| URL: | recipelister.com |
| Full analysis: | https://app.any.run/tasks/ecf6b239-5405-47c8-849e-2235d530c298 |
| Verdict: | Malicious activity |
| Analysis date: | May 27, 2025, 19:50:01 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MD5: | F154E393EA8A5A105D972C66FE65DACA |
| SHA1: | D7787F11559B38FDFBF2D45C1EB3ED61EEC7033C |
| SHA256: | 623D191DCED7BF2FED9E5239F77A5D0CFE1766E8EDCF46A1CE86E40B1B702CE7 |
| SSDEEP: | 3:wtHpI:Sm |
MALICIOUS
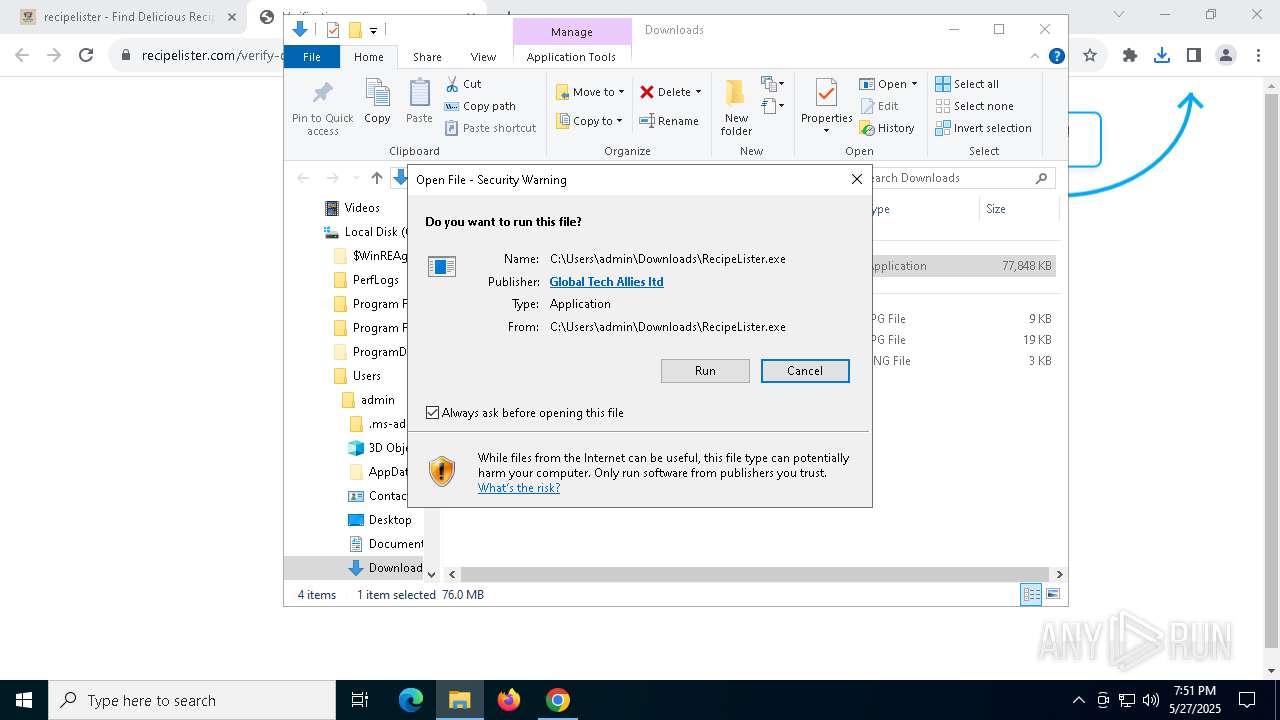
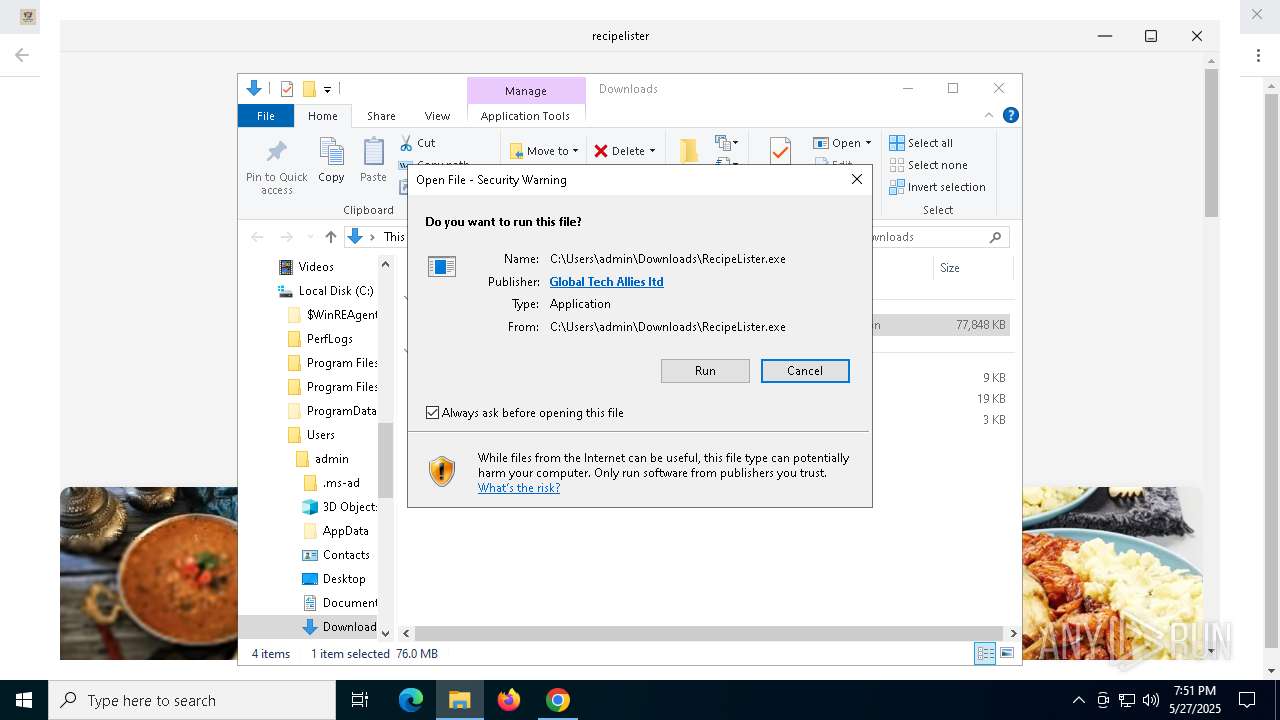
Executing a file with an untrusted certificate
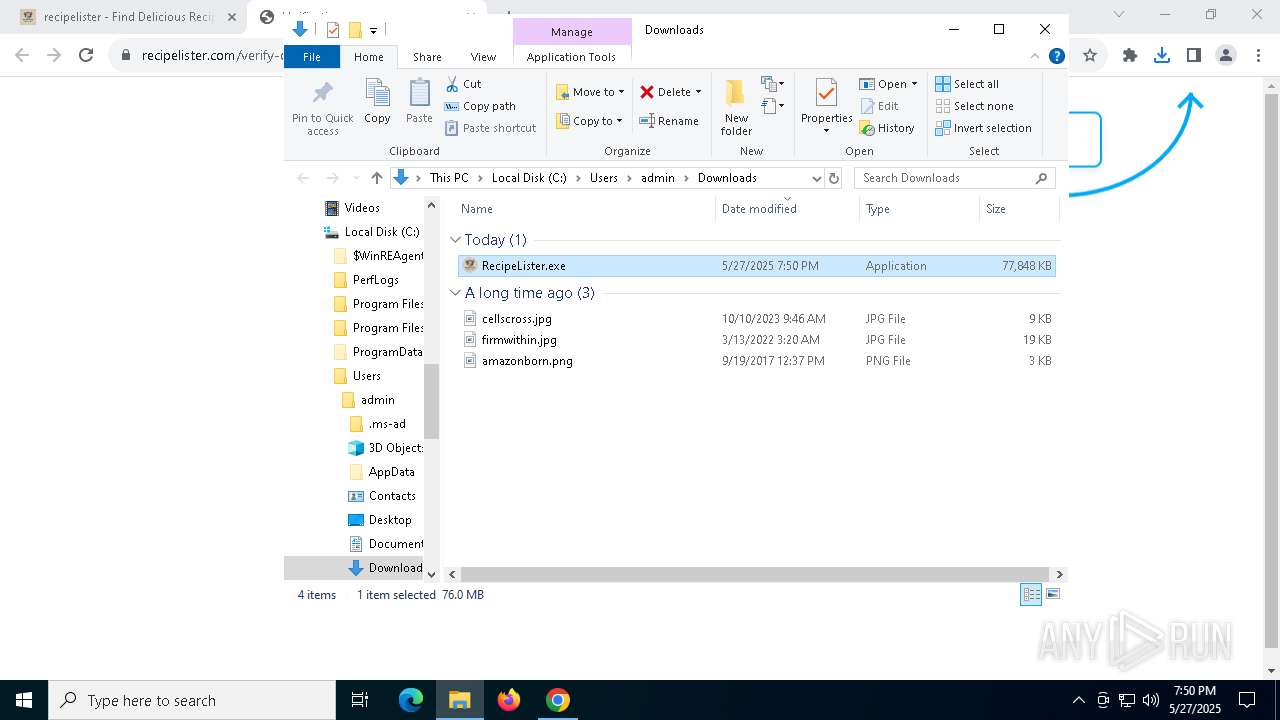
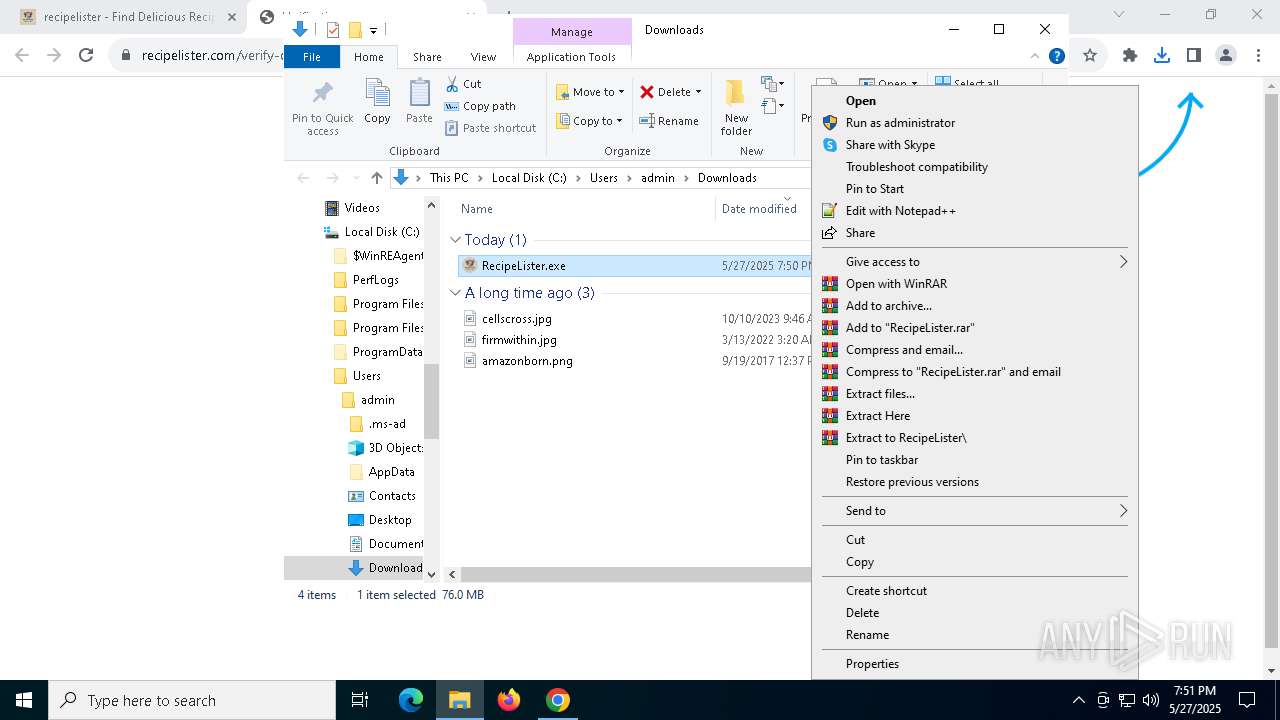
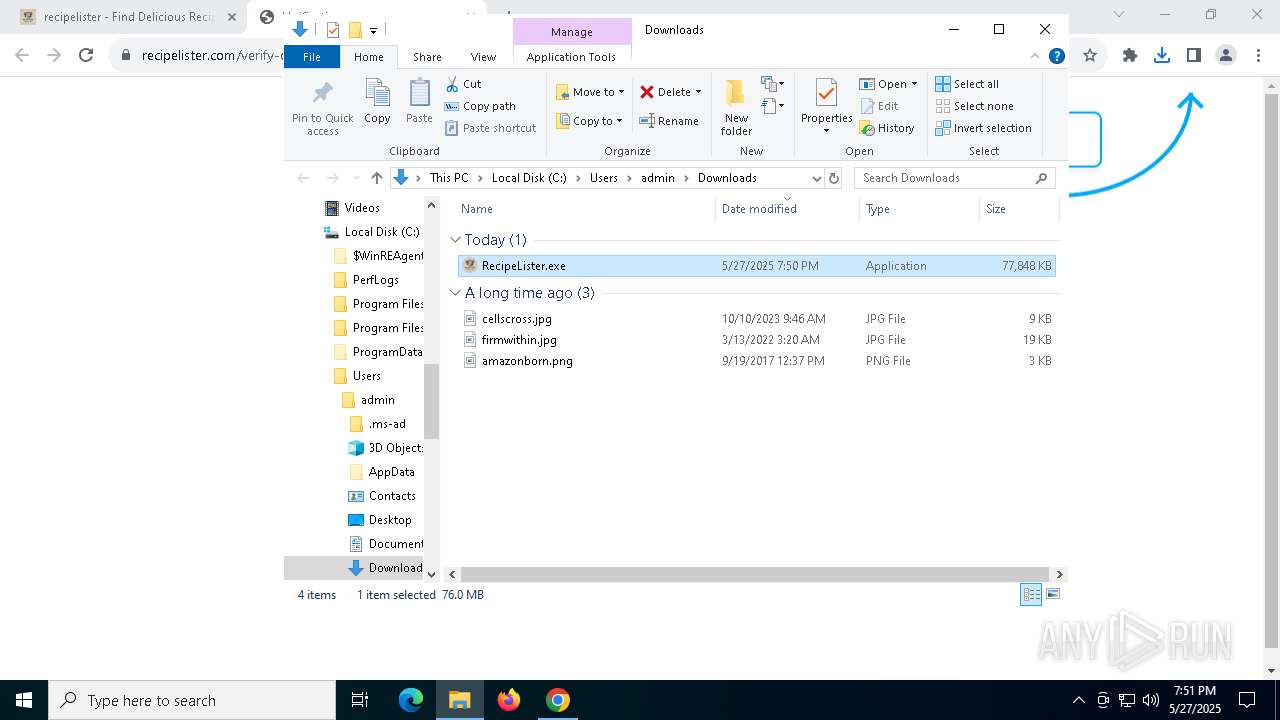
- RecipeLister.exe (PID: 2568)
- RecipeLister.exe (PID: 856)
SUSPICIOUS
Creates file in the systems drive root
- explorer.exe (PID: 5492)
Malware-specific behavior (creating "System.dll" in Temp)
- RecipeLister.exe (PID: 2568)
- RecipeLister.exe (PID: 856)
The process creates files with name similar to system file names
- RecipeLister.exe (PID: 2568)
- RecipeLister.exe (PID: 856)
Drops 7-zip archiver for unpacking
- RecipeLister.exe (PID: 2568)
- RecipeLister.exe (PID: 856)
Executable content was dropped or overwritten
- RecipeLister.exe (PID: 2568)
- RecipeLister.exe (PID: 856)
Reads security settings of Internet Explorer
- RecipeLister.exe (PID: 2568)
- RecipeLister.exe (PID: 856)
- Recipe Finder - Recipe Lister.exe (PID: 5304)
Process drops legitimate windows executable
- RecipeLister.exe (PID: 856)
- RecipeLister.exe (PID: 2568)
Application launched itself
- Recipe Finder - Recipe Lister.exe (PID: 5304)
Sets XML DOM element text (SCRIPT)
- Recipe Finder - Recipe Lister.exe (PID: 5304)
INFO
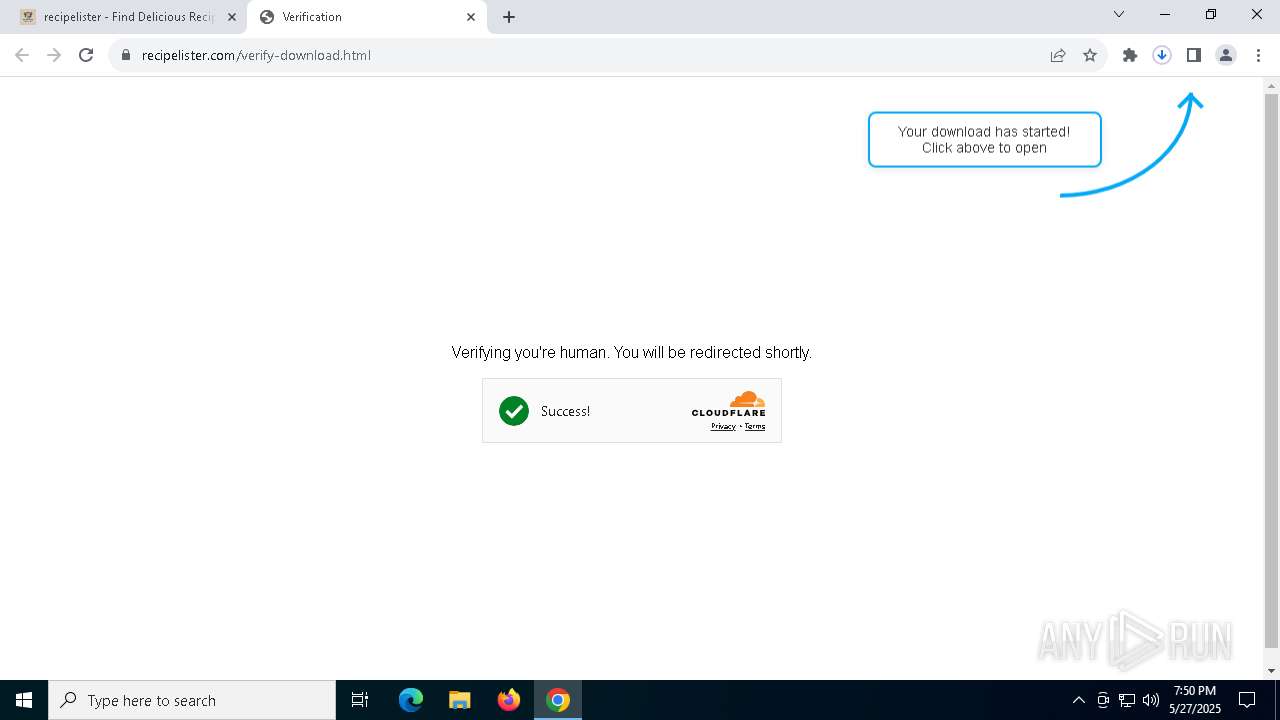
Launch of the file from Downloads directory
- chrome.exe (PID: 8128)
Executable content was dropped or overwritten
- chrome.exe (PID: 5960)
Reads the software policy settings
- explorer.exe (PID: 5492)
- slui.exe (PID: 7836)
Creates files or folders in the user directory
- explorer.exe (PID: 5492)
- Recipe Finder - Recipe Lister.exe (PID: 5304)
- Recipe Finder - Recipe Lister.exe (PID: 8056)
Reads security settings of Internet Explorer
- explorer.exe (PID: 5492)
Checks proxy server information
- explorer.exe (PID: 5492)
- Recipe Finder - Recipe Lister.exe (PID: 5304)
Checks supported languages
- RecipeLister.exe (PID: 2568)
- Recipe Finder - Recipe Lister.exe (PID: 5304)
- Recipe Finder - Recipe Lister.exe (PID: 8056)
- Recipe Finder - Recipe Lister.exe (PID: 3300)
- Recipe Finder - Recipe Lister.exe (PID: 5452)
- Recipe Finder - Recipe Lister.exe (PID: 4528)
- Recipe Finder - Recipe Lister.exe (PID: 6264)
- RecipeLister.exe (PID: 856)
Application launched itself
- chrome.exe (PID: 5960)
Create files in a temporary directory
- RecipeLister.exe (PID: 2568)
- RecipeLister.exe (PID: 856)
- Recipe Finder - Recipe Lister.exe (PID: 5304)
The sample compiled with english language support
- RecipeLister.exe (PID: 2568)
- RecipeLister.exe (PID: 856)
Reads the computer name
- RecipeLister.exe (PID: 856)
- Recipe Finder - Recipe Lister.exe (PID: 5304)
- Recipe Finder - Recipe Lister.exe (PID: 4528)
- Recipe Finder - Recipe Lister.exe (PID: 8056)
- RecipeLister.exe (PID: 2568)
Reads Environment values
- Recipe Finder - Recipe Lister.exe (PID: 5304)
Reads product name
- Recipe Finder - Recipe Lister.exe (PID: 5304)
Process checks computer location settings
- Recipe Finder - Recipe Lister.exe (PID: 5452)
- Recipe Finder - Recipe Lister.exe (PID: 5304)
- Recipe Finder - Recipe Lister.exe (PID: 3300)
- Recipe Finder - Recipe Lister.exe (PID: 6264)
Reads the machine GUID from the registry
- Recipe Finder - Recipe Lister.exe (PID: 5304)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
162
Monitored processes
30
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 664 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=3484 --field-trial-handle=1916,i,15872769774542169465,9738570700990531626,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 856 | "C:\Users\admin\Downloads\RecipeLister.exe" | C:\Users\admin\Downloads\RecipeLister.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Recipe finder app powered by recipelister.com Version: 1.0.0 Modules
| |||||||||||||||
| 2568 | "C:\Users\admin\Downloads\RecipeLister.exe" | C:\Users\admin\Downloads\RecipeLister.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Recipe finder app powered by recipelister.com Exit code: 1 Version: 1.0.0 Modules
| |||||||||||||||
| 3020 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=122.0.6261.70 --initial-client-data=0x21c,0x220,0x224,0x1f8,0x228,0x7ffc88eedc40,0x7ffc88eedc4c,0x7ffc88eedc58 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 3300 | "C:\Users\admin\AppData\Local\Temp\2w1rXpxZnwDUwuTeNvdD6FUkeI0\Recipe Finder - Recipe Lister.exe" --type=renderer --user-data-dir="C:\Users\admin\AppData\Roaming\recipe-finder" --app-path="C:\Users\admin\AppData\Local\Temp\2w1rXpxZnwDUwuTeNvdD6FUkeI0\resources\app.asar" --no-sandbox --no-zygote --first-renderer-process --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=4 --mojo-platform-channel-handle=2860 --field-trial-handle=1300,i,4957410836596604084,3657026138914628198,262144 --enable-features=kWebSQLAccess --disable-features=SpareRendererForSitePerProcess,WinDelaySpellcheckServiceInit,WinRetrieveSuggestionsOnlyOnDemand --variations-seed-version /prefetch:1 | C:\Users\admin\AppData\Local\Temp\2w1rXpxZnwDUwuTeNvdD6FUkeI0\Recipe Finder - Recipe Lister.exe | — | Recipe Finder - Recipe Lister.exe | |||||||||||
User: admin Company: GitHub, Inc. Integrity Level: HIGH Description: Recipe Finder - Recipe Lister Version: 1.0.0 Modules
| |||||||||||||||
| 3968 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5068 --field-trial-handle=1916,i,15872769774542169465,9738570700990531626,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 4528 | "C:\Users\admin\AppData\Local\Temp\2w1rXpxZnwDUwuTeNvdD6FUkeI0\Recipe Finder - Recipe Lister.exe" --type=gpu-process --user-data-dir="C:\Users\admin\AppData\Roaming\recipe-finder" --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=1676 --field-trial-handle=1300,i,4957410836596604084,3657026138914628198,262144 --enable-features=kWebSQLAccess --disable-features=SpareRendererForSitePerProcess,WinDelaySpellcheckServiceInit,WinRetrieveSuggestionsOnlyOnDemand --variations-seed-version /prefetch:2 | C:\Users\admin\AppData\Local\Temp\2w1rXpxZnwDUwuTeNvdD6FUkeI0\Recipe Finder - Recipe Lister.exe | — | Recipe Finder - Recipe Lister.exe | |||||||||||
User: admin Company: GitHub, Inc. Integrity Level: LOW Description: Recipe Finder - Recipe Lister Version: 1.0.0 Modules
| |||||||||||||||
| 5304 | "C:\Users\admin\AppData\Local\Temp\2w1rXpxZnwDUwuTeNvdD6FUkeI0\Recipe Finder - Recipe Lister.exe" | C:\Users\admin\AppData\Local\Temp\2w1rXpxZnwDUwuTeNvdD6FUkeI0\Recipe Finder - Recipe Lister.exe | — | RecipeLister.exe | |||||||||||
User: admin Company: GitHub, Inc. Integrity Level: HIGH Description: Recipe Finder - Recipe Lister Version: 1.0.0 Modules
| |||||||||||||||
| 5452 | "C:\Users\admin\AppData\Local\Temp\2w1rXpxZnwDUwuTeNvdD6FUkeI0\Recipe Finder - Recipe Lister.exe" --type=renderer --user-data-dir="C:\Users\admin\AppData\Roaming\recipe-finder" --app-path="C:\Users\admin\AppData\Local\Temp\2w1rXpxZnwDUwuTeNvdD6FUkeI0\resources\app.asar" --enable-sandbox --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3240 --field-trial-handle=1300,i,4957410836596604084,3657026138914628198,262144 --enable-features=kWebSQLAccess --disable-features=SpareRendererForSitePerProcess,WinDelaySpellcheckServiceInit,WinRetrieveSuggestionsOnlyOnDemand --variations-seed-version /prefetch:1 | C:\Users\admin\AppData\Local\Temp\2w1rXpxZnwDUwuTeNvdD6FUkeI0\Recipe Finder - Recipe Lister.exe | — | Recipe Finder - Recipe Lister.exe | |||||||||||
User: admin Company: GitHub, Inc. Integrity Level: LOW Description: Recipe Finder - Recipe Lister Version: 1.0.0 Modules
| |||||||||||||||
| 5492 | C:\WINDOWS\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
35 350
Read events
35 248
Write events
78
Delete events
24
Modification events
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:00000000000F02EA |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456BFA0DB55E4278845B426357D5B5F97B3 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FeatureUsage\AppBadgeUpdated |
| Operation: | write | Name: | Chrome |
Value: 6 | |||
| (PID) Process: | (5960) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (5960) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (5960) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (5960) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (5960) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (8128) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 0100000000000000BF3A21A940CFDB01 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Ribbon |
| Operation: | write | Name: | QatItems |
Value: 3C7369713A637573746F6D554920786D6C6E733A7369713D22687474703A2F2F736368656D61732E6D6963726F736F66742E636F6D2F77696E646F77732F323030392F726962626F6E2F716174223E3C7369713A726962626F6E206D696E696D697A65643D2266616C7365223E3C7369713A71617420706F736974696F6E3D2230223E3C7369713A736861726564436F6E74726F6C733E3C7369713A636F6E74726F6C206964513D227369713A3136313238222076697369626C653D2266616C73652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3136313239222076697369626C653D2266616C73652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3132333532222076697369626C653D2266616C73652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3132333834222076697369626C653D22747275652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3132333336222076697369626C653D22747275652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3132333537222076697369626C653D2266616C73652220617267756D656E743D223022202F3E3C2F7369713A736861726564436F6E74726F6C733E3C2F7369713A7161743E3C2F7369713A726962626F6E3E3C2F7369713A637573746F6D55493E | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Toolbar\ShellBrowser |
| Operation: | write | Name: | ITBar7Layout |
Value: 13000000000000000000000020000000100000000000000001000000010700005E01000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
36
Suspicious files
92
Text files
56
Unknown types
250
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5960 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF10c14e.TMP | — | |
MD5:— | SHA256:— | |||
| 5960 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF10c14e.TMP | — | |
MD5:— | SHA256:— | |||
| 5960 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5960 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF10c15e.TMP | — | |
MD5:— | SHA256:— | |||
| 5960 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5960 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5960 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF10c15e.TMP | — | |
MD5:— | SHA256:— | |||
| 5960 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5960 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF10c16d.TMP | — | |
MD5:— | SHA256:— | |||
| 5960 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
63
DNS requests
59
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4688 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4688 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5492 | explorer.exe | GET | 200 | 18.173.205.57:80 | http://ocsps.ssl.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT4XPMAgX8rbNb10iD9IkFVxGbTWwQUW8pe5d7SgarNqC1kUbbZcpuX5k8CEG7dTyXnMX05gVcxNM%2FB3KA%3D | unknown | — | — | whitelisted |
5492 | explorer.exe | GET | 200 | 18.173.205.57:80 | http://ocsps.ssl.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBROpre88MpUocDyy2wCPdWKwtQZDwQUAYmUuf60M13w8fqF%2BSRGhKNXaV4CED%2FPMYE3OZi7YghPjS3TGKM%3D | unknown | — | — | whitelisted |
1040 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac6mhlwypzipnufijdvfyhdgvt4q_67/khaoiebndkojlmppeemjhbpbandiljpe_67_win_kfegpqlp6gezs4ree2ol2br2ym.crx3 | unknown | — | — | whitelisted |
1040 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac6mhlwypzipnufijdvfyhdgvt4q_67/khaoiebndkojlmppeemjhbpbandiljpe_67_win_kfegpqlp6gezs4ree2ol2br2ym.crx3 | unknown | — | — | whitelisted |
1040 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac6mhlwypzipnufijdvfyhdgvt4q_67/khaoiebndkojlmppeemjhbpbandiljpe_67_win_kfegpqlp6gezs4ree2ol2br2ym.crx3 | unknown | — | — | whitelisted |
1040 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac6mhlwypzipnufijdvfyhdgvt4q_67/khaoiebndkojlmppeemjhbpbandiljpe_67_win_kfegpqlp6gezs4ree2ol2br2ym.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7292 | chrome.exe | 108.177.15.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
5960 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7292 | chrome.exe | 104.21.11.185:443 | recipelister.com | CLOUDFLARENET | — | unknown |
7292 | chrome.exe | 216.58.212.170:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
recipelister.com |
| unknown |
accounts.google.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
content-autofill.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7292 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
7292 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |