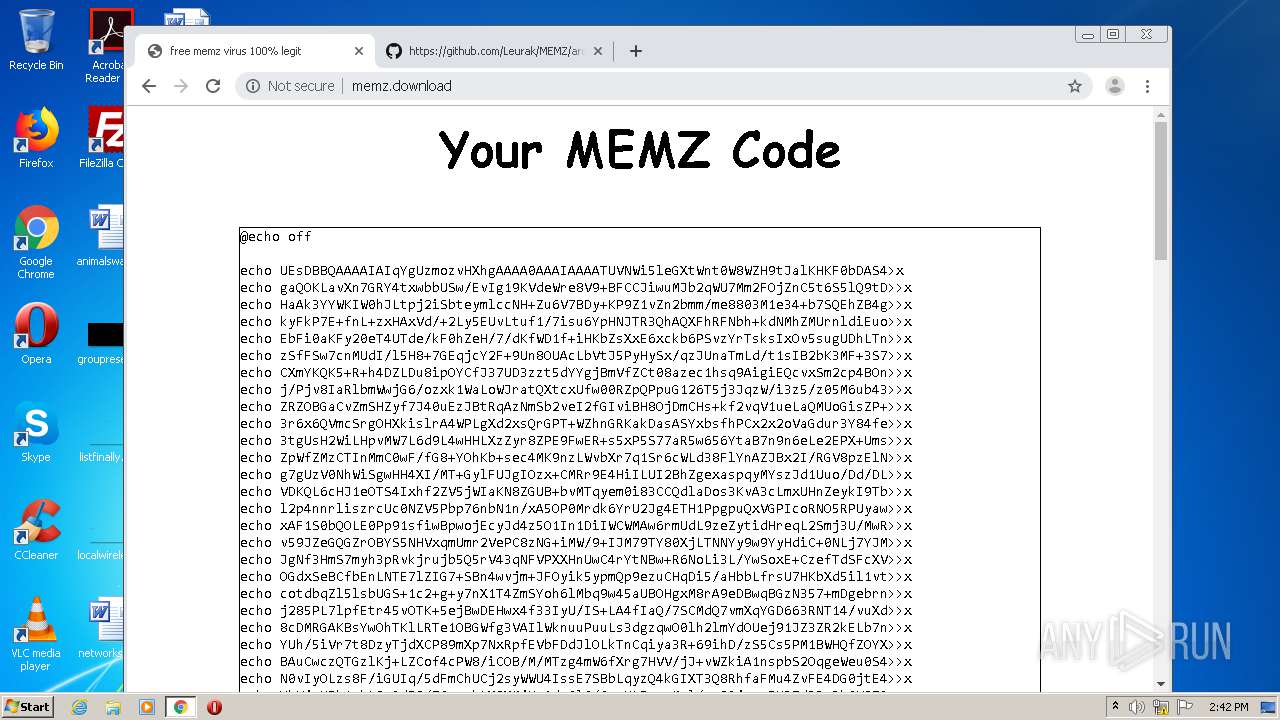
analyze malware
- Huge database of samples and IOCs
- Custom VM setup
- Unlimited submissions
- Interactive approach
| download: | index.html |
| Full analysis: | https://app.any.run/tasks/b80b3a75-f499-44e8-a48d-641a347f6e85 |
| Verdict: | Malicious activity |
| Analysis date: | November 29, 2020, 14:37:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, ASCII text |
| MD5: | 079F8F48B25BC8AEC7244F4E997D73B5 |
| SHA1: | 25A1D6F6E6DCB4FFCD0BF773832F2F8BB242278E |
| SHA256: | 62B61B7CDD1D20B98DA4486DB600A4852D88AD8765C4C94A2FBB5286D8C84719 |
| SSDEEP: | 12:BMQt5FYo9+OEutJarDz0rCuKXfsx0sGJA9jL:WC5/Za7+3xR9v |
MALICIOUS
No malicious indicators.SUSPICIOUS
Modifies files in Chrome extension folder
- chrome.exe (PID: 2996)
INFO
Reads settings of System Certificates
- iexplore.exe (PID: 2596)
- iexplore.exe (PID: 1332)
- iexplore.exe (PID: 2352)
- chrome.exe (PID: 444)
- iexplore.exe (PID: 2200)
Changes settings of System certificates
- iexplore.exe (PID: 2596)
- iexplore.exe (PID: 1332)
- iexplore.exe (PID: 2352)
Changes internet zones settings
- iexplore.exe (PID: 2352)
Application launched itself
- iexplore.exe (PID: 2352)
- iexplore.exe (PID: 2596)
- chrome.exe (PID: 2996)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2596)
- iexplore.exe (PID: 1332)
- iexplore.exe (PID: 2352)
Reads internet explorer settings
- iexplore.exe (PID: 2596)
- iexplore.exe (PID: 1332)
- iexplore.exe (PID: 2200)
Creates files in the user directory
- iexplore.exe (PID: 2352)
- iexplore.exe (PID: 2200)
Reads the hosts file
- chrome.exe (PID: 444)
- chrome.exe (PID: 2996)
Manual execution by user
- chrome.exe (PID: 2996)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .html | | | HyperText Markup Language (100) |
|---|
EXIF
HTML
| Keywords: | - |
|---|---|
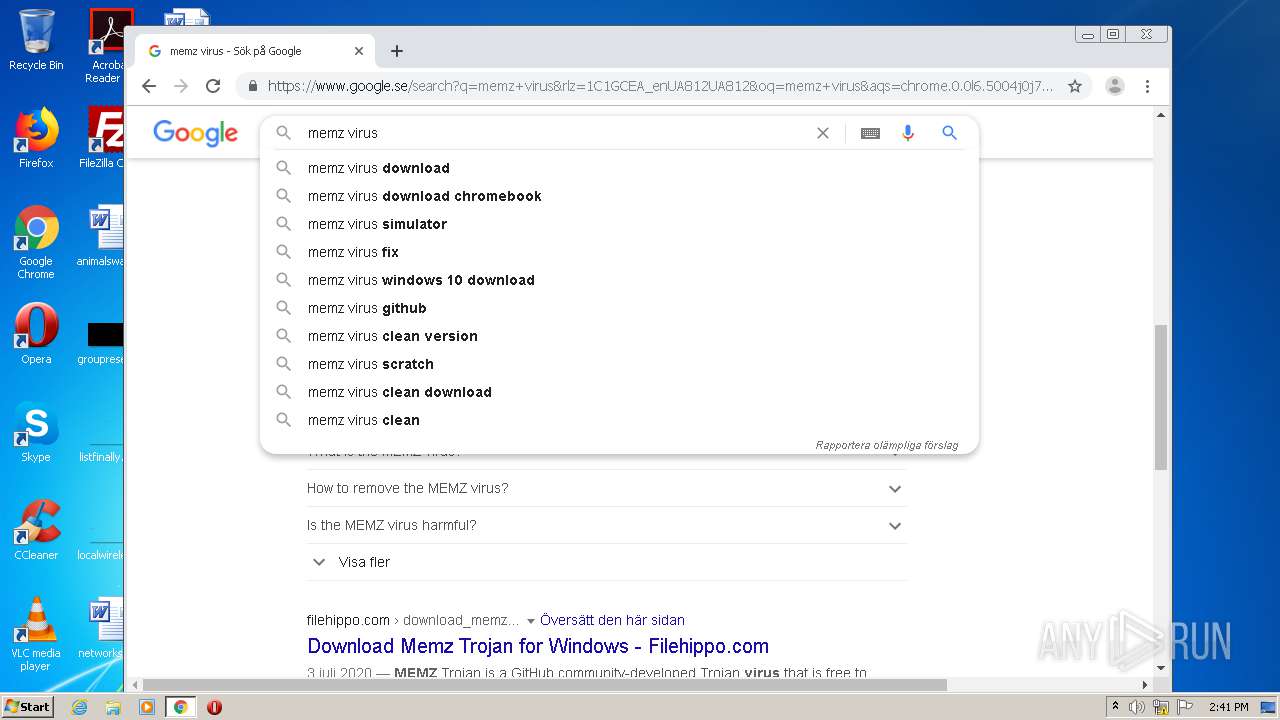
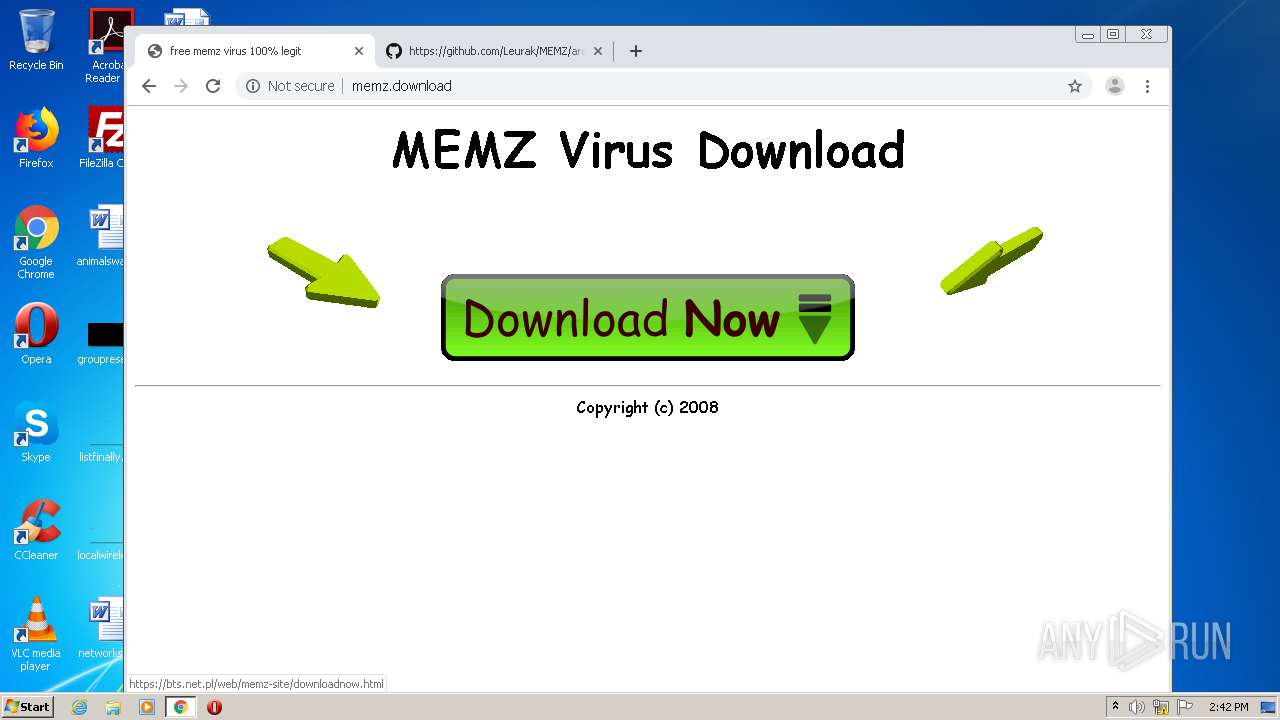
| Description: | get your free memz viruzz for free. use this safely or you will get fucking spanked. |
| Title: | free memz virus 100% legit |
Total processes
123
Monitored processes
85
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 2352 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\AppData\Local\Temp\index.html | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) | ||||
| 2596 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2352 CREDAT:144385 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) | ||||
| 1332 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2352 CREDAT:144390 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) | ||||
| 2200 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2352 CREDAT:398593 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | |
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) | ||||
| 2996 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | |
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 75.0.3770.100 | ||||
| 532 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=75.0.3770.100 --initial-client-data=0x7c,0x80,0x84,0x78,0x88,0x6ec6a9d0,0x6ec6a9e0,0x6ec6a9ec | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 75.0.3770.100 | ||||
| 948 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=3016 --on-initialized-event-handle=324 --parent-handle=328 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 75.0.3770.100 | ||||
| 3684 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1028,12813712267330727298,16195011973842947495,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=8701795882382426941 --mojo-platform-channel-handle=1048 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 75.0.3770.100 | ||||
| 444 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1028,12813712267330727298,16195011973842947495,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --service-request-channel-token=14984912219682256810 --mojo-platform-channel-handle=1616 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | |
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 75.0.3770.100 | ||||
| 1196 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1028,12813712267330727298,16195011973842947495,131072 --enable-features=PasswordImport --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=1648812112006292104 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2272 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 | ||||
Total events
2 252
Read events
1 770
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
424
Text files
353
Unknown types
83
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2596 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\CabD888.tmp | — | |
MD5:— | SHA256:— | |||
| 2596 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\TarD889.tmp | — | |
MD5:— | SHA256:— | |||
| 1332 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\CabD8B7.tmp | — | |
MD5:— | SHA256:— | |||
| 1332 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\TarD8C8.tmp | — | |
MD5:— | SHA256:— | |||
| 1332 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C70BFA2D9DC40914ACED8BBED973B1E3_0AAC2086786434F6533EB54D1FBF050C | binary | |
MD5:983E10ADC538CA60F5AC0BE4618092D8 | SHA256:95CF84DB250E136C4EEAD52664EF5305E7503C08F47EEC0920251A463FDADFC0 | |||
| 2596 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\04FC23A773A43B5EED263BBAF545D686_0EE68C905AC58CD361640846A866098F | binary | |
MD5:91EB8F1F7F7D8B8F0E727B539BEFF2B9 | SHA256:016439609474A37CC9D8BAB0AFCCE2F54D57678421EF6B7BD8DCCE6B9853603B | |||
| 2596 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C70BFA2D9DC40914ACED8BBED973B1E3_0AAC2086786434F6533EB54D1FBF050C | binary | |
MD5:983E10ADC538CA60F5AC0BE4618092D8 | SHA256:95CF84DB250E136C4EEAD52664EF5305E7503C08F47EEC0920251A463FDADFC0 | |||
| 2596 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C70BFA2D9DC40914ACED8BBED973B1E3_0AAC2086786434F6533EB54D1FBF050C | der | |
MD5:A017047280111D640ABB0C897FCD4EA3 | SHA256:BB04723E0F5EF498CE03B62F4C47CD41E9C80EC857100AECE8F9AC55FA7BCCE0 | |||
| 2596 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\68FAF71AF355126BCA00CE2E73CC7374_A88E46230AD93776AD6952BFE1EC0FFF | der | |
MD5:01BB306E71DFD4687775C5D72429C2C1 | SHA256:250986F93D19C3E17ACA6647A2747D96B494124FA107F0461F591D8255096762 | |||
| 2596 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\04FC23A773A43B5EED263BBAF545D686_0EE68C905AC58CD361640846A866098F | der | |
MD5:39048516B0FF4DB7BEC9FCDF83C369BA | SHA256:01604C97ACAA9F0F9B3285F40F76733184159195F0A17A0F5D755CEABCD79EA6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
59
TCP/UDP connections
457
DNS requests
293
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2596 | iexplore.exe | GET | 200 | 95.101.27.77:80 | http://subca.ocsp-certum.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTYOkzrrCGQj08njZXbUQQpkoUmuQQUCHbNywf%2FJPbFze27kLzihDdGdfcCEQDQS2%2Fl3VvSIefHTPZGizFG | unknown | der | 1.63 Kb | whitelisted |
1332 | iexplore.exe | GET | 200 | 95.101.27.77:80 | http://subca.ocsp-certum.com/MFAwTjBMMEowSDAJBgUrDgMCGgUABBQcn6glOULIBQemtTWi1FD7IEbk4gQUVJndm%2F%2Fopw6jGZ1bvkJX3zD8jzICDzEdft3kkgIIu9he9yYrug%3D%3D | unknown | der | 1.55 Kb | whitelisted |
2596 | iexplore.exe | GET | 200 | 95.101.27.81:80 | http://repository.certum.pl/hsha2.cer | unknown | der | 1.09 Kb | whitelisted |
2596 | iexplore.exe | GET | 200 | 95.101.27.81:80 | http://repository.certum.pl/gscasha2.cer | unknown | der | 1.20 Kb | whitelisted |
2200 | iexplore.exe | GET | 200 | 13.107.5.80:80 | http://api.bing.com/qsml.aspx?query=memz&maxwidth=32765&rowheight=20§ionHeight=160&FORM=IE11SS&market=en-US | US | xml | 233 b | whitelisted |
2596 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
2200 | iexplore.exe | GET | 200 | 13.107.5.80:80 | http://api.bing.com/qsml.aspx?query=mem&maxwidth=32765&rowheight=20§ionHeight=160&FORM=IE11SS&market=en-US | US | xml | 235 b | whitelisted |
1332 | iexplore.exe | GET | 200 | 95.101.27.77:80 | http://subca.ocsp-certum.com/MFAwTjBMMEowSDAJBgUrDgMCGgUABBQcn6glOULIBQemtTWi1FD7IEbk4gQUVJndm%2F%2Fopw6jGZ1bvkJX3zD8jzICDzEdft3kkgIIu9he9yYrug%3D%3D | unknown | der | 1.55 Kb | whitelisted |
1332 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
2596 | iexplore.exe | GET | 200 | 95.101.27.121:80 | http://subca.ocsp-certum.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTYOkzrrCGQj08njZXbUQQpkoUmuQQUCHbNywf%2FJPbFze27kLzihDdGdfcCEQDQS2%2Fl3VvSIefHTPZGizFG | unknown | der | 1.63 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2352 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2596 | iexplore.exe | 80.211.245.94:443 | bts.net.pl | Aruba S.p.A. | IT | suspicious |
2596 | iexplore.exe | 95.101.27.121:80 | subca.ocsp-certum.com | Akamai Technologies, Inc. | — | unknown |
2596 | iexplore.exe | 95.101.27.81:80 | repository.certum.pl | Akamai Technologies, Inc. | — | unknown |
2596 | iexplore.exe | 95.101.27.77:80 | subca.ocsp-certum.com | Akamai Technologies, Inc. | — | unknown |
1332 | iexplore.exe | 95.101.27.77:80 | subca.ocsp-certum.com | Akamai Technologies, Inc. | — | unknown |
1332 | iexplore.exe | 95.101.27.121:80 | subca.ocsp-certum.com | Akamai Technologies, Inc. | — | unknown |
1332 | iexplore.exe | 80.211.245.94:443 | bts.net.pl | Aruba S.p.A. | IT | suspicious |
2596 | iexplore.exe | 95.101.27.112:80 | repository.certum.pl | Akamai Technologies, Inc. | — | suspicious |
2596 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
bts.net.pl |
| suspicious |
repository.certum.pl |
| whitelisted |
subca.ocsp-certum.com |
| whitelisted |
h.ocsp-certum.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ieonline.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |