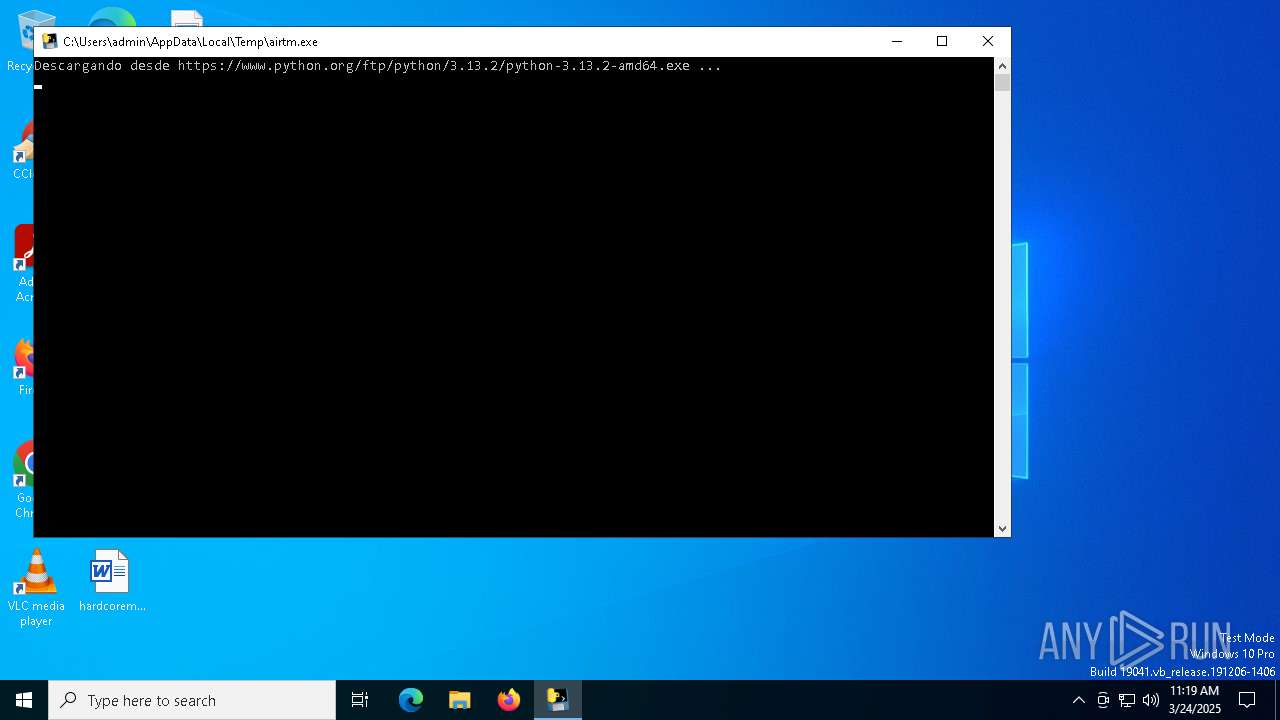
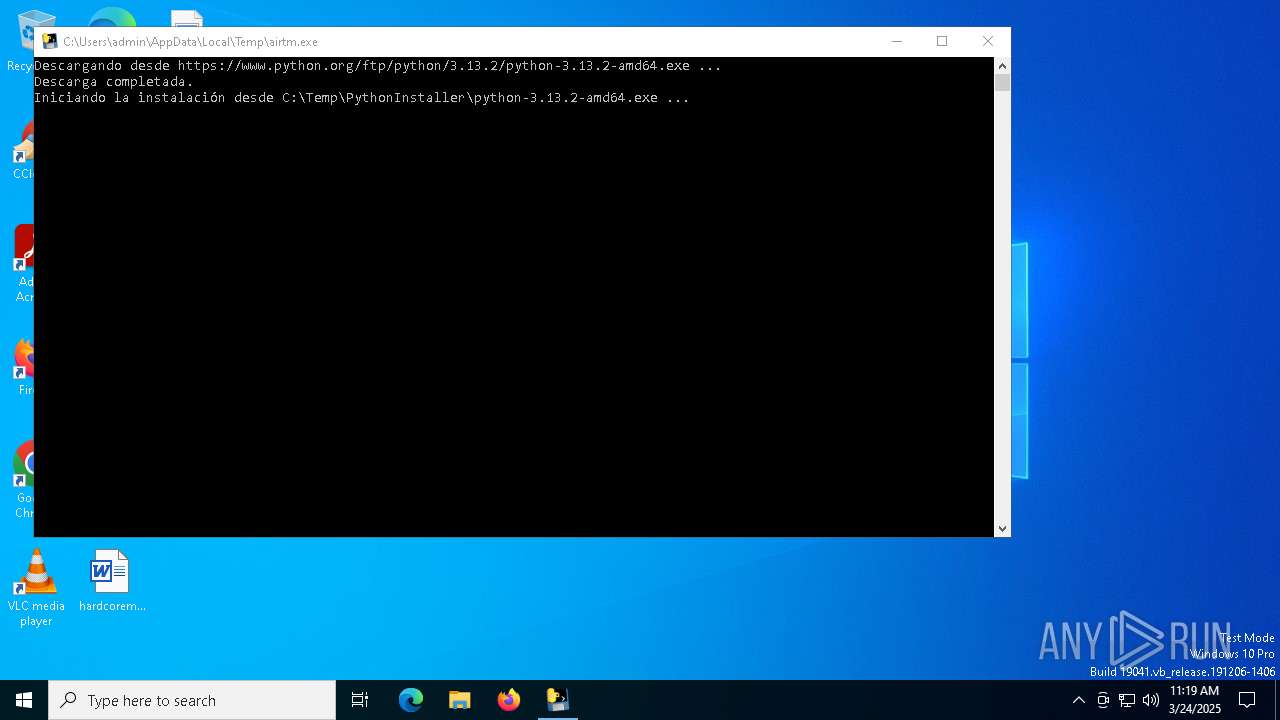
| File name: | airtm.exe |
| Full analysis: | https://app.any.run/tasks/80635e17-0b4e-4159-8459-1daab8e3e597 |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2025, 11:19:20 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 7 sections |
| MD5: | 6802BFFEB68F32F25DAA2FD21817BACC |
| SHA1: | 64E8201BC57B1ED1B0F336413C7702BEDFB78C24 |
| SHA256: | 61F612DCC8784E630A441647CBFD4D70EF95705FFA510465BA53D619FAFD00BC |
| SSDEEP: | 98304:1xb2i3vqeLnc1ZaDPHUFK/uXbQx2U00qu0kheuJSFdVWsyqEVKhHs7UJDZ2pli9V:6KVNnTy9KNUfuMl9 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- airtm.exe (PID: 7856)
- airtm.exe (PID: 7924)
- python-3.13.2-amd64.exe (PID: 1760)
- python-3.13.2-amd64.exe (PID: 7640)
- python-3.13.2-amd64.exe (PID: 3300)
The process drops C-runtime libraries
- airtm.exe (PID: 7856)
- python-3.13.2-amd64.exe (PID: 1760)
- msiexec.exe (PID: 7844)
- python-3.13.2-amd64.exe (PID: 7640)
Process drops legitimate windows executable
- airtm.exe (PID: 7856)
- python-3.13.2-amd64.exe (PID: 1760)
- python-3.13.2-amd64.exe (PID: 7640)
- msiexec.exe (PID: 7844)
Application launched itself
- airtm.exe (PID: 7856)
Process drops python dynamic module
- airtm.exe (PID: 7856)
- msiexec.exe (PID: 7844)
Loads Python modules
- airtm.exe (PID: 7924)
Searches for installed software
- python-3.13.2-amd64.exe (PID: 1760)
- dllhost.exe (PID: 7412)
Reads security settings of Internet Explorer
- python-3.13.2-amd64.exe (PID: 1760)
Starts itself from another location
- python-3.13.2-amd64.exe (PID: 1760)
Executes as Windows Service
- VSSVC.exe (PID: 7380)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 7844)
Starts CMD.EXE for commands execution
- airtm.exe (PID: 7924)
INFO
Checks supported languages
- airtm.exe (PID: 7856)
- airtm.exe (PID: 7924)
- python-3.13.2-amd64.exe (PID: 7640)
- python-3.13.2-amd64.exe (PID: 1760)
- msiexec.exe (PID: 7844)
- python-3.13.2-amd64.exe (PID: 3300)
Reads the computer name
- airtm.exe (PID: 7856)
- python-3.13.2-amd64.exe (PID: 7640)
- python-3.13.2-amd64.exe (PID: 1760)
Create files in a temporary directory
- airtm.exe (PID: 7856)
- python-3.13.2-amd64.exe (PID: 1760)
- python-3.13.2-amd64.exe (PID: 3300)
The sample compiled with english language support
- airtm.exe (PID: 7856)
- python-3.13.2-amd64.exe (PID: 1760)
- msiexec.exe (PID: 7844)
- python-3.13.2-amd64.exe (PID: 7640)
- airtm.exe (PID: 7924)
- python-3.13.2-amd64.exe (PID: 3300)
Checks proxy server information
- airtm.exe (PID: 7924)
Process checks computer location settings
- python-3.13.2-amd64.exe (PID: 1760)
Manages system restore points
- SrTasks.exe (PID: 7552)
Creates files or folders in the user directory
- python-3.13.2-amd64.exe (PID: 1760)
PyInstaller has been detected (YARA)
- airtm.exe (PID: 7856)
Executable content was dropped or overwritten
- msiexec.exe (PID: 7844)
Reads the software policy settings
- msiexec.exe (PID: 7844)
Reads the machine GUID from the registry
- python-3.13.2-amd64.exe (PID: 7640)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:03:24 10:50:39+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.42 |
| CodeSize: | 178688 |
| InitializedDataSize: | 153600 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xc380 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
146
Monitored processes
12
Malicious processes
4
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1760 | "C:\Users\admin\AppData\Local\Temp\{06CDC7F1-09E9-4C81-92BC-97C878F7A6C8}\.cr\python-3.13.2-amd64.exe" -burn.clean.room="C:\Temp\PythonInstaller\python-3.13.2-amd64.exe" -burn.filehandle.attached=584 -burn.filehandle.self=736 /quiet InstallAllUsers=1 PrependPath=1 /log "C:\Temp\PythonInstaller\python_install.log" | C:\Users\admin\AppData\Local\Temp\{06CDC7F1-09E9-4C81-92BC-97C878F7A6C8}\.cr\python-3.13.2-amd64.exe | python-3.13.2-amd64.exe | ||||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python 3.13.2 (64-bit) Version: 3.13.2150.0 Modules
| |||||||||||||||
| 3300 | "C:\Temp\PythonInstaller\python-3.13.2-amd64.exe" /quiet InstallAllUsers=1 PrependPath=1 /log "C:\Temp\PythonInstaller\python_install.log" | C:\Temp\PythonInstaller\python-3.13.2-amd64.exe | cmd.exe | ||||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python 3.13.2 (64-bit) Version: 3.13.2150.0 Modules
| |||||||||||||||
| 7372 | C:\WINDOWS\system32\cmd.exe /c ""C:\Temp\PythonInstaller\python-3.13.2-amd64.exe" /quiet InstallAllUsers=1 PrependPath=1 /log "C:\Temp\PythonInstaller\python_install.log"" | C:\Windows\System32\cmd.exe | — | airtm.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7380 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7412 | C:\WINDOWS\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7552 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | dllhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Windows System Protection background tasks. Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7640 | "C:\Users\admin\AppData\Local\Temp\{41FED61A-A38A-4C1C-A688-B55DD12828E5}\.be\python-3.13.2-amd64.exe" -q -burn.elevated BurnPipe.{D4BC239F-1218-47E1-A7B4-DDDCC521BAB2} {7343F839-DFEB-4FB7-B546-69E97A19D75F} 1760 | C:\Users\admin\AppData\Local\Temp\{41FED61A-A38A-4C1C-A688-B55DD12828E5}\.be\python-3.13.2-amd64.exe | python-3.13.2-amd64.exe | ||||||||||||
User: admin Company: Python Software Foundation Integrity Level: HIGH Description: Python 3.13.2 (64-bit) Version: 3.13.2150.0 Modules
| |||||||||||||||
| 7836 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7844 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7856 | "C:\Users\admin\AppData\Local\Temp\airtm.exe" | C:\Users\admin\AppData\Local\Temp\airtm.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
15 782
Read events
14 333
Write events
1 403
Delete events
46
Modification events
| (PID) Process: | (7640) python-3.13.2-amd64.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4000000000000000D63FB8A3AE9CDB01D81D00003C1D0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7412) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 4800000000000000B1CA6FA4AE9CDB01F41C0000F41D0000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7412) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 4800000000000000B1CA6FA4AE9CDB01F41C0000F41D0000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7412) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4800000000000000075A79A4AE9CDB01F41C0000F41D0000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7412) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000D63FB8A3AE9CDB01F41C0000F41D0000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7412) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 48000000000000005B9274A4AE9CDB01F41C0000F41D0000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7412) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 480000000000000069C10AA5AE9CDB01F41C0000F41D0000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7380) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000001D1719A5AE9CDB01D41C000010100000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7380) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000006B7A1BA5AE9CDB01D41C000054120000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7380) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000006B7A1BA5AE9CDB01D41C00007C180000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
66
Suspicious files
67
Text files
653
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1760 | python-3.13.2-amd64.exe | C:\Users\admin\AppData\Local\Temp\{41FED61A-A38A-4C1C-A688-B55DD12828E5}\.ba\PythonBA.dll | executable | |
MD5:340F07086B36D94B974928197A259CBC | SHA256:979B8ED7E4D682DBD4BCD4ADF9FF8C4DEA204FFEB9AD89AA1844C5F86BA8D1D9 | |||
| 1760 | python-3.13.2-amd64.exe | C:\Users\admin\AppData\Local\Temp\{41FED61A-A38A-4C1C-A688-B55DD12828E5}\.ba\SideBar.png | image | |
MD5:888EB713A0095756252058C9727E088A | SHA256:79434BD1368F47F08ACF6DB66638531D386BF15166D78D9BFEA4DA164C079067 | |||
| 1760 | python-3.13.2-amd64.exe | C:\Users\admin\AppData\Local\Temp\{41FED61A-A38A-4C1C-A688-B55DD12828E5}\.ba\Default.thm | xml | |
MD5:1D2CBC76A6A70F60729EE66D6876BB66 | SHA256:D0D3351D4CDE77EB245B026D677E4AE5177A50EE0B9A43DB23349F1AB5DEEDC9 | |||
| 7856 | airtm.exe | C:\Users\admin\AppData\Local\Temp\_MEI78562\python313.dll | executable | |
MD5:501080884BED38CB8801A307C9D7B7B4 | SHA256:BF68CF819A1E865170430C10E91C18B427AEF88DB1DA1742020443864AA2B749 | |||
| 7412 | dllhost.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 1760 | python-3.13.2-amd64.exe | C:\Users\admin\AppData\Local\Temp\{41FED61A-A38A-4C1C-A688-B55DD12828E5}\.ba\Default.wxl | xml | |
MD5:E1A9ABB2936BC6E980C9BACEBE71C5A9 | SHA256:7F30044D0B14262F8BACD2891A810B127550CA56FC4D0E1D619AE489AAF6EC18 | |||
| 7856 | airtm.exe | C:\Users\admin\AppData\Local\Temp\_MEI78562\unicodedata.pyd | executable | |
MD5:C0B4C55CE3711AF914B2015F707E4452 | SHA256:A67EEC238162FDE20AC24CA7DF931792734AAD0611BE22D1B3A71BC15ACF72F3 | |||
| 7856 | airtm.exe | C:\Users\admin\AppData\Local\Temp\_MEI78562\select.pyd | executable | |
MD5:2663E22900AB5791C6687A264473AE1E | SHA256:BAEE284995B22D495FD12FA8378077E470978DB1522C61BFB9AF37FB827F33D1 | |||
| 3300 | python-3.13.2-amd64.exe | C:\Users\admin\AppData\Local\Temp\{06CDC7F1-09E9-4C81-92BC-97C878F7A6C8}\.cr\python-3.13.2-amd64.exe | executable | |
MD5:E31453864AC4EBF06CFCAE1FAF4A9464 | SHA256:3F1C60F03213432EB0D93CABFFA8C3DCBD3211D98FFDA60A5B87EE432A2587D3 | |||
| 7856 | airtm.exe | C:\Users\admin\AppData\Local\Temp\_MEI78562\libssl-3.dll | executable | |
MD5:4FF168AAA6A1D68E7957175C8513F3A2 | SHA256:2E4D35B681A172D3298CAF7DC670451BE7A8BA27C26446EFC67470742497A950 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
31
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7972 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7488 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7488 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7844 | msiexec.exe | GET | 200 | 204.79.197.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBTDHsfuqfubd3pihvq4mgQVWgHWNwQUyH7SaoUqG8oZmAQHJ89QEE9oqKICEzMAAAAHh6M0o3uljhwAAAAAAAc%3D | unknown | — | — | whitelisted |
7844 | msiexec.exe | GET | 200 | 204.79.197.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBQ0NE46krjtIffEj0l00lckKsLufgQUJEWZoXeQKnzDyoOwbmQWhCr4LGcCEzMAAqUUWCjwxly7WnsAAAACpRQ%3D | unknown | — | — | whitelisted |
7844 | msiexec.exe | GET | 200 | 204.79.197.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBTOQYLFSE5GO%2FpaRVfYu7d9gZEbQAQU2UEpsA8PY2zvadf1zSmepEhqMOYCEzMAAAAEllBL0tvuy4gAAAAAAAQ%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5024 | RUXIMICS.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7924 | airtm.exe | 151.101.128.223:443 | www.python.org | FASTLY | US | whitelisted |
3216 | svchost.exe | 20.198.162.78:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
6544 | svchost.exe | 40.126.32.133:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.python.org |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |