9C316D78DF2F2941807E7430B30CE25BBED | |||
| 3952 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:477916EFB88A373723F281B8A9BC2EA4 | SHA256:F8C4753F90B6CCCCFB7FC260ACCB0BA935A8E56898FCB3BBF10845FF3B8EE27B | |||
| 3952 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRF{DC814365-A569-4C32-AB87-C8CA8694A218}.tmp | binary | |
MD5:7E518FFE9344AB3E442E390B82271260 | SHA256:063E6685671AABA93C90D8B2918D651BA1CADB73715C4653A233983B14C1F43D | |||
| 3952 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\20200323-sitrep-63-covid-19.doc | binary | |
MD5:75EF7A36C13A8827418673E4C5EFA639 | SHA256:8B7878EDEAC4156F8AD6E14F0C983931D261ECDC5587B15EDD6A39C2C66D127E | |||
| 3952 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{59C3E6C1-8BBB-44DA-8C8C-0D8BB9CF1028}.tmp | smt | |
MD5:5D4D94EE7E06BBB0AF9584119797B23A | SHA256:4826C0D860AF884D3343CA6460B0006A7A2CE7DBCCC4D743208585D997CC5FD1 | |||
| 3952 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{0032525E-1BA4-45CE-96BC-B6866F860E48}.tmp | binary | |
MD5:0F4C51A4EFD78D6758C89681C48582FA | SHA256:B7A6713E12B1D6B08A5DC0600C529D07DA2D48DF57914496C42383D1BB7AB9B2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3680 | svchost.exe | 31.170.167.123:80 | www.tempinfo.96.lt | Hostinger International Limited | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.tempinfo.96.lt |
| malicious |