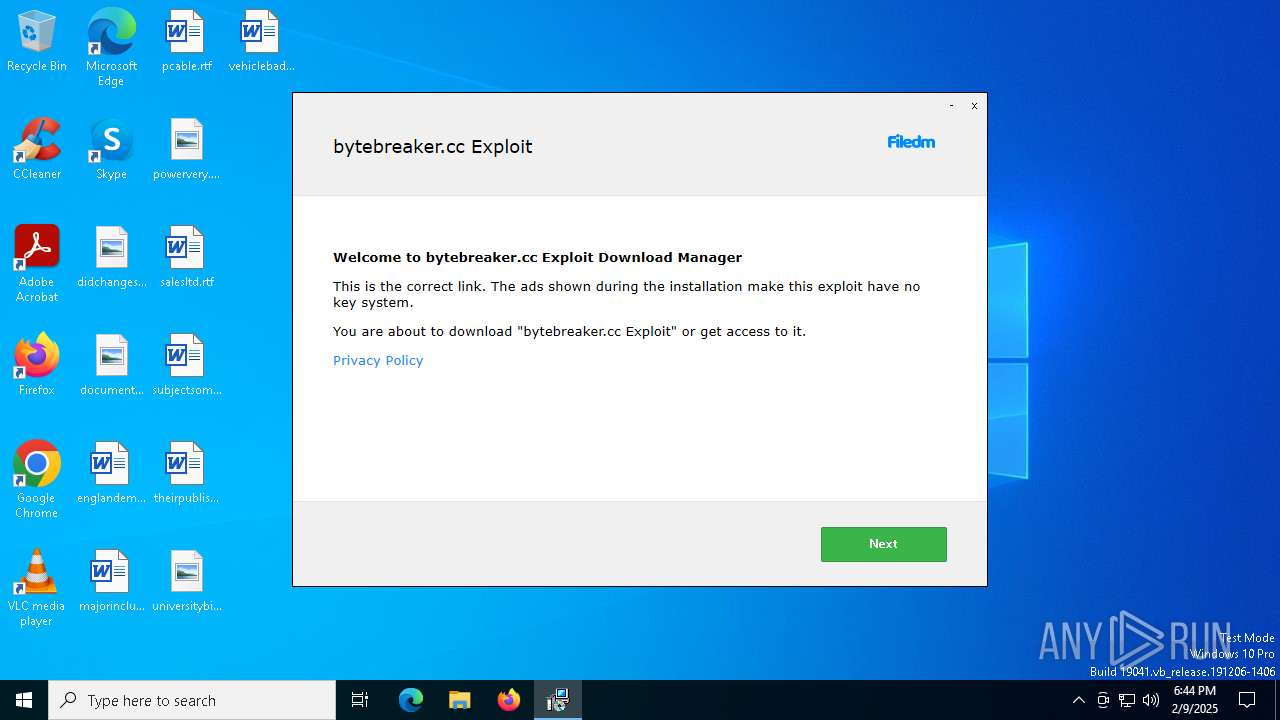
| File name: | bytebreaker.cc Exploit_12633821.exe |
| Full analysis: | https://app.any.run/tasks/9f019ff3-bd82-4f96-bda2-7695caa8f9d7 |
| Verdict: | Malicious activity |
| Analysis date: | February 09, 2025, 18:44:32 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 15D1C495FF66BF7CEA8A6D14BFDF0A20 |
| SHA1: | 942814521FA406A225522F208AC67F90DBDE0AE7 |
| SHA256: | 61C2C4A5D7C14F77EE88871DED4CC7F1E49DAE3E4EF209504C66FEDF4D22DE42 |
| SSDEEP: | 98304:DtjM+LgnHM8mNLNpOmMGl2p9tjIQh+1GHp8PGmDFzMVv3kdcpR41TBN14BC6SkPT:Kw8 |
MALICIOUS
GENERIC has been found (auto)
- bytebreaker.cc Exploit_12633821.exe (PID: 6320)
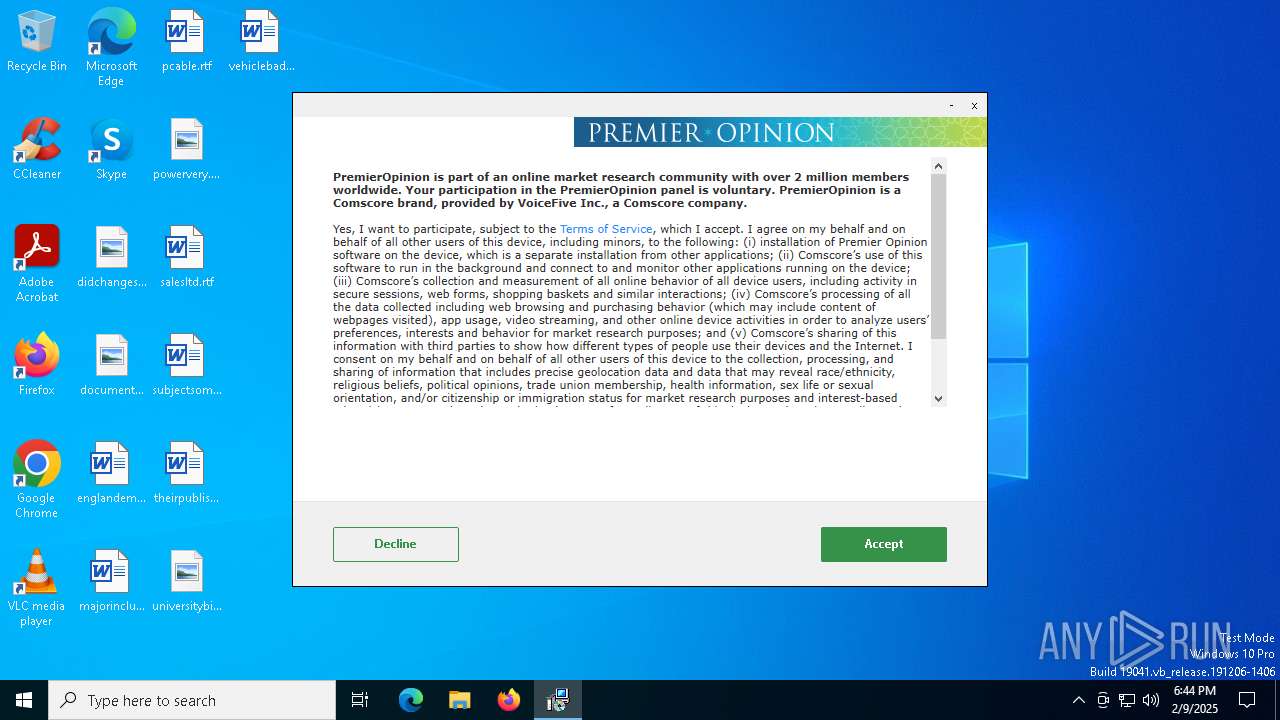
PREMIEROPINION mutex has been found
- ContentI3.exe (PID: 6596)
OSSPROXY mutex has been found
- ContentI3.exe (PID: 6596)
SUSPICIOUS
Reads security settings of Internet Explorer
- bytebreaker.cc Exploit_12633821.exe (PID: 6320)
- setup.exe (PID: 6896)
- ContentI3.exe (PID: 6596)
Executable content was dropped or overwritten
- bytebreaker.cc Exploit_12633821.exe (PID: 6320)
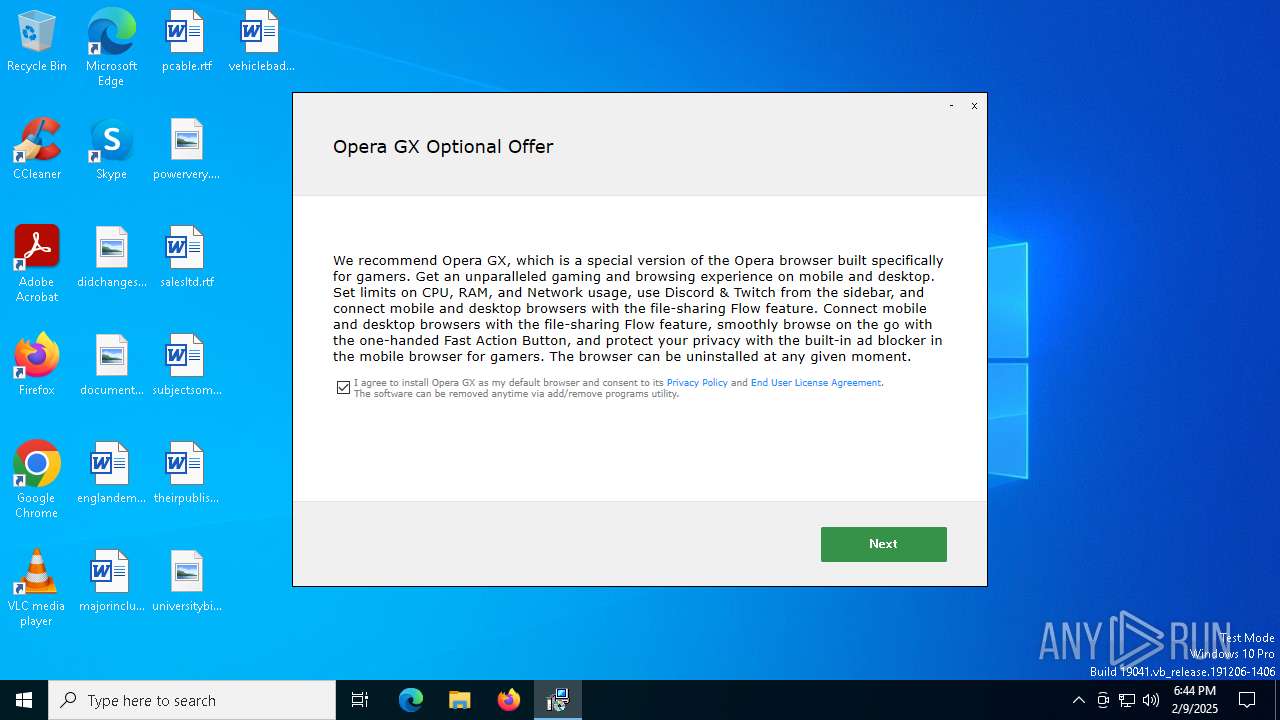
- OperaGX.exe (PID: 6864)
- setup.exe (PID: 6920)
- setup.exe (PID: 7008)
- setup.exe (PID: 6896)
- setup.exe (PID: 7044)
- setup.exe (PID: 7100)
- Opera_GX_assistant_73.0.3856.382_Setup.exe_sfx.exe (PID: 4392)
Checks Windows Trust Settings
- bytebreaker.cc Exploit_12633821.exe (PID: 6320)
- setup.exe (PID: 6896)
Application launched itself
- setup.exe (PID: 6896)
- setup.exe (PID: 7044)
- assistant_installer.exe (PID: 6712)
Starts itself from another location
- setup.exe (PID: 6896)
INFO
The sample compiled with english language support
- bytebreaker.cc Exploit_12633821.exe (PID: 6320)
- OperaGX.exe (PID: 6864)
- setup.exe (PID: 6920)
- setup.exe (PID: 6896)
- setup.exe (PID: 7008)
- setup.exe (PID: 7044)
- setup.exe (PID: 7100)
- Opera_GX_assistant_73.0.3856.382_Setup.exe_sfx.exe (PID: 4392)
Checks supported languages
- bytebreaker.cc Exploit_12633821.exe (PID: 6320)
- OperaGX.exe (PID: 6864)
- setup.exe (PID: 6920)
- setup.exe (PID: 7008)
- setup.exe (PID: 6896)
- setup.exe (PID: 7044)
- setup.exe (PID: 7100)
- Opera_GX_assistant_73.0.3856.382_Setup.exe_sfx.exe (PID: 4392)
- assistant_installer.exe (PID: 6712)
- assistant_installer.exe (PID: 6736)
- ContentI3.exe (PID: 6596)
Reads the computer name
- bytebreaker.cc Exploit_12633821.exe (PID: 6320)
- setup.exe (PID: 6896)
- setup.exe (PID: 7044)
- assistant_installer.exe (PID: 6712)
- ContentI3.exe (PID: 6596)
Reads the machine GUID from the registry
- bytebreaker.cc Exploit_12633821.exe (PID: 6320)
- setup.exe (PID: 6896)
Checks proxy server information
- bytebreaker.cc Exploit_12633821.exe (PID: 6320)
- setup.exe (PID: 6896)
Creates files or folders in the user directory
- bytebreaker.cc Exploit_12633821.exe (PID: 6320)
- setup.exe (PID: 6896)
- setup.exe (PID: 6920)
- setup.exe (PID: 7044)
- ContentI3.exe (PID: 6596)
Reads the software policy settings
- bytebreaker.cc Exploit_12633821.exe (PID: 6320)
- setup.exe (PID: 6896)
Create files in a temporary directory
- OperaGX.exe (PID: 6864)
- setup.exe (PID: 6896)
- setup.exe (PID: 6920)
- setup.exe (PID: 7008)
- setup.exe (PID: 7044)
- setup.exe (PID: 7100)
- Opera_GX_assistant_73.0.3856.382_Setup.exe_sfx.exe (PID: 4392)
- bytebreaker.cc Exploit_12633821.exe (PID: 6320)
Process checks computer location settings
- bytebreaker.cc Exploit_12633821.exe (PID: 6320)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:10:18 17:00:18+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.22 |
| CodeSize: | 4353024 |
| InitializedDataSize: | 1675776 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x398c98 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Unknown (0) |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| FileDescription: | Download Manager |
| FileVersion: | 1 |
| InternalName: | Download Manager |
| LegalCopyright: | Download Manager |
| OriginalFileName: | Download Manager |
| ProductName: | Download Manager |
| ProductVersion: | 1 |
Total processes
139
Monitored processes
13
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4392 | "C:\Users\admin\AppData\Local\Temp\.opera\Opera GX Installer Temp\opera_package_202502091844531\assistant\Opera_GX_assistant_73.0.3856.382_Setup.exe_sfx.exe" | C:\Users\admin\AppData\Local\Temp\.opera\Opera GX Installer Temp\opera_package_202502091844531\assistant\Opera_GX_assistant_73.0.3856.382_Setup.exe_sfx.exe | setup.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Opera installer SFX Exit code: 0 Version: 73.0.3856.382 Modules
| |||||||||||||||
| 6184 | "C:\Users\admin\AppData\Local\Temp\bytebreaker.cc Exploit_12633821.exe" | C:\Users\admin\AppData\Local\Temp\bytebreaker.cc Exploit_12633821.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Download Manager Exit code: 3221226540 Version: 1 Modules
| |||||||||||||||
| 6320 | "C:\Users\admin\AppData\Local\Temp\bytebreaker.cc Exploit_12633821.exe" | C:\Users\admin\AppData\Local\Temp\bytebreaker.cc Exploit_12633821.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Download Manager Version: 1 Modules
| |||||||||||||||
| 6596 | "C:\Users\admin\AppData\Local\Temp\PremierOpinion\ContentI3.exe" -c:1538 -t:InstallUnion | C:\Users\admin\AppData\Local\Temp\PremierOpinion\ContentI3.exe | bytebreaker.cc Exploit_12633821.exe | ||||||||||||
User: admin Company: VoiceFive Networks, Inc. Integrity Level: HIGH Description: PremierOpinion Installer Exit code: 0 Version: 1.0.8.1 (Build 1) Modules
| |||||||||||||||
| 6712 | "C:\Users\admin\AppData\Local\Temp\.opera\Opera GX Installer Temp\opera_package_202502091844531\assistant\assistant_installer.exe" --version | C:\Users\admin\AppData\Local\Temp\.opera\Opera GX Installer Temp\opera_package_202502091844531\assistant\assistant_installer.exe | setup.exe | ||||||||||||
User: admin Company: Opera Software Integrity Level: HIGH Description: Opera GX Browser Assistant Installer Exit code: 0 Version: 73.0.3856.382 Modules
| |||||||||||||||
| 6736 | "C:\Users\admin\AppData\Local\Temp\.opera\Opera GX Installer Temp\opera_package_202502091844531\assistant\assistant_installer.exe" --type=crashpad-handler /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Roaming\Opera Software\Opera GX Stable\Crash Reports" "--crash-count-file=C:\Users\admin\AppData\Roaming\Opera Software\Opera GX Stable\crash_count.txt" --url=https://crashstats-collector.opera.com/collector/submit --annotation=channel=Stable --annotation=plat=Win32 --annotation=prod=OperaDesktopGX --annotation=ver=73.0.3856.382 --initial-client-data=0x2a4,0x2a8,0x2ac,0x280,0x2b0,0x354f48,0x354f58,0x354f64 | C:\Users\admin\AppData\Local\Temp\.opera\Opera GX Installer Temp\opera_package_202502091844531\assistant\assistant_installer.exe | — | assistant_installer.exe | |||||||||||
User: admin Company: Opera Software Integrity Level: HIGH Description: Opera GX Browser Assistant Installer Exit code: 0 Version: 73.0.3856.382 Modules
| |||||||||||||||
| 6864 | C:\Users\admin\AppData\Local\OperaGX.exe --silent --allusers=0 | C:\Users\admin\AppData\Local\OperaGX.exe | bytebreaker.cc Exploit_12633821.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Opera installer SFX Version: 116.0.5366.103 Modules
| |||||||||||||||
| 6896 | C:\Users\admin\AppData\Local\Temp\7zS0DAEC1E3\setup.exe --silent --allusers=0 --server-tracking-blob=MGFkYzI2N2UwMTkxNmIyN2Q0YmYzZmUwNmQ1OWI3ZDhhZTZmNzk5ZDdlM2VmYjBlMjRmYmFlN2I3ODBhZWVmMzp7ImNvdW50cnkiOiJERSIsImVkaXRpb24iOiJzdGQtMiIsImluc3RhbGxlcl9uYW1lIjoiT3BlcmFHWFNldHVwLmV4ZSIsInByb2R1Y3QiOiJvcGVyYV9neCIsInF1ZXJ5IjoiL29wZXJhX2d4L3N0YWJsZS9lZGl0aW9uL3N0ZC0yP3V0bV9zb3VyY2U9UFdOZ2FtZXMmdXRtX21lZGl1bT1wYSZ1dG1fY2FtcGFpZ249UFdOX0RFX1BCNV85NDE2XzM1NzUmdXRtX2lkPTBjZjAyOGMzMWMxMjQ0MDM4MzBiMDAxOWVhMjdmZDY4IiwidGltZXN0YW1wIjoiMTczOTEyNjY5MC41MDAwIiwidXNlcmFnZW50IjoiTW96aWxsYS80LjAgKGNvbXBhdGlibGU7IE1TSUUgNy4wOyBXaW5kb3dzIE5UIDYuMjsgV09XNjQ7IFRyaWRlbnQvNy4wOyAuTkVUNC4wQzsgLk5FVDQuMEU7IC5ORVQgQ0xSIDIuMC41MDcyNzsgLk5FVCBDTFIgMy4wLjMwNzI5OyAuTkVUIENMUiAzLjUuMzA3MjkpIiwidXRtIjp7ImNhbXBhaWduIjoiUFdOX0RFX1BCNV85NDE2XzM1NzUiLCJpZCI6IjBjZjAyOGMzMWMxMjQ0MDM4MzBiMDAxOWVhMjdmZDY4IiwibWVkaXVtIjoicGEiLCJzb3VyY2UiOiJQV05nYW1lcyJ9LCJ1dWlkIjoiMGJjYWI3NGItYTNiYS00YjFhLWFjNDgtZTEwMWZlMmZjYzNkIn0= | C:\Users\admin\AppData\Local\Temp\7zS0DAEC1E3\setup.exe | OperaGX.exe | ||||||||||||
User: admin Company: Opera Software Integrity Level: HIGH Description: Opera GX Installer Version: 116.0.5366.103 Modules
| |||||||||||||||
| 6920 | C:\Users\admin\AppData\Local\Temp\7zS0DAEC1E3\setup.exe --type=crashpad-handler /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Roaming\Opera Software\Opera GX Stable\Crash Reports" "--crash-count-file=C:\Users\admin\AppData\Roaming\Opera Software\Opera GX Stable\crash_count.txt" --url=https://crashstats-collector-2.opera.com/ --annotation=channel=Stable --annotation=plat=Win32 --annotation=prod=OperaDesktopGX --annotation=ver=116.0.5366.103 --initial-client-data=0x32c,0x330,0x334,0x308,0x338,0x71be300c,0x71be3018,0x71be3024 | C:\Users\admin\AppData\Local\Temp\7zS0DAEC1E3\setup.exe | setup.exe | ||||||||||||
User: admin Company: Opera Software Integrity Level: HIGH Description: Opera GX Installer Version: 116.0.5366.103 Modules
| |||||||||||||||
Total events
7 436
Read events
7 416
Write events
18
Delete events
2
Modification events
| (PID) Process: | (6320) bytebreaker.cc Exploit_12633821.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6320) bytebreaker.cc Exploit_12633821.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6320) bytebreaker.cc Exploit_12633821.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6320) bytebreaker.cc Exploit_12633821.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Opera |
| Operation: | write | Name: | installed |
Value: 1 | |||
| (PID) Process: | (6896) setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6896) setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6896) setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (7044) setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Opera Software |
| Operation: | write | Name: | Last Opera GX Stable Install Path |
Value: C:\Users\admin\AppData\Local\Programs\Opera GX\ | |||
| (PID) Process: | (6320) bytebreaker.cc Exploit_12633821.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\InstallUnion\1538 |
| Operation: | write | Name: | BundleOfferActionUid |
Value: qE2Aawm_QDsaO10rT55555 | |||
| (PID) Process: | (6320) bytebreaker.cc Exploit_12633821.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\InstallUnion\1538 |
| Operation: | write | Name: | dt_age |
Value: 1 | |||
Executable files
17
Suspicious files
48
Text files
13
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6320 | bytebreaker.cc Exploit_12633821.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:C9BE626E9715952E9B70F92F912B9787 | SHA256:C13E8D22800C200915F87F71C31185053E4E60CA25DE2E41E160E09CD2D815D4 | |||
| 6320 | bytebreaker.cc Exploit_12633821.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:68861DEA2DB0FB8BBC578265E63BC767 | SHA256:F8DE27E76515C3BB89834334137168989E154AC9B369550CA3BD1A0A3835E0AA | |||
| 6320 | bytebreaker.cc Exploit_12633821.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\service[1].htm | text | |
MD5:1894A65D335B50555DAE4F84DFC3D19C | SHA256:B70098A064973CA926DBF950F5320E696A894EB88E81E2059D8547E9966CCDAC | |||
| 6320 | bytebreaker.cc Exploit_12633821.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\923CD0F3EDBB3759A875E7FE664C6C90_E177412028F15791C29E67CACD8927FC | binary | |
MD5:53D1D70D928A5A5F1938BA3F97102707 | SHA256:738166E3C800F8B8317CAD076B3574CB891F235860A30DB6BB4F76A98304EAEB | |||
| 6320 | bytebreaker.cc Exploit_12633821.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\geo[1].htm | text | |
MD5:01547D40A85775CFD194C6F25AEE2E1A | SHA256:664CC2D99589643856CCF0577110AA8BF489AA1045EFC56D3B5CA31C3633FF19 | |||
| 6320 | bytebreaker.cc Exploit_12633821.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\923CD0F3EDBB3759A875E7FE664C6C90_E177412028F15791C29E67CACD8927FC | binary | |
MD5:7ECD5841EEA1E46CFE770D0B1C891A04 | SHA256:ADBF48DCAF10123316CC38B65690B43896C867CED9B2DCD948E67CE94D0E6D7F | |||
| 6320 | bytebreaker.cc Exploit_12633821.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\05DDC6AA91765AACACDB0A5F96DF8199 | binary | |
MD5:EB4224E5E8B0C834065DDFE3430F81C9 | SHA256:FDAFE1BBFDD38CC9BBD663945258B221786D28FC5BFCB138F4F46ED8B5C3765D | |||
| 6320 | bytebreaker.cc Exploit_12633821.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\05DDC6AA91765AACACDB0A5F96DF8199 | binary | |
MD5:E935BC5762068CAF3E24A2683B1B8A88 | SHA256:A8ACCFCFEB51BD73DF23B91F4D89FF1A9EB7438EF5B12E8AFDA1A6FF1769E89D | |||
| 6320 | bytebreaker.cc Exploit_12633821.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:971C514F84BBA0785F80AA1C23EDFD79 | SHA256:F157ED17FCAF8837FA82F8B69973848C9B10A02636848F995698212A08F31895 | |||
| 6320 | bytebreaker.cc Exploit_12633821.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C2C9D7FCC58B6FD9BF152E66809C1BBE_9962014287DF49023620C3F0C27B8ACE | binary | |
MD5:8A42BA5FC10C31769D97C1C3EB8DC434 | SHA256:8B634DF94073701A1A8A5BCD84B702C0EFC3429E36BF0EADE8BE6A0C8CEEA172 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
27
TCP/UDP connections
57
DNS requests
33
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6896 | setup.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | — | — | whitelisted |
5532 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6320 | bytebreaker.cc Exploit_12633821.exe | GET | 200 | 142.250.184.227:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | whitelisted |
6320 | bytebreaker.cc Exploit_12633821.exe | GET | 200 | 142.250.184.227:80 | http://o.pki.goog/s/wr3/URM/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQSq0i5t2Pafi2Gw9uzwnc7KTctWgQUx4H1%2FY6I2QA8TWOiUDEkoM4j%2FiMCEFET1OsgXJOMCsceBPevDRA%3D | unknown | — | — | whitelisted |
6320 | bytebreaker.cc Exploit_12633821.exe | GET | 200 | 142.250.184.227:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6320 | bytebreaker.cc Exploit_12633821.exe | GET | 200 | 18.245.38.41:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEkzUBtJnwJkc3SmanzgxeYU%3D | unknown | — | — | whitelisted |
6320 | bytebreaker.cc Exploit_12633821.exe | GET | 200 | 142.250.184.227:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
6320 | bytebreaker.cc Exploit_12633821.exe | GET | 200 | 142.250.184.227:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | whitelisted |
6320 | bytebreaker.cc Exploit_12633821.exe | GET | 200 | 142.250.184.227:80 | http://o.pki.goog/s/wr3/fgA/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQSq0i5t2Pafi2Gw9uzwnc7KTctWgQUx4H1%2FY6I2QA8TWOiUDEkoM4j%2FiMCEH4AzC8CtsuHCuCmoKpV7Vk%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6076 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6320 | bytebreaker.cc Exploit_12633821.exe | 35.190.60.70:443 | www.dlsft.com | GOOGLE | US | whitelisted |
6320 | bytebreaker.cc Exploit_12633821.exe | 142.250.184.227:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
6320 | bytebreaker.cc Exploit_12633821.exe | 104.21.96.1:443 | filedm.com | CLOUDFLARENET | — | malicious |
1076 | svchost.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 40.126.31.129:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
6320 | bytebreaker.cc Exploit_12633821.exe | 13.32.121.122:443 | dpd.securestudies.com | AMAZON-02 | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.dlsft.com |
| unknown |
ocsp.pki.goog |
| whitelisted |
c.pki.goog |
| whitelisted |
o.pki.goog |
| whitelisted |
dlsft.com |
| unknown |
filedm.com |
| malicious |
go.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
dpd.securestudies.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| whitelisted |
Threats
Process | Message |
|---|---|
bytebreaker.cc Exploit_12633821.exe | at getFileInfo.@307@46 (this://app/main.html(329))
|
bytebreaker.cc Exploit_12633821.exe | Error: (undefined) has no property - value
|
bytebreaker.cc Exploit_12633821.exe | |
bytebreaker.cc Exploit_12633821.exe | |
bytebreaker.cc Exploit_12633821.exe | at initializeDynamicVariables (this://app/main.html(351))
|
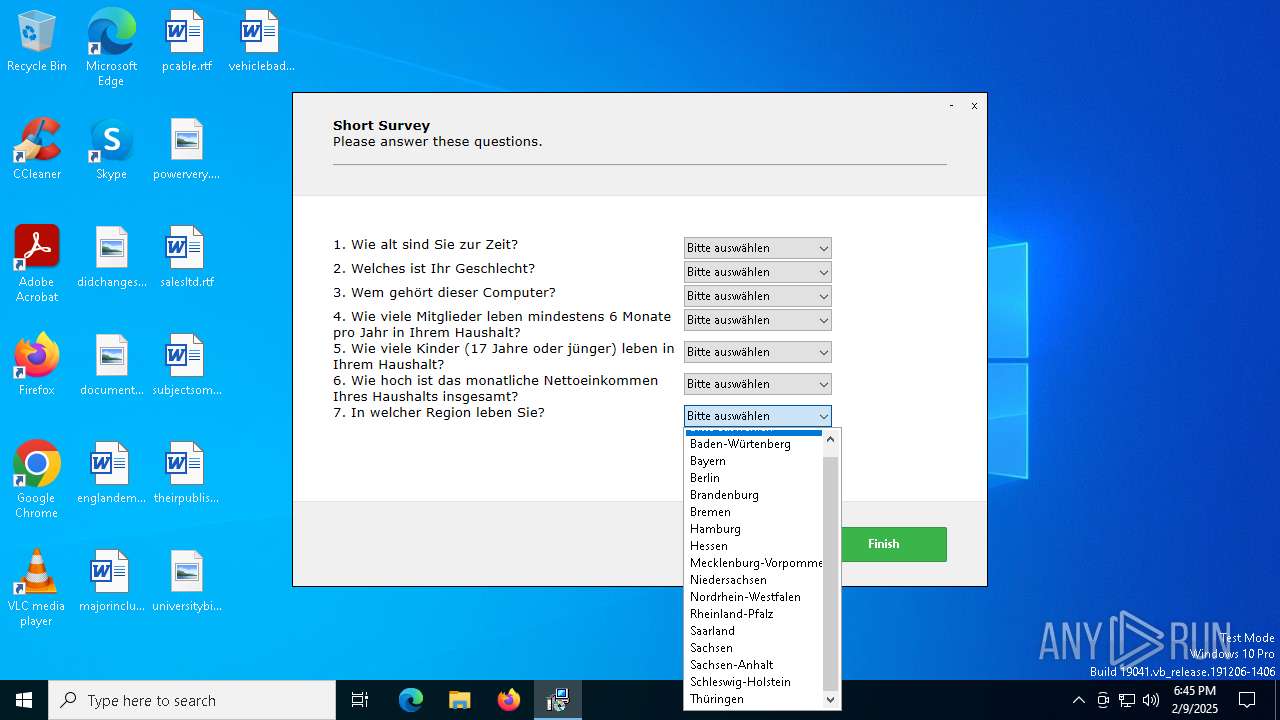
bytebreaker.cc Exploit_12633821.exe | scanning node questions /questions
|
bytebreaker.cc Exploit_12633821.exe | scanning node question /questions/question
|
bytebreaker.cc Exploit_12633821.exe | scanning node question /questions/question
|
bytebreaker.cc Exploit_12633821.exe | scanning node question /questions/question
|
bytebreaker.cc Exploit_12633821.exe | scanning node question /questions/question
|