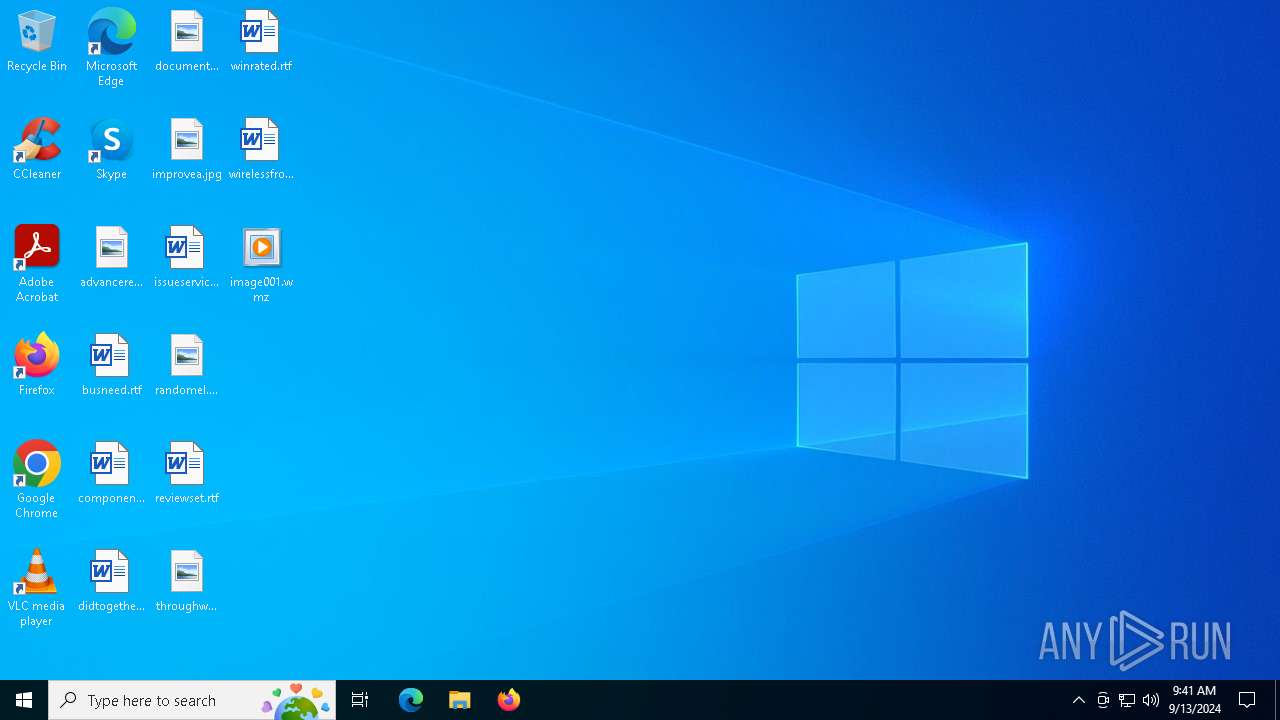
| File name: | image001.wmz |
| Full analysis: | https://app.any.run/tasks/5bfde8c7-7d40-4869-8c16-58185b5ce14d |
| Verdict: | Malicious activity |
| Analysis date: | September 13, 2024, 09:40:18 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
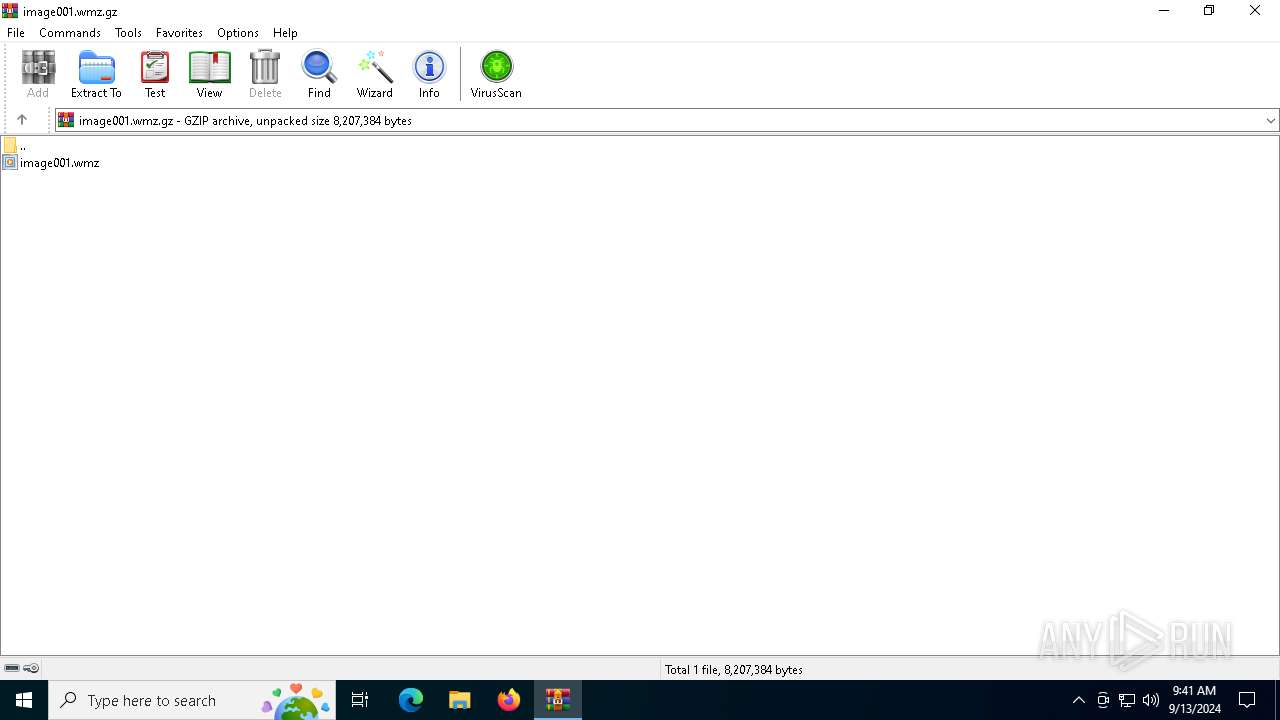
| MIME: | application/gzip |
| File info: | gzip compressed data, max speed, from NTFS filesystem (NT), original size modulo 2^32 8207384 |
| MD5: | D727AC19A2F38E5188AAC62BEEB79F7F |
| SHA1: | 4EEF07BF8428E7A69FF730EEE463343150CC61CA |
| SHA256: | 626E43D94BBFE1F454680148F7D92EE003DA2832C33A03798EAEF0E5B6275F67 |
| SSDEEP: | 24576:K/0ipqDpdwG58mK7mAKBH+qkPdOmVfNPVMS9zV9:K/0ipqDpdwG58T7mAKBH+LPdOmVfNP2C |
MALICIOUS
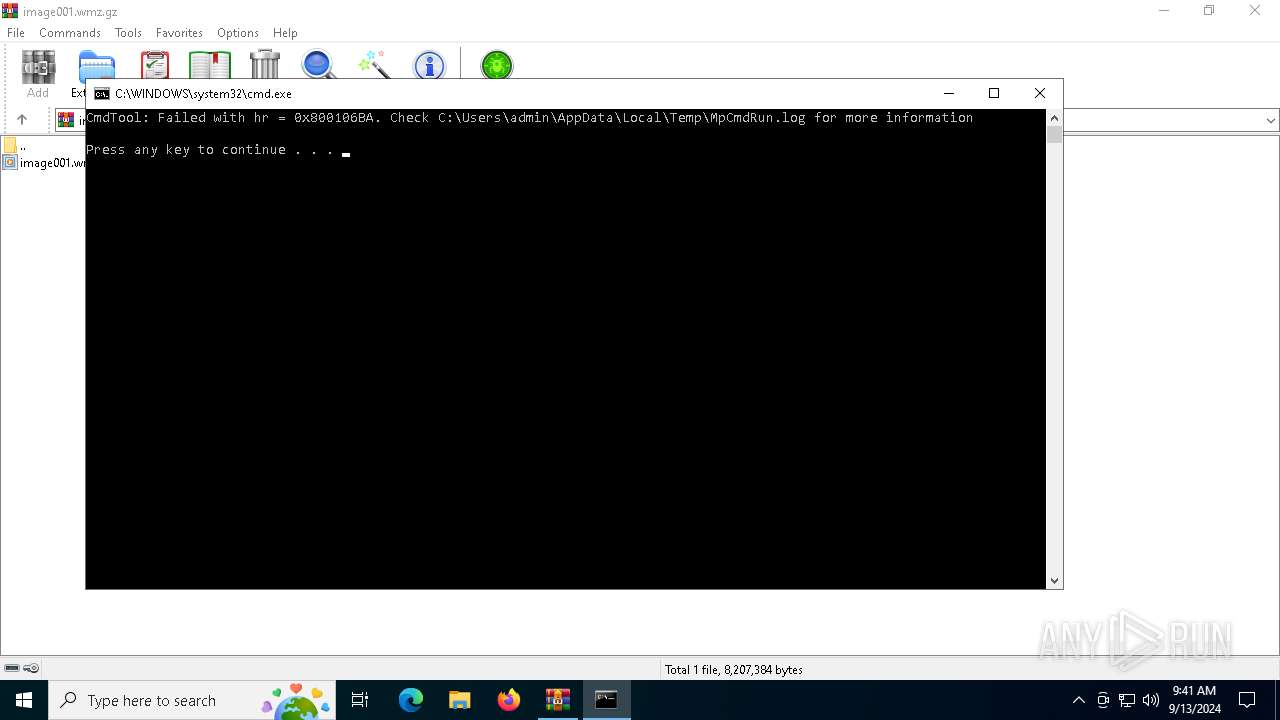
Antivirus name has been found in the command line (generic signature)
- MpCmdRun.exe (PID: 4008)
SUSPICIOUS
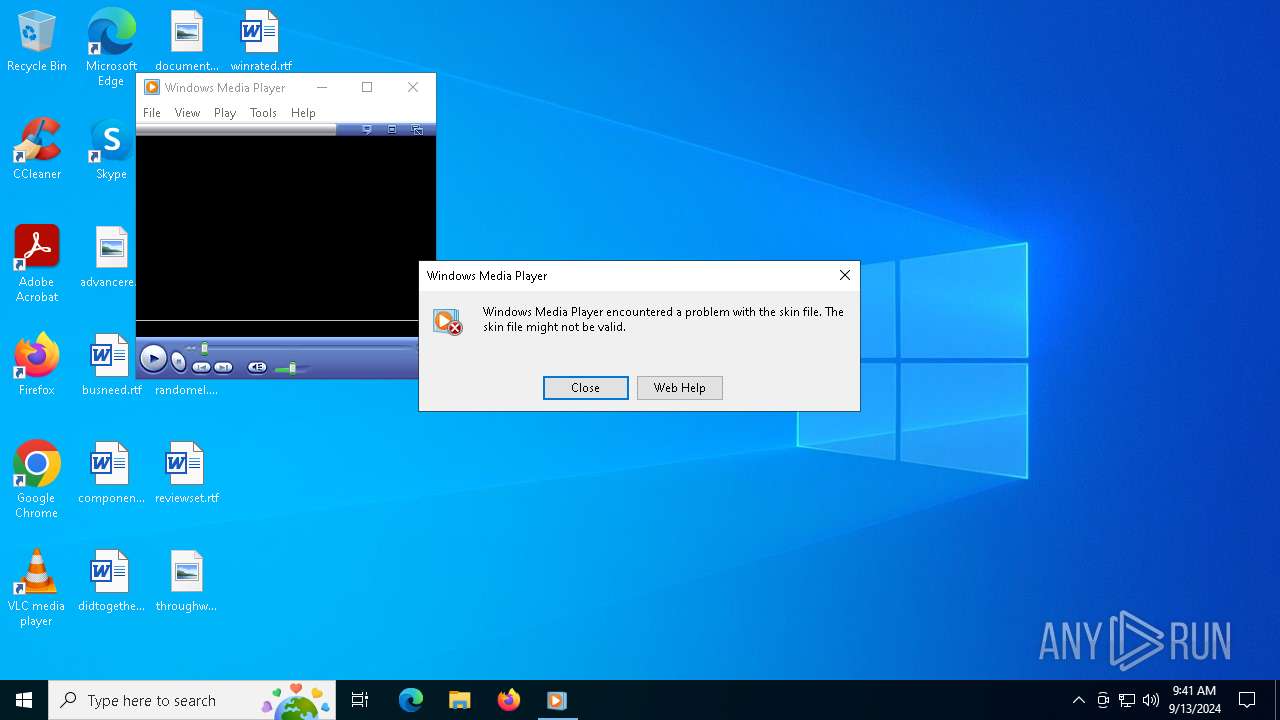
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4804)
- wmplayer.exe (PID: 1656)
- wmplayer.exe (PID: 6916)
- setup_wm.exe (PID: 6564)
- wmplayer.exe (PID: 3964)
- wmplayer.exe (PID: 3256)
- wmplayer.exe (PID: 2520)
Reads Internet Explorer settings
- wmplayer.exe (PID: 6916)
- wmplayer.exe (PID: 3964)
- wmplayer.exe (PID: 3256)
- wmplayer.exe (PID: 2520)
Reads Microsoft Outlook installation path
- wmplayer.exe (PID: 6916)
- wmplayer.exe (PID: 3964)
- wmplayer.exe (PID: 3256)
- wmplayer.exe (PID: 2520)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 4804)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 4804)
INFO
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 4804)
Checks supported languages
- wmplayer.exe (PID: 1656)
- setup_wm.exe (PID: 6564)
- wmplayer.exe (PID: 3964)
- wmplayer.exe (PID: 3256)
- MpCmdRun.exe (PID: 4008)
- wmplayer.exe (PID: 2520)
- wmplayer.exe (PID: 6916)
Reads the computer name
- wmplayer.exe (PID: 1656)
- setup_wm.exe (PID: 6564)
- wmplayer.exe (PID: 6916)
- wmplayer.exe (PID: 3964)
- MpCmdRun.exe (PID: 4008)
- wmplayer.exe (PID: 3256)
- wmplayer.exe (PID: 2520)
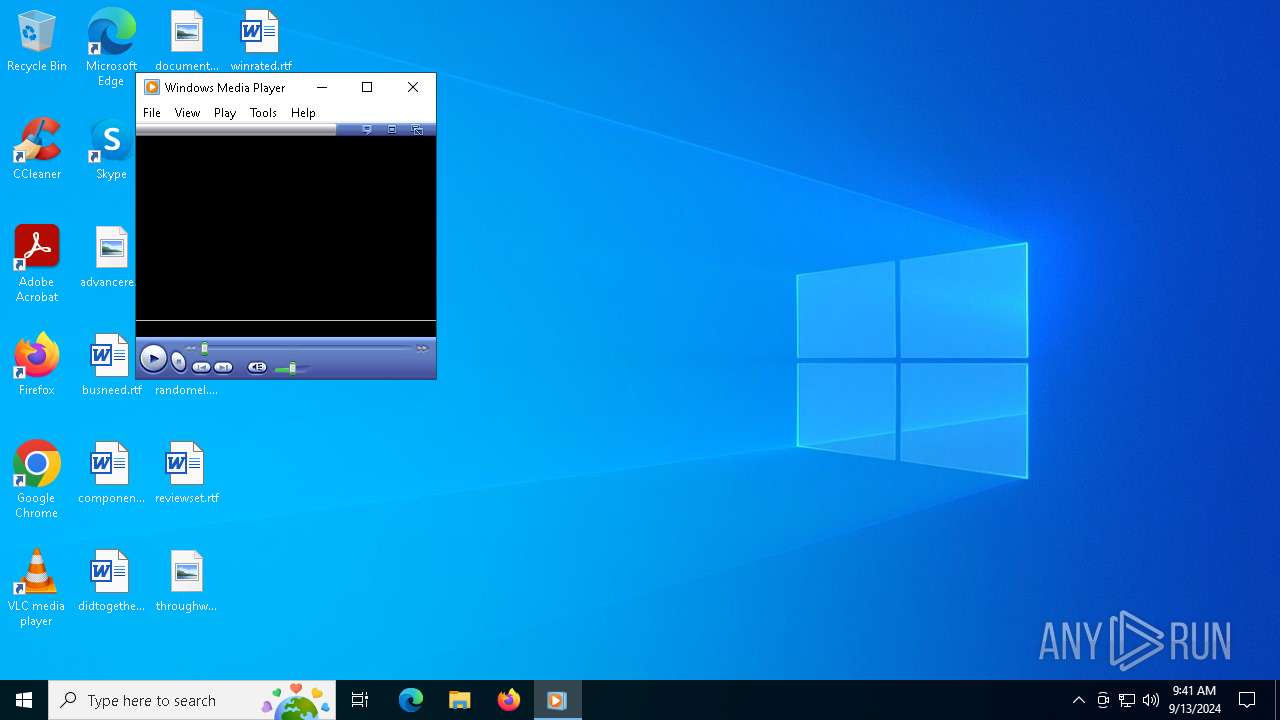
The process uses the downloaded file
- wmplayer.exe (PID: 1656)
- unregmp2.exe (PID: 2340)
- WinRAR.exe (PID: 4804)
- wmplayer.exe (PID: 6916)
- wmplayer.exe (PID: 3964)
- wmplayer.exe (PID: 3256)
- setup_wm.exe (PID: 6564)
- unregmp2.exe (PID: 2128)
Process checks computer location settings
- wmplayer.exe (PID: 1656)
- wmplayer.exe (PID: 6916)
- wmplayer.exe (PID: 3964)
- wmplayer.exe (PID: 3256)
- wmplayer.exe (PID: 2520)
- setup_wm.exe (PID: 6564)
Create files in a temporary directory
- unregmp2.exe (PID: 2340)
- MpCmdRun.exe (PID: 4008)
Reads security settings of Internet Explorer
- unregmp2.exe (PID: 2340)
- unregmp2.exe (PID: 2128)
Reads the machine GUID from the registry
- wmplayer.exe (PID: 6916)
- wmplayer.exe (PID: 3964)
- wmplayer.exe (PID: 3256)
- wmplayer.exe (PID: 2520)
Creates files or folders in the user directory
- wmplayer.exe (PID: 6916)
- wmplayer.exe (PID: 3964)
- wmplayer.exe (PID: 3256)
- wmplayer.exe (PID: 2520)
- unregmp2.exe (PID: 1224)
Checks proxy server information
- wmplayer.exe (PID: 6916)
- wmplayer.exe (PID: 3964)
- wmplayer.exe (PID: 3256)
- wmplayer.exe (PID: 2520)
- slui.exe (PID: 1048)
Reads the software policy settings
- wmplayer.exe (PID: 6916)
- slui.exe (PID: 2768)
- slui.exe (PID: 1048)
Manual execution by a user
- wmplayer.exe (PID: 3256)
- wmplayer.exe (PID: 2520)
Sends debugging messages
- wmplayer.exe (PID: 2520)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .z/gz/gzip | | | GZipped data (100) |
|---|
EXIF
ZIP
| Compression: | Deflated |
|---|---|
| Flags: | (none) |
| ModifyDate: | 0000:00:00 00:00:00 |
| ExtraFlags: | Fastest Algorithm |
| OperatingSystem: | NTFS filesystem (NT) |
Total processes
150
Monitored processes
17
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR4804.27208\Rar$Scan38588.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1048 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1224 | "C:\WINDOWS\SysNative\unregmp2.exe" /AsyncFirstLogon /REENTRANT | C:\Windows\System32\unregmp2.exe | — | unregmp2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Windows Media Player Setup Utility Exit code: 0 Version: 12.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1608 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
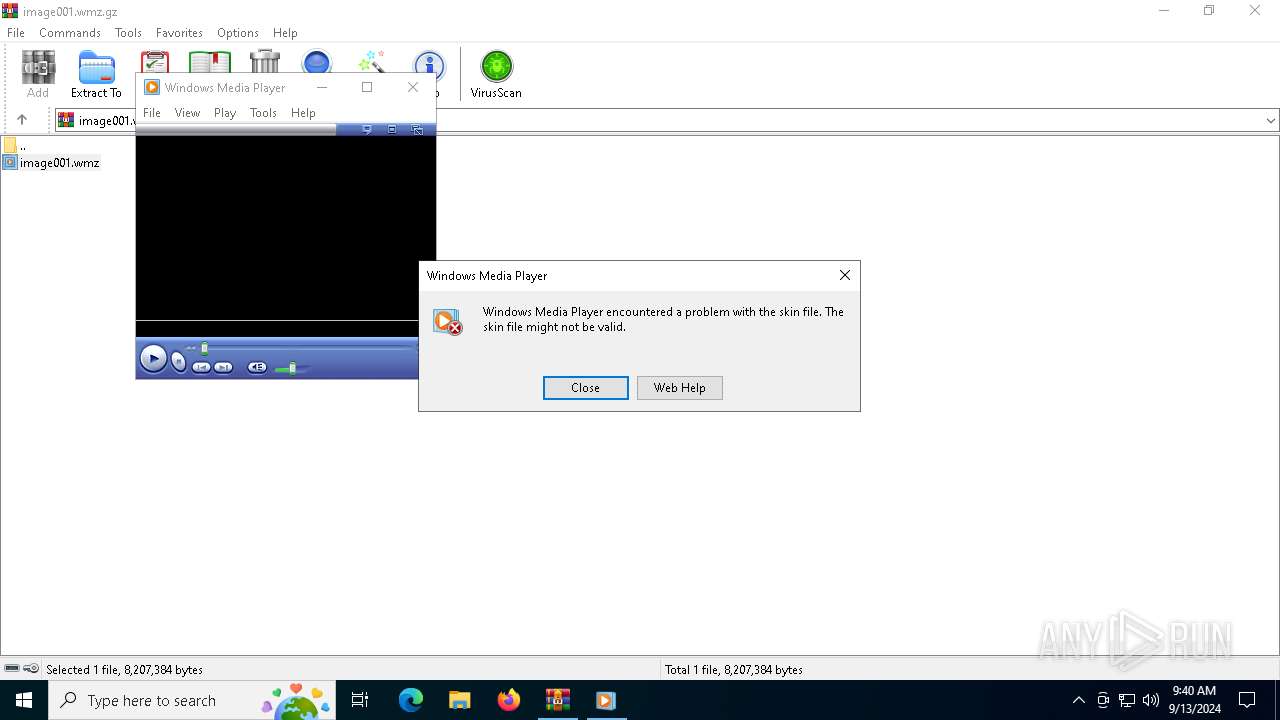
| 1656 | "C:\Program Files (x86)\Windows Media Player\wmplayer.exe" /layout:"C:\Users\admin\AppData\Local\Temp\Rar$DIa4804.23720\image001.wmz" | C:\Program Files (x86)\Windows Media Player\wmplayer.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Exit code: 0 Version: 12.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2128 | C:\WINDOWS\system32\unregmp2.exe /ShowWMP /SetShowState /CreateMediaLibrary | C:\Windows\SysWOW64\unregmp2.exe | — | setup_wm.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Windows Media Player Setup Utility Exit code: 0 Version: 12.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2340 | "C:\Windows\System32\unregmp2.exe" /AsyncFirstLogon | C:\Windows\SysWOW64\unregmp2.exe | — | wmplayer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Windows Media Player Setup Utility Exit code: 0 Version: 12.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2520 | "C:\Program Files (x86)\Windows Media Player\wmplayer.exe" /prefetch:1 | C:\Program Files (x86)\Windows Media Player\wmplayer.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Exit code: 0 Version: 12.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2768 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3256 | "C:\Program Files (x86)\Windows Media Player\wmplayer.exe" /layout:"C:\Users\admin\Desktop\image001.wmz" | C:\Program Files (x86)\Windows Media Player\wmplayer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Exit code: 0 Version: 12.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
18 078
Read events
17 570
Write events
465
Delete events
43
Modification events
| (PID) Process: | (4804) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (4804) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\image001.wmz.gz | |||
| (PID) Process: | (4804) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4804) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4804) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4804) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4804) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.wmz\OpenWithProgids |
| Operation: | write | Name: | WMP11.AssocFile.WMZ |
Value: | |||
| (PID) Process: | (6564) setup_wm.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\MediaPlayer\Preferences |
| Operation: | delete value | Name: | UsageTracking |
Value: | |||
| (PID) Process: | (6564) setup_wm.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\MediaPlayer\Preferences |
| Operation: | delete value | Name: | ForceUsageTracking |
Value: | |||
| (PID) Process: | (6564) setup_wm.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\MediaPlayer\Preferences |
| Operation: | delete value | Name: | SQMLaunchIndex |
Value: | |||
Executable files
0
Suspicious files
8
Text files
8
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4804 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa4804.23720\image001.wmz | — | |
MD5:— | SHA256:— | |||
| 4804 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa4804.25980\image001.wmz | — | |
MD5:— | SHA256:— | |||
| 4804 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4804.27208\image001.wmz.gz\image001.wmz | — | |
MD5:— | SHA256:— | |||
| 4804 | WinRAR.exe | C:\Users\admin\Desktop\image001.wmz | — | |
MD5:— | SHA256:— | |||
| 1224 | unregmp2.exe | C:\Users\admin\AppData\Local\Microsoft\Media Player\LocalMLS_3.wmdb | binary | |
MD5:36C13F5A06458890A580FB8DA6427EDF | SHA256:9C8249C18959AF4165B9D22094F9D60FA8757A275612B0C5AAFD1E9921D388B7 | |||
| 6916 | wmplayer.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\21253908F3CB05D51B1C2DA8B681A785 | binary | |
MD5:0C5D78245C50CE4A117025CC4D945BCC | SHA256:DE5A7E221E9AAA6A1CF835691A6504C21CCFD4BB16DC181D1A71AC355F616C8E | |||
| 1224 | unregmp2.exe | C:\Users\admin\AppData\Local\Microsoft\Media Player\CurrentDatabase_400.wmdb | binary | |
MD5:79AEACC048DB9CA31E1BAF148FFC66C6 | SHA256:9974FC100ABF3300E5EBCAB88D7BA8F66158429E8EBB155F7118AECCC062FFF7 | |||
| 1224 | unregmp2.exe | C:\Users\admin\AppData\Local\Microsoft\Windows Media\12.0\WMSDKNSD.XML | text | |
MD5:A9B5DA9AEC61657B32393D96217165F0 | SHA256:9F4611369CF65B33D886489B2486FCA7B1E83E0DC998D35B15B3AA4C8478A28D | |||
| 6916 | wmplayer.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\21253908F3CB05D51B1C2DA8B681A785 | der | |
MD5:1B7FD5177461034E4086724C5845E927 | SHA256:065AF18C229898A1C2A8D989911ADCD9B1E2AB14B1953EBF8EAF34AE37EA1627 | |||
| 2520 | wmplayer.exe | C:\Users\admin\AppData\Local\Microsoft\Media Player\wmpfolders.wmdb | text | |
MD5:89B5318D435F83601C3C533770157377 | SHA256:D559AF4EF376C1A97238187AF2B63623246E77E5CFAB40B0C03220B86534DEC5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
58
DNS requests
24
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6252 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6916 | wmplayer.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6108 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6844 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6844 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6252 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6268 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6252 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6252 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6916 | wmplayer.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6916 | wmplayer.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3260 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
Process | Message |
|---|---|
wmplayer.exe | Thumbnail Cache: Attempting to replace an entry that is in use
|