| File name: | Voicemail_+Transcription+_ATT006151.docx |
| Full analysis: | https://app.any.run/tasks/b572d391-07a2-429a-8748-b64309df8e22 |
| Verdict: | Malicious activity |
| Analysis date: | January 10, 2025, 18:26:59 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | AADE183DE3081570BB4DE15212AEF943 |
| SHA1: | F92F9C30F2D38F966BC7BF1936A33445FA102CD3 |
| SHA256: | 61F604564C77FA2E0F48CCC8643D9F1C25BB2F5B67A5D727AED3721FF136164A |
| SSDEEP: | 1536:EIoZHS2iS/Tc9F1gnGChtnOm3uBOX+iwsPUK6F:uVS2tbwFaHnOmeBOZfUbF |
MALICIOUS
Suspicious URL found
- WINWORD.EXE (PID: 6244)
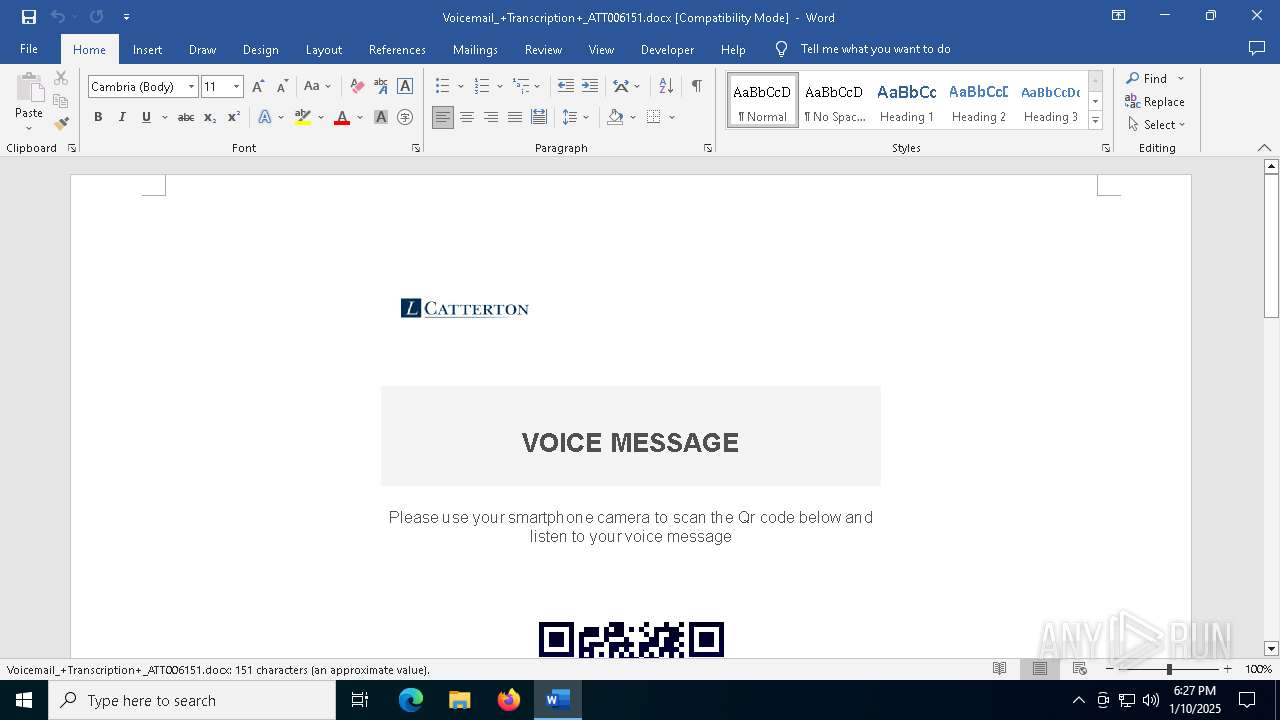
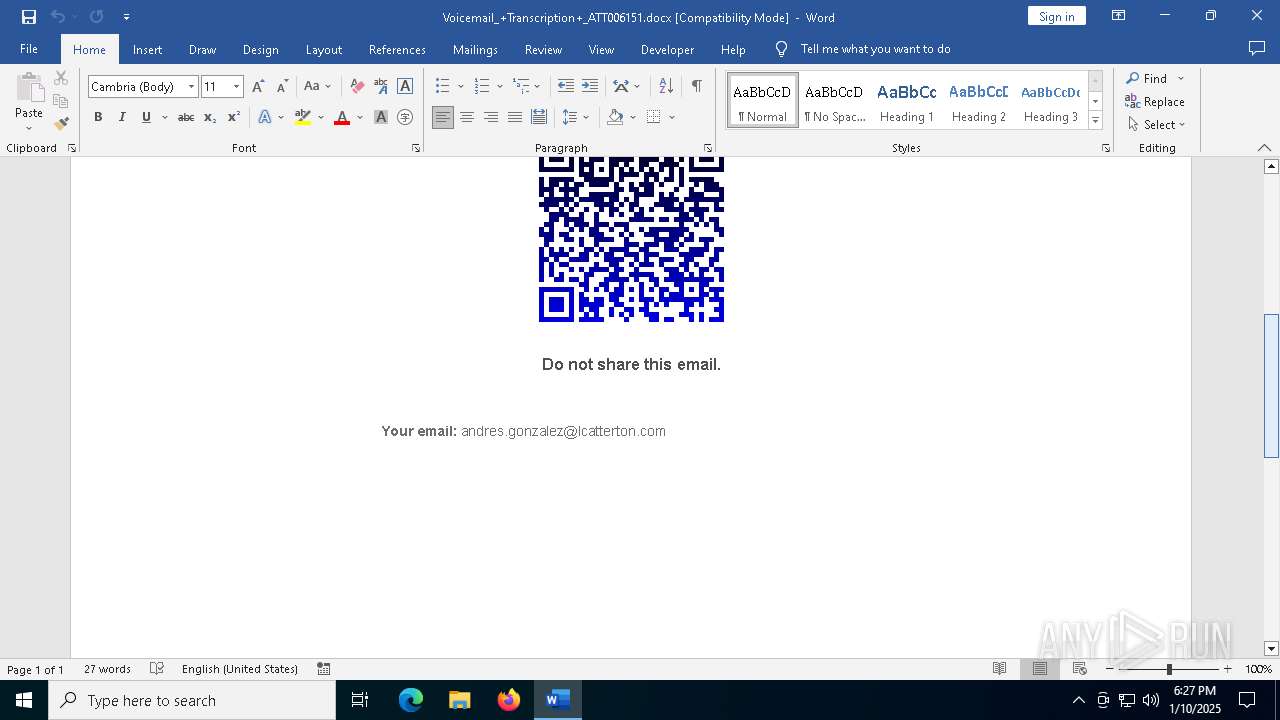
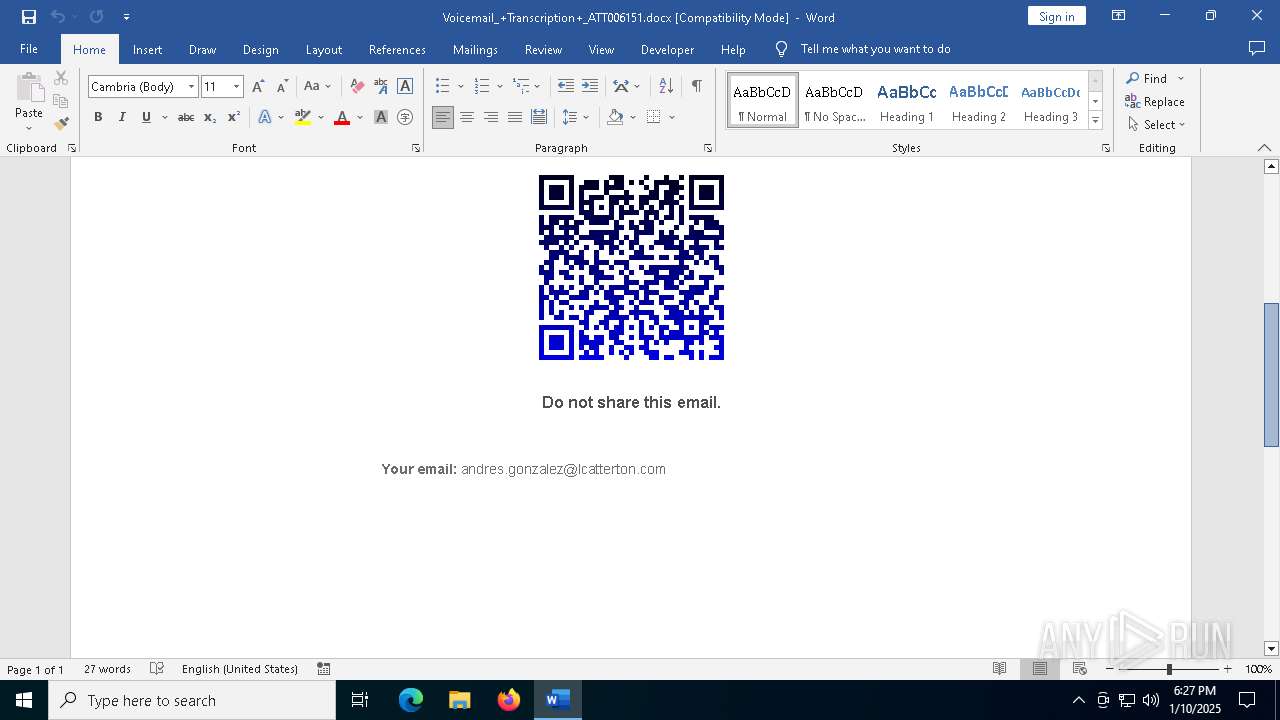
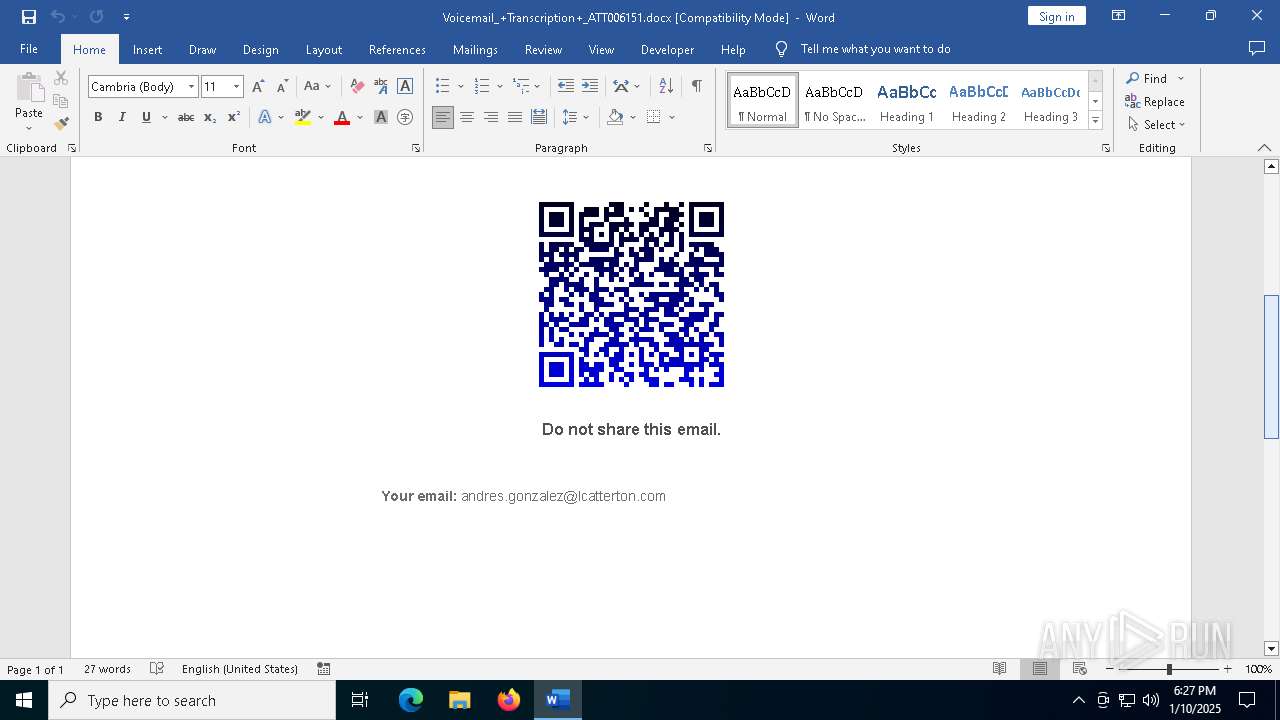
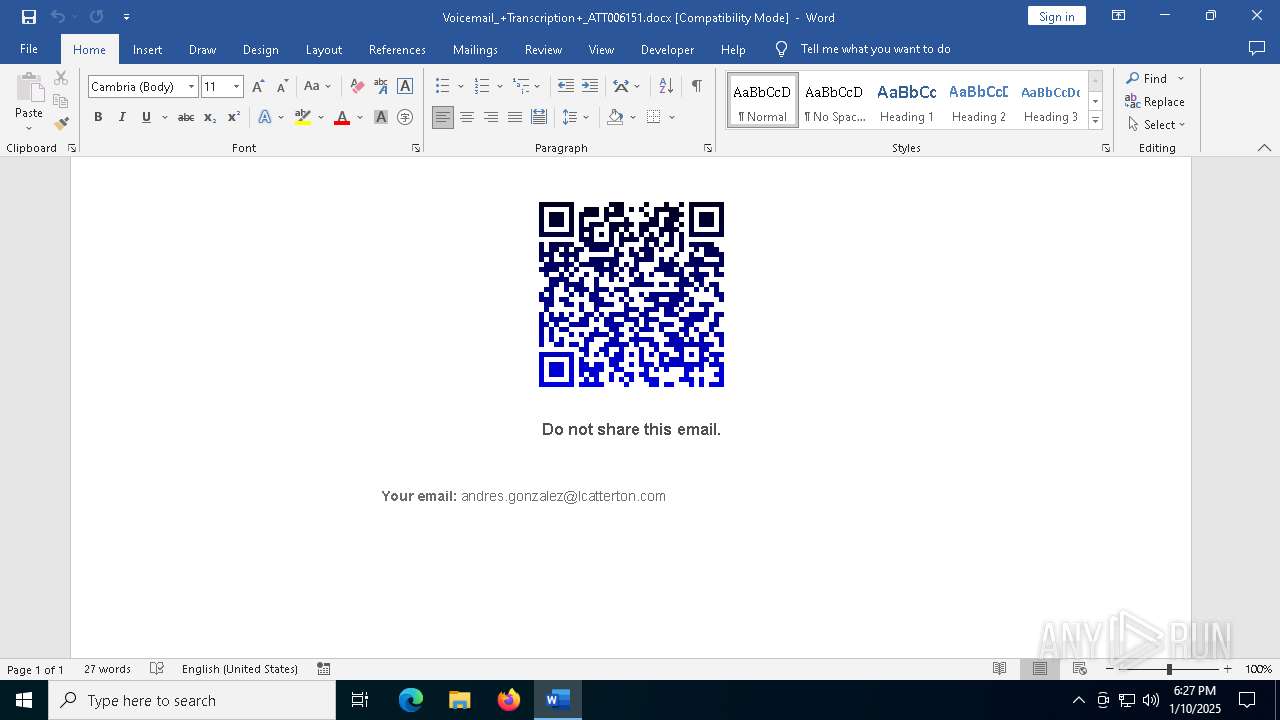
QR code contains URL with email
- WINWORD.EXE (PID: 6244)
SUSPICIOUS
No suspicious indicators.INFO
Sends debugging messages
- WINWORD.EXE (PID: 6244)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docx | | | Word Microsoft Office Open XML Format document (52.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (38.8) |
| .zip | | | ZIP compressed archive (8.8) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:01:10 18:01:52 |
| ZipCRC: | 0xd0aea7fc |
| ZipCompressedSize: | 411 |
| ZipUncompressedSize: | 1788 |
| ZipFileName: | [Content_Types].xml |
XMP
| Title: | - |
|---|---|
| Subject: | - |
| Creator: | python-docx |
| Description: | generated by python-docx |
XML
| Keywords: | - |
|---|---|
| LastModifiedBy: | - |
| RevisionNumber: | 1 |
| CreateDate: | 2013:12:23 23:15:00Z |
| ModifyDate: | 2013:12:23 23:15:00Z |
| Category: | - |
| Template: | Normal.dotm |
| TotalEditTime: | - |
| Pages: | 1 |
| Words: | - |
| Characters: | - |
| Application: | Microsoft Macintosh Word |
| DocSecurity: | None |
| Lines: | - |
| Paragraphs: | - |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: | - |
| Manager: | - |
| Company: | - |
| LinksUpToDate: | No |
| CharactersWithSpaces: | - |
| SharedDoc: | No |
| HyperlinkBase: | - |
| HyperlinksChanged: | No |
| AppVersion: | 14 |
Total processes
133
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6244 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n C:\Users\admin\AppData\Local\Temp\Voicemail_+Transcription+_ATT006151.docx /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 6804 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "F5565311-95AB-4913-A680-101661EA7D9C" "8B58A87A-AABC-46D4-9BF5-0B65A24ADAC9" "6244" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
Total events
13 591
Read events
13 251
Write events
318
Delete events
22
Modification events
| (PID) Process: | (6244) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Word\Resiliency\DocumentRecovery\13594F |
| Operation: | write | Name: | 13594F |
Value: 04000000641800004A00000043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C0056006F006900630065006D00610069006C005F002B005400720061006E0073006300720069007000740069006F006E002B005F004100540054003000300036003100350031002E0064006F00630078002800000056006F006900630065006D00610069006C005F002B005400720061006E0073006300720069007000740069006F006E002B005F004100540054003000300036003100350031002E0064006F00630078000000000001000000000000000319253F8D63DB014F5913004F591300000000001F050000000000000000000000000000000000000000000000000000FFFFFFFF00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000FFFFFFFF0000000000000000 | |||
| (PID) Process: | (6244) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | y:+ |
Value: 㩹+ᡤ | |||
| (PID) Process: | (6244) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\WINWORD\6244 |
| Operation: | write | Name: | 0 |
Value: 0B0E106AA3C770E9095B4CA449041E0060DA02230046958FD2FFD3F1D8ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC9062E2230666479624937656646427346777234454557527A75726C472B4176664351554D69715459336D7633424D3D22CA0D2201A201C2190000C50E8908C91003783634C511E430D2120B770069006E0077006F00720064002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (6244) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | ,a+ |
Value: 2C612B006418000002000000000000004FC225418D63DB01B200000001000000740000003200000063003A005C00700072006F006700720061006D002000660069006C00650073005C006D006900630072006F0073006F006600740020006F00660066006900630065005C0072006F006F0074005C006F0066006600690063006500310036005C00670065006E006B006F002E0064006C006C0000006D006900630072006F0073006F0066007400200077006F00720064002000D0C6E0ACC0C9200094CD00AC200030AEA5B20000 | |||
| (PID) Process: | (6244) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | ,a+ |
Value: 愬+ᡤ | |||
| (PID) Process: | (6244) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\WINWORD\6244 |
| Operation: | write | Name: | 0 |
Value: 0B0E106AA3C770E9095B4CA449041E0060DA02230046958FD2FFD3F1D8ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC9062E2230666479624937656646427346777234454557527A75726C472B4176664351554D69715459336D7633424D3D22CA0D2201A200C2190000C50E8908C91003783634C511E430D2120B770069006E0077006F00720064002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (6244) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Roaming |
| Operation: | write | Name: | RoamingConfigurableSettings |
Value: DC00000000000000803A090041060100010001000000000000000000000000000000000000000000201C0000201C00008051010080510100805101008051010080F4030080F4030080F403002C01000084030000805101000000000084030000805101000A0000001E0000001E000000000000000000000080510100010000000100000000000000000000000000000000000000008D2700008D2700008D2700010000000A000000805101000000300000003000000030000000000084030000805101001E0000008403000080510100050000000500000005000000 | |||
| (PID) Process: | (6244) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Roaming |
| Operation: | write | Name: | RoamingConfigurableSettings |
Value: DC00000000000000803A0900E907010005000A0012001B0007004E01000000000000000000000000201C0000201C00008051010080510100805101008051010080F4030080F4030080F403002C01000084030000805101000000000084030000805101000A0000001E0000001E000000000000000000000080510100010000000100000000000000000000000000000000000000008D2700008D2700008D2700010000000A000000805101000000300000003000000030000000000084030000805101001E0000008403000080510100050000000500000005000000 | |||
| (PID) Process: | (6244) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Roaming |
| Operation: | write | Name: | RoamingLastSyncTimeWord |
Value: E907010005000A0012001B0007005D01 | |||
| (PID) Process: | (6244) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Roaming |
| Operation: | write | Name: | RoamingLastWriteTimeWord |
Value: E907010005000A0012001B0007005D01 | |||
Executable files
30
Suspicious files
115
Text files
17
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6244 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:813E04DCDD0030E64D72A6947E51292D | SHA256:D1479039B9E0DC8431BEC3527796A1909943258F2F9BE1100BE88DEF0B360D52 | |||
| 6244 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\fb3b0dbfee58fac8.customDestinations-ms | binary | |
MD5:E4A1661C2C886EBB688DEC494532431C | SHA256:B76875C50EF704DBBF7F02C982445971D1BBD61AEBE2E4B28DDC58A1D66317D5 | |||
| 6244 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Personalization\Governance\Anonymous\floodgatecampaigns.json | binary | |
MD5:AE42B57BCF3F8E6A211D2C5AAE681E58 | SHA256:736D00A1BBF637A13B6D3AC0FE1BB185BD64A73613C2B13C59F1D1843083AC21 | |||
| 6244 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:DDBFED57ECB8DC66902562092901C97C | SHA256:A3E87742D8A8B730BBF294AF490C2E3D99B1E92F48BBBD767132F08973FDD5AD | |||
| 6244 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\UsageMetricsStore\FileActivityStoreV3\Word\ASkwMDAwMDAwMC0wMDAwLTAwMDAtMDAwMC0wMDAwMDAwMDAwMDBfTnVsbAA.S | binary | |
MD5:4EEA2D493A8B9D8C6AB726CFA703AE21 | SHA256:92FD8AF7F32D7D63F6814AB04DAAF05819DC362089CEFA1B8EBDD5AB186367CB | |||
| 6244 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 6244 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:C875B8E0ACA3DB61043B1BA3B3D79385 | SHA256:944888D4933FB9CF40E42E41DA32A89FC9AF19FFA176246AFBACE123A9028A77 | |||
| 6244 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\mso571C.tmp | image | |
MD5:ED3C1C40B68BA4F40DB15529D5443DEC | SHA256:039FE79B74E6D3D561E32D4AF570E6CA70DB6BB3718395BE2BF278B9E601279A | |||
| 6244 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Personalization\Governance\Anonymous\floodgatecampaigns.json.tmp | binary | |
MD5:AE42B57BCF3F8E6A211D2C5AAE681E58 | SHA256:736D00A1BBF637A13B6D3AC0FE1BB185BD64A73613C2B13C59F1D1843083AC21 | |||
| 6244 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:71A1407A7319F8E35C6B9E7D3DD0E793 | SHA256:616E3E561DBFC729DDC325394F74FA3906C9038956A9A7CCA0E689444A63216E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
79
DNS requests
27
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.164.72:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6244 | WINWORD.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6244 | WINWORD.EXE | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | — | — | whitelisted |
6244 | WINWORD.EXE | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_08-31-2010.crl | unknown | — | — | whitelisted |
6244 | WINWORD.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
6244 | WINWORD.EXE | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | unknown | — | — | whitelisted |
6244 | WINWORD.EXE | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.164.72:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
6092 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6244 | WINWORD.EXE | 52.109.28.46:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6244 | WINWORD.EXE | 52.113.194.132:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5064 | SearchApp.exe | 2.23.227.208:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ecs.office.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
login.live.com |
| whitelisted |
Threats
Process | Message |
|---|---|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|