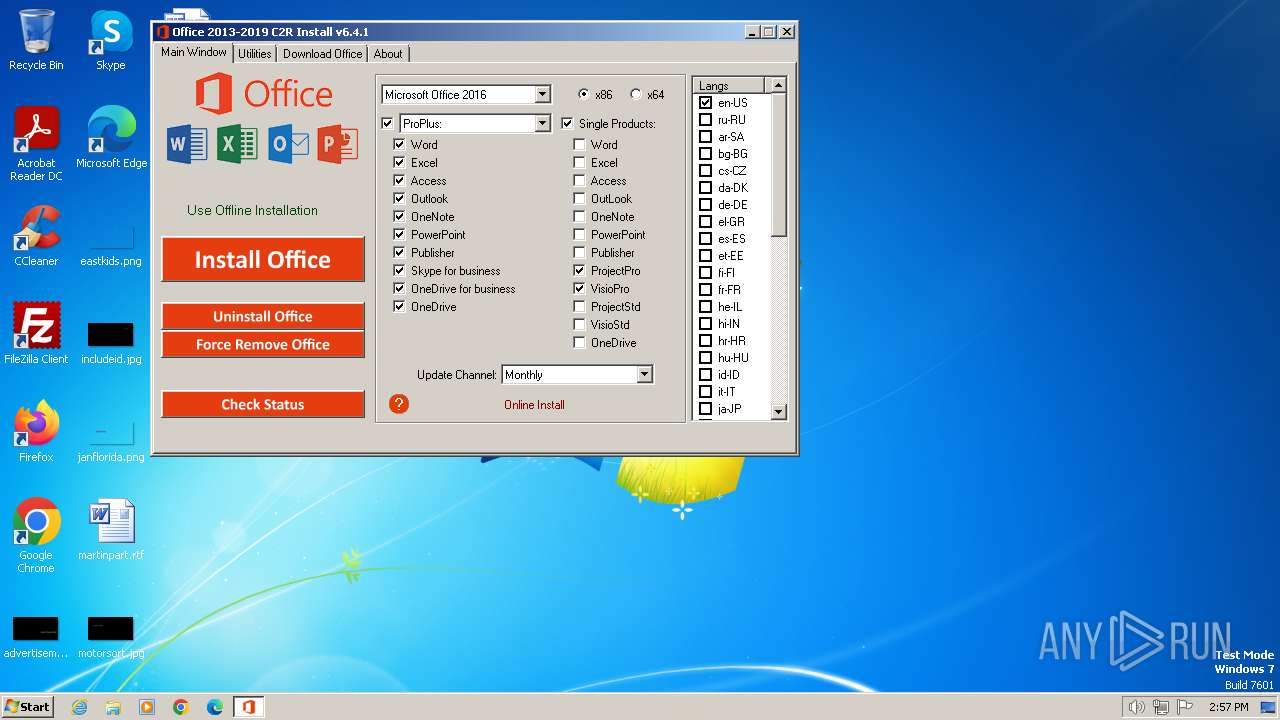
| File name: | OInstall.exe |
| Full analysis: | https://app.any.run/tasks/9393aee6-3ba2-4ec1-aa4c-599f0b6b3afe |
| Verdict: | Malicious activity |
| Analysis date: | March 28, 2024, 14:57:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | B99FAC79315B274F536A73E57DD10649 |
| SHA1: | 5B479138D2D7CF8EAEA1713D5E1B06758A8808E5 |
| SHA256: | 623344AA7C04D12756D890223DF826D6D7637FAE951407C29692CA40F6857B20 |
| SSDEEP: | 196608:/VrCEhhtHnNQoeXEXpTaCDnp2OU/vp0BWjmJJnwEYrbZu59mmrS3xUMxUgd3PJMu:9+YttbeXep2CDp2x/vqJnMZu59pr4OgT |
MALICIOUS
Drops the executable file immediately after the start
- OInstall.exe (PID: 2892)
- files.dat (PID: 2688)
- OfficeClickToRun.exe (PID: 984)
- setup.exe (PID: 3324)
Run PowerShell with an invisible window
- powershell.exe (PID: 2972)
Creates a writable file in the system directory
- OfficeClickToRun.exe (PID: 984)
Scans artifacts that could help determine the target
- OfficeC2RClient.exe (PID: 1736)
SUSPICIOUS
Process drops legitimate windows executable
- OInstall.exe (PID: 2892)
- files.dat (PID: 2688)
- setup.exe (PID: 3324)
- OfficeClickToRun.exe (PID: 984)
Starts CMD.EXE for commands execution
- OInstall.exe (PID: 2892)
Drops 7-zip archiver for unpacking
- OInstall.exe (PID: 2892)
Starts application with an unusual extension
- cmd.exe (PID: 1496)
The executable file from the user directory is run by the CMD process
- files.dat (PID: 2688)
- setup.exe (PID: 3324)
The process drops C-runtime libraries
- files.dat (PID: 2688)
- setup.exe (PID: 3324)
Starts a Microsoft application from unusual location
- setup.exe (PID: 3324)
Reads security settings of Internet Explorer
- setup.exe (PID: 3324)
- OfficeClickToRun.exe (PID: 1596)
- OfficeClickToRun.exe (PID: 984)
- OfficeC2RClient.exe (PID: 1736)
Reads settings of System Certificates
- setup.exe (PID: 3324)
- OfficeClickToRun.exe (PID: 1596)
- OfficeC2RClient.exe (PID: 1736)
Checks Windows Trust Settings
- setup.exe (PID: 3324)
- OfficeClickToRun.exe (PID: 984)
Searches for installed software
- setup.exe (PID: 3324)
The process hide an interactive prompt from the user
- setup.exe (PID: 3324)
The process bypasses the loading of PowerShell profile settings
- setup.exe (PID: 3324)
Starts POWERSHELL.EXE for commands execution
- setup.exe (PID: 3324)
Reads the Internet Settings
- setup.exe (PID: 3324)
- OfficeClickToRun.exe (PID: 1596)
- powershell.exe (PID: 2972)
- OfficeC2RClient.exe (PID: 1736)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 2972)
Executes as Windows Service
- OfficeClickToRun.exe (PID: 984)
INFO
Reads Environment values
- OInstall.exe (PID: 2892)
- OfficeClickToRun.exe (PID: 984)
- OfficeClickToRun.exe (PID: 1596)
- OfficeC2RClient.exe (PID: 1736)
Reads the computer name
- OInstall.exe (PID: 2892)
- setup.exe (PID: 3324)
- OfficeClickToRun.exe (PID: 1596)
- OfficeClickToRun.exe (PID: 984)
- OfficeC2RClient.exe (PID: 1736)
Checks supported languages
- OInstall.exe (PID: 2892)
- files.dat (PID: 2688)
- setup.exe (PID: 3324)
- OfficeClickToRun.exe (PID: 1596)
- OfficeClickToRun.exe (PID: 984)
- OfficeC2RClient.exe (PID: 1736)
Create files in a temporary directory
- OInstall.exe (PID: 2892)
- files.dat (PID: 2688)
- setup.exe (PID: 3324)
- OfficeClickToRun.exe (PID: 1596)
- OfficeC2RClient.exe (PID: 1736)
Reads Microsoft Office registry keys
- setup.exe (PID: 3324)
- OfficeClickToRun.exe (PID: 1596)
- OfficeClickToRun.exe (PID: 984)
- OfficeC2RClient.exe (PID: 1736)
Reads the machine GUID from the registry
- setup.exe (PID: 3324)
- OfficeClickToRun.exe (PID: 1596)
- OfficeClickToRun.exe (PID: 984)
- OfficeC2RClient.exe (PID: 1736)
Reads the software policy settings
- setup.exe (PID: 3324)
- OfficeClickToRun.exe (PID: 1596)
- OfficeClickToRun.exe (PID: 984)
- OfficeC2RClient.exe (PID: 1736)
Checks proxy server information
- setup.exe (PID: 3324)
- OfficeClickToRun.exe (PID: 1596)
- OfficeClickToRun.exe (PID: 984)
- OfficeC2RClient.exe (PID: 1736)
Process checks computer location settings
- setup.exe (PID: 3324)
- OfficeClickToRun.exe (PID: 1596)
- OfficeClickToRun.exe (PID: 984)
- OfficeC2RClient.exe (PID: 1736)
Creates files or folders in the user directory
- setup.exe (PID: 3324)
- OfficeClickToRun.exe (PID: 1596)
- OfficeC2RClient.exe (PID: 1736)
Creates files in the program directory
- setup.exe (PID: 3324)
- OfficeClickToRun.exe (PID: 984)
Manual execution by a user
- OfficeC2RClient.exe (PID: 1736)
Reads CPU info
- OfficeClickToRun.exe (PID: 1596)
Reads product name
- OfficeClickToRun.exe (PID: 1596)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (76) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.6) |
| .exe | | | Generic Win/DOS Executable (5.6) |
| .exe | | | DOS Executable Generic (5.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:08:01 04:34:53+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 9592832 |
| InitializedDataSize: | 86016 |
| UninitializedDataSize: | 8470528 |
| EntryPoint: | 0x113a5c0 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.4.1.0 |
| ProductVersionNumber: | 6.4.1.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Unknown (0) |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| ProductName: | Office 2013-2016 C2R Install |
| FileDescription: | Office 2013-2016 C2R Install |
Total processes
57
Monitored processes
11
Malicious processes
7
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 984 | "C:\Program Files\Common Files\Microsoft Shared\ClickToRun\OfficeClickToRun.exe" /service | C:\Program Files\Common Files\Microsoft Shared\ClickToRun\OfficeClickToRun.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Office Click-to-Run (SxS) Version: 16.0.12527.22286 Modules
| |||||||||||||||
| 1496 | "C:\Windows\System32\cmd.exe" /D /c files.dat -y -pkmsauto | C:\Windows\System32\cmd.exe | — | OInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1596 | deliverymechanism=492350f6-3a01-4f97-b9c0-c7c6ddf67d60 platform=x86 productreleaseid=none forcecentcheck= culture=en-us defaultplatform=False storeid= lcid=1033 b= totalclientcabsize=21067269 productstoadd=ProjectProRetail.16_en-us_x-none|ProplusRetail.16_en-us_x-none|VisioProRetail.16_en-us_x-none scenariosubtype=ODT scenario=unknown updatesenabled.16=True acceptalleulas.16=True cdnbaseurl.16=http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60 version.16=16.0.12527.22286 mediatype.16=CDN visioproretail.excludedapps.16=onedrive baseurl.16=http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60 projectproretail.excludedapps.16=onedrive sourcetype.16=CDN flt.downloadappvcab=unknown flt.useclientcabmanager=unknown flt.useexptransportinplacepl=unknown flt.useaddons=unknown flt.useofficehelperaddon=unknown flt.useonedriveclientaddon=unknown | C:\Program Files\Common Files\Microsoft Shared\ClickToRun\OfficeClickToRun.exe | setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Office Click-to-Run (SxS) Version: 16.0.12527.22286 Modules
| |||||||||||||||
| 1736 | "C:\Program Files\Common Files\Microsoft Shared\ClickToRun\OfficeC2RClient.exe" /progressandlaunch AppTargets="root\office16\excel.exe|root\office16\groove.exe|root\office16\lync.exe|root\office16\msaccess.exe|root\office16\mspub.exe|root\office16\onenote.exe|root\office16\outlook.exe|root\office16\powerpnt.exe|root\office16\visio.exe|root\office16\winproj.exe|root\office16\winword.exe" ManualUpgrade=False ScenarioToTrack="Scenario:{FB9843BB-0D8A-4347-A227-C759C3FC9103}@INSTALL" | C:\Program Files\Common Files\Microsoft Shared\ClickToRun\OfficeC2RClient.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office Click-to-Run Client Version: 16.0.12527.22286 Modules
| |||||||||||||||
| 2124 | "C:\Users\admin\AppData\Local\Temp\OInstall.exe" | C:\Users\admin\AppData\Local\Temp\OInstall.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Office 2013-2016 C2R Install Exit code: 3221226540 Modules
| |||||||||||||||
| 2208 | "C:\Windows\System32\cmd.exe" /D /c copy C:\Windows\system32\Tasks\OInstall "C:\Windows\Temp\OInstall.tmp" /Y | C:\Windows\System32\cmd.exe | — | OInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2688 | files.dat -y -pkmsauto | C:\Users\admin\AppData\Local\Temp\files\files.dat | — | cmd.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7z Console SFX Exit code: 0 Version: 9.20 Modules
| |||||||||||||||
| 2892 | "C:\Users\admin\AppData\Local\Temp\OInstall.exe" | C:\Users\admin\AppData\Local\Temp\OInstall.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Office 2013-2016 C2R Install Modules
| |||||||||||||||
| 2972 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -NoProfile -NonInteractive -WindowStyle Hidden -Command "& { $isOfficeInstalled = Get-AppxPackage Microsoft.Office.Desktop -allusers; if ($isOfficeInstalled -eq $null) { Out-File -FilePath 'C:\Users\admin\AppData\Local\Temp\Centennial.Detection.IsCentennialOfficeInstalled.scratch' -InputObject '0' -Encoding ascii; } else { Out-File -FilePath 'C:\Users\admin\AppData\Local\Temp\Centennial.Detection.IsCentennialOfficeInstalled.scratch' -InputObject '1' -Encoding ascii } }" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 3072 | "C:\Windows\System32\cmd.exe" /D /c C:\Users\admin\AppData\Local\Temp\files\Setup.exe /configure Configure.xml | C:\Windows\System32\cmd.exe | — | OInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
37 858
Read events
37 330
Write events
455
Delete events
73
Modification events
| (PID) Process: | (2892) OInstall.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\MediaResources\DirectSound\Speaker Configuration |
| Operation: | write | Name: | Speaker Configuration |
Value: 4 | |||
| (PID) Process: | (3324) setup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\Experiment\officeclicktorun |
| Operation: | write | Name: | FirstSessionTriggered |
Value: 1 | |||
| (PID) Process: | (3324) setup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources |
| Operation: | write | Name: | UIFallbackLanguages |
Value: x-none | |||
| (PID) Process: | (3324) setup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources |
| Operation: | write | Name: | HelpLanguageTag |
Value: en-US | |||
| (PID) Process: | (3324) setup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources |
| Operation: | write | Name: | PreferredEditingLanguage |
Value: en-US | |||
| (PID) Process: | (3324) setup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources |
| Operation: | write | Name: | PreviousPreferredEditingLanguage |
Value: en-US | |||
| (PID) Process: | (3324) setup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources |
| Operation: | write | Name: | WordChangeInstallLanguage |
Value: No | |||
| (PID) Process: | (3324) setup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources |
| Operation: | write | Name: | WordMailChangeInstallLanguage |
Value: No | |||
| (PID) Process: | (3324) setup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources |
| Operation: | write | Name: | XLChangeInstallLanguage |
Value: No | |||
| (PID) Process: | (3324) setup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources |
| Operation: | write | Name: | PPTChangeInstallLanguage |
Value: No | |||
Executable files
200
Suspicious files
22
Text files
41
Unknown types
36
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2892 | OInstall.exe | C:\Users\admin\AppData\Local\Temp\files\setup.exe | executable | |
MD5:— | SHA256:— | |||
| 2892 | OInstall.exe | C:\Users\admin\AppData\Local\Temp\files\files.dat | executable | |
MD5:— | SHA256:— | |||
| 2688 | files.dat | C:\Users\admin\AppData\Local\Temp\files\Configure.xml | text | |
MD5:— | SHA256:— | |||
| 2688 | files.dat | C:\Users\admin\AppData\Local\Temp\files\Uninstall.xml | text | |
MD5:— | SHA256:— | |||
| 2688 | files.dat | C:\Users\admin\AppData\Local\Temp\files\x86\cleanospp.exe | executable | |
MD5:— | SHA256:— | |||
| 2688 | files.dat | C:\Users\admin\AppData\Local\Temp\files\x64\cleanospp.exe | executable | |
MD5:— | SHA256:— | |||
| 2688 | files.dat | C:\Users\admin\AppData\Local\Temp\files\x86\msvcr100.dll | executable | |
MD5:— | SHA256:— | |||
| 2688 | files.dat | C:\Users\admin\AppData\Local\Temp\files\x64\msvcr100.dll | executable | |
MD5:— | SHA256:— | |||
| 2892 | OInstall.exe | C:\Users\admin\AppData\Local\Temp\files\Configure.xml | text | |
MD5:— | SHA256:— | |||
| 3324 | setup.exe | C:\Users\admin\AppData\Local\Temp\OfficeC2R7073A32E-D35D-48C1-B0F9-103255DAC10F\v32_16.0.12527.22286.cab | compressed | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
38
TCP/UDP connections
45
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3324 | setup.exe | HEAD | 200 | 184.25.50.195:80 | http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/v32_16.0.12527.22286.cab | unknown | — | — | unknown |
3324 | setup.exe | HEAD | 200 | 184.25.50.195:80 | http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/v32_16.0.12527.22286.cab | unknown | — | — | unknown |
3324 | setup.exe | GET | 200 | 184.25.50.195:80 | http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/v32_16.0.12527.22286.cab | unknown | — | — | unknown |
3324 | setup.exe | HEAD | 200 | 184.25.50.195:80 | http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/16.0.12527.22286/i320.cab | unknown | — | — | unknown |
984 | OfficeClickToRun.exe | HEAD | 200 | 184.25.50.195:80 | http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/16.0.12527.22286/s321033.cab | unknown | — | — | unknown |
984 | OfficeClickToRun.exe | HEAD | 200 | 184.25.50.195:80 | http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/16.0.12527.22286/s321033.cab | unknown | — | — | unknown |
856 | svchost.exe | HEAD | 200 | 184.25.50.195:80 | http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/16.0.12527.22286/s321033.cab | unknown | — | — | unknown |
856 | svchost.exe | GET | 206 | 184.25.50.195:80 | http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/16.0.12527.22286/s321033.cab | unknown | — | — | unknown |
856 | svchost.exe | GET | 200 | 184.25.50.195:80 | http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/16.0.12527.22286/s321033.cab | unknown | — | — | unknown |
856 | svchost.exe | HEAD | 200 | 184.25.50.195:80 | http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/16.0.12527.22286/s321033.cab | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3324 | setup.exe | 13.107.43.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3324 | setup.exe | 13.107.5.88:443 | client-office365-tas.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3324 | setup.exe | 52.109.89.117:443 | mrodevicemgr.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
3324 | setup.exe | 52.111.229.19:443 | nexusrules.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3324 | setup.exe | 184.25.50.195:80 | officecdn.microsoft.com | Akamai International B.V. | DE | unknown |
3324 | setup.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
nexusrules.officeapps.live.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
client-office365-tas.msedge.net |
| whitelisted |
mrodevicemgr.officeapps.live.com |
| whitelisted |
officecdn.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
vortex-win.data.microsoft.com |
| whitelisted |
nexus.officeapps.live.com |
| whitelisted |