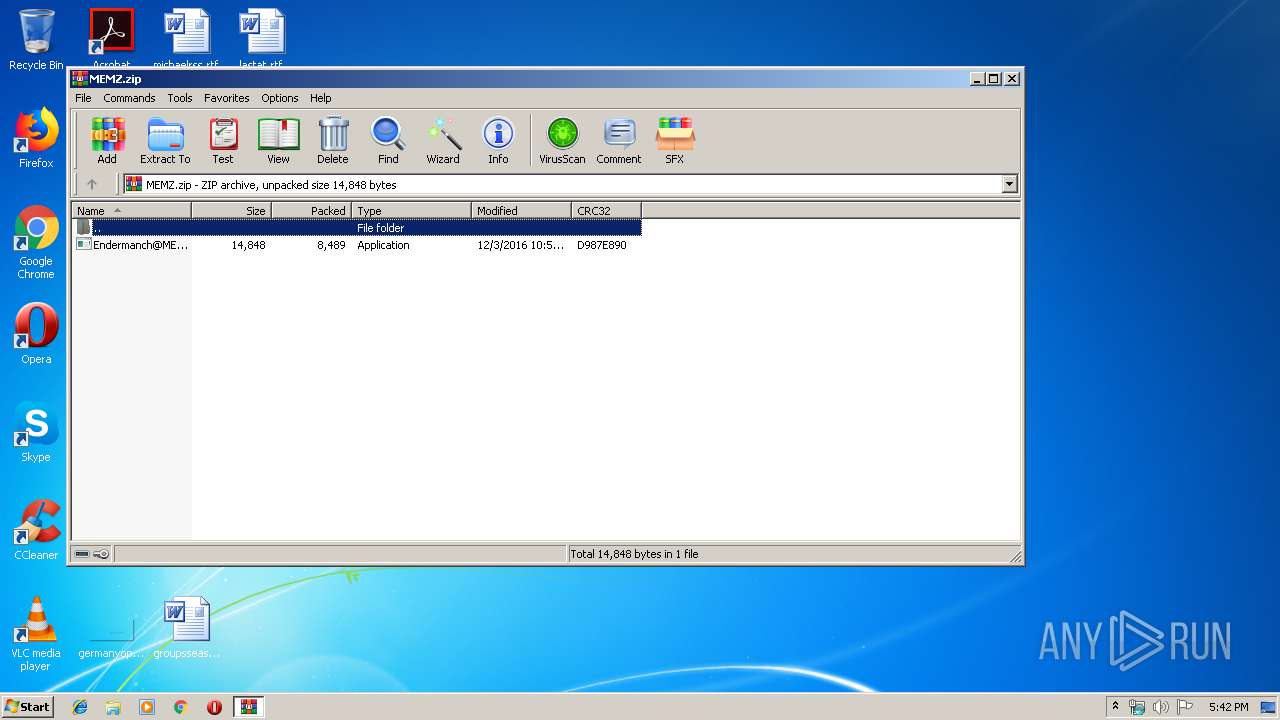
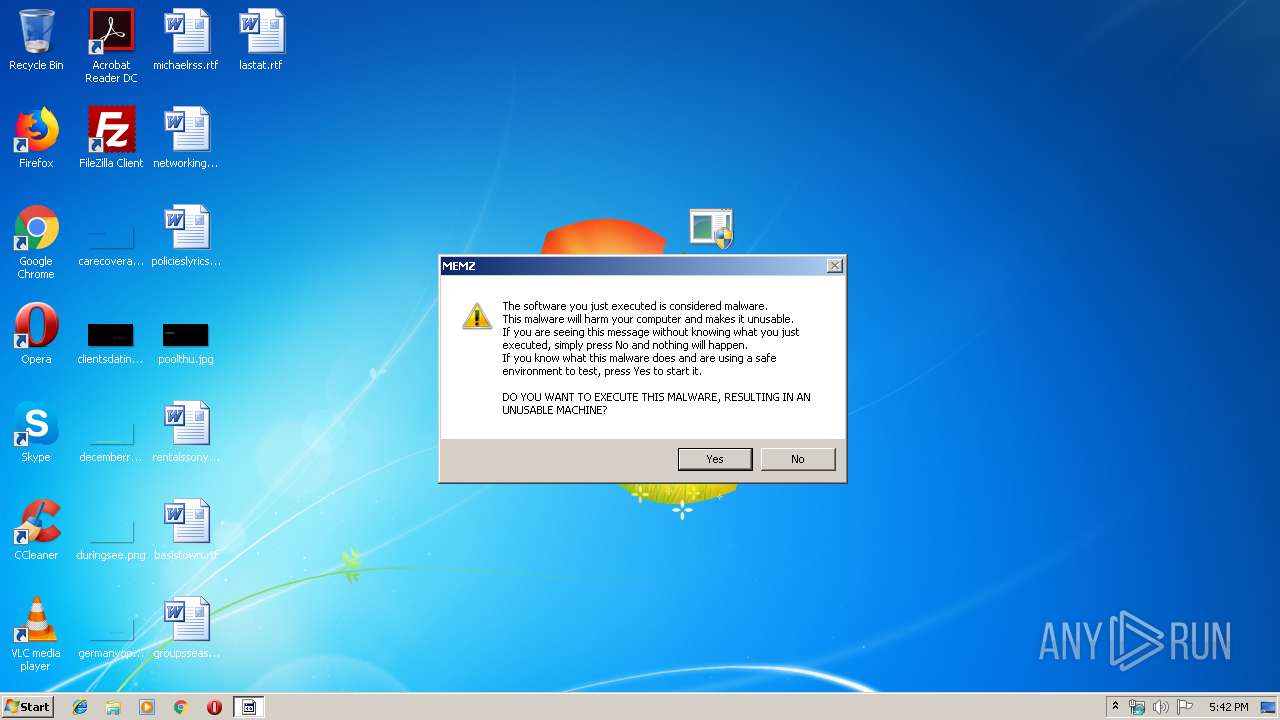
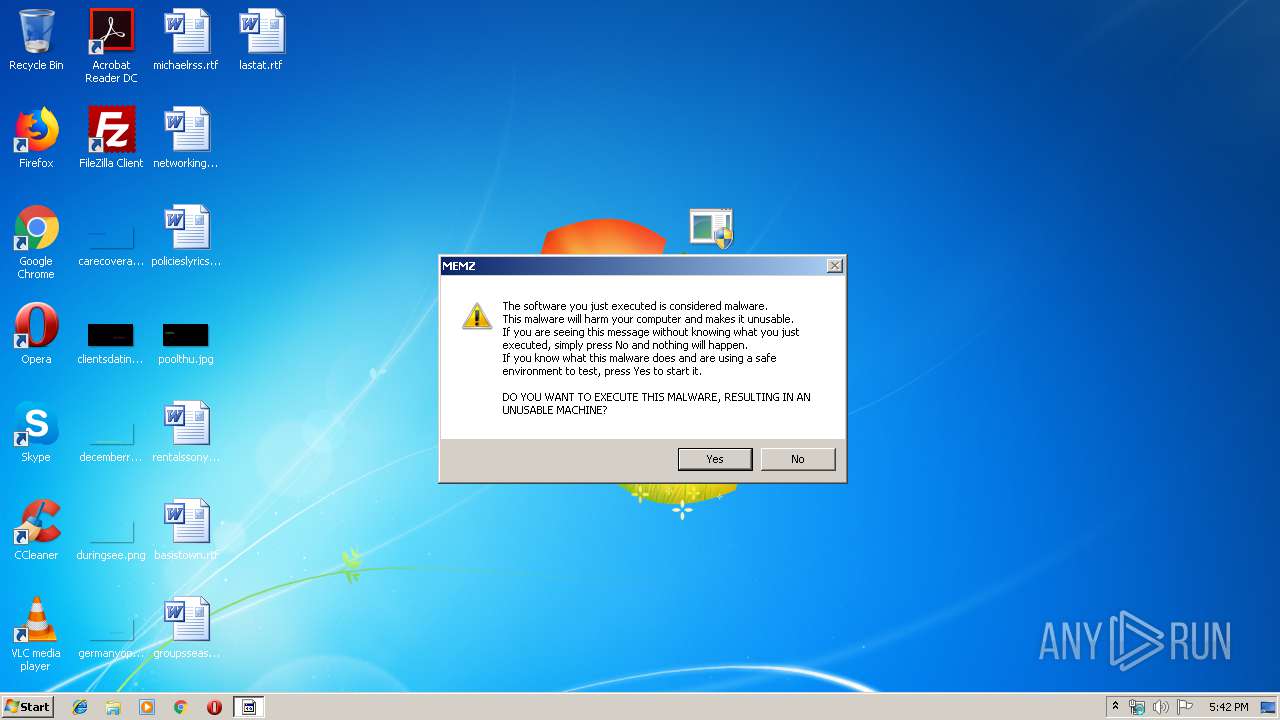
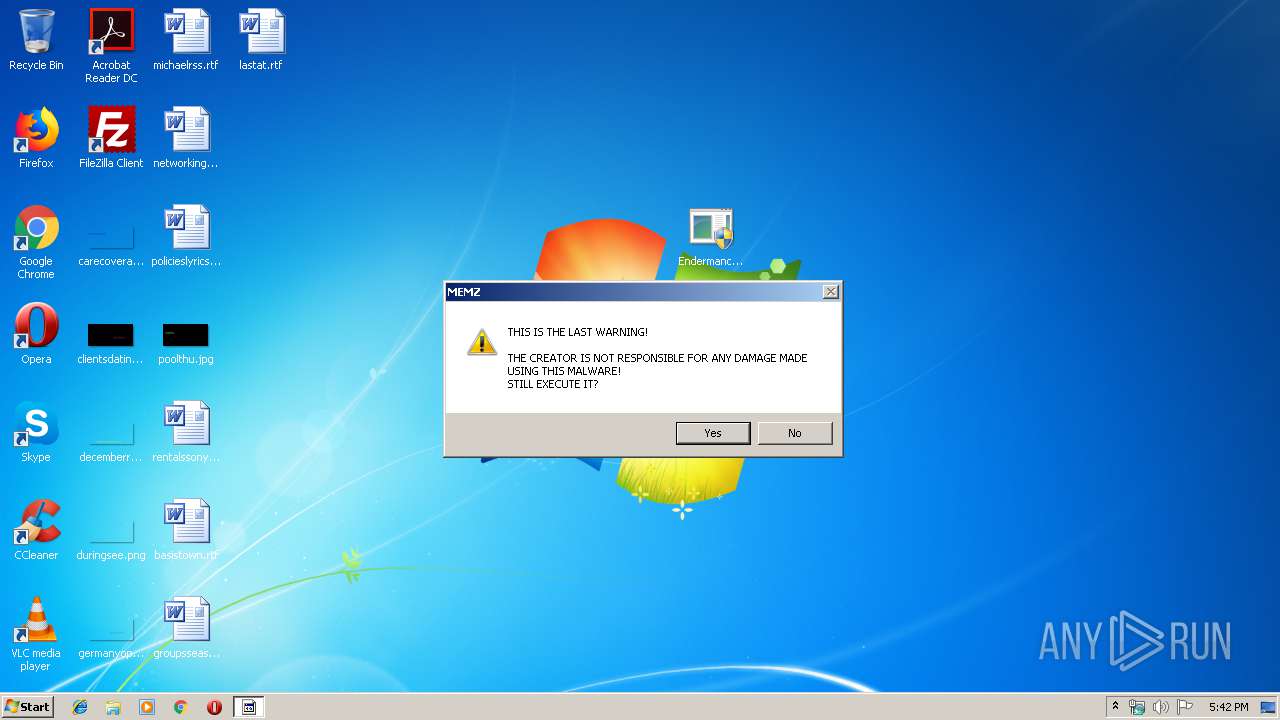
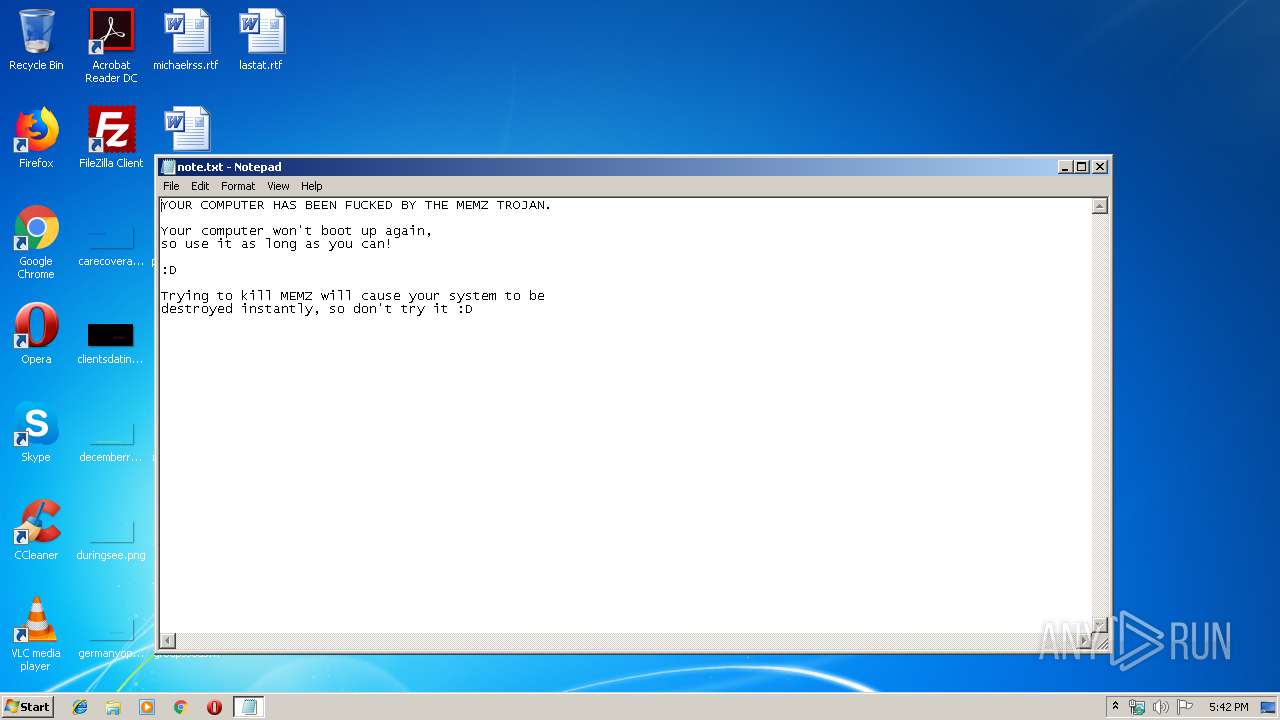
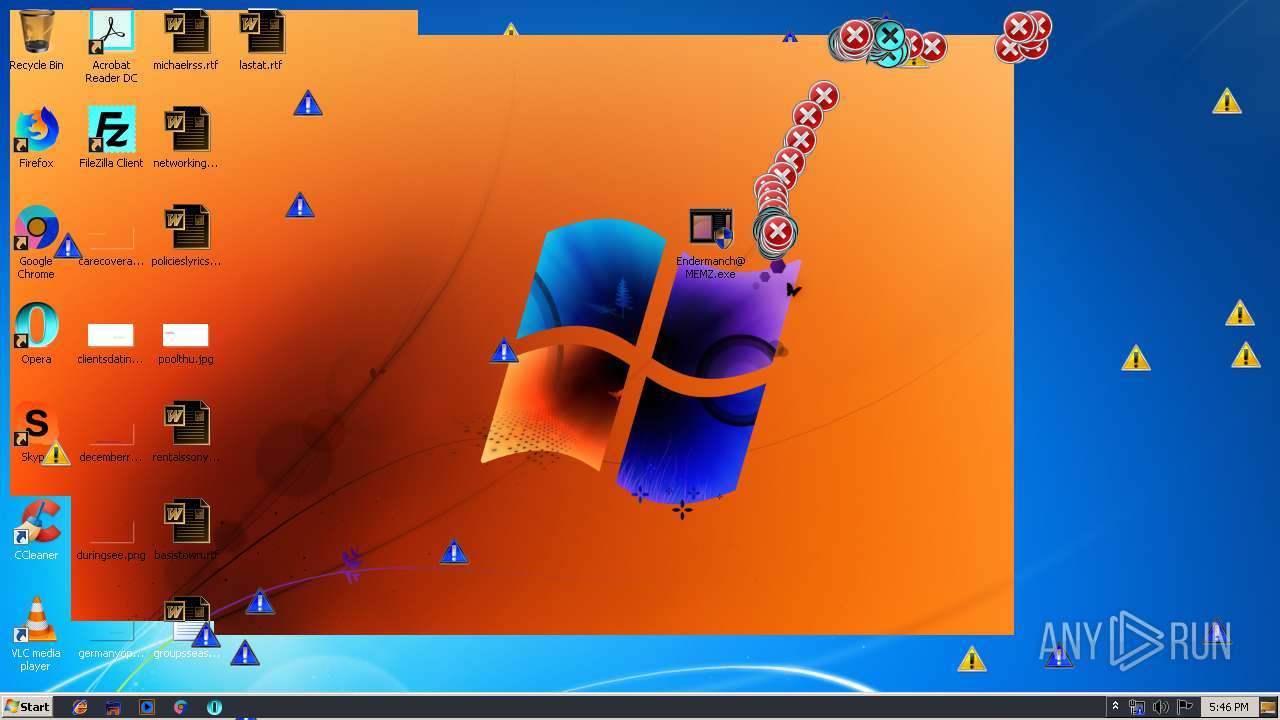
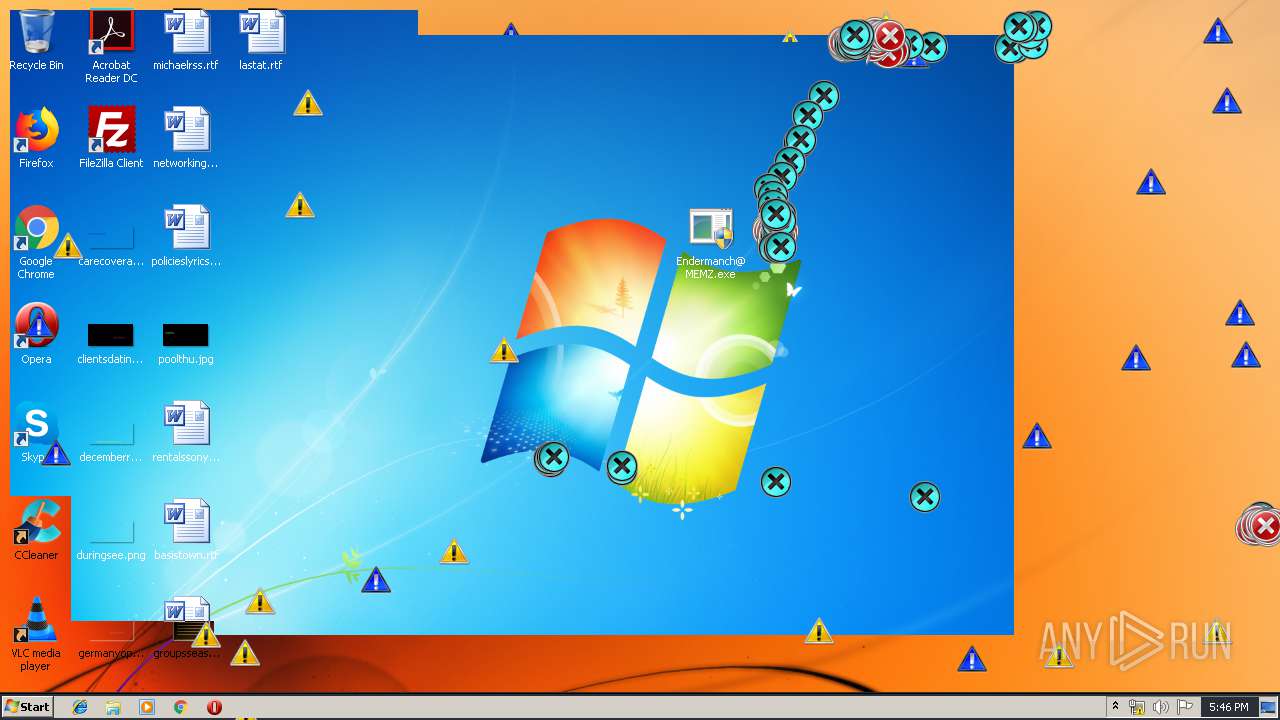
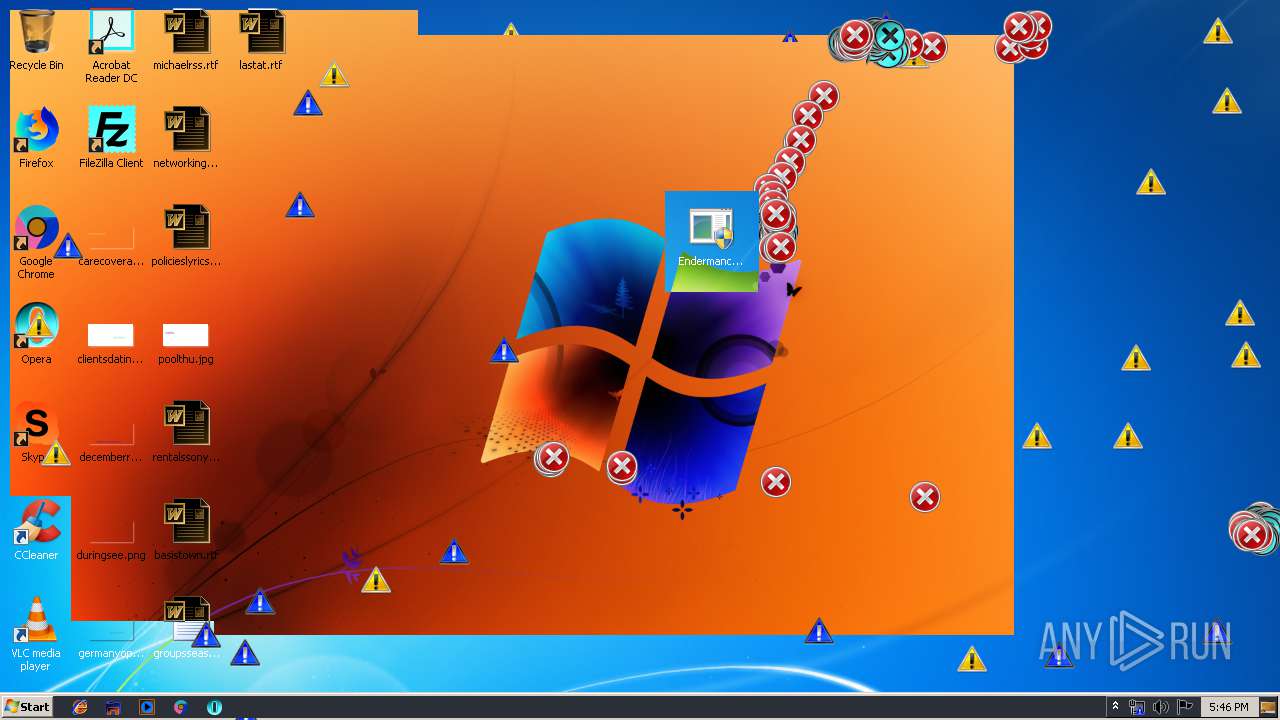
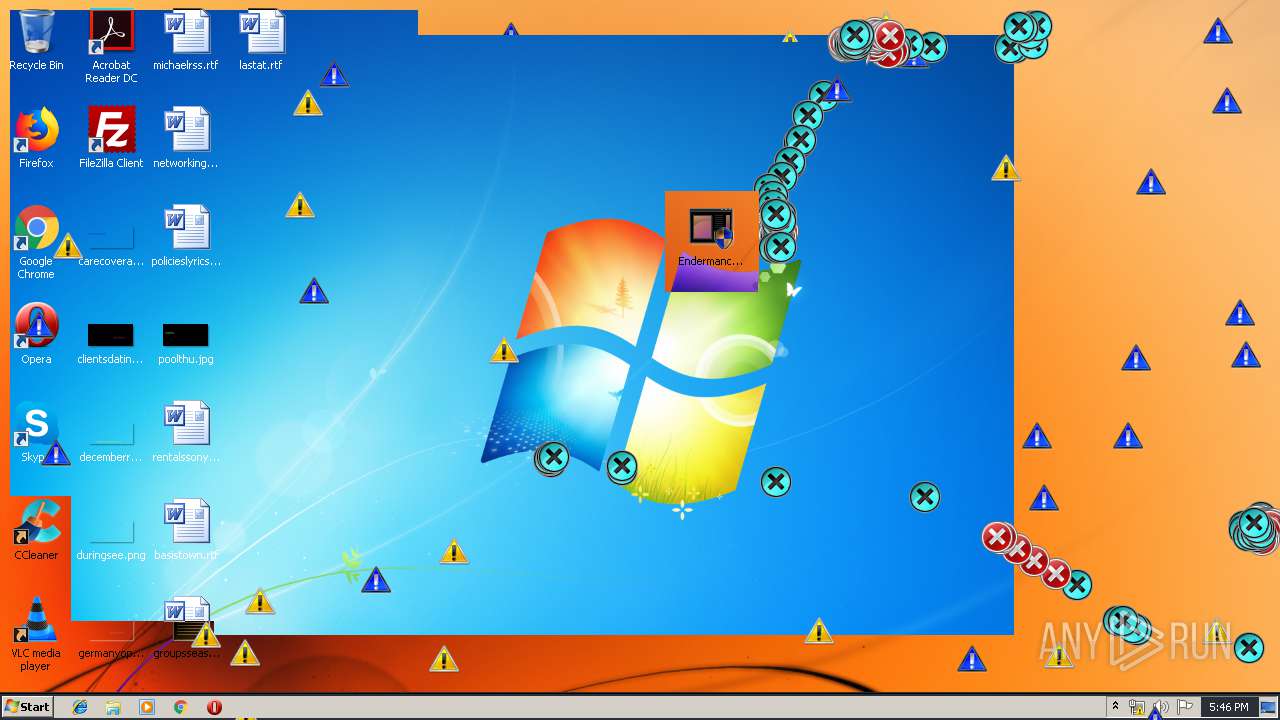
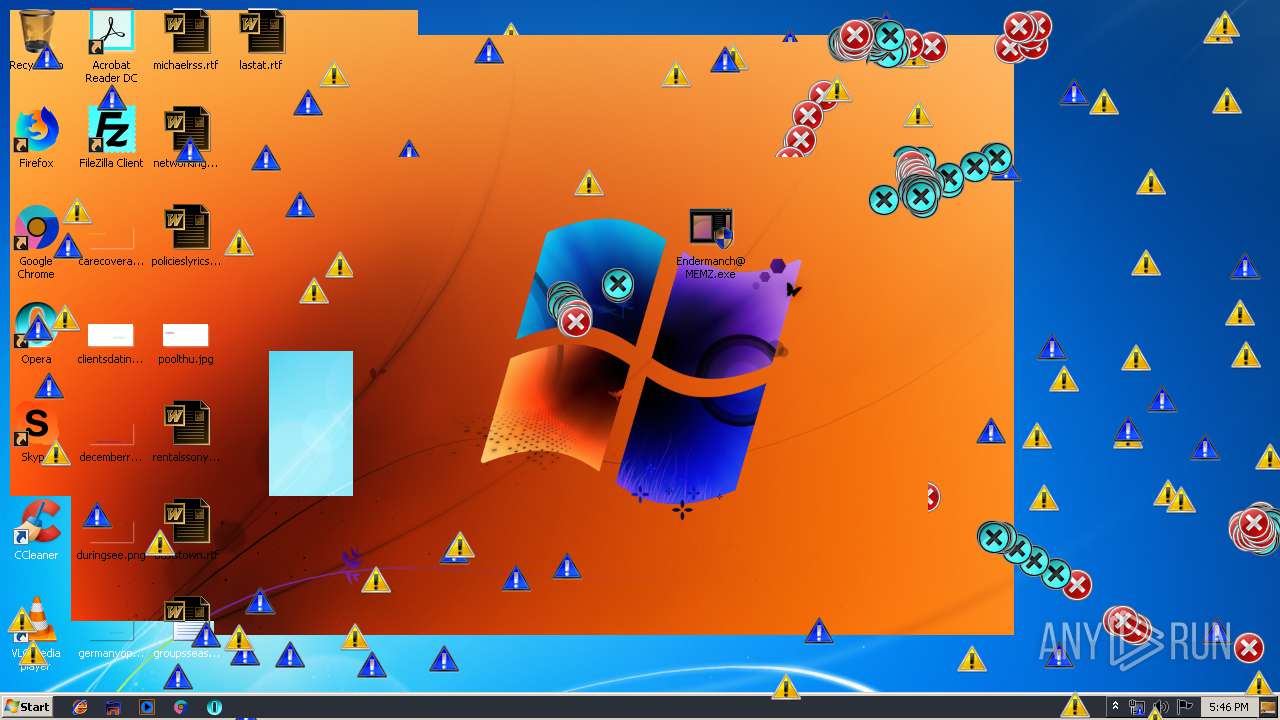
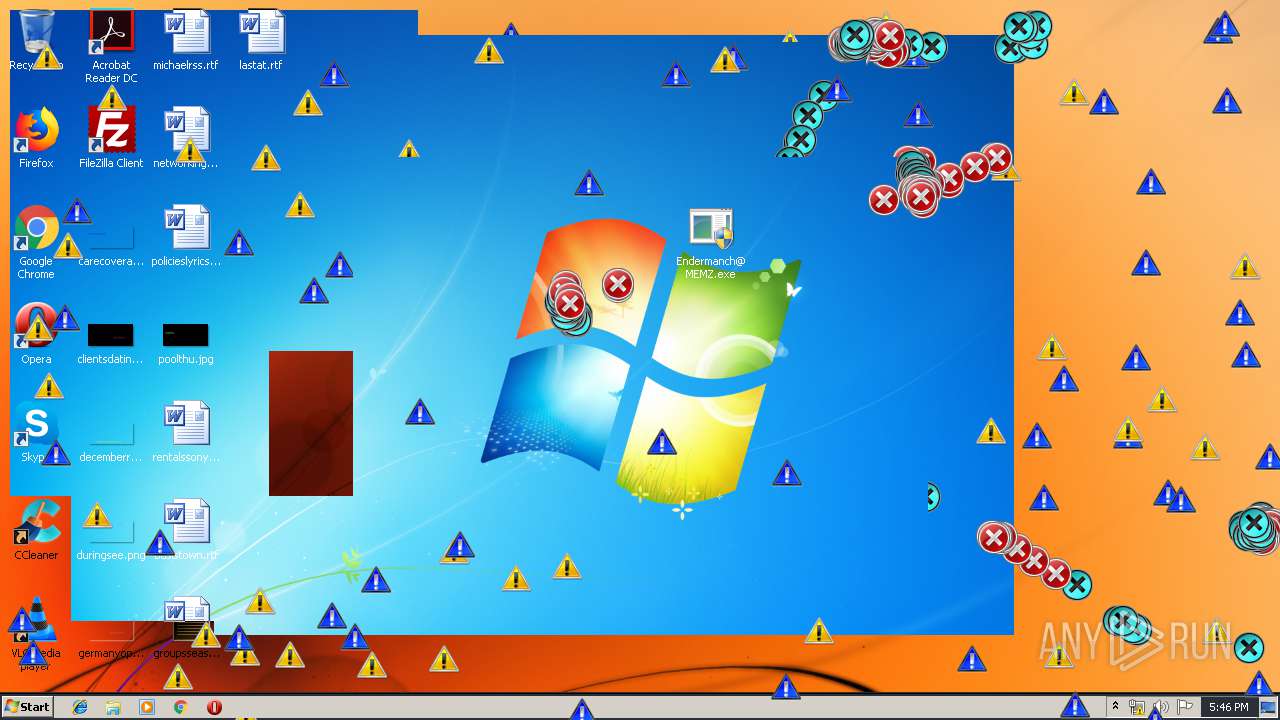
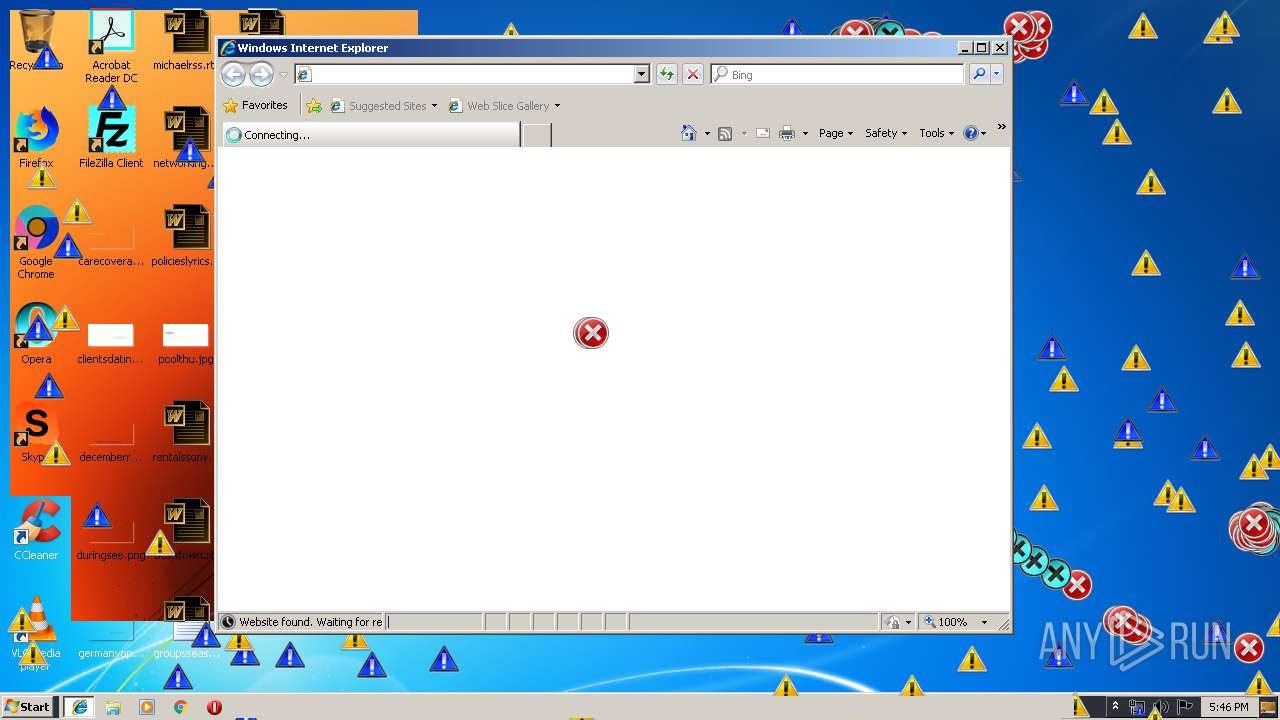
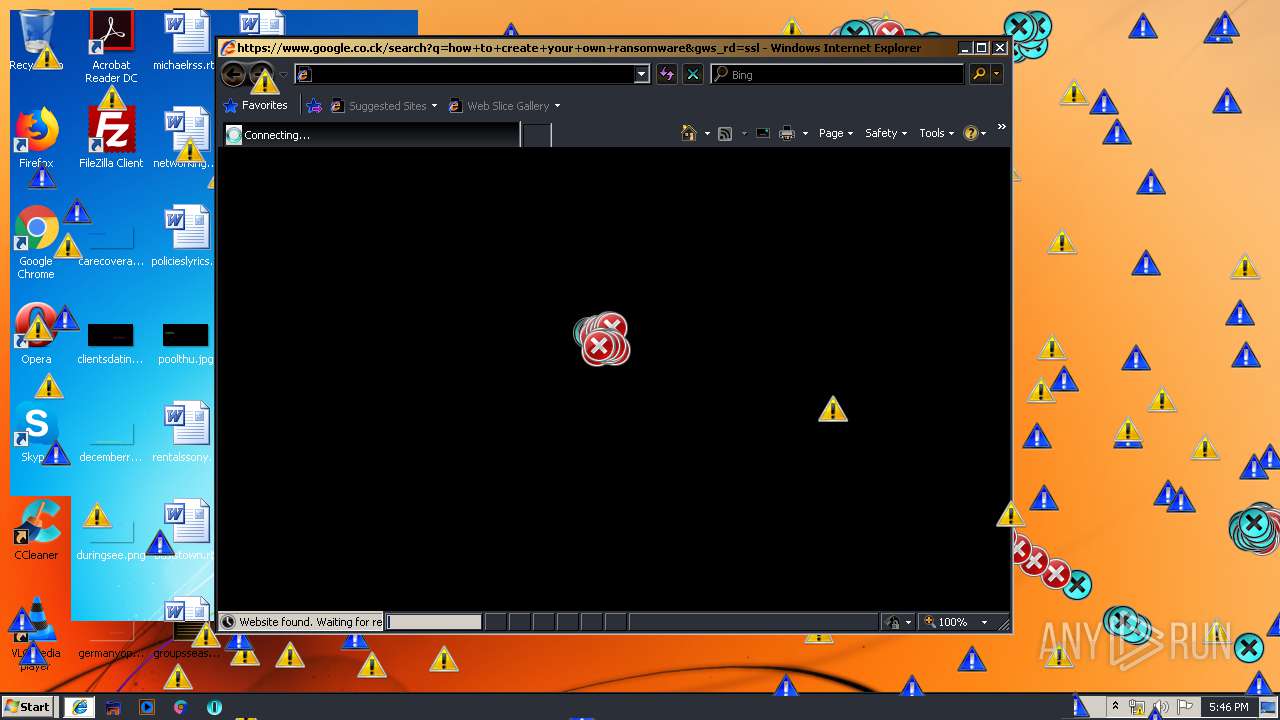
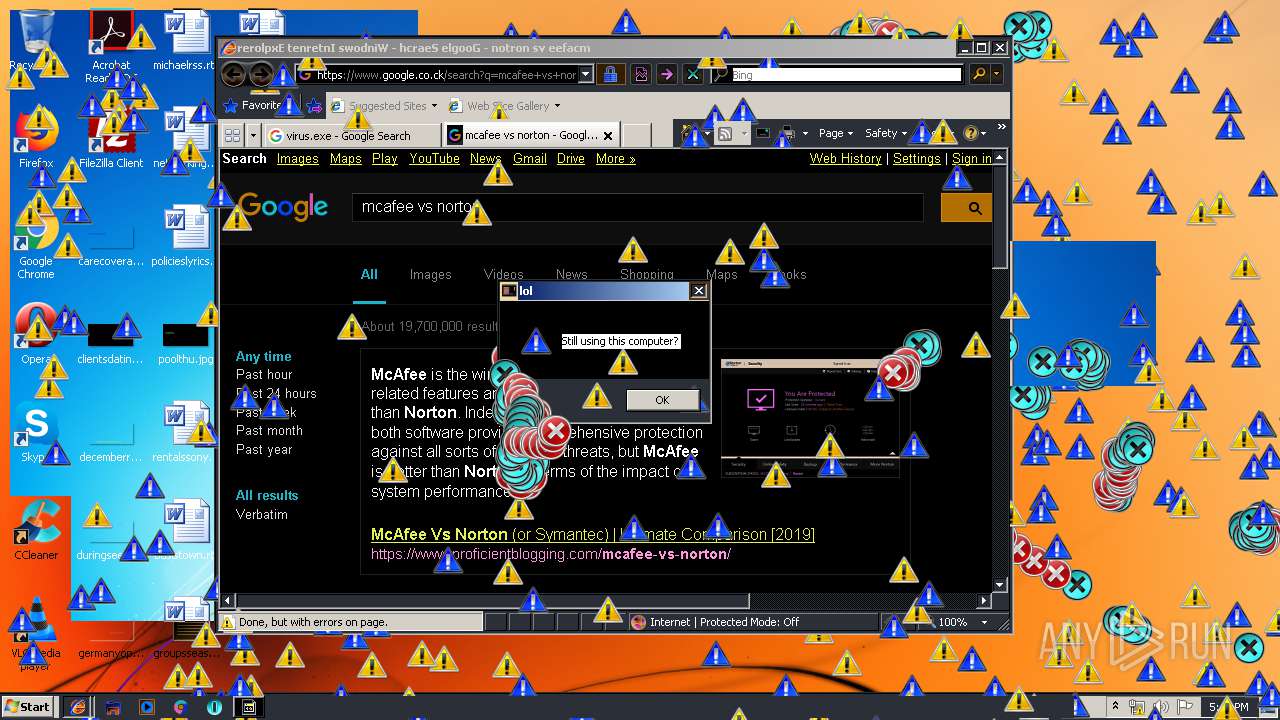
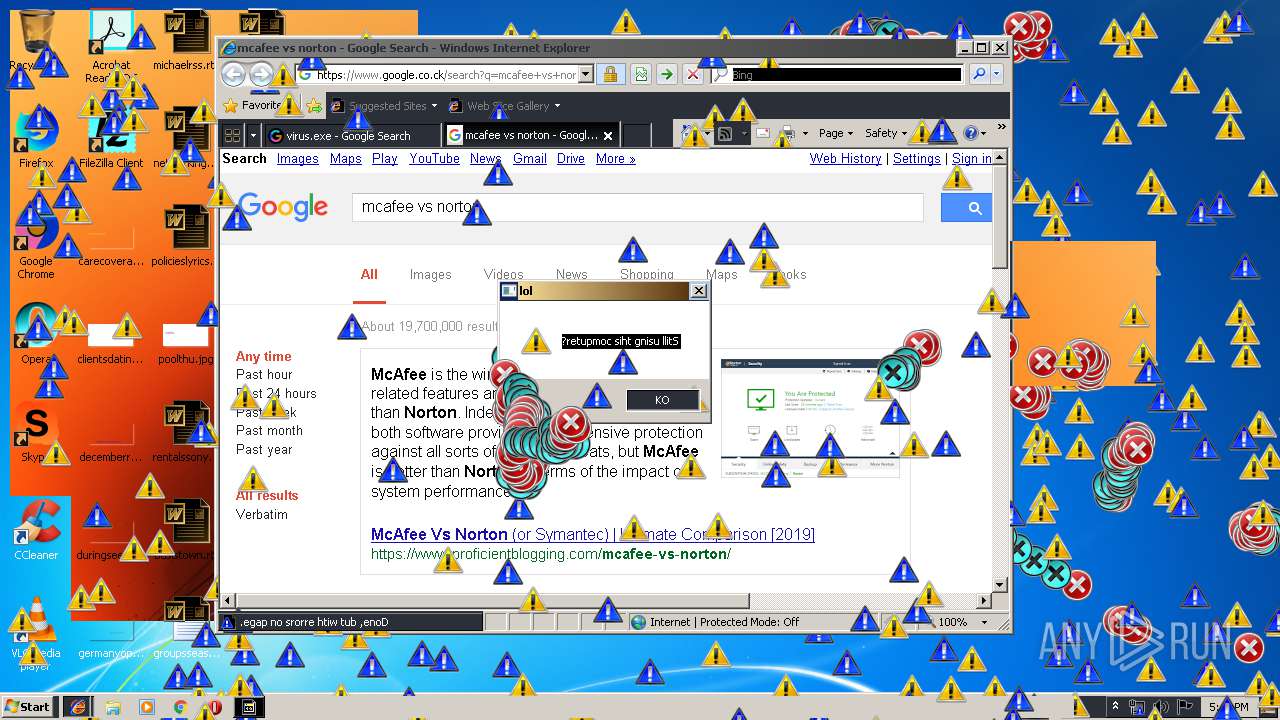
| download: | MEMZ.zip |
| Full analysis: | https://app.any.run/tasks/d82e0762-1c20-45b1-8b49-fa14effcda16 |
| Verdict: | Malicious activity |
| Analysis date: | October 14, 2019, 16:41:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 69977A5D1C648976D47B69EA3AA8FCAA |
| SHA1: | 4630CC15000C0D3149350B9ECDA6CFC8F402938A |
| SHA256: | 61CA4D8DD992C763B47BEBB9B5FACB68A59FF0A594C2FF215AA4143B593AE9DC |
| SSDEEP: | 192:8xI2dw4xXlsUjs1ScK3ZeD6dUqENj710+MZ9R1SVBIpp:b2dHiosKA6OqEx2t9R1SLIL |
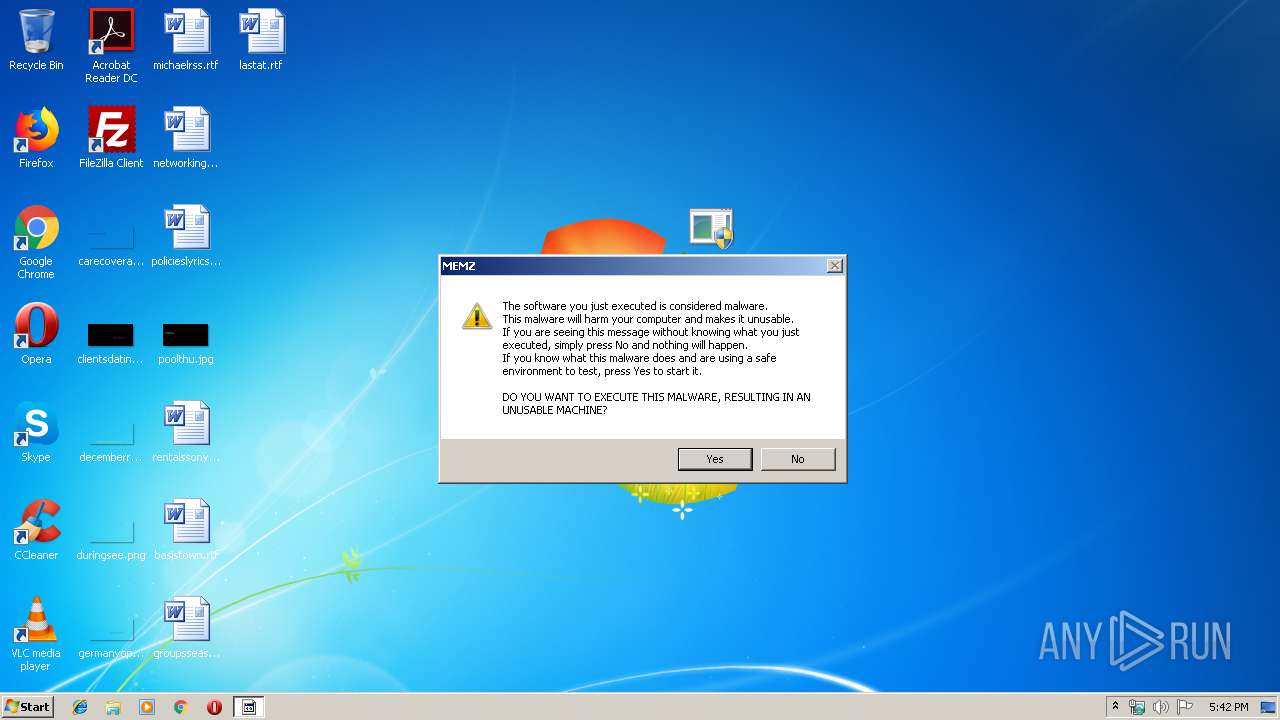
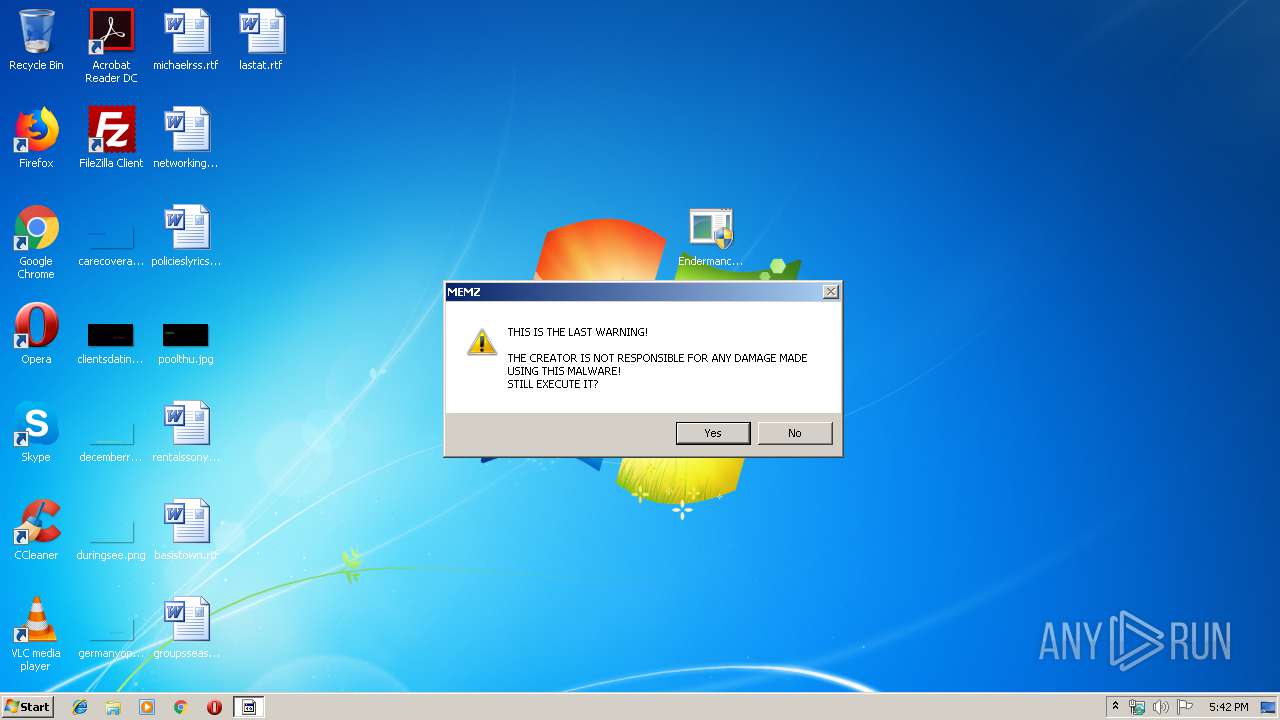
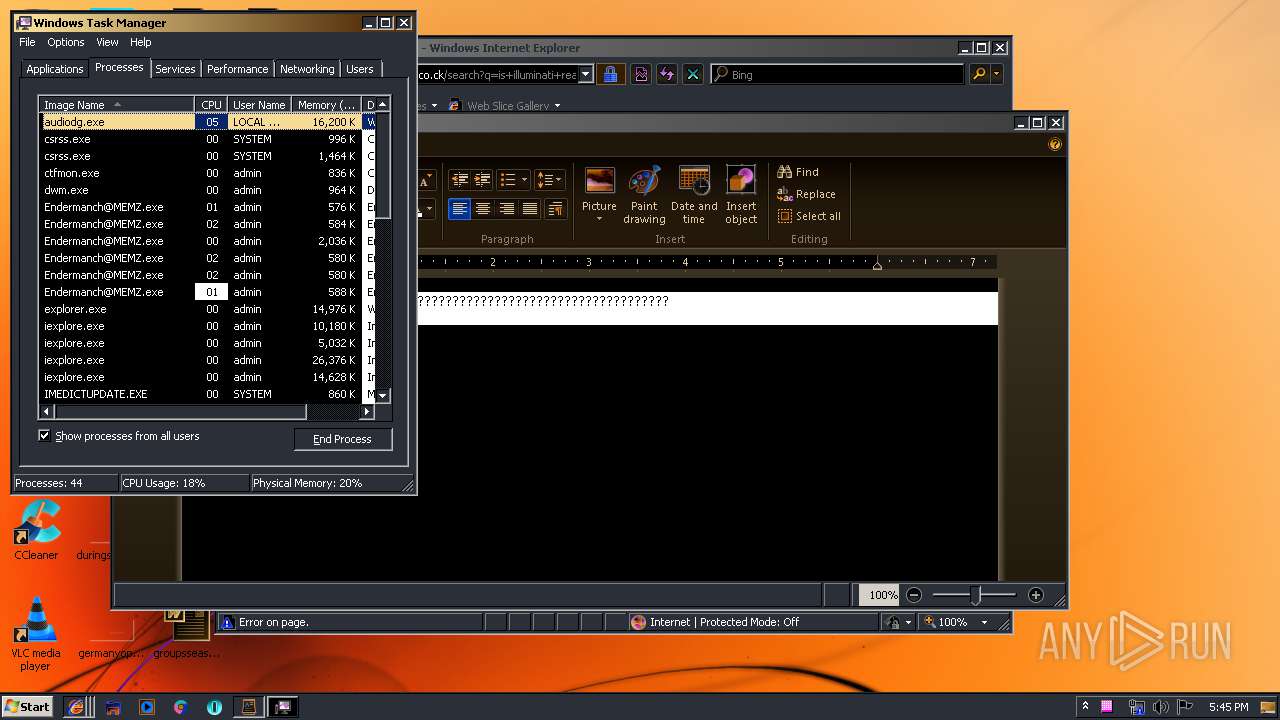
MALICIOUS
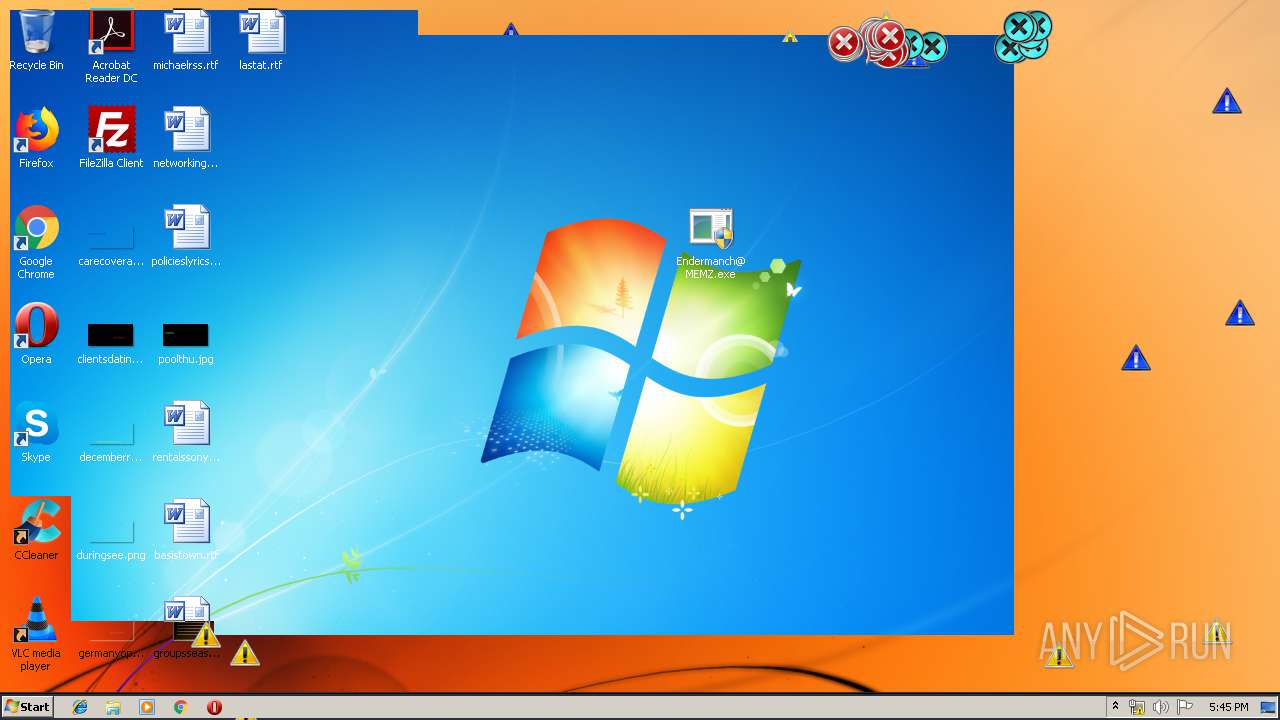
Application was dropped or rewritten from another process
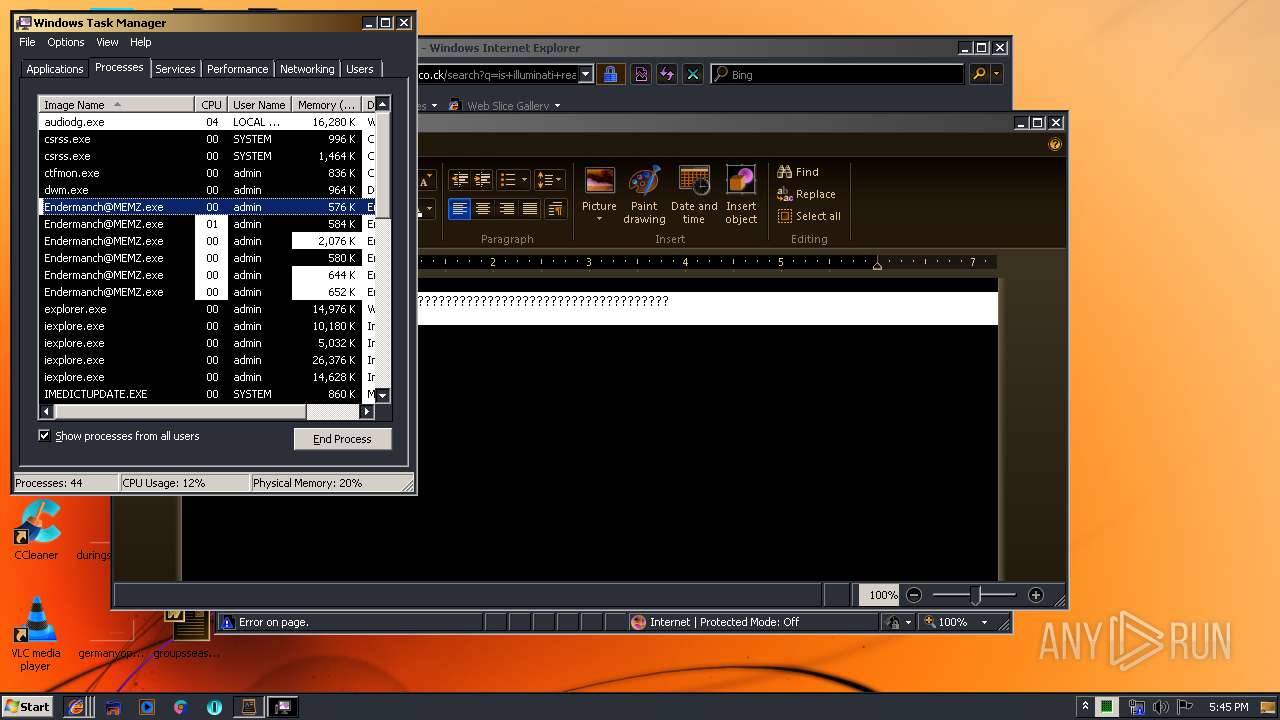
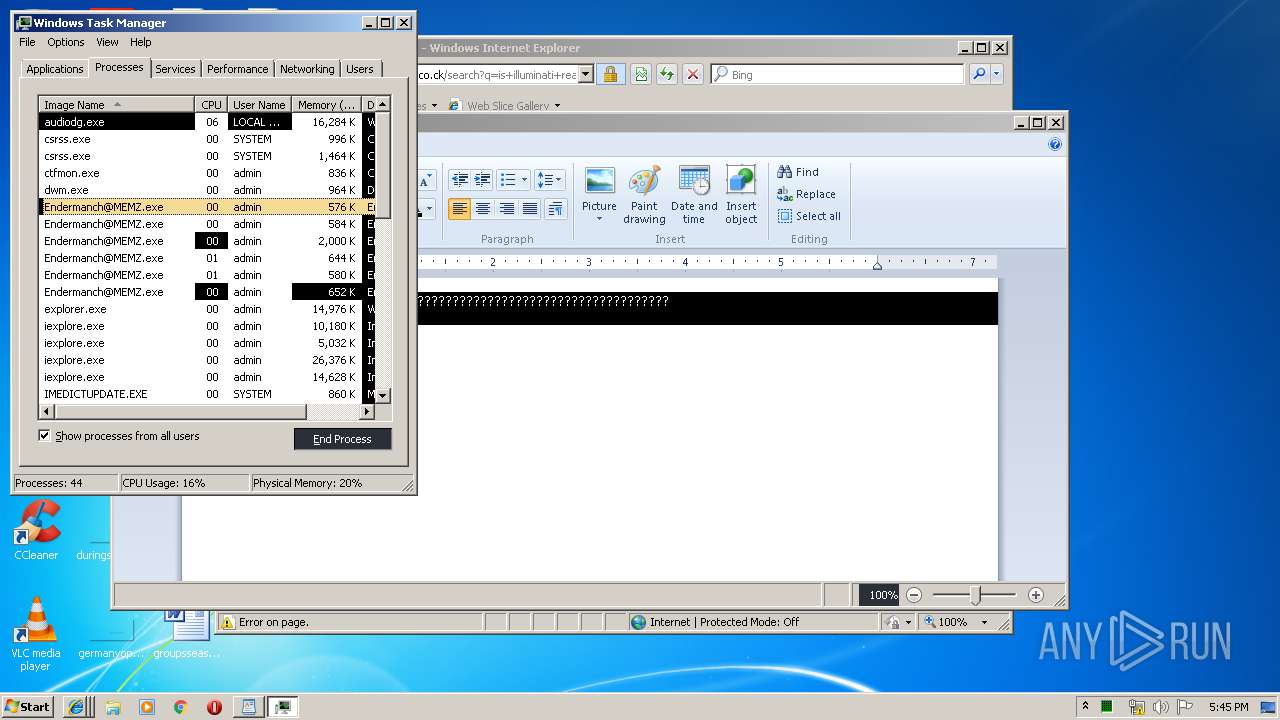
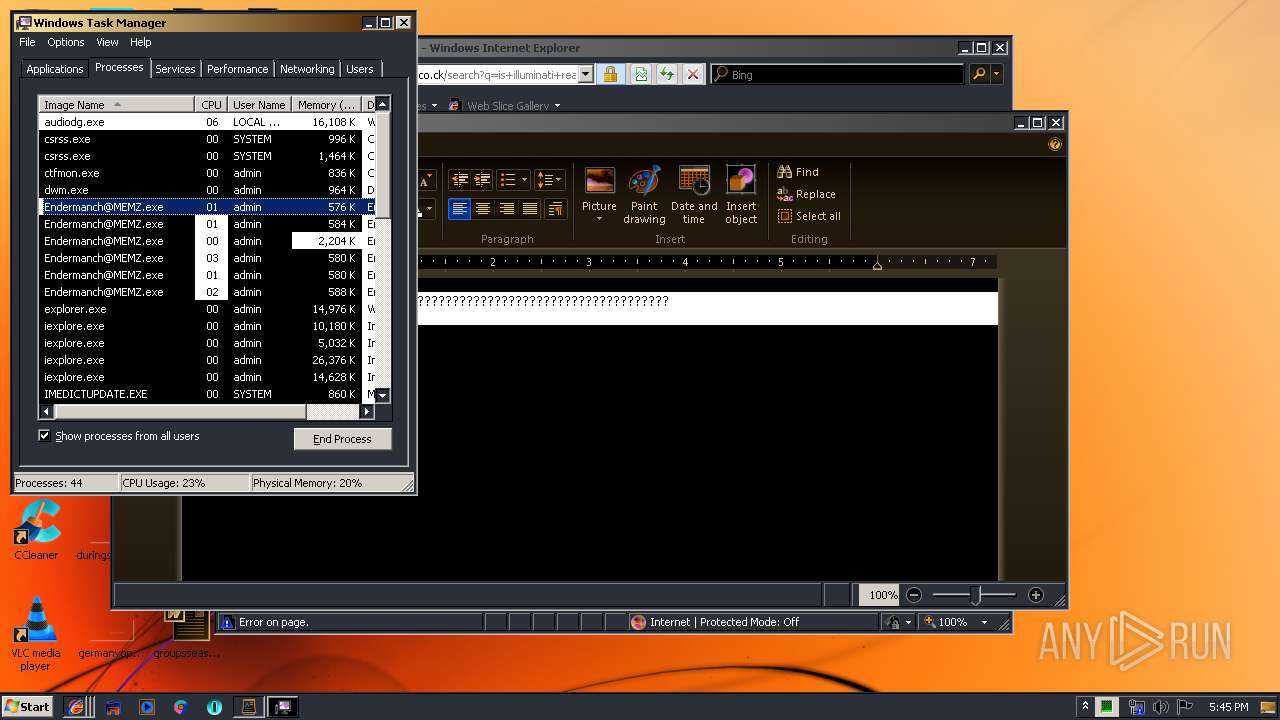
- Endermanch@MEMZ.exe (PID: 3908)
- Endermanch@MEMZ.exe (PID: 2004)
- Endermanch@MEMZ.exe (PID: 2156)
- Endermanch@MEMZ.exe (PID: 1484)
- Endermanch@MEMZ.exe (PID: 3228)
- Endermanch@MEMZ.exe (PID: 2276)
- Endermanch@MEMZ.exe (PID: 2500)
- Endermanch@MEMZ.exe (PID: 3836)
- Endermanch@MEMZ.exe (PID: 4032)
- Endermanch@MEMZ.exe (PID: 2372)
- Endermanch@MEMZ.exe (PID: 2456)
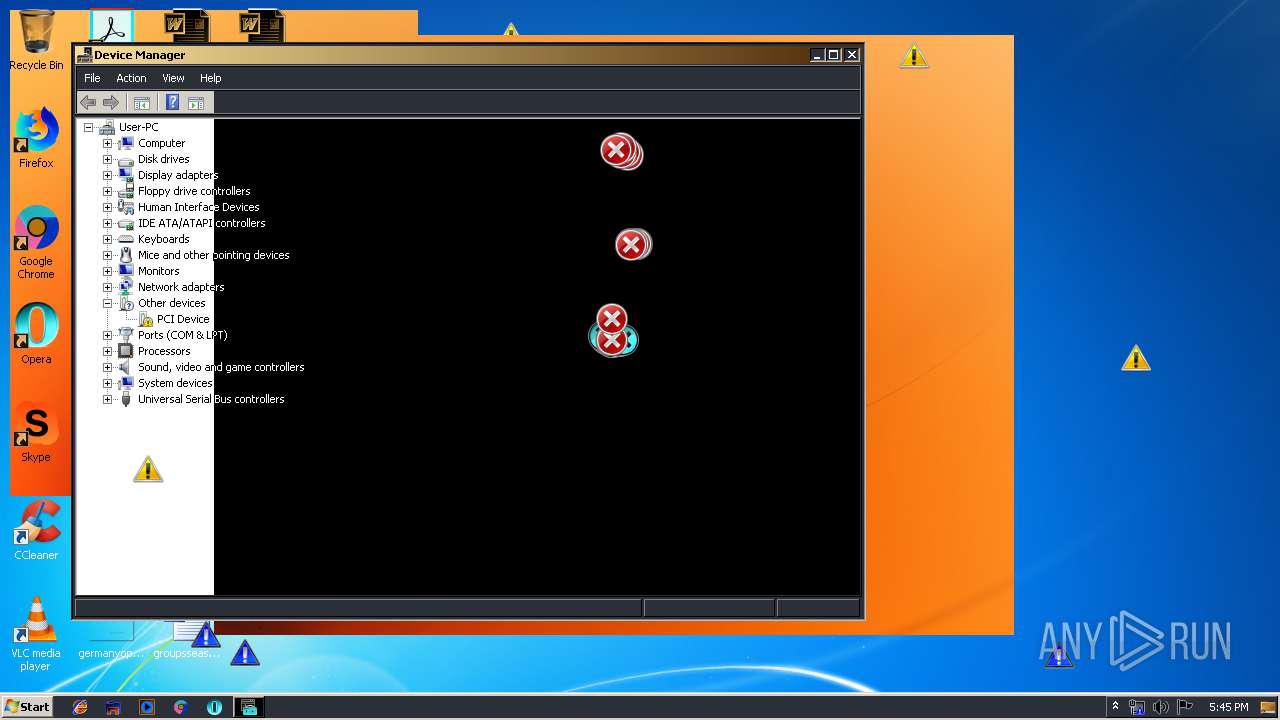
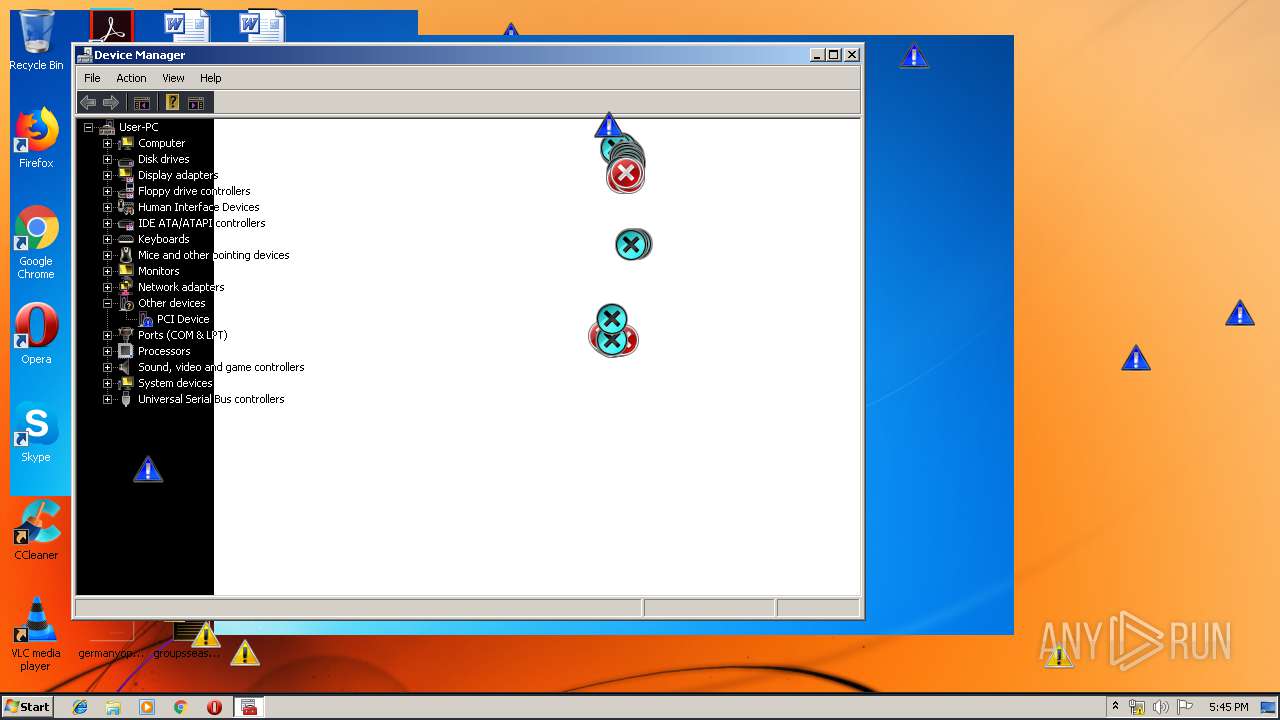
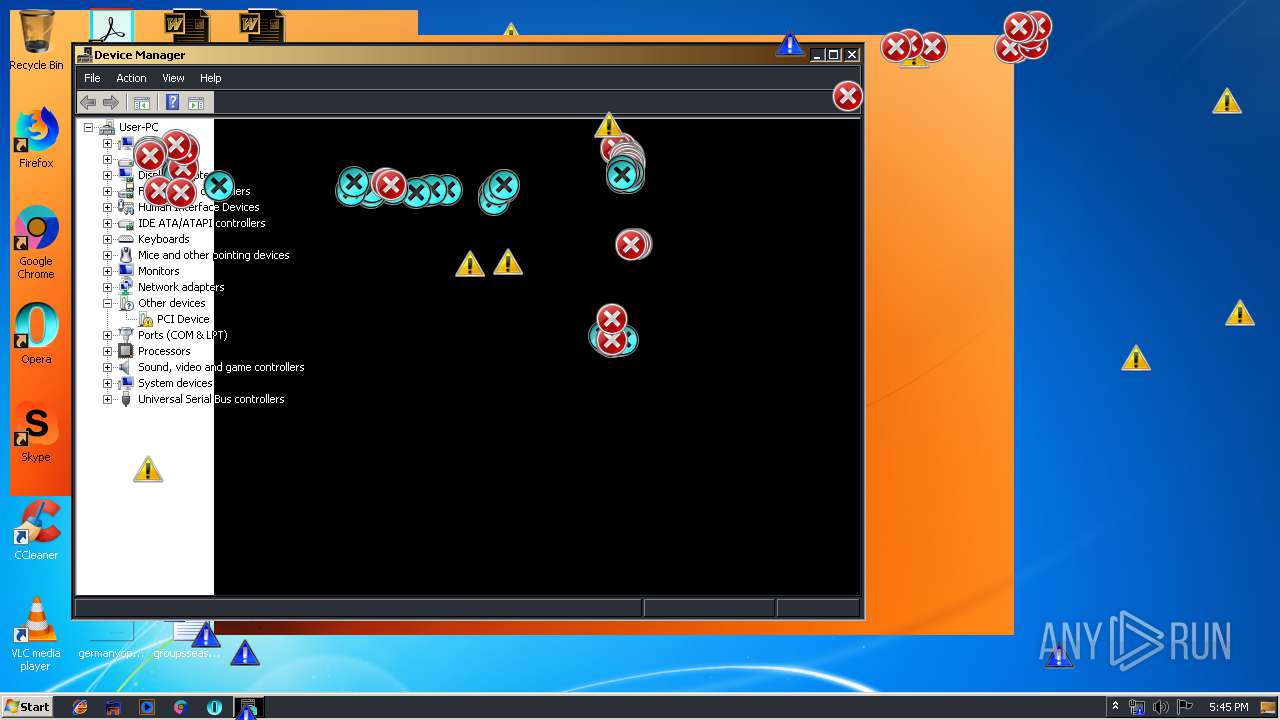
Low-level write access rights to disk partition
- Endermanch@MEMZ.exe (PID: 2372)
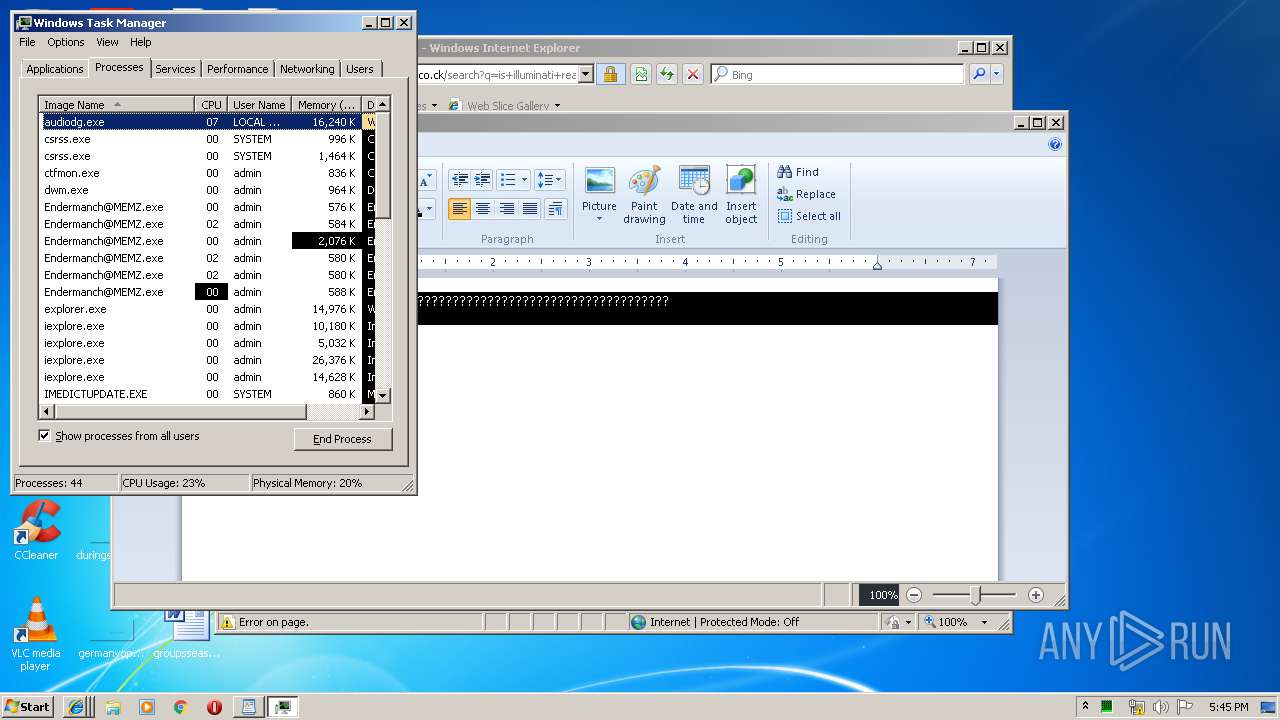
SUSPICIOUS
Application launched itself
- Endermanch@MEMZ.exe (PID: 3228)
Low-level read access rights to disk partition
- Endermanch@MEMZ.exe (PID: 2372)
- msconfig.exe (PID: 2160)
Creates files in the user directory
- Endermanch@MEMZ.exe (PID: 2372)
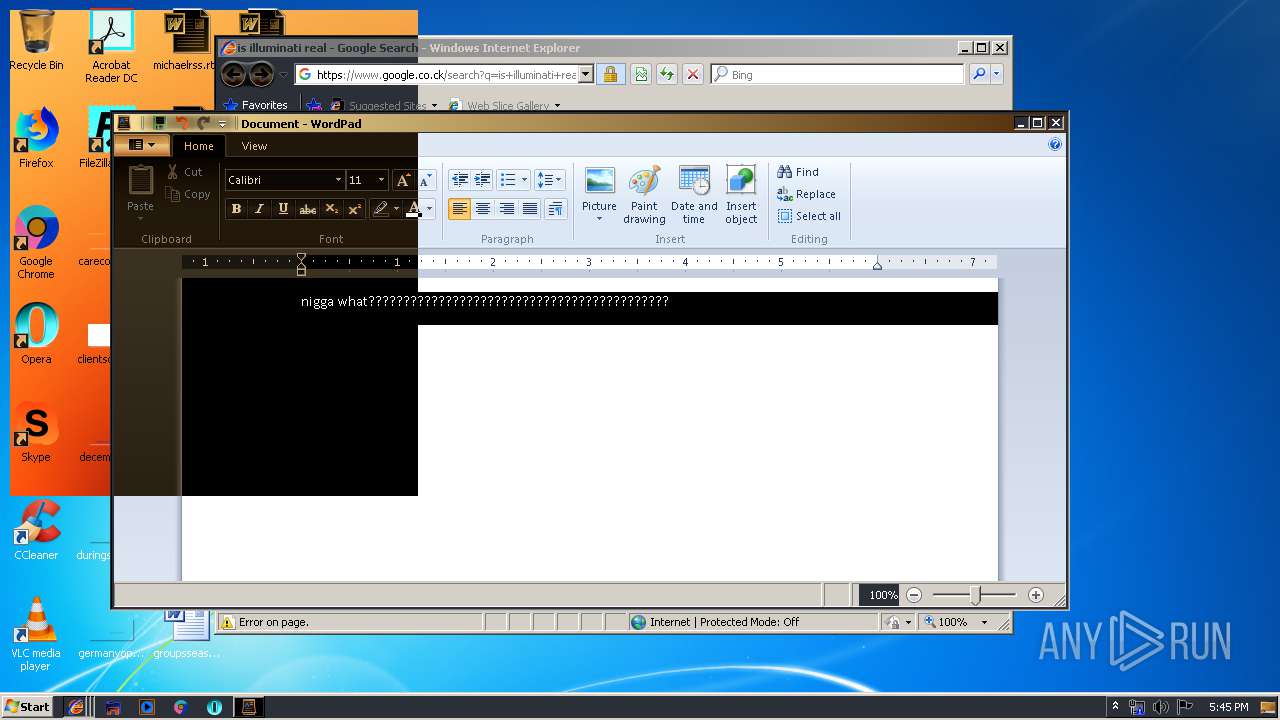
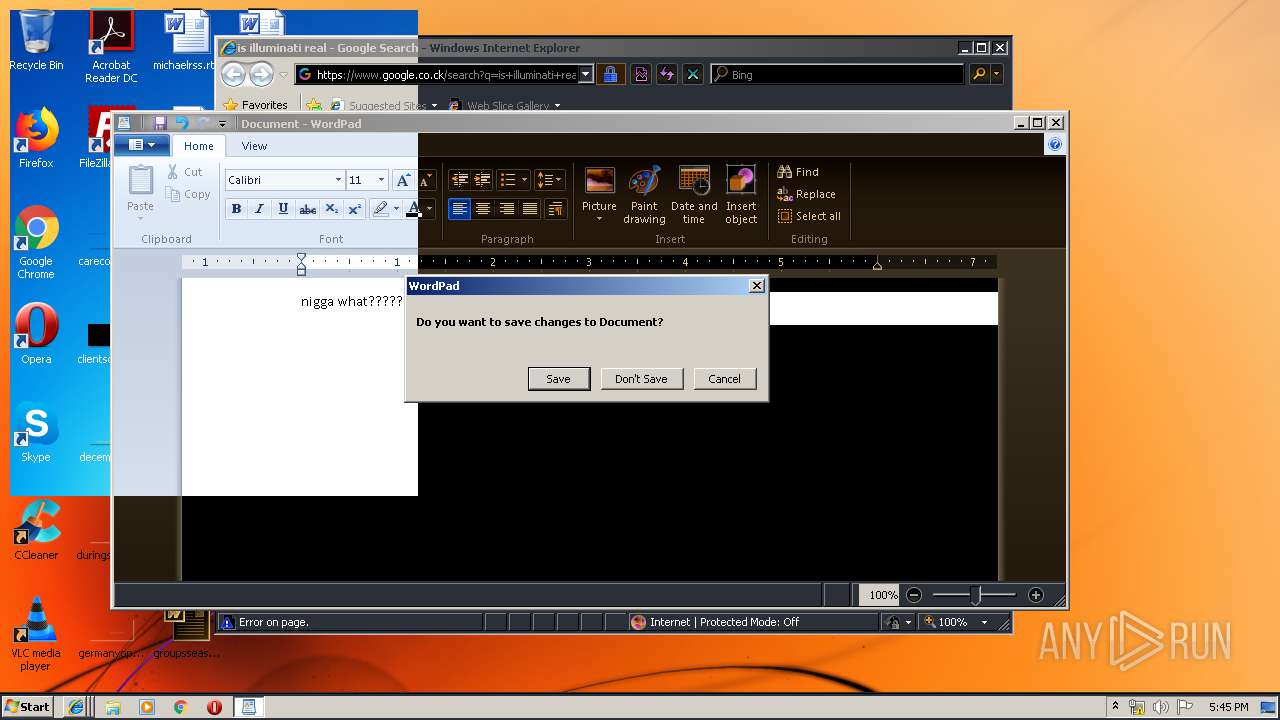
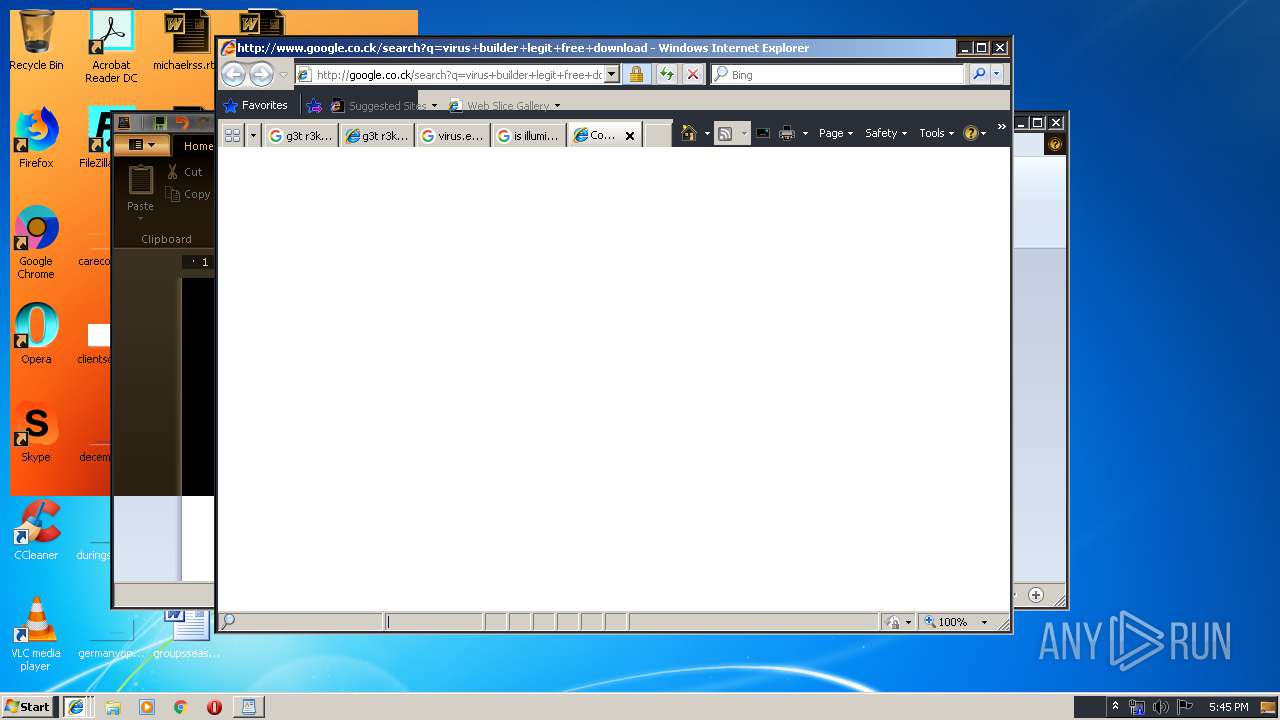
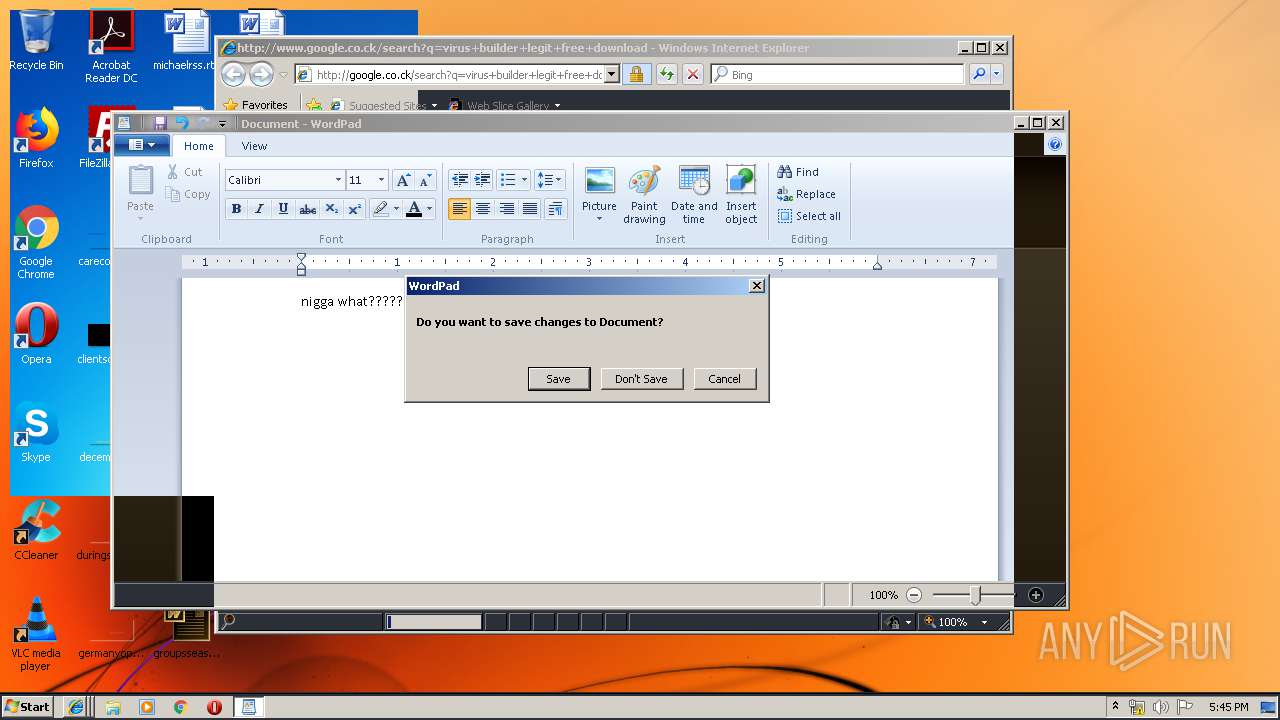
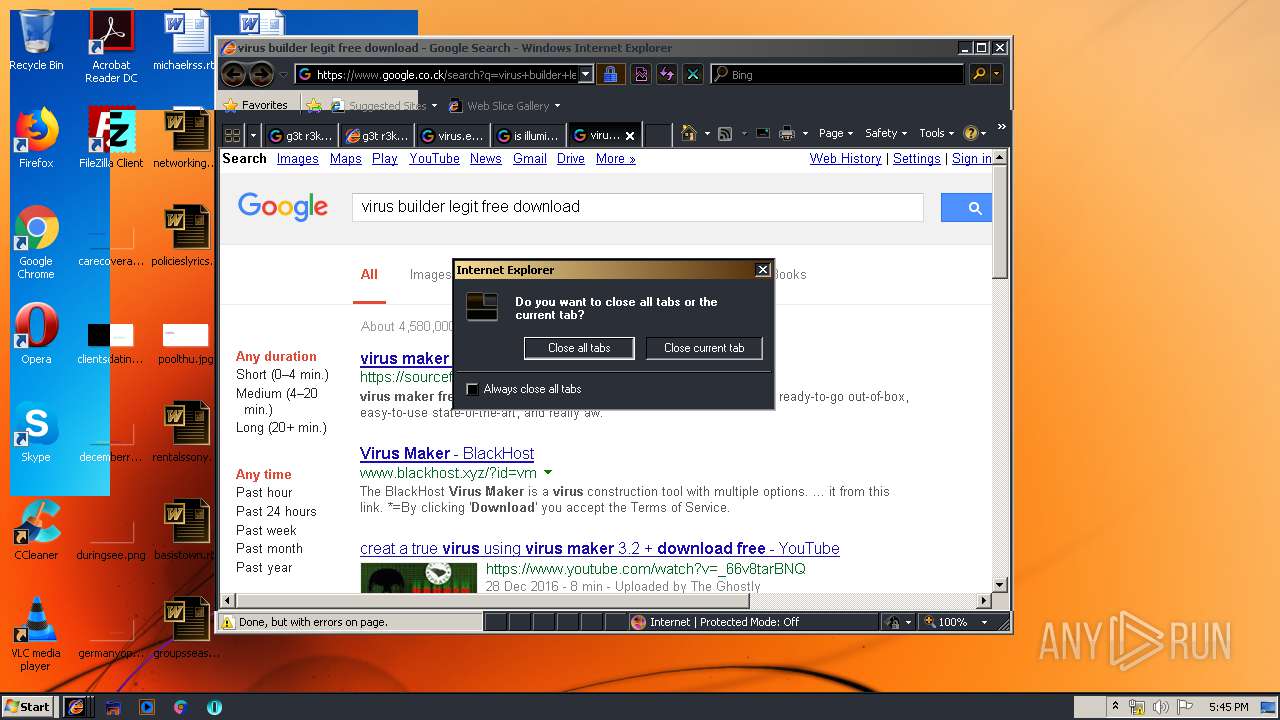
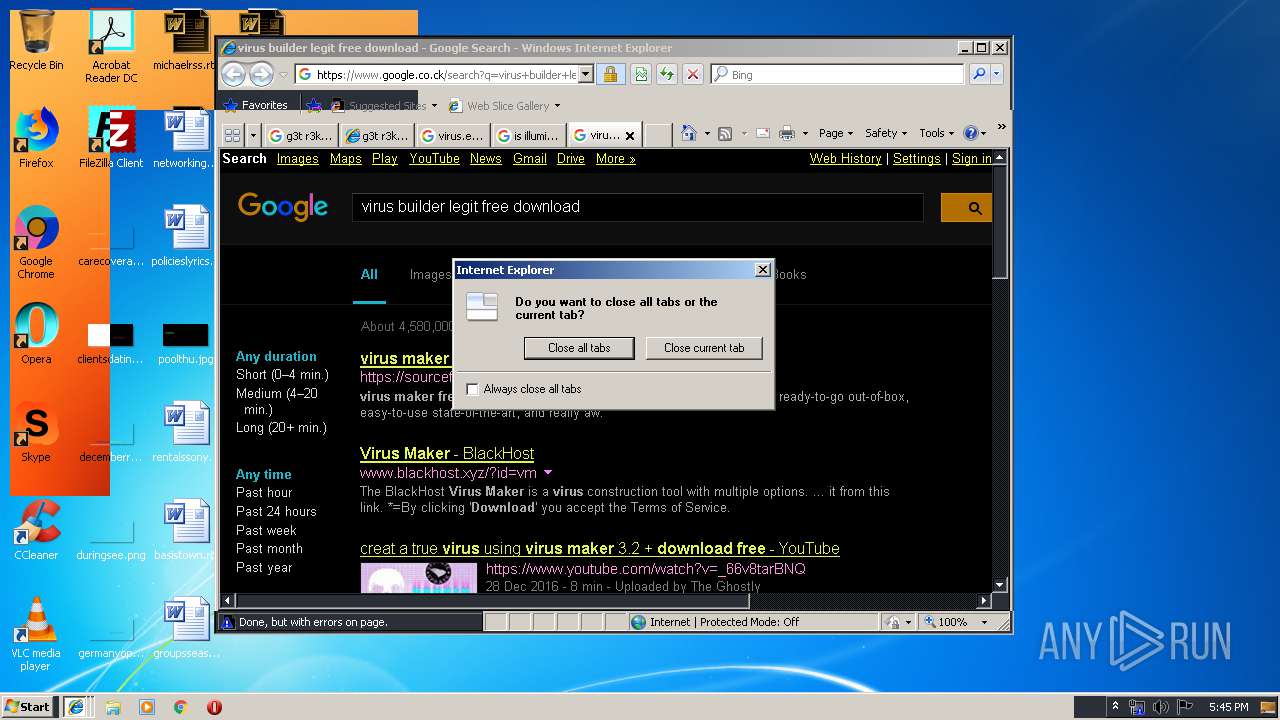
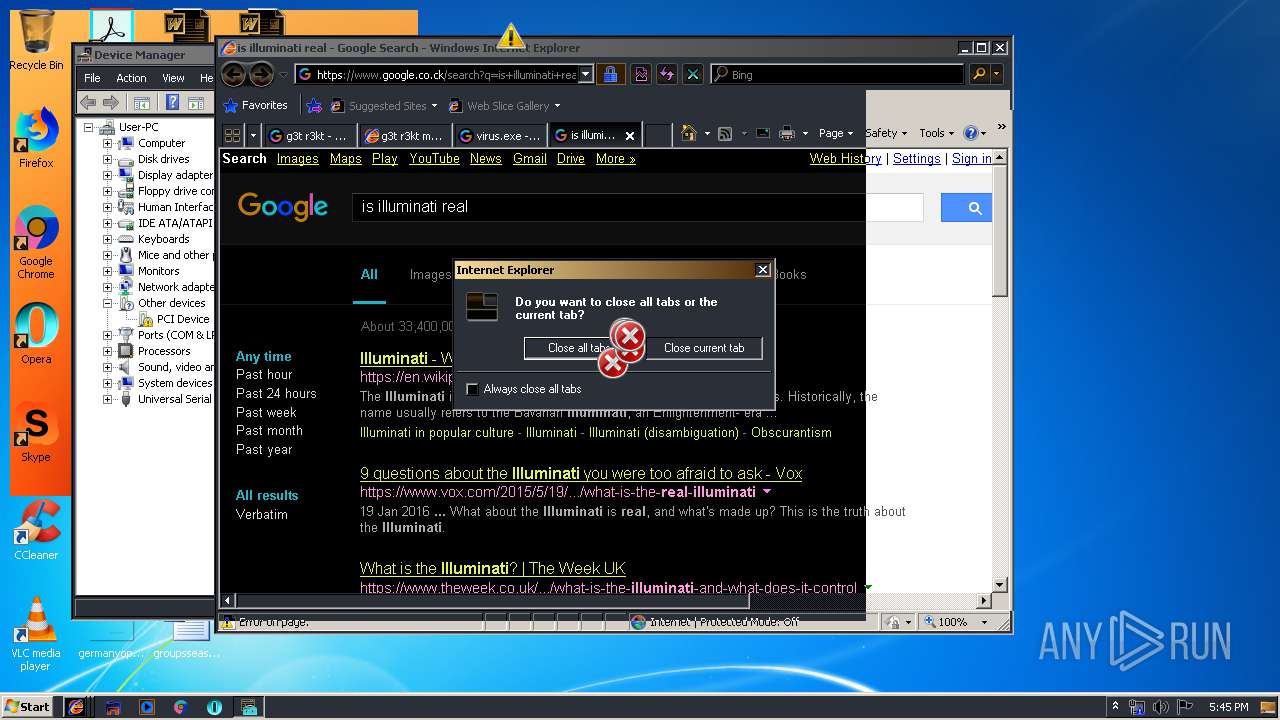
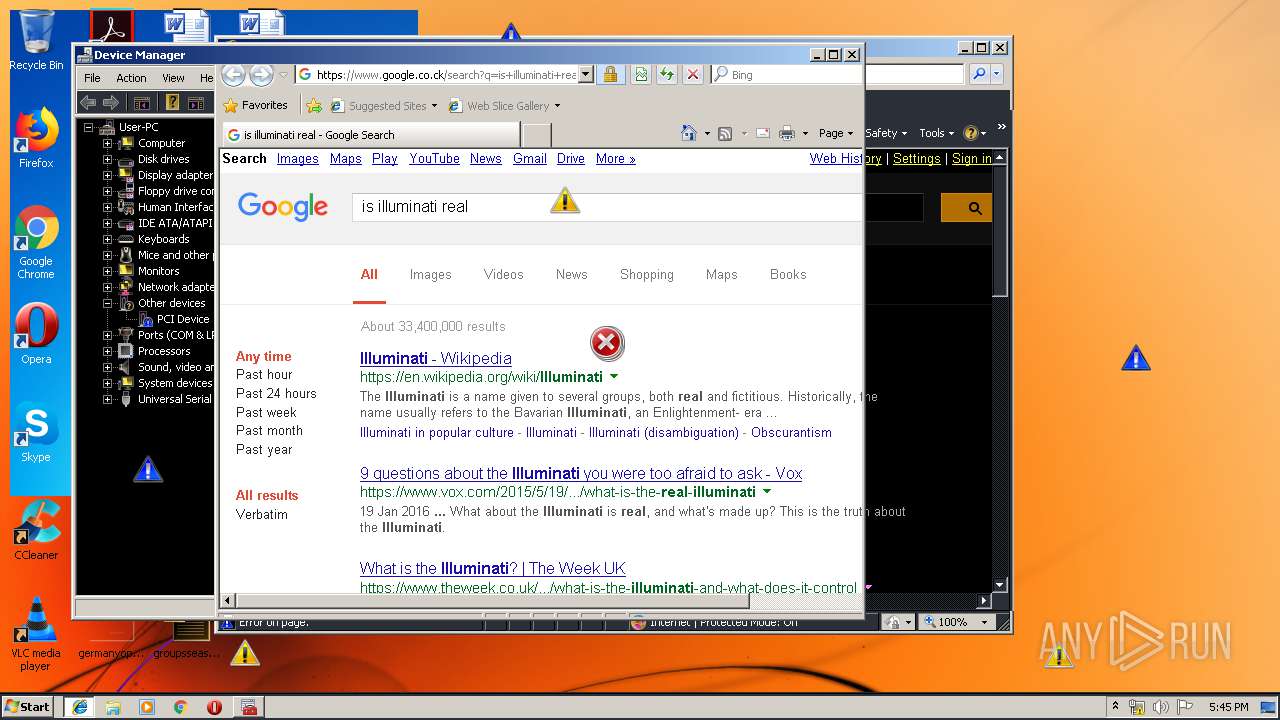
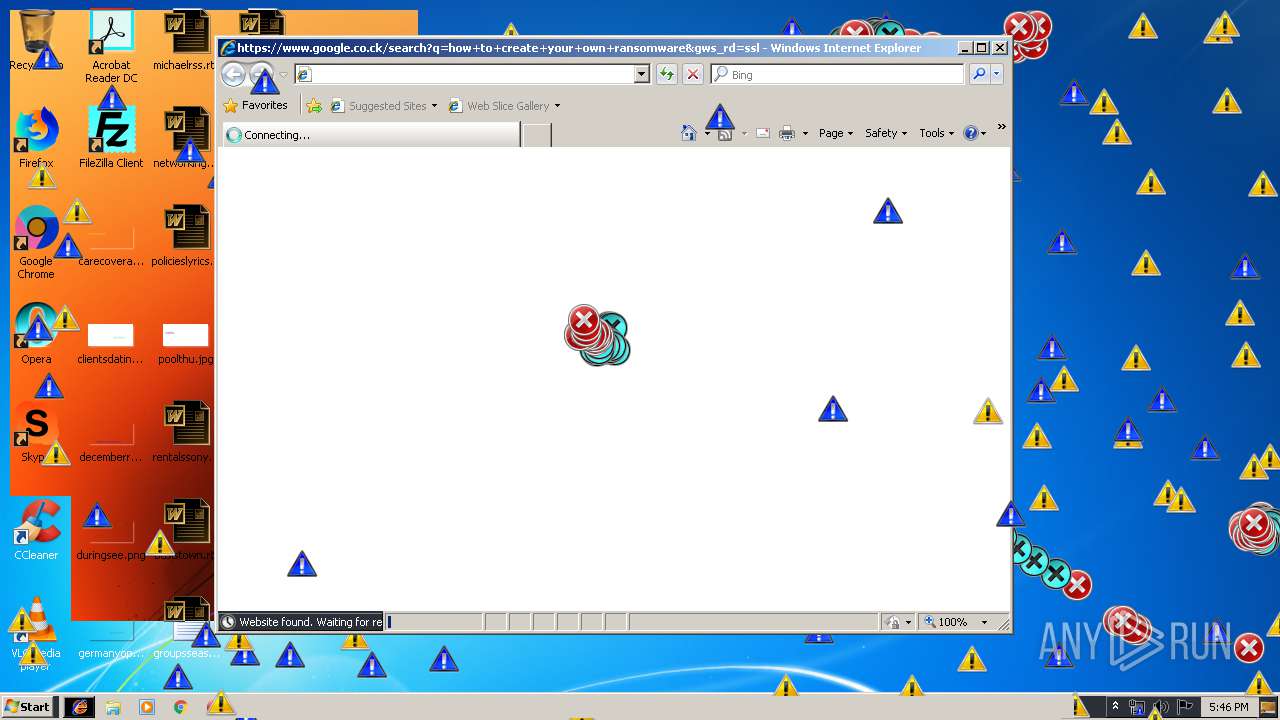
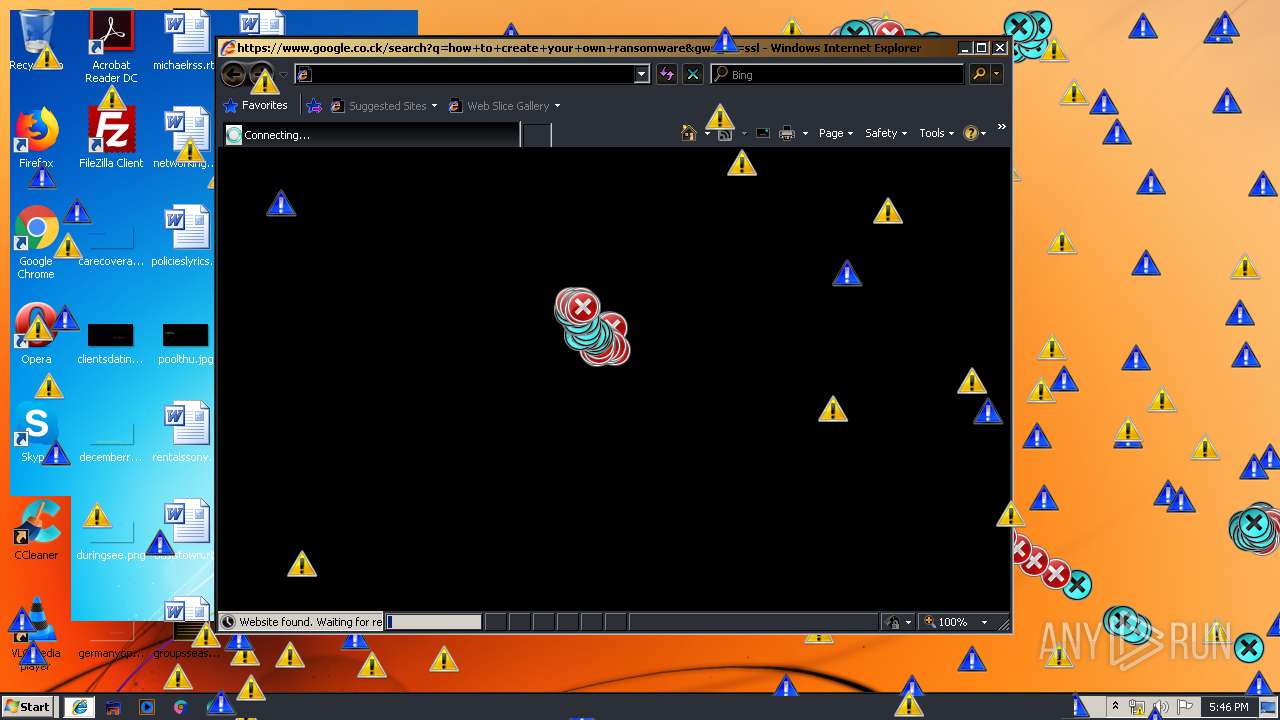
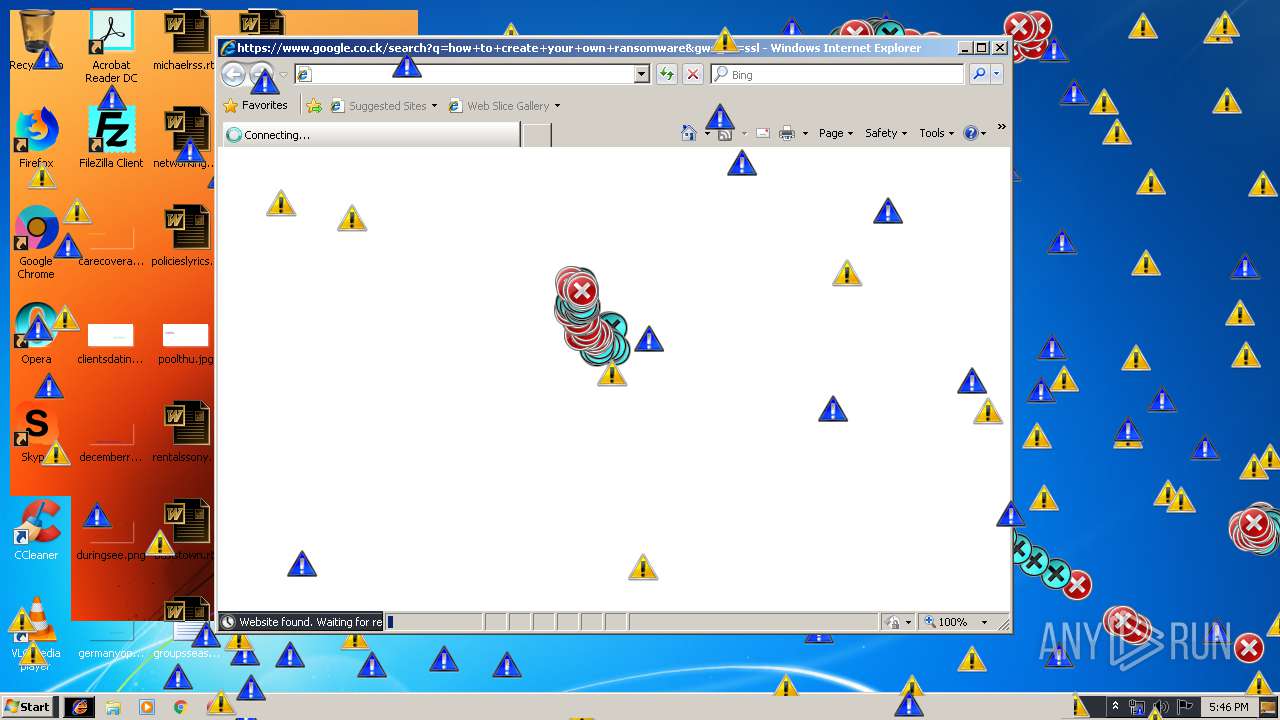
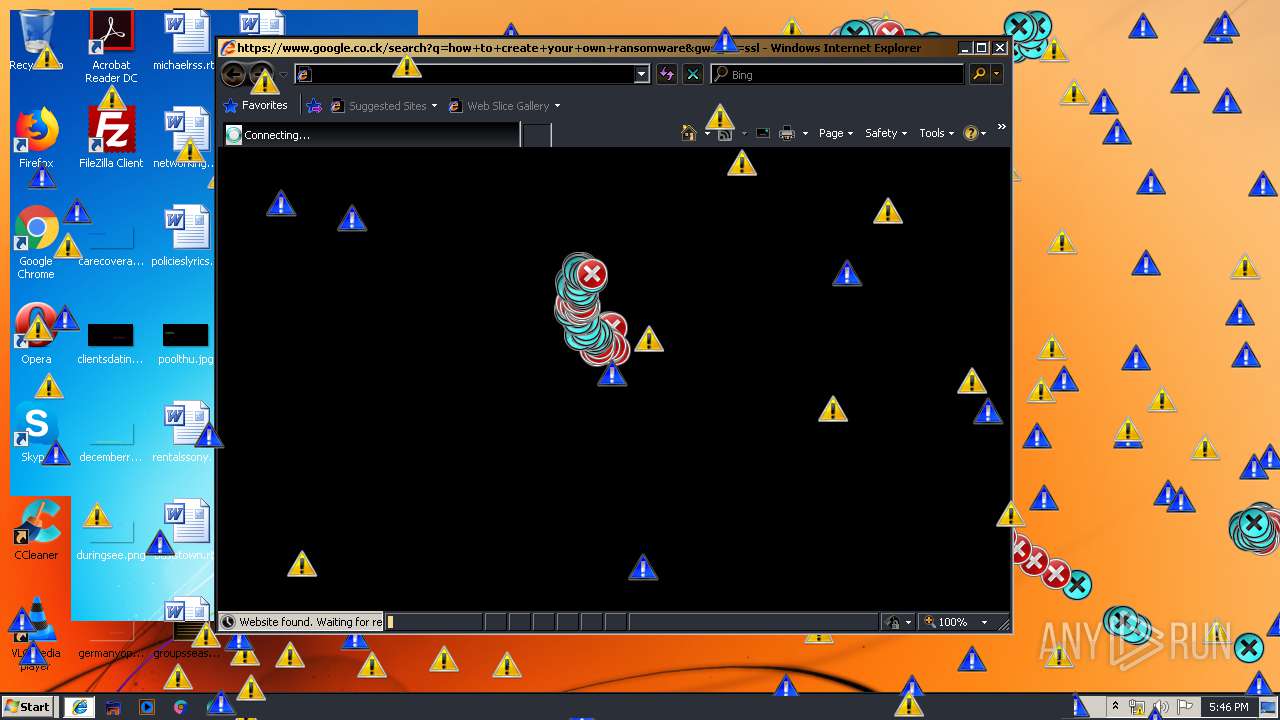
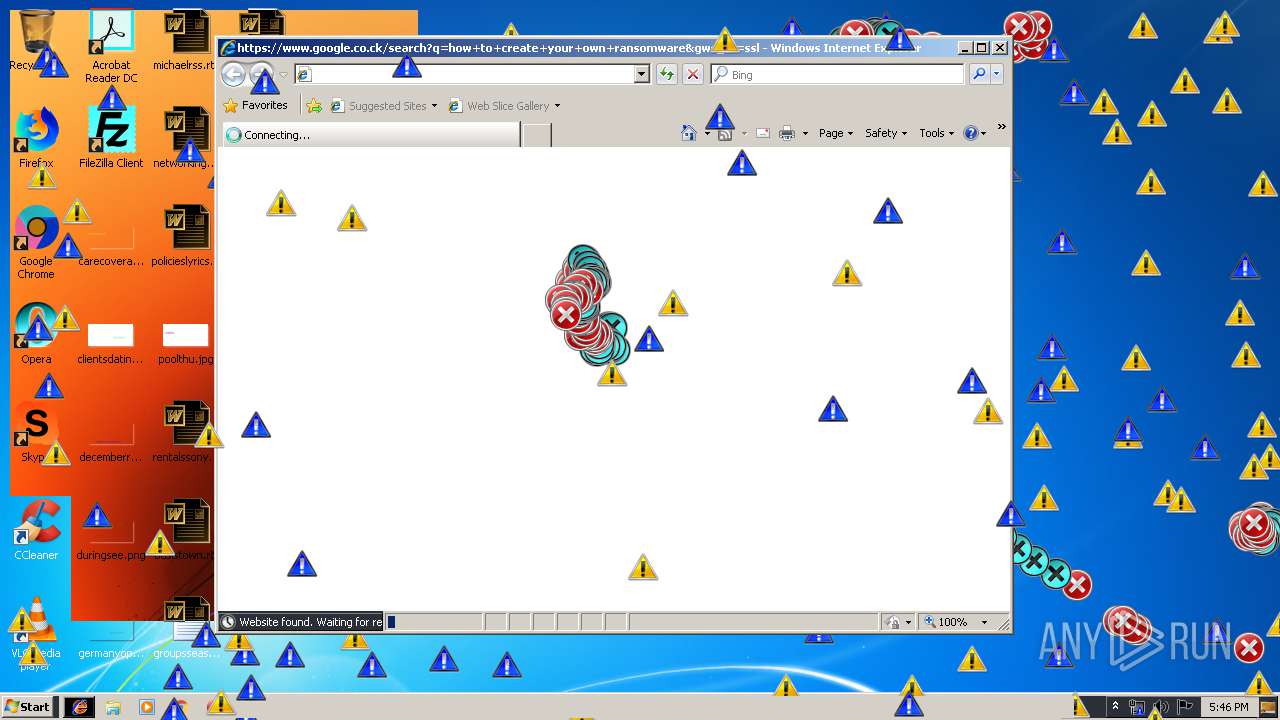
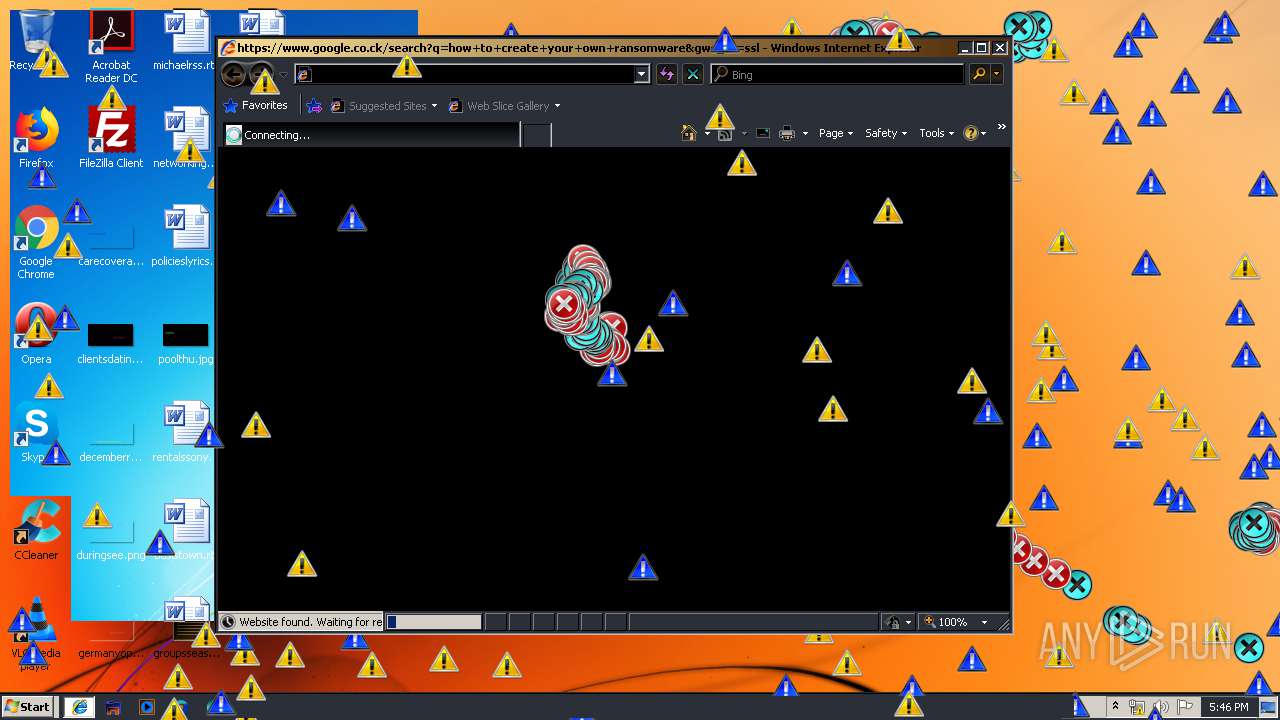
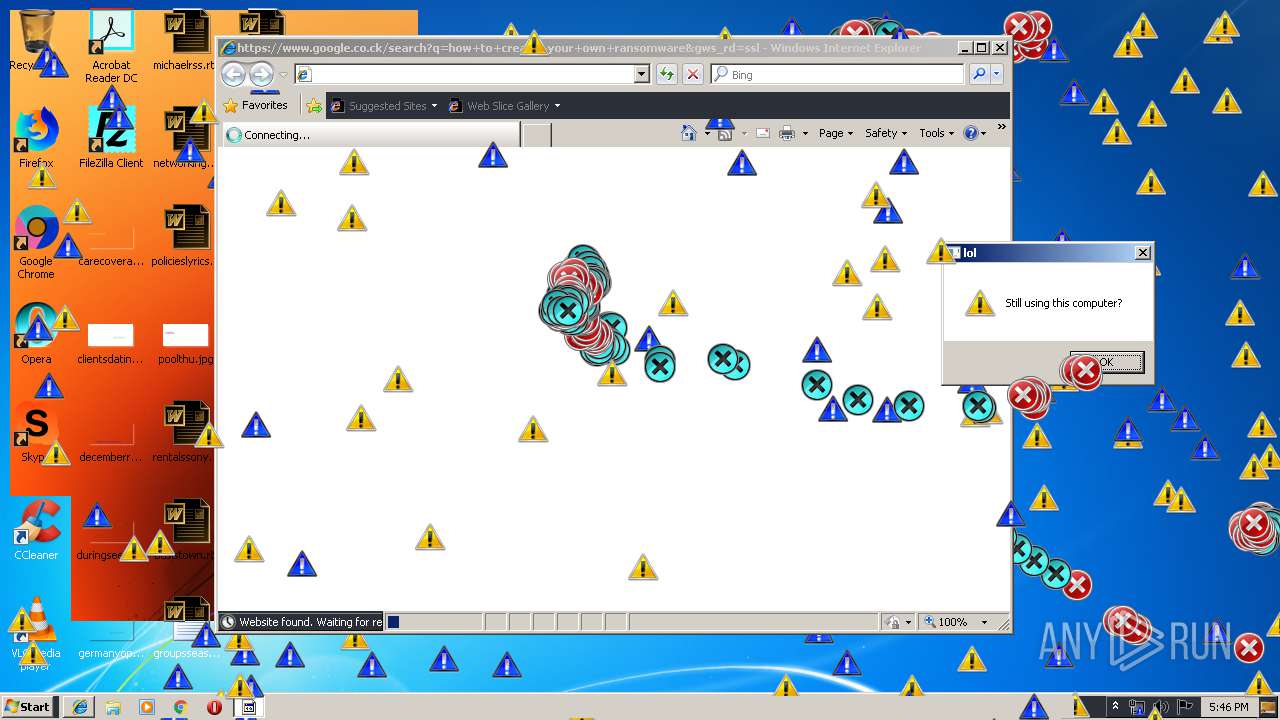
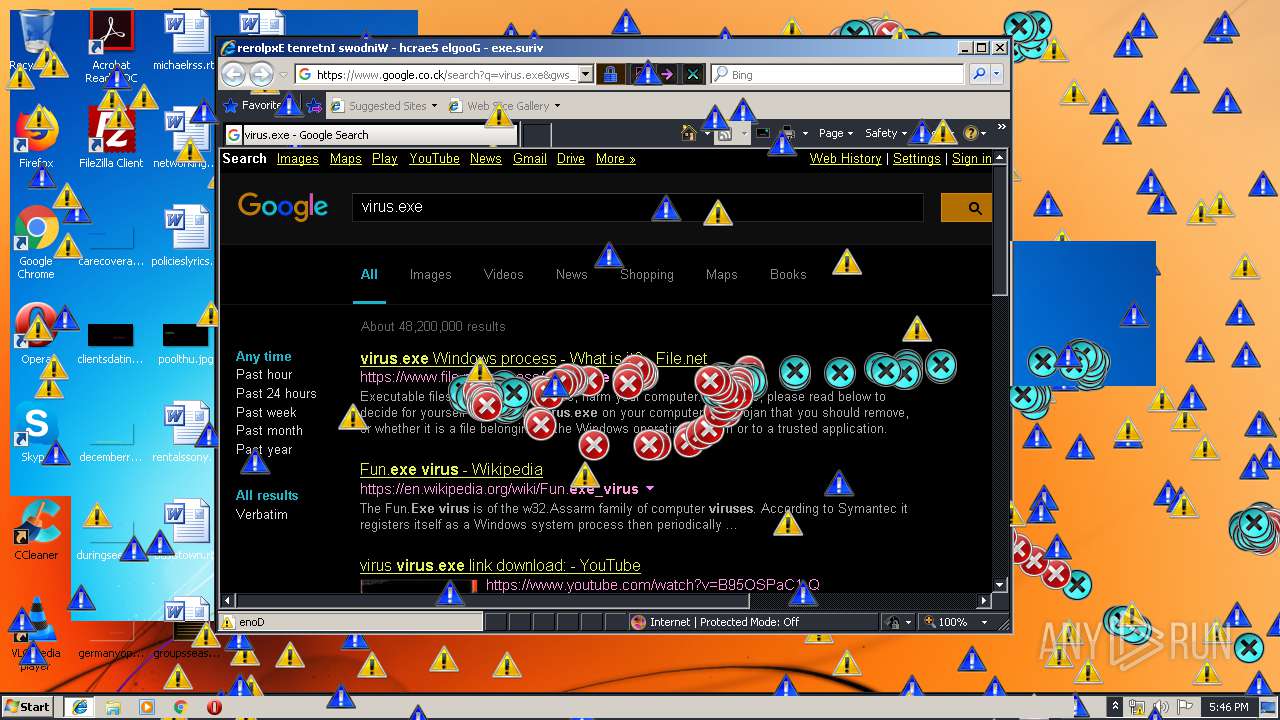
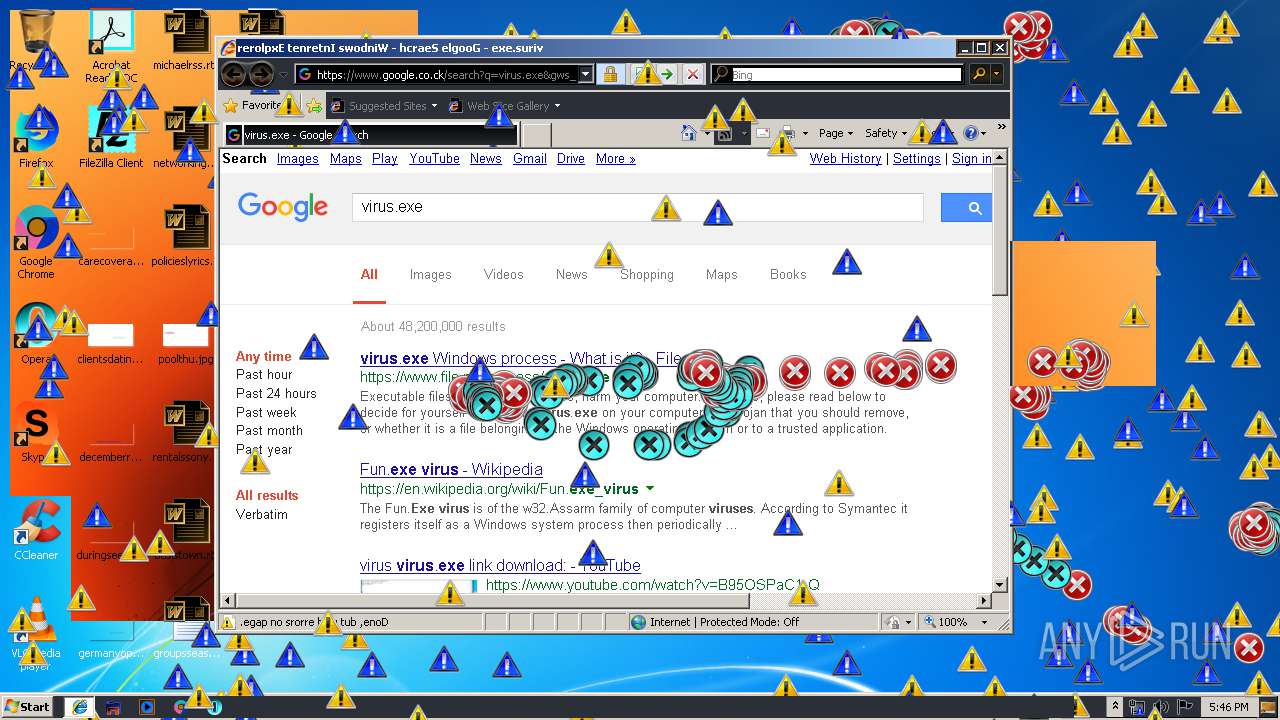
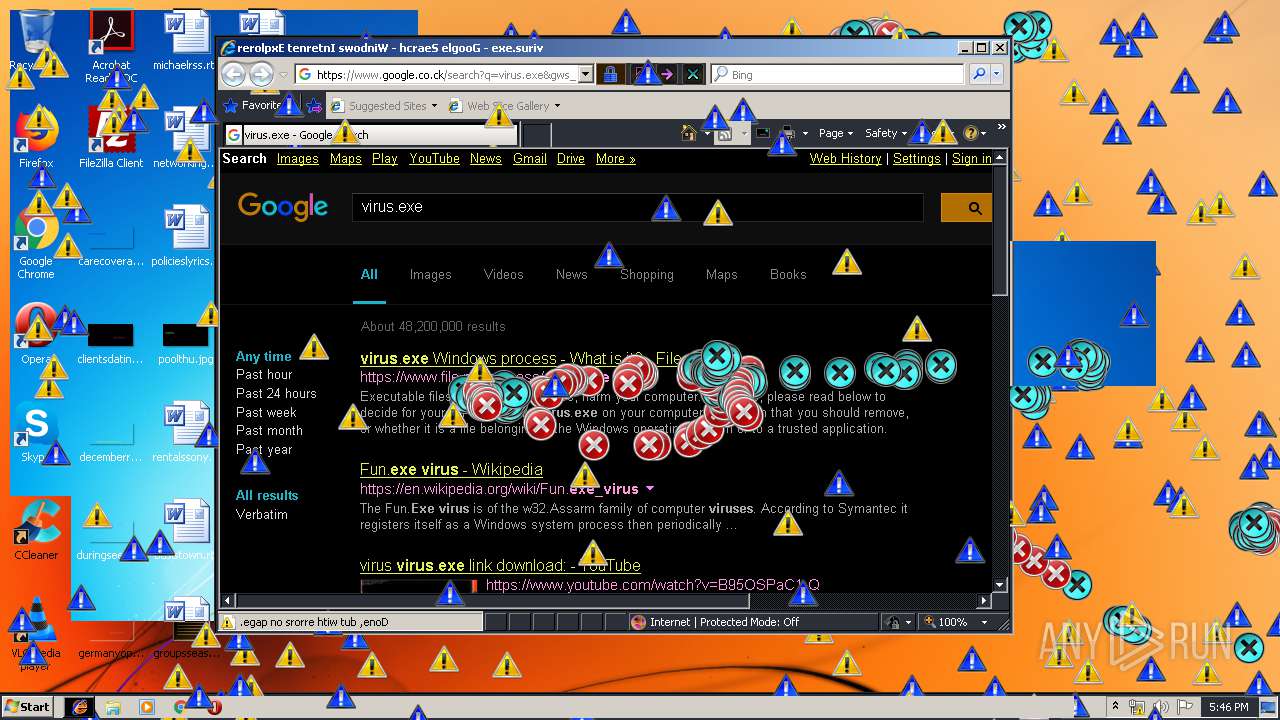
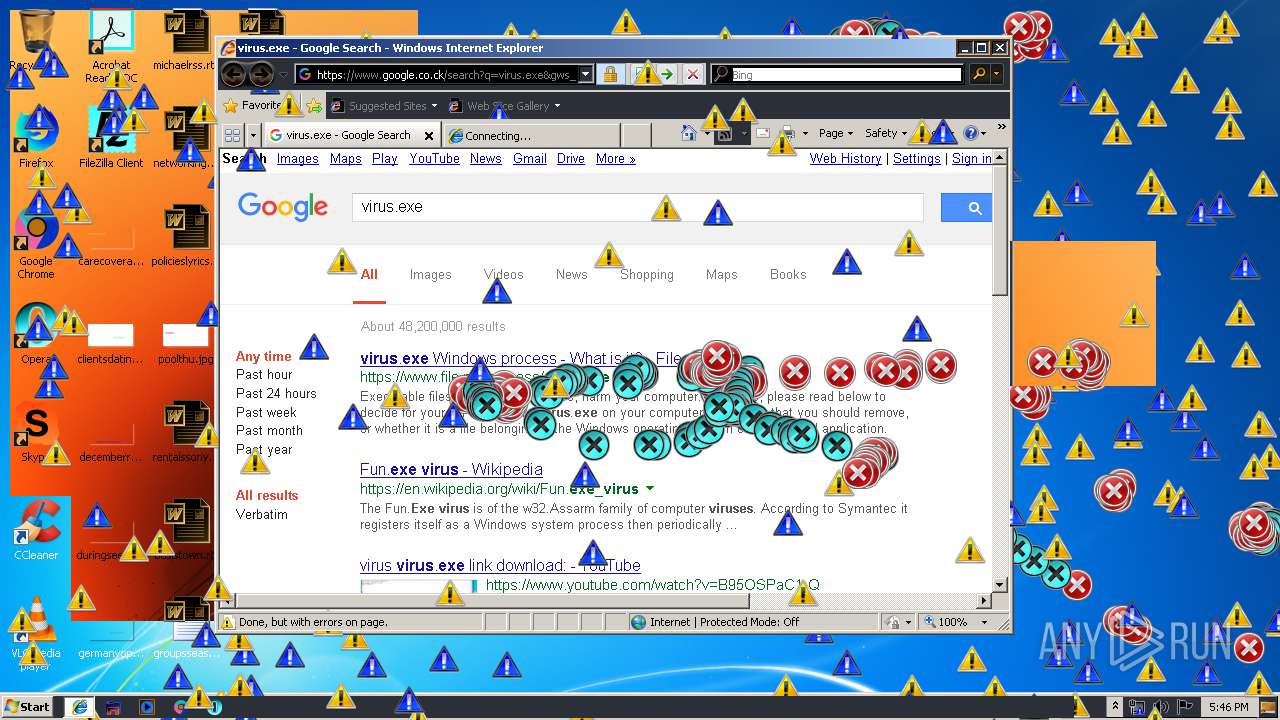
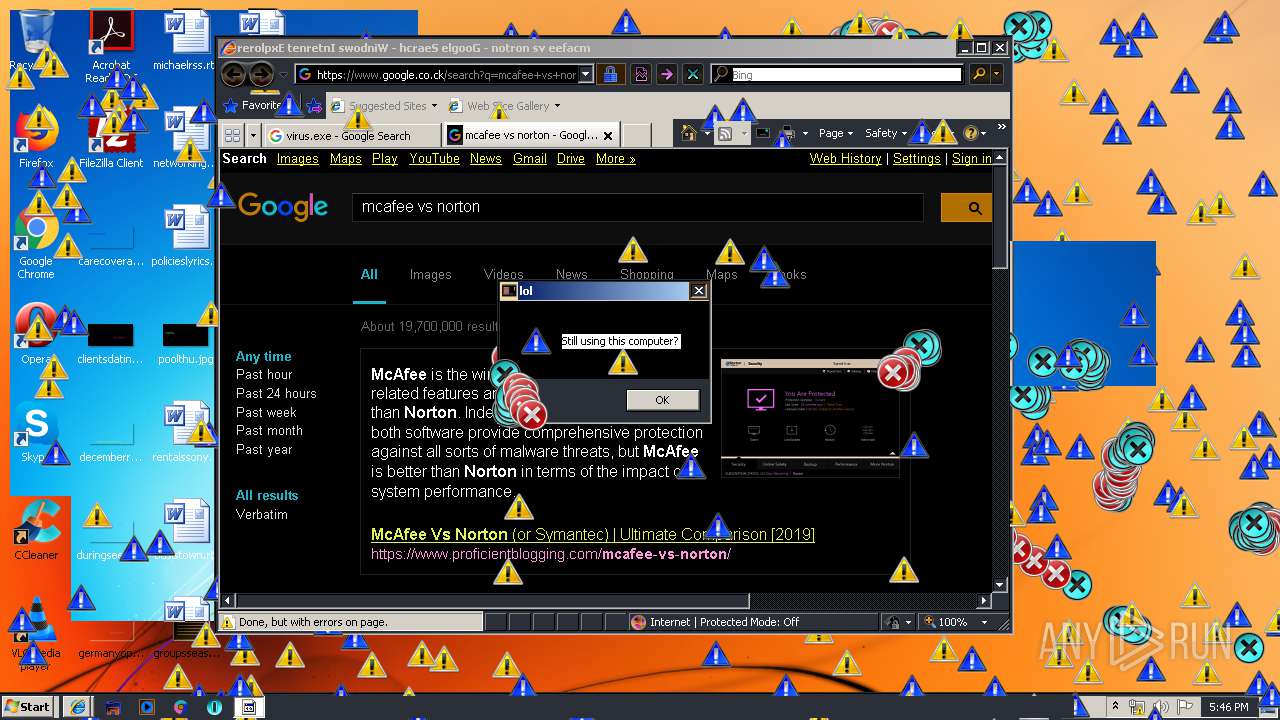
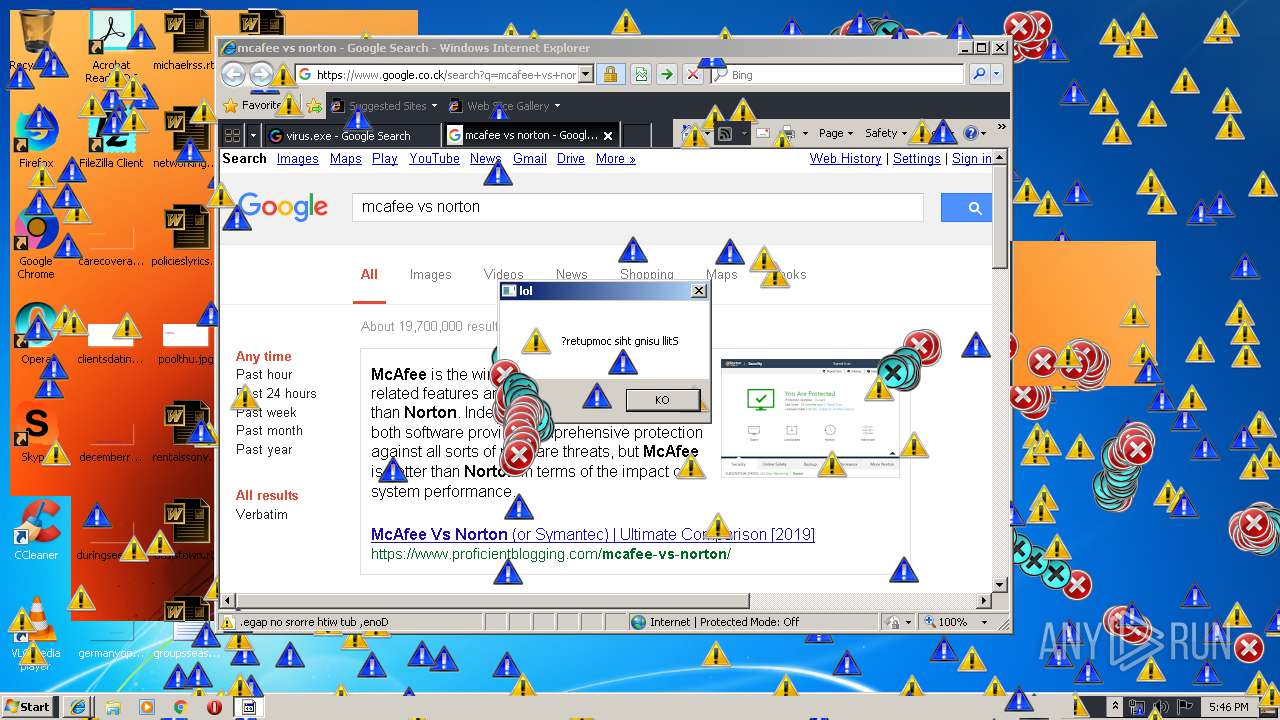
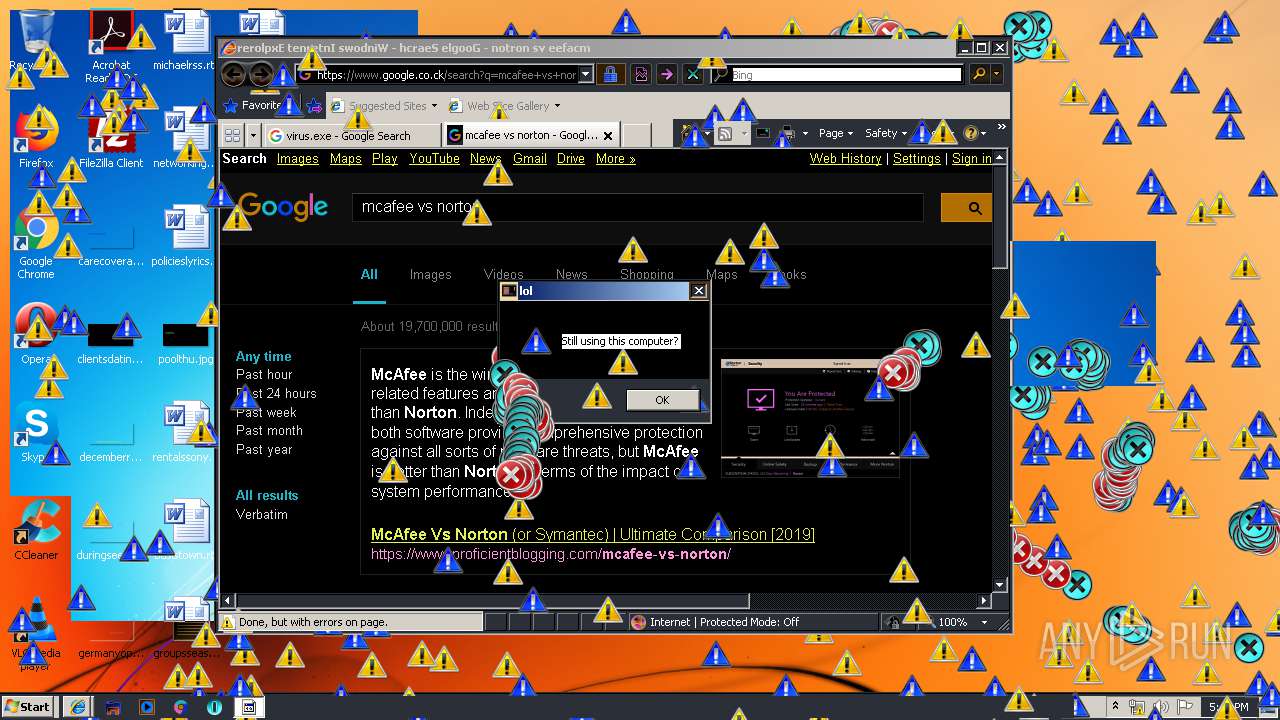
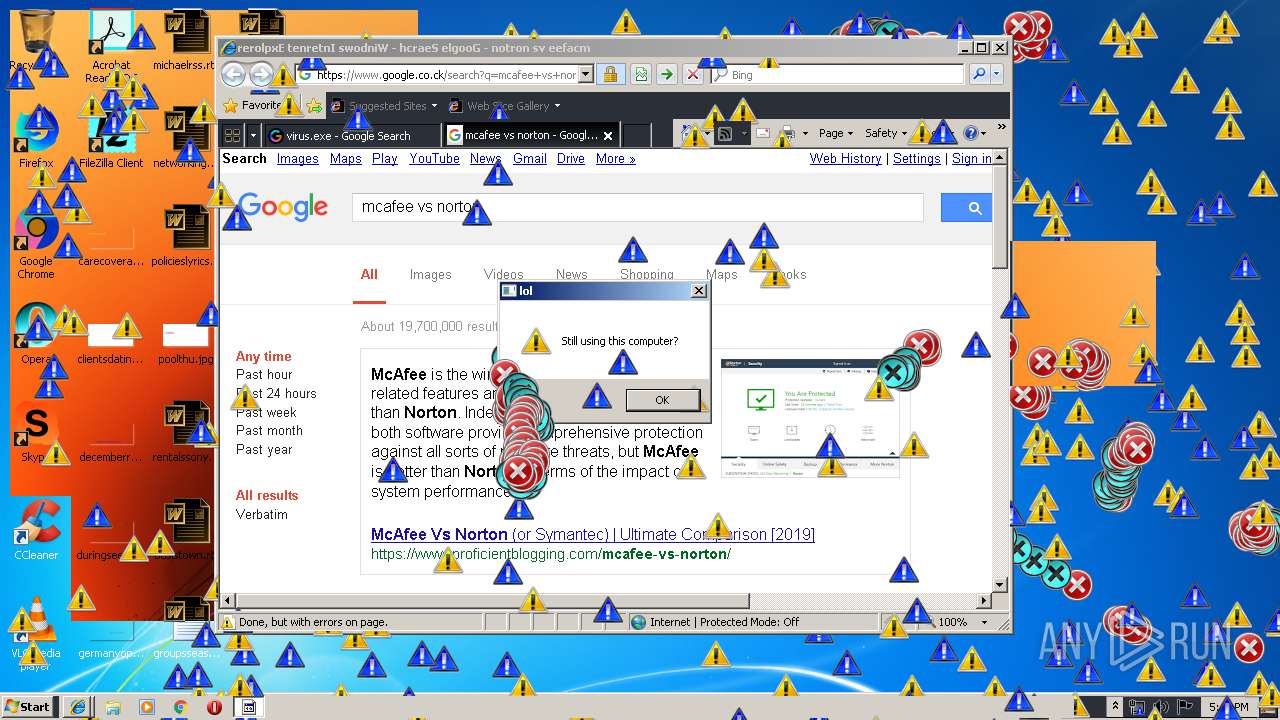
Starts Internet Explorer
- Endermanch@MEMZ.exe (PID: 2372)
INFO
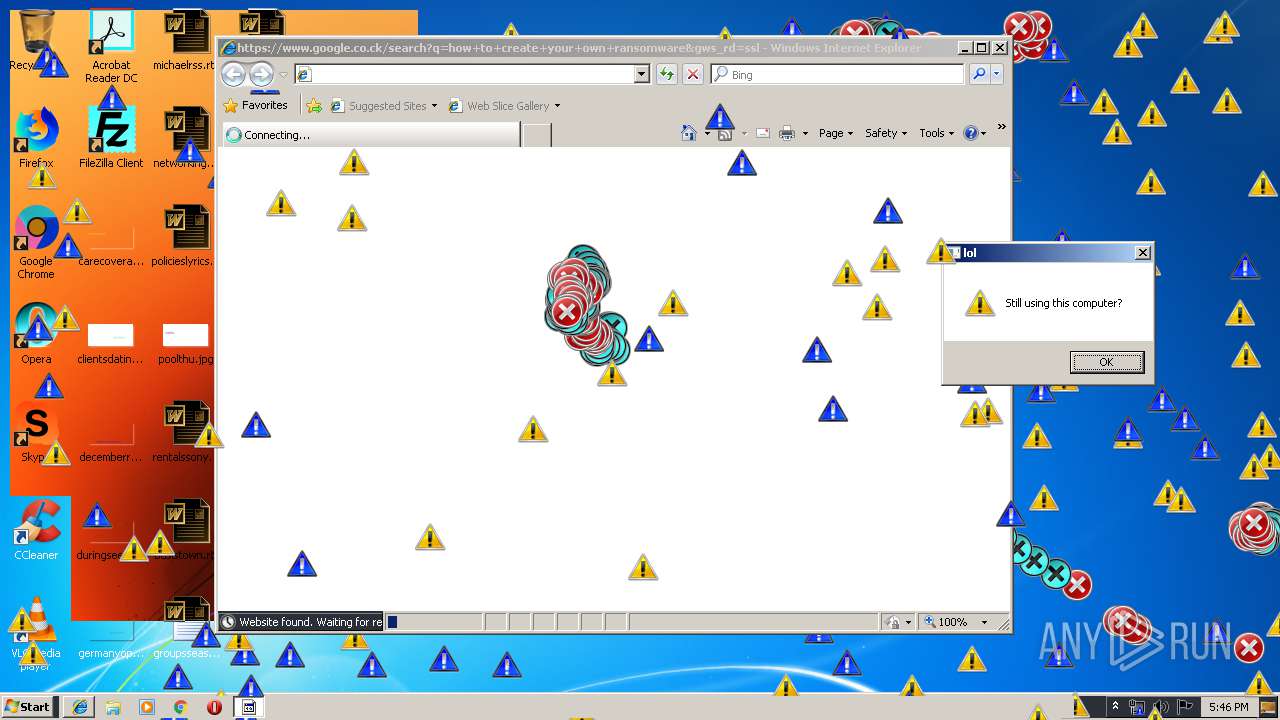
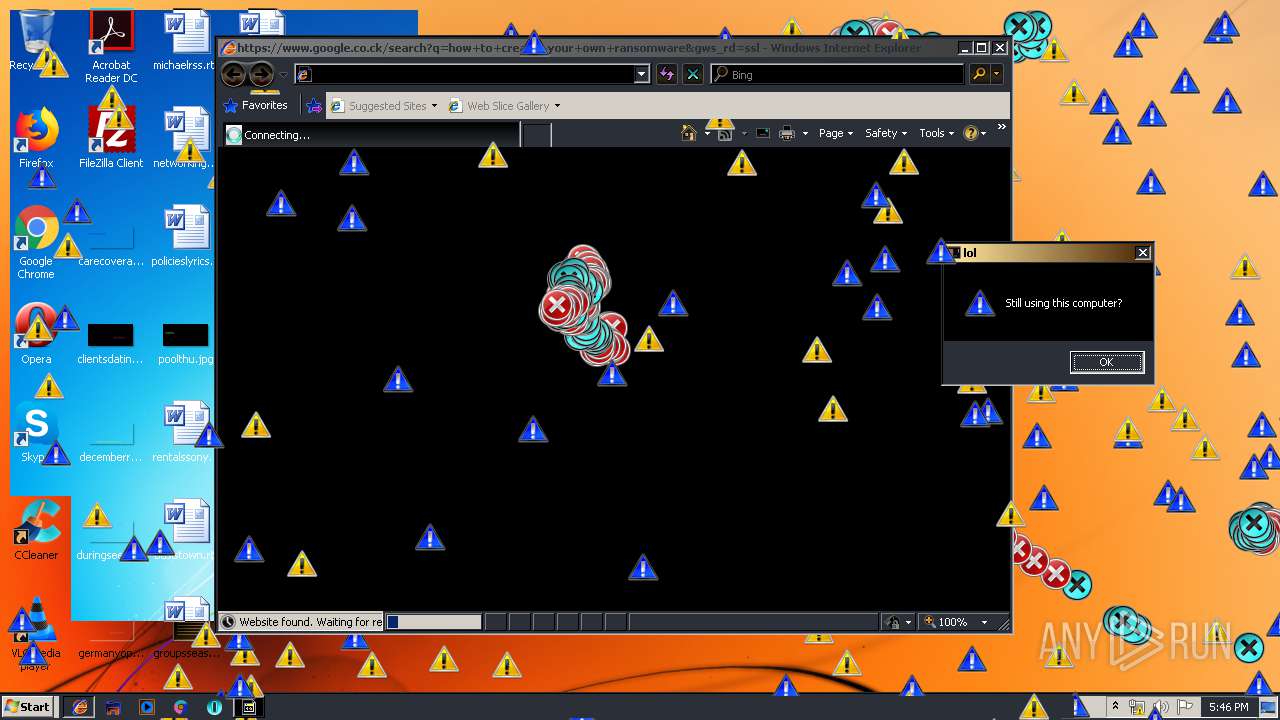
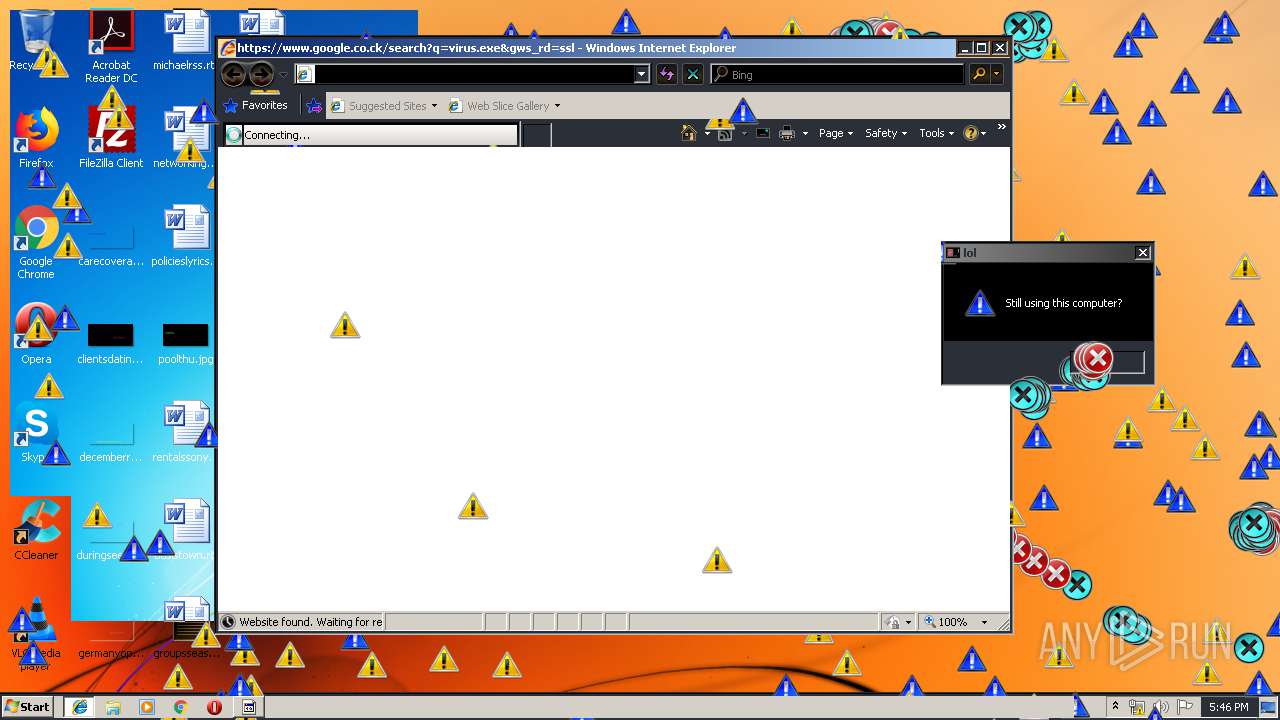
Manual execution by user
- Endermanch@MEMZ.exe (PID: 3908)
- Endermanch@MEMZ.exe (PID: 2004)
- Endermanch@MEMZ.exe (PID: 3228)
- Endermanch@MEMZ.exe (PID: 2156)
- Endermanch@MEMZ.exe (PID: 2456)
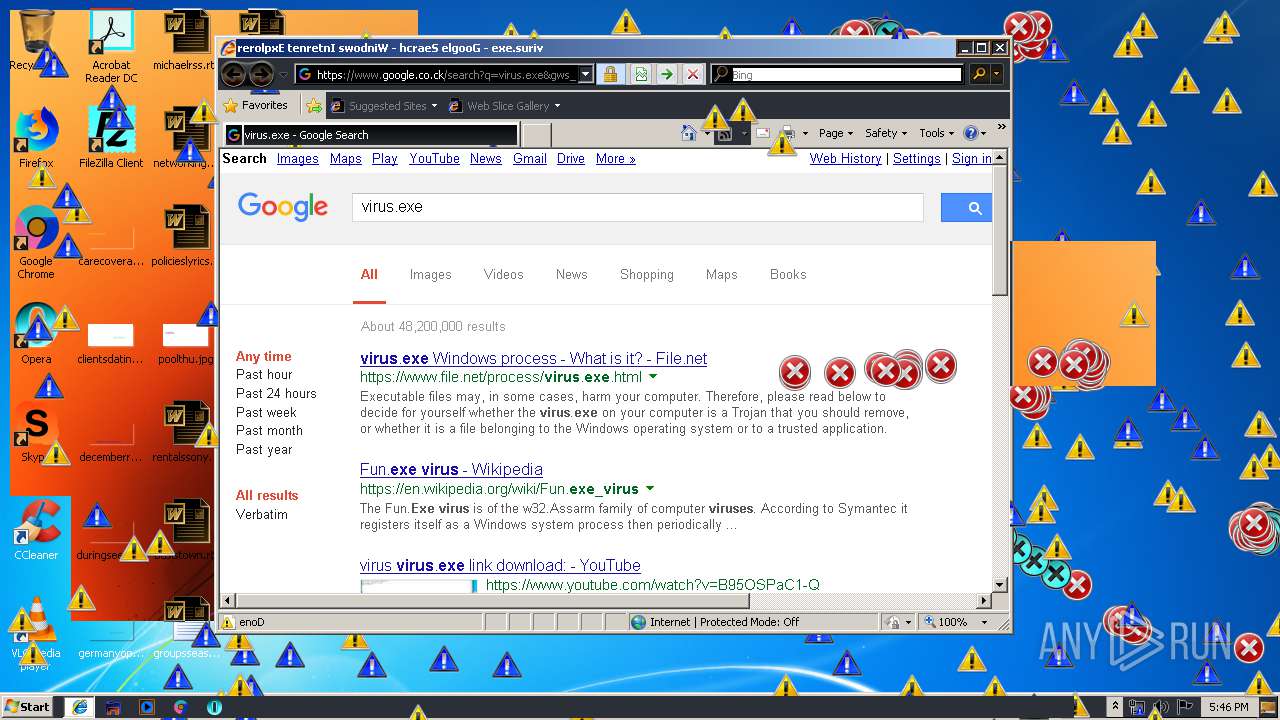
Changes internet zones settings
- iexplore.exe (PID: 2840)
- iexplore.exe (PID: 3304)
- iexplore.exe (PID: 2888)
Reads internet explorer settings
- iexplore.exe (PID: 1560)
- iexplore.exe (PID: 3940)
- iexplore.exe (PID: 3128)
- iexplore.exe (PID: 3680)
- iexplore.exe (PID: 2124)
- iexplore.exe (PID: 2244)
- iexplore.exe (PID: 4012)
Creates files in the user directory
- iexplore.exe (PID: 1560)
- iexplore.exe (PID: 3940)
- iexplore.exe (PID: 3680)
- iexplore.exe (PID: 2124)
- iexplore.exe (PID: 3128)
- iexplore.exe (PID: 3304)
- iexplore.exe (PID: 4012)
- iexplore.exe (PID: 2244)
Reads Internet Cache Settings
- iexplore.exe (PID: 1560)
- iexplore.exe (PID: 3940)
- iexplore.exe (PID: 2124)
- iexplore.exe (PID: 4012)
Application launched itself
- iexplore.exe (PID: 3304)
- iexplore.exe (PID: 2888)
Reads settings of System Certificates
- iexplore.exe (PID: 3304)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
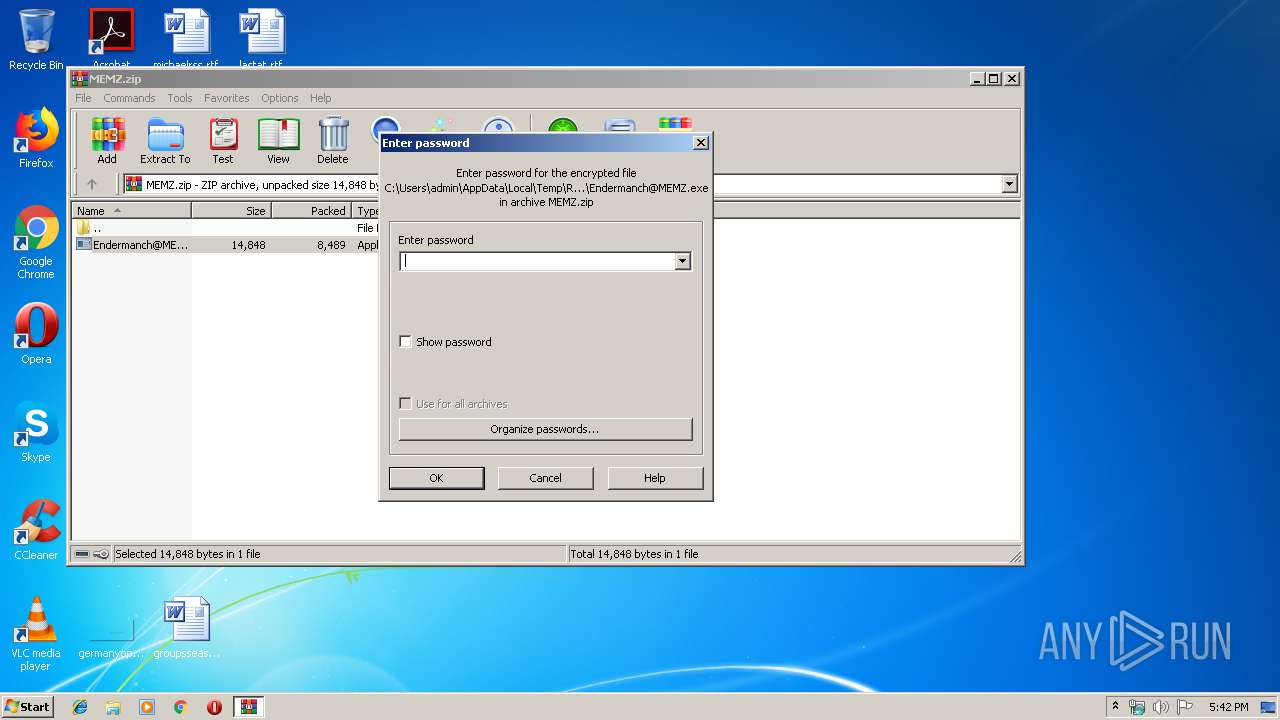
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2016:12:03 13:51:10 |
| ZipCRC: | 0xd987e890 |
| ZipCompressedSize: | 8489 |
| ZipUncompressedSize: | 14848 |
| ZipFileName: | Endermanch@MEMZ.exe |
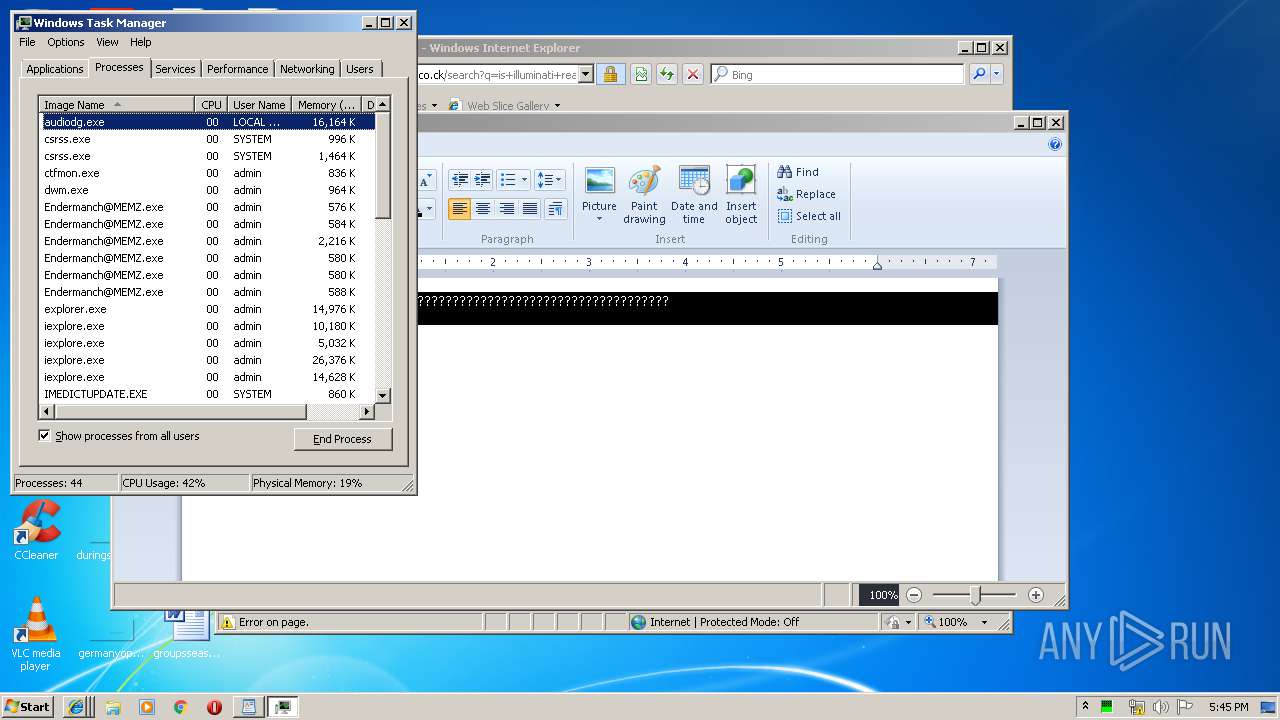
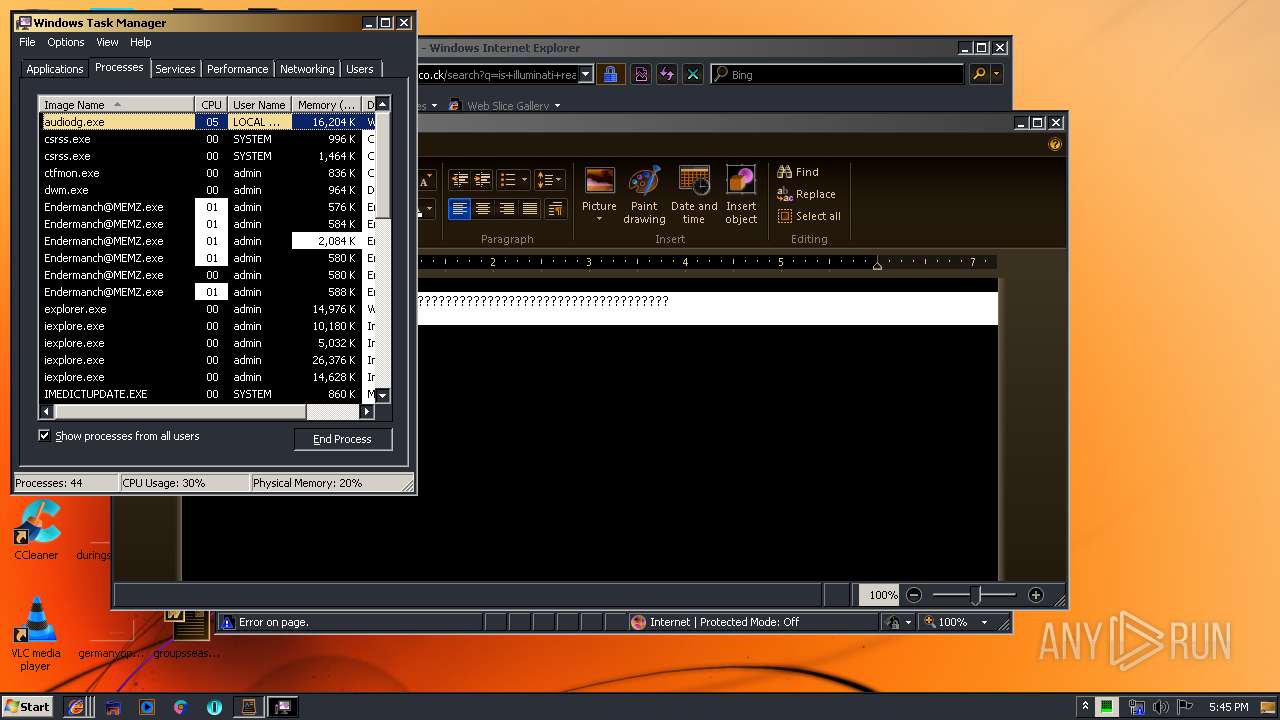
Total processes
74
Monitored processes
27
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
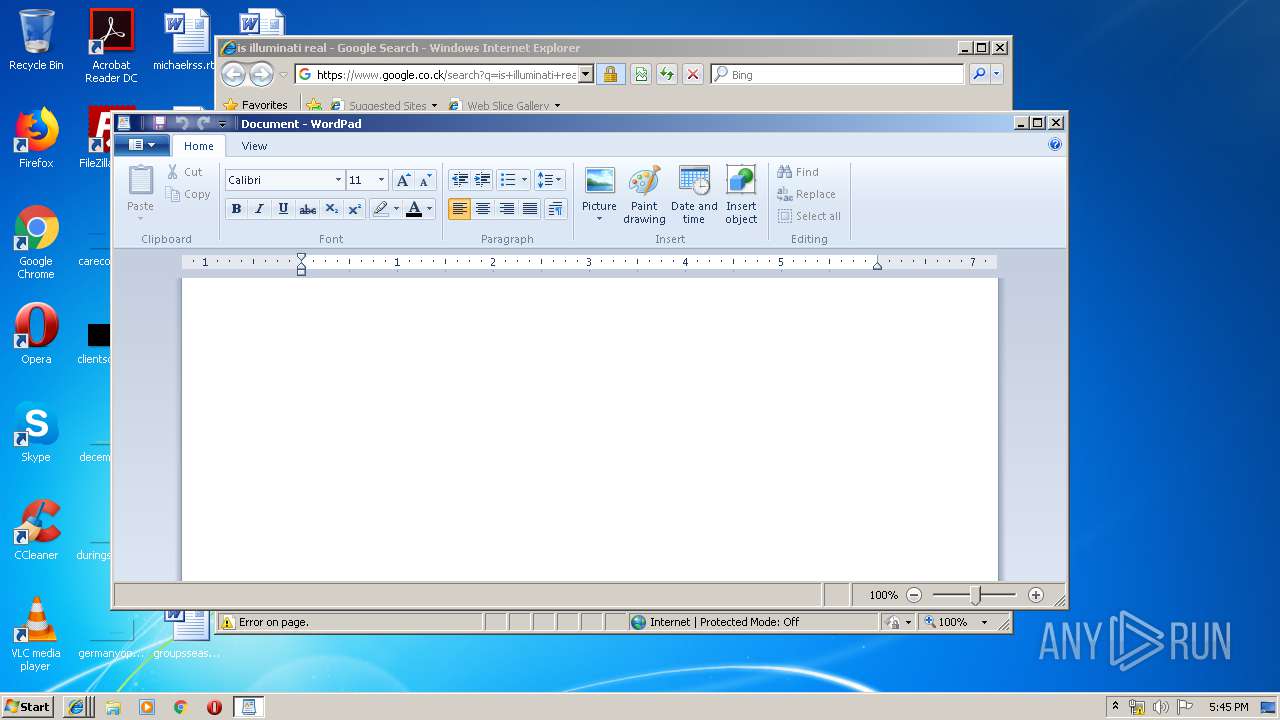
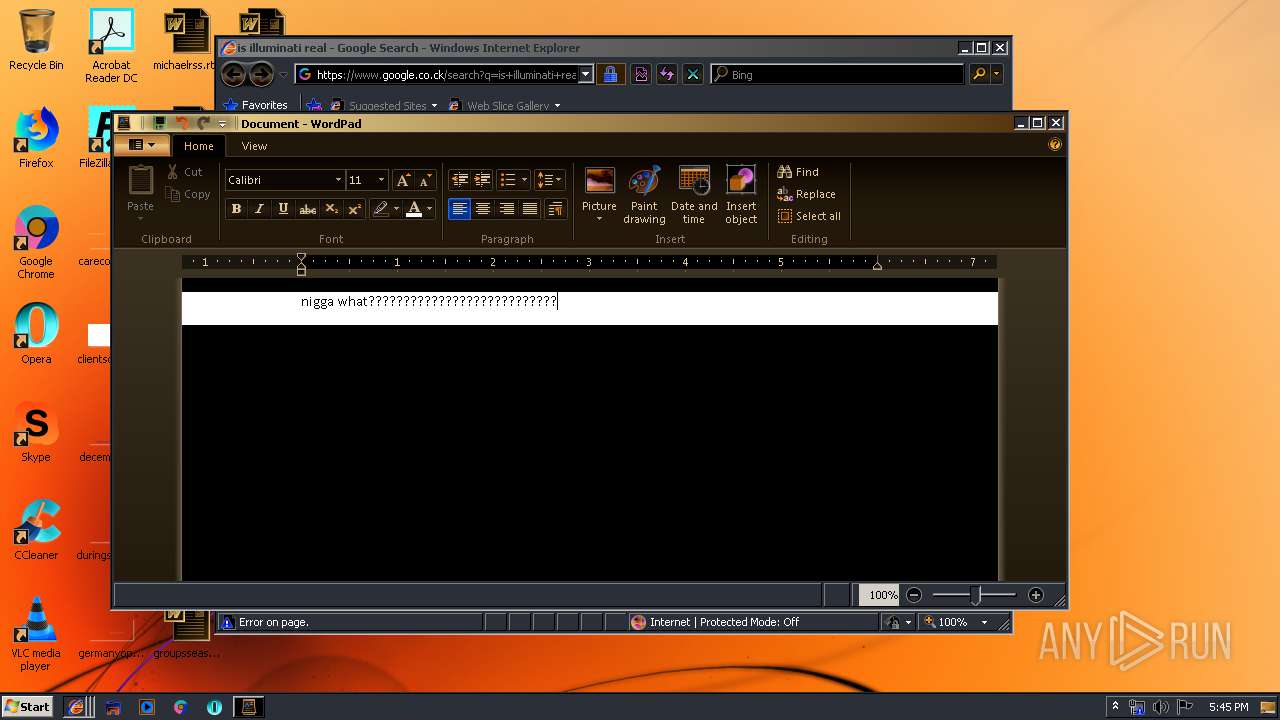
| 892 | "C:\Program Files\Windows NT\Accessories\wordpad.exe" | C:\Program Files\Windows NT\Accessories\wordpad.exe | — | Endermanch@MEMZ.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Wordpad Application Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
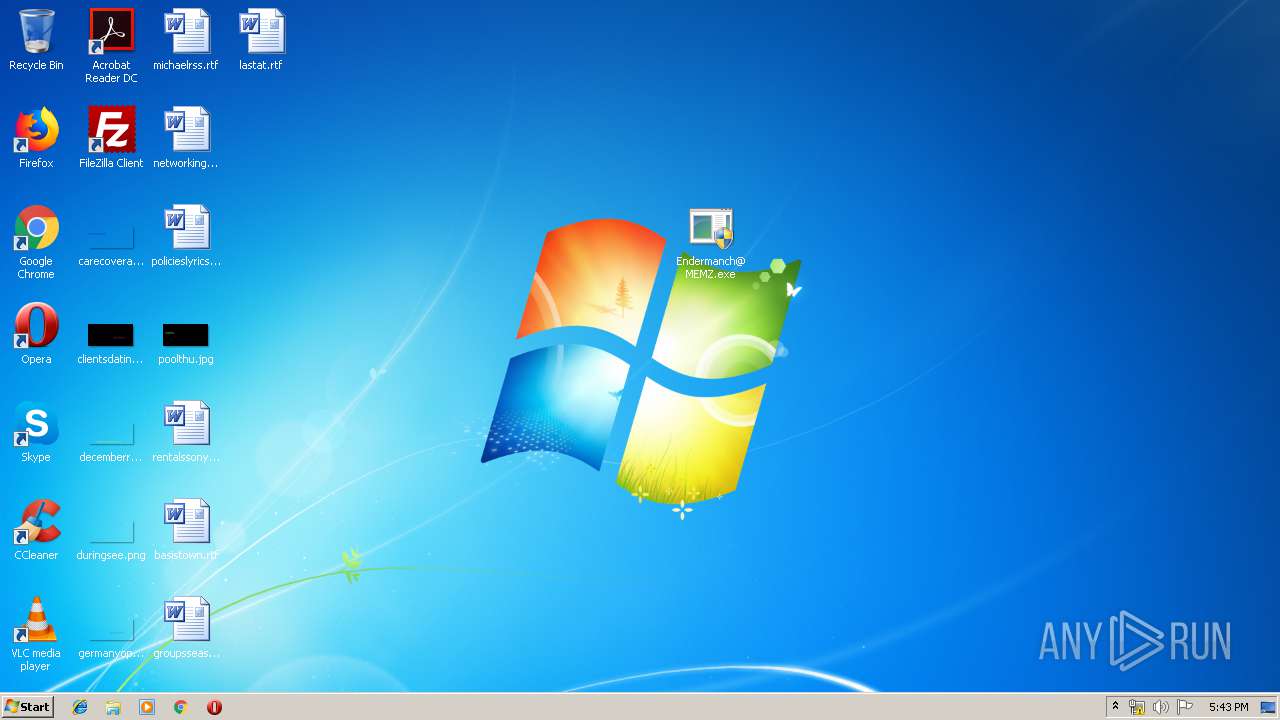
| 1484 | "C:\Users\admin\Desktop\Endermanch@MEMZ.exe" /watchdog | C:\Users\admin\Desktop\Endermanch@MEMZ.exe | — | Endermanch@MEMZ.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1560 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2840 CREDAT:79873 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2004 | "C:\Users\admin\Desktop\Endermanch@MEMZ.exe" | C:\Users\admin\Desktop\Endermanch@MEMZ.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2124 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3304 CREDAT:14342 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2156 | "C:\Users\admin\Desktop\Endermanch@MEMZ.exe" | C:\Users\admin\Desktop\Endermanch@MEMZ.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2160 | "C:\Windows\System32\msconfig.exe" | C:\Windows\System32\msconfig.exe | — | Endermanch@MEMZ.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: System Configuration Utility Exit code: 20 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2244 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2888 CREDAT:79873 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2276 | "C:\Users\admin\Desktop\Endermanch@MEMZ.exe" /watchdog | C:\Users\admin\Desktop\Endermanch@MEMZ.exe | — | Endermanch@MEMZ.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2372 | "C:\Users\admin\Desktop\Endermanch@MEMZ.exe" /main | C:\Users\admin\Desktop\Endermanch@MEMZ.exe | Endermanch@MEMZ.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
2 710
Read events
2 284
Write events
421
Delete events
5
Modification events
| (PID) Process: | (2508) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2508) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2508) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2508) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\MEMZ.zip | |||
| (PID) Process: | (2508) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2508) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2508) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2508) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2508) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2508) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
0
Suspicious files
15
Text files
103
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2508 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2508.33234\Endermanch@MEMZ.exe | — | |
MD5:— | SHA256:— | |||
| 1560 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\admin@google.co[1].txt | — | |
MD5:— | SHA256:— | |||
| 2840 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2840 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 1560 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\search[1].txt | — | |
MD5:— | SHA256:— | |||
| 1560 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\admin@google.co[2].txt | text | |
MD5:— | SHA256:— | |||
| 1560 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\admin@google.co[4].txt | text | |
MD5:— | SHA256:— | |||
| 2840 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFCDA0D65371D4D31C.TMP | — | |
MD5:— | SHA256:— | |||
| 1560 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\search[1].htm | html | |
MD5:— | SHA256:— | |||
| 2840 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFE3117C2C6469C5A6.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
80
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
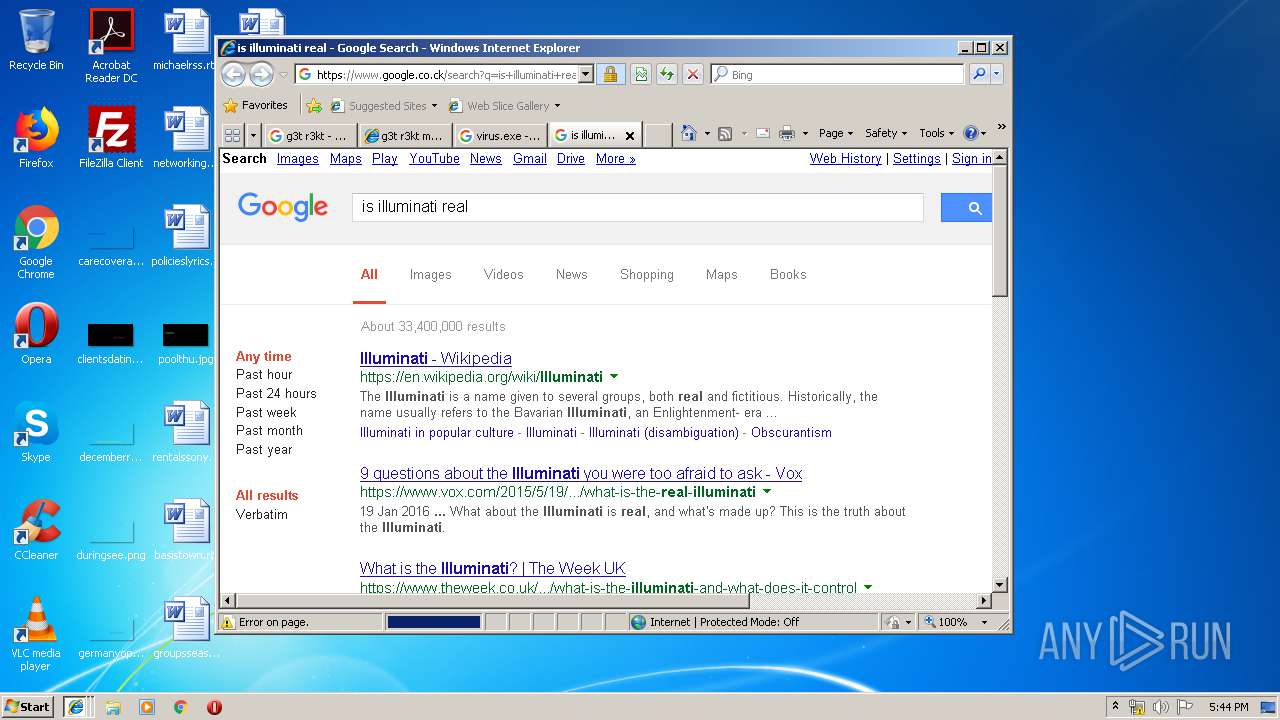
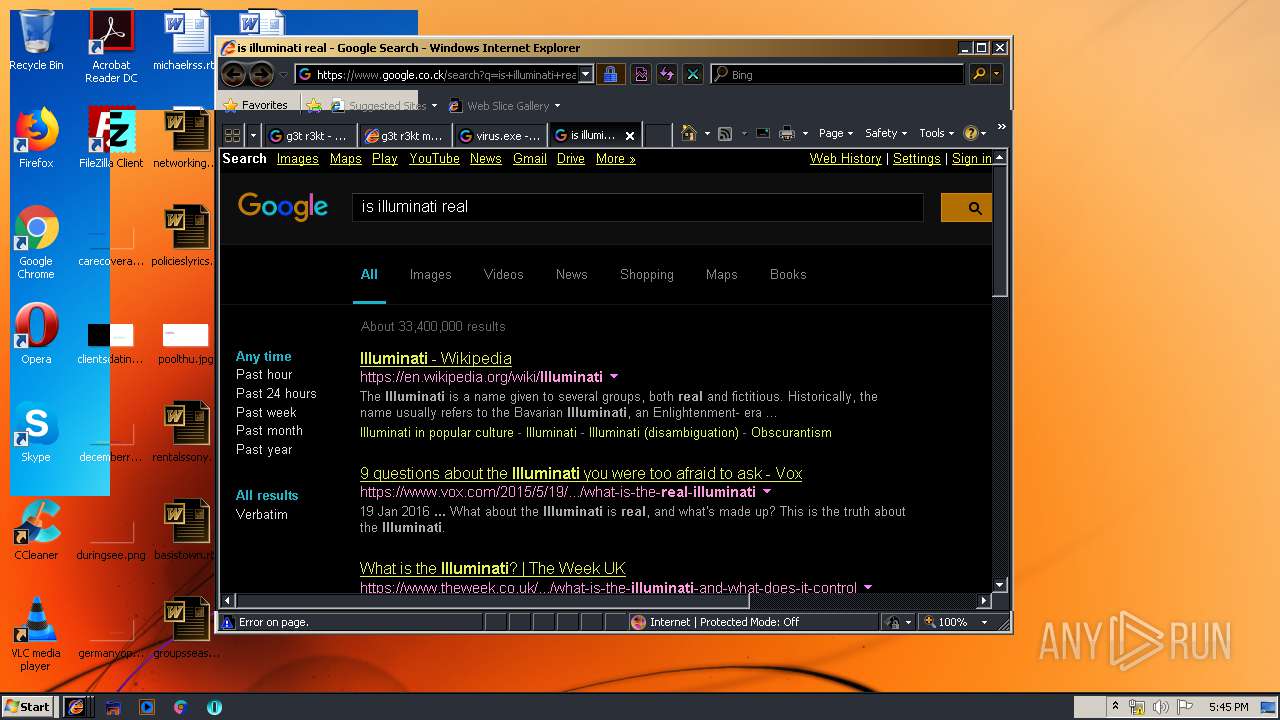
1560 | iexplore.exe | GET | 301 | 216.58.207.36:80 | http://google.co.ck/search?q=is+illuminati+real | US | html | 248 b | whitelisted |
4012 | iexplore.exe | GET | 301 | 216.58.207.36:80 | http://google.co.ck/search?q=mcafee+vs+norton | US | html | 246 b | whitelisted |
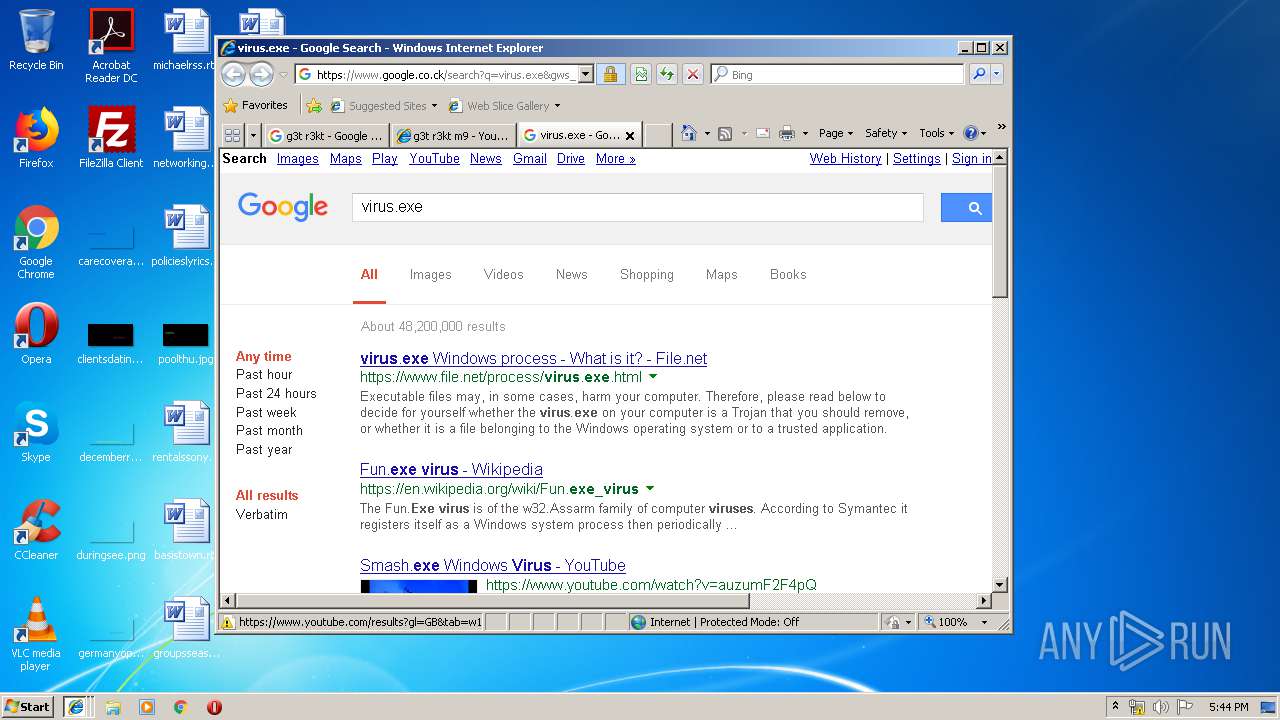
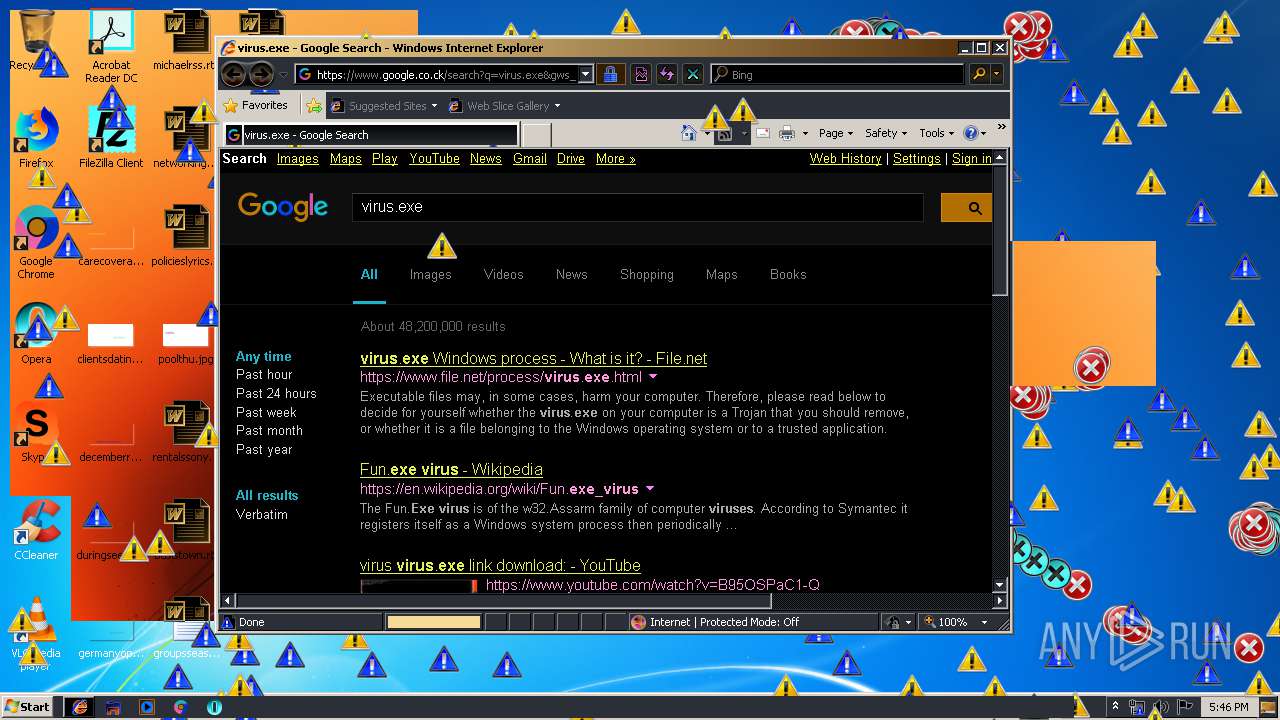
2244 | iexplore.exe | GET | 302 | 172.217.22.67:80 | http://www.google.co.ck/search?q=virus.exe | US | html | 255 b | whitelisted |
4012 | iexplore.exe | GET | 302 | 172.217.22.67:80 | http://www.google.co.ck/search?q=mcafee+vs+norton | US | html | 262 b | whitelisted |
2124 | iexplore.exe | GET | 302 | 172.217.22.67:80 | http://www.google.co.ck/search?q=virus.exe | US | html | 255 b | whitelisted |
2840 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
3940 | iexplore.exe | GET | 301 | 216.58.207.36:80 | http://google.co.ck/search?q=is+illuminati+real | US | html | 248 b | whitelisted |
3940 | iexplore.exe | GET | 301 | 216.58.207.36:80 | http://google.co.ck/search?q=g3t+r3kt | US | html | 238 b | whitelisted |
1560 | iexplore.exe | GET | 302 | 172.217.22.67:80 | http://www.google.co.ck/search?q=is+illuminati+real | US | html | 264 b | whitelisted |
3680 | iexplore.exe | GET | 302 | 172.217.22.67:80 | http://www.google.co.ck/search?q=g3t+r3kt | US | html | 254 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2840 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
1560 | iexplore.exe | 172.217.22.67:80 | www.google.co.ck | Google Inc. | US | whitelisted |
1560 | iexplore.exe | 172.217.22.67:443 | www.google.co.ck | Google Inc. | US | whitelisted |
1560 | iexplore.exe | 172.217.22.110:443 | encrypted-tbn1.gstatic.com | Google Inc. | US | whitelisted |
1560 | iexplore.exe | 172.217.22.14:443 | encrypted-tbn0.gstatic.com | Google Inc. | US | whitelisted |
1560 | iexplore.exe | 172.217.23.142:443 | encrypted-tbn2.gstatic.com | Google Inc. | US | whitelisted |
3940 | iexplore.exe | 216.58.207.36:80 | google.co.ck | Google Inc. | US | whitelisted |
3940 | iexplore.exe | 172.217.22.67:80 | www.google.co.ck | Google Inc. | US | whitelisted |
3940 | iexplore.exe | 172.217.22.67:443 | www.google.co.ck | Google Inc. | US | whitelisted |
3680 | iexplore.exe | 216.58.207.36:80 | google.co.ck | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.co.ck |
| whitelisted |
www.bing.com |
| whitelisted |
www.google.co.ck |
| whitelisted |
encrypted-tbn3.gstatic.com |
| whitelisted |
encrypted-tbn1.gstatic.com |
| whitelisted |
encrypted-tbn0.gstatic.com |
| whitelisted |
encrypted-tbn2.gstatic.com |
| whitelisted |
www.youtube.com |
| whitelisted |
s.ytimg.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |