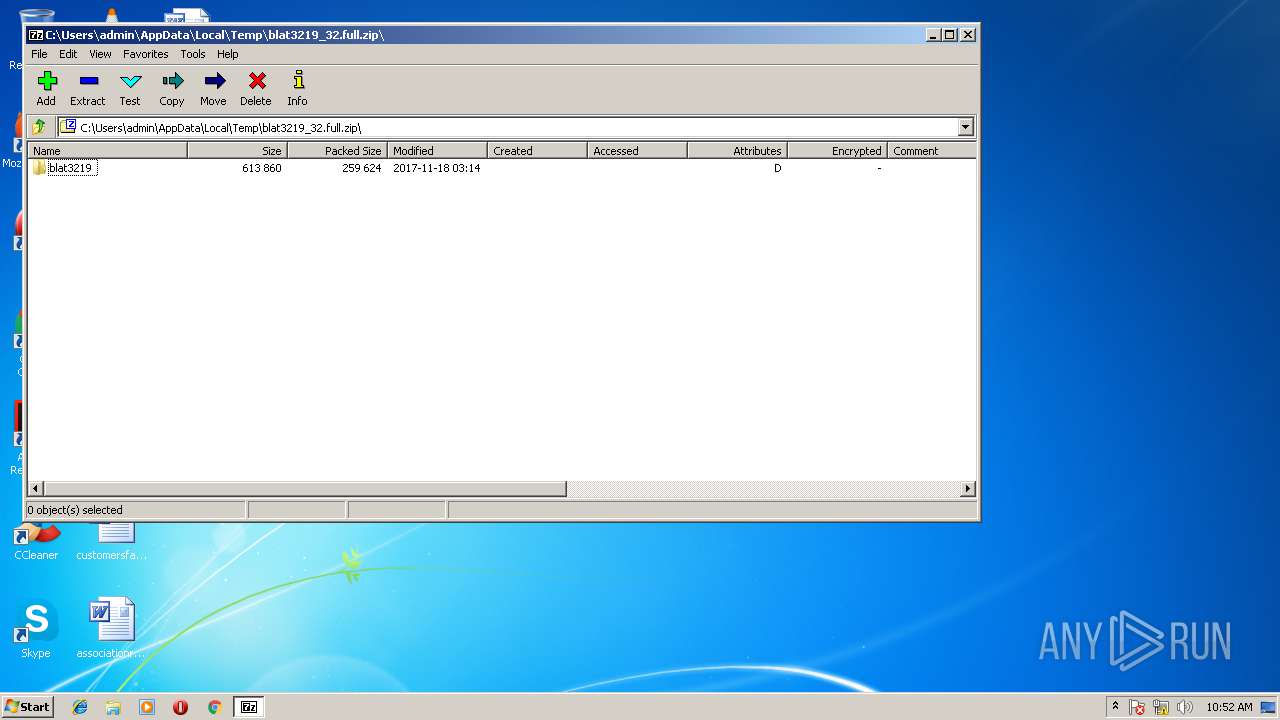
| File name: | blat3219_32.full.zip |
| Full analysis: | https://app.any.run/tasks/ae9c56d1-fd70-4daf-9a71-8d5a4570bac9 |
| Verdict: | Suspicious activity |
| Analysis date: | March 08, 2018, 10:51:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | FD7D5F5C5319917E4530AD923A43B21D |
| SHA1: | 563F3F47BBC861B5E8C93021DAC51373E7838E2E |
| SHA256: | 61FB1CCB0275AEA519A0CDF07ECE2687CB82A7906C2D000DA57FC55F137D1F66 |
| SSDEEP: | 6144:YSQddzr3K/PsElaOTrRJunEzkS8dk4RJ8RI9:YSiQUGamjhkS8FJ8+9 |
MALICIOUS
Application loaded dropped or rewritten executable
- SearchProtocolHost.exe (PID: 1680)
Application was dropped or rewritten from another process
- blat.exe (PID: 3908)
- blat.exe (PID: 3620)
SUSPICIOUS
No suspicious indicators.INFO
Dropped object may contain URL's
- 7zFM.exe (PID: 1088)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2017:11:18 03:14:21 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | blat3219/ |
Total processes
38
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1088 | "C:\Program Files\7-Zip\7zFM.exe" "C:\Users\admin\AppData\Local\Temp\blat3219_32.full.zip" | C:\Program Files\7-Zip\7zFM.exe | explorer.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip File Manager Exit code: 0 Version: 16.04 Modules
| |||||||||||||||
| 1680 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe6_ Global\UsGthrCtrlFltPipeMssGthrPipe6 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3620 | "C:\Users\admin\Desktop\blat.exe" | C:\Users\admin\Desktop\blat.exe | — | explorer.exe | |||||||||||
User: admin Company: http://www.blat.net/ Integrity Level: MEDIUM Description: A Win32 command line eMail tool Exit code: 1 Version: 3.2.19 Modules
| |||||||||||||||
| 3908 | "C:\Users\admin\Desktop\blat3219\full\blat.exe" | C:\Users\admin\Desktop\blat3219\full\blat.exe | — | explorer.exe | |||||||||||
User: admin Company: http://www.blat.net/ Integrity Level: MEDIUM Description: A Win32 command line eMail tool Exit code: 1 Version: 3.2.19 Modules
| |||||||||||||||
Total events
365
Read events
360
Write events
5
Delete events
0
Modification events
| (PID) Process: | (1680) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\8F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1680) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\8F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\ieframe.dll,-912 |
Value: HTML Document | |||
| (PID) Process: | (1680) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\8F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\notepad.exe,-469 |
Value: Text Document | |||
Executable files
2
Suspicious files
0
Text files
11
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1088 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE04431F50\blat3219\docs\file_id.diz | text | |
MD5:D4D3C60B8793B63609098B54E8C129AE | SHA256:F3B2D654FDC729112656786768E5BBA56C5A99426E20F7DCA60C216D5050C0A7 | |||
| 1088 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE04431F50\blat3219\full\blatdll.h | text | |
MD5:9AB1724530ACAAAAABA291E5A682C918 | SHA256:6CEDD03DDA2EC124F54C7DA8B5B2223486351141003F303D6E01743F2FEDC023 | |||
| 1088 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE04431F50\blat3219\full\blat.lib | obj | |
MD5:B84B293B554DB8B2A1700988D10F6E50 | SHA256:4E8DA639AED232805BED1D65B387AEAD5F65379DBC72C389A977AB6C01A231E0 | |||
| 1088 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE04431F50\blat3219\docs\cgi\blat-fail.htm | html | |
MD5:E3AD15C86A2CA3A925DF330AFC299954 | SHA256:5E9E1C0AC16684E7F4CA4B721FEDB52A8EE5FAAFF8B63B7BEF4F8A47F288C0E3 | |||
| 1088 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE04431F50\blat3219\full\blat.dll | executable | |
MD5:4DCA9A0C4AD55A5E2CCBB0EE1A9894D9 | SHA256:0ECA7A343252A925176767D26712176CFCA1F41F08A2944A53B1BF0162422679 | |||
| 1088 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE04431F50\blat3219\docs\cgi\blat-cgi.htm | html | |
MD5:932C8D36379825239E83590B7A8CD269 | SHA256:2A00BD0B4EF00A524FE835DDF3D184F21DB7C7A97A6DCBD984EF01929EC9C799 | |||
| 1088 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE04431F50\blat3219\docs\syntax.txt | text | |
MD5:717D82B582B8B6C0B15D21BBC6CC9DD1 | SHA256:EE24C35ADD4381BDE4B9B1FF693B00000D17612E642C89E8D8539F007680EF4A | |||
| 1088 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE04431F50\blat3219\docs\credits.html | text | |
MD5:80540DDF85CE46D9BF7402BA2C15BAA2 | SHA256:98900E428380D954654516D53613A324A44E58D074BA3B4E4EEFD0CCEE7054B0 | |||
| 1088 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE04431F50\blat3219\docs\readme.txt | text | |
MD5:EE5BCED4B8DD23C067592E743AA00655 | SHA256:747CFEDFCAEEAE0127AE34A8B7DB227973415AD462ACE7E5428F590D5CC7DEF1 | |||
| 1088 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE04431F50\blat3219\docs\ChangeLog.txt | text | |
MD5:036C5208E41458DE355316D0BA98297D | SHA256:833882AE80E58666D0F16A95BDB6FFE88CC128731FB8E7BF0948175F99464FC0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 216.58.205.238:80 | — | Google Inc. | US | whitelisted |