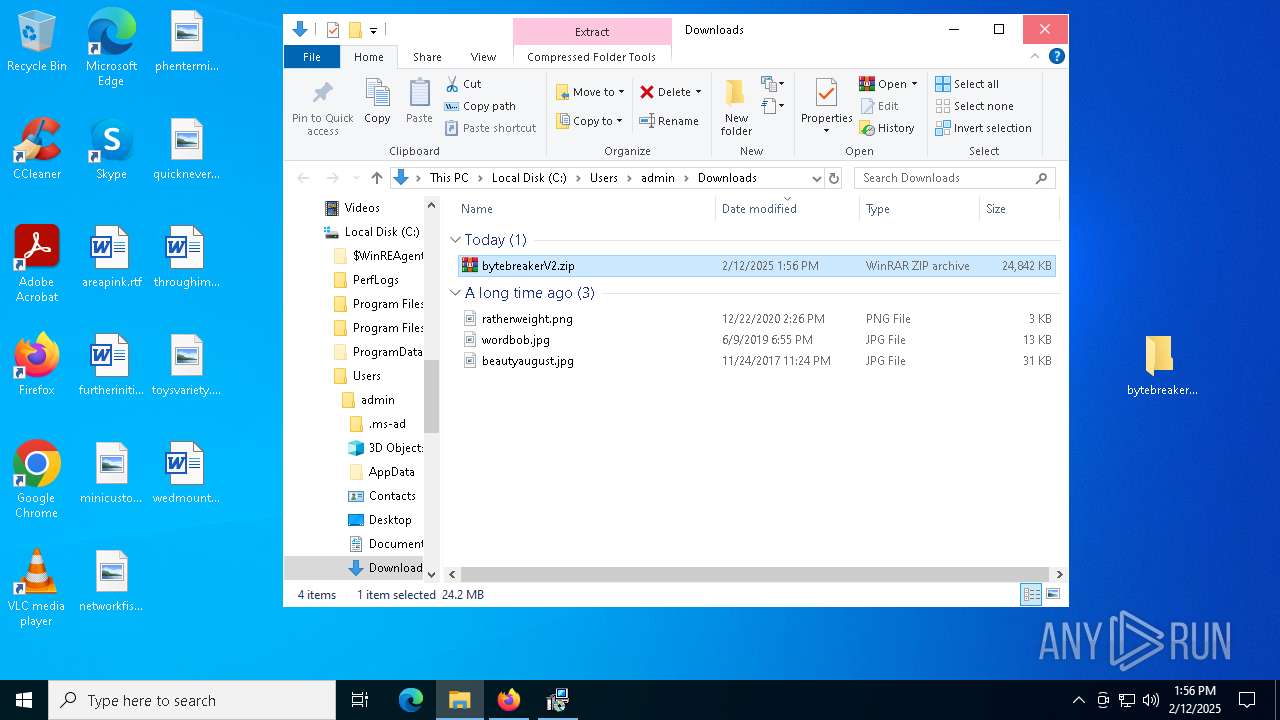
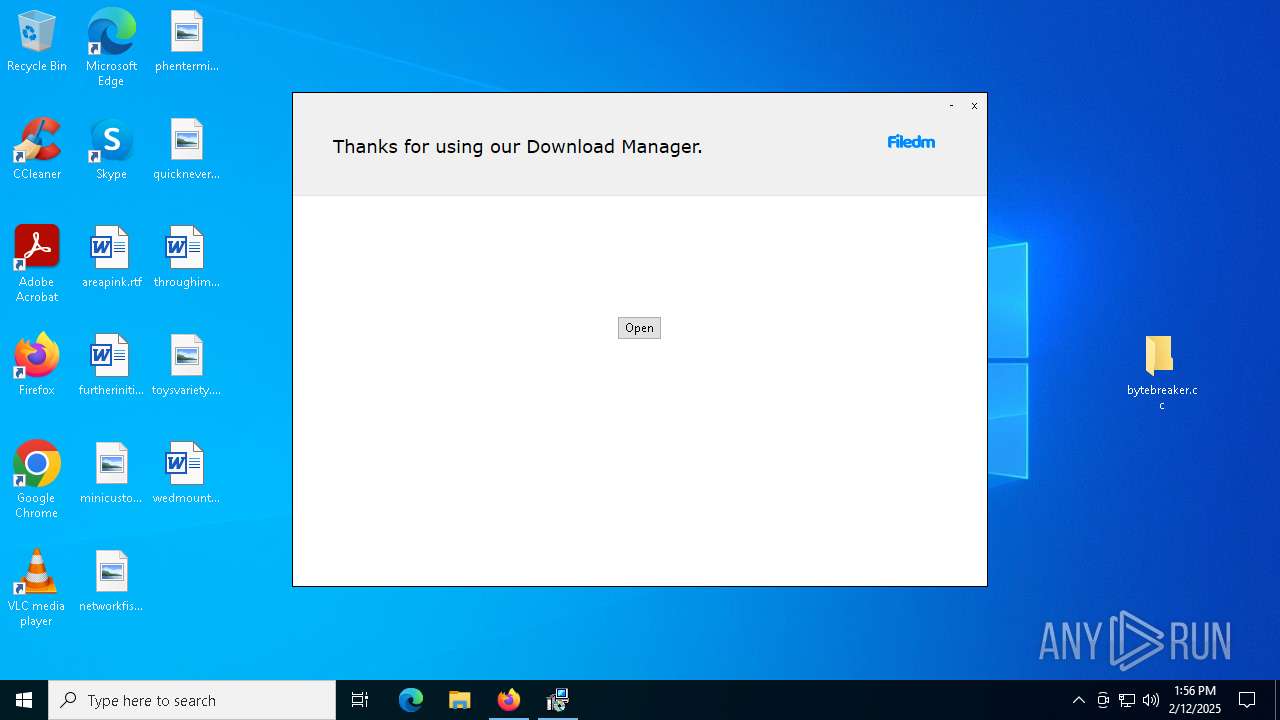
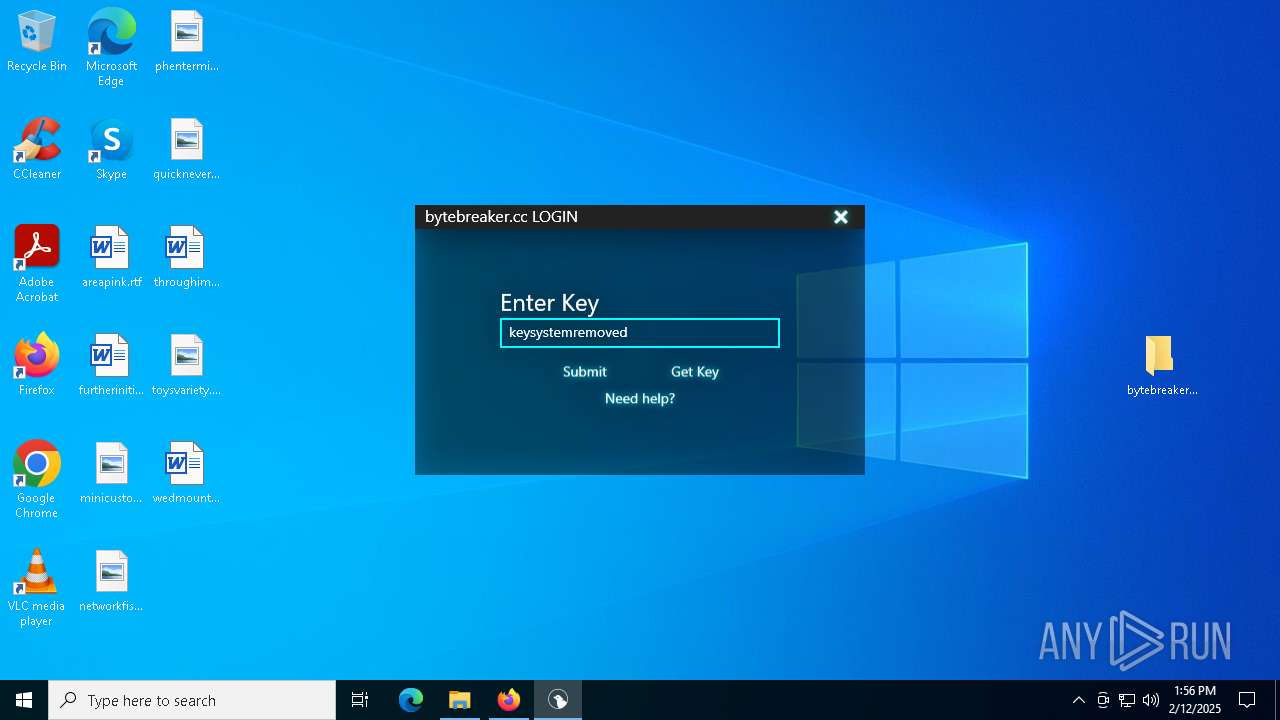
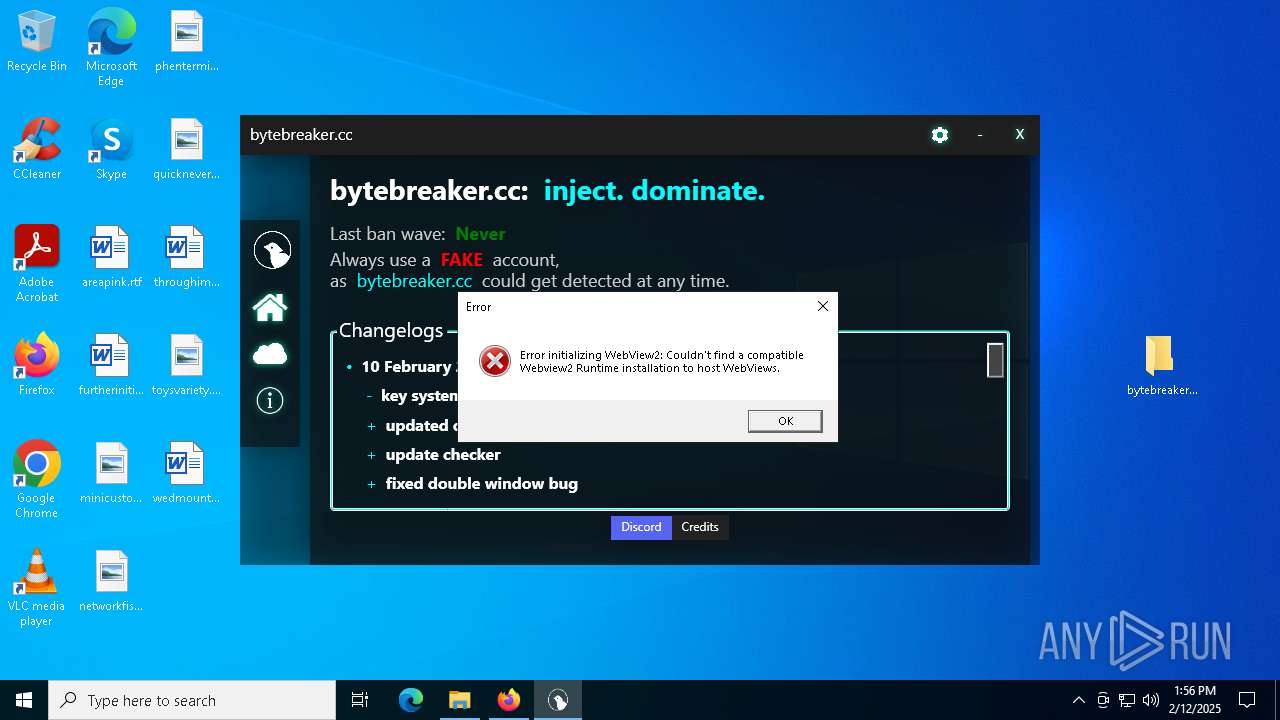
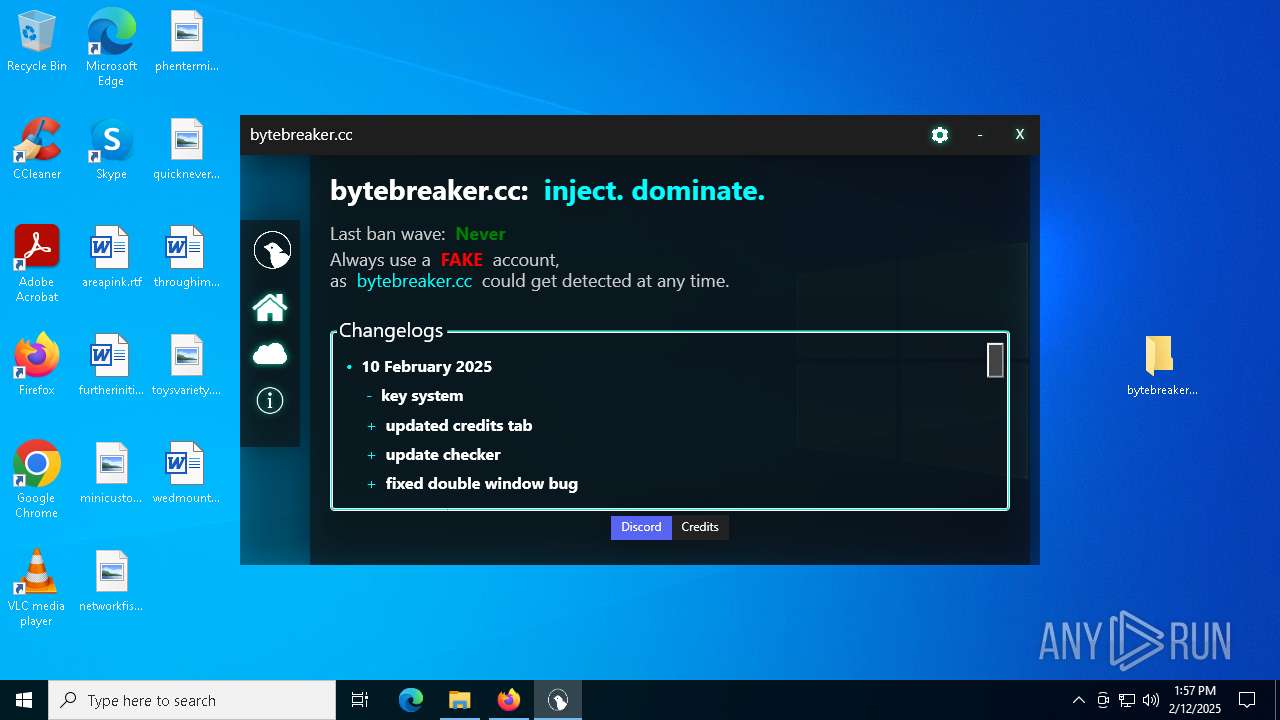
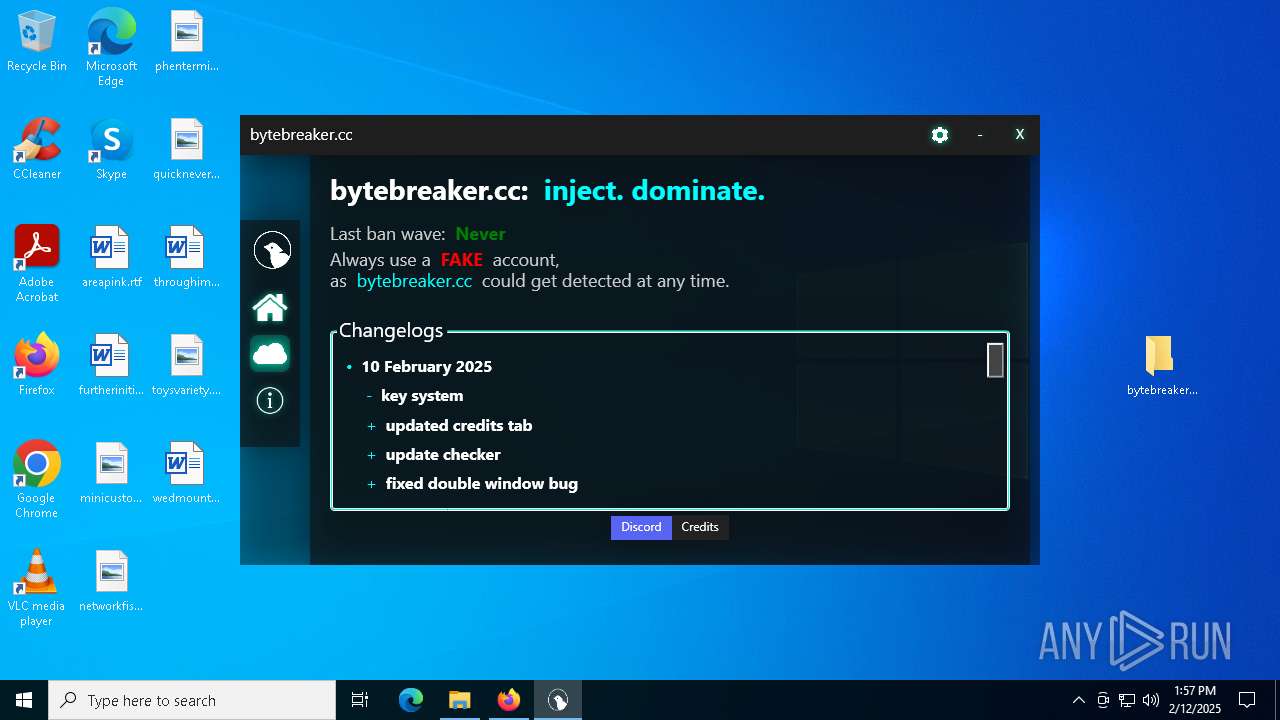
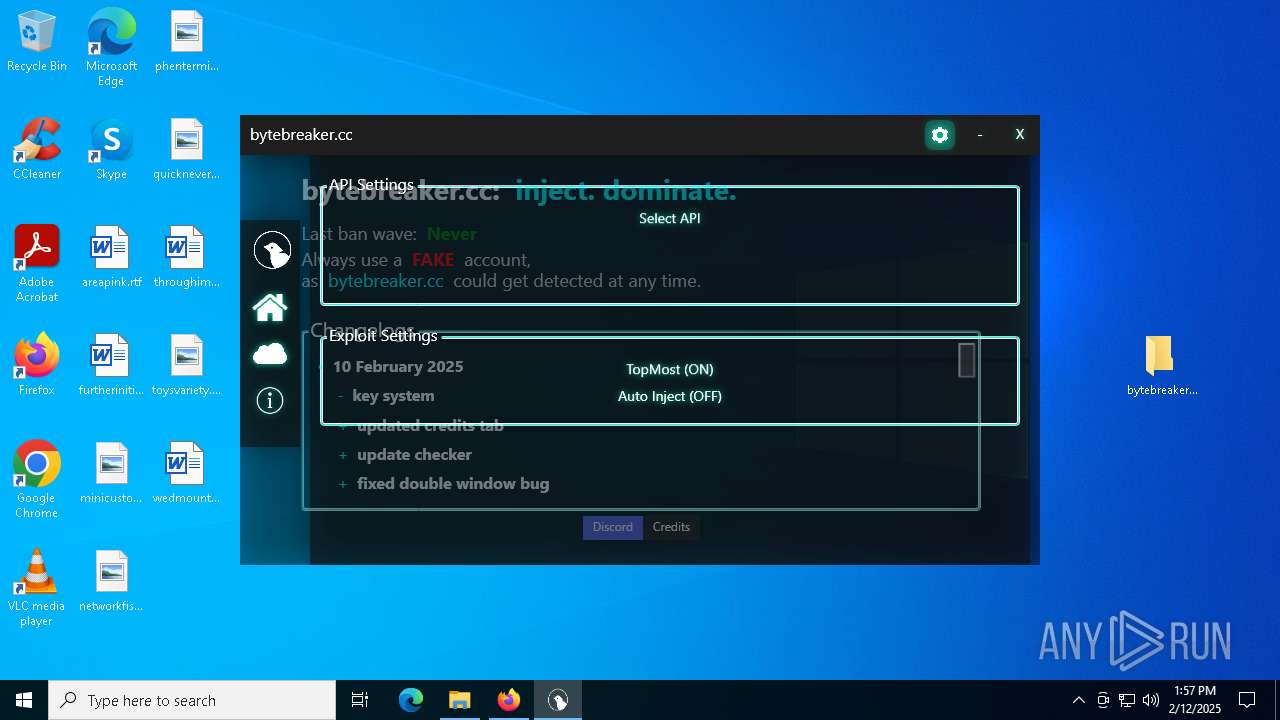
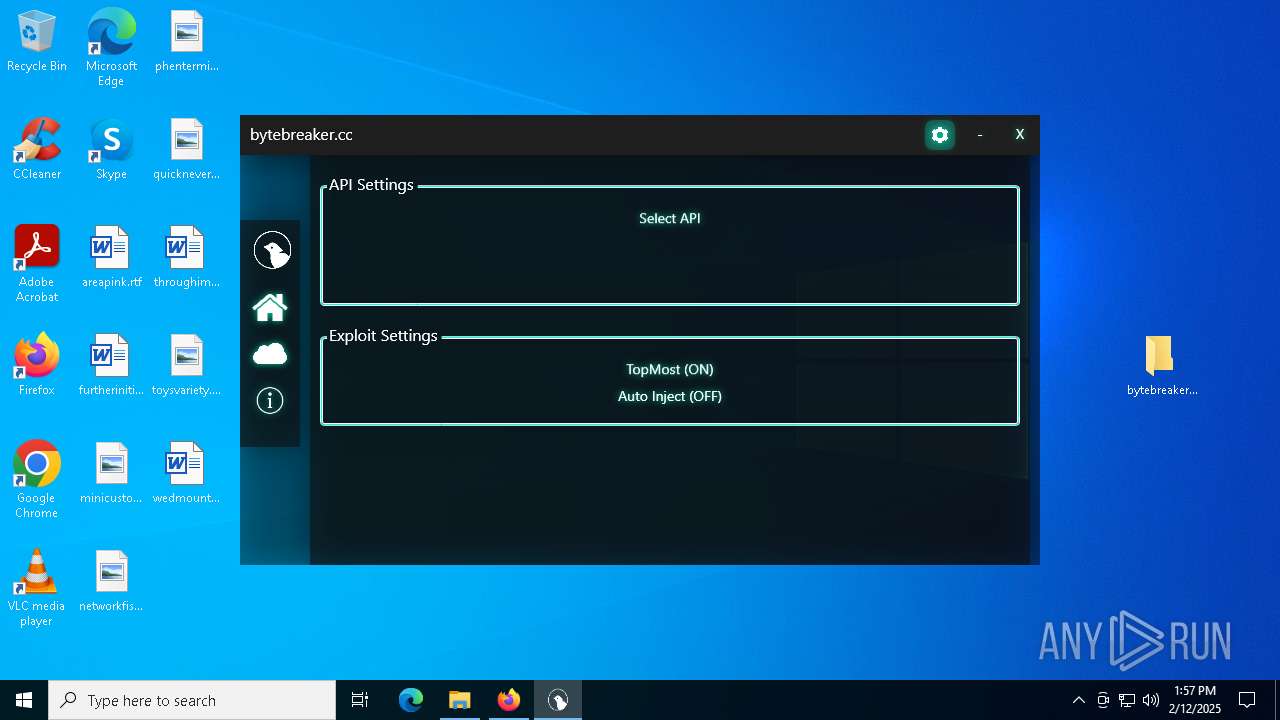
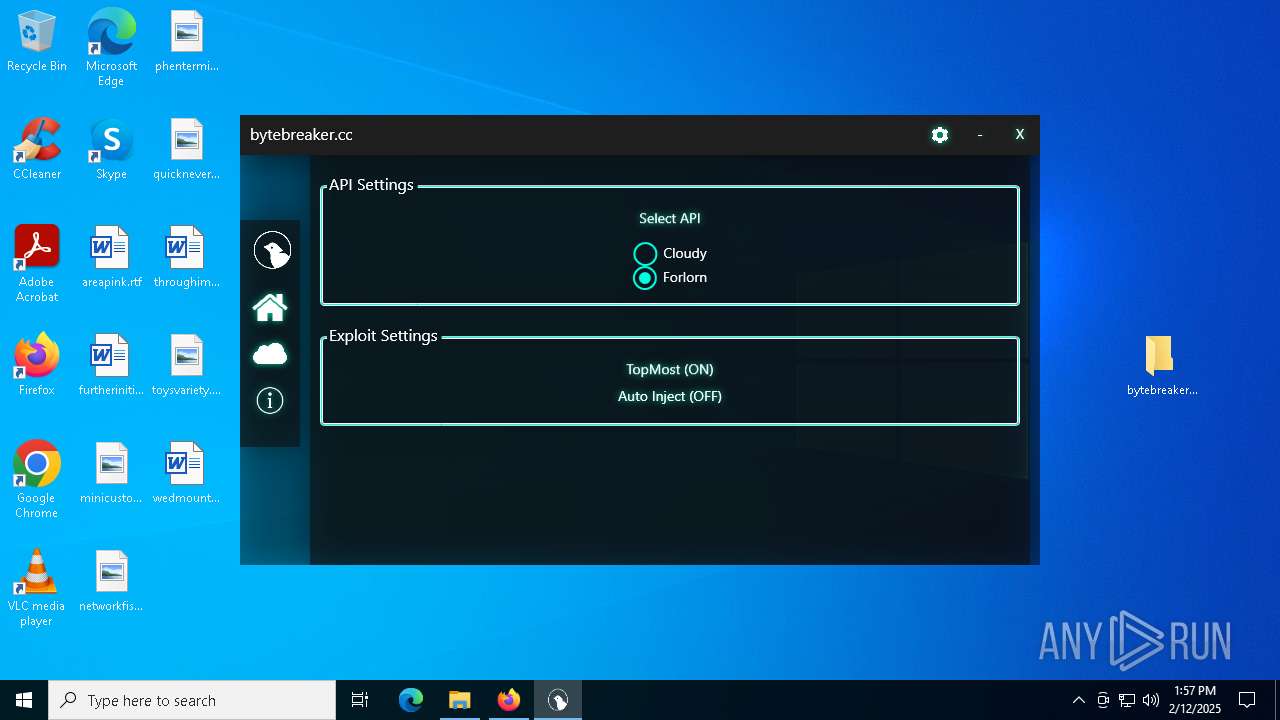
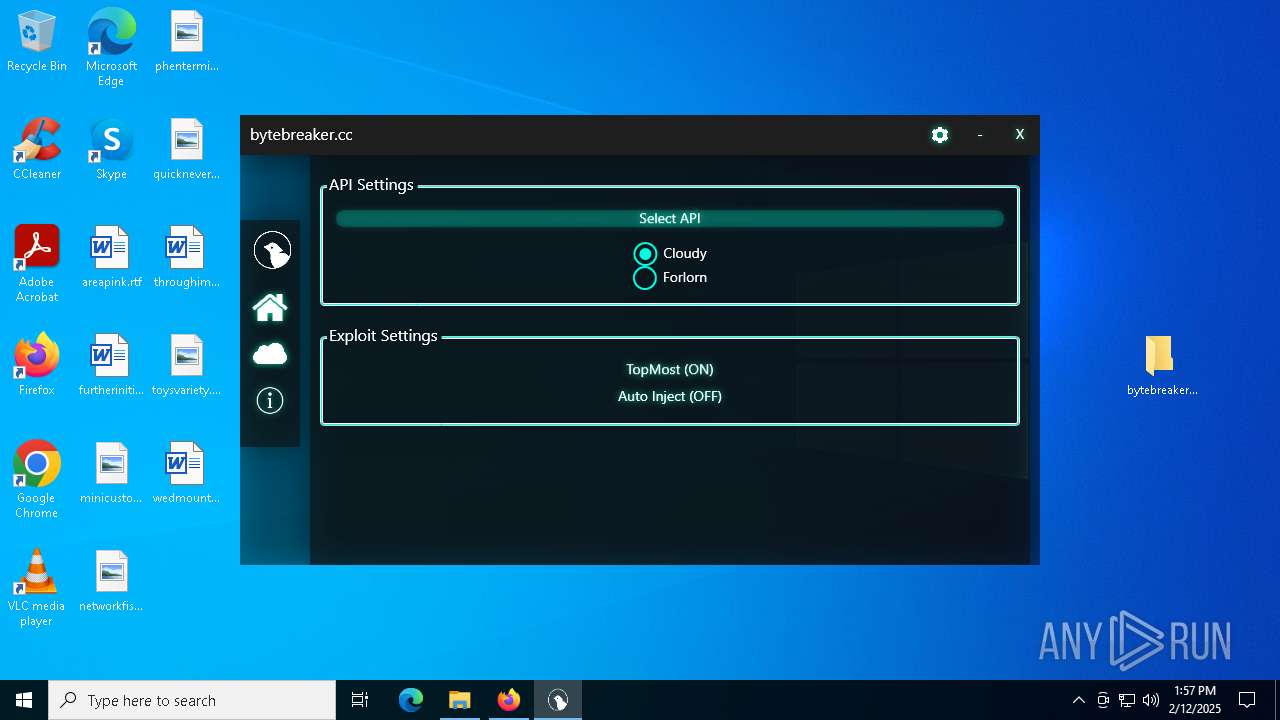
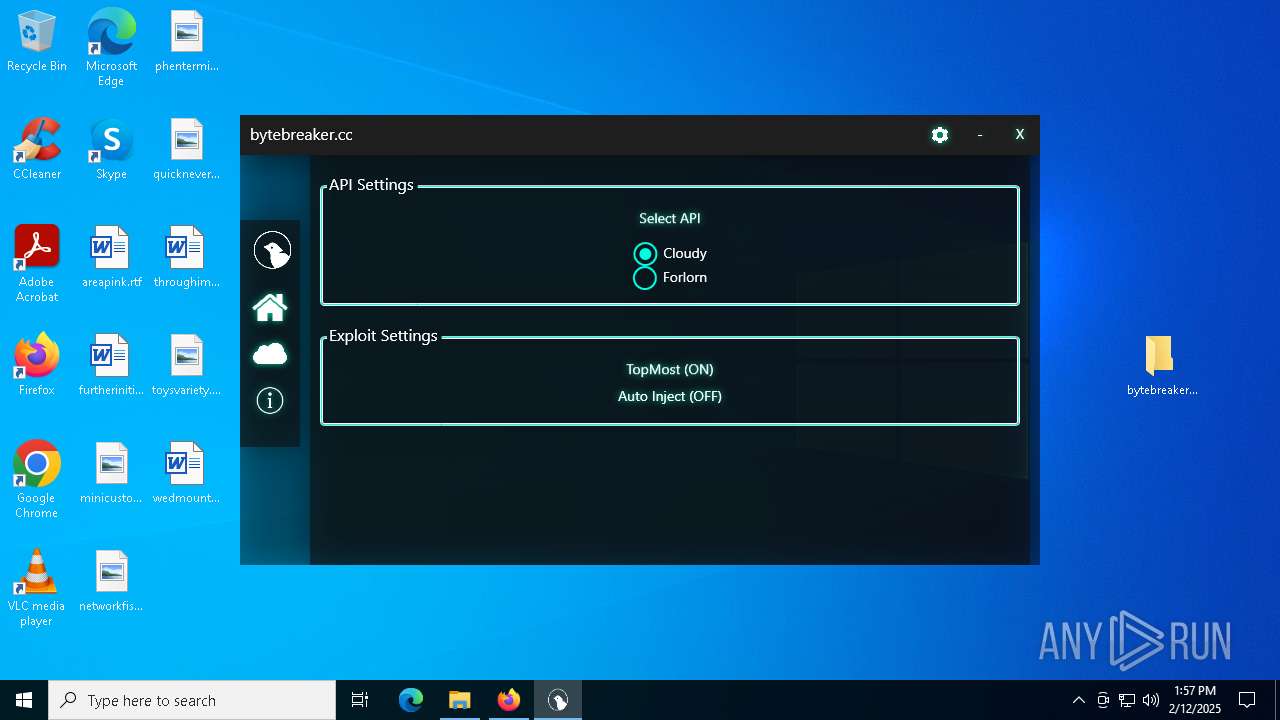
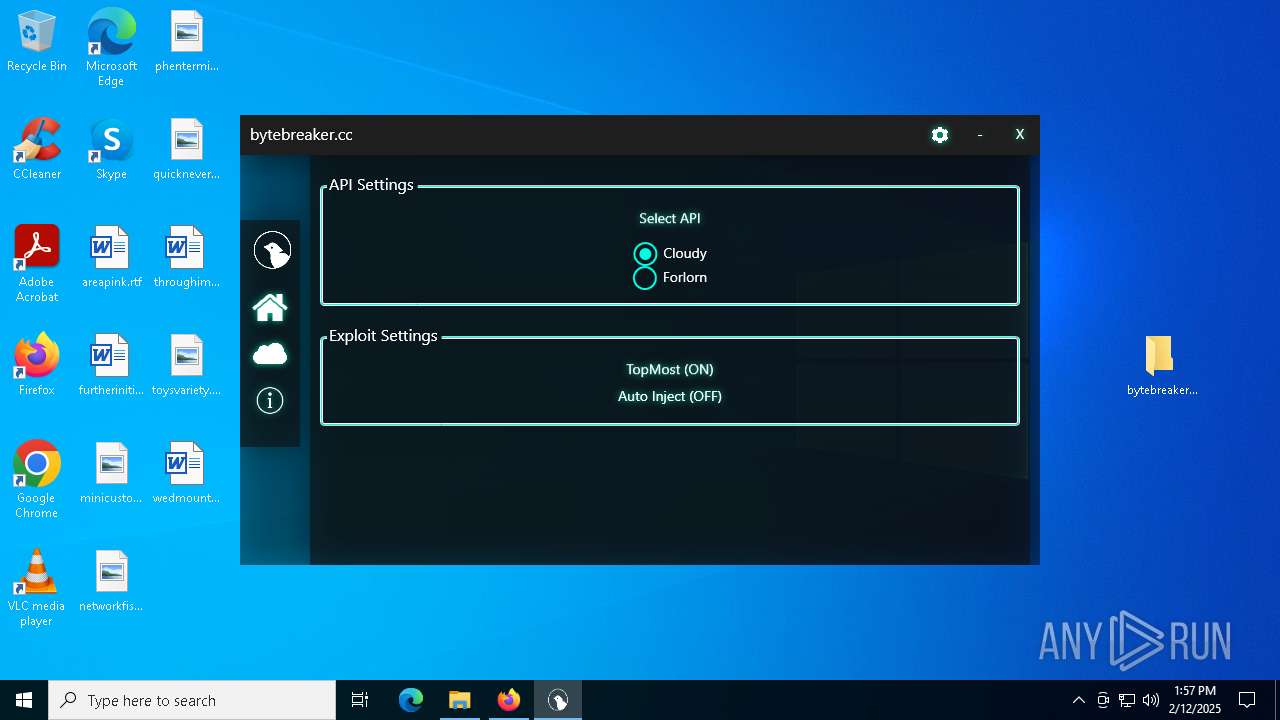
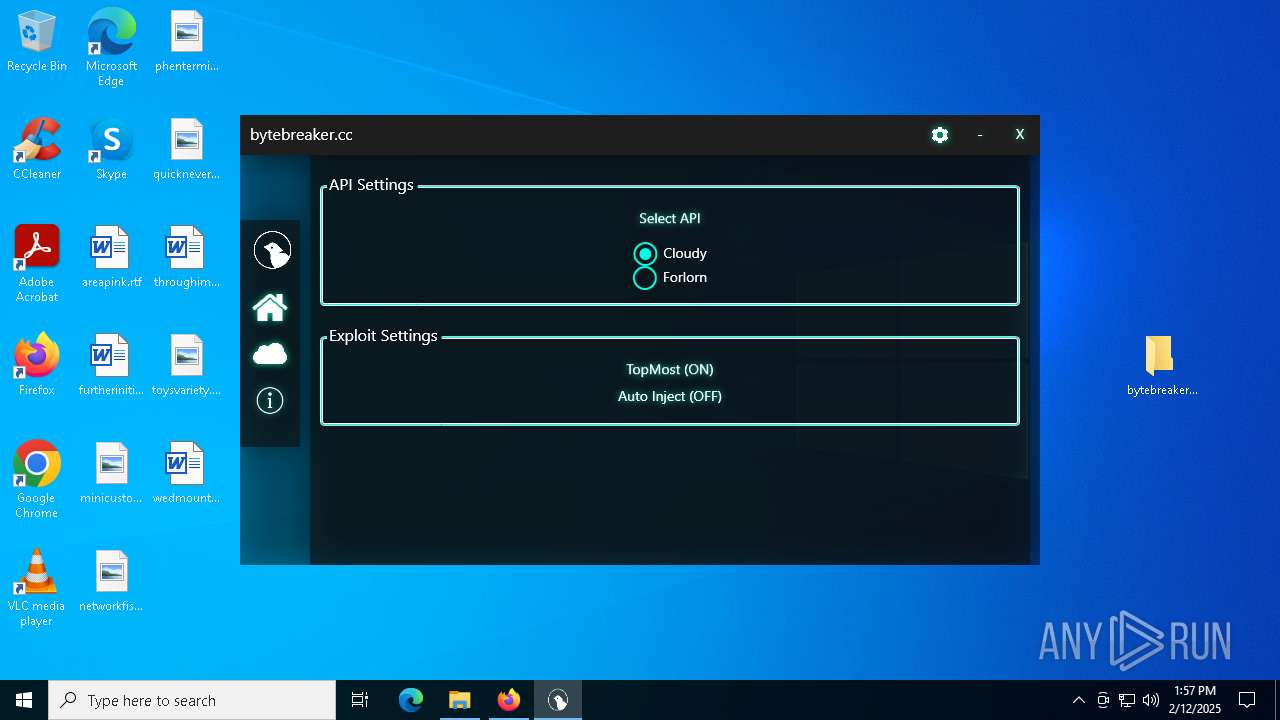
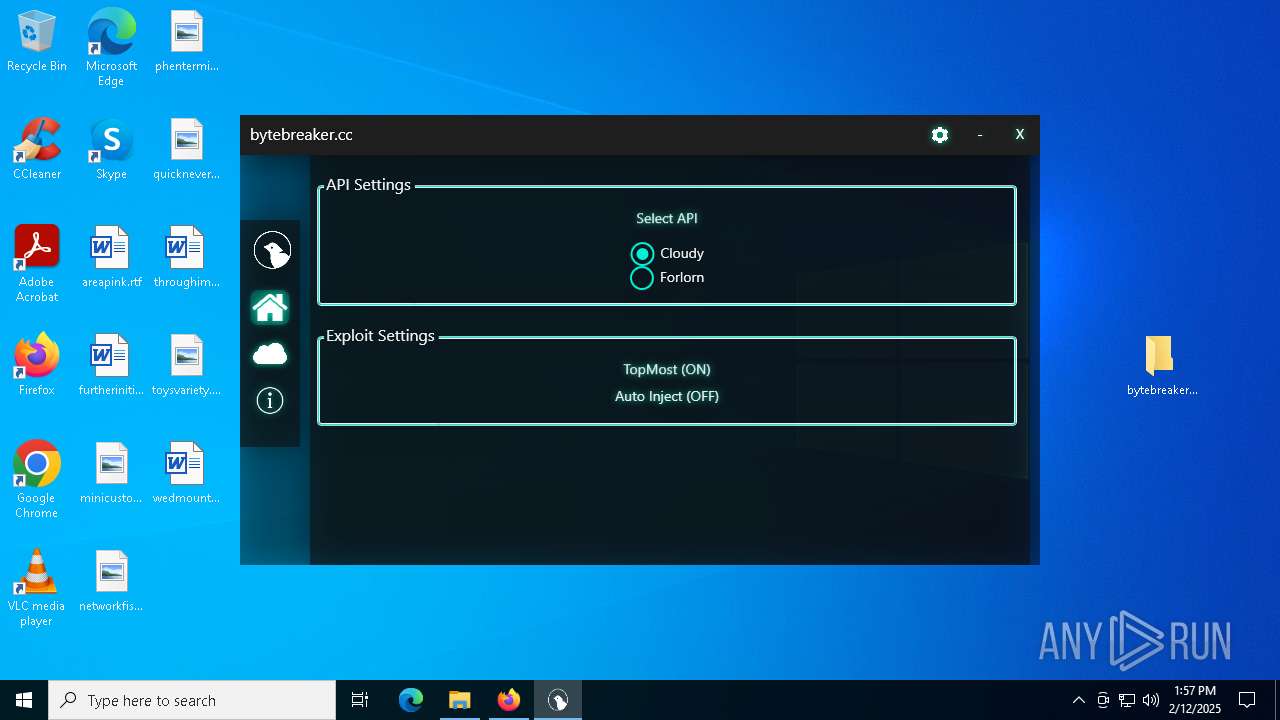
| File name: | bytebreaker.cc Exploit_31035209.exe |
| Full analysis: | https://app.any.run/tasks/7e3e143c-80ad-422f-a68b-82192457f476 |
| Verdict: | Malicious activity |
| Analysis date: | February 12, 2025, 13:55:06 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 15D1C495FF66BF7CEA8A6D14BFDF0A20 |
| SHA1: | 942814521FA406A225522F208AC67F90DBDE0AE7 |
| SHA256: | 61C2C4A5D7C14F77EE88871DED4CC7F1E49DAE3E4EF209504C66FEDF4D22DE42 |
| SSDEEP: | 98304:DtjM+LgnHM8mNLNpOmMGl2p9tjIQh+1GHp8PGmDFzMVv3kdcpR41TBN14BC6SkPT:Kw8 |
MALICIOUS
GENERIC has been found (auto)
- bytebreaker.cc Exploit_31035209.exe (PID: 6512)
SUSPICIOUS
Reads security settings of Internet Explorer
- bytebreaker.cc Exploit_31035209.exe (PID: 6512)
There is functionality for taking screenshot (YARA)
- bytebreaker.cc Exploit_31035209.exe (PID: 6512)
Start notepad (likely ransomware note)
- bytebreaker.cc Exploit_31035209.exe (PID: 6512)
Checks Windows Trust Settings
- bytebreaker.cc Exploit_31035209.exe (PID: 6512)
Process drops legitimate windows executable
- WinRAR.exe (PID: 6032)
INFO
Checks proxy server information
- bytebreaker.cc Exploit_31035209.exe (PID: 6512)
- bytebreaker.exe (PID: 4996)
Creates files or folders in the user directory
- bytebreaker.cc Exploit_31035209.exe (PID: 6512)
Reads the computer name
- bytebreaker.cc Exploit_31035209.exe (PID: 6512)
- bytebreaker.exe (PID: 4996)
Checks supported languages
- bytebreaker.cc Exploit_31035209.exe (PID: 6512)
- bytebreaker.exe (PID: 4996)
Reads the machine GUID from the registry
- bytebreaker.cc Exploit_31035209.exe (PID: 6512)
- bytebreaker.exe (PID: 4996)
Reads security settings of Internet Explorer
- notepad.exe (PID: 6176)
Reads the software policy settings
- bytebreaker.cc Exploit_31035209.exe (PID: 6512)
- bytebreaker.exe (PID: 4996)
The sample compiled with english language support
- bytebreaker.cc Exploit_31035209.exe (PID: 6512)
- WinRAR.exe (PID: 6032)
Application launched itself
- firefox.exe (PID: 4308)
- firefox.exe (PID: 5712)
Manual execution by a user
- firefox.exe (PID: 4308)
- WinRAR.exe (PID: 6032)
- bytebreaker.exe (PID: 4996)
Process checks computer location settings
- bytebreaker.cc Exploit_31035209.exe (PID: 6512)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6032)
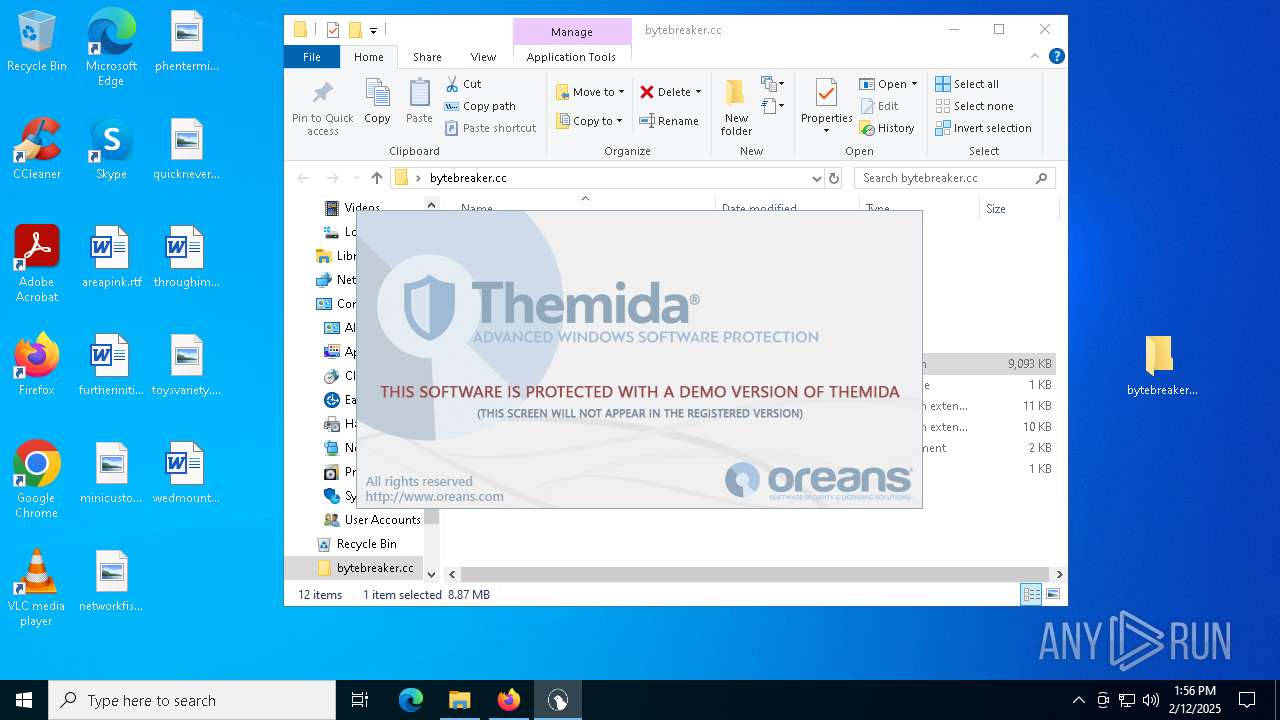
Themida protector has been detected
- bytebreaker.exe (PID: 4996)
Create files in a temporary directory
- bytebreaker.exe (PID: 4996)
Reads Environment values
- bytebreaker.exe (PID: 4996)
Disables trace logs
- bytebreaker.exe (PID: 4996)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:10:18 17:00:18+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.22 |
| CodeSize: | 4353024 |
| InitializedDataSize: | 1675776 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x398c98 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Unknown (0) |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
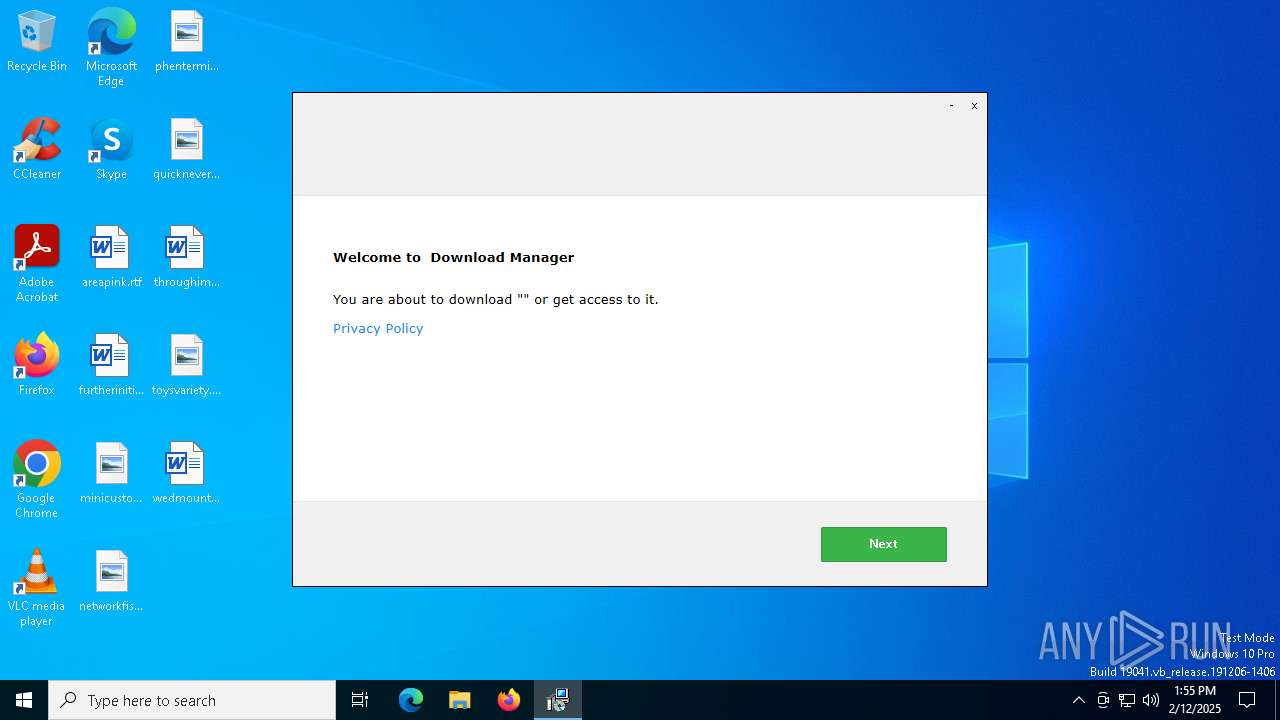
| FileDescription: | Download Manager |
| FileVersion: | 1 |
| InternalName: | Download Manager |
| LegalCopyright: | Download Manager |
| OriginalFileName: | Download Manager |
| ProductName: | Download Manager |
| ProductVersion: | 1 |
Total processes
146
Monitored processes
17
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1228 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4884 -parentBuildID 20240213221259 -sandboxingKind 0 -prefsHandle 4784 -prefMapHandle 4916 -prefsLen 36588 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {50309141-6b6a-4a87-9b73-c36b215f5bd2} 5712 "\\.\pipe\gecko-crash-server-pipe.5712" 16f2314eb10 utility | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3928 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5052 -childID 5 -isForBrowser -prefsHandle 5128 -prefMapHandle 5132 -prefsLen 31144 -prefMapSize 244583 -jsInitHandle 1156 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {ea9d7eda-b1e7-4d74-a40d-0e9712f86bfb} 5712 "\\.\pipe\gecko-crash-server-pipe.5712" 16f24520d90 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 4308 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 4708 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4992 -childID 3 -isForBrowser -prefsHandle 4984 -prefMapHandle 4980 -prefsLen 31144 -prefMapSize 244583 -jsInitHandle 1156 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {fa652d6b-3e0e-467d-bf60-bae78ba9914a} 5712 "\\.\pipe\gecko-crash-server-pipe.5712" 16f2437dd90 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 4996 | "C:\Users\admin\Desktop\bytebreaker.cc\bytebreaker.exe" | C:\Users\admin\Desktop\bytebreaker.cc\bytebreaker.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: ByteBreaker Version: 1.0.0.0 Modules
| |||||||||||||||
| 5652 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5056 -childID 4 -isForBrowser -prefsHandle 5004 -prefMapHandle 5008 -prefsLen 31144 -prefMapSize 244583 -jsInitHandle 1156 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {c84e8038-3ca2-4fd0-bb05-af9c890b31ae} 5712 "\\.\pipe\gecko-crash-server-pipe.5712" 16f2437df50 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 5712 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 6032 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\bytebreakerV2.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
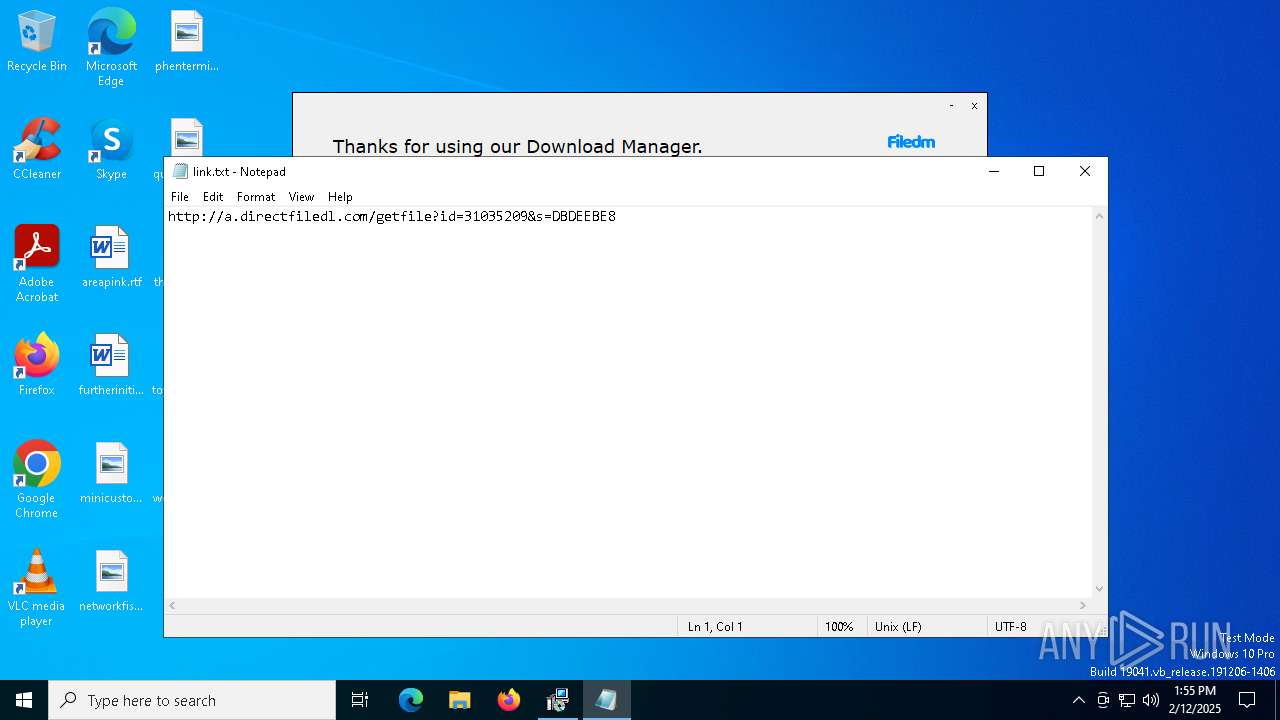
| 6176 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\link.txt | C:\Windows\SysWOW64\notepad.exe | — | bytebreaker.cc Exploit_31035209.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
17 446
Read events
17 409
Write events
37
Delete events
0
Modification events
| (PID) Process: | (6512) bytebreaker.cc Exploit_31035209.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6512) bytebreaker.cc Exploit_31035209.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6512) bytebreaker.cc Exploit_31035209.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6512) bytebreaker.cc Exploit_31035209.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.txt\OpenWithProgids |
| Operation: | write | Name: | txtfile |
Value: | |||
| (PID) Process: | (5712) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (6032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\bytebreakerV2.zip | |||
| (PID) Process: | (6032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
Executable files
13
Suspicious files
449
Text files
119
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6512 | bytebreaker.cc Exploit_31035209.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:691CC3A637642037EFB3DBAE3D9E95FC | SHA256:424825E6B2986E8B19D0D739469B6421C2FDEE2CCDAAA9D31DB4E44AB24E5B03 | |||
| 6512 | bytebreaker.cc Exploit_31035209.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\05DDC6AA91765AACACDB0A5F96DF8199 | binary | |
MD5:D4467E1D7ECE220D895D6FC4B3FE82DB | SHA256:F7DA7DC4090B477D85F45C3AB81EECB146C9E238BE767009BB8472DEAAB0ED73 | |||
| 5712 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 6512 | bytebreaker.cc Exploit_31035209.exe | C:\Users\admin\AppData\Local\link.txt | text | |
MD5:7D39AC1A6DE585EC9E5A2679389C5B8A | SHA256:D562DF8DB1247FC71F44A64EADDEE0F2564A532F287E2D50DC59833F901648DE | |||
| 6512 | bytebreaker.cc Exploit_31035209.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\923CD0F3EDBB3759A875E7FE664C6C90_E177412028F15791C29E67CACD8927FC | binary | |
MD5:37A89D3A00D7B0D408DF0FD9D9548275 | SHA256:EF6FE86D749641A700D5F6AE4AEC818D17F63F117887EC79143424BE6F18C431 | |||
| 6512 | bytebreaker.cc Exploit_31035209.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\923CD0F3EDBB3759A875E7FE664C6C90_E177412028F15791C29E67CACD8927FC | binary | |
MD5:BD282185350E0AC2B4B6EB0709F768F0 | SHA256:FB0C376214B12950E5A32859F01E78FEAA17ADB6C39AB68CA1CA9DDF27433099 | |||
| 6512 | bytebreaker.cc Exploit_31035209.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\service[1].htm | text | |
MD5:AE211C5DE70B9DE757033075E1DA99DE | SHA256:6019172E02C00F5101EDB26970F63E4A4EC87BC7ECC2255DEA39B9C56E2D3556 | |||
| 6512 | bytebreaker.cc Exploit_31035209.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:C9F5DA3AFB12C140AC9777A62CB872E8 | SHA256:7479717A3CFEC1C72184D39CAB822516E7493B42C8D0BBE0C2876A1940E894E0 | |||
| 6512 | bytebreaker.cc Exploit_31035209.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\geo[1].htm | text | |
MD5:317AA682289E804944B06F857A4EC6D1 | SHA256:DCA14E535F749FC67838B2125E5ABFBF1FDAB73CE9198CC82ED5188ED86F3346 | |||
| 6512 | bytebreaker.cc Exploit_31035209.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:C9BE626E9715952E9B70F92F912B9787 | SHA256:C13E8D22800C200915F87F71C31185053E4E60CA25DE2E41E160E09CD2D815D4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
41
TCP/UDP connections
89
DNS requests
124
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1488 | svchost.exe | GET | 200 | 23.48.23.190:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.190:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1488 | svchost.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6512 | bytebreaker.cc Exploit_31035209.exe | GET | 200 | 172.217.23.99:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | whitelisted |
6512 | bytebreaker.cc Exploit_31035209.exe | GET | 200 | 216.58.212.163:80 | http://o.pki.goog/s/wr3/fgA/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQSq0i5t2Pafi2Gw9uzwnc7KTctWgQUx4H1%2FY6I2QA8TWOiUDEkoM4j%2FiMCEH4AzC8CtsuHCuCmoKpV7Vk%3D | unknown | — | — | whitelisted |
6512 | bytebreaker.cc Exploit_31035209.exe | GET | 200 | 142.250.186.163:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | whitelisted |
5712 | firefox.exe | POST | 200 | 216.58.212.163:80 | http://o.pki.goog/s/wr3/jLM | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.190:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1488 | svchost.exe | 23.48.23.190:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1488 | svchost.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 92.123.104.29:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.54.109.203:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 40.126.31.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 23.54.109.203:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.dlsft.com |
| unknown |
ocsp.pki.goog |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
Process | Message |
|---|---|
bytebreaker.cc Exploit_31035209.exe | |
bytebreaker.cc Exploit_31035209.exe | at getFileInfo.@307@46 (this://app/main.html(329))
|
bytebreaker.cc Exploit_31035209.exe | Error: (undefined) has no property - value
|
bytebreaker.cc Exploit_31035209.exe | |
bytebreaker.cc Exploit_31035209.exe | at initializeDynamicVariables (this://app/main.html(351))
|
bytebreaker.cc Exploit_31035209.exe | scanning node question /questions/question
|
bytebreaker.cc Exploit_31035209.exe | scanning node question /questions/question
|
bytebreaker.cc Exploit_31035209.exe | scanning node questions /questions
|
bytebreaker.cc Exploit_31035209.exe | scanning node question /questions/question
|
bytebreaker.cc Exploit_31035209.exe | scanning node question /questions/question
|