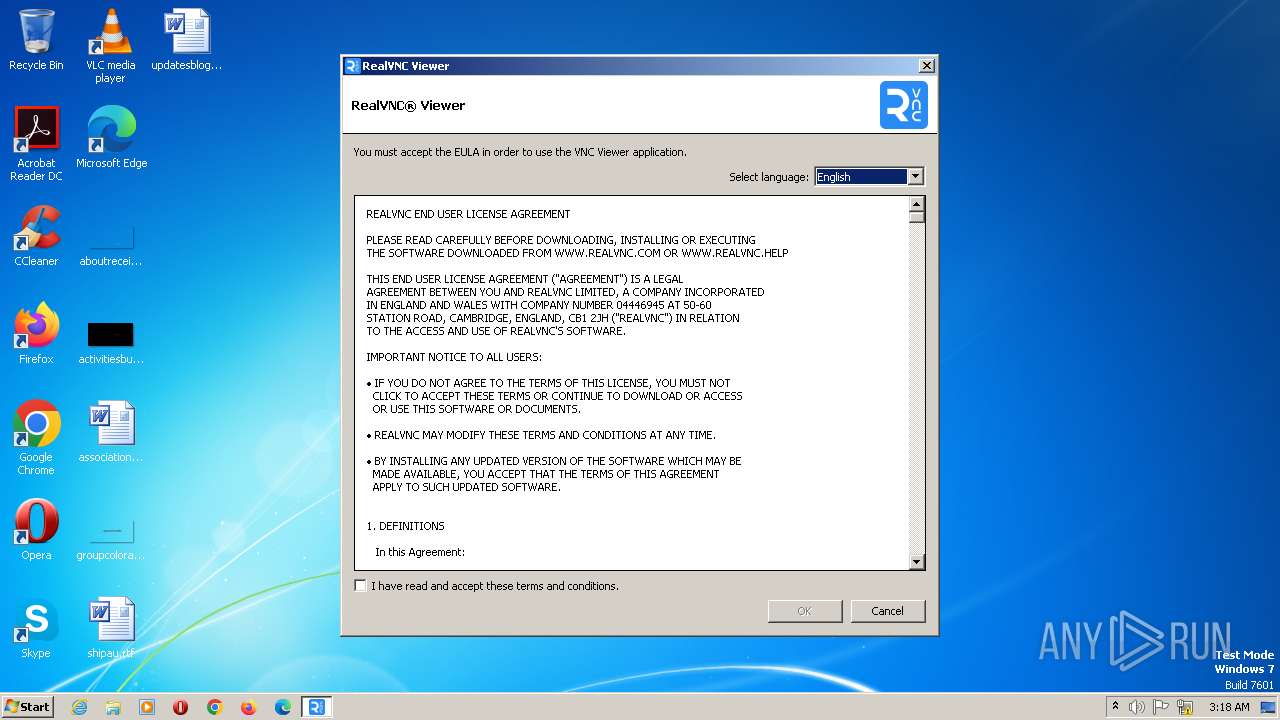
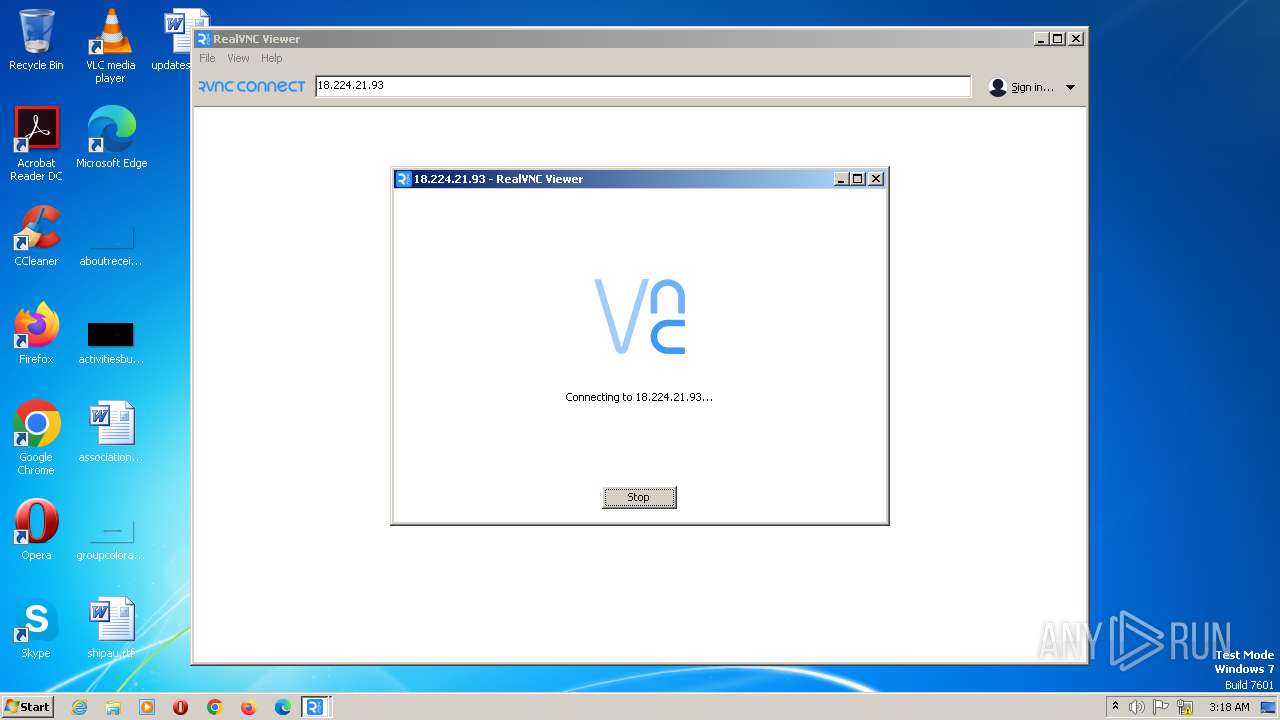
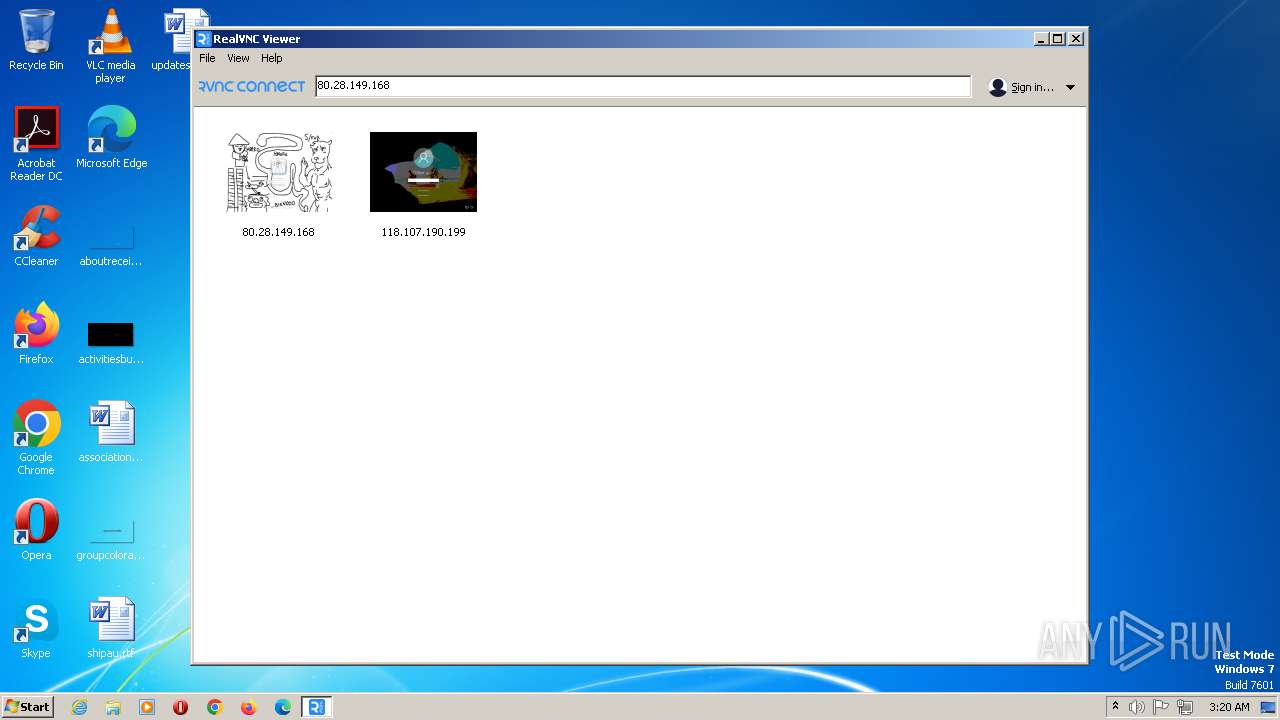
| File name: | VNC-Viewer-7.5.1-Windows-64bit.exe |
| Full analysis: | https://app.any.run/tasks/ce250a80-67d5-4964-9f8c-b9e14a62f564 |
| Verdict: | Malicious activity |
| Analysis date: | August 04, 2023, 03:18:01 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | 5E343F3422E53B115C433250C5AE0B54 |
| SHA1: | 5C002D127BC884C0FB834435A7EBB2B23A0706EE |
| SHA256: | 624AEF6C1ADD55BB540A3C61B581F4008720EAB7478C4711F54E815F457C7FEA |
| SSDEEP: | 196608:HO9sYnLkWzB+irelD+U4PfmzLE2LmFzvpF1V:HOvLrCB+U4PfmzI2LmFzr |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the Internet Settings
- VNC-Viewer-7.5.1-Windows-64bit.exe (PID: 3060)
- VNC-Viewer-7.5.1-Windows-64bit.exe (PID: 2208)
- VNC-Viewer-7.5.1-Windows-64bit.exe (PID: 244)
- VNC-Viewer-7.5.1-Windows-64bit.exe (PID: 1120)
- VNC-Viewer-7.5.1-Windows-64bit.exe (PID: 712)
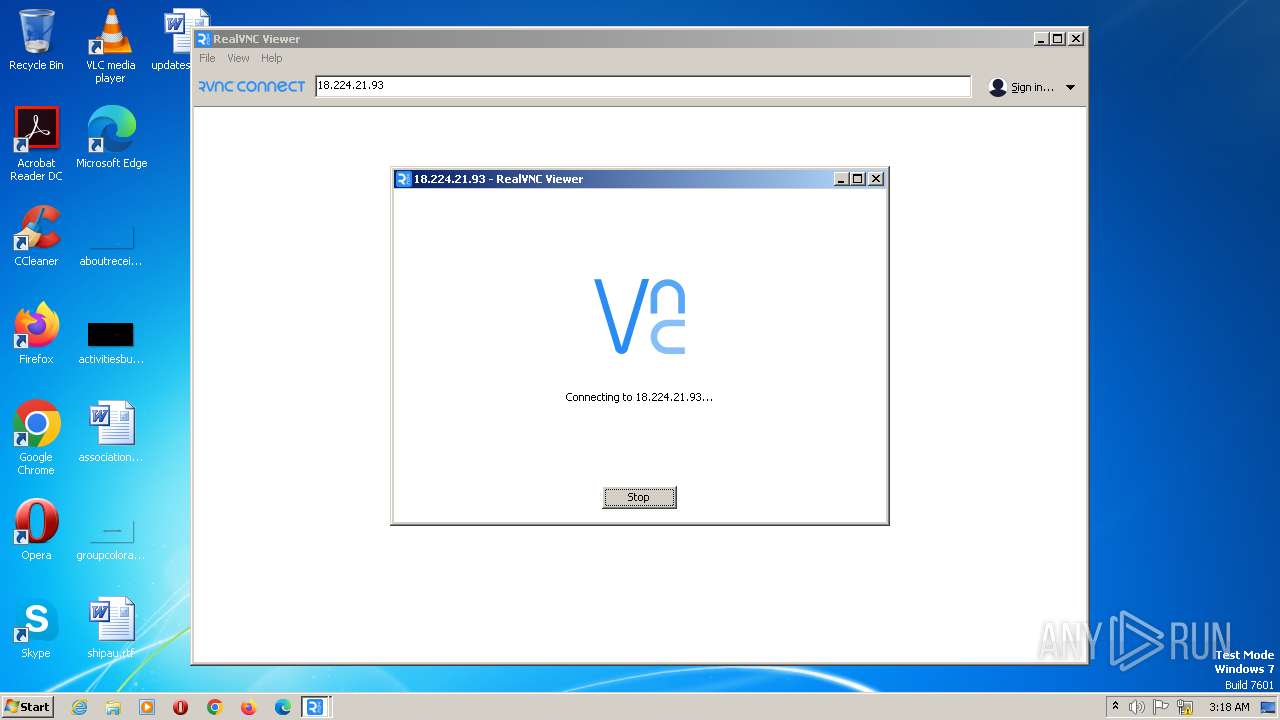
Connects to unusual port
- VNC-Viewer-7.5.1-Windows-64bit.exe (PID: 2208)
- VNC-Viewer-7.5.1-Windows-64bit.exe (PID: 244)
- VNC-Viewer-7.5.1-Windows-64bit.exe (PID: 1120)
- VNC-Viewer-7.5.1-Windows-64bit.exe (PID: 712)
Application launched itself
- VNC-Viewer-7.5.1-Windows-64bit.exe (PID: 3060)
INFO
Reads the computer name
- VNC-Viewer-7.5.1-Windows-64bit.exe (PID: 3060)
- VNC-Viewer-7.5.1-Windows-64bit.exe (PID: 2208)
- VNC-Viewer-7.5.1-Windows-64bit.exe (PID: 1120)
- VNC-Viewer-7.5.1-Windows-64bit.exe (PID: 244)
- VNC-Viewer-7.5.1-Windows-64bit.exe (PID: 712)
The process checks LSA protection
- VNC-Viewer-7.5.1-Windows-64bit.exe (PID: 3060)
- VNC-Viewer-7.5.1-Windows-64bit.exe (PID: 2208)
- VNC-Viewer-7.5.1-Windows-64bit.exe (PID: 1120)
- VNC-Viewer-7.5.1-Windows-64bit.exe (PID: 712)
- VNC-Viewer-7.5.1-Windows-64bit.exe (PID: 244)
Reads the machine GUID from the registry
- VNC-Viewer-7.5.1-Windows-64bit.exe (PID: 2208)
- VNC-Viewer-7.5.1-Windows-64bit.exe (PID: 3060)
- VNC-Viewer-7.5.1-Windows-64bit.exe (PID: 244)
- VNC-Viewer-7.5.1-Windows-64bit.exe (PID: 1120)
- VNC-Viewer-7.5.1-Windows-64bit.exe (PID: 712)
Checks supported languages
- VNC-Viewer-7.5.1-Windows-64bit.exe (PID: 244)
- VNC-Viewer-7.5.1-Windows-64bit.exe (PID: 2208)
- VNC-Viewer-7.5.1-Windows-64bit.exe (PID: 1120)
- VNC-Viewer-7.5.1-Windows-64bit.exe (PID: 3060)
- VNC-Viewer-7.5.1-Windows-64bit.exe (PID: 712)
Creates files or folders in the user directory
- VNC-Viewer-7.5.1-Windows-64bit.exe (PID: 3060)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (18) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (2.9) |
| .exe | | | Generic Win/DOS Executable (1.3) |
| .exe | | | DOS Executable Generic (1.3) |
EXIF
EXE
| ProgramName: | VNC® Viewer |
|---|---|
| ProductVersion: | 7.5.1 (r50075) |
| ProductName: | VNC® |
| OriginalFileName: | vncviewer.exe |
| LegalTrademarks: | RealVNC and VNC are trademarks of RealVNC Ltd and are protected by trademark registrations and/or pending trademark applications in the European Union, United States of America and other jurisdictions. |
| LegalCopyright: | Copyright © RealVNC Ltd. |
| InternalName: | vncviewer |
| FileVersion: | 7.5.1 (r50075) |
| FileDescription: | VNC® Viewer |
| CompanyName: | RealVNC |
| CharacterSet: | Unicode |
| LanguageCode: | English (British) |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Windows NT 32-bit |
| FileFlags: | (none) |
| FileFlagsMask: | 0x003f |
| ProductVersionNumber: | 7.5.1.50075 |
| FileVersionNumber: | 7.5.1.50075 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 6 |
| ImageVersion: | - |
| OSVersion: | 6 |
| EntryPoint: | 0x60a180 |
| UninitializedDataSize: | - |
| InitializedDataSize: | 3786240 |
| CodeSize: | 7127552 |
| LinkerVersion: | 14.16 |
| PEType: | PE32+ |
| ImageFileCharacteristics: | Executable, Large address aware |
| TimeStamp: | 2023:05:30 12:07:58+00:00 |
| MachineType: | AMD AMD64 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_AMD64 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 30-May-2023 12:07:58 |
| Detected languages: |
|
| Debug artifacts: |
|
| CompanyName: | RealVNC |
| FileDescription: | VNC® Viewer |
| FileVersion: | 7.5.1 (r50075) |
| InternalName: | vncviewer |
| LegalCopyright: | Copyright © RealVNC Ltd. |
| LegalTrademarks: | RealVNC and VNC are trademarks of RealVNC Ltd and are protected by trademark registrations and/or pending trademark applications in the European Union, United States of America and other jurisdictions. |
| OriginalFilename: | vncviewer.exe |
| ProductName: | VNC® |
| ProductVersion: | 7.5.1 (r50075) |
| ProgramName: | VNC® Viewer |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000138 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_AMD64 |
| Number of sections: | 8 |
| Time date stamp: | 30-May-2023 12:07:58 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00F0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x006CC0CC | 0x006CC200 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.49397 |
.rdata | 0x006CE000 | 0x002A3890 | 0x002A3A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.51998 |
.data | 0x00972000 | 0x0002A7B0 | 0x00018A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.57193 |
.pdata | 0x0099D000 | 0x00052DA0 | 0x00052E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.54842 |
.rodata | 0x009F0000 | 0x00000890 | 0x00000A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 3.81285 |
.gehcont( | 0x009F1000 | 0x00000028 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 0.203682 |
.rsrc | 0x009F2000 | 0x00080EB0 | 0x00081000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.05178 |
.reloc | 0x00A73000 | 0x0000B7C8 | 0x0000B800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 5.46526 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.19874 | 1678 | Latin 1 / Western European | English - United States | RT_MANIFEST |
2 | 4.65517 | 1128 | Latin 1 / Western European | English - United States | RT_ICON |
3 | 4.17421 | 4264 | Latin 1 / Western European | English - United States | RT_ICON |
4 | 3.9793 | 4264 | Latin 1 / Western European | English - United States | RT_ICON |
5 | 3.68509 | 9640 | Latin 1 / Western European | English - United States | RT_ICON |
6 | 3.48661 | 9640 | Latin 1 / Western European | English - United States | RT_ICON |
7 | 7.94883 | 10622 | Latin 1 / Western European | English - United States | RT_ICON |
ADDRESSBOOK_2X.PNG | 5.794 | 177 | Latin 1 / Western European | English - United States | BUILTINRESOURCE |
ADDRESSBOOK_SEL_2X.PNG | 5.62152 | 177 | Latin 1 / Western European | English - United States | BUILTINRESOURCE |
ANNOTATEOFF.PNG | 7.46722 | 985 | Latin 1 / Western European | English - United States | BUILTINRESOURCE |
Imports
ADVAPI32.dll |
COMCTL32.dll |
COMDLG32.dll |
CRYPT32.dll |
GDI32.dll |
IMM32.dll |
KERNEL32.dll |
OLEAUT32.dll |
SHELL32.dll |
USER32.dll |
Total processes
34
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
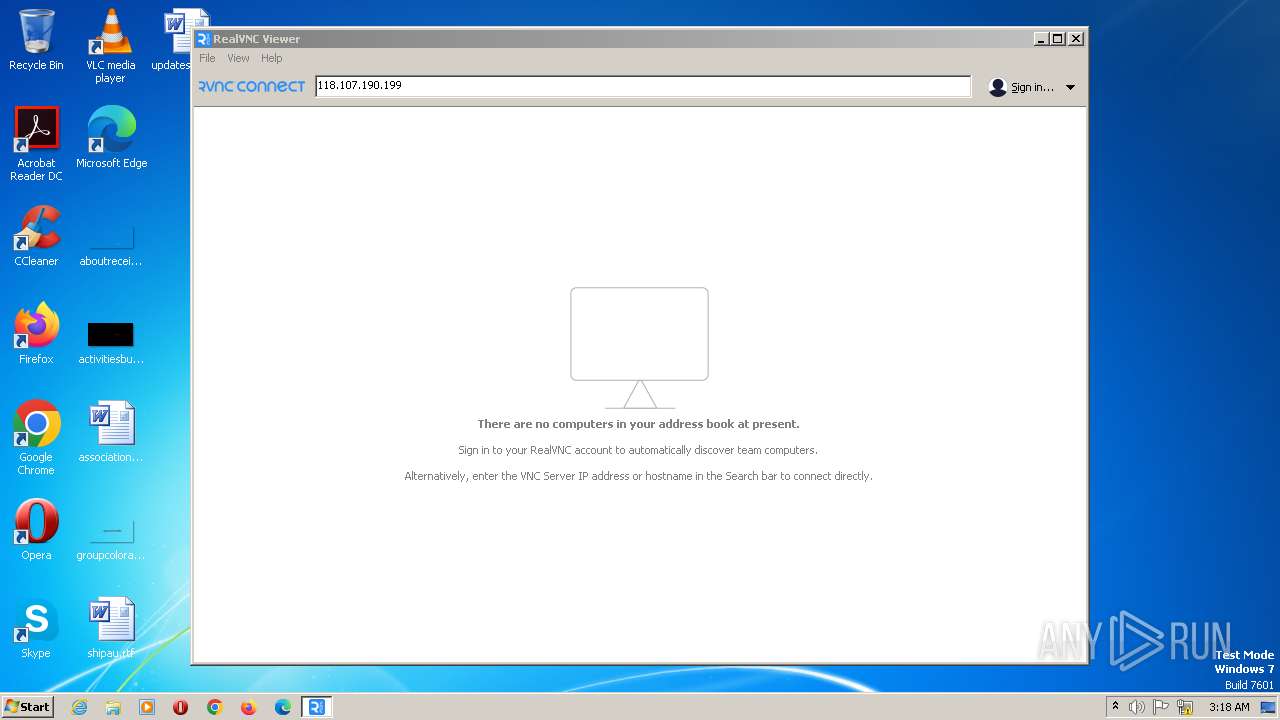
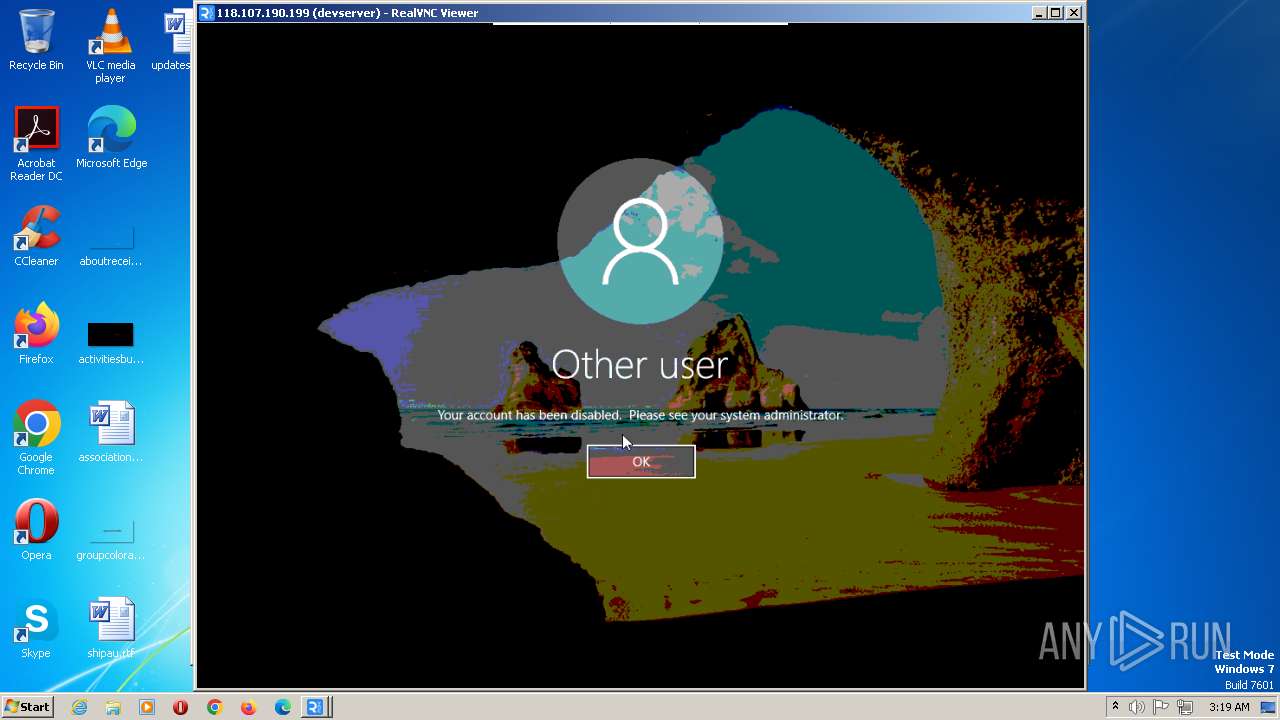
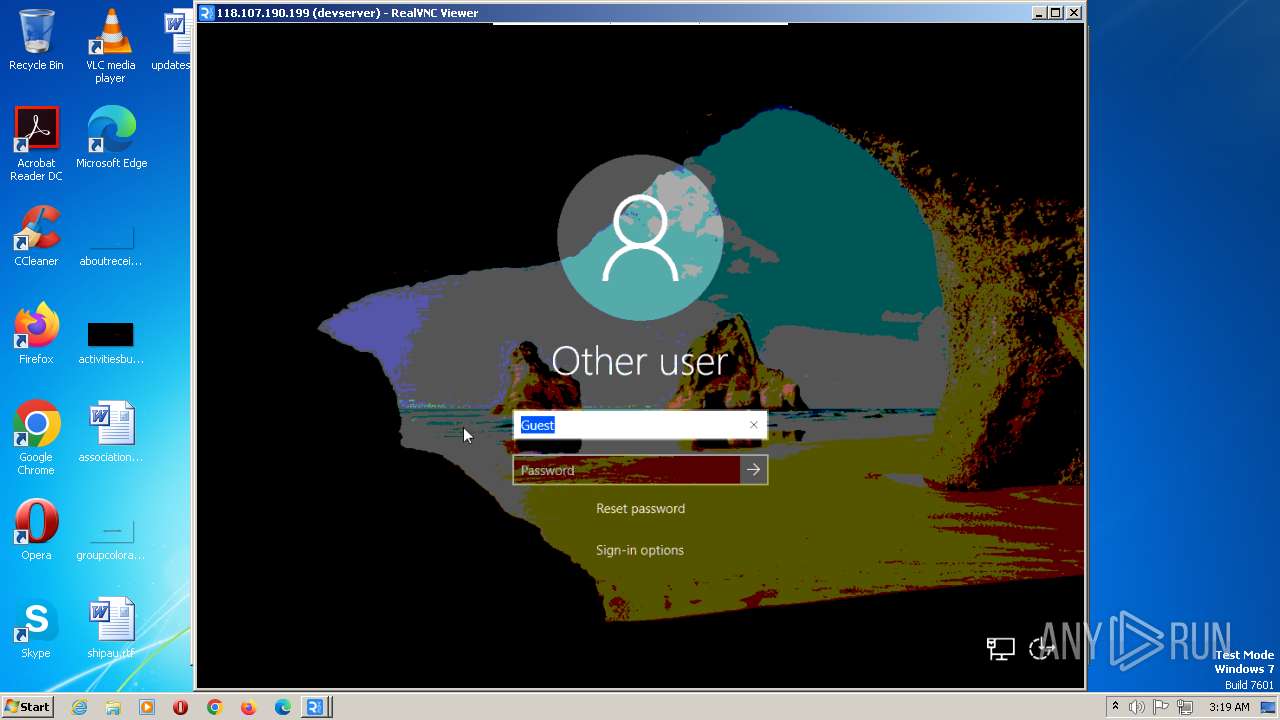
| 244 | C:\Users\admin\AppData\Roaming\VNC-Viewer-7.5.1-Windows-64bit.exe -child 118.107.190.199 -hash f9240995d5c0c81a7665b11606c491b1ecfc6ed848225610becdc707197a73ad -sid S-1-5-21-3896776584-4254864009-862391680-1000 RealVNC.admin.vncviewer.launchpipe.1545172113 | C:\Users\admin\AppData\Roaming\VNC-Viewer-7.5.1-Windows-64bit.exe | VNC-Viewer-7.5.1-Windows-64bit.exe | ||||||||||||
User: admin Company: RealVNC Integrity Level: MEDIUM Description: VNC® Viewer Exit code: 0 Version: 7.5.1 (r50075) Modules
| |||||||||||||||
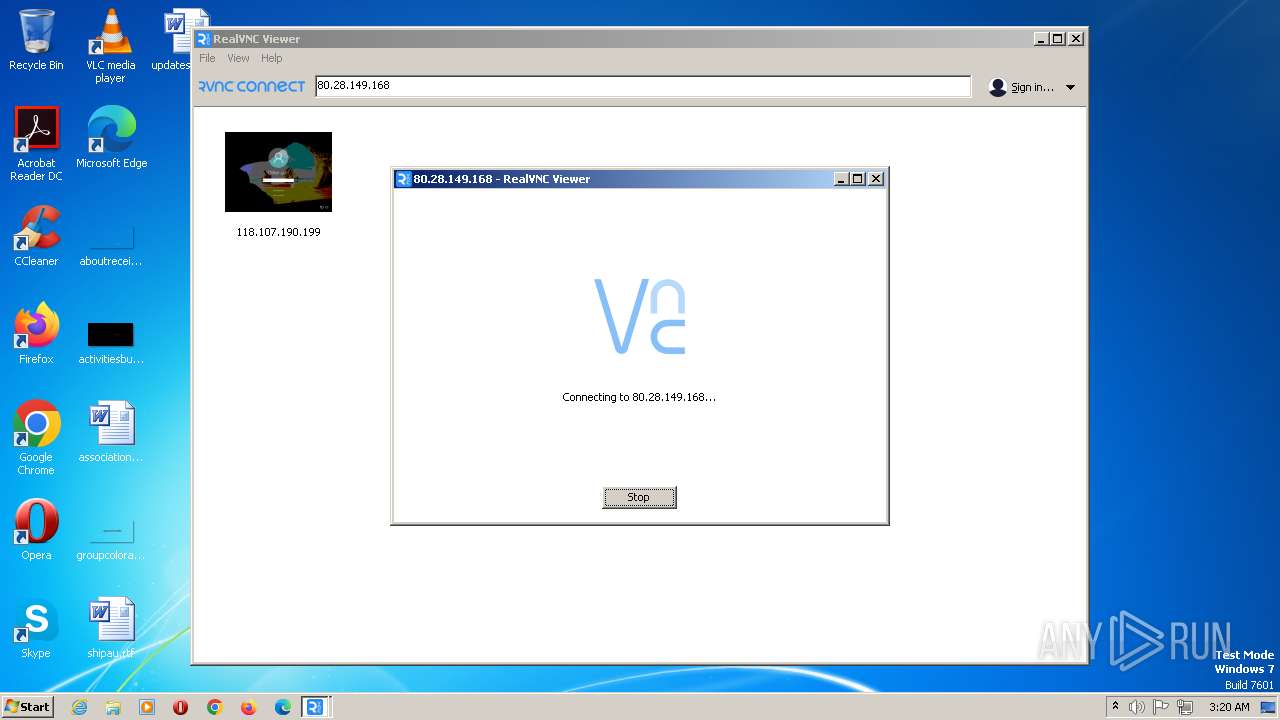
| 712 | C:\Users\admin\AppData\Roaming\VNC-Viewer-7.5.1-Windows-64bit.exe -child 80.28.149.168 -hash 918a4de029d4095b1f16b6a78b5851394229248077089e94fd5adf00c07bf3b6 -sid S-1-5-21-3896776584-4254864009-862391680-1000 RealVNC.admin.vncviewer.launchpipe.3689056748 | C:\Users\admin\AppData\Roaming\VNC-Viewer-7.5.1-Windows-64bit.exe | VNC-Viewer-7.5.1-Windows-64bit.exe | ||||||||||||
User: admin Company: RealVNC Integrity Level: MEDIUM Description: VNC® Viewer Exit code: 0 Version: 7.5.1 (r50075) Modules
| |||||||||||||||
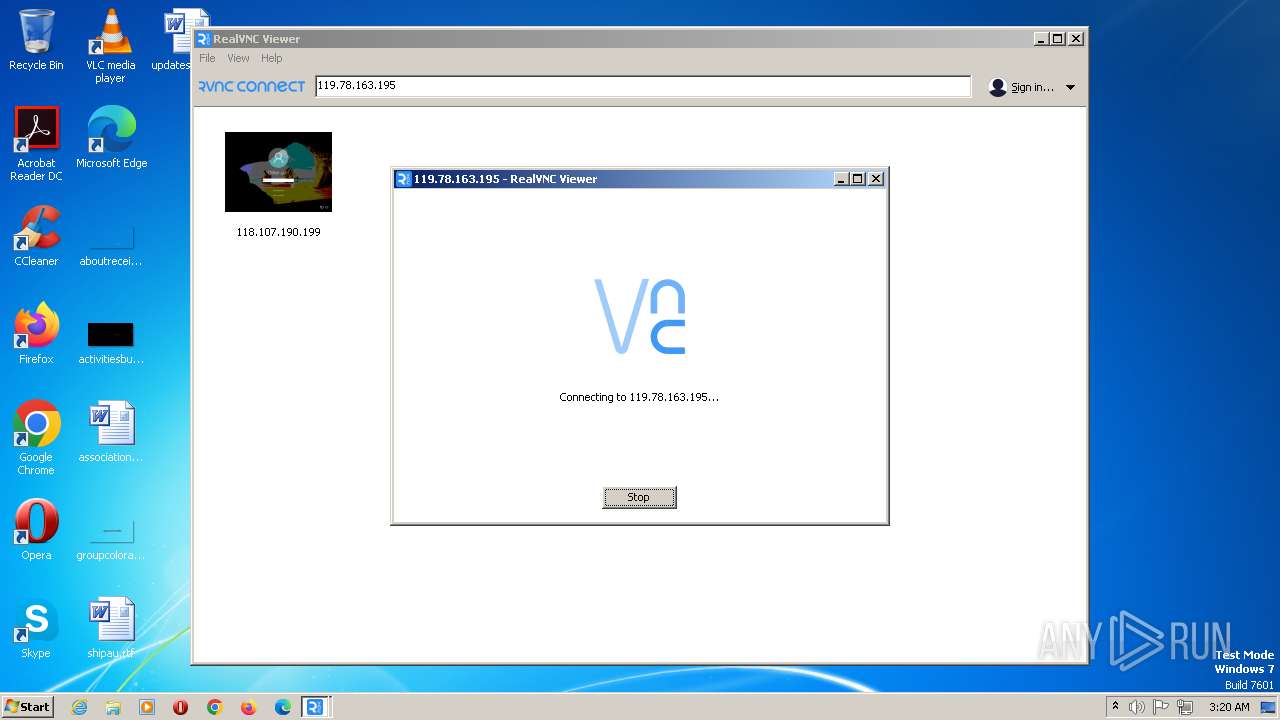
| 1120 | C:\Users\admin\AppData\Roaming\VNC-Viewer-7.5.1-Windows-64bit.exe -child 119.78.163.195 -hash 392aa2057242eec11d2661934d02fecbd620c0ee8c80b8823469c560fc3fb650 -sid S-1-5-21-3896776584-4254864009-862391680-1000 RealVNC.admin.vncviewer.launchpipe.1382060758 | C:\Users\admin\AppData\Roaming\VNC-Viewer-7.5.1-Windows-64bit.exe | VNC-Viewer-7.5.1-Windows-64bit.exe | ||||||||||||
User: admin Company: RealVNC Integrity Level: MEDIUM Description: VNC® Viewer Exit code: 0 Version: 7.5.1 (r50075) Modules
| |||||||||||||||
| 2208 | C:\Users\admin\AppData\Roaming\VNC-Viewer-7.5.1-Windows-64bit.exe -child 18.224.21.93 -hash 9a8aa714e58b05c9ff23db8ecddc1086a08321f9e6c2d9d0b842c47839dbbd3c -sid S-1-5-21-3896776584-4254864009-862391680-1000 RealVNC.admin.vncviewer.launchpipe.3755501234 | C:\Users\admin\AppData\Roaming\VNC-Viewer-7.5.1-Windows-64bit.exe | VNC-Viewer-7.5.1-Windows-64bit.exe | ||||||||||||
User: admin Company: RealVNC Integrity Level: MEDIUM Description: VNC® Viewer Exit code: 0 Version: 7.5.1 (r50075) Modules
| |||||||||||||||
| 3060 | "C:\Users\admin\AppData\Roaming\VNC-Viewer-7.5.1-Windows-64bit.exe" | C:\Users\admin\AppData\Roaming\VNC-Viewer-7.5.1-Windows-64bit.exe | explorer.exe | ||||||||||||
User: admin Company: RealVNC Integrity Level: MEDIUM Description: VNC® Viewer Exit code: 0 Version: 7.5.1 (r50075) Modules
| |||||||||||||||
Total events
2 431
Read events
2 424
Write events
7
Delete events
0
Modification events
| (PID) Process: | (2208) VNC-Viewer-7.5.1-Windows-64bit.exe | Key: | HKEY_CURRENT_USER\Software\RealVNC\vncviewer |
| Operation: | write | Name: | _AnlInclRate |
Value: 0.0025 | |||
| (PID) Process: | (244) VNC-Viewer-7.5.1-Windows-64bit.exe | Key: | HKEY_CURRENT_USER\Software\RealVNC\vncviewer |
| Operation: | write | Name: | _AnlInclRate |
Value: 0.0025 | |||
| (PID) Process: | (1120) VNC-Viewer-7.5.1-Windows-64bit.exe | Key: | HKEY_CURRENT_USER\Software\RealVNC\vncviewer |
| Operation: | write | Name: | _AnlInclRate |
Value: 0.0025 | |||
| (PID) Process: | (712) VNC-Viewer-7.5.1-Windows-64bit.exe | Key: | HKEY_CURRENT_USER\Software\RealVNC\vncviewer |
| Operation: | write | Name: | _AnlInclRate |
Value: 0.0025 | |||
| (PID) Process: | (712) VNC-Viewer-7.5.1-Windows-64bit.exe | Key: | HKEY_CURRENT_USER\Software\RealVNC\vncviewer\KnownHosts |
| Operation: | write | Name: | 80.28.149.168::5900/extra |
Value: 0100 | |||
Executable files
0
Suspicious files
6
Text files
13
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3060 | VNC-Viewer-7.5.1-Windows-64bit.exe | C:\Users\admin\AppData\Local\RealVNC\vncviewer.log | text | |
MD5:C326F6A426484EB651DB8ADCF70830A1 | SHA256:EE52DABA4CDC526843C250E6C2BD29A5DC8AF8762B98D0975CCF1B6E70AD8045 | |||
| 3060 | VNC-Viewer-7.5.1-Windows-64bit.exe | C:\Users\admin\AppData\Roaming\RealVNC\ViewerStore\d74b787a-02d5-4711-baec-fc2ce83ba2ee.jrle | binary | |
MD5:16CA765E70A1D96350466367DCD8973E | SHA256:CF4EE8DCA7960344CB79888F9F0D7080FF00D42BD64AC50939B40131F37F1AA4 | |||
| 3060 | VNC-Viewer-7.5.1-Windows-64bit.exe | C:\Users\admin\AppData\Roaming\RealVNC\ViewerStore\d74b787a-02d5-4711-baec-fc2ce83ba2ee.vnc | text | |
MD5:74C064B74A5B33FF37423C7A838B5720 | SHA256:0E1550AFAF5A0D6AA6C7D7941B7A7A678950D7877B63F7DBF39B53DF2FE0EB51 | |||
| 3060 | VNC-Viewer-7.5.1-Windows-64bit.exe | C:\Users\admin\AppData\Roaming\RealVNC\ViewerStore\d237f3a9-7079-44eb-8ef8-6c3f05c5822f.vnc.tmp | text | |
MD5:C57E4A1D9A24F6E2D232720446F97C64 | SHA256:25F1501A3406F33FA3F89E6922FA1AB1458EE782C578067A50CF05FC5B5068E7 | |||
| 3060 | VNC-Viewer-7.5.1-Windows-64bit.exe | C:\Users\admin\AppData\Roaming\RealVNC\ViewerStore\d74b787a-02d5-4711-baec-fc2ce83ba2ee.vnc.tmp | text | |
MD5:74C064B74A5B33FF37423C7A838B5720 | SHA256:0E1550AFAF5A0D6AA6C7D7941B7A7A678950D7877B63F7DBF39B53DF2FE0EB51 | |||
| 3060 | VNC-Viewer-7.5.1-Windows-64bit.exe | C:\Users\admin\AppData\Local\RealVNC\vncviewer.d\BootstrapCache.pkg | binary | |
MD5:386BCE9FBA12D1C299E208CAE647366A | SHA256:E69EF971F2698196F7181672AC39D315DBD57418A32BA9E1747E4A384744C4D7 | |||
| 3060 | VNC-Viewer-7.5.1-Windows-64bit.exe | C:\Users\admin\AppData\Local\RealVNC\vncviewer.d\BootstrapCache.pkg.tmp | binary | |
MD5:386BCE9FBA12D1C299E208CAE647366A | SHA256:E69EF971F2698196F7181672AC39D315DBD57418A32BA9E1747E4A384744C4D7 | |||
| 3060 | VNC-Viewer-7.5.1-Windows-64bit.exe | C:\Users\admin\AppData\Roaming\RealVNC\ViewerStore\d237f3a9-7079-44eb-8ef8-6c3f05c5822f.vnc | text | |
MD5:C57E4A1D9A24F6E2D232720446F97C64 | SHA256:25F1501A3406F33FA3F89E6922FA1AB1458EE782C578067A50CF05FC5B5068E7 | |||
| 3060 | VNC-Viewer-7.5.1-Windows-64bit.exe | C:\Users\admin\AppData\Roaming\RealVNC\ViewerStore\d237f3a9-7079-44eb-8ef8-6c3f05c5822f.jrle | binary | |
MD5:95F1AD49FCA009CDE618E3AA906275CA | SHA256:AB6DD3C1F0727A65A6FF9ACFB4BBF3E4D18E052EDE8002F8569939F0C7001E2F | |||
| 3060 | VNC-Viewer-7.5.1-Windows-64bit.exe | C:\Users\admin\AppData\Roaming\RealVNC\ViewerStore\d237f3a9-7079-44eb-8ef8-6c3f05c5822f.jrle.tmp | binary | |
MD5:95F1AD49FCA009CDE618E3AA906275CA | SHA256:AB6DD3C1F0727A65A6FF9ACFB4BBF3E4D18E052EDE8002F8569939F0C7001E2F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
17
DNS requests
2
Threats
3
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
328 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3060 | VNC-Viewer-7.5.1-Windows-64bit.exe | 165.254.191.229:443 | hb-c.services.vnc.com | NTT-LTD-2914 | US | unknown |
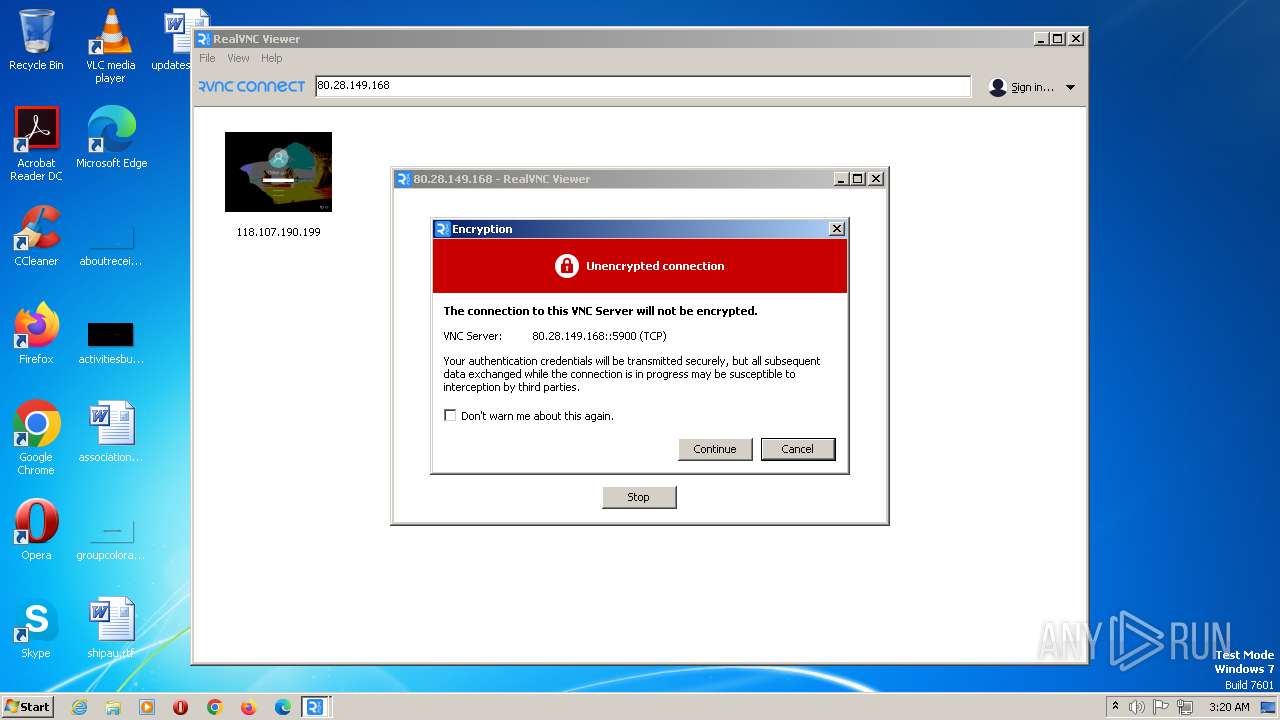
712 | VNC-Viewer-7.5.1-Windows-64bit.exe | 80.28.149.168:5900 | — | — | — | suspicious |
1120 | VNC-Viewer-7.5.1-Windows-64bit.exe | 119.78.163.195:5900 | — | — | — | unknown |
2208 | VNC-Viewer-7.5.1-Windows-64bit.exe | 18.224.21.93:5900 | — | — | — | unknown |
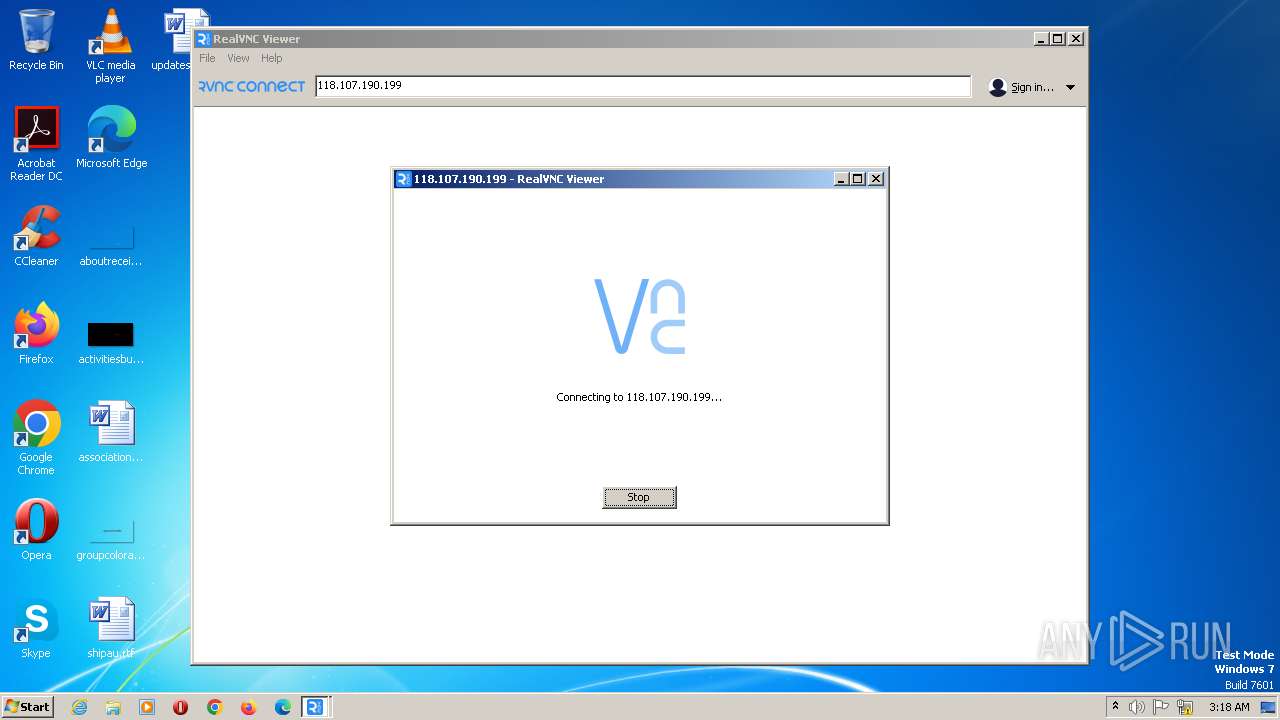
244 | VNC-Viewer-7.5.1-Windows-64bit.exe | 118.107.190.199:5900 | — | — | — | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
hb-c.services.vnc.com |
| unknown |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
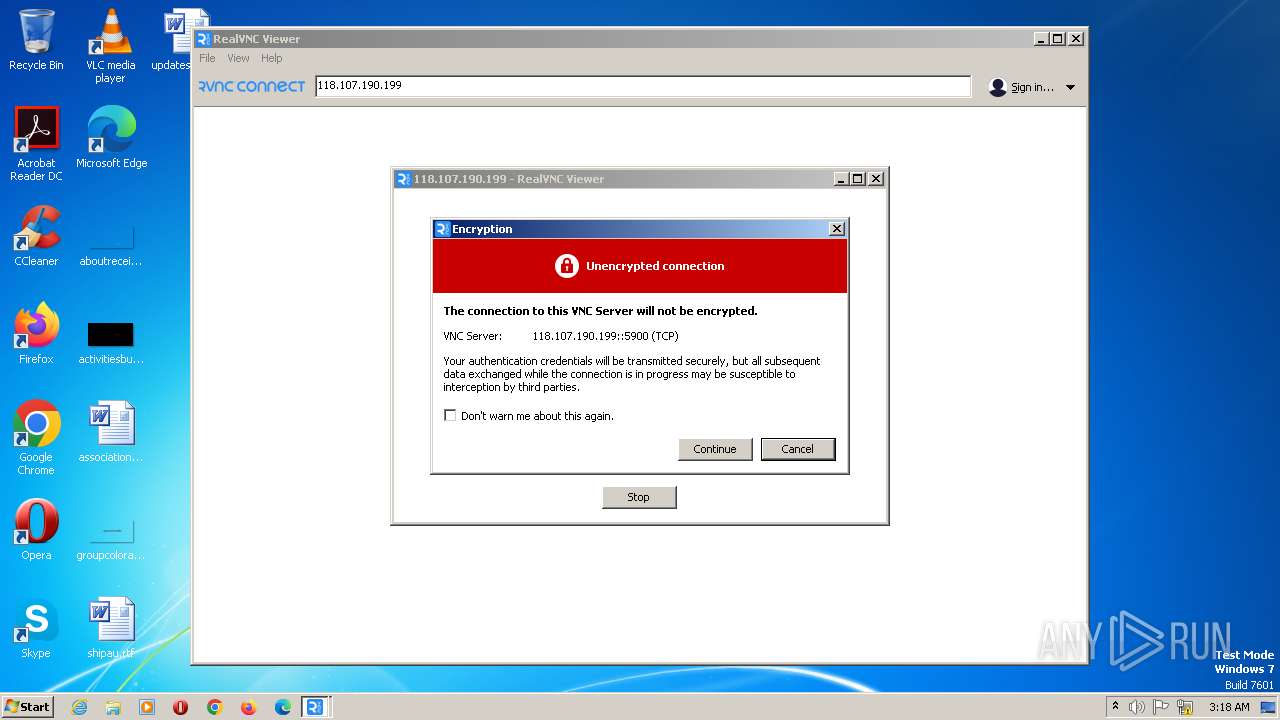
244 | VNC-Viewer-7.5.1-Windows-64bit.exe | Potential Corporate Privacy Violation | SUSPICIOUS [ANY.RUN] VNC negotiation was detected (ProtocolVersion message) |
712 | VNC-Viewer-7.5.1-Windows-64bit.exe | Potential Corporate Privacy Violation | SUSPICIOUS [ANY.RUN] VNC negotiation was detected (Server Security type - None) |
1 ETPRO signatures available at the full report