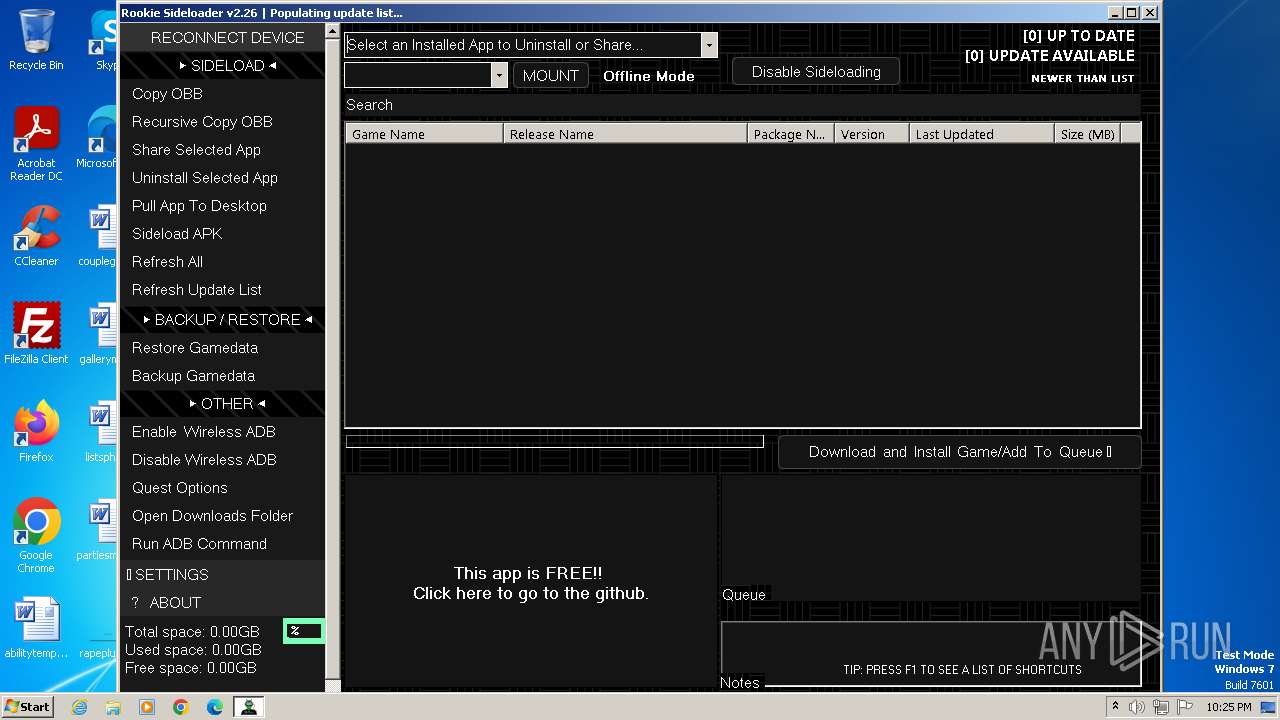
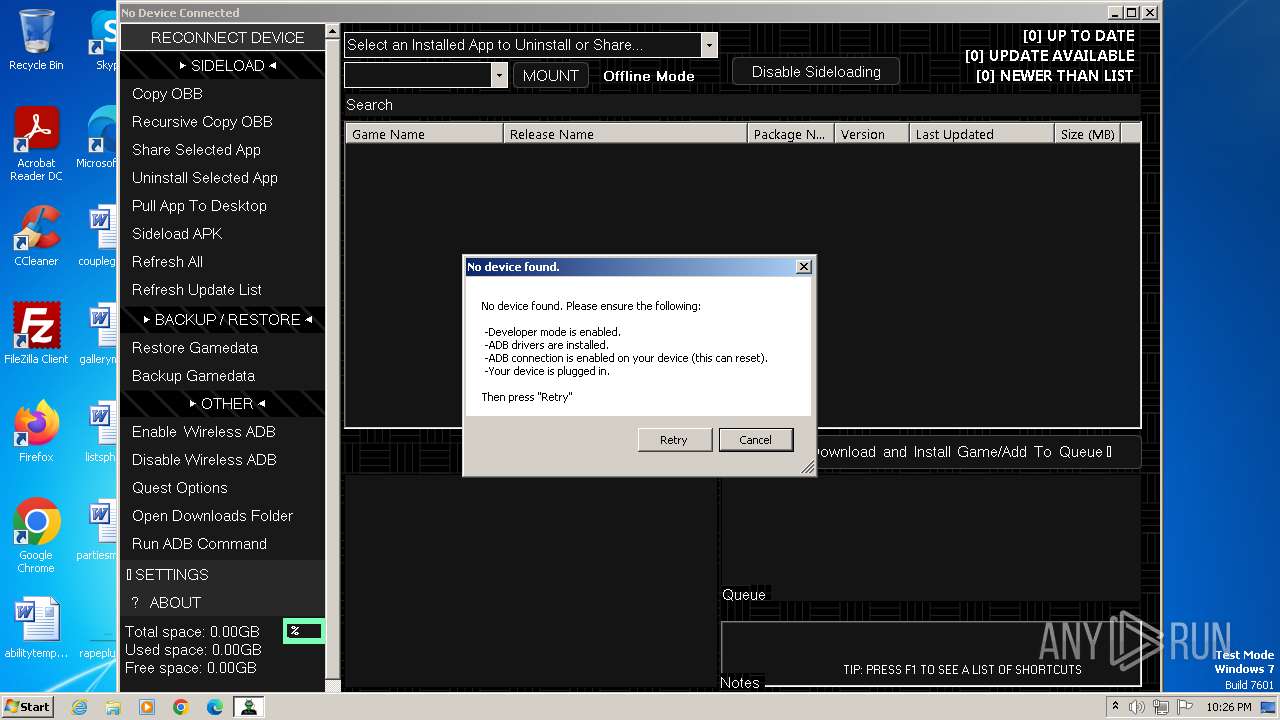
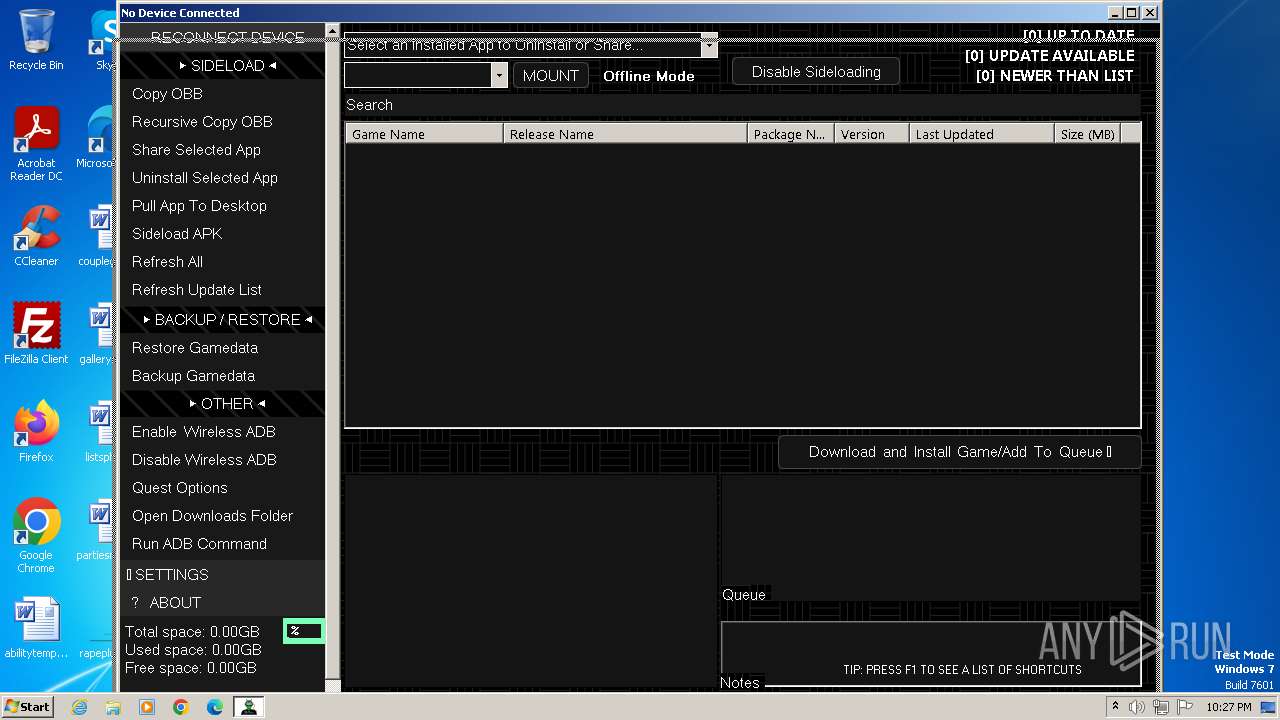
| File name: | AndroidSideloader v2.26.exe |
| Full analysis: | https://app.any.run/tasks/de9eb848-2913-4699-83fe-f9f2ecbc940c |
| Verdict: | Malicious activity |
| Analysis date: | December 10, 2023, 22:23:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 1158E107E5A5FB9BF3AE7BCC8276F429 |
| SHA1: | EA46F63D51C2C8FB641E9C23C5E206E9CA4FBA6D |
| SHA256: | 6278D167AC356CDAD30CD5A8EA37A7522F823515731AB64F4D1271BF38FB9497 |
| SSDEEP: | 98304:CcEQQMDXQmfYGBHkBPUHexnMO93WGY+PF:UY |
MALICIOUS
Drops the executable file immediately after the start
- AndroidSideloader v2.26.exe (PID: 280)
- 7z.exe (PID: 1152)
SUSPICIOUS
Reads settings of System Certificates
- AndroidSideloader v2.26.exe (PID: 280)
Reads the Internet Settings
- AndroidSideloader v2.26.exe (PID: 280)
- AndroidSideloader v2.26.exe (PID: 3944)
Drops 7-zip archiver for unpacking
- AndroidSideloader v2.26.exe (PID: 280)
Application launched itself
- adb.exe (PID: 4036)
- AndroidSideloader v2.26.exe (PID: 280)
- adb.exe (PID: 1872)
INFO
Reads Environment values
- AndroidSideloader v2.26.exe (PID: 280)
- AndroidSideloader v2.26.exe (PID: 3944)
Checks supported languages
- AndroidSideloader v2.26.exe (PID: 280)
- wmpnscfg.exe (PID: 2820)
- 7z.exe (PID: 1152)
- 7z.exe (PID: 3964)
- adb.exe (PID: 3080)
- adb.exe (PID: 1064)
- adb.exe (PID: 3388)
- rclone.exe (PID: 2608)
- rclone.exe (PID: 3204)
- AndroidSideloader v2.26.exe (PID: 3944)
- adb.exe (PID: 1872)
- adb.exe (PID: 4036)
- adb.exe (PID: 3408)
- adb.exe (PID: 2028)
- adb.exe (PID: 2584)
- adb.exe (PID: 2972)
- adb.exe (PID: 3724)
- adb.exe (PID: 3560)
- adb.exe (PID: 3400)
- adb.exe (PID: 1248)
- adb.exe (PID: 1604)
- adb.exe (PID: 3844)
- wmpnscfg.exe (PID: 2296)
- adb.exe (PID: 1612)
- adb.exe (PID: 1028)
- adb.exe (PID: 1452)
- adb.exe (PID: 2472)
- adb.exe (PID: 1160)
- adb.exe (PID: 2936)
- adb.exe (PID: 3824)
- adb.exe (PID: 3280)
- adb.exe (PID: 2648)
- adb.exe (PID: 1128)
- adb.exe (PID: 1760)
- adb.exe (PID: 2480)
- adb.exe (PID: 2672)
- adb.exe (PID: 3444)
- adb.exe (PID: 3628)
- adb.exe (PID: 680)
- adb.exe (PID: 3120)
- adb.exe (PID: 2884)
- adb.exe (PID: 2512)
- adb.exe (PID: 3476)
- adb.exe (PID: 3716)
Reads the computer name
- AndroidSideloader v2.26.exe (PID: 280)
- wmpnscfg.exe (PID: 2820)
- 7z.exe (PID: 1152)
- 7z.exe (PID: 3964)
- adb.exe (PID: 3388)
- rclone.exe (PID: 2608)
- rclone.exe (PID: 3204)
- AndroidSideloader v2.26.exe (PID: 3944)
- adb.exe (PID: 3408)
- wmpnscfg.exe (PID: 2296)
Reads the machine GUID from the registry
- AndroidSideloader v2.26.exe (PID: 280)
- AndroidSideloader v2.26.exe (PID: 3944)
Manual execution by a user
- wmpnscfg.exe (PID: 2820)
- wmpnscfg.exe (PID: 2296)
Create files in a temporary directory
- AndroidSideloader v2.26.exe (PID: 280)
- 7z.exe (PID: 3964)
- adb.exe (PID: 3388)
- AndroidSideloader v2.26.exe (PID: 3944)
Creates files or folders in the user directory
- AndroidSideloader v2.26.exe (PID: 280)
- AndroidSideloader v2.26.exe (PID: 3944)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (63.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (23.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
| .exe | | | Generic Win/DOS Executable (1.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2059:02:11 10:21:06+01:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 3800064 |
| InitializedDataSize: | 413184 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3a1ade |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.0.0.0 |
| ProductVersionNumber: | 2.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | Rookie Sideloader |
| CompanyName: | Rookie.WTF |
| FileDescription: | AndroidSideloader |
| FileVersion: | 2.0.0.0 |
| InternalName: | AndroidSideloader.exe |
| LegalCopyright: | Copyright © 2020 |
| LegalTrademarks: | - |
| OriginalFileName: | AndroidSideloader.exe |
| ProductName: | AndroidSideloader |
| ProductVersion: | 2.0.0.0 |
| AssemblyVersion: | 2.0.0.0 |
Total processes
119
Monitored processes
44
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 280 | "C:\Users\admin\AppData\Local\Temp\AndroidSideloader v2.26.exe" | C:\Users\admin\AppData\Local\Temp\AndroidSideloader v2.26.exe | explorer.exe | ||||||||||||
User: admin Company: Rookie.WTF Integrity Level: MEDIUM Description: AndroidSideloader Exit code: 4294967295 Version: 2.0.0.0 Modules
| |||||||||||||||
| 680 | "C:\RSL\platform-tools\adb.exe" shell df | C:\RSL\platform-tools\adb.exe | — | AndroidSideloader v2.26.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 1028 | "C:\RSL\platform-tools\adb.exe" shell df | C:\RSL\platform-tools\adb.exe | — | AndroidSideloader v2.26.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 1064 | "C:\RSL\platform-tools\adb.exe" kill-server | C:\RSL\platform-tools\adb.exe | — | AndroidSideloader v2.26.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1128 | "C:\RSL\platform-tools\adb.exe" devices | C:\RSL\platform-tools\adb.exe | — | AndroidSideloader v2.26.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1152 | "7z.exe" x "C:\Users\admin\AppData\Local\Temp\_adb.7z" -y -o"C:\RSL\platform-tools" -bsp1 | C:\Users\admin\AppData\Local\Temp\7z.exe | — | AndroidSideloader v2.26.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip Standalone Console Exit code: 0 Version: 23.01 Modules
| |||||||||||||||
| 1160 | "C:\RSL\platform-tools\adb.exe" shell df | C:\RSL\platform-tools\adb.exe | — | AndroidSideloader v2.26.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 1248 | "C:\RSL\platform-tools\adb.exe" shell df | C:\RSL\platform-tools\adb.exe | — | AndroidSideloader v2.26.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 1452 | "C:\RSL\platform-tools\adb.exe" devices | C:\RSL\platform-tools\adb.exe | — | AndroidSideloader v2.26.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1604 | "C:\RSL\platform-tools\adb.exe" shell dumpsys battery | C:\RSL\platform-tools\adb.exe | — | AndroidSideloader v2.26.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
Total events
10 998
Read events
10 970
Write events
28
Delete events
0
Modification events
| (PID) Process: | (280) AndroidSideloader v2.26.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (280) AndroidSideloader v2.26.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (280) AndroidSideloader v2.26.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (280) AndroidSideloader v2.26.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (280) AndroidSideloader v2.26.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3944) AndroidSideloader v2.26.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3944) AndroidSideloader v2.26.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3944) AndroidSideloader v2.26.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3944) AndroidSideloader v2.26.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
16
Suspicious files
93
Text files
1 671
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 280 | AndroidSideloader v2.26.exe | C:\Users\admin\AppData\Local\Temp\_adb.7z | compressed | |
MD5:27AE76B35B749CD5403AD0D3C0D88C81 | SHA256:ED7B071824883FC679DEA0BF8CC9E858904E227645F5779FD44289214B12E621 | |||
| 280 | AndroidSideloader v2.26.exe | C:\Users\admin\AppData\Local\Temp\Rookie Offline.cmd | text | |
MD5:513248E44025E42FD2B8F9280501A8BB | SHA256:7DD245A6267A6D9500EE6B13A29FBDD80CEF9A020162C0E24A228558C58FA092 | |||
| 280 | AndroidSideloader v2.26.exe | C:\Users\admin\AppData\Local\Temp\Sideloader Launcher.exe | executable | |
MD5:A53A5E70248EB3DA58DEFA74B0554704 | SHA256:98BC8CF1C6A59EF70D6431E1E92887984E5B21C8FBC85B4AD23CCC70589C4B1F | |||
| 280 | AndroidSideloader v2.26.exe | C:\Users\admin\AppData\Local\Rookie.WTF\AndroidSideloader_v2.26.e_Url_fdmnrxjtcnt05z3kbaycbgbpyzyqwjep\2.0.0.0\ex2p0jgl.newcfg | xml | |
MD5:ADACA2EE75FABFDF08D8C2B21AACDCA7 | SHA256:5C0062156176D0DABC42CE0E3C39396A7231EFB0B434DD8EB4527AA509DD32E3 | |||
| 1152 | 7z.exe | C:\RSL\platform-tools\dmtracedump.exe | executable | |
MD5:2CBAAAC5DD49A6C8F57318A04B3FD1DB | SHA256:E57495D334295F42230EADB50E80D8D278FD822554063892001BC78BE829AC93 | |||
| 280 | AndroidSideloader v2.26.exe | C:\Users\admin\AppData\Local\Temp\7z.exe | executable | |
MD5:8F57948E69C82BF98704F129C5460576 | SHA256:F00836A63BE7EBF14E1B8C40100C59777FE3432506B330927EA1F1B7FD47EE44 | |||
| 280 | AndroidSideloader v2.26.exe | C:\Users\admin\AppData\Local\Rookie.WTF\AndroidSideloader_v2.26.e_Url_fdmnrxjtcnt05z3kbaycbgbpyzyqwjep\2.0.0.0\user.config | xml | |
MD5:3B74CDD40B65BCC98CE28EFF79405E3F | SHA256:7B2C167CE495D91D5E36807FC09201B47316AA89F64960199F42922A06EBDF8F | |||
| 1152 | 7z.exe | C:\RSL\platform-tools\adb.exe | executable | |
MD5:F6E68C4CC8CC3288FD5A411F54D8CAE2 | SHA256:FD488A4E13D4C71ACCE69E209164398A056FBA5A559B7F00C1351390604E5B98 | |||
| 1152 | 7z.exe | C:\RSL\platform-tools\aapt.exe | executable | |
MD5:8CB1DAFAD773D619618EE7F7D88CC68C | SHA256:1C1D856F8D8C63C0E72ED71DFBA334905F5495DC6F111F48612BE6F6FFC87A00 | |||
| 1152 | 7z.exe | C:\RSL\platform-tools\AdbWinUsbApi.dll | executable | |
MD5:0E24119DAF1909E398FA1850B6112077 | SHA256:25207C506D29C4E8DCEB61B4BD50E8669BA26012988A43FBF26A890B1E60FC97 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
11
DNS requests
6
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
280 | AndroidSideloader v2.26.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?0cc59c33b578ce14 | unknown | compressed | 65.2 Kb | unknown |
280 | AndroidSideloader v2.26.exe | GET | 200 | 172.64.149.23:80 | http://zerossl.crt.sectigo.com/ZeroSSLECCDomainSecureSiteCA.crt | unknown | binary | 905 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
280 | AndroidSideloader v2.26.exe | 140.82.121.4:443 | github.com | GITHUB | US | unknown |
280 | AndroidSideloader v2.26.exe | 185.199.109.133:443 | raw.githubusercontent.com | FASTLY | US | unknown |
280 | AndroidSideloader v2.26.exe | 95.217.6.16:443 | downloads.rclone.org | Hetzner Online GmbH | FI | unknown |
280 | AndroidSideloader v2.26.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
280 | AndroidSideloader v2.26.exe | 185.247.224.87:443 | vrpirates.wiki | Flokinet Ltd | SC | unknown |
280 | AndroidSideloader v2.26.exe | 172.64.149.23:80 | zerossl.crt.sectigo.com | CLOUDFLARENET | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
github.com |
| shared |
raw.githubusercontent.com |
| shared |
downloads.rclone.org |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
vrpirates.wiki |
| unknown |
zerossl.crt.sectigo.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
280 | AndroidSideloader v2.26.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |