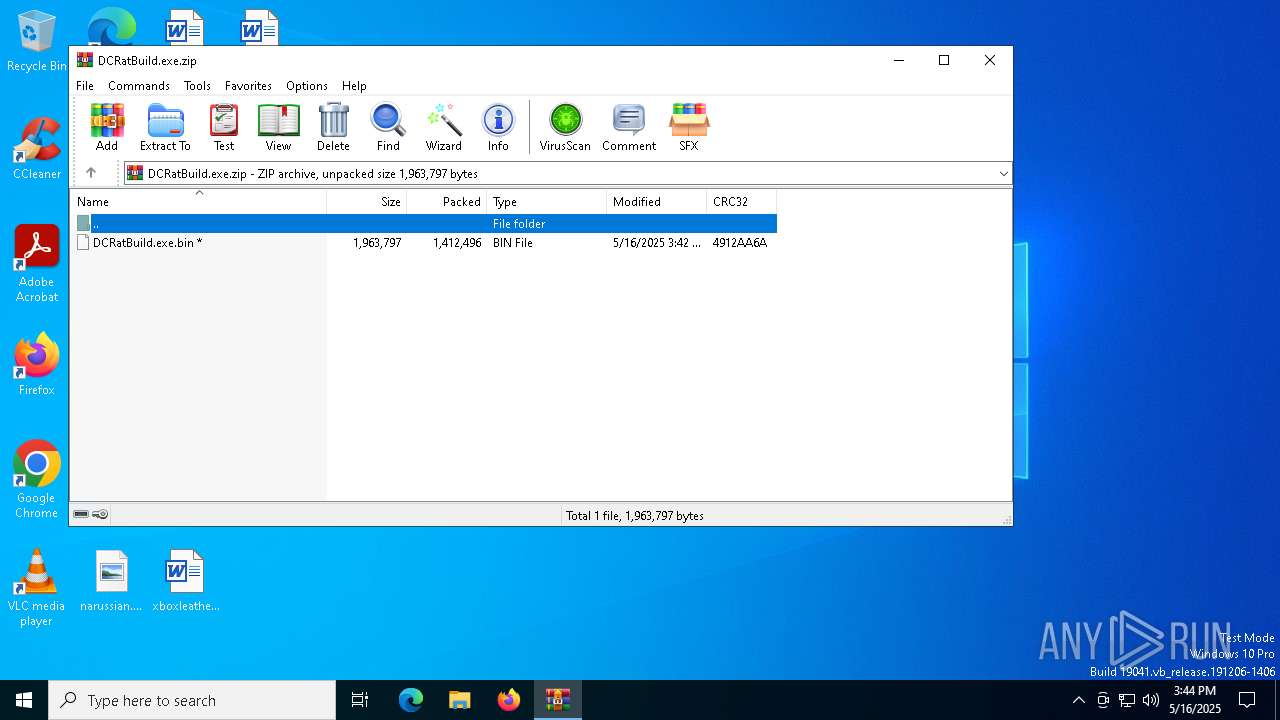
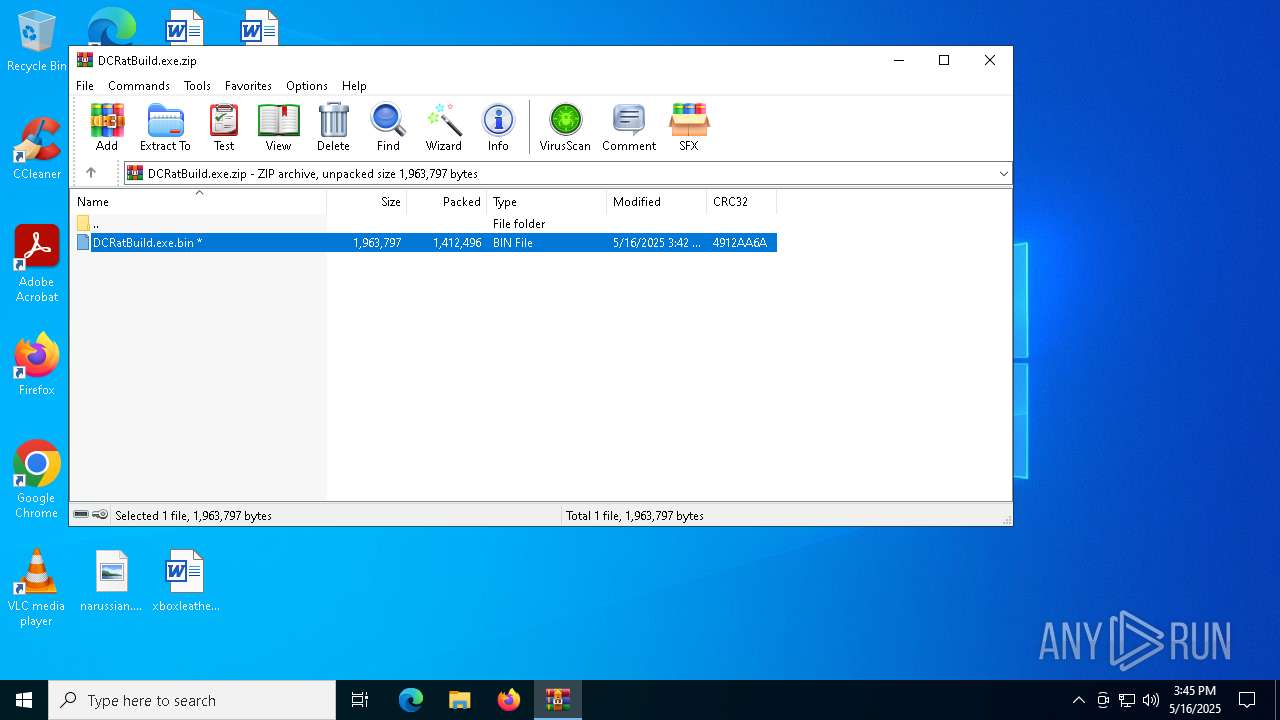
| File name: | DCRatBuild.exe.zip |
| Full analysis: | https://app.any.run/tasks/b04bc597-38a4-46f5-85c7-85bc729a8d28 |
| Verdict: | Malicious activity |
| Threats: | DCrat, also known as Dark Crystal RAT, is a remote access trojan (RAT), which was first introduced in 2018. It is a modular malware that can be customized to perform different tasks. For instance, it can steal passwords, crypto wallet information, hijack Telegram and Steam accounts, and more. Attackers may use a variety of methods to distribute DCrat, but phishing email campaigns are the most common. |
| Analysis date: | May 16, 2025, 15:44:50 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
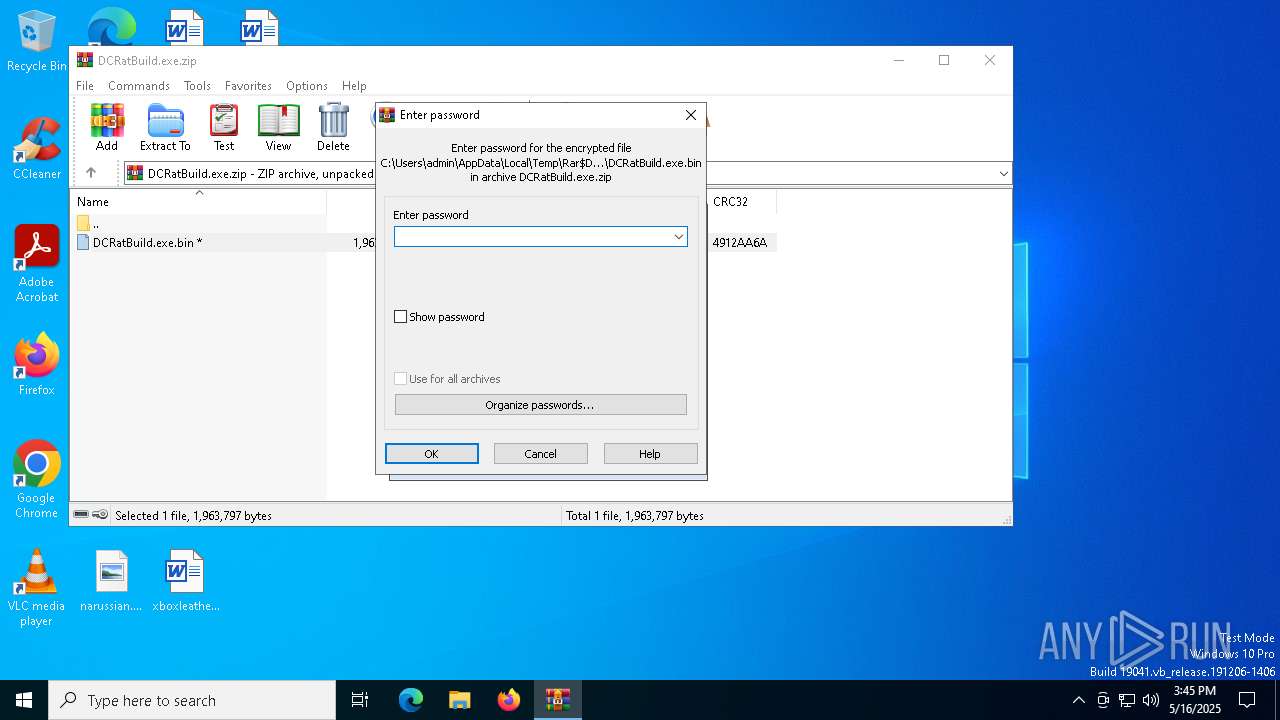
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 89E9C3E72E85C4F8592D0525F2BBD8FE |
| SHA1: | 1CB8EAF750F6D2E49ACA8E164B1EF89767B3844F |
| SHA256: | 626626F27AE96B820ACF17875EA72A69978573F600902BF8832E28AA06B41B12 |
| SSDEEP: | 49152:YnwJUCM1zf05ux6WXC3k5txmYPojEbtOec+rXaJeimtf6Pr/w6WHAf4hPyWadqc6:YnYUCmj052n5tZPrtrXacHtkc6WHOAyq |
MALICIOUS
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 7148)
- wscript.exe (PID: 5136)
DCRAT mutex has been found
- RuntimeBroker.exe (PID: 4336)
- RuntimeBroker.exe (PID: 6760)
- mscomSaves.exe (PID: 1328)
- RuntimeBroker.exe (PID: 6256)
- RuntimeBroker.exe (PID: 3024)
- RuntimeBroker.exe (PID: 5064)
- RuntimeBroker.exe (PID: 6048)
- mscomSaves.exe (PID: 4988)
- RuntimeBroker.exe (PID: 2136)
- mscomSaves.exe (PID: 2064)
- RuntimeBroker.exe (PID: 236)
- mscomSaves.exe (PID: 4300)
- RuntimeBroker.exe (PID: 3300)
- mscomSaves.exe (PID: 5280)
- RuntimeBroker.exe (PID: 6644)
DCRAT has been detected (YARA)
- slui.exe (PID: 2516)
SUSPICIOUS
Executable content was dropped or overwritten
- DCRatBuild.exe (PID: 1804)
- mscomSaves.exe (PID: 1328)
Executing commands from a ".bat" file
- wscript.exe (PID: 7148)
- mscomSaves.exe (PID: 1328)
- RuntimeBroker.exe (PID: 4336)
- RuntimeBroker.exe (PID: 6760)
- RuntimeBroker.exe (PID: 6256)
- RuntimeBroker.exe (PID: 3024)
- RuntimeBroker.exe (PID: 5064)
- RuntimeBroker.exe (PID: 6048)
- wscript.exe (PID: 5136)
- mscomSaves.exe (PID: 4988)
- RuntimeBroker.exe (PID: 2136)
- mscomSaves.exe (PID: 2064)
- RuntimeBroker.exe (PID: 236)
- mscomSaves.exe (PID: 4300)
- RuntimeBroker.exe (PID: 3300)
- RuntimeBroker.exe (PID: 6644)
- mscomSaves.exe (PID: 5280)
- RuntimeBroker.exe (PID: 5504)
- mscomSaves.exe (PID: 5228)
- RuntimeBroker.exe (PID: 856)
- mscomSaves.exe (PID: 6132)
- mscomSaves.exe (PID: 6228)
- mscomSaves.exe (PID: 2780)
- RuntimeBroker.exe (PID: 3028)
- mscomSaves.exe (PID: 3032)
- mscomSaves.exe (PID: 5968)
- mscomSaves.exe (PID: 236)
- mscomSaves.exe (PID: 4380)
- mscomSaves.exe (PID: 2896)
- mscomSaves.exe (PID: 240)
- mscomSaves.exe (PID: 864)
- mscomSaves.exe (PID: 1168)
- mscomSaves.exe (PID: 5404)
- mscomSaves.exe (PID: 5008)
- mscomSaves.exe (PID: 6080)
- mscomSaves.exe (PID: 6032)
- mscomSaves.exe (PID: 3300)
Runs shell command (SCRIPT)
- wscript.exe (PID: 7148)
- wscript.exe (PID: 5136)
Reads security settings of Internet Explorer
- DCRatBuild.exe (PID: 1804)
- mscomSaves.exe (PID: 1328)
- RuntimeBroker.exe (PID: 4336)
- RuntimeBroker.exe (PID: 6760)
- RuntimeBroker.exe (PID: 6256)
- RuntimeBroker.exe (PID: 3024)
- RuntimeBroker.exe (PID: 5064)
- RuntimeBroker.exe (PID: 6048)
- mscomSaves.exe (PID: 4988)
- RuntimeBroker.exe (PID: 2136)
- mscomSaves.exe (PID: 2064)
- RuntimeBroker.exe (PID: 236)
- mscomSaves.exe (PID: 4300)
- DCRatBuild.exe (PID: 5112)
- RuntimeBroker.exe (PID: 3300)
- mscomSaves.exe (PID: 5280)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 7148)
- mscomSaves.exe (PID: 1328)
- RuntimeBroker.exe (PID: 4336)
- RuntimeBroker.exe (PID: 6760)
- RuntimeBroker.exe (PID: 6256)
- RuntimeBroker.exe (PID: 3024)
- RuntimeBroker.exe (PID: 5064)
- wscript.exe (PID: 5136)
- RuntimeBroker.exe (PID: 6048)
- mscomSaves.exe (PID: 4988)
- RuntimeBroker.exe (PID: 2136)
- mscomSaves.exe (PID: 2064)
- RuntimeBroker.exe (PID: 236)
- RuntimeBroker.exe (PID: 3300)
- RuntimeBroker.exe (PID: 6644)
- mscomSaves.exe (PID: 5280)
- mscomSaves.exe (PID: 5228)
- mscomSaves.exe (PID: 6228)
- RuntimeBroker.exe (PID: 5504)
- RuntimeBroker.exe (PID: 856)
- mscomSaves.exe (PID: 6132)
- mscomSaves.exe (PID: 3032)
- RuntimeBroker.exe (PID: 3028)
- mscomSaves.exe (PID: 2780)
- mscomSaves.exe (PID: 4300)
- mscomSaves.exe (PID: 236)
- mscomSaves.exe (PID: 5968)
- mscomSaves.exe (PID: 4380)
- mscomSaves.exe (PID: 240)
- mscomSaves.exe (PID: 1168)
- mscomSaves.exe (PID: 2896)
- mscomSaves.exe (PID: 5008)
- mscomSaves.exe (PID: 6080)
- mscomSaves.exe (PID: 3300)
- mscomSaves.exe (PID: 864)
- mscomSaves.exe (PID: 5404)
- mscomSaves.exe (PID: 6032)
Reads the date of Windows installation
- mscomSaves.exe (PID: 1328)
- RuntimeBroker.exe (PID: 4336)
- RuntimeBroker.exe (PID: 6760)
- RuntimeBroker.exe (PID: 6256)
- RuntimeBroker.exe (PID: 3024)
- RuntimeBroker.exe (PID: 5064)
- RuntimeBroker.exe (PID: 6048)
- mscomSaves.exe (PID: 4988)
- RuntimeBroker.exe (PID: 2136)
- mscomSaves.exe (PID: 2064)
- RuntimeBroker.exe (PID: 236)
- mscomSaves.exe (PID: 4300)
- RuntimeBroker.exe (PID: 3300)
- mscomSaves.exe (PID: 5280)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 1012)
- cmd.exe (PID: 2568)
- cmd.exe (PID: 872)
- cmd.exe (PID: 4376)
- cmd.exe (PID: 6272)
- cmd.exe (PID: 3396)
- cmd.exe (PID: 3020)
- cmd.exe (PID: 960)
- cmd.exe (PID: 5868)
- cmd.exe (PID: 3240)
- cmd.exe (PID: 5304)
- cmd.exe (PID: 1676)
- cmd.exe (PID: 2096)
- cmd.exe (PID: 5188)
Starts application with an unusual extension
- cmd.exe (PID: 1012)
- cmd.exe (PID: 6132)
- cmd.exe (PID: 3100)
- cmd.exe (PID: 2568)
- cmd.exe (PID: 924)
- cmd.exe (PID: 4188)
- cmd.exe (PID: 2384)
- cmd.exe (PID: 5956)
- cmd.exe (PID: 5952)
- cmd.exe (PID: 872)
- cmd.exe (PID: 4376)
- cmd.exe (PID: 6736)
- cmd.exe (PID: 4304)
- cmd.exe (PID: 2096)
- cmd.exe (PID: 4892)
- cmd.exe (PID: 6272)
- cmd.exe (PID: 1328)
- cmd.exe (PID: 4980)
- cmd.exe (PID: 516)
- cmd.exe (PID: 3396)
- cmd.exe (PID: 960)
- cmd.exe (PID: 3020)
- cmd.exe (PID: 1004)
- cmd.exe (PID: 3240)
- cmd.exe (PID: 5868)
- cmd.exe (PID: 2564)
- cmd.exe (PID: 2096)
- cmd.exe (PID: 1676)
- cmd.exe (PID: 5304)
- cmd.exe (PID: 236)
- cmd.exe (PID: 5452)
- cmd.exe (PID: 3032)
- cmd.exe (PID: 6700)
- cmd.exe (PID: 5188)
Probably delay the execution using 'w32tm.exe'
- cmd.exe (PID: 6132)
- cmd.exe (PID: 3100)
- cmd.exe (PID: 924)
- cmd.exe (PID: 4188)
- cmd.exe (PID: 2384)
- cmd.exe (PID: 5956)
- cmd.exe (PID: 5952)
- cmd.exe (PID: 6736)
- cmd.exe (PID: 4304)
- cmd.exe (PID: 2096)
- cmd.exe (PID: 4892)
- cmd.exe (PID: 1328)
- cmd.exe (PID: 4980)
- cmd.exe (PID: 516)
- cmd.exe (PID: 1004)
- cmd.exe (PID: 2564)
- cmd.exe (PID: 236)
- cmd.exe (PID: 6700)
- cmd.exe (PID: 5452)
- cmd.exe (PID: 3032)
- cmd.exe (PID: 6456)
The process creates files with name similar to system file names
- mscomSaves.exe (PID: 1328)
INFO
Manual execution by a user
- DCRatBuild.exe (PID: 1804)
- DCRatBuild.exe (PID: 5112)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 900)
Checks supported languages
- DCRatBuild.exe (PID: 1804)
- mscomSaves.exe (PID: 1328)
- RuntimeBroker.exe (PID: 4336)
- chcp.com (PID: 736)
- chcp.com (PID: 5892)
- RuntimeBroker.exe (PID: 6760)
- chcp.com (PID: 672)
- RuntimeBroker.exe (PID: 6256)
- chcp.com (PID: 5756)
- RuntimeBroker.exe (PID: 3024)
- chcp.com (PID: 2316)
- RuntimeBroker.exe (PID: 5064)
- RuntimeBroker.exe (PID: 6048)
- chcp.com (PID: 2980)
- chcp.com (PID: 4040)
- chcp.com (PID: 7020)
- RuntimeBroker.exe (PID: 2136)
- mscomSaves.exe (PID: 4988)
- chcp.com (PID: 1388)
- mscomSaves.exe (PID: 2064)
- chcp.com (PID: 5780)
- chcp.com (PID: 5232)
- RuntimeBroker.exe (PID: 236)
- mscomSaves.exe (PID: 4300)
- RuntimeBroker.exe (PID: 3300)
- chcp.com (PID: 1452)
- mscomSaves.exe (PID: 5280)
- DCRatBuild.exe (PID: 5112)
- chcp.com (PID: 3028)
- RuntimeBroker.exe (PID: 6644)
- chcp.com (PID: 3240)
Drops encrypted VBS script (Microsoft Script Encoder)
- DCRatBuild.exe (PID: 1804)
Reads the computer name
- DCRatBuild.exe (PID: 1804)
- mscomSaves.exe (PID: 1328)
- RuntimeBroker.exe (PID: 4336)
- RuntimeBroker.exe (PID: 6760)
- RuntimeBroker.exe (PID: 6256)
- RuntimeBroker.exe (PID: 3024)
- RuntimeBroker.exe (PID: 5064)
- RuntimeBroker.exe (PID: 6048)
- DCRatBuild.exe (PID: 5112)
- mscomSaves.exe (PID: 4988)
- RuntimeBroker.exe (PID: 2136)
- mscomSaves.exe (PID: 2064)
- RuntimeBroker.exe (PID: 236)
- mscomSaves.exe (PID: 4300)
- RuntimeBroker.exe (PID: 3300)
- mscomSaves.exe (PID: 5280)
- RuntimeBroker.exe (PID: 6644)
Reads the machine GUID from the registry
- mscomSaves.exe (PID: 1328)
- RuntimeBroker.exe (PID: 4336)
- RuntimeBroker.exe (PID: 6760)
- RuntimeBroker.exe (PID: 3024)
- RuntimeBroker.exe (PID: 5064)
- RuntimeBroker.exe (PID: 6048)
- RuntimeBroker.exe (PID: 6256)
- mscomSaves.exe (PID: 4988)
- RuntimeBroker.exe (PID: 2136)
- mscomSaves.exe (PID: 2064)
- RuntimeBroker.exe (PID: 236)
- mscomSaves.exe (PID: 4300)
- RuntimeBroker.exe (PID: 3300)
- mscomSaves.exe (PID: 5280)
- RuntimeBroker.exe (PID: 6644)
Reads Environment values
- mscomSaves.exe (PID: 1328)
- RuntimeBroker.exe (PID: 4336)
- RuntimeBroker.exe (PID: 6760)
- RuntimeBroker.exe (PID: 6256)
- RuntimeBroker.exe (PID: 3024)
- RuntimeBroker.exe (PID: 5064)
- RuntimeBroker.exe (PID: 6048)
- mscomSaves.exe (PID: 4988)
- RuntimeBroker.exe (PID: 2136)
- mscomSaves.exe (PID: 2064)
- RuntimeBroker.exe (PID: 236)
- mscomSaves.exe (PID: 4300)
- RuntimeBroker.exe (PID: 3300)
- mscomSaves.exe (PID: 5280)
- RuntimeBroker.exe (PID: 6644)
Process checks computer location settings
- DCRatBuild.exe (PID: 1804)
- mscomSaves.exe (PID: 1328)
- RuntimeBroker.exe (PID: 4336)
- RuntimeBroker.exe (PID: 6760)
- RuntimeBroker.exe (PID: 6256)
- RuntimeBroker.exe (PID: 3024)
- RuntimeBroker.exe (PID: 5064)
- DCRatBuild.exe (PID: 5112)
- RuntimeBroker.exe (PID: 6048)
- mscomSaves.exe (PID: 4988)
- RuntimeBroker.exe (PID: 2136)
- mscomSaves.exe (PID: 2064)
- RuntimeBroker.exe (PID: 236)
- mscomSaves.exe (PID: 4300)
- RuntimeBroker.exe (PID: 3300)
- mscomSaves.exe (PID: 5280)
Changes the display of characters in the console
- cmd.exe (PID: 1012)
- cmd.exe (PID: 6132)
- cmd.exe (PID: 3100)
- cmd.exe (PID: 2568)
- cmd.exe (PID: 924)
- cmd.exe (PID: 4188)
- cmd.exe (PID: 2384)
- cmd.exe (PID: 5956)
- cmd.exe (PID: 5952)
- cmd.exe (PID: 872)
- cmd.exe (PID: 4376)
- cmd.exe (PID: 6736)
- cmd.exe (PID: 4304)
- cmd.exe (PID: 2096)
- cmd.exe (PID: 1328)
- cmd.exe (PID: 4892)
- cmd.exe (PID: 6272)
- cmd.exe (PID: 3396)
- cmd.exe (PID: 4980)
- cmd.exe (PID: 516)
- cmd.exe (PID: 1004)
- cmd.exe (PID: 960)
- cmd.exe (PID: 3020)
- cmd.exe (PID: 2564)
- cmd.exe (PID: 5868)
- cmd.exe (PID: 3240)
- cmd.exe (PID: 2096)
- cmd.exe (PID: 1676)
- cmd.exe (PID: 5304)
- cmd.exe (PID: 236)
- cmd.exe (PID: 5452)
- cmd.exe (PID: 3032)
- cmd.exe (PID: 6700)
- cmd.exe (PID: 5188)
Create files in a temporary directory
- mscomSaves.exe (PID: 1328)
- RuntimeBroker.exe (PID: 4336)
- RuntimeBroker.exe (PID: 6760)
- RuntimeBroker.exe (PID: 6256)
- RuntimeBroker.exe (PID: 3024)
- RuntimeBroker.exe (PID: 5064)
- RuntimeBroker.exe (PID: 6048)
- mscomSaves.exe (PID: 4988)
- RuntimeBroker.exe (PID: 2136)
- mscomSaves.exe (PID: 2064)
- RuntimeBroker.exe (PID: 236)
- mscomSaves.exe (PID: 4300)
- RuntimeBroker.exe (PID: 3300)
- mscomSaves.exe (PID: 5280)
Checks proxy server information
- RuntimeBroker.exe (PID: 4336)
- RuntimeBroker.exe (PID: 6760)
- RuntimeBroker.exe (PID: 6256)
- RuntimeBroker.exe (PID: 3024)
- RuntimeBroker.exe (PID: 5064)
- RuntimeBroker.exe (PID: 6048)
- mscomSaves.exe (PID: 4988)
- RuntimeBroker.exe (PID: 2136)
- mscomSaves.exe (PID: 2064)
- RuntimeBroker.exe (PID: 236)
- mscomSaves.exe (PID: 4300)
- slui.exe (PID: 2516)
- RuntimeBroker.exe (PID: 3300)
- mscomSaves.exe (PID: 5280)
- RuntimeBroker.exe (PID: 6644)
Disables trace logs
- RuntimeBroker.exe (PID: 4336)
- RuntimeBroker.exe (PID: 6760)
- RuntimeBroker.exe (PID: 3024)
- RuntimeBroker.exe (PID: 5064)
- RuntimeBroker.exe (PID: 6048)
- RuntimeBroker.exe (PID: 6256)
- mscomSaves.exe (PID: 4988)
- RuntimeBroker.exe (PID: 2136)
- mscomSaves.exe (PID: 2064)
- RuntimeBroker.exe (PID: 236)
- mscomSaves.exe (PID: 4300)
- RuntimeBroker.exe (PID: 3300)
- mscomSaves.exe (PID: 5280)
- RuntimeBroker.exe (PID: 6644)
Failed to create an executable file in Windows directory
- mscomSaves.exe (PID: 1328)
Reads the software policy settings
- slui.exe (PID: 2516)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2025:05:16 15:42:52 |
| ZipCRC: | 0x4912aa6a |
| ZipCompressedSize: | 1412496 |
| ZipUncompressedSize: | 1963797 |
| ZipFileName: | DCRatBuild.exe.bin |
Total processes
316
Monitored processes
186
Malicious processes
33
Suspicious processes
15
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | "C:\PortBrowsermonitorcommonSvc\RuntimeBroker.exe" | C:\PortBrowsermonitorcommonSvc\RuntimeBroker.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.2.7.1277 Modules
| |||||||||||||||
| 236 | "C:\PortBrowsermonitorcommonSvc\mscomSaves.exe" | C:\PortBrowsermonitorcommonSvc\mscomSaves.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.2.7.1277 Modules
| |||||||||||||||
| 236 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\9rsY8ZYMRr.bat" " | C:\Windows\System32\cmd.exe | — | mscomSaves.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 240 | "C:\PortBrowsermonitorcommonSvc\mscomSaves.exe" | C:\PortBrowsermonitorcommonSvc\mscomSaves.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.2.7.1277 Modules
| |||||||||||||||
| 516 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\sMcwJl1juU.bat" " | C:\Windows\System32\cmd.exe | — | mscomSaves.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 540 | w32tm /stripchart /computer:localhost /period:5 /dataonly /samples:2 | C:\Windows\System32\w32tm.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Time Service Diagnostic Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | w32tm /stripchart /computer:localhost /period:5 /dataonly /samples:2 | C:\Windows\System32\w32tm.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Time Service Diagnostic Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 672 | chcp 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | w32tm /stripchart /computer:localhost /period:5 /dataonly /samples:2 | C:\Windows\System32\w32tm.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Time Service Diagnostic Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | chcp 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
50 147
Read events
50 110
Write events
37
Delete events
0
Modification events
| (PID) Process: | (900) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (900) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (900) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (900) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\DCRatBuild.exe.zip | |||
| (PID) Process: | (900) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (900) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (900) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (900) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (900) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (900) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000200000003000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
7
Suspicious files
1
Text files
77
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1804 | DCRatBuild.exe | C:\PortBrowsermonitorcommonSvc\mscomSaves.exe | executable | |
MD5:61195E62FD58DF2BD09567E8C53351B5 | SHA256:C2C2A6517D39F819FB8C27A6D563A5EDAA3219F825689618A0622F06557469F3 | |||
| 1328 | mscomSaves.exe | C:\PortBrowsermonitorcommonSvc\cc11b995f2a76d | text | |
MD5:FC74F4A4744231E421954041433772EB | SHA256:9FE6B272DED95BD340BFC8C560F4A07F9665032F820B51A59CBF2D928B551598 | |||
| 6760 | RuntimeBroker.exe | C:\Users\admin\AppData\Local\Temp\T1GDl5ZfBw | text | |
MD5:5ABB3725ADBAD9815E874C1264BC7EA7 | SHA256:D84A14980CC53392BC50E73897361DACC92FD73BBC736F1DE2E06924AD6E7484 | |||
| 1328 | mscomSaves.exe | C:\Users\Public\RuntimeBroker.exe | executable | |
MD5:61195E62FD58DF2BD09567E8C53351B5 | SHA256:C2C2A6517D39F819FB8C27A6D563A5EDAA3219F825689618A0622F06557469F3 | |||
| 4336 | RuntimeBroker.exe | C:\Users\admin\AppData\Local\Temp\ouKNAwWJ47 | text | |
MD5:0834158F85D91A5BDA904E6CB2BE3A57 | SHA256:A0C8229FE914ACF825546EE6CB5BB845009827B5DE1B566DB95013819914BF84 | |||
| 1328 | mscomSaves.exe | C:\PortBrowsermonitorcommonSvc\RuntimeBroker.exe | executable | |
MD5:61195E62FD58DF2BD09567E8C53351B5 | SHA256:C2C2A6517D39F819FB8C27A6D563A5EDAA3219F825689618A0622F06557469F3 | |||
| 1328 | mscomSaves.exe | C:\Users\Public\9e8d7a4ca61bd9 | text | |
MD5:27D896D007E51A7F25E8A4C16F16BD68 | SHA256:46B98025F161CE8E01984391A5D6E3B7F3726AA63530231D473F508947673EB8 | |||
| 1804 | DCRatBuild.exe | C:\PortBrowsermonitorcommonSvc\upN7AudNOsu7fM1TSB96pcMycwlqh.bat | text | |
MD5:34BEE2E90C83A630BFFB67B8C36ADB9B | SHA256:03B81AB65BF7B3F5C08A1B9B6F1E74773751D162C016EF2E21975CF400FB7BA3 | |||
| 1328 | mscomSaves.exe | C:\PortBrowsermonitorcommonSvc\fontdrvhost.exe | executable | |
MD5:61195E62FD58DF2BD09567E8C53351B5 | SHA256:C2C2A6517D39F819FB8C27A6D563A5EDAA3219F825689618A0622F06557469F3 | |||
| 1328 | mscomSaves.exe | C:\PortBrowsermonitorcommonSvc\04b7f02c163e52 | text | |
MD5:FC9A3C718087690FB83F8C7703DD783B | SHA256:F7780D2D7FF8EF664912F520C1A5EDFA1343069CC6A1C59DECE26B0B804D9511 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
191
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2096 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2096 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.1:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |