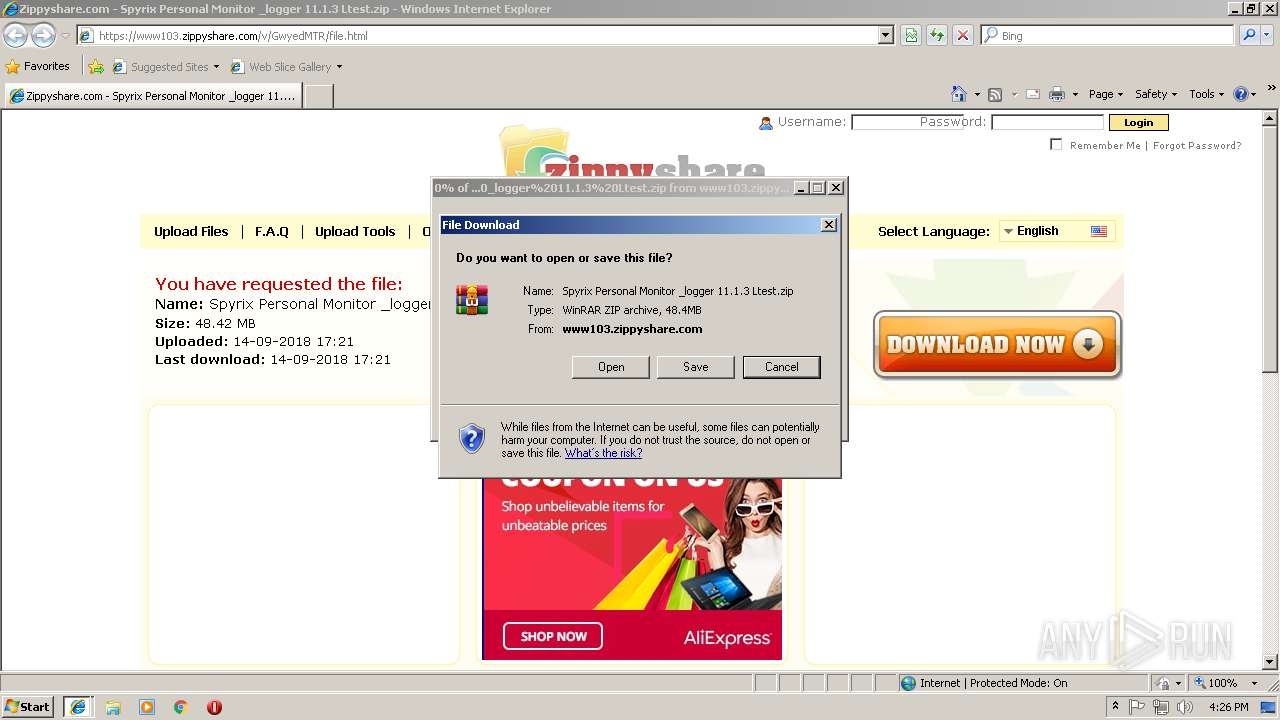
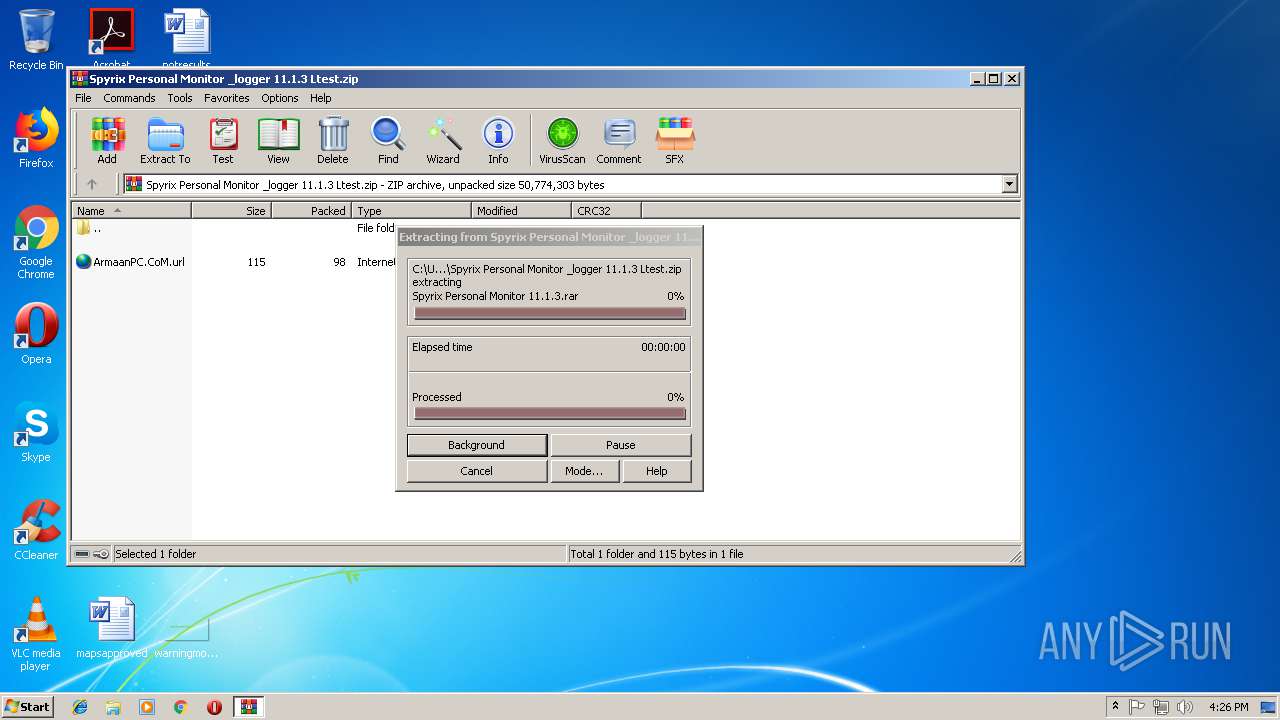
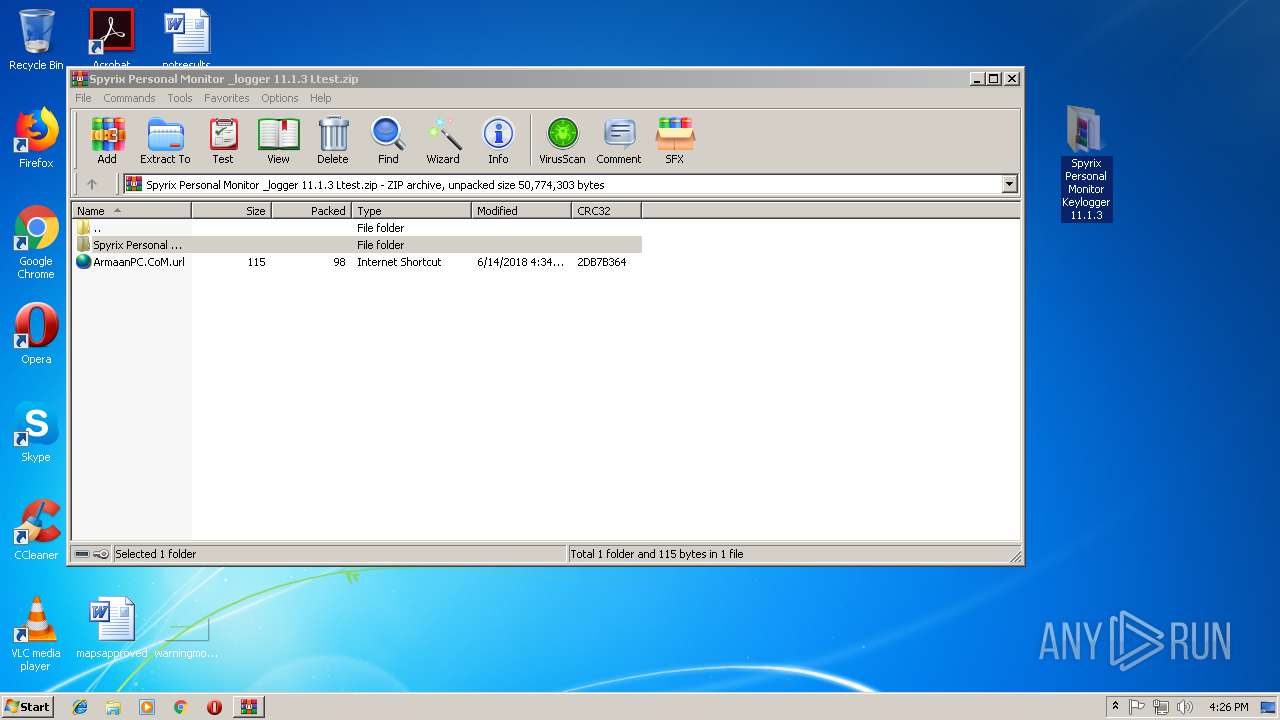
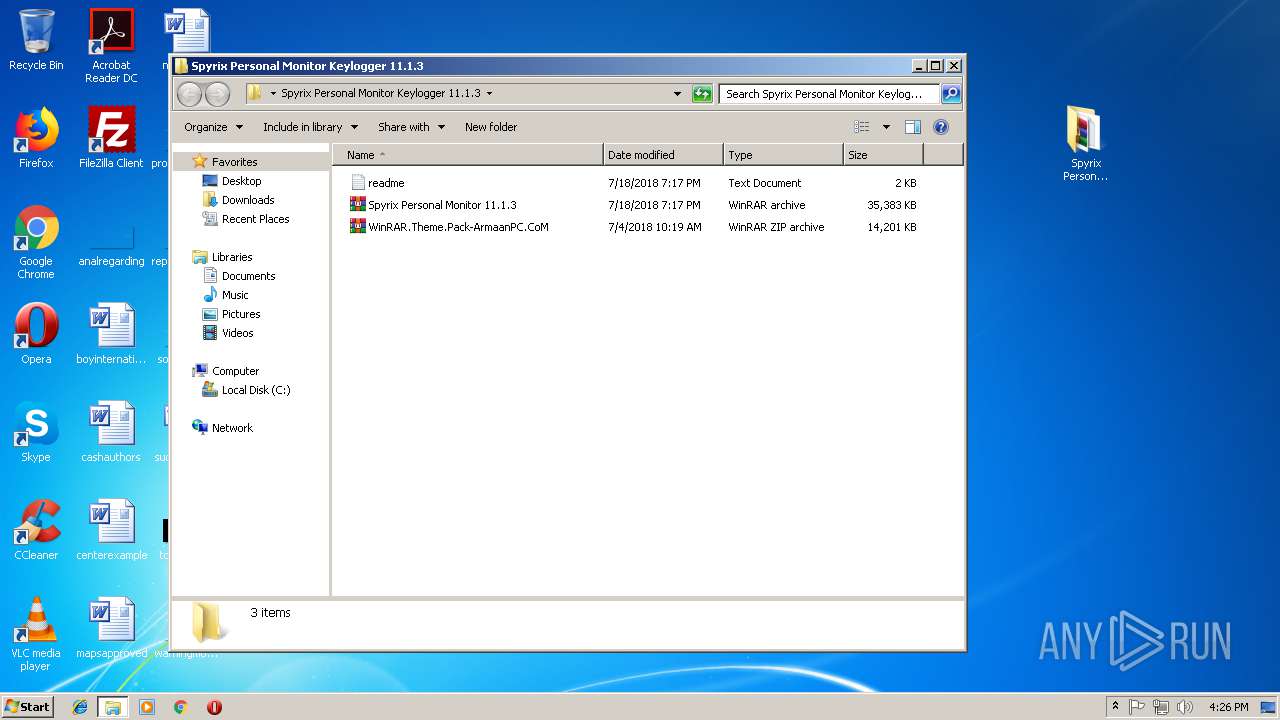
| URL: | https://www103.zippyshare.com/v/GwyedMTR/file.html |
| Full analysis: | https://app.any.run/tasks/f98135a4-918e-487a-aed9-664e1a402b41 |
| Verdict: | Malicious activity |
| Analysis date: | September 14, 2018, 15:25:50 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | FF61C70A36DBA8E1746C213C1434A04D |
| SHA1: | 5FED3A3C32282A3976846242D9B9E7618A4678BA |
| SHA256: | 61E546F0884571710FD8BA02BB4A38B9F65D1F219FDA4C795938D12109696829 |
| SSDEEP: | 3:N8DSUVtGKjKiMxLUJ:2OMtGjiMxLUJ |
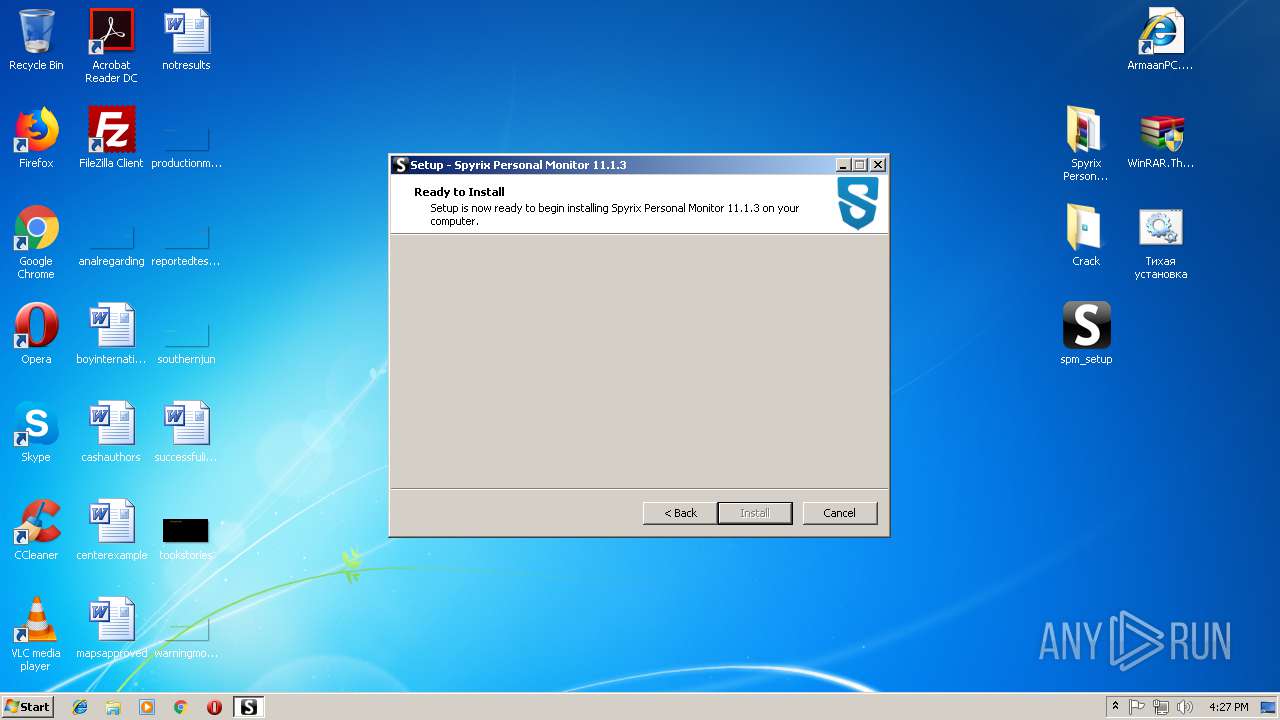
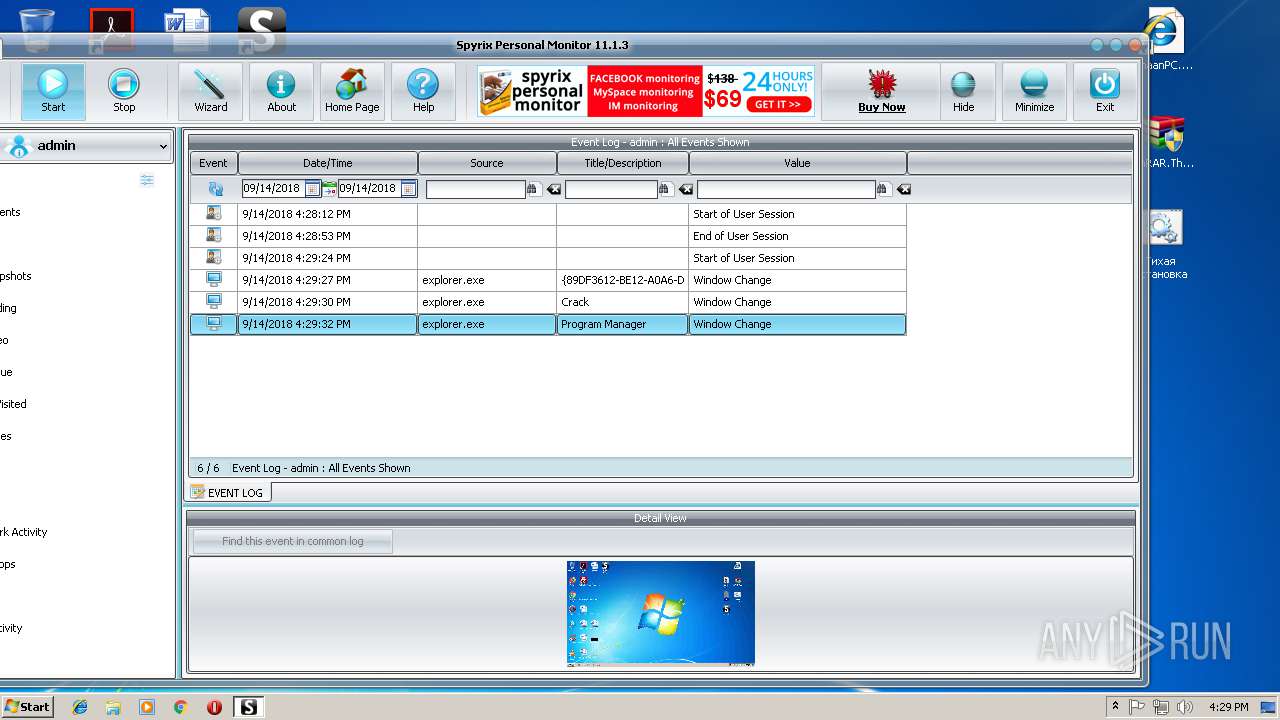
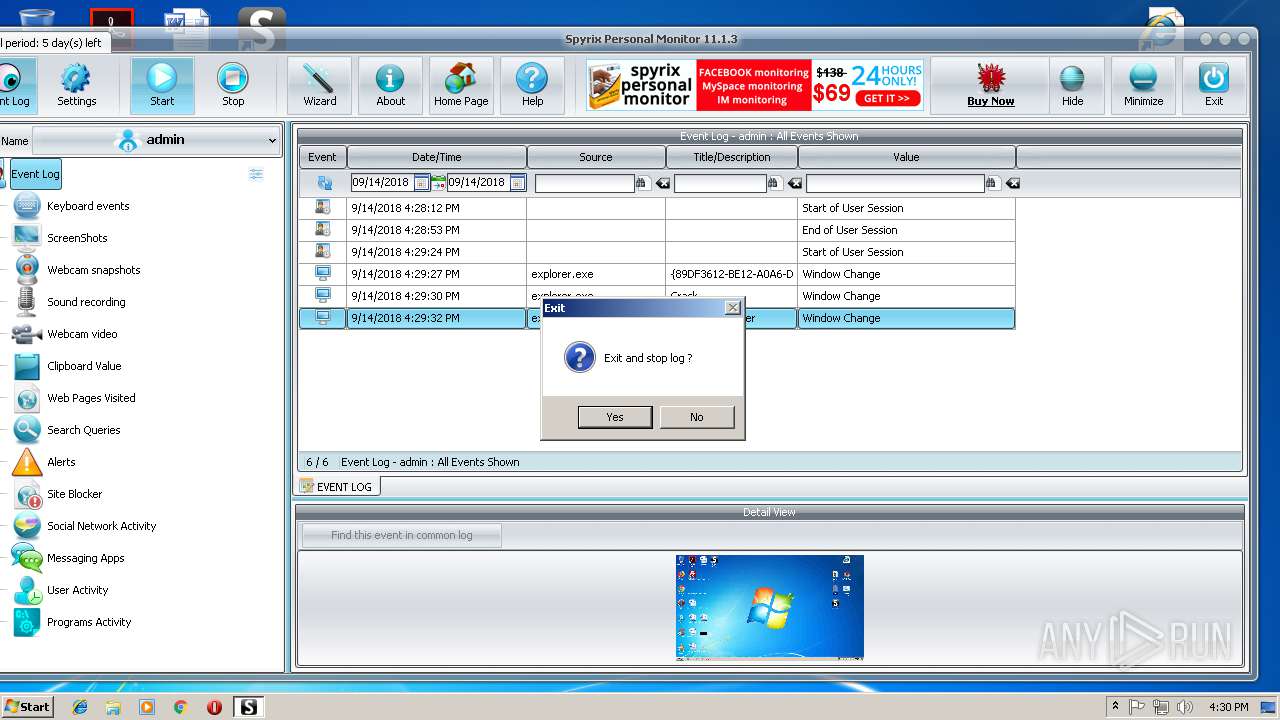
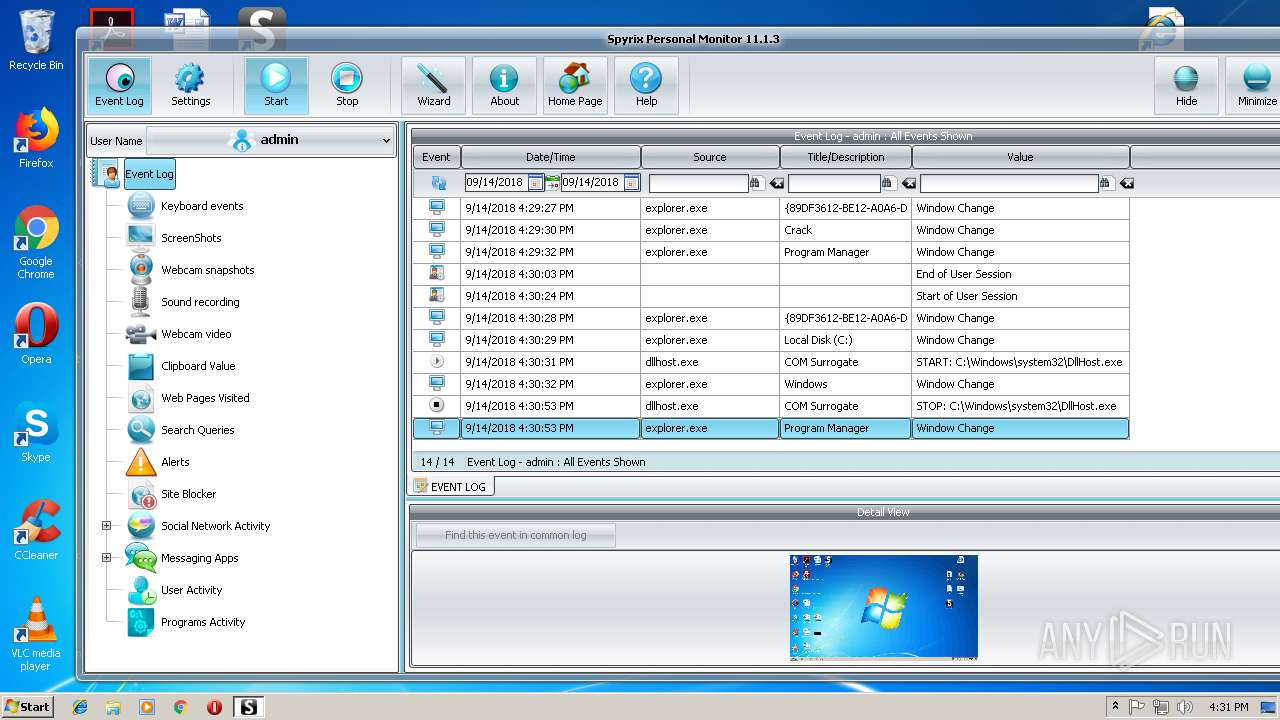
MALICIOUS
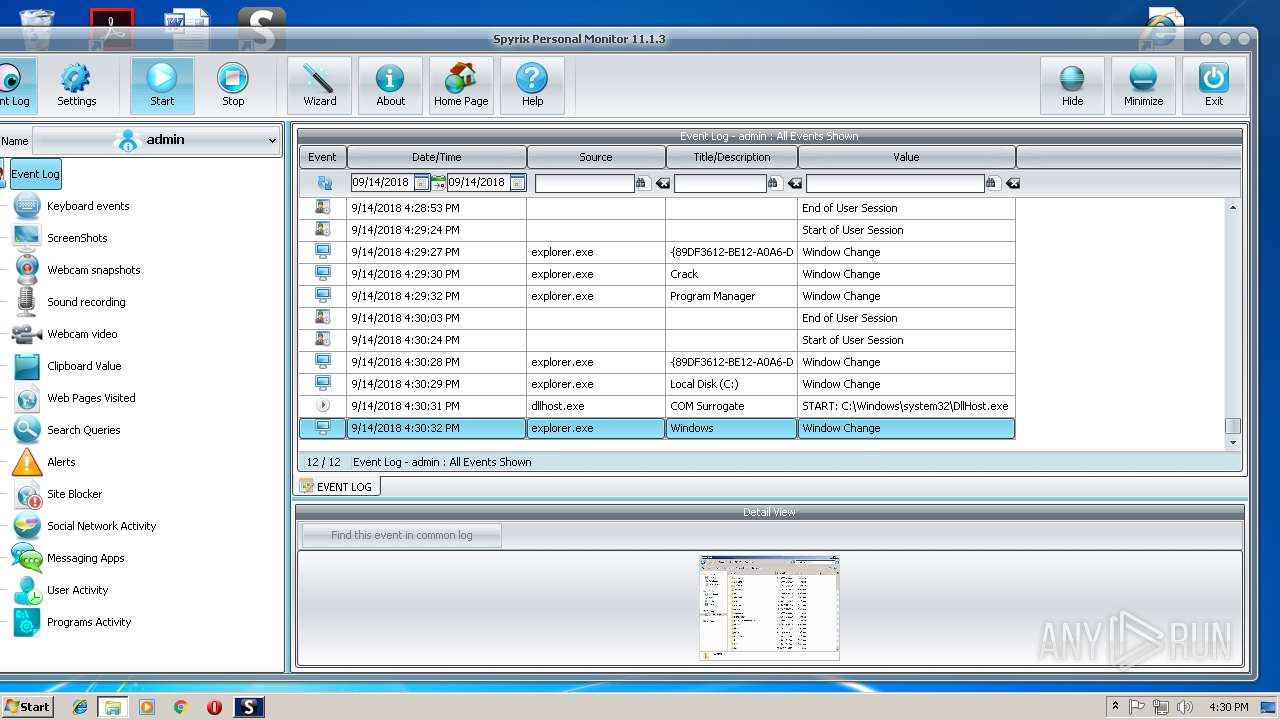
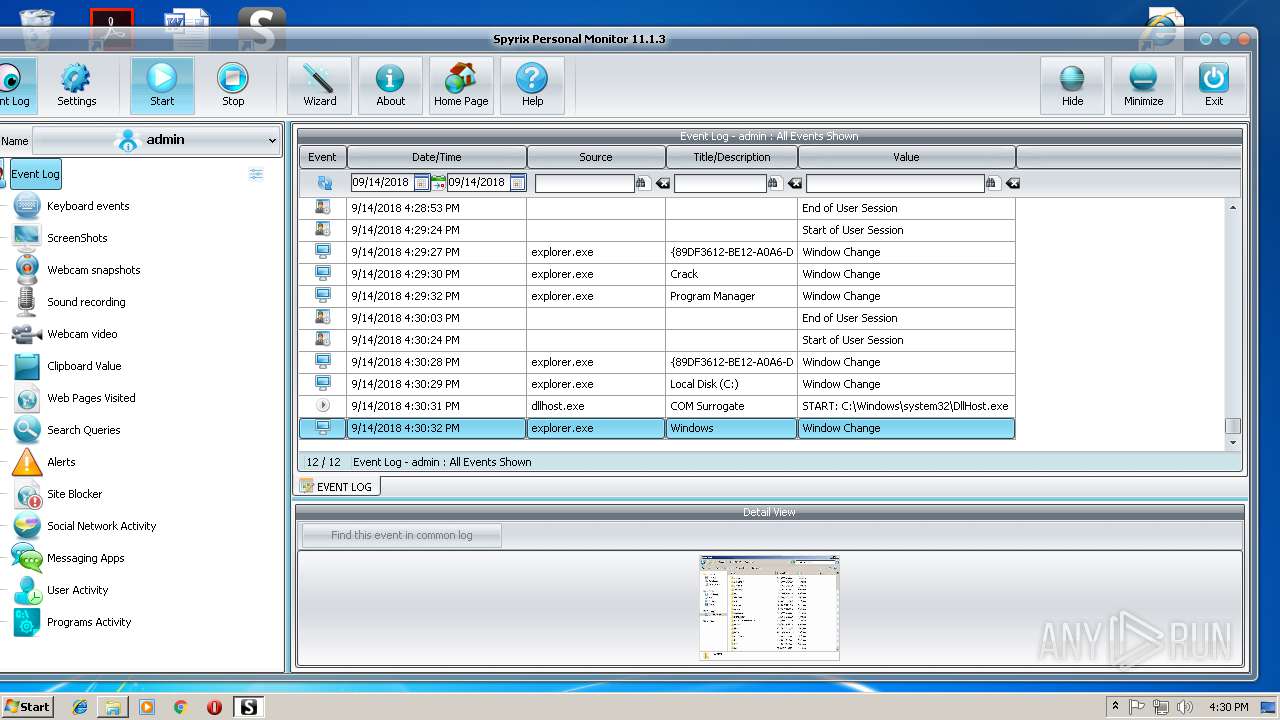
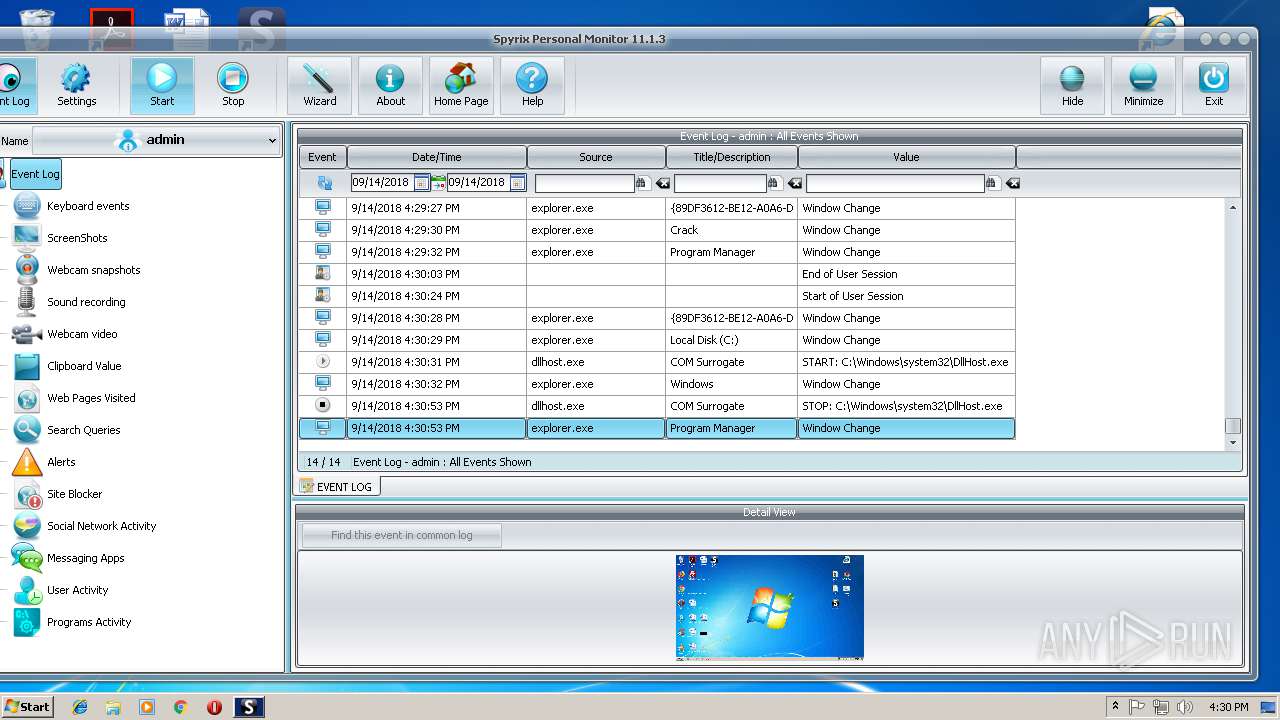
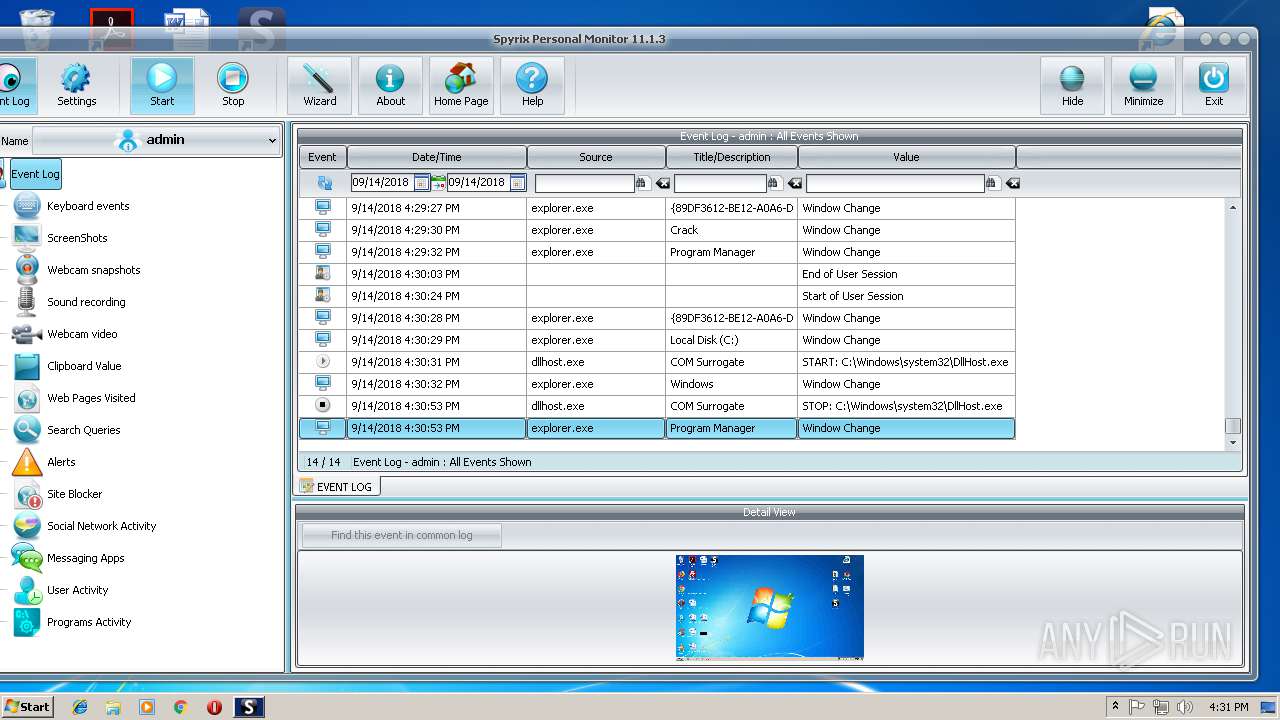
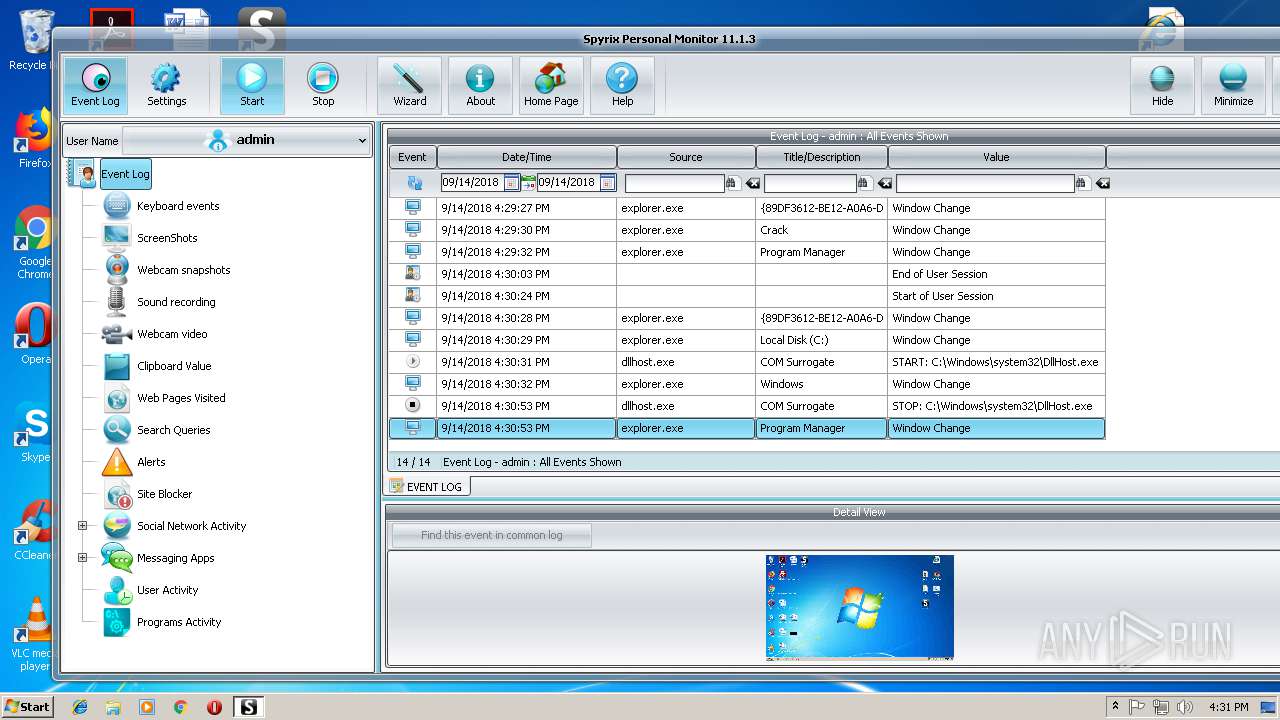
Application was dropped or rewritten from another process
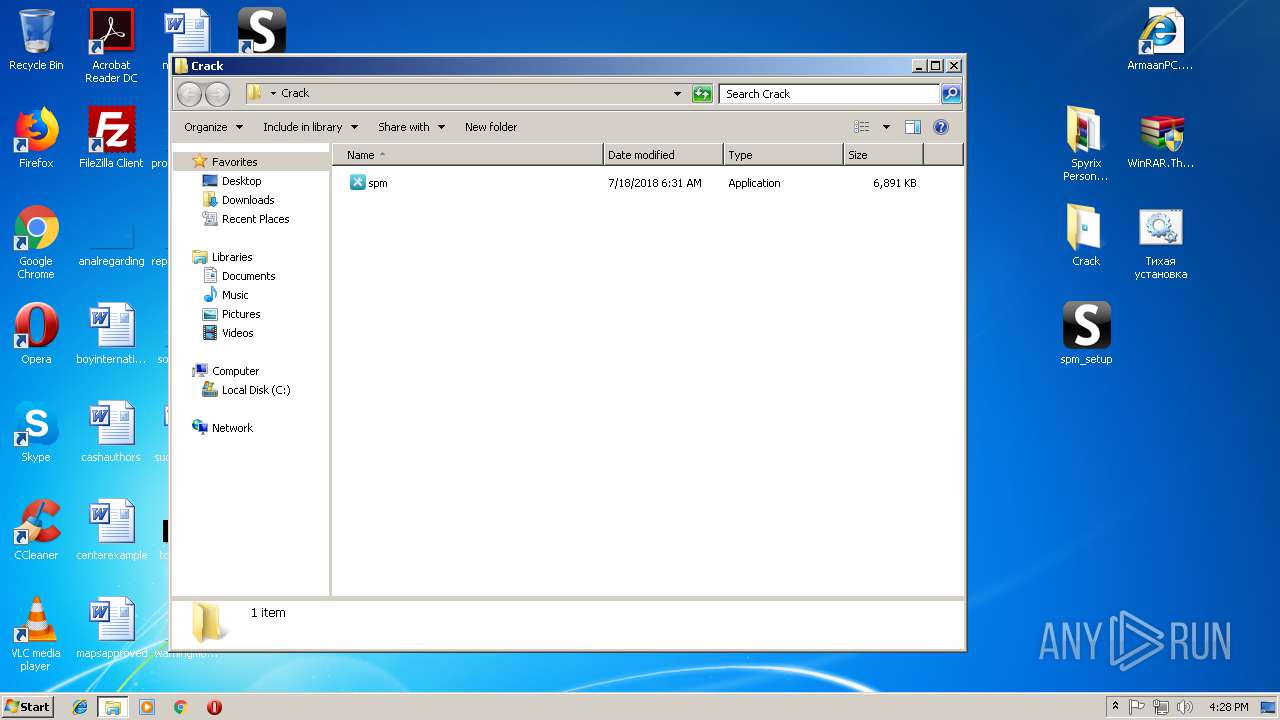
- spm_setup.exe (PID: 3204)
- spm_setup.exe (PID: 3984)
- spm.exe (PID: 3144)
- spmm.exe (PID: 2056)
- spm.exe (PID: 3624)
- spmm.exe (PID: 1484)
- spm.exe (PID: 2372)
- spm.exe (PID: 2312)
- spm.exe (PID: 2800)
- runkey.exe (PID: 2208)
- spmm.exe (PID: 2016)
- spm.exe (PID: 3216)
- spm.exe (PID: 704)
Changes the autorun value in the registry
- spm_setup.tmp (PID: 3788)
Saves itself using automatic execution at hidden regitry location
- spm_setup.tmp (PID: 3788)
Loads dropped or rewritten executable
- spm.exe (PID: 3144)
- spm.exe (PID: 3624)
- spm.exe (PID: 2372)
- spm.exe (PID: 2800)
- spm.exe (PID: 3216)
SUSPICIOUS
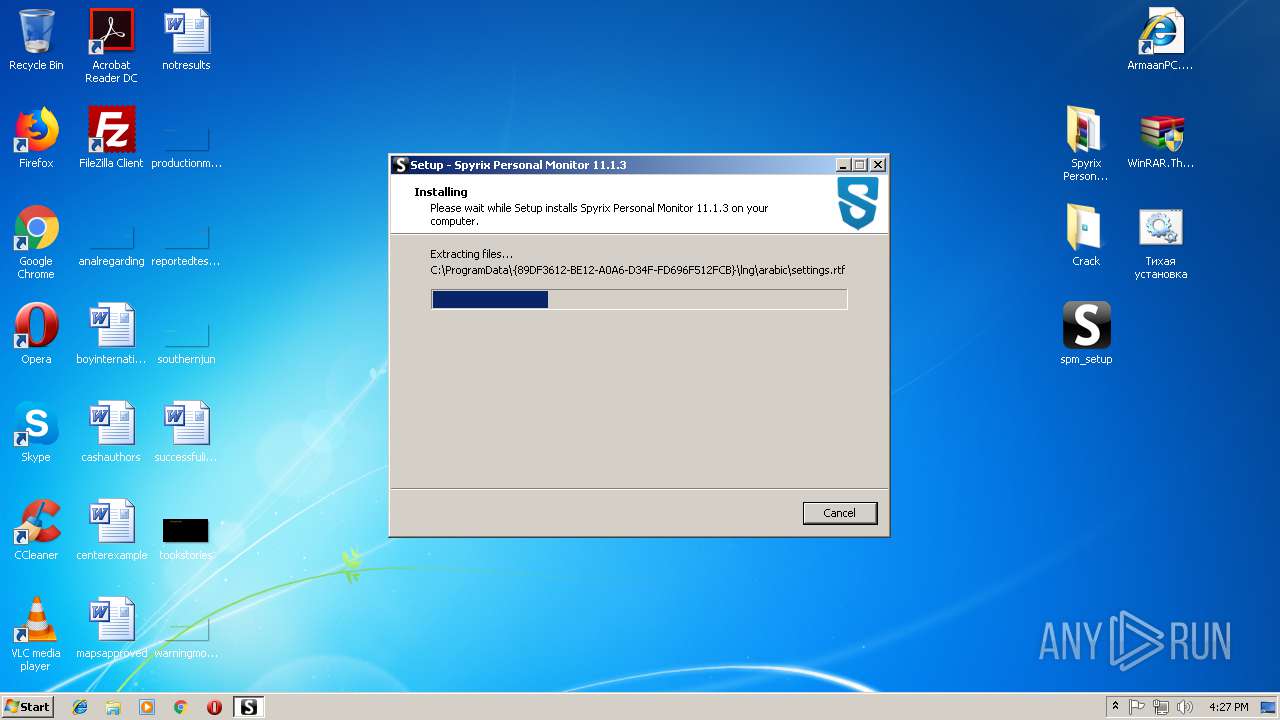
Executable content was dropped or overwritten
- spm_setup.exe (PID: 3204)
- spm_setup.exe (PID: 3984)
- spm_setup.tmp (PID: 3788)
- WinRAR.exe (PID: 3612)
Reads the Windows organization settings
- spm_setup.tmp (PID: 3788)
Reads Windows owner settings
- spm_setup.tmp (PID: 3788)
Creates files in the Windows directory
- spm_setup.tmp (PID: 3788)
Reads the machine GUID from the registry
- spm.exe (PID: 3144)
- spm.exe (PID: 3624)
- spm.exe (PID: 2800)
Creates files in the program directory
- spm.exe (PID: 3144)
- spmm.exe (PID: 2056)
- spm.exe (PID: 3624)
- spm.exe (PID: 2800)
INFO
Changes internet zones settings
- iexplore.exe (PID: 544)
Reads Internet Cache Settings
- iexplore.exe (PID: 2912)
- iexplore.exe (PID: 544)
Reads internet explorer settings
- iexplore.exe (PID: 2912)
Creates files in the user directory
- iexplore.exe (PID: 2912)
Reads settings of System Certificates
- iexplore.exe (PID: 544)
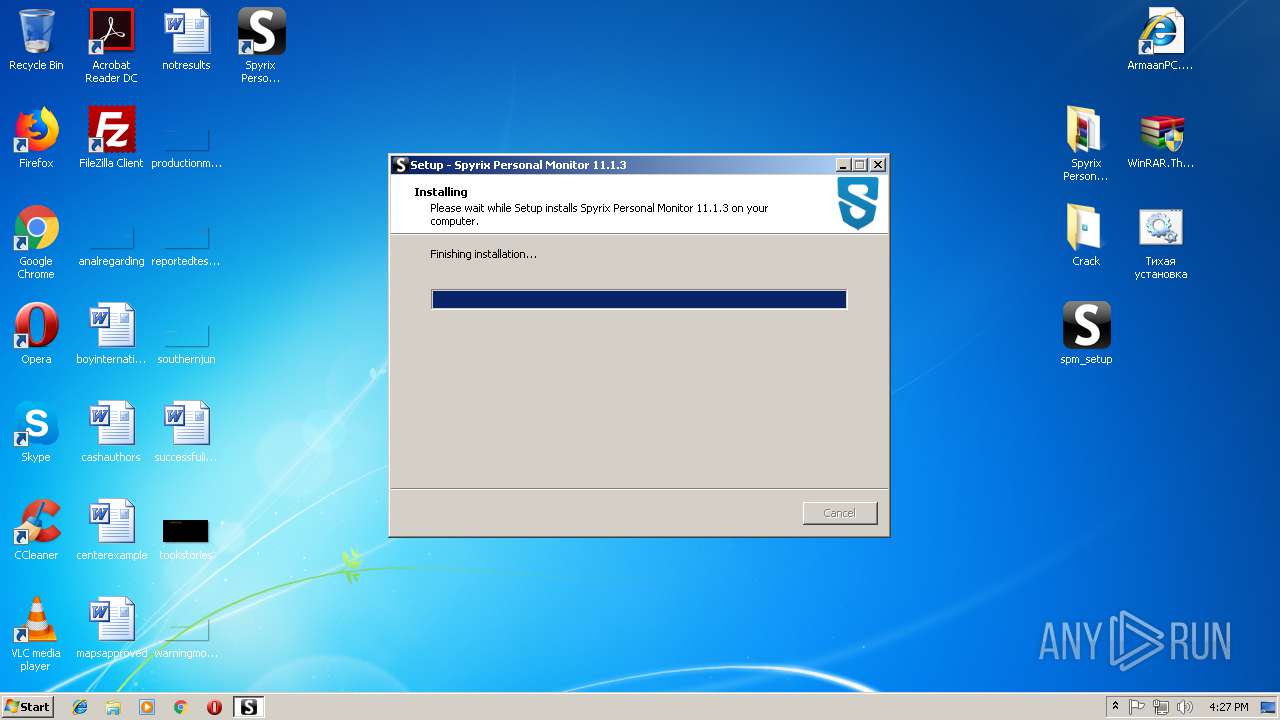
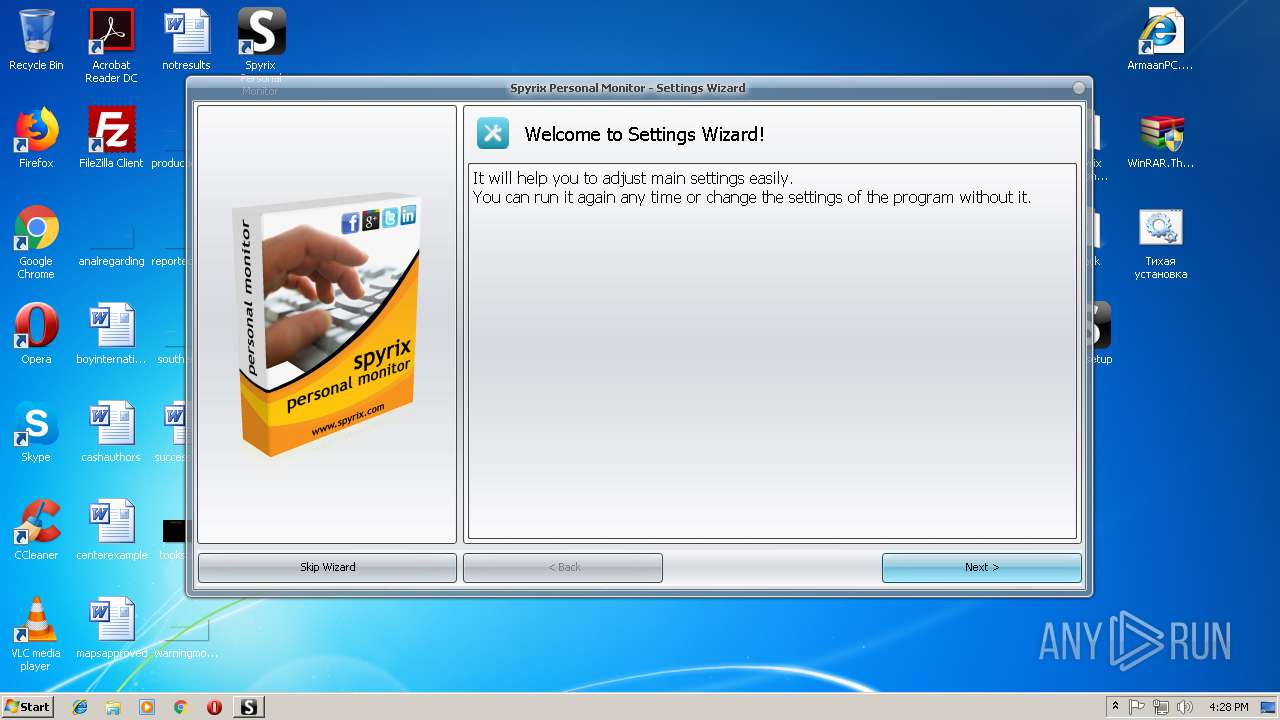
Application was dropped or rewritten from another process
- spm_setup.tmp (PID: 2676)
- spm_setup.tmp (PID: 3788)
Application launched itself
- iexplore.exe (PID: 544)
Loads dropped or rewritten executable
- spm_setup.tmp (PID: 3788)
Creates a software uninstall entry
- spm_setup.tmp (PID: 3788)
Creates files in the program directory
- spm_setup.tmp (PID: 3788)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
68
Monitored processes
22
Malicious processes
7
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 544 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 704 | "C:\ProgramData\{89DF3612-BE12-A0A6-D34F-FD696F512FCB}\spm.exe" | C:\ProgramData\{89DF3612-BE12-A0A6-D34F-FD696F512FCB}\spm.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: System component Exit code: 0 Version: 1.0.11.1 Modules
| |||||||||||||||
| 1476 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\Spyrix Personal Monitor _logger 11.1.3 Ltest.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | iexplore.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1484 | "C:\ProgramData\{89DF3612-BE12-A0A6-D34F-FD696F512FCB}\spmm.exe" "Spyrix Personal Monitor 11.1.3" | C:\ProgramData\{89DF3612-BE12-A0A6-D34F-FD696F512FCB}\spmm.exe | — | spm.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2016 | "C:\ProgramData\{89DF3612-BE12-A0A6-D34F-FD696F512FCB}\spmm.exe" "Spyrix Personal Monitor 11.1.3" | C:\ProgramData\{89DF3612-BE12-A0A6-D34F-FD696F512FCB}\spmm.exe | — | spm.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2056 | "C:\ProgramData\{89DF3612-BE12-A0A6-D34F-FD696F512FCB}\spmm.exe" "Spyrix Personal Monitor 11.1.3" | C:\ProgramData\{89DF3612-BE12-A0A6-D34F-FD696F512FCB}\spmm.exe | — | spm.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2208 | "C:\Windows\runkey.exe" | C:\Windows\runkey.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2312 | "C:\Users\admin\Desktop\Crack\spm.exe" | C:\Users\admin\Desktop\Crack\spm.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: System component Exit code: 0 Version: 1.0.11.1 Modules
| |||||||||||||||
| 2372 | "C:\ProgramData\{89DF3612-BE12-A0A6-D34F-FD696F512FCB}\spm.exe" | C:\ProgramData\{89DF3612-BE12-A0A6-D34F-FD696F512FCB}\spm.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: System component Exit code: 0 Version: 1.0.11.1 Modules
| |||||||||||||||
| 2676 | "C:\Users\admin\AppData\Local\Temp\is-S8MBF.tmp\spm_setup.tmp" /SL5="$C0224,29706695,152064,C:\Users\admin\Desktop\spm_setup.exe" | C:\Users\admin\AppData\Local\Temp\is-S8MBF.tmp\spm_setup.tmp | — | spm_setup.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
Total events
2 789
Read events
2 544
Write events
235
Delete events
10
Modification events
| (PID) Process: | (544) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (544) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (544) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (544) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (544) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (544) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000005C000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (544) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {7F0F43A7-B832-11E8-BFAB-5254004AAD11} |
Value: 0 | |||
| (PID) Process: | (544) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (544) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 2 | |||
| (PID) Process: | (544) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E207090005000E000F001A000600C903 | |||
Executable files
20
Suspicious files
10
Text files
651
Unknown types
38
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 544 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\R9ZEWH8D\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 544 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2912 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\BWPPCY0O\display[1].php | — | |
MD5:— | SHA256:— | |||
| 2912 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\U2ZG9DE0\viewjs-b5af86fa1522edfe99ee6c9472e53cc88f2dc9a5[1].js | text | |
MD5:— | SHA256:— | |||
| 2912 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\sw[1].js | text | |
MD5:— | SHA256:— | |||
| 2912 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@zippyshare[2].txt | text | |
MD5:— | SHA256:— | |||
| 2912 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@aliexpress[1].txt | — | |
MD5:— | SHA256:— | |||
| 2912 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\U2ZG9DE0\display[1].php | text | |
MD5:— | SHA256:— | |||
| 2912 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@track.iafov[1].txt | — | |
MD5:— | SHA256:— | |||
| 2912 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\addthis_widget[1].js | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
26
DNS requests
20
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2912 | iexplore.exe | GET | 302 | 184.25.158.9:80 | http://s.click.aliexpress.com/e/bFmyn62G?af=30799&dp=HO__10474__10274b7031a922ce43435a84abbbae&cv=&u_id= | US | — | — | whitelisted |
2912 | iexplore.exe | GET | 200 | 185.50.68.110:80 | http://ads.socibox.net/ad/300x250.php | TR | html | 826 b | suspicious |
2912 | iexplore.exe | GET | 302 | 184.25.158.9:80 | http://s.click.aliexpress.com/e/NBPH0WG?bz=300*250 | US | — | — | whitelisted |
2912 | iexplore.exe | GET | 302 | 34.253.156.154:80 | http://track.iafov.com/aff_c?offer_id=10474&aff_id=30799&aff_click_id=5b9bd318067a2c00010a6860 | IE | html | 300 b | unknown |
544 | iexplore.exe | GET | 200 | 131.253.33.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
544 | iexplore.exe | 131.253.33.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2912 | iexplore.exe | 104.111.228.202:443 | s7.addthis.com | Akamai International B.V. | NL | whitelisted |
2912 | iexplore.exe | 172.217.18.3:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
2912 | iexplore.exe | 108.168.193.189:443 | beta.mybestmv.com | SoftLayer Technologies Inc. | US | suspicious |
2912 | iexplore.exe | 212.32.252.65:443 | reklamstore.go2affise.com | LeaseWeb Netherlands B.V. | NL | unknown |
2912 | iexplore.exe | 23.45.98.42:443 | www.gearbest.com | Akamai International B.V. | NL | whitelisted |
2912 | iexplore.exe | 104.16.118.230:443 | velocecdn.com | Cloudflare Inc | US | shared |
2912 | iexplore.exe | 185.50.68.110:80 | ads.socibox.net | Istanbuldc Veri Merkezi Ltd. Sti | TR | suspicious |
2912 | iexplore.exe | 104.111.216.213:443 | ae01.alicdn.com | Akamai International B.V. | NL | whitelisted |
2912 | iexplore.exe | 172.217.22.100:443 | www.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
www103.zippyshare.com |
| unknown |
p232207.clksite.com |
| whitelisted |
d10lumateci472.cloudfront.net |
| whitelisted |
www.maxonclick.com |
| whitelisted |
s7.addthis.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
beta.mybestmv.com |
| malicious |
mybestmv.com |
| unknown |
fonts.gstatic.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2912 | iexplore.exe | Potentially Bad Traffic | ET INFO Multiple Javascript Unescapes - Common Obfuscation Observed in Phish Landing |