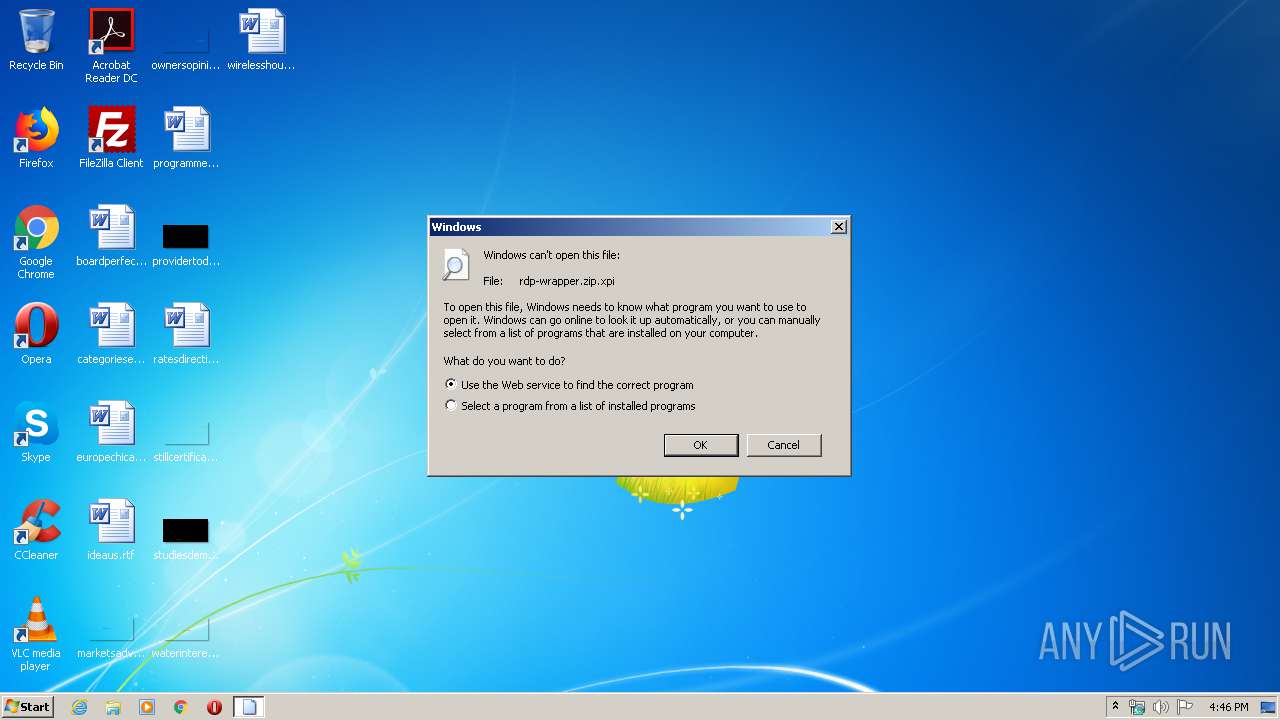
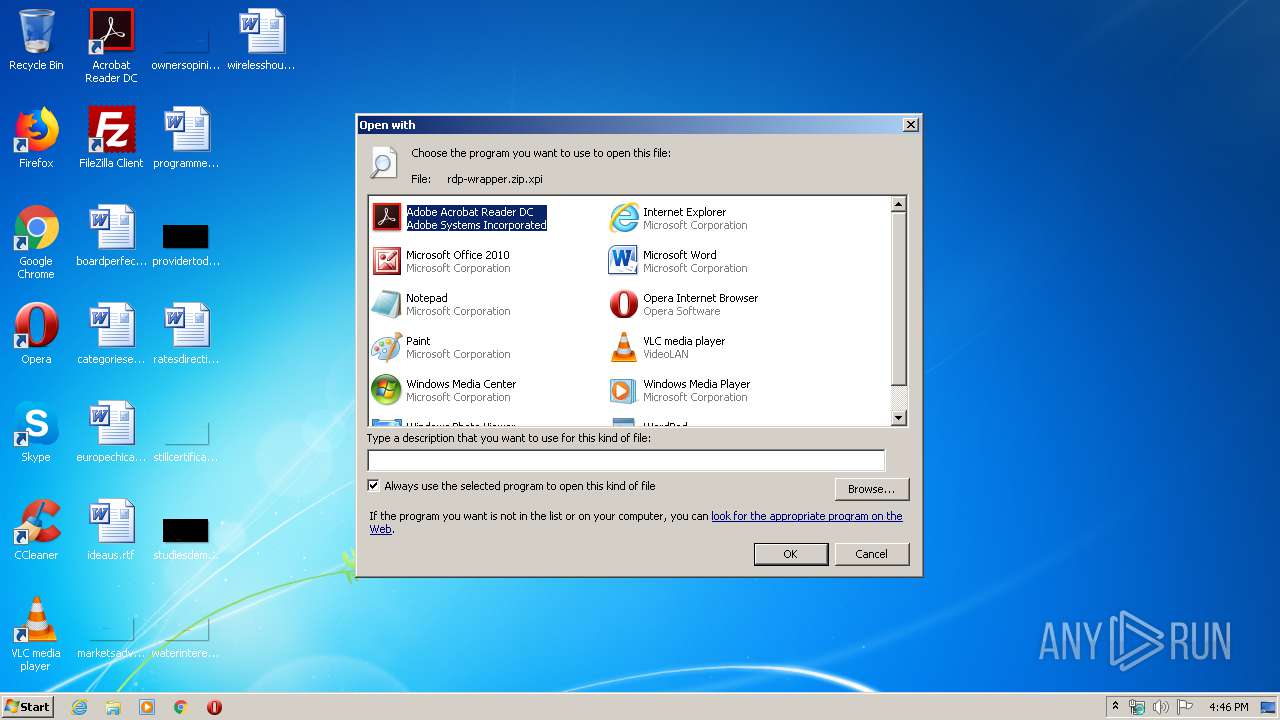
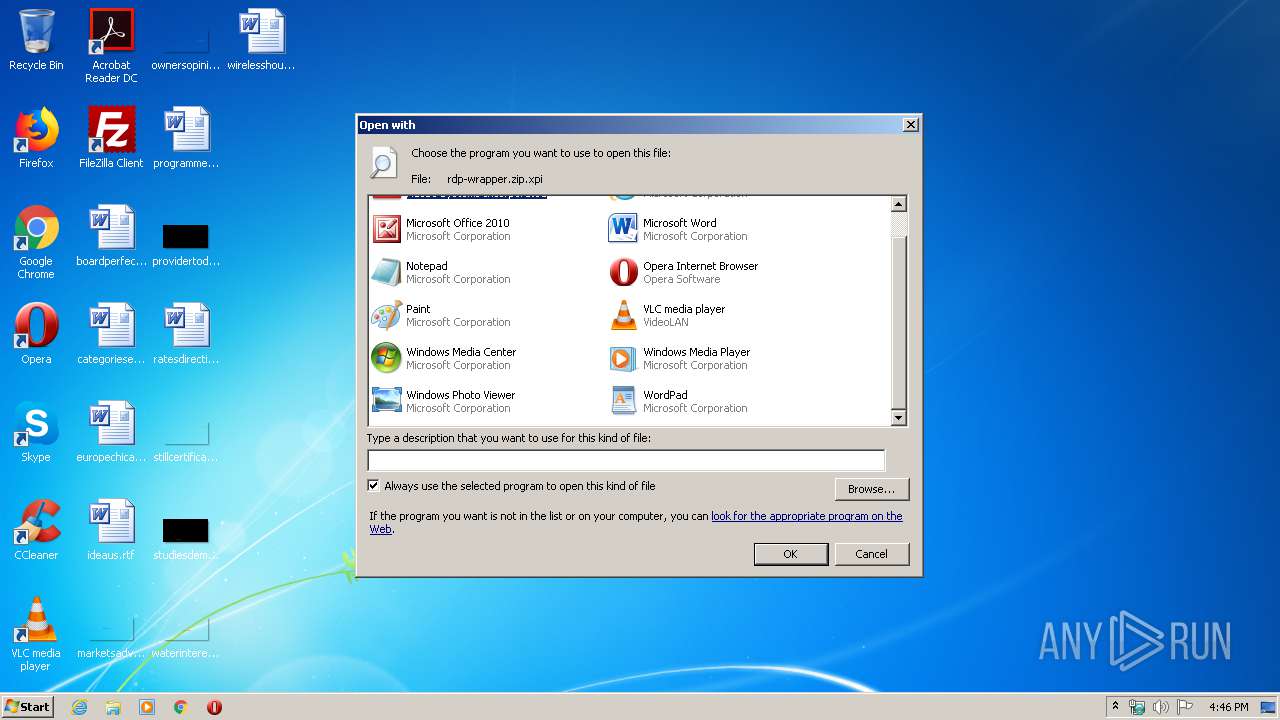
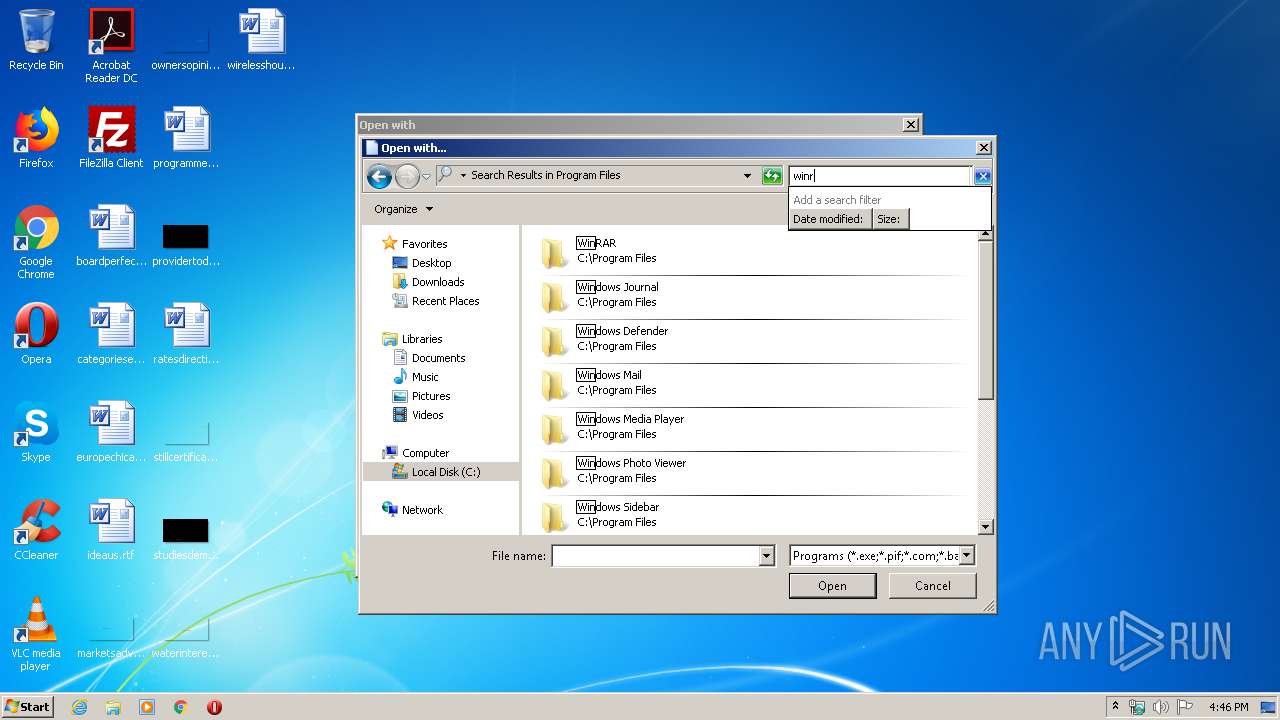
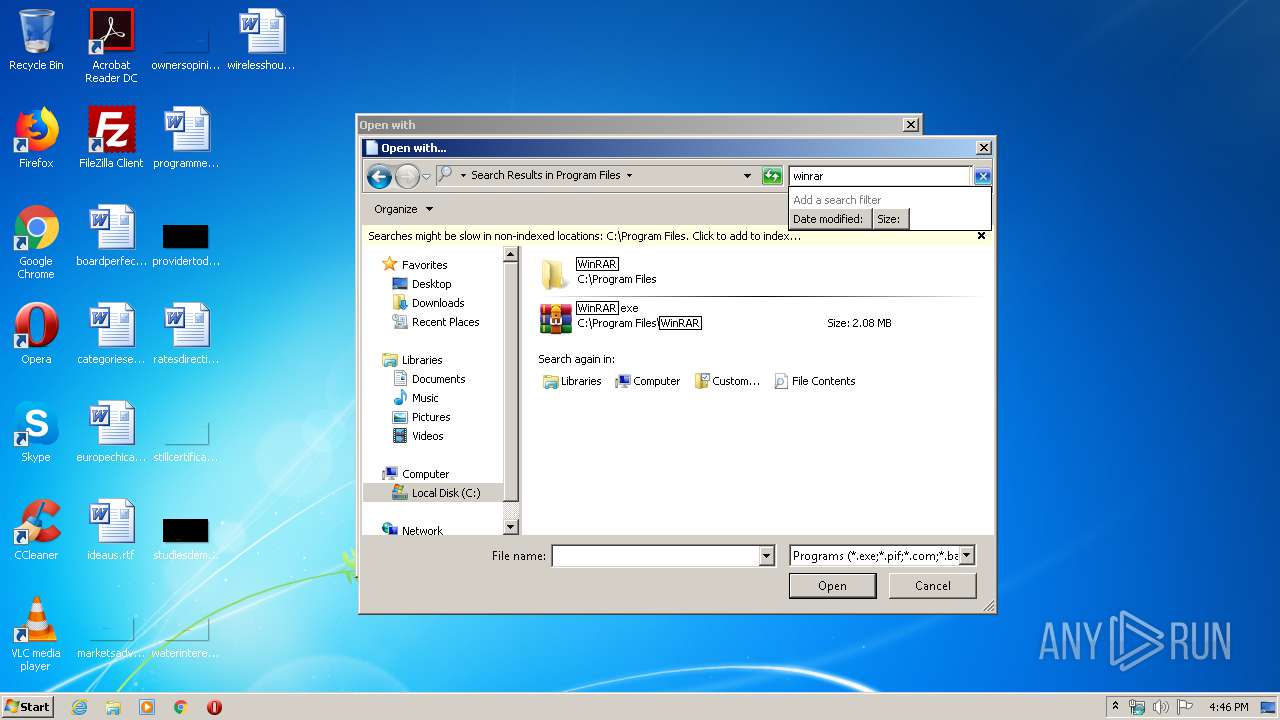
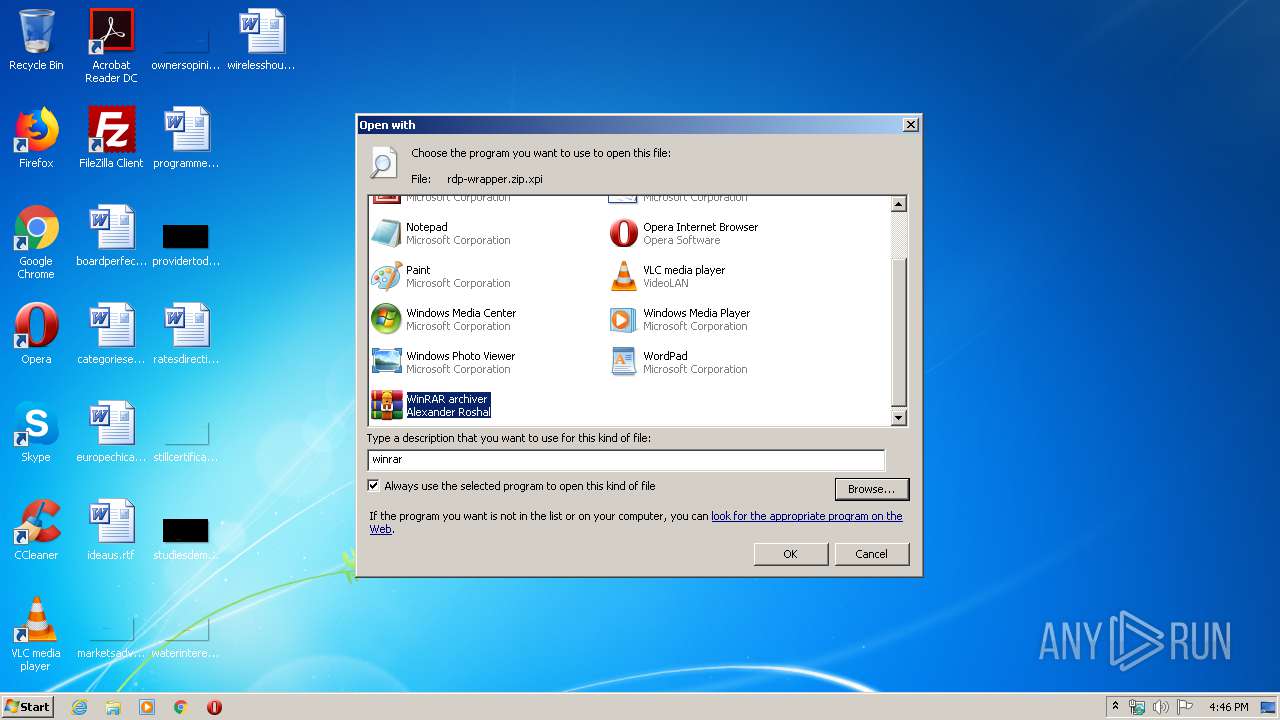
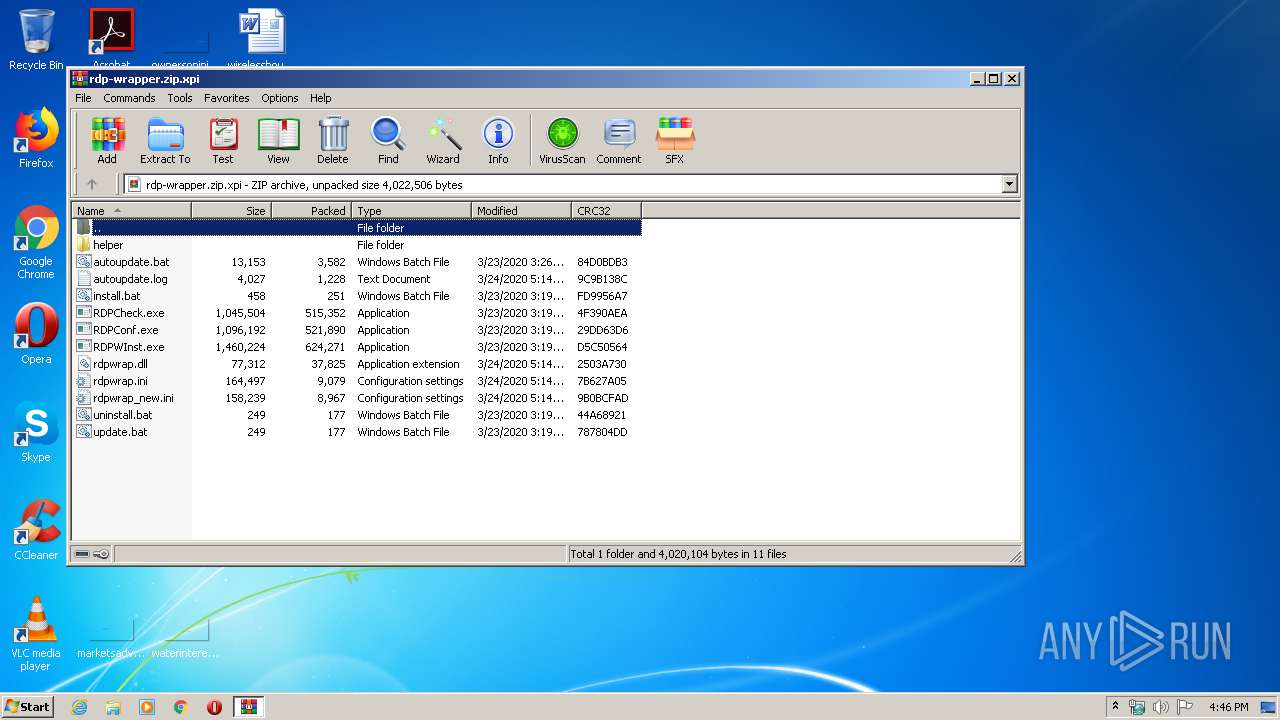
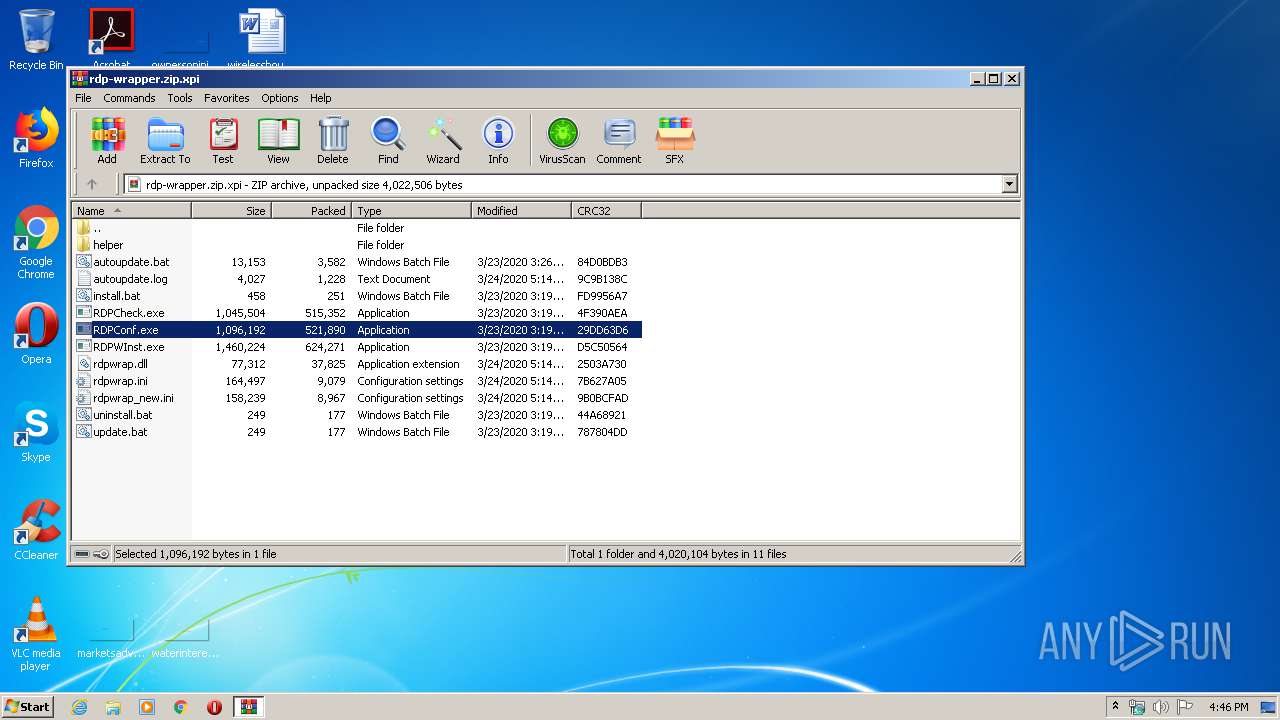
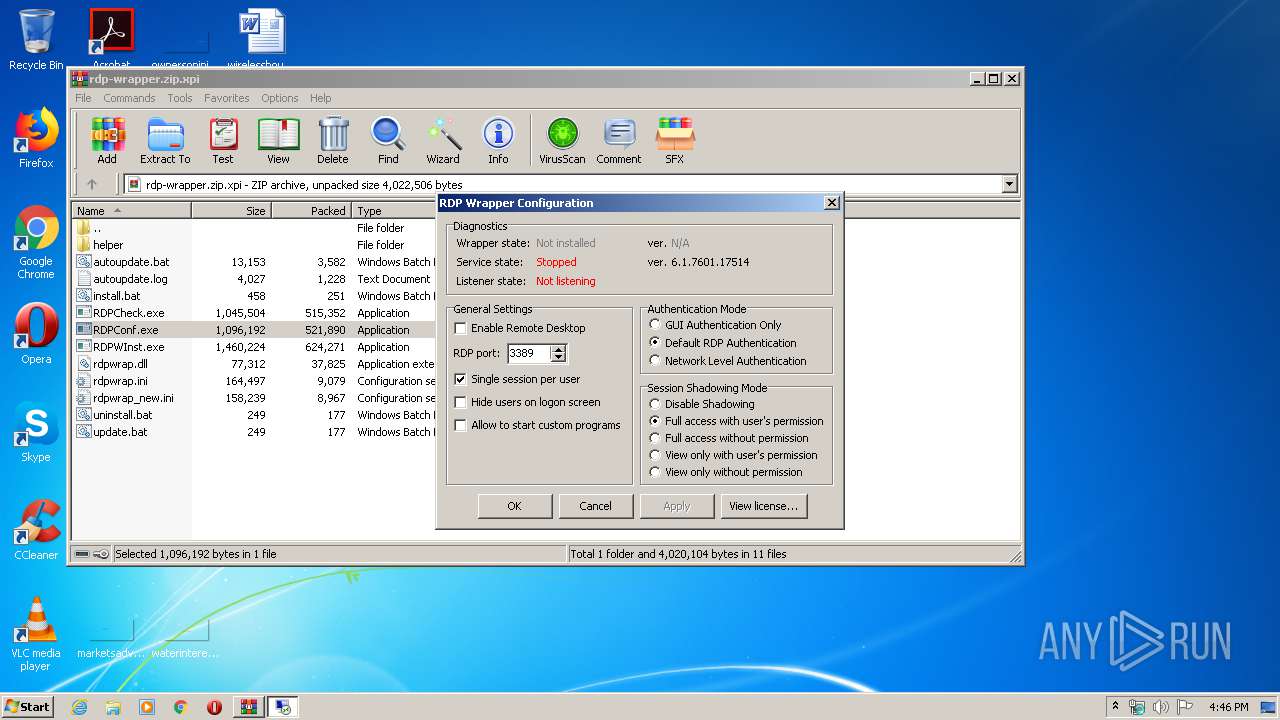
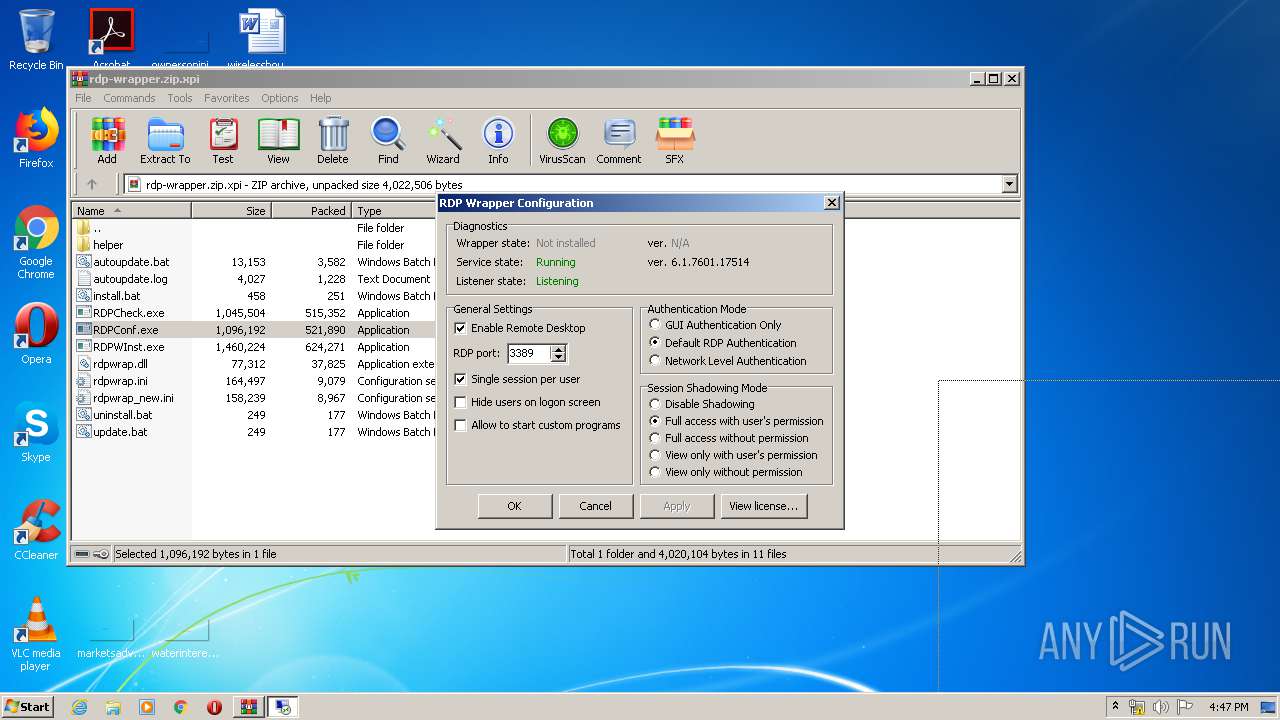
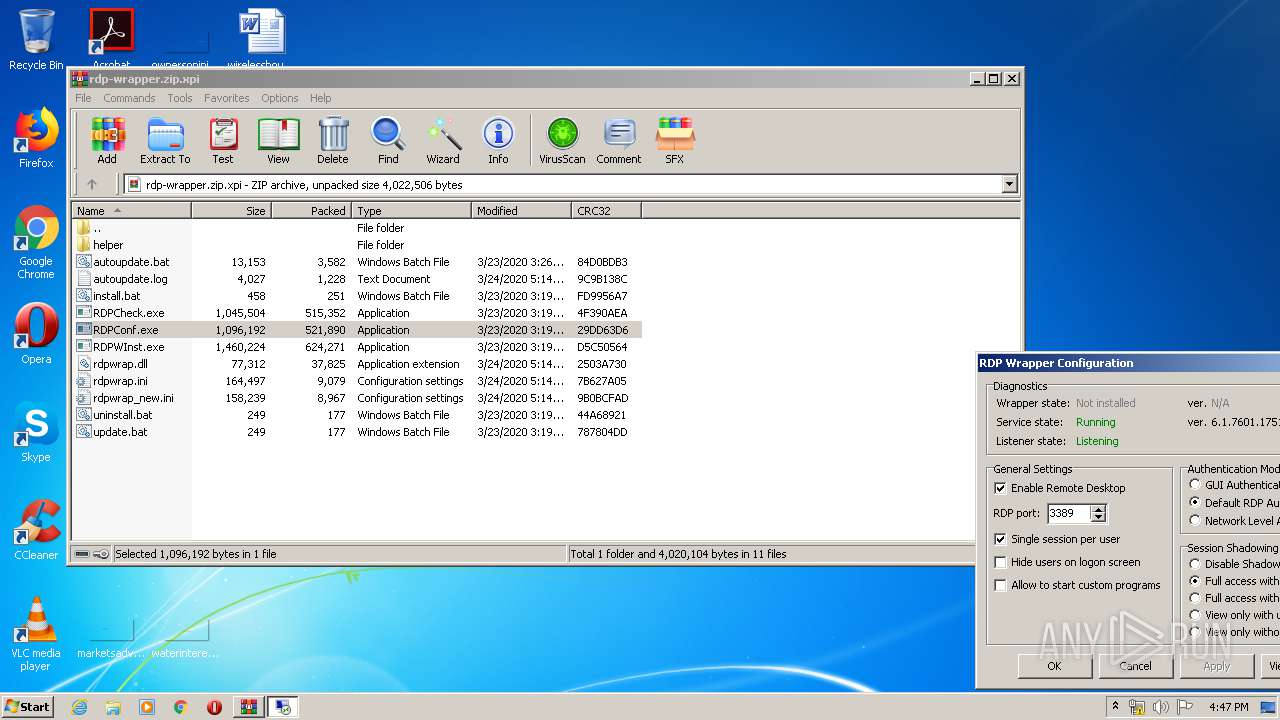
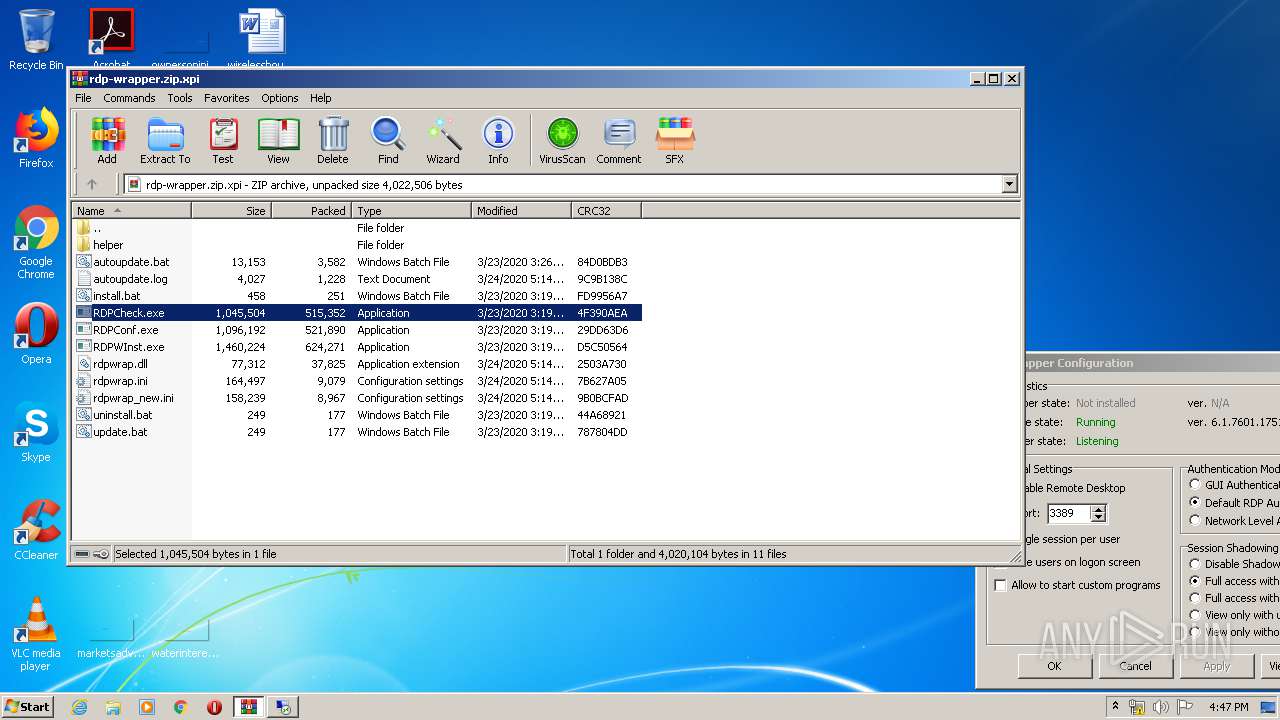
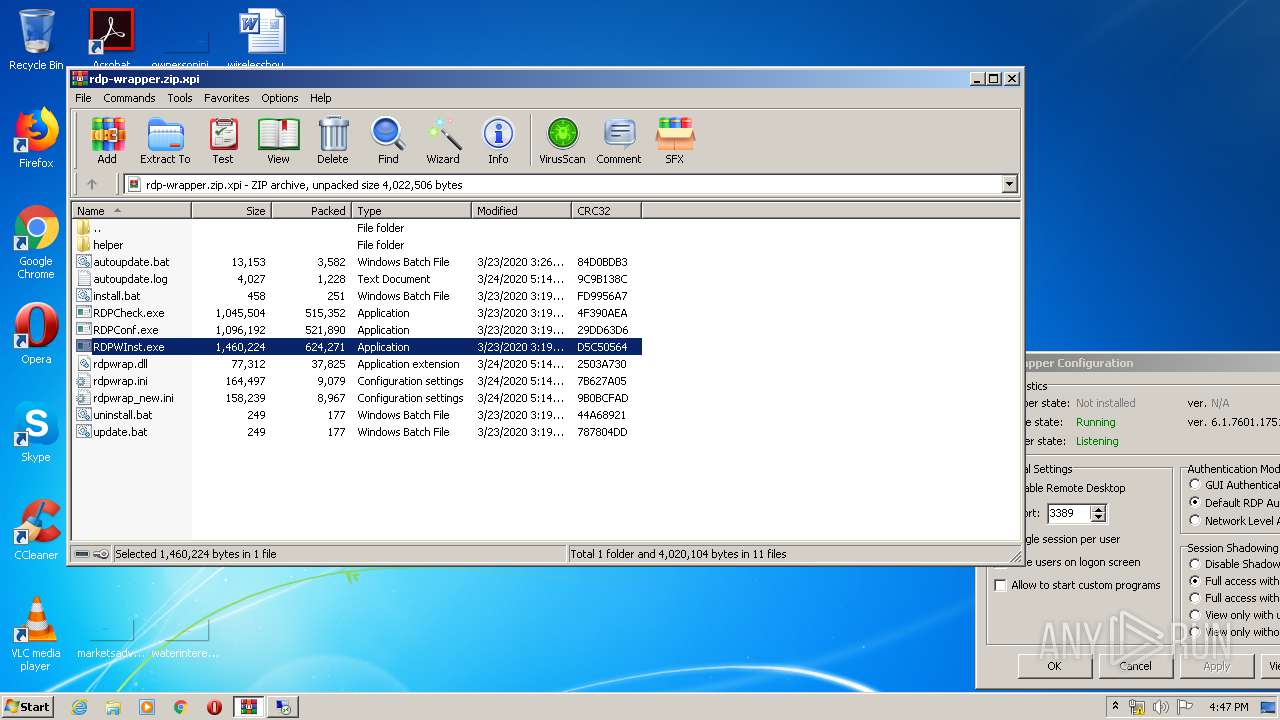
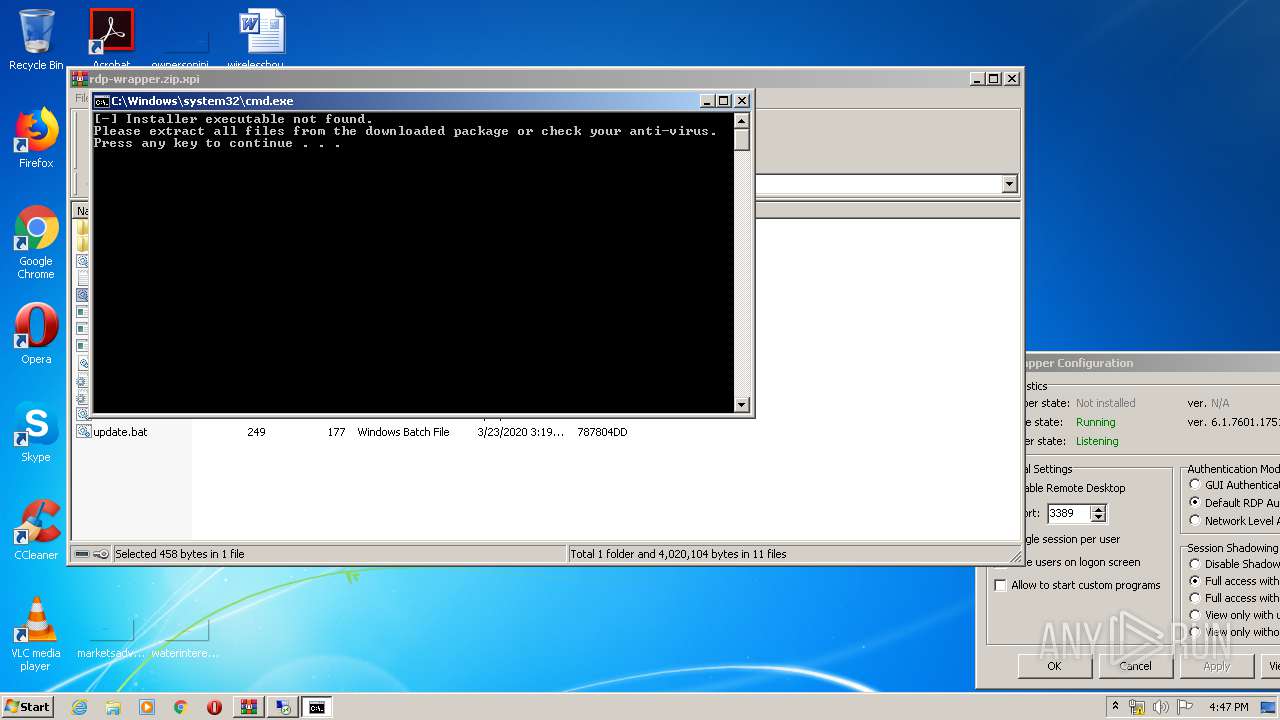
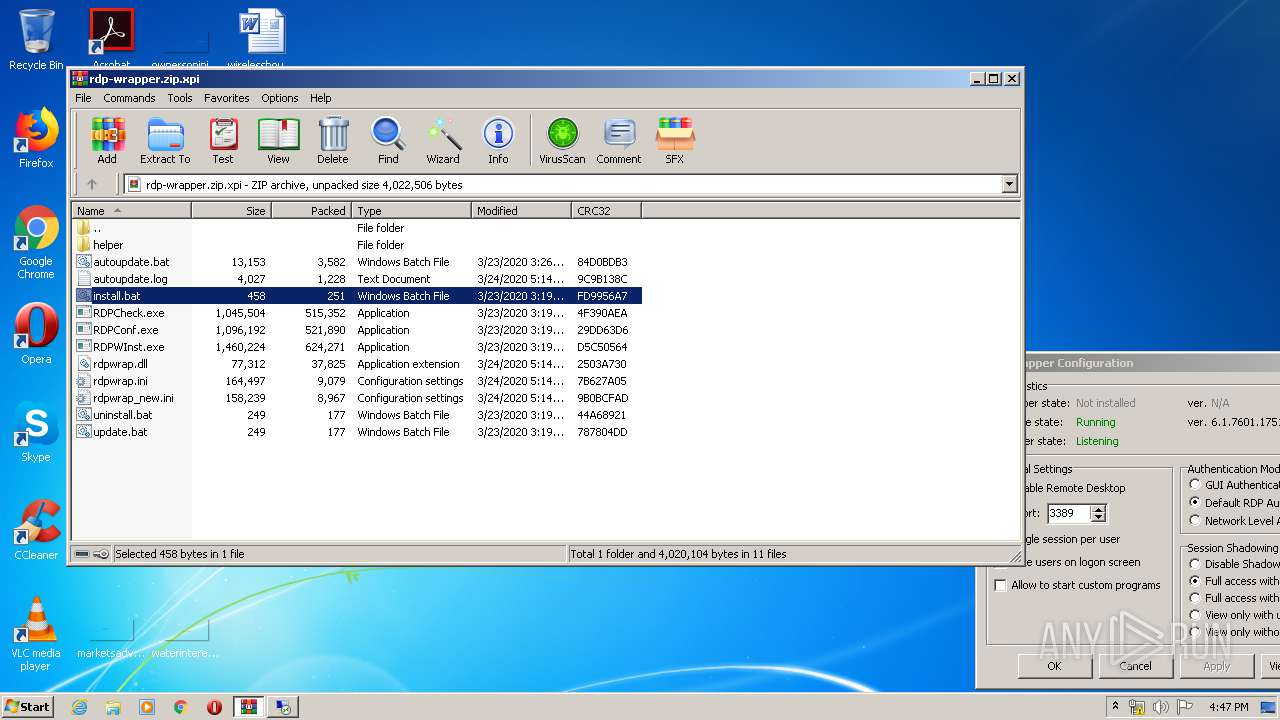
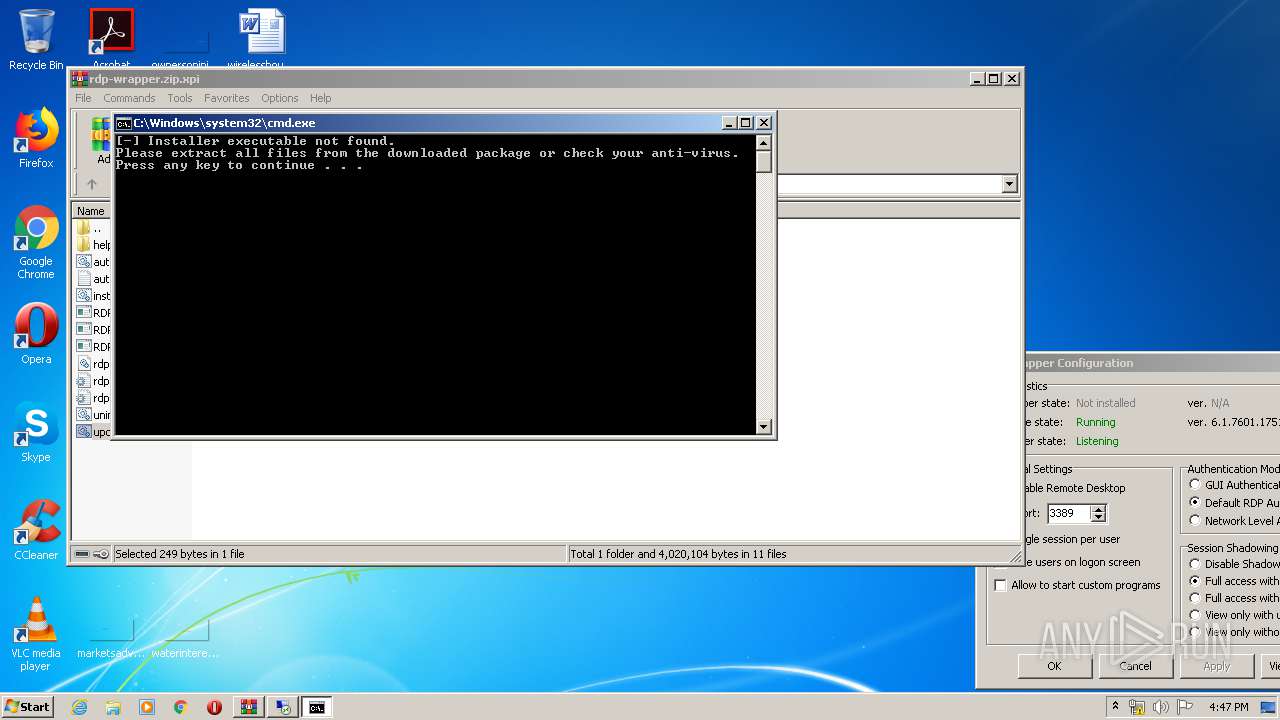
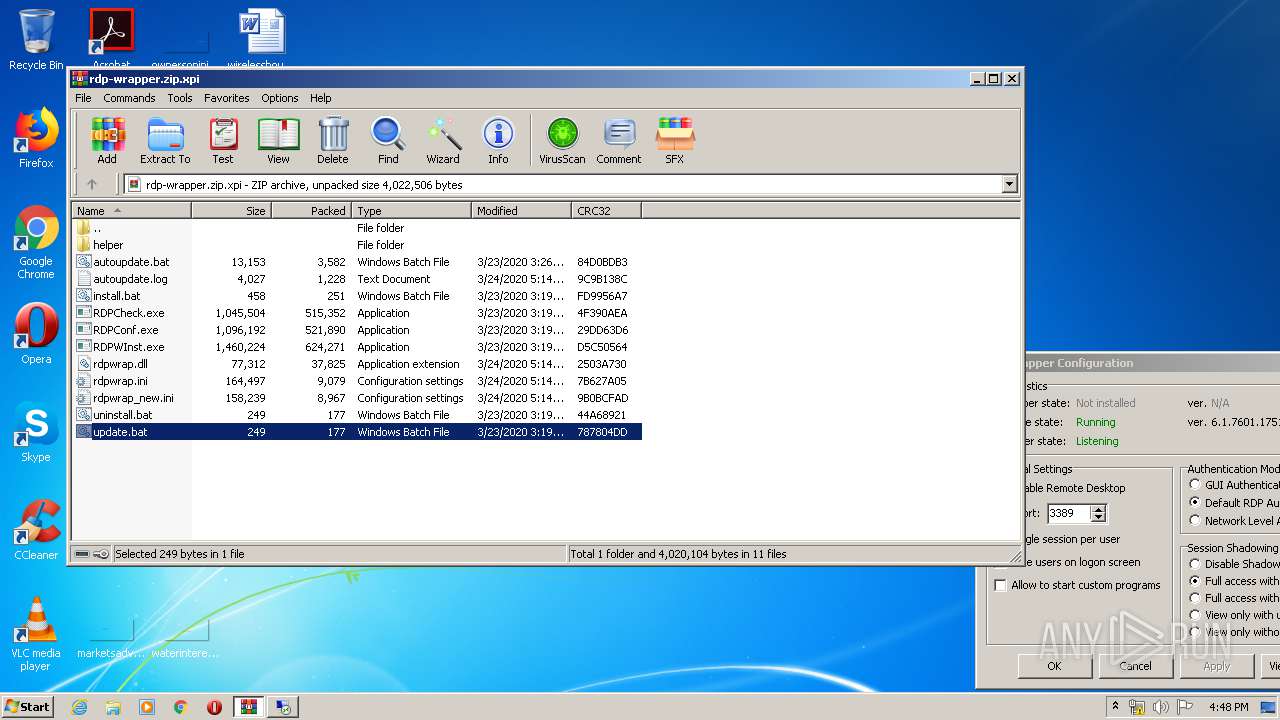
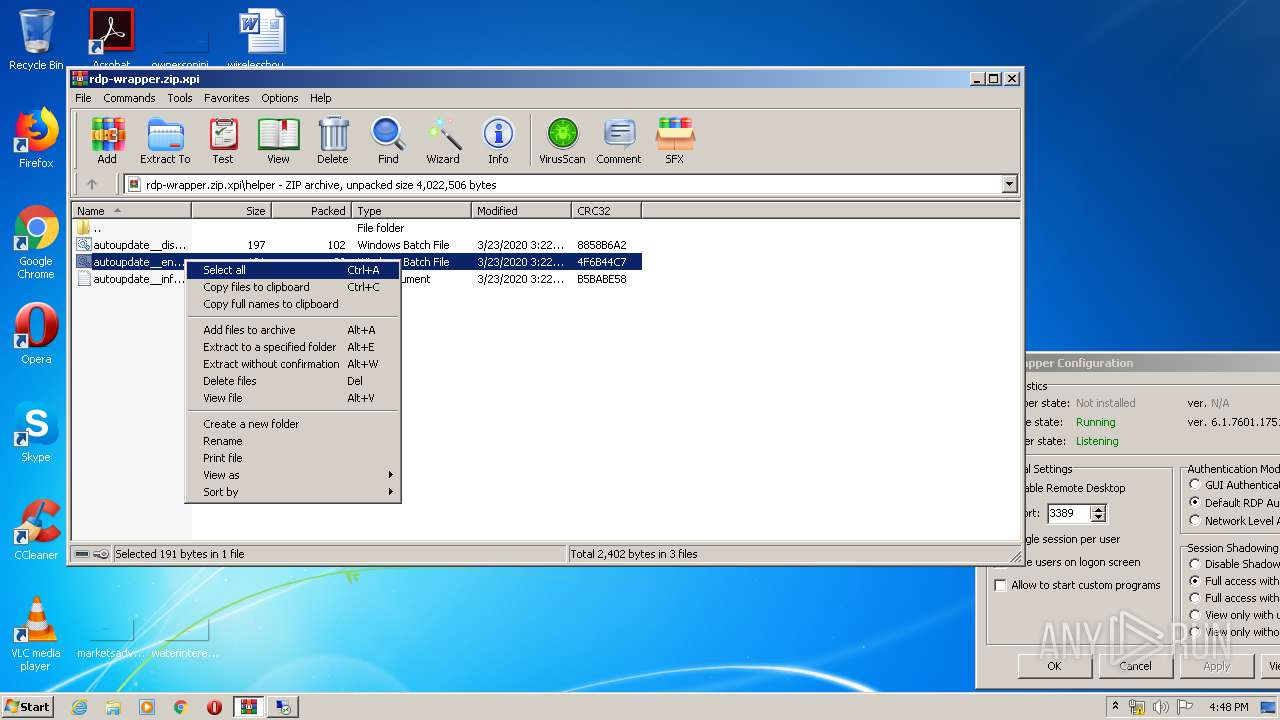
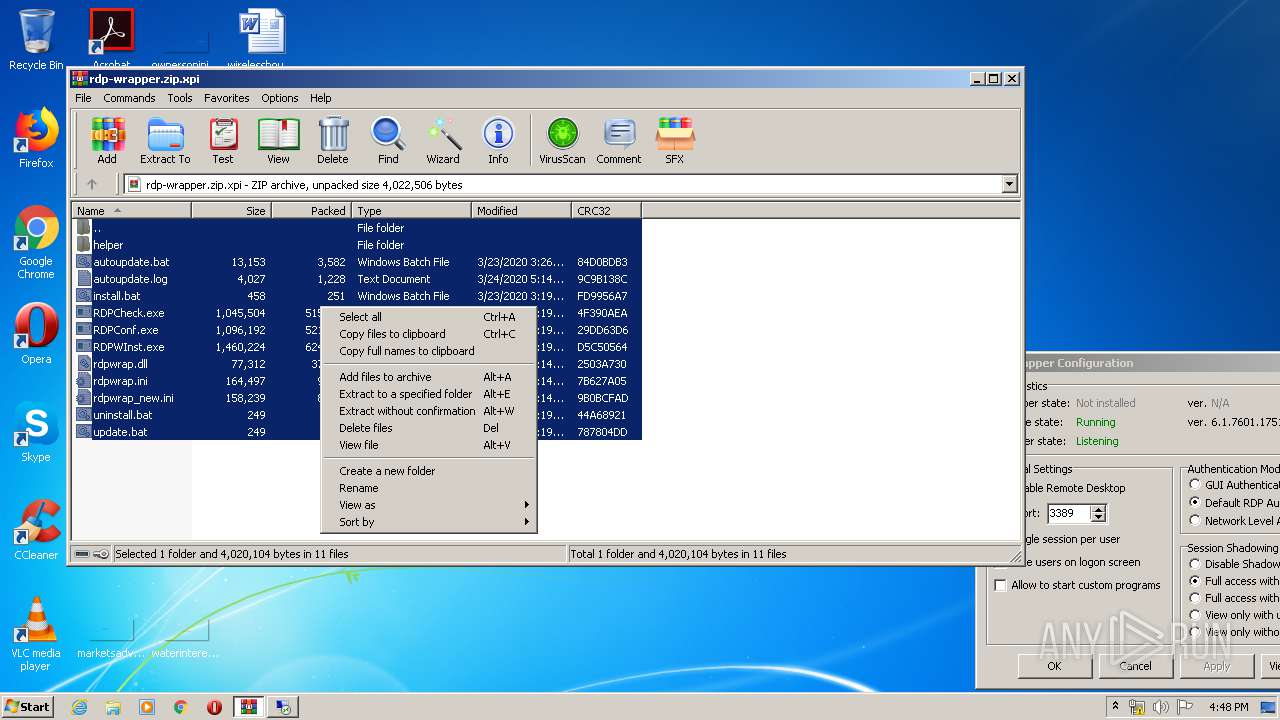
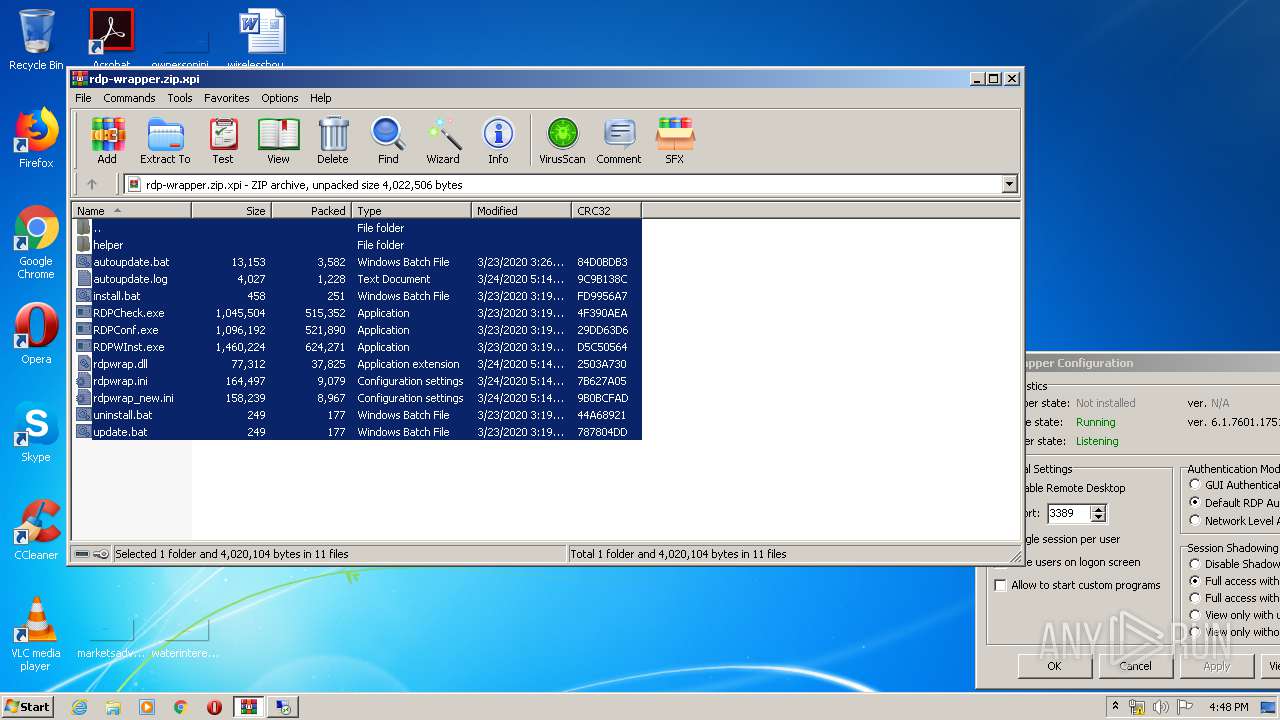
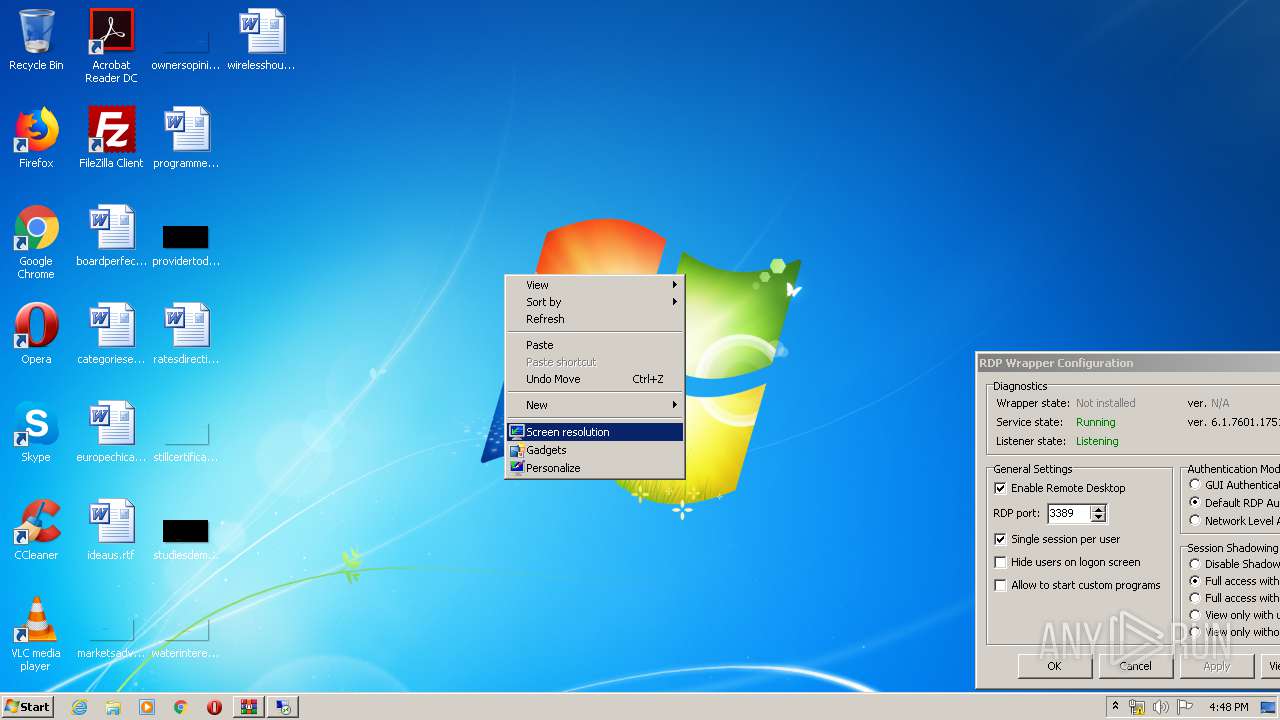
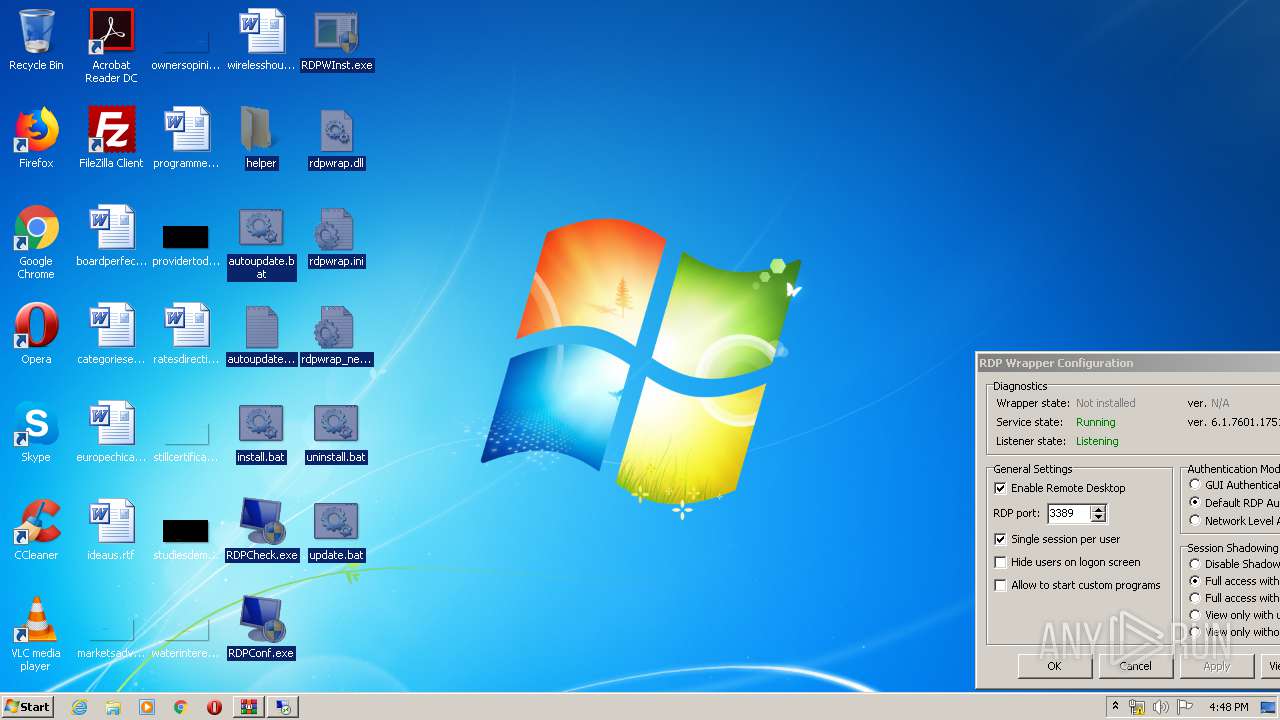
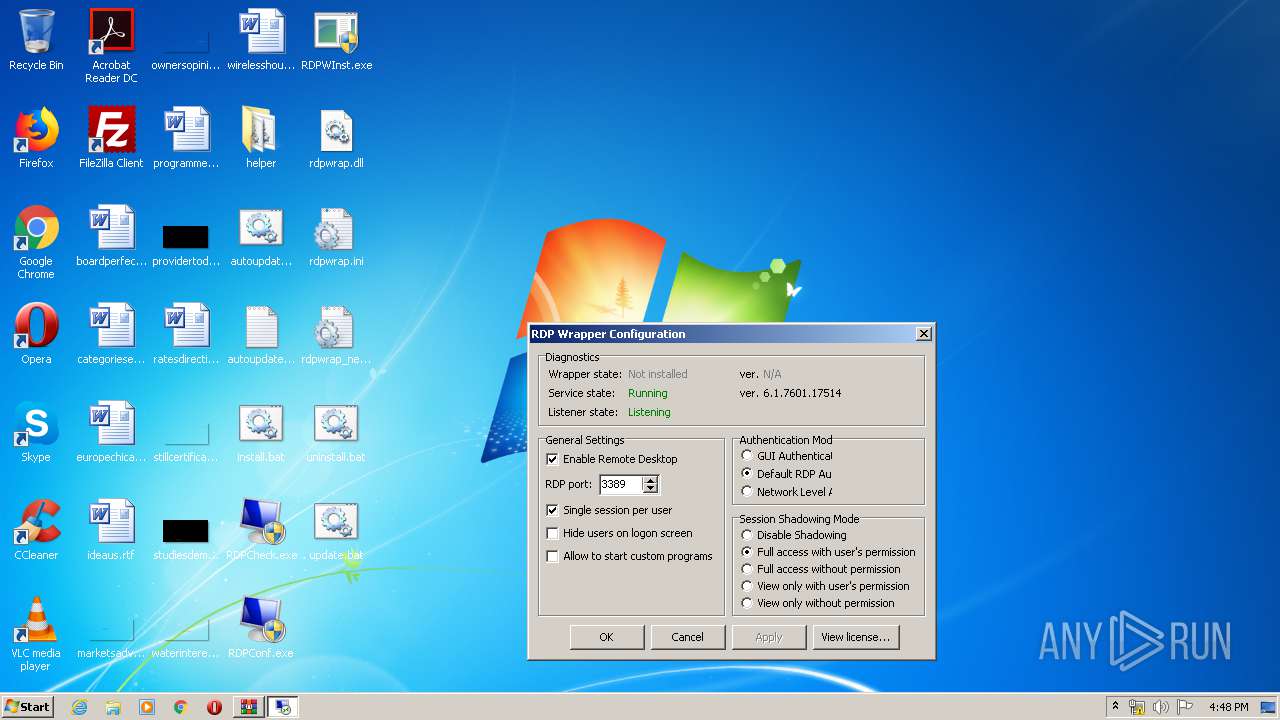
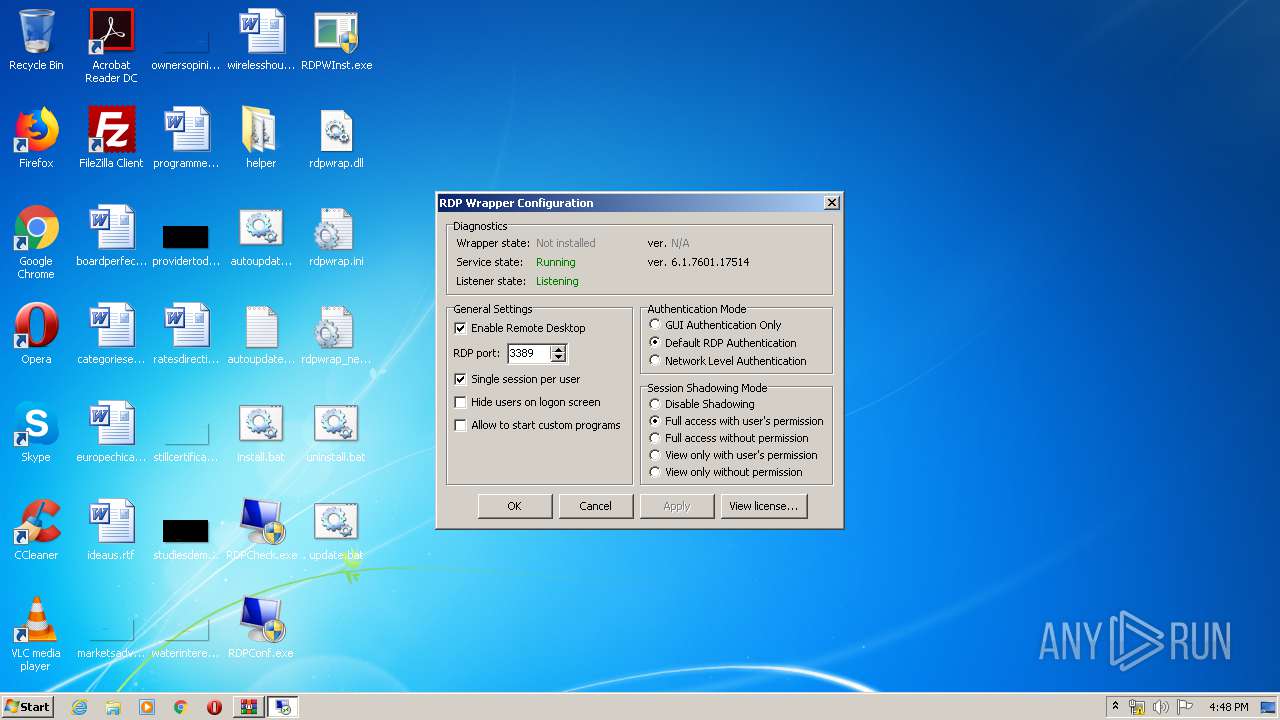
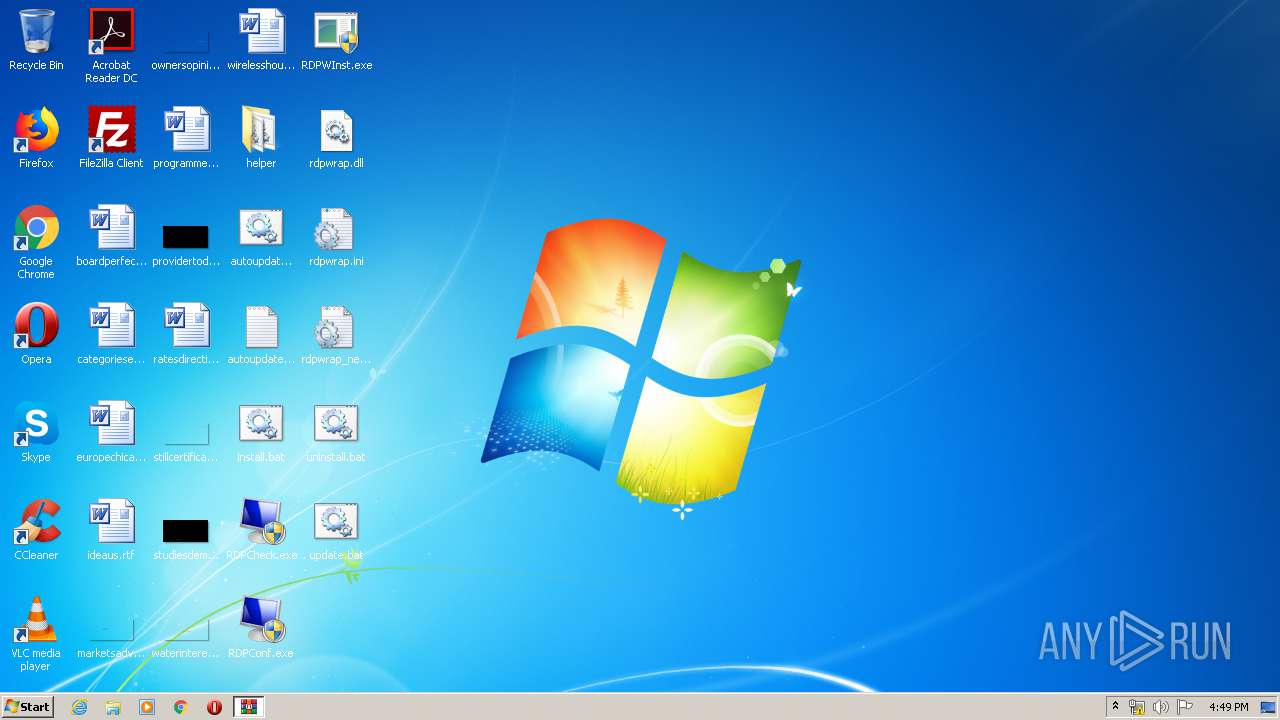
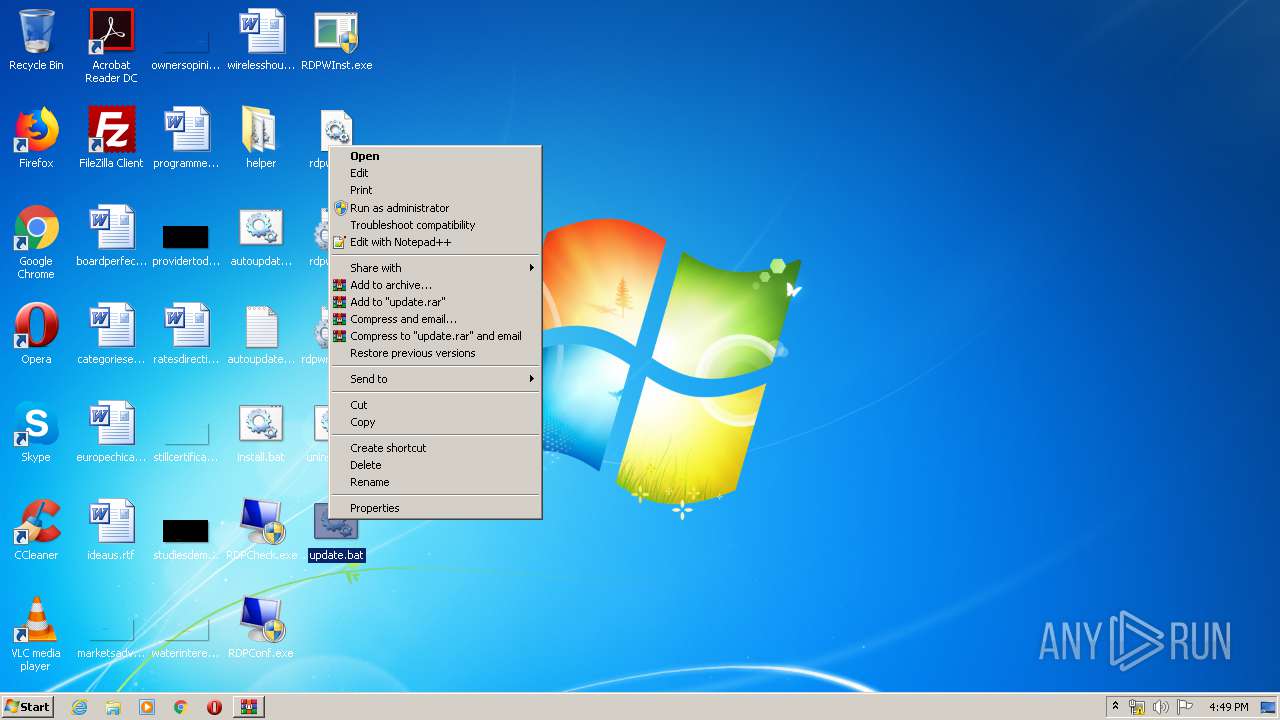
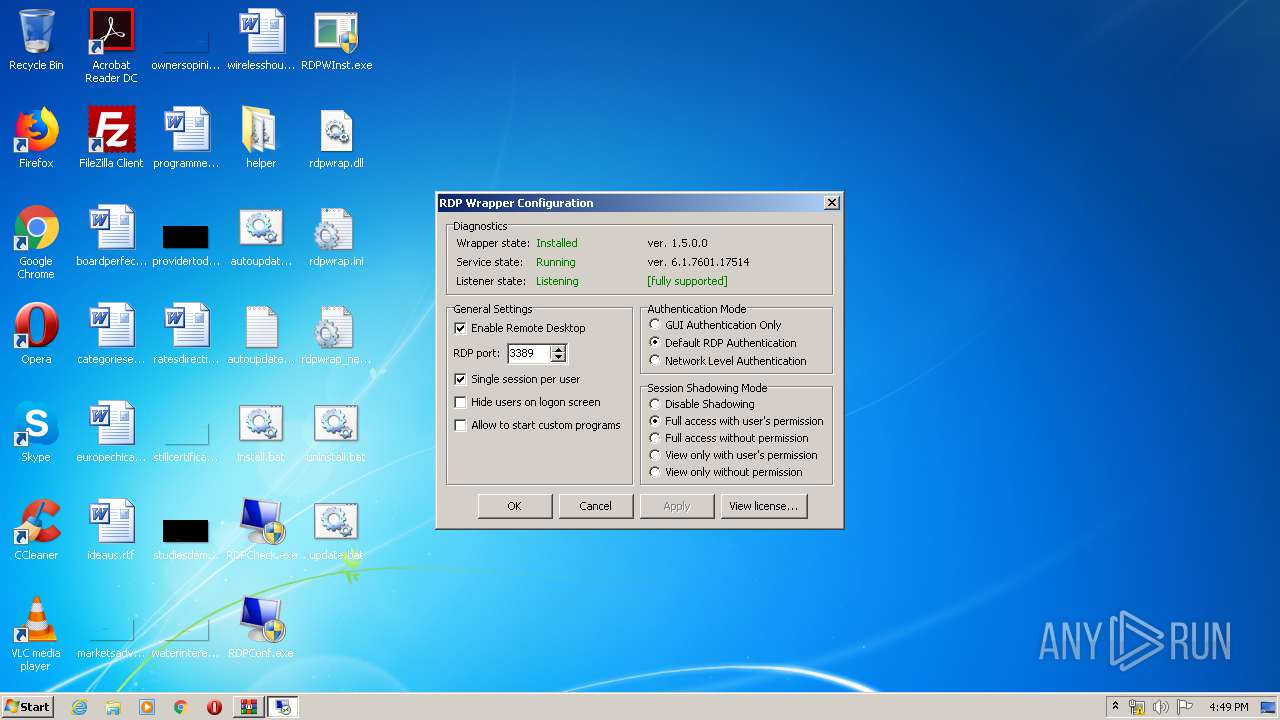
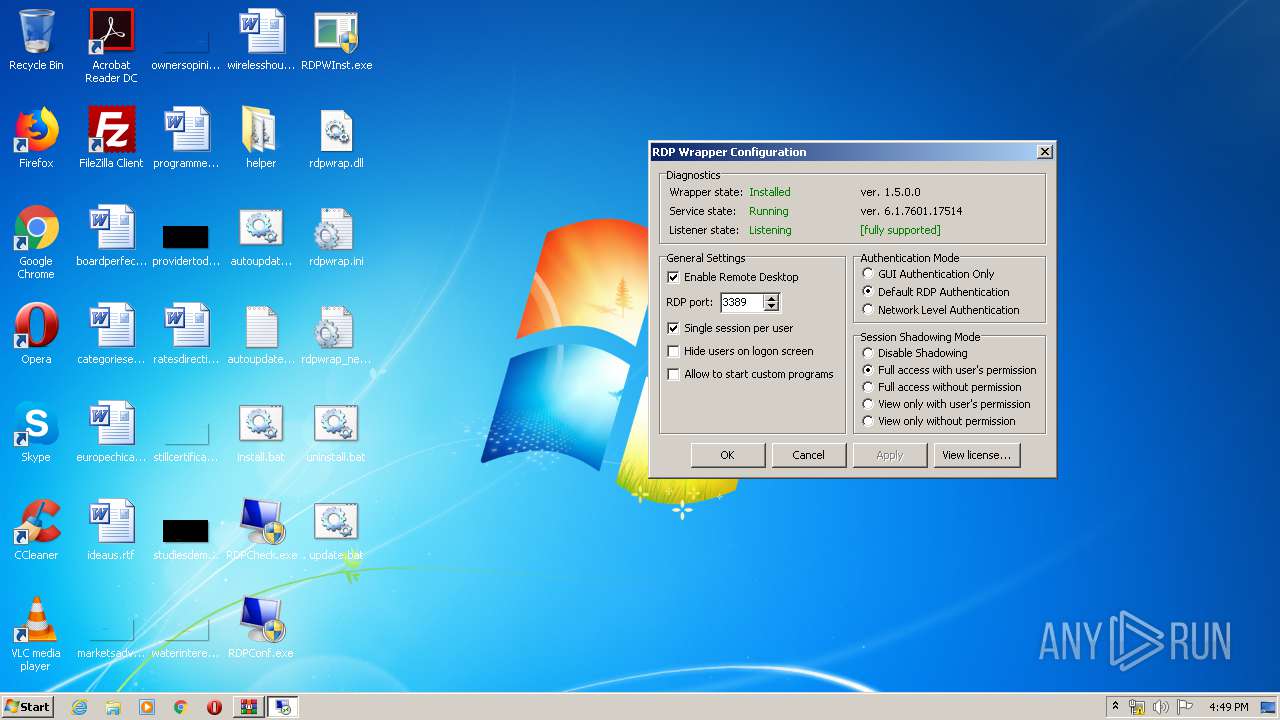
| File name: | rdp-wrapper.zip |
| Full analysis: | https://app.any.run/tasks/dad42661-4f82-4649-a00d-986a6af1f383 |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2020, 16:45:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 768308ED9BAC100CE3DE00E30E650668 |
| SHA1: | 34E37F73DE10FAE74CB10819FD2DE93C5DBCF68D |
| SHA256: | 6287E63F05854C31D166BBAC6555AC9796FA796E2F9E3E0D2503F24F6FECF847 |
| SSDEEP: | 49152:eg7VPEQlBGqb5rIlUdGSxjsmxoWZs0jHI8VbKJ:TVMaBtbmoTxjOWOMHRbM |
MALICIOUS
Application was dropped or rewritten from another process
- RDPWInst.exe (PID: 2820)
- RDPWInst.exe (PID: 3680)
- RDPConf.exe (PID: 3276)
- RDPConf.exe (PID: 540)
- RDPCheck.exe (PID: 1412)
- RDPCheck.exe (PID: 1860)
- RDPWInst.exe (PID: 1940)
- RDPWInst.exe (PID: 3732)
- RDPWInst.exe (PID: 1488)
- RDPWInst.exe (PID: 3380)
- RDPConf.exe (PID: 2408)
- RDPConf.exe (PID: 2300)
- RDPCheck.exe (PID: 1052)
- RDPCheck.exe (PID: 2252)
- RDPWInst.exe (PID: 3796)
- RDPConf.exe (PID: 2408)
- RDPConf.exe (PID: 3072)
- RDPConf.exe (PID: 2460)
- RDPWInst.exe (PID: 1564)
- RDPConf.exe (PID: 3376)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 2956)
- svchost.exe (PID: 1748)
Creates or modifies windows services
- RDPWInst.exe (PID: 3380)
Changes settings of System certificates
- RDPWInst.exe (PID: 3380)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 772)
- RDPWInst.exe (PID: 3380)
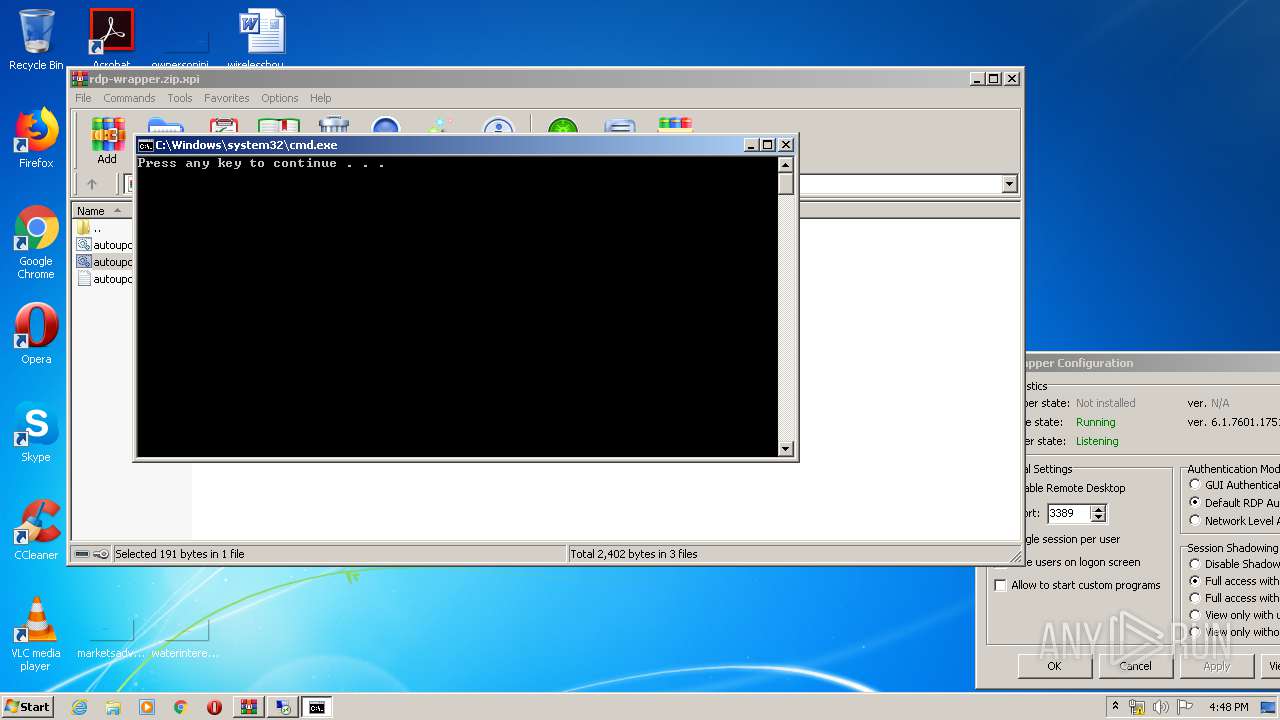
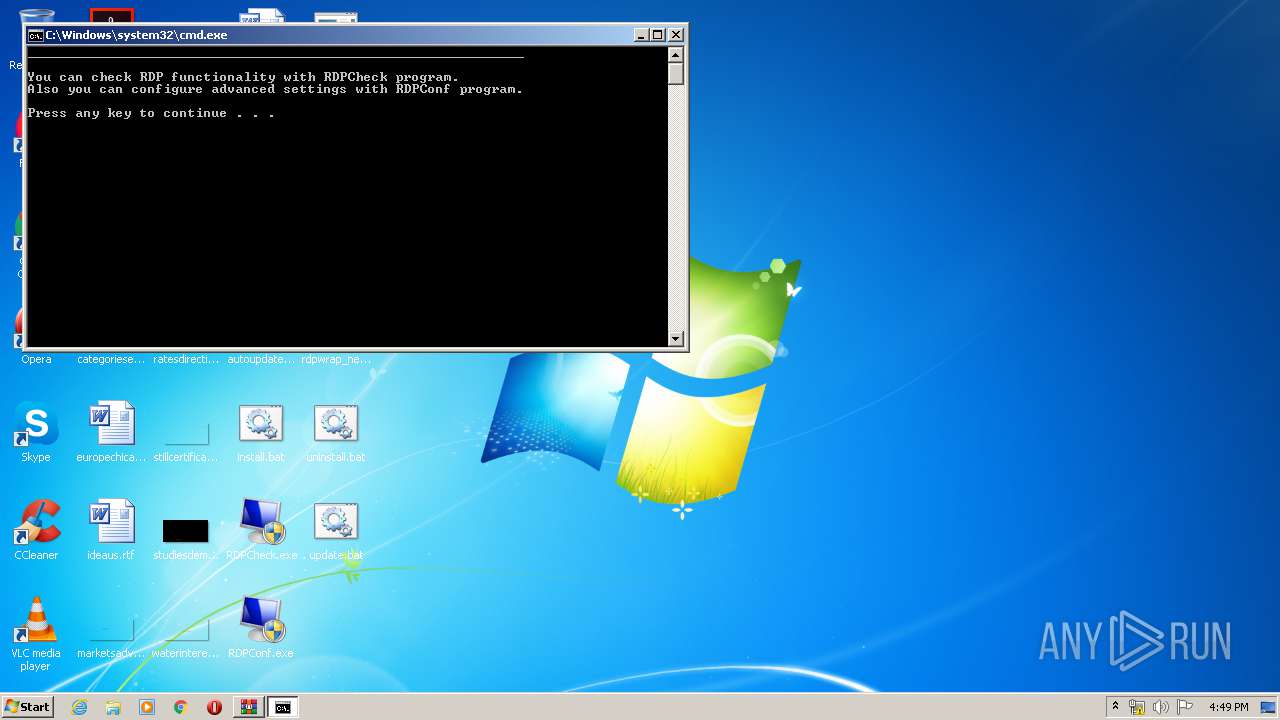
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 772)
Reads Internet Cache Settings
- RDPWInst.exe (PID: 3380)
Creates files in the program directory
- RDPWInst.exe (PID: 3380)
Uses NETSH.EXE for network configuration
- RDPWInst.exe (PID: 3380)
Adds / modifies Windows certificates
- RDPWInst.exe (PID: 3380)
INFO
Modifies the open verb of a shell class
- rundll32.exe (PID: 3292)
Manual execution by user
- cmd.exe (PID: 3604)
- RDPConf.exe (PID: 2460)
- RDPConf.exe (PID: 2408)
- RDPCheck.exe (PID: 1052)
- RDPConf.exe (PID: 2300)
- RDPCheck.exe (PID: 2252)
- cmd.exe (PID: 3240)
- RDPConf.exe (PID: 3072)
- RDPConf.exe (PID: 2408)
- RDPConf.exe (PID: 3376)
- RDPWInst.exe (PID: 1564)
- RDPWInst.exe (PID: 2820)
Reads settings of System Certificates
- RDPWInst.exe (PID: 3380)
Reads the hosts file
- svchost.exe (PID: 1748)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:03:23 15:26:17 |
| ZipCRC: | 0x84d0bdb3 |
| ZipCompressedSize: | 3582 |
| ZipUncompressedSize: | 13153 |
| ZipFileName: | autoupdate.bat |
Total processes
113
Monitored processes
30
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
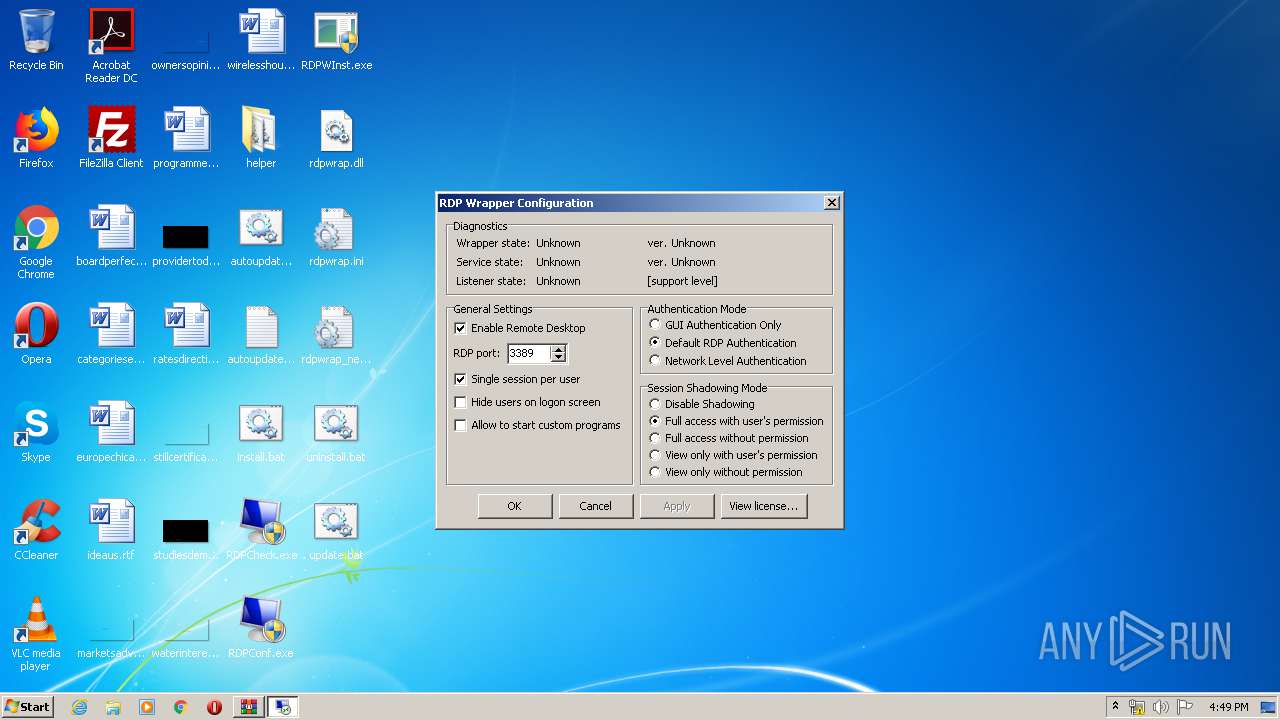
| 540 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa772.23827\RDPConf.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa772.23827\RDPConf.exe | WinRAR.exe | ||||||||||||
User: admin Company: Stas'M Corp. Integrity Level: HIGH Description: RDP Configuration Program Exit code: 0 Version: 1.4.0.0 Modules
| |||||||||||||||
| 772 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\rdp-wrapper.zip.xpi" | C:\Program Files\WinRAR\WinRAR.exe | rundll32.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
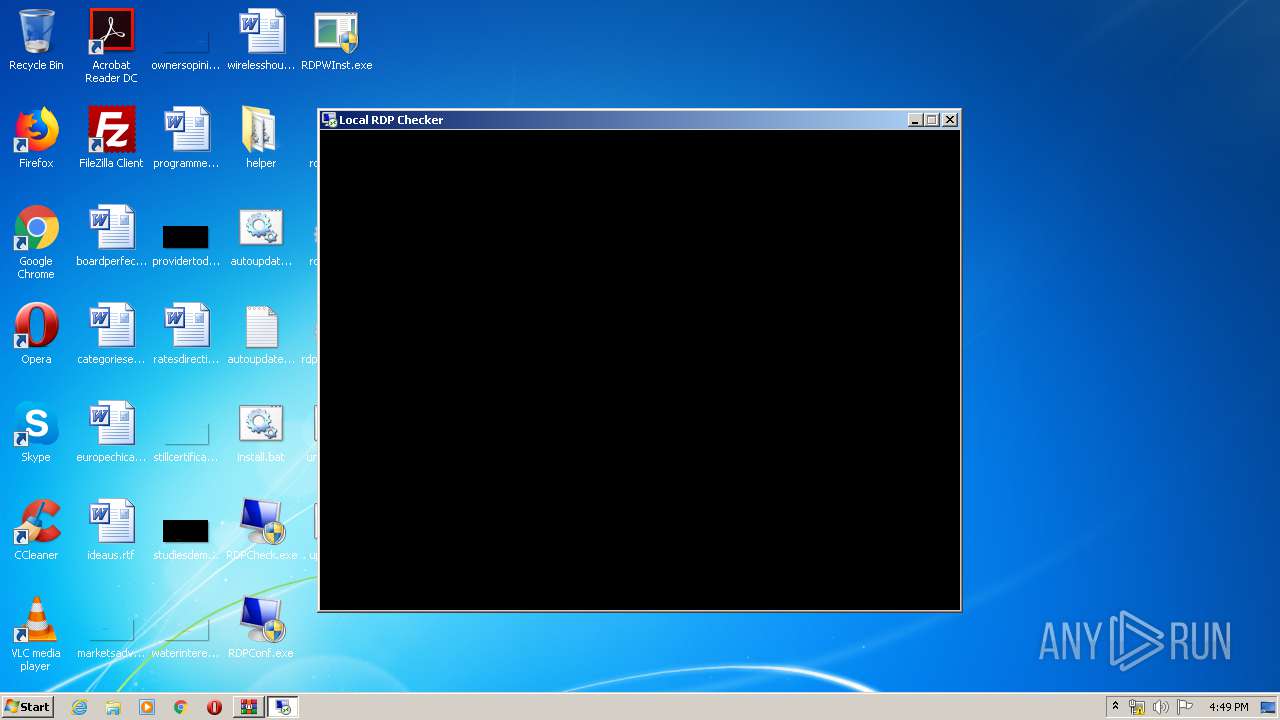
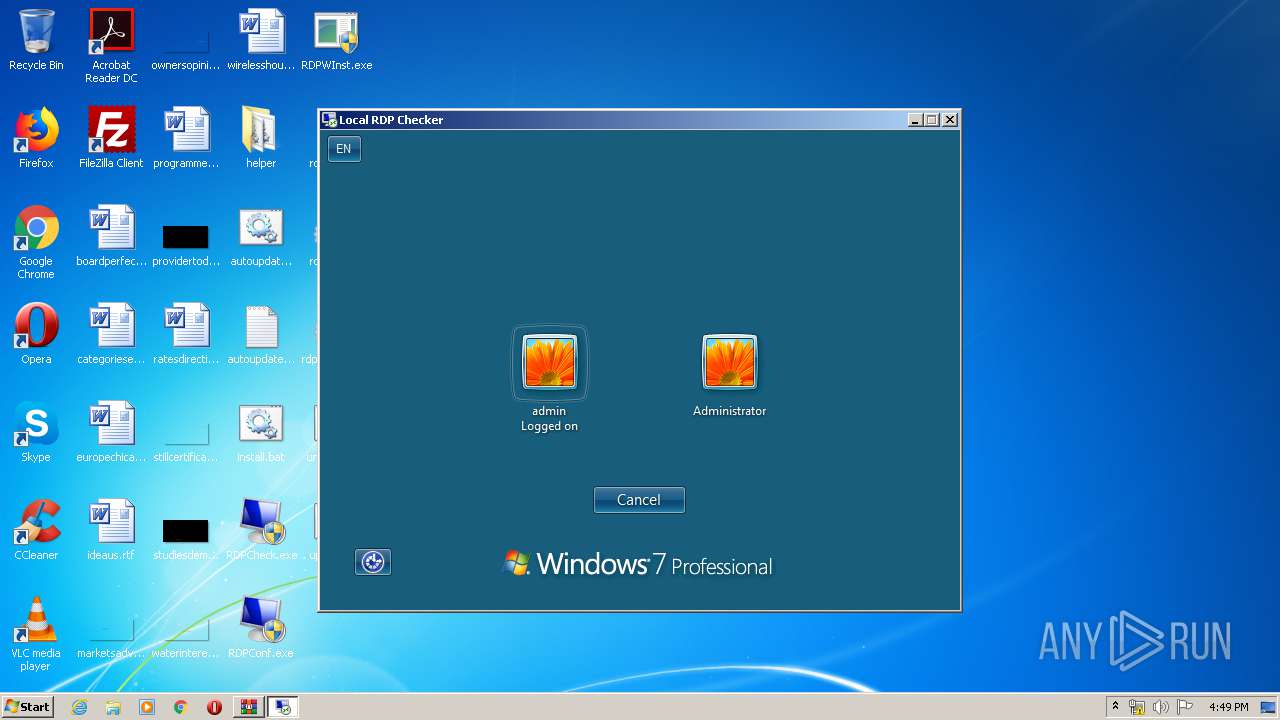
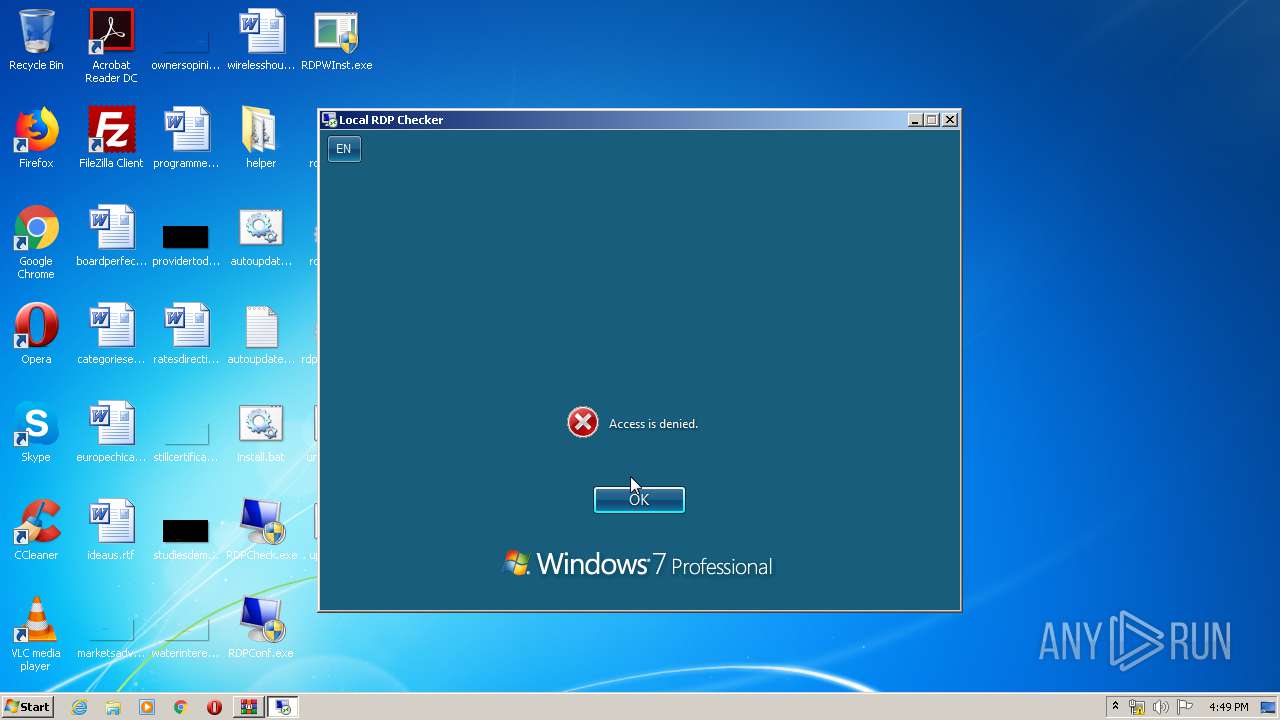
| 1052 | "C:\Users\admin\Desktop\RDPCheck.exe" | C:\Users\admin\Desktop\RDPCheck.exe | — | explorer.exe | |||||||||||
User: admin Company: Stas'M Corp. Integrity Level: MEDIUM Description: Local RDP Checker Exit code: 3221226540 Version: 2.2.0.0 Modules
| |||||||||||||||
| 1084 | cmd /c ""C:\Users\admin\AppData\Local\Temp\Rar$DIa772.30161\install.bat" " | C:\Windows\system32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1412 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa772.27369\RDPCheck.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa772.27369\RDPCheck.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Stas'M Corp. Integrity Level: MEDIUM Description: Local RDP Checker Exit code: 3221226540 Version: 2.2.0.0 Modules
| |||||||||||||||
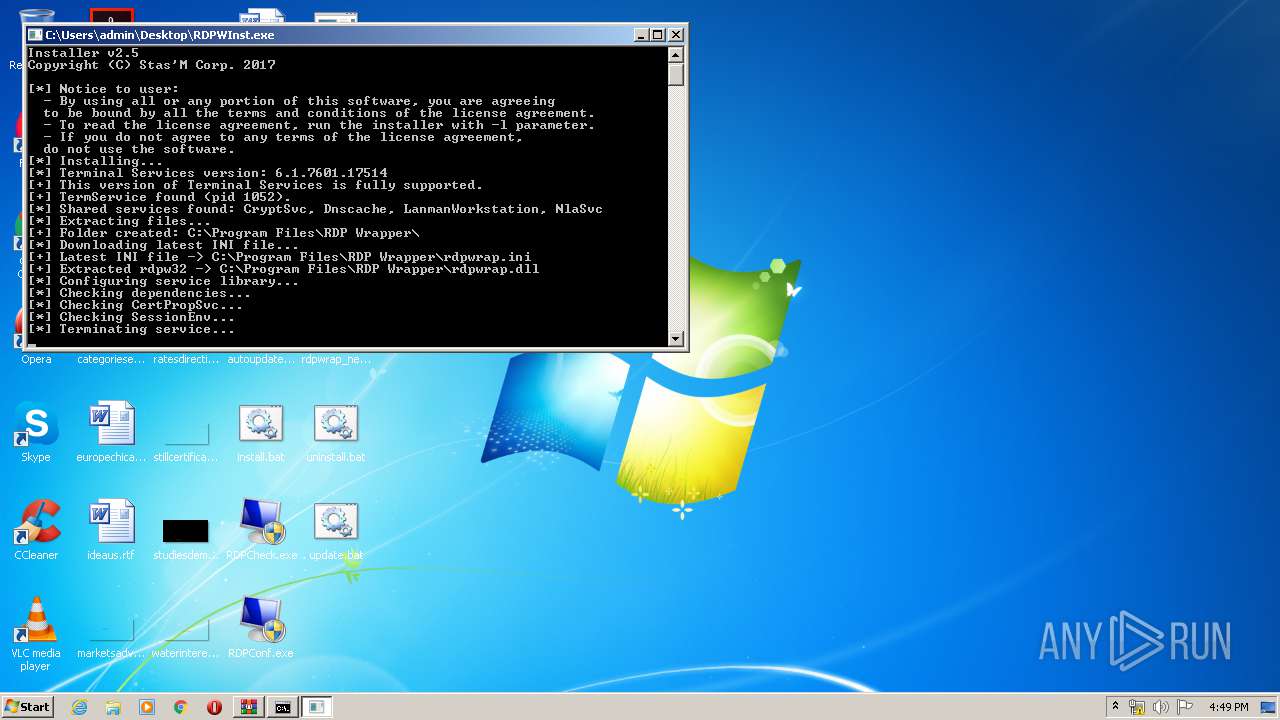
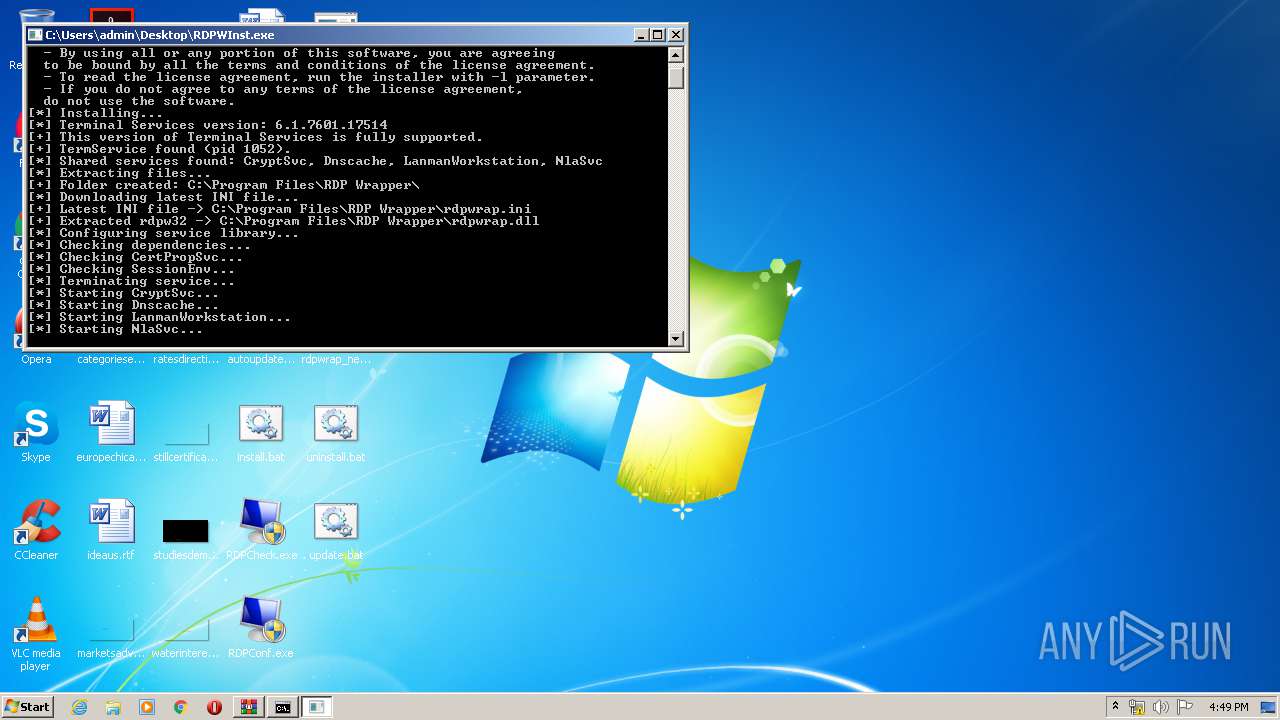
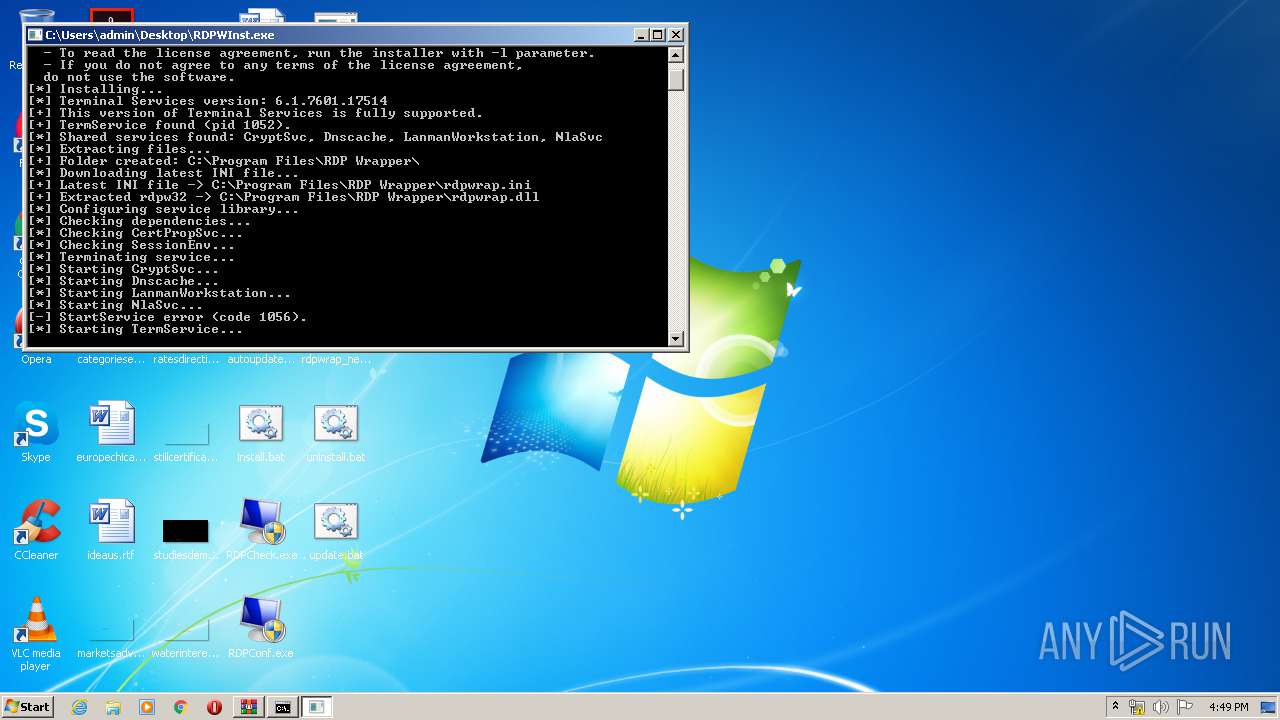
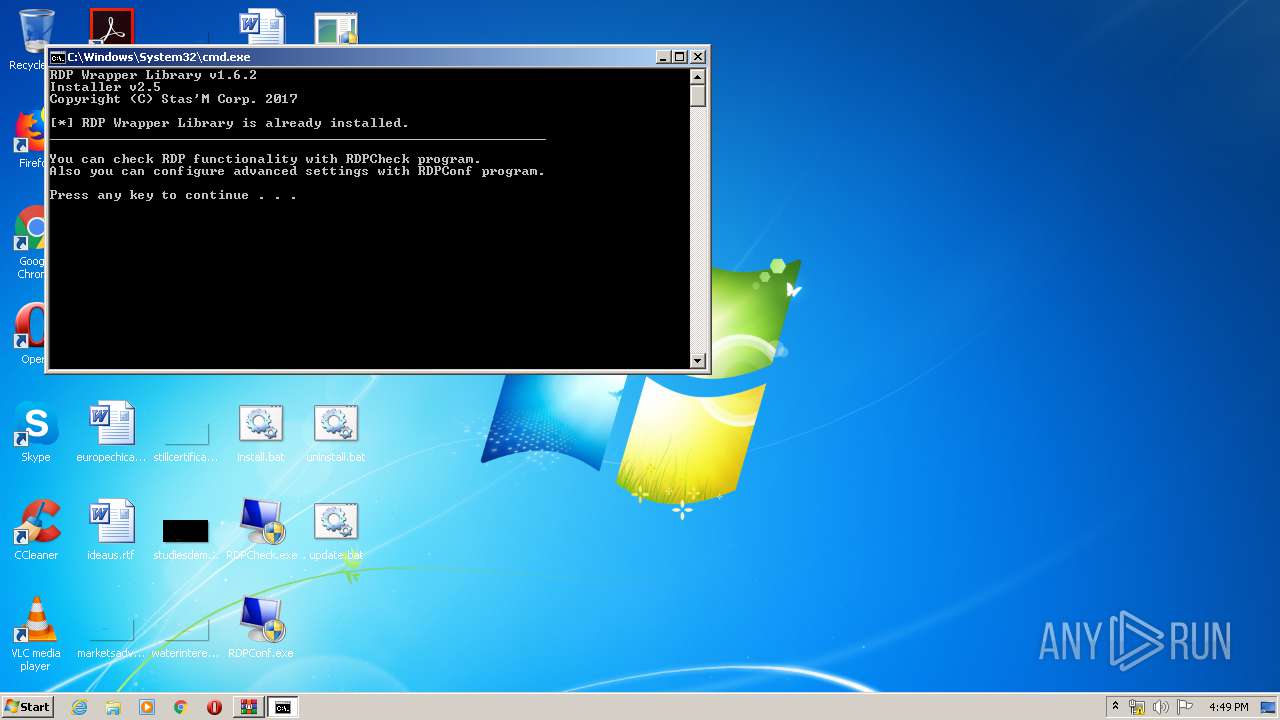
| 1488 | "C:\Users\admin\Desktop\RDPWInst.exe" -i -o | C:\Users\admin\Desktop\RDPWInst.exe | — | cmd.exe | |||||||||||
User: admin Company: Stas'M Corp. Integrity Level: MEDIUM Description: RDP Wrapper Library Installer Exit code: 3221226540 Version: 2.5.0.0 Modules
| |||||||||||||||
| 1564 | "C:\Users\admin\Desktop\RDPWInst.exe" | C:\Users\admin\Desktop\RDPWInst.exe | — | explorer.exe | |||||||||||
User: admin Company: Stas'M Corp. Integrity Level: MEDIUM Description: RDP Wrapper Library Installer Exit code: 3221226540 Version: 2.5.0.0 Modules
| |||||||||||||||
| 1748 | C:\Windows\System32\svchost.exe -k NetworkService | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1860 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa772.27369\RDPCheck.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa772.27369\RDPCheck.exe | WinRAR.exe | ||||||||||||
User: admin Company: Stas'M Corp. Integrity Level: HIGH Description: Local RDP Checker Exit code: 0 Version: 2.2.0.0 Modules
| |||||||||||||||
| 1940 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa772.29058\RDPWInst.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa772.29058\RDPWInst.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Stas'M Corp. Integrity Level: MEDIUM Description: RDP Wrapper Library Installer Exit code: 3221226540 Version: 2.5.0.0 Modules
| |||||||||||||||
Total events
4 929
Read events
3 417
Write events
1 510
Delete events
2
Modification events
| (PID) Process: | (3292) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe |
Value: Adobe Acrobat Reader DC | |||
| (PID) Process: | (3292) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\eHome\ehshell.exe |
Value: Windows Media Center | |||
| (PID) Process: | (3292) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\mspaint.exe |
Value: Paint | |||
| (PID) Process: | (3292) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\NOTEPAD.EXE |
Value: Notepad | |||
| (PID) Process: | (3292) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\PROGRA~1\MICROS~1\Office14\OIS.EXE |
Value: Microsoft Office 2010 | |||
| (PID) Process: | (3292) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Opera\Opera.exe |
Value: Opera Internet Browser | |||
| (PID) Process: | (3292) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Windows Photo Viewer\PhotoViewer.dll |
Value: Windows Photo Viewer | |||
| (PID) Process: | (3292) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\VideoLAN\VLC\vlc.exe |
Value: VLC media player | |||
| (PID) Process: | (3292) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE |
Value: Microsoft Word | |||
| (PID) Process: | (3292) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
17
Suspicious files
7
Text files
45
Unknown types
1
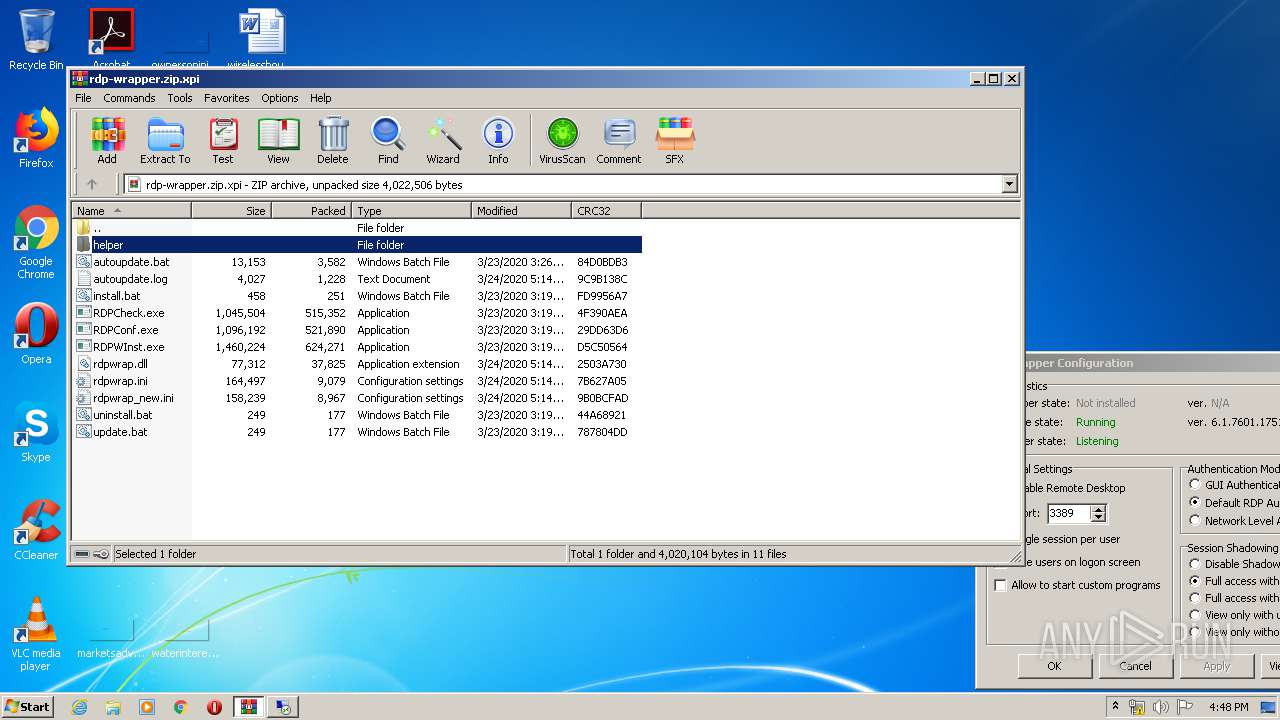
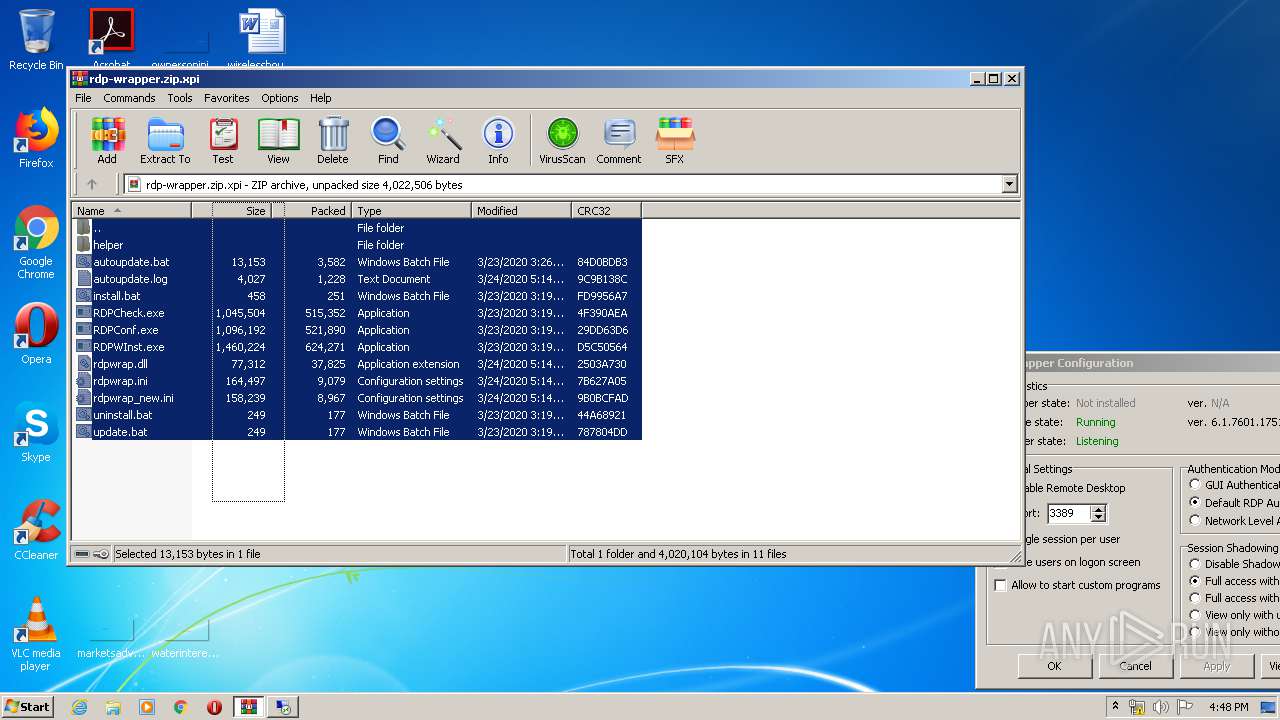
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 772 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa772.23827\autoupdate.bat | text | |
MD5:— | SHA256:— | |||
| 772 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa772.23827\helper\autoupdate__info.txt | text | |
MD5:— | SHA256:— | |||
| 772 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa772.23827\autoupdate.log | text | |
MD5:— | SHA256:— | |||
| 772 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa772.23827\RDPCheck.exe | executable | |
MD5:8F82226B2F24D470C02F6664F67F23F7 | SHA256:5603338A1F8DBB46EFB8E0869DB3491D5DB92F362711D6680F91ECC5D18BFADF | |||
| 772 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa772.23827\helper\autoupdate__enable_autorun_on_startup.bat | text | |
MD5:24D9715C7B22E358957D3D5A4A9D71A0 | SHA256:ED1634F0D2BC05BE4EAD480479938723C70A919125E3B80F9273C219BF246D32 | |||
| 772 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa772.23827\install.bat | text | |
MD5:CBAD5B2CA73917006791882274F769E8 | SHA256:022364EE1FCE61C8A867216C79F223BF47692CD648E3FD6B244FC615B86E4C58 | |||
| 772 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa772.27369\autoupdate.bat | text | |
MD5:— | SHA256:— | |||
| 772 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa772.23827\RDPWInst.exe | executable | |
MD5:3288C284561055044C489567FD630AC2 | SHA256:AC92D4C6397EB4451095949AC485EF4EC38501D7BB6F475419529AE67E297753 | |||
| 772 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa772.23827\RDPConf.exe | executable | |
MD5:03FB8E478F4BA100D37A136231FA2F78 | SHA256:3C0E5D6863B03283AFDA9BD188501757D47DC57FC4BBA2BDBB0D9BAA34487FE0 | |||
| 772 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa772.27369\autoupdate.log | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
2
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3380 | RDPWInst.exe | GET | 200 | 72.21.91.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEATh56TcXPLzbcArQrhdFZ8%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3380 | RDPWInst.exe | 151.101.0.133:443 | raw.githubusercontent.com | Fastly | US | malicious |
3380 | RDPWInst.exe | 72.21.91.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
raw.githubusercontent.com |
| shared |
ocsp.digicert.com |
| whitelisted |