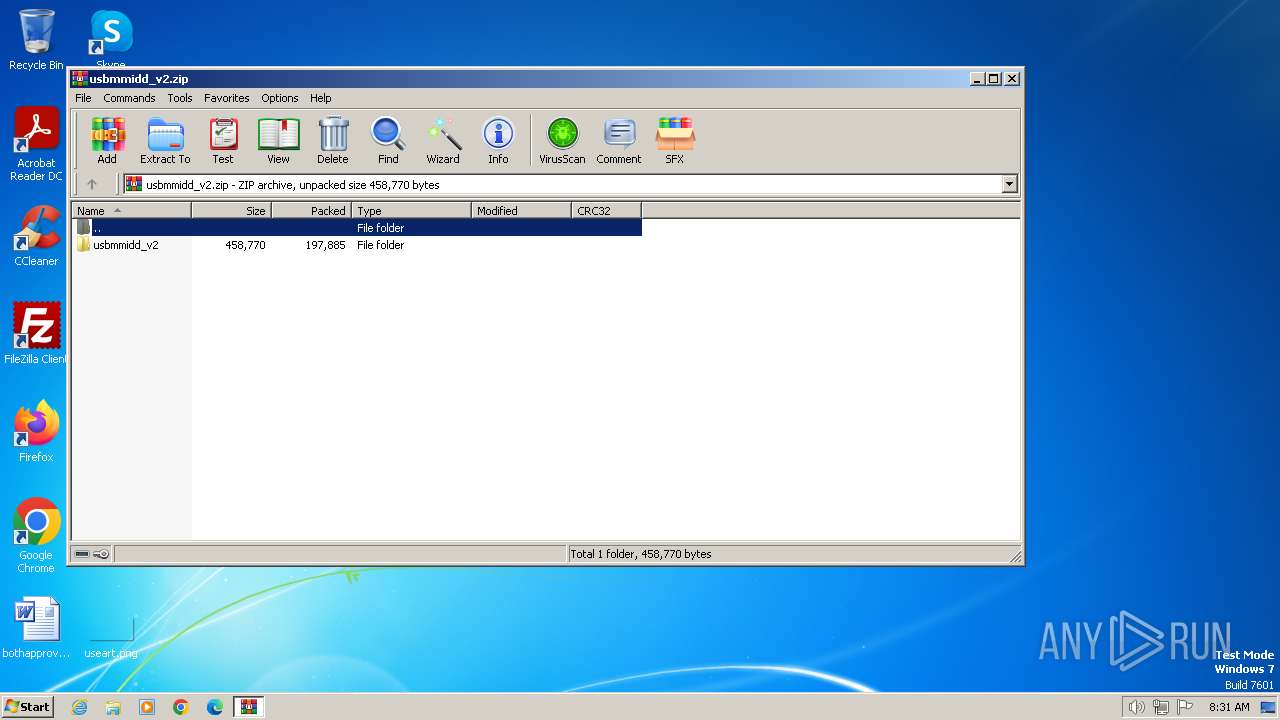
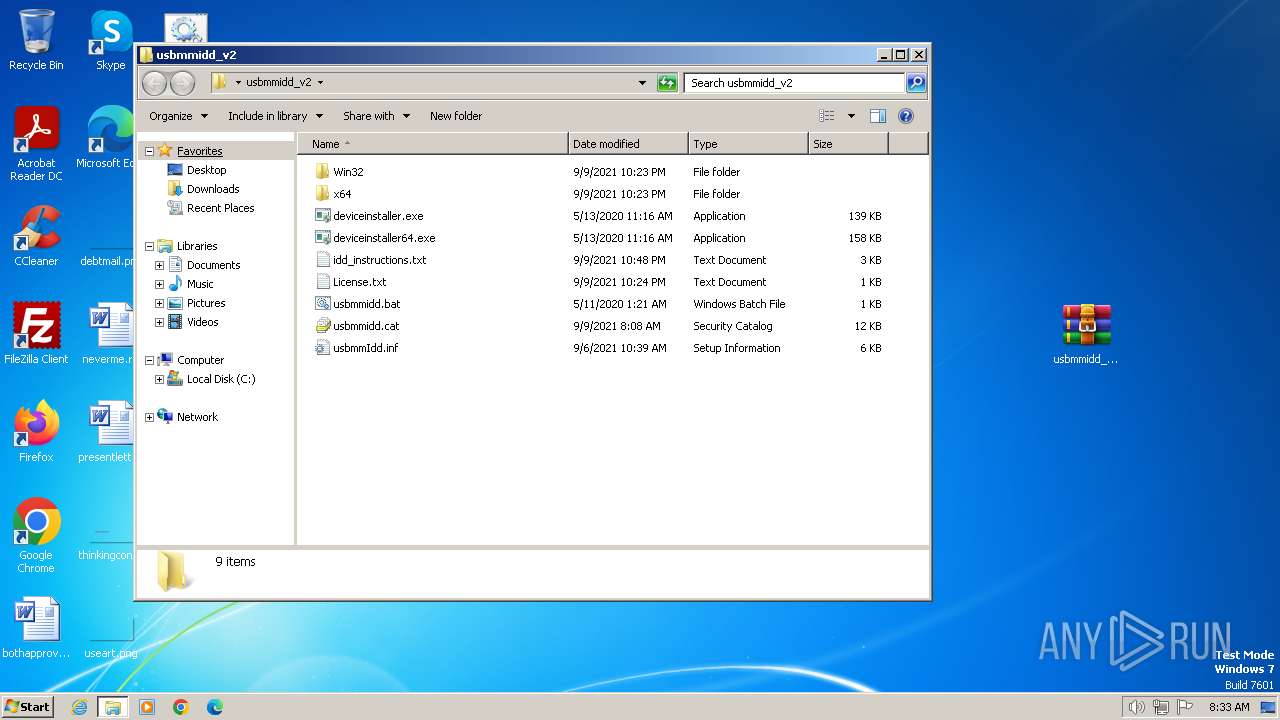
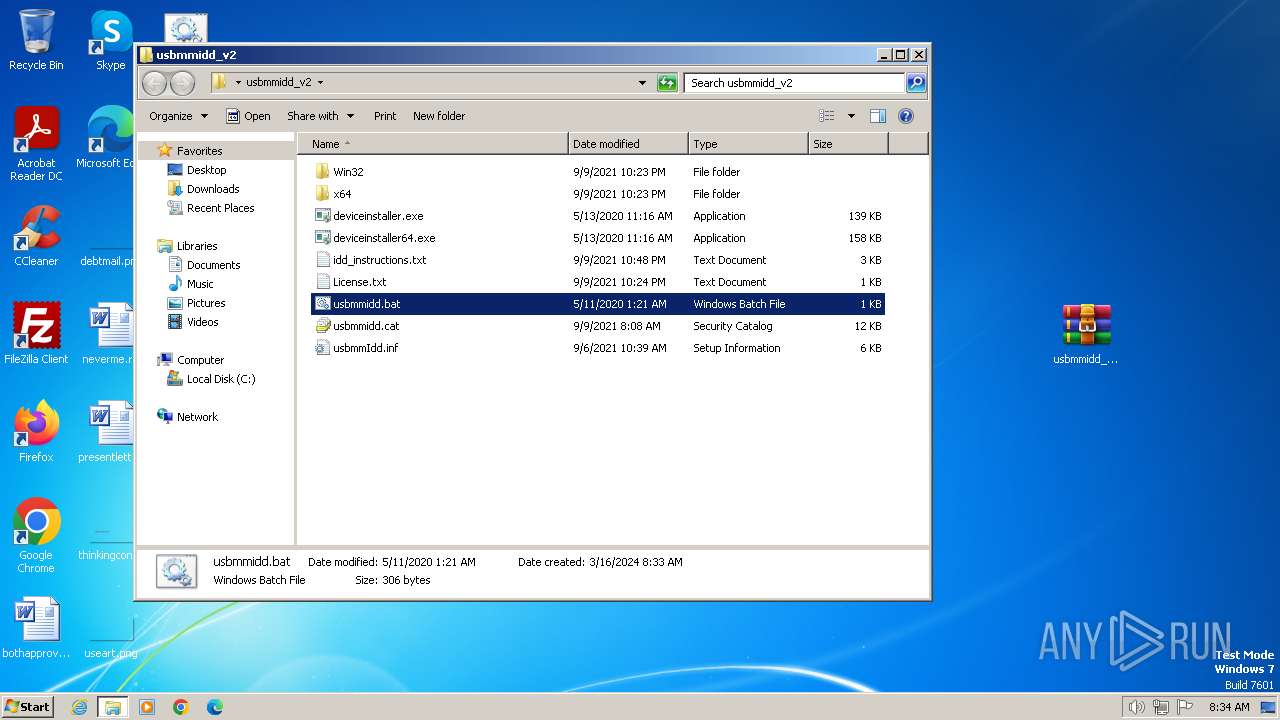
| File name: | usbmmidd_v2.zip |
| Full analysis: | https://app.any.run/tasks/bdc748f5-5bb1-48ab-b8ea-51f4cfe23042 |
| Verdict: | Malicious activity |
| Analysis date: | March 16, 2024, 08:31:15 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | D282869544C02F34F09F0202E9C5DD9F |
| SHA1: | 477FAD66342DC42C5B88681BA823F400F75FAC49 |
| SHA256: | 629B51E9944762BAE73948171C65D09A79595CF4C771A82EBC003FBBA5B24F51 |
| SSDEEP: | 3072:OsBLxHK2MtFNrhz130iP/r6sPP+FBDYfq53GLWRT6vytRSlZv:ZBLxUdrhZ3V/esH+nSwRTUycZv |
MALICIOUS
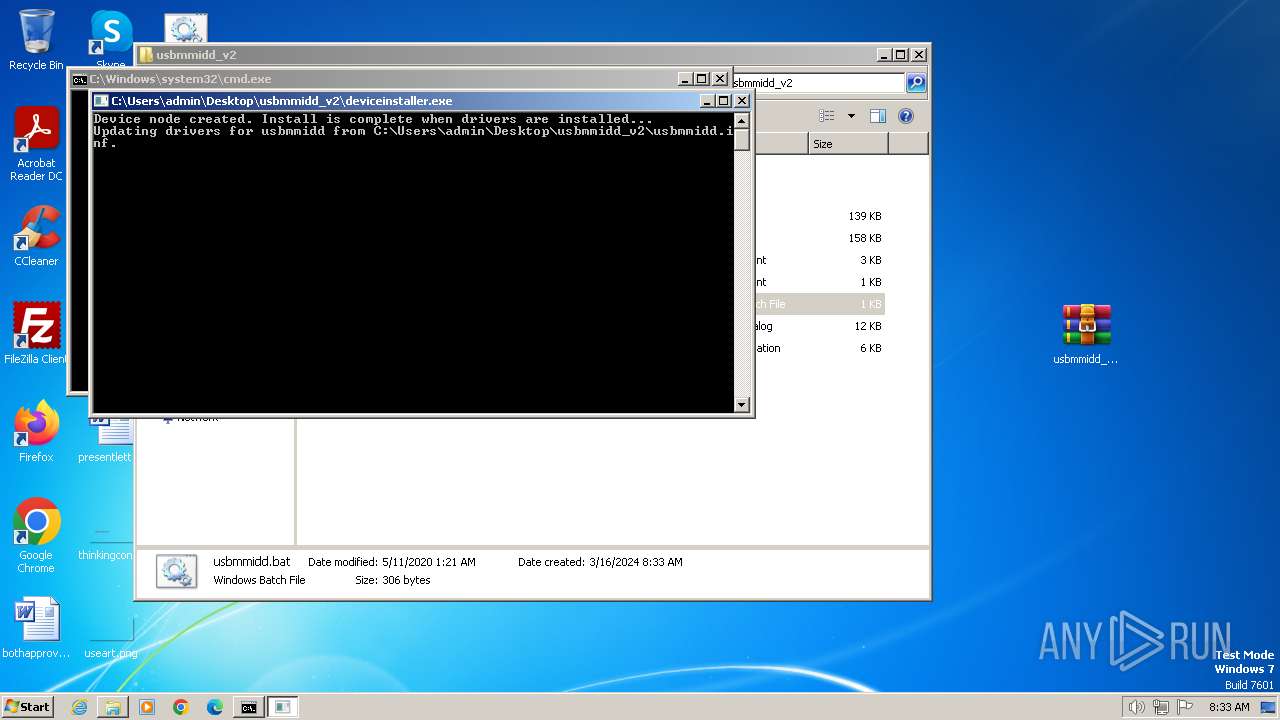
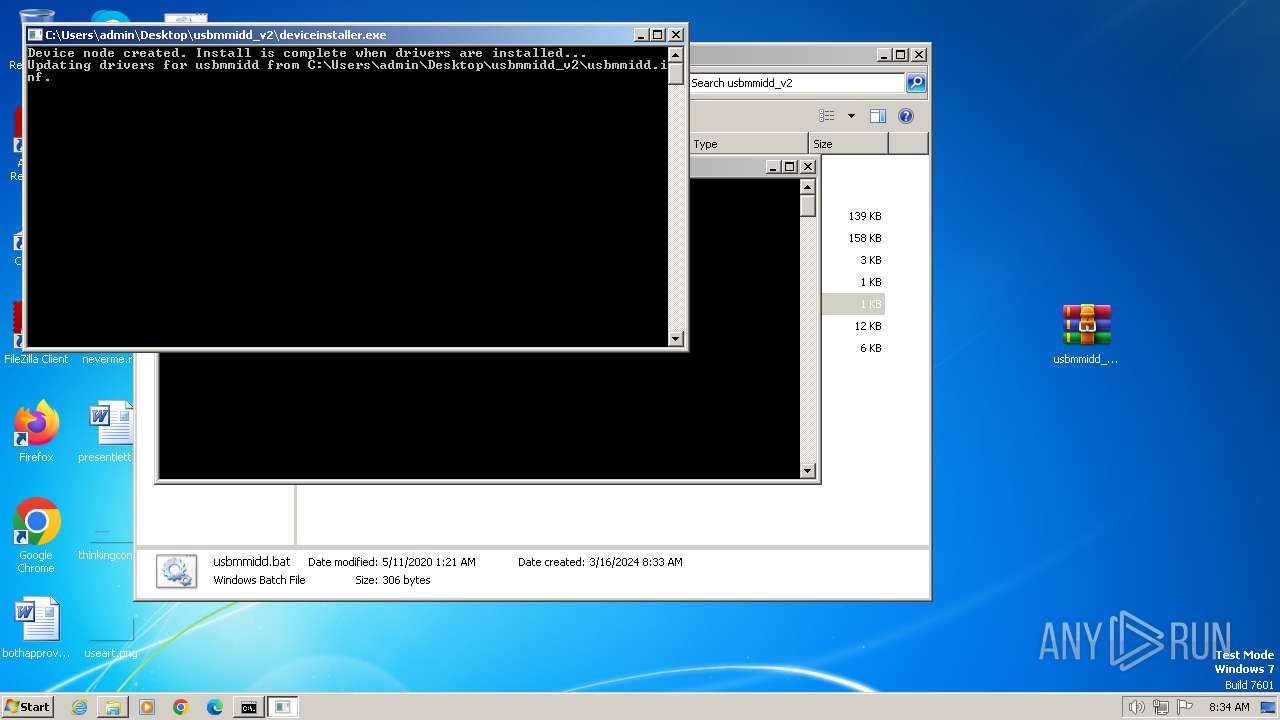
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3936)
- deviceinstaller.exe (PID: 752)
- drvinst.exe (PID: 3484)
- drvinst.exe (PID: 3572)
- drvinst.exe (PID: 2756)
- drvinst.exe (PID: 1888)
- drvinst.exe (PID: 3008)
- drvinst.exe (PID: 3616)
- drvinst.exe (PID: 1792)
Creates a writable file in the system directory
- drvinst.exe (PID: 3484)
- drvinst.exe (PID: 3572)
- drvinst.exe (PID: 2756)
- drvinst.exe (PID: 1888)
- drvinst.exe (PID: 3008)
- drvinst.exe (PID: 3616)
- drvinst.exe (PID: 1792)
Steals credentials from Web Browsers
- taskhost.exe (PID: 3960)
- setup.exe (PID: 3076)
Changes the autorun value in the registry
- unregmp2.exe (PID: 2688)
- regsvr32.exe (PID: 1352)
Create files in the Startup directory
- regsvr32.exe (PID: 1352)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3936)
- deviceinstaller.exe (PID: 752)
- deviceinstaller.exe (PID: 2408)
- deviceinstaller.exe (PID: 3004)
- deviceinstaller.exe (PID: 2776)
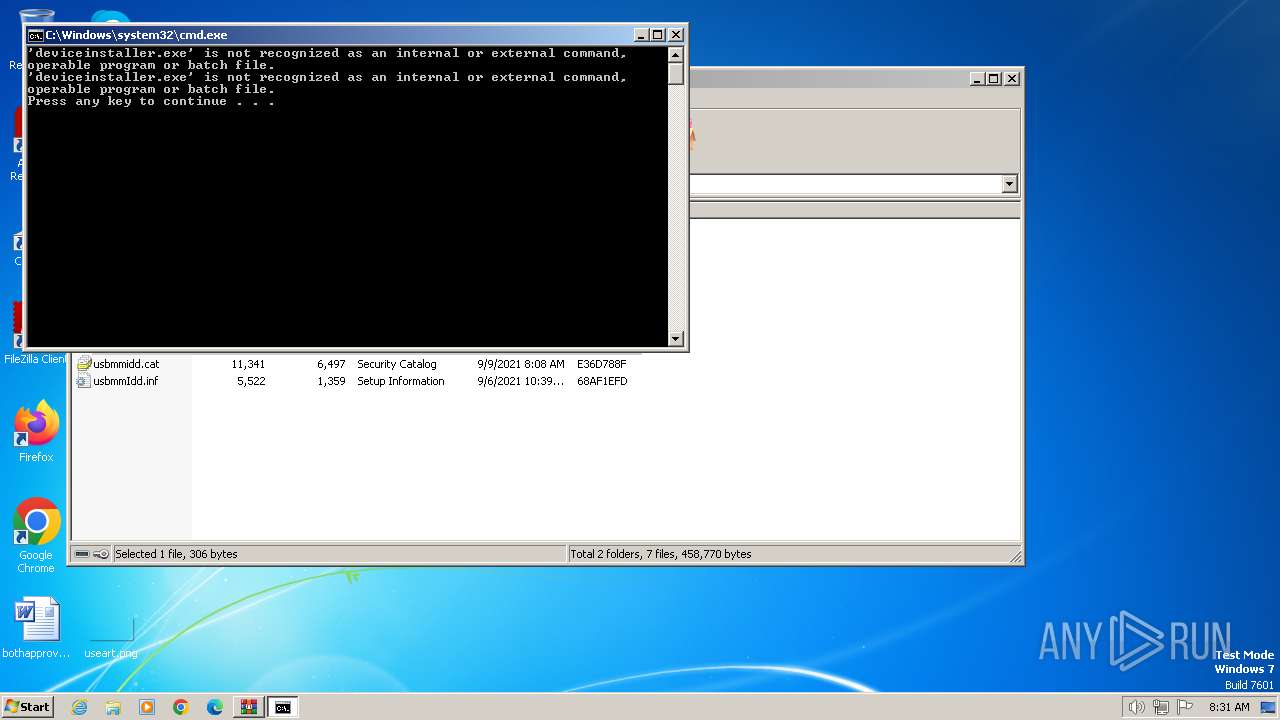
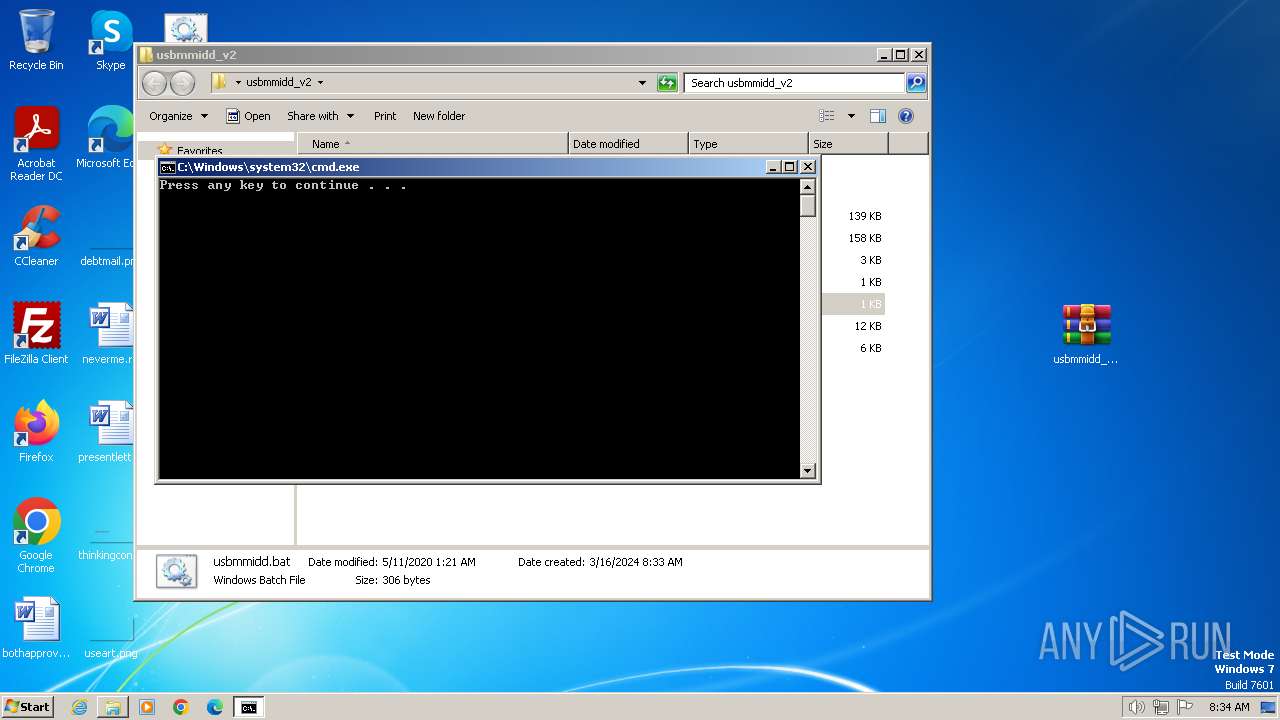
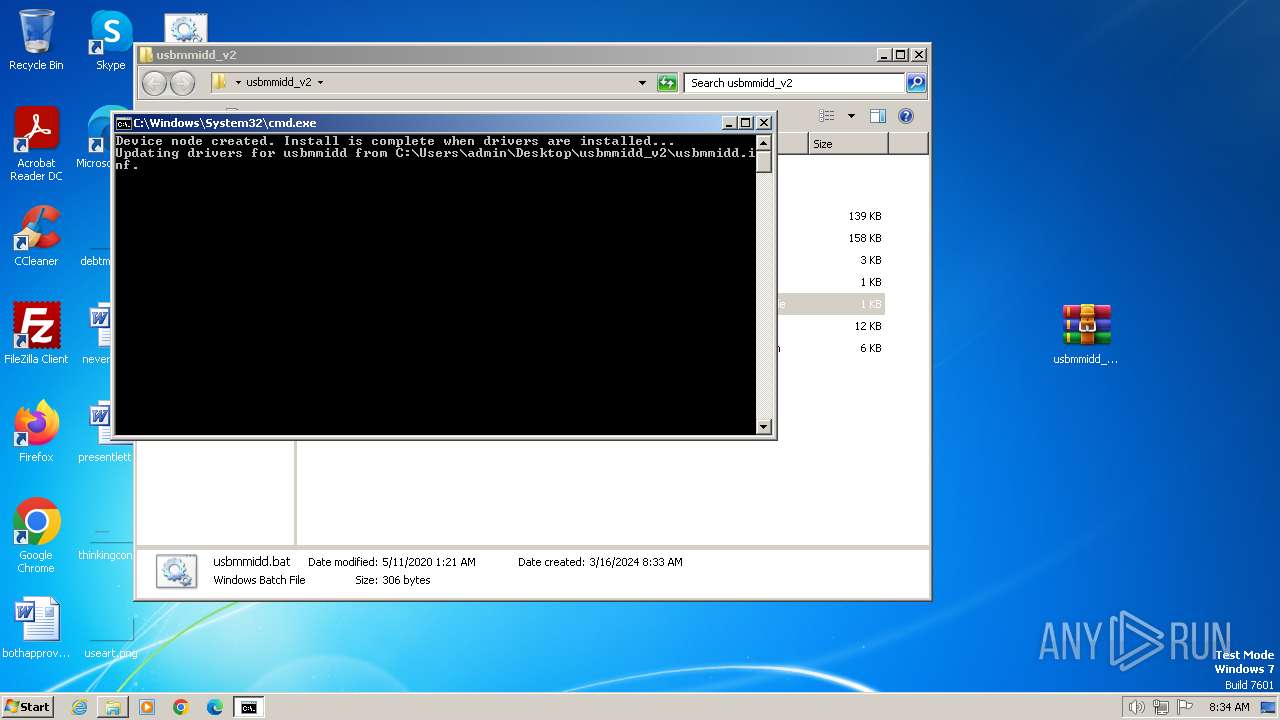
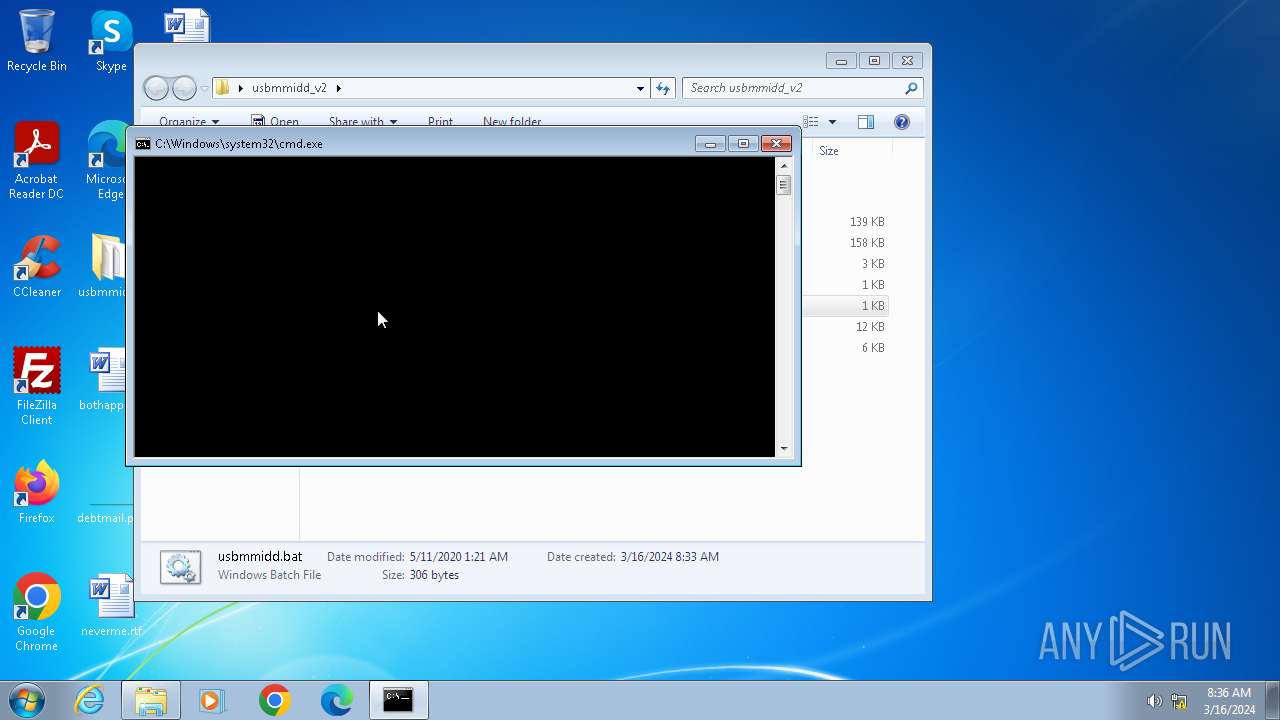
Executing commands from a ".bat" file
- WinRAR.exe (PID: 3936)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 3936)
- cmd.exe (PID: 2960)
- cmd.exe (PID: 3252)
- cmd.exe (PID: 2160)
- cmd.exe (PID: 3384)
- cmd.exe (PID: 2600)
Application launched itself
- cmd.exe (PID: 2960)
- cmd.exe (PID: 3252)
- cmd.exe (PID: 2160)
- cmd.exe (PID: 3384)
- ie4uinit.exe (PID: 4048)
- rundll32.exe (PID: 4052)
- setup.exe (PID: 3076)
- cmd.exe (PID: 2600)
Reads the Internet Settings
- cmd.exe (PID: 2956)
- cmd.exe (PID: 3828)
- cmd.exe (PID: 3764)
- cmd.exe (PID: 3776)
- taskhost.exe (PID: 3960)
- sipnotify.exe (PID: 2644)
- ie4uinit.exe (PID: 4048)
- rundll32.exe (PID: 4052)
- rundll32.exe (PID: 3068)
- ie4uinit.exe (PID: 2860)
- ie4uinit.exe (PID: 3884)
- sipnotify.exe (PID: 636)
- cmd.exe (PID: 2632)
Reads settings of System Certificates
- deviceinstaller.exe (PID: 752)
- deviceinstaller.exe (PID: 2408)
- deviceinstaller.exe (PID: 3004)
- sipnotify.exe (PID: 636)
- deviceinstaller.exe (PID: 2776)
Checks Windows Trust Settings
- deviceinstaller.exe (PID: 752)
- drvinst.exe (PID: 3484)
- drvinst.exe (PID: 3572)
- deviceinstaller.exe (PID: 2408)
- drvinst.exe (PID: 1888)
- deviceinstaller.exe (PID: 3004)
- drvinst.exe (PID: 3008)
- drvinst.exe (PID: 3616)
- drvinst.exe (PID: 1792)
- drvinst.exe (PID: 2756)
- deviceinstaller.exe (PID: 2776)
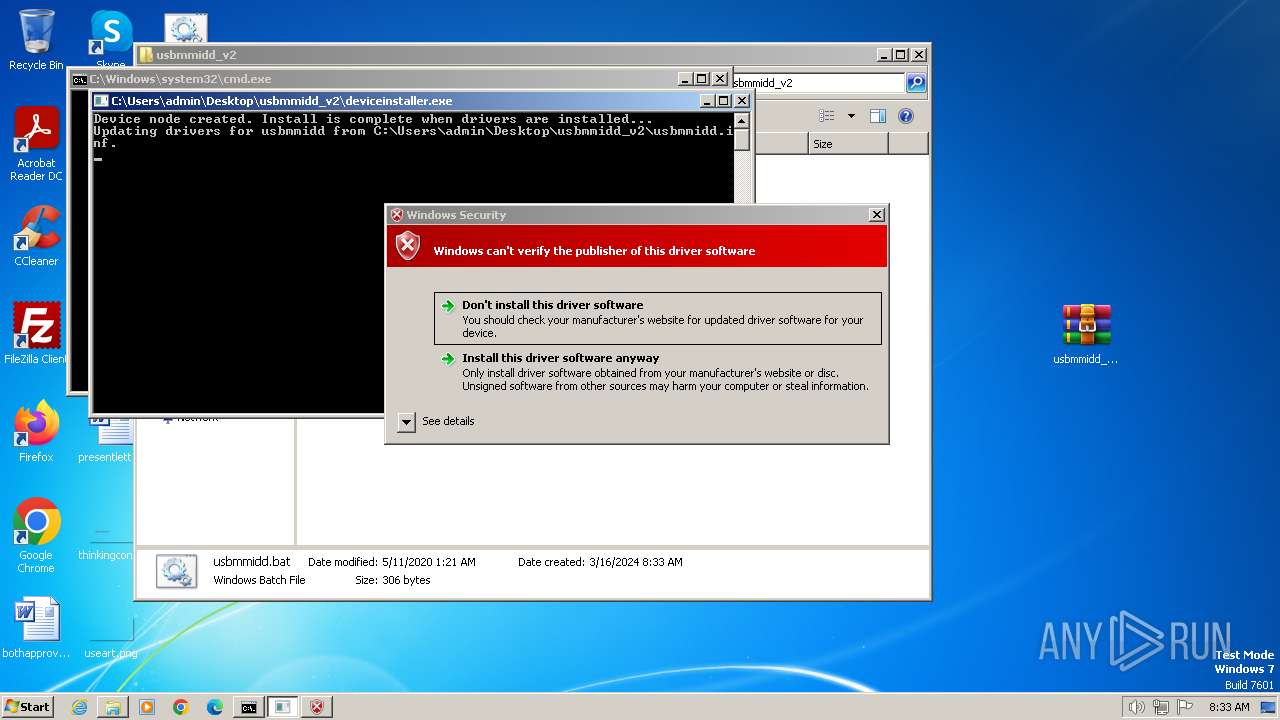
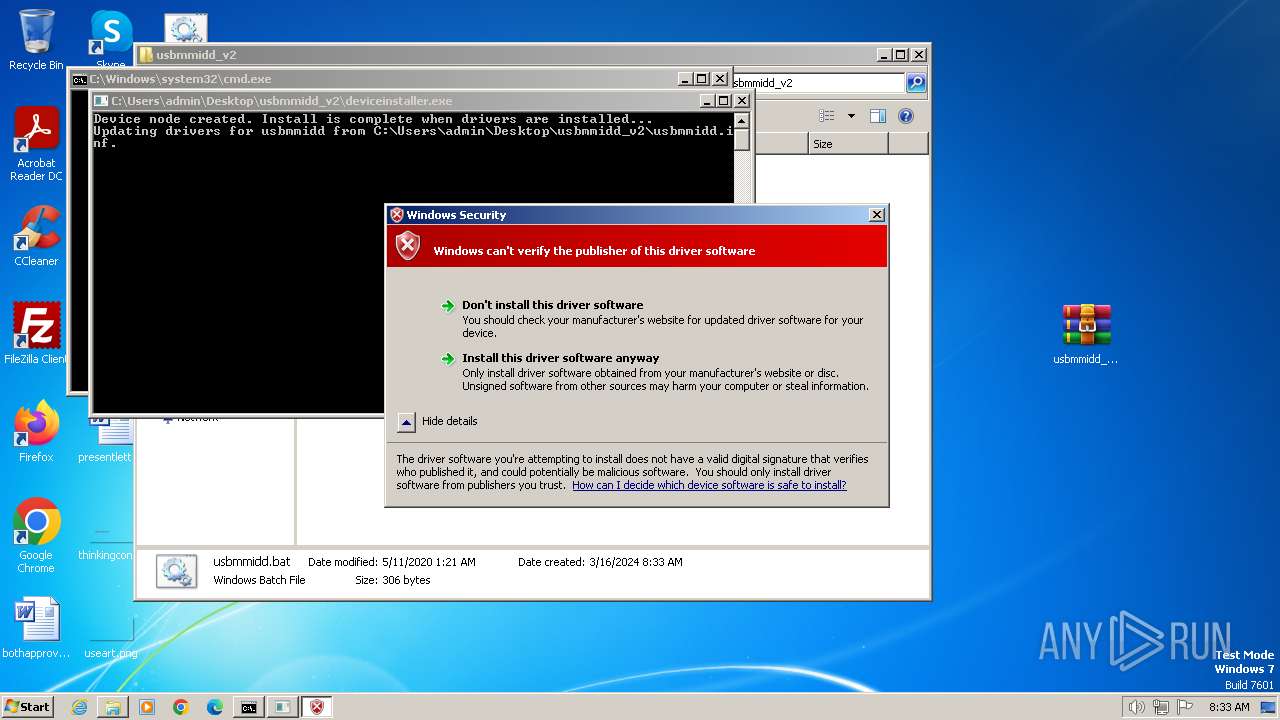
Executable content was dropped or overwritten
- deviceinstaller.exe (PID: 752)
- drvinst.exe (PID: 3484)
- drvinst.exe (PID: 3572)
- drvinst.exe (PID: 2756)
- drvinst.exe (PID: 1888)
- drvinst.exe (PID: 3008)
- drvinst.exe (PID: 3616)
- drvinst.exe (PID: 1792)
Creates files in the driver directory
- drvinst.exe (PID: 3484)
- drvinst.exe (PID: 3572)
- drvinst.exe (PID: 2756)
- drvinst.exe (PID: 1888)
- drvinst.exe (PID: 3008)
- drvinst.exe (PID: 3616)
- drvinst.exe (PID: 1792)
Executes as Windows Service
- VSSVC.exe (PID: 2868)
- taskhost.exe (PID: 3960)
- EOSNotify.exe (PID: 2736)
The process executes via Task Scheduler
- sipnotify.exe (PID: 2644)
- ctfmon.exe (PID: 1712)
- sipnotify.exe (PID: 636)
Changes internet zones settings
- ie4uinit.exe (PID: 4048)
Reads Internet Explorer settings
- ie4uinit.exe (PID: 4048)
Reads Microsoft Outlook installation path
- ie4uinit.exe (PID: 4048)
Uses RUNDLL32.EXE to load library
- ie4uinit.exe (PID: 4048)
- rundll32.exe (PID: 4052)
Write to the desktop.ini file (may be used to cloak folders)
- ie4uinit.exe (PID: 4048)
- unregmp2.exe (PID: 2688)
- regsvr32.exe (PID: 1352)
Changes default file association
- unregmp2.exe (PID: 2688)
INFO
Checks supported languages
- deviceinstaller.exe (PID: 1496)
- deviceinstaller.exe (PID: 752)
- drvinst.exe (PID: 3484)
- drvinst.exe (PID: 3572)
- deviceinstaller.exe (PID: 2036)
- deviceinstaller.exe (PID: 2408)
- drvinst.exe (PID: 1888)
- deviceinstaller.exe (PID: 3676)
- deviceinstaller.exe (PID: 2432)
- deviceinstaller.exe (PID: 3196)
- deviceinstaller.exe (PID: 3004)
- drvinst.exe (PID: 3616)
- drvinst.exe (PID: 3008)
- drvinst.exe (PID: 2756)
- deviceinstaller.exe (PID: 2584)
- deviceinstaller.exe (PID: 948)
- setup.exe (PID: 3076)
- setup.exe (PID: 1556)
- setup.exe (PID: 3716)
- IMEKLMG.EXE (PID: 2040)
- IMEKLMG.EXE (PID: 2128)
- IMKRMIG.EXE (PID: 2468)
- wmpnscfg.exe (PID: 3376)
- wmpnscfg.exe (PID: 3744)
- IMEKLMG.EXE (PID: 1444)
- wmpnscfg.exe (PID: 2400)
- wmpnscfg.exe (PID: 2420)
- deviceinstaller.exe (PID: 1392)
- drvinst.exe (PID: 1792)
- deviceinstaller.exe (PID: 2776)
- IMEKLMG.EXE (PID: 348)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3936)
- WinRAR.exe (PID: 2052)
Create files in a temporary directory
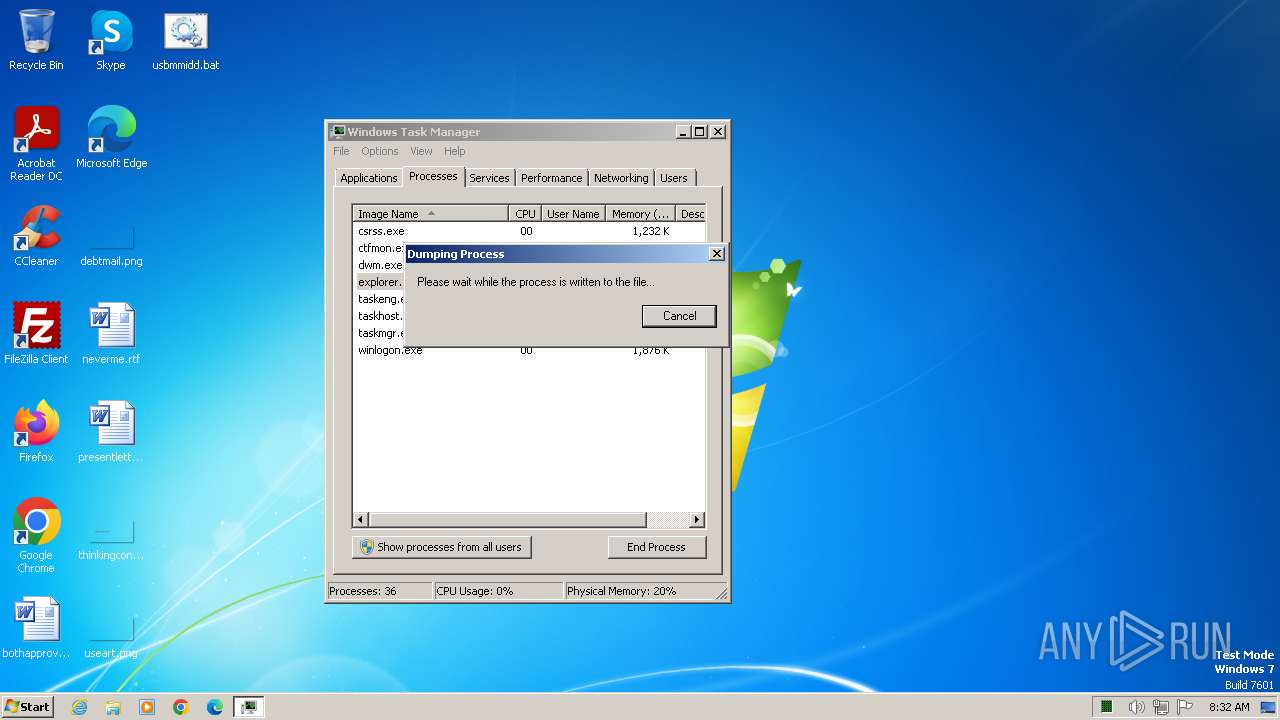
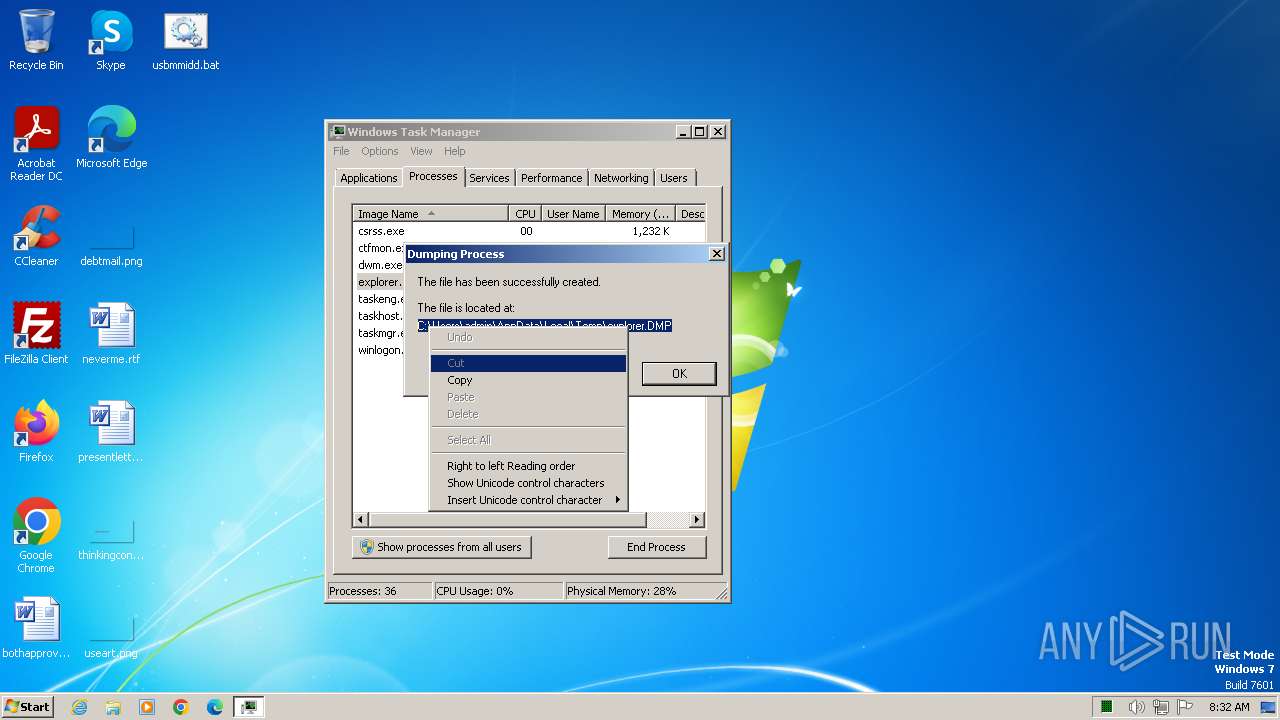
- taskmgr.exe (PID: 2432)
- deviceinstaller.exe (PID: 752)
- rundll32.exe (PID: 3516)
- rundll32.exe (PID: 480)
Manual execution by a user
- explorer.exe (PID: 2244)
- WinRAR.exe (PID: 3616)
- cmd.exe (PID: 2160)
- taskmgr.exe (PID: 2432)
- WinRAR.exe (PID: 2052)
- cmd.exe (PID: 3252)
- deviceinstaller.exe (PID: 2732)
- deviceinstaller.exe (PID: 3636)
- deviceinstaller.exe (PID: 2432)
- deviceinstaller.exe (PID: 3196)
- cmd.exe (PID: 3384)
- deviceinstaller.exe (PID: 1124)
- deviceinstaller.exe (PID: 1392)
- ie4uinit.exe (PID: 4048)
- ie4uinit.exe (PID: 2860)
- unregmp2.exe (PID: 2688)
- ie4uinit.exe (PID: 3884)
- regsvr32.exe (PID: 1352)
- chrmstp.exe (PID: 1368)
- setup.exe (PID: 3076)
- IMEKLMG.EXE (PID: 2128)
- IMEKLMG.EXE (PID: 2040)
- wmpnscfg.exe (PID: 3376)
- wmpnscfg.exe (PID: 3744)
- IMEKLMG.EXE (PID: 1444)
- IMEKLMG.EXE (PID: 348)
- wmpnscfg.exe (PID: 2400)
- cmd.exe (PID: 2600)
- wmpnscfg.exe (PID: 2420)
- deviceinstaller.exe (PID: 948)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2052)
Reads the computer name
- deviceinstaller.exe (PID: 752)
- drvinst.exe (PID: 3484)
- drvinst.exe (PID: 3572)
- deviceinstaller.exe (PID: 2036)
- deviceinstaller.exe (PID: 2408)
- drvinst.exe (PID: 2756)
- drvinst.exe (PID: 1888)
- deviceinstaller.exe (PID: 3676)
- deviceinstaller.exe (PID: 3004)
- drvinst.exe (PID: 3008)
- drvinst.exe (PID: 3616)
- drvinst.exe (PID: 1792)
- deviceinstaller.exe (PID: 2584)
- setup.exe (PID: 1556)
- IMEKLMG.EXE (PID: 2128)
- setup.exe (PID: 3716)
- IMEKLMG.EXE (PID: 2040)
- wmpnscfg.exe (PID: 3376)
- wmpnscfg.exe (PID: 3744)
- IMEKLMG.EXE (PID: 1444)
- IMEKLMG.EXE (PID: 348)
- wmpnscfg.exe (PID: 2400)
- wmpnscfg.exe (PID: 2420)
- deviceinstaller.exe (PID: 2776)
Reads the software policy settings
- deviceinstaller.exe (PID: 752)
- drvinst.exe (PID: 3484)
- drvinst.exe (PID: 3572)
- deviceinstaller.exe (PID: 2408)
- drvinst.exe (PID: 1888)
- deviceinstaller.exe (PID: 3004)
- drvinst.exe (PID: 3008)
- drvinst.exe (PID: 3616)
- drvinst.exe (PID: 2756)
- drvinst.exe (PID: 1792)
- sipnotify.exe (PID: 636)
- deviceinstaller.exe (PID: 2776)
Reads the machine GUID from the registry
- deviceinstaller.exe (PID: 752)
- drvinst.exe (PID: 3484)
- drvinst.exe (PID: 3572)
- deviceinstaller.exe (PID: 2408)
- drvinst.exe (PID: 1888)
- deviceinstaller.exe (PID: 3004)
- drvinst.exe (PID: 3008)
- drvinst.exe (PID: 3616)
- drvinst.exe (PID: 2756)
- drvinst.exe (PID: 1792)
- deviceinstaller.exe (PID: 2776)
Creates files or folders in the user directory
- rundll32.exe (PID: 3516)
- rundll32.exe (PID: 480)
Reads security settings of Internet Explorer
- ie4uinit.exe (PID: 4048)
- sipnotify.exe (PID: 636)
Checks proxy server information
- ie4uinit.exe (PID: 4048)
Creates files in the program directory
- ie4uinit.exe (PID: 4048)
- chrmstp.exe (PID: 980)
- chrmstp.exe (PID: 1368)
- setup.exe (PID: 3076)
- setup.exe (PID: 1556)
- setup.exe (PID: 3716)
Application launched itself
- chrmstp.exe (PID: 1368)
- chrmstp.exe (PID: 980)
- msedge.exe (PID: 1236)
Process checks whether UAC notifications are on
- IMEKLMG.EXE (PID: 2040)
- IMEKLMG.EXE (PID: 2128)
- IMEKLMG.EXE (PID: 348)
- IMEKLMG.EXE (PID: 1444)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:05:13 11:16:44 |
| ZipCRC: | 0xc1e97d1b |
| ZipCompressedSize: | 54351 |
| ZipUncompressedSize: | 142336 |
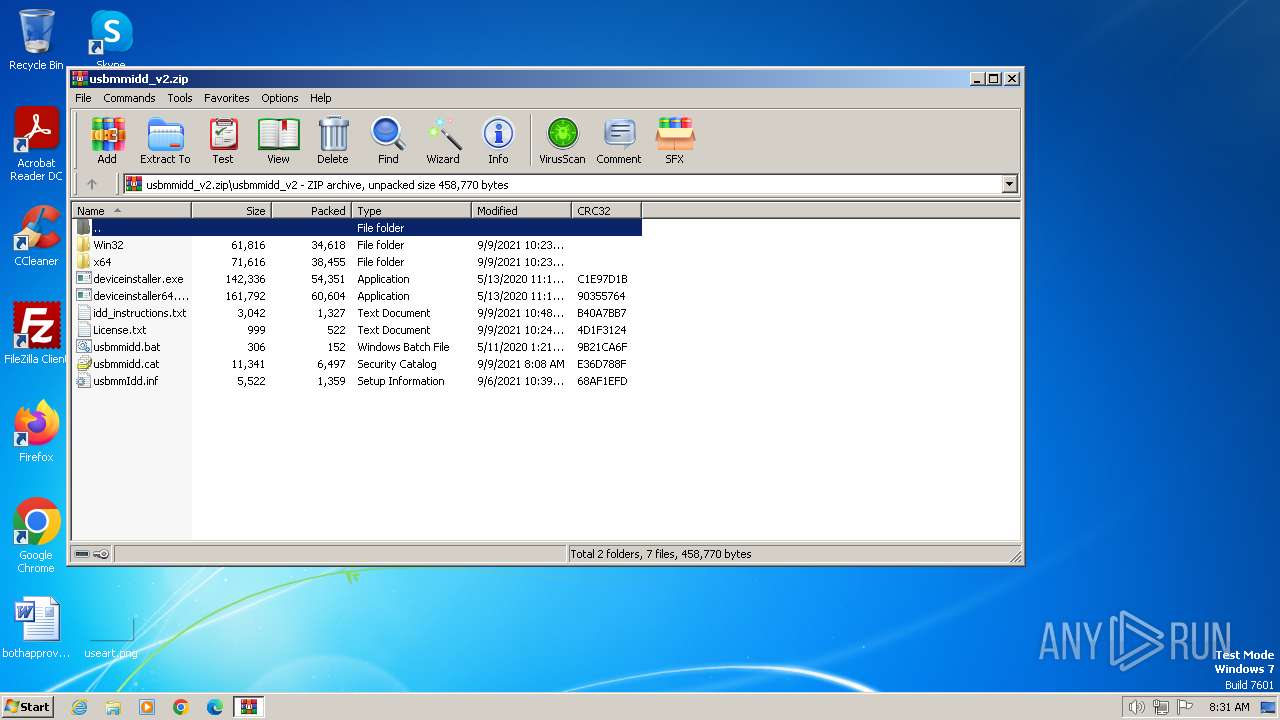
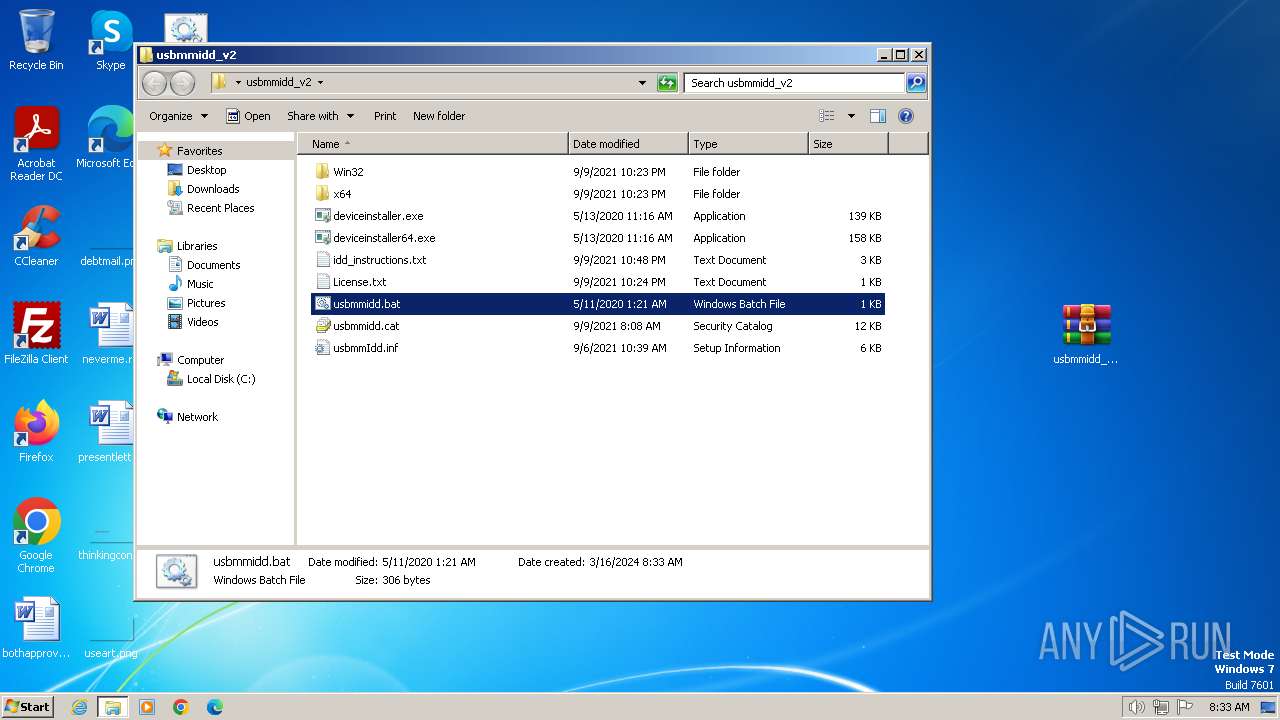
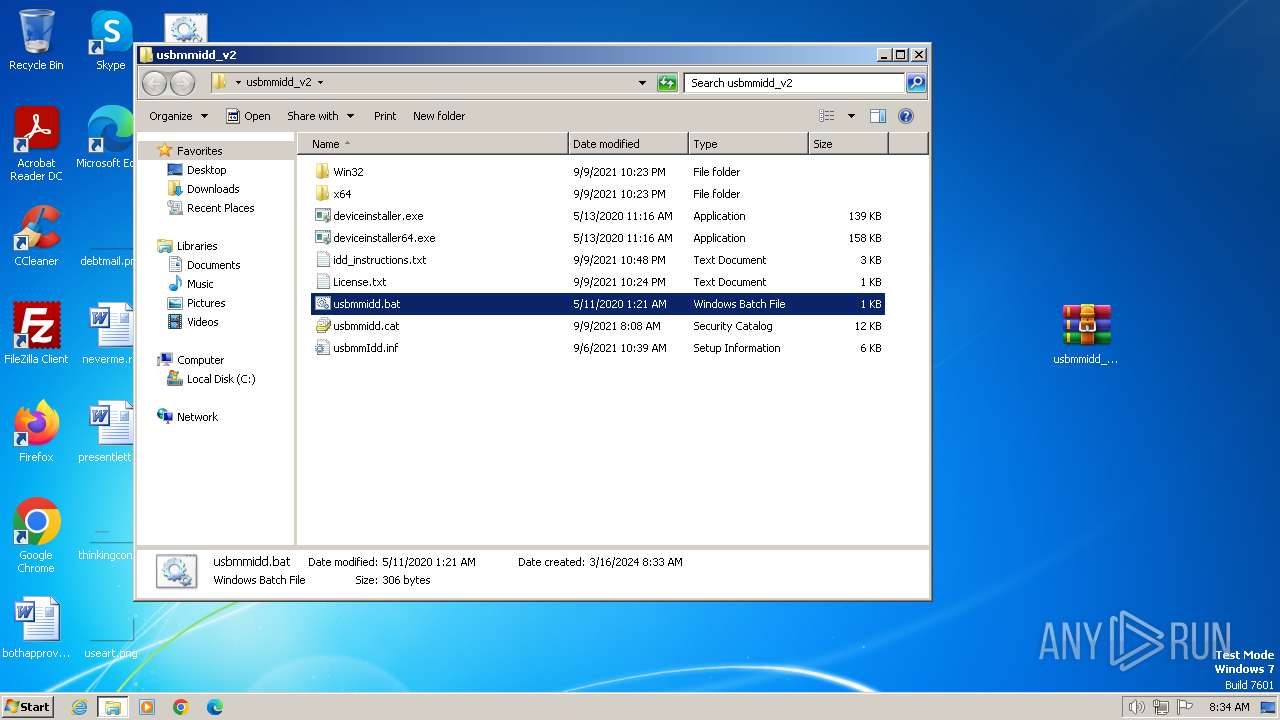
| ZipFileName: | usbmmidd_v2/deviceinstaller.exe |
Total processes
245
Monitored processes
93
Malicious processes
20
Suspicious processes
10
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 348 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /KOR /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 480 | rundll32.exe C:\Windows\system32\newdev.dll,pDiDeviceInstallNotification \\.\pipe\PNP_Device_Install_Pipe_1.{d3d16b73-77b0-46ea-b86f-8c8d095d4edf} "(null)" | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 636 | C:\Windows\system32\sipnotify.exe -LogonOrUnlock | C:\Windows\System32\sipnotify.exe | taskeng.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: sipnotify Exit code: 0 Version: 6.1.7602.20480 (win7sp1_ldr_escrow.191010-1716) Modules
| |||||||||||||||
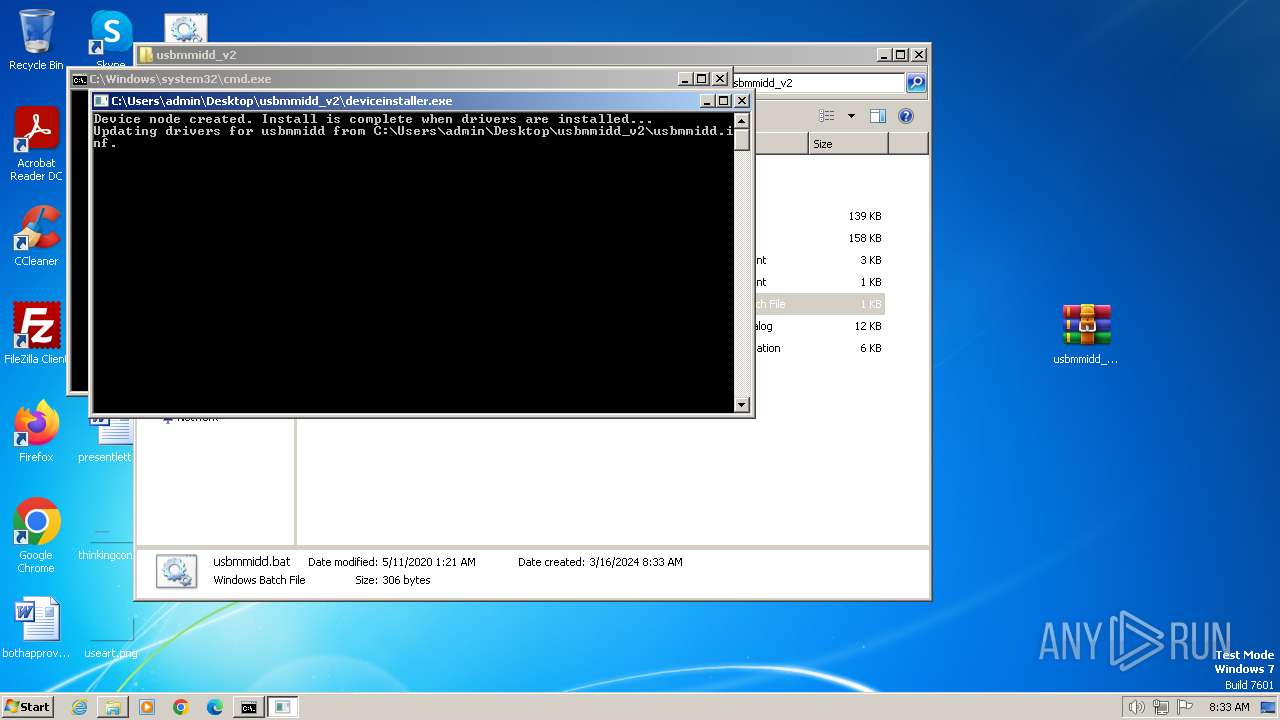
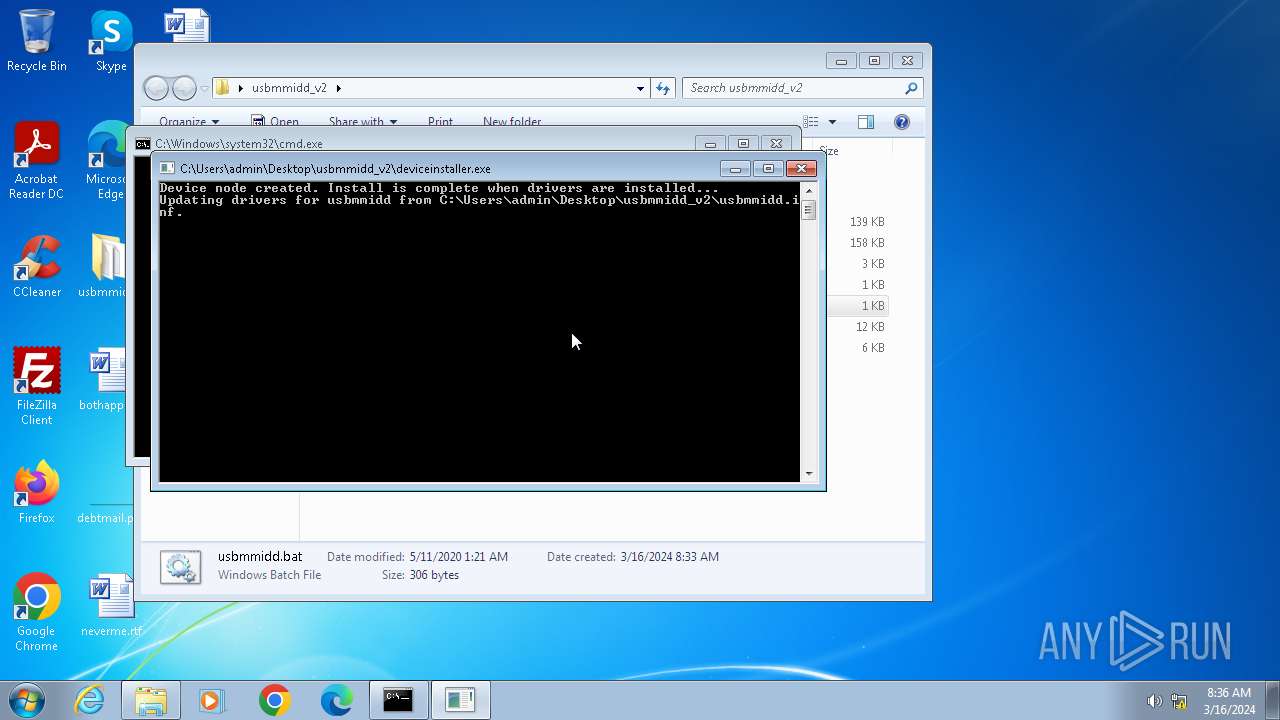
| 752 | "C:\Users\admin\Desktop\usbmmidd_v2\deviceinstaller.exe" install usbmmidd.inf usbmmidd | C:\Users\admin\Desktop\usbmmidd_v2\deviceinstaller.exe | cmd.exe | ||||||||||||
User: admin Company: Amyuni Technologies Integrity Level: HIGH Description: USB Mobile Monitor Device Installer Exit code: 1 Version: 1, 0, 2, 9 Modules
| |||||||||||||||
| 948 | "C:\Users\admin\Desktop\usbmmidd_v2\deviceinstaller.exe" | C:\Users\admin\Desktop\usbmmidd_v2\deviceinstaller.exe | explorer.exe | ||||||||||||
User: admin Company: Amyuni Technologies Integrity Level: HIGH Description: USB Mobile Monitor Device Installer Exit code: 3 Version: 1, 0, 2, 9 Modules
| |||||||||||||||
| 980 | "C:\Program Files\Google\Chrome\Application\109.0.5414.120\Installer\chrmstp.exe" --system-level --verbose-logging --installerdata="C:\Program Files\Google\Chrome\Application\master_preferences" --create-shortcuts=1 --install-level=0 | C:\Program Files\Google\Chrome\Application\109.0.5414.120\Installer\chrmstp.exe | — | chrmstp.exe | |||||||||||
User: Administrator Company: Google LLC Integrity Level: HIGH Description: Google Chrome Installer Exit code: 73 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1112 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\Administrator\AppData\Local\Microsoft\Edge\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\Administrator\AppData\Local\Microsoft\Edge\User Data\Crashpad" "--metrics-dir=C:\Users\Administrator\AppData\Local\Microsoft\Edge\User Data" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=109.0.5414.149 "--annotation=exe=C:\Program Files\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win32 "--annotation=prod=Microsoft Edge" --annotation=ver=109.0.1518.115 --initial-client-data=0xc4,0xc8,0xcc,0x98,0xd4,0x698df598,0x698df5a8,0x698df5b4 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1124 | "C:\Users\admin\Desktop\usbmmidd_v2\deviceinstaller.exe" | C:\Users\admin\Desktop\usbmmidd_v2\deviceinstaller.exe | — | explorer.exe | |||||||||||
User: admin Company: Amyuni Technologies Integrity Level: MEDIUM Description: USB Mobile Monitor Device Installer Exit code: 3221226540 Version: 1, 0, 2, 9 Modules
| |||||||||||||||
| 1124 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=1656 --field-trial-handle=1308,i,17087470133814600537,3156935407693453985,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1236 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --continue-active-setup | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | setup.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
66 249
Read events
64 316
Write events
1 650
Delete events
283
Modification events
| (PID) Process: | (3936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3936) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\usbmmidd_v2.zip | |||
| (PID) Process: | (3936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
46
Suspicious files
51
Text files
100
Unknown types
44
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
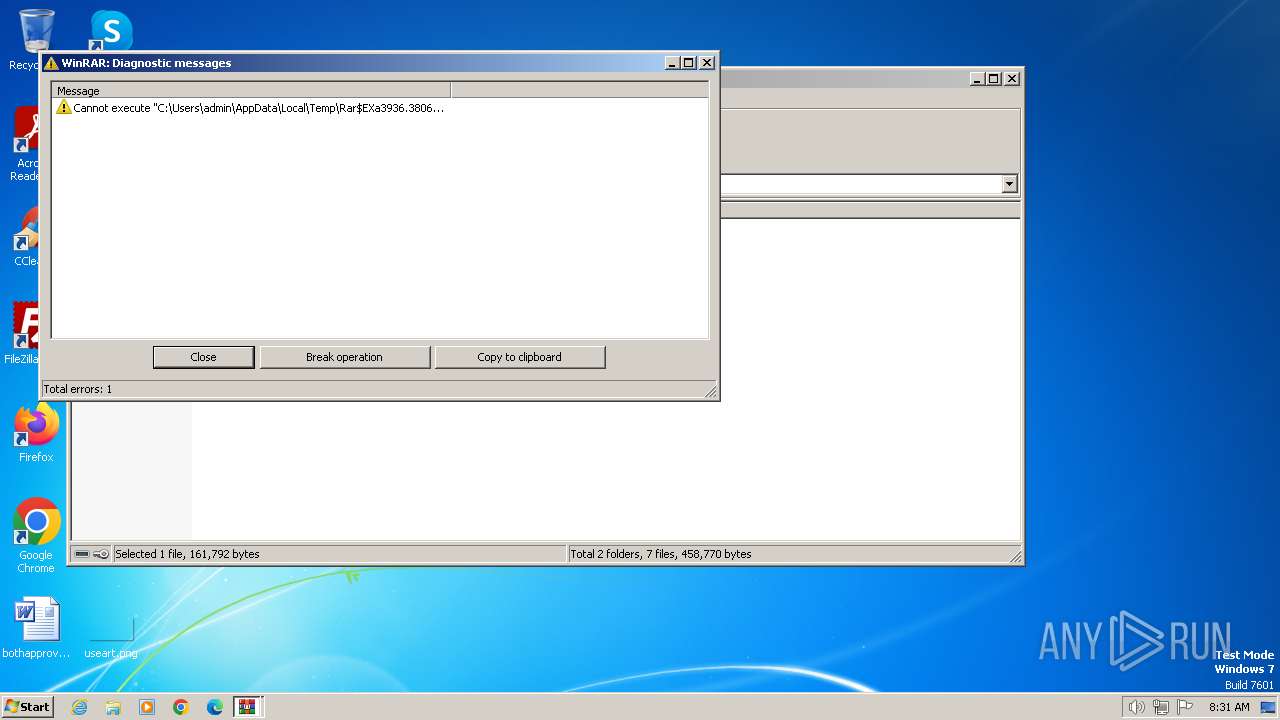
| 3936 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3936.38062\usbmmidd_v2\usbmmidd.bat | text | |
MD5:BD43653A6BA586A0074798FC87238B71 | SHA256:442F084B310DE46ED9C70F64574FA79559554EA8931C92EE05F8ED7C8D8C0DFC | |||
| 2432 | taskmgr.exe | C:\Users\admin\AppData\Local\Temp\explorer.DMP | — | |
MD5:— | SHA256:— | |||
| 3936 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3936.38515\usbmmidd_v2\deviceinstaller.exe | executable | |
MD5:9DC576103B6C58580612C060310D5897 | SHA256:918BE90CCCF70CCD20D42F564710335F1B6A7322ECEF8E432737B6A4D2743A6C | |||
| 3936 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3936.38062\usbmmidd_v2\x64\usbmmIdd.dll | executable | |
MD5:EE848C427145609D998725A38E7AD9AF | SHA256:DC135D675127113915A7E5AA9FE57C84EDAD6BE41D0890B265EF124AB26EA9E3 | |||
| 3936 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3936.38062\usbmmidd_v2\usbmmIdd.inf | txt | |
MD5:0A09DAB1C9A7F2E685CD7F8B5BD43EC0 | SHA256:A8750CA15A86742F3012886C9932BB974158CD2D9779CF891C730D976A47726A | |||
| 3936 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3936.38515\usbmmidd_v2\deviceinstaller64.exe | executable | |
MD5:41283E1240ACFC163F0E697073F07413 | SHA256:E9BAA02CDAE921ACF0AAE4D8E8C29A4CDF4057AB61F9C60862B7CC439E2753F7 | |||
| 3936 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3936.38515\usbmmidd_v2\License.txt | text | |
MD5:B2F8C01EB38B20AF6C5A7D82D9ADAE7A | SHA256:44C73FC4110979899DBB5054662DE581F7D4350939F19BB2D50574F613314BA2 | |||
| 3936 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3936.38062\usbmmidd_v2\Win32\usbmmIdd.dll | executable | |
MD5:35B4CD69A125D475A9456E0FE43B6514 | SHA256:07CEEBAECF203FEF39117576D8B49D803C0FB1F6C7AA5175A6EBAB110D54FED2 | |||
| 3936 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3936.38062\usbmmidd_v2\usbmmidd.cat | cat | |
MD5:E5F60B2F3A491983EAC00DC7DC7C408B | SHA256:470149C4CF9970BA59070AA7C9409C9F63A15727DE99BAB53E7E51F55310779F | |||
| 3936 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3936.38515\usbmmidd_v2\usbmmidd.cat | cat | |
MD5:E5F60B2F3A491983EAC00DC7DC7C408B | SHA256:470149C4CF9970BA59070AA7C9409C9F63A15727DE99BAB53E7E51F55310779F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
11
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
636 | sipnotify.exe | HEAD | 200 | 23.197.138.118:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133550517640000000 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2644 | sipnotify.exe | 23.197.138.118:80 | query.prod.cms.rt.microsoft.com | Akamai International B.V. | US | unknown |
1116 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
636 | sipnotify.exe | 23.197.138.118:80 | query.prod.cms.rt.microsoft.com | Akamai International B.V. | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
query.prod.cms.rt.microsoft.com |
| whitelisted |
dns.msftncsi.com |
| shared |