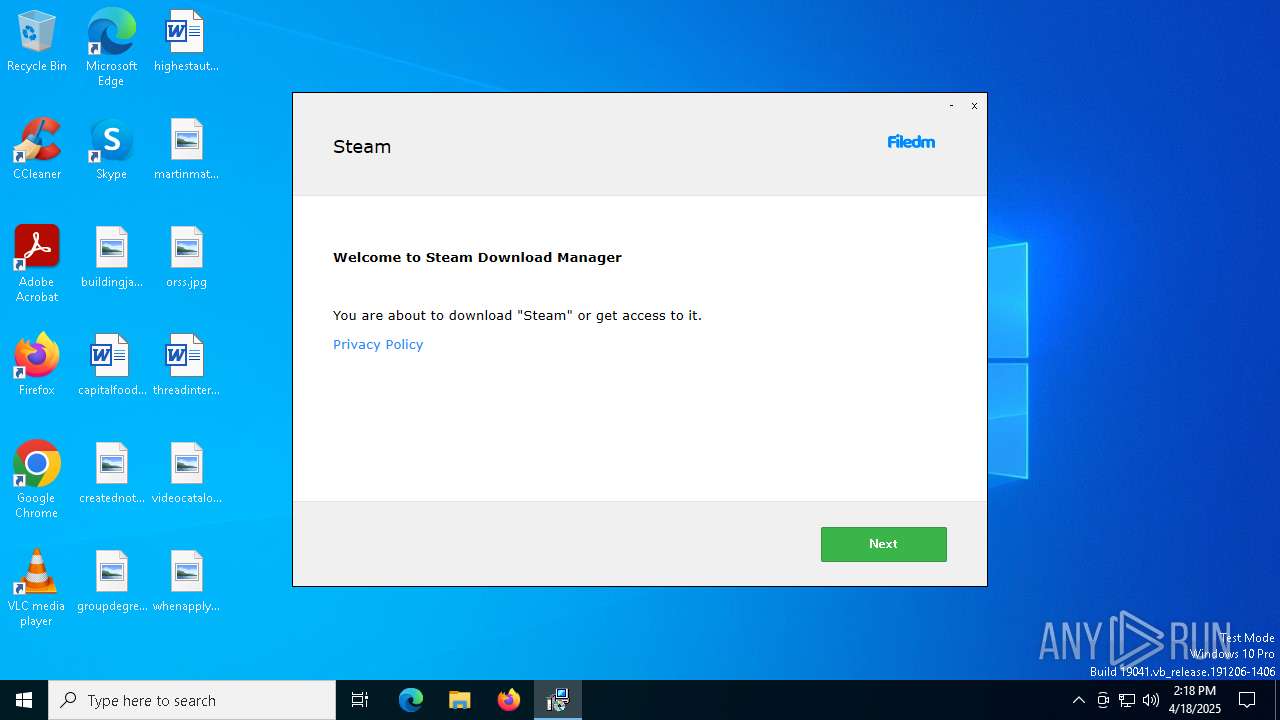
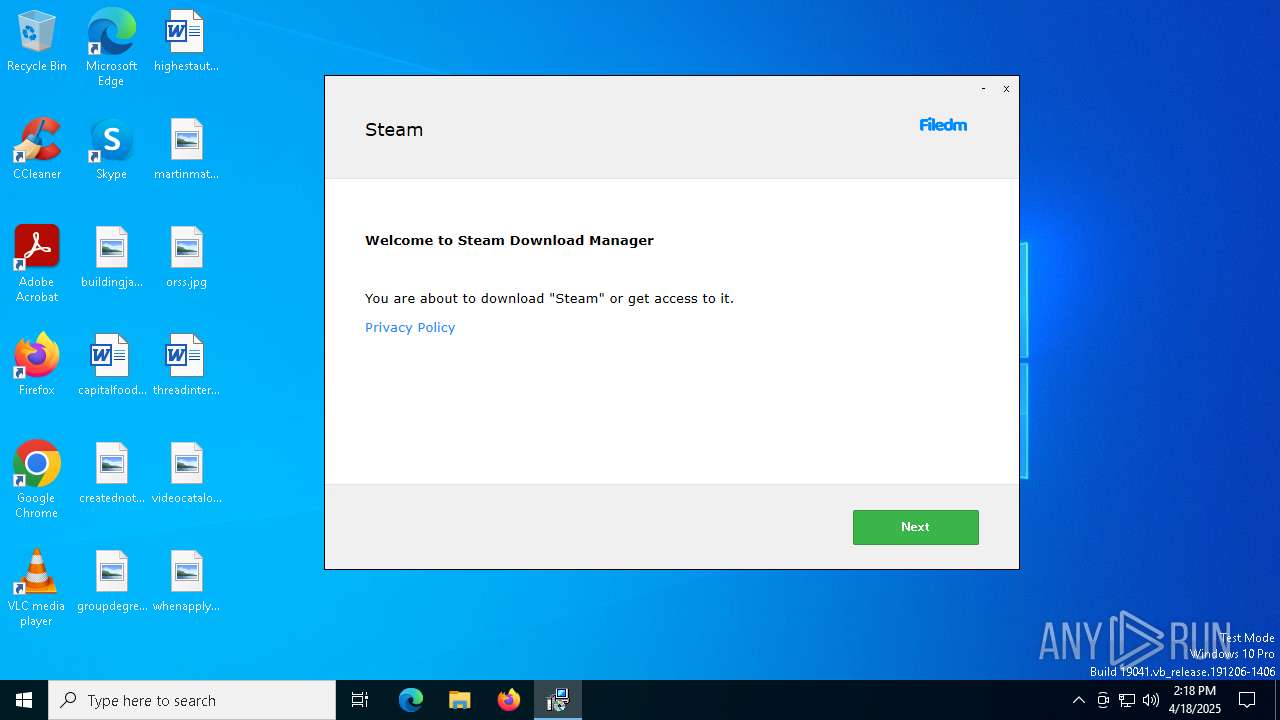
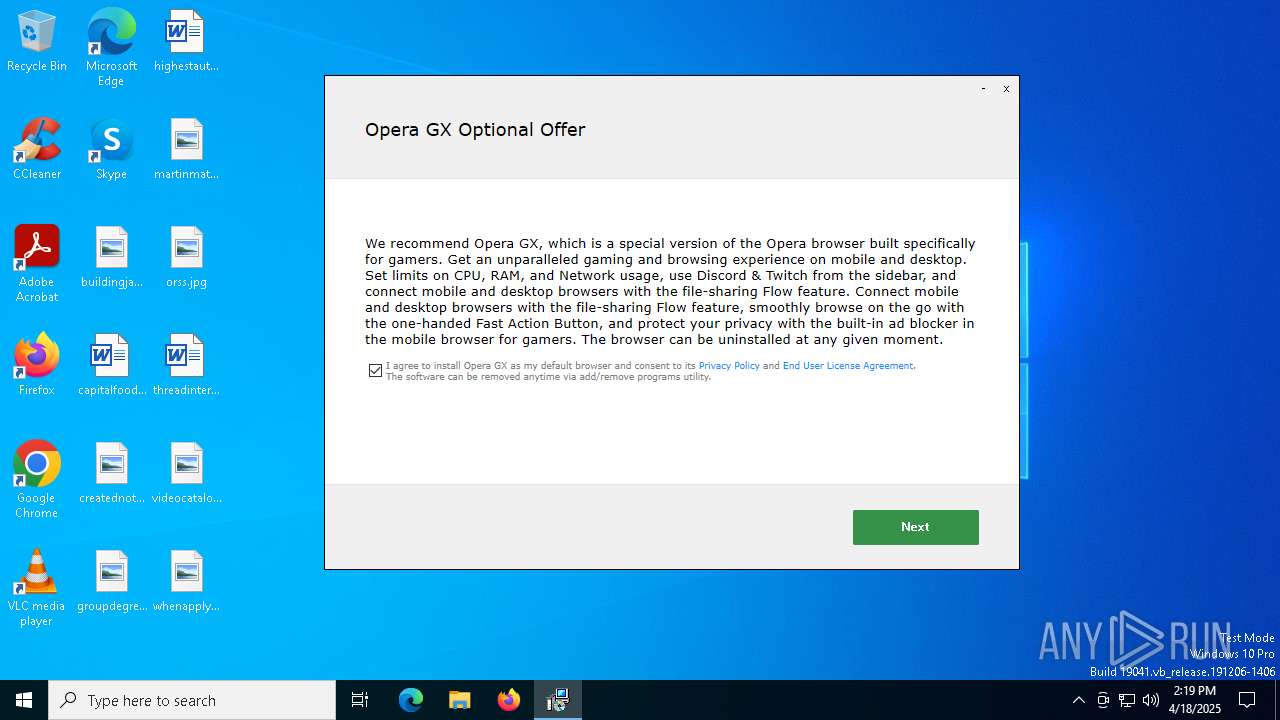
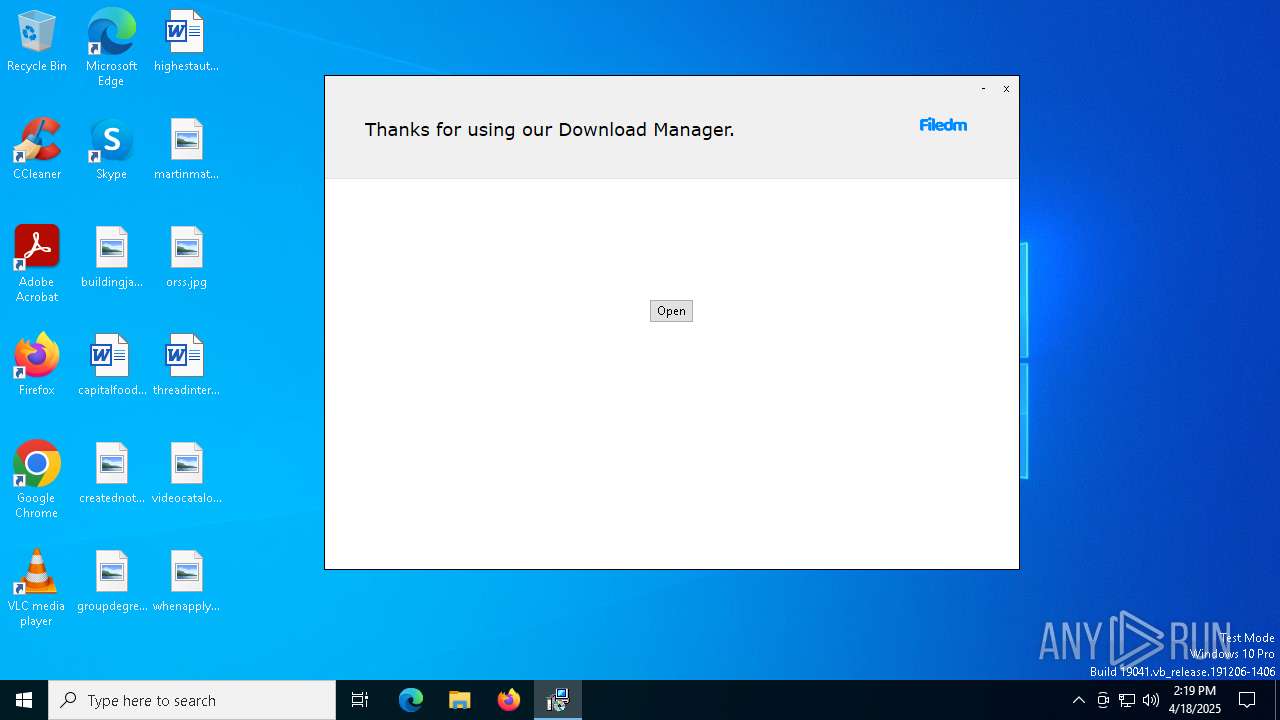
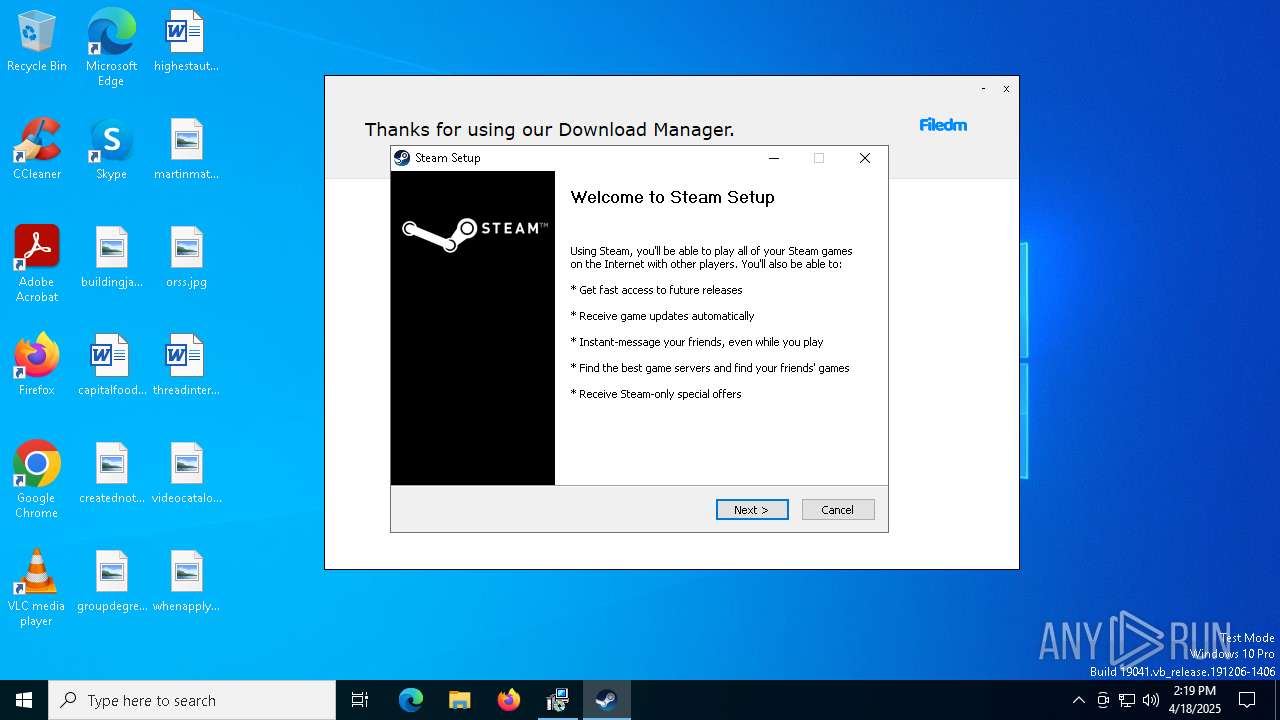
| File name: | oxygen.exe |
| Full analysis: | https://app.any.run/tasks/75fad195-931f-40a4-9ffa-92170131e81e |
| Verdict: | Malicious activity |
| Analysis date: | April 18, 2025, 14:18:38 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 15D1C495FF66BF7CEA8A6D14BFDF0A20 |
| SHA1: | 942814521FA406A225522F208AC67F90DBDE0AE7 |
| SHA256: | 61C2C4A5D7C14F77EE88871DED4CC7F1E49DAE3E4EF209504C66FEDF4D22DE42 |
| SSDEEP: | 98304:DtjM+LgnHM8mNLNpOmMGl2p9tjIQh+1GHp8PGmDFzMVv3kdcpR41TBN14BC6SkPT:Kw8 |
MALICIOUS
GENERIC has been found (auto)
- oxygen.exe (PID: 7224)
SUSPICIOUS
Reads security settings of Internet Explorer
- oxygen.exe (PID: 7224)
There is functionality for taking screenshot (YARA)
- oxygen.exe (PID: 7224)
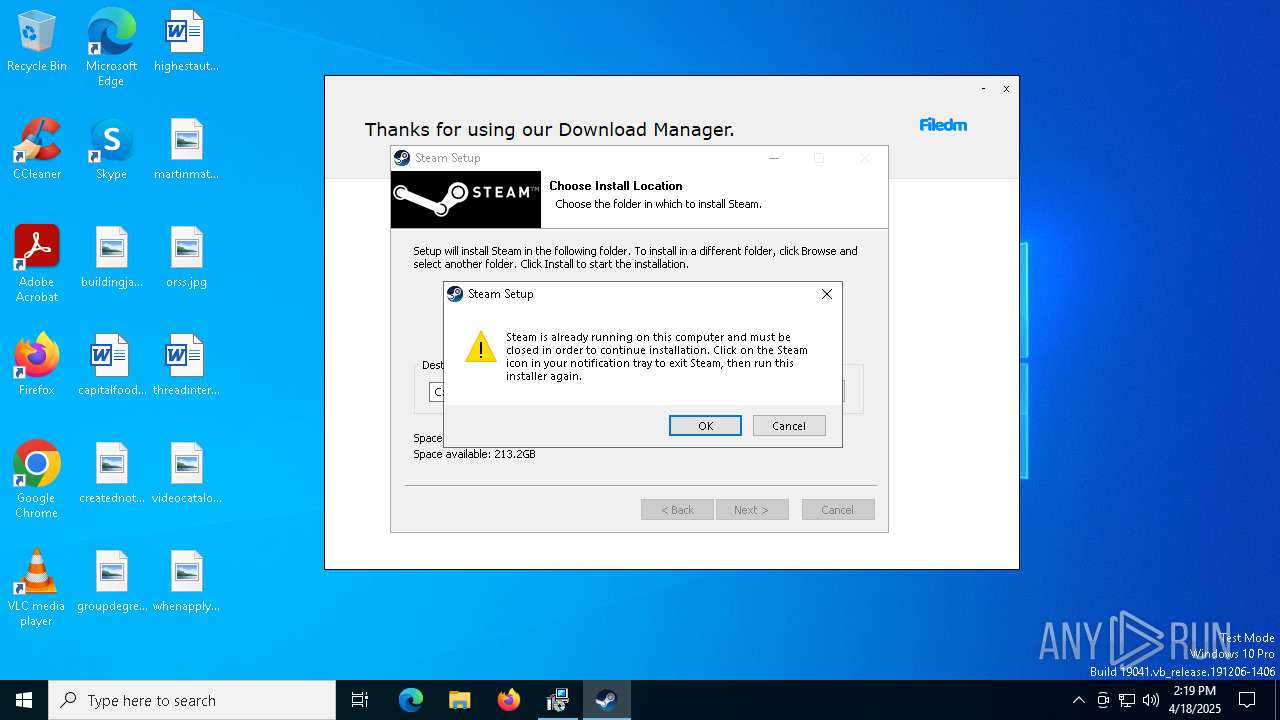
Executable content was dropped or overwritten
- oxygen.exe (PID: 7224)
- Steam.exe (PID: 7964)
- Steam.exe (PID: 7988)
The process creates files with name similar to system file names
- Steam.exe (PID: 7964)
- Steam.exe (PID: 7988)
Malware-specific behavior (creating "System.dll" in Temp)
- Steam.exe (PID: 7964)
- Steam.exe (PID: 7988)
INFO
The sample compiled with english language support
- oxygen.exe (PID: 7224)
- Steam.exe (PID: 7964)
Reads the software policy settings
- oxygen.exe (PID: 7224)
Reads the computer name
- oxygen.exe (PID: 7224)
- Steam.exe (PID: 7964)
Checks supported languages
- oxygen.exe (PID: 7224)
- Steam.exe (PID: 7964)
- Steam.exe (PID: 7988)
Reads the machine GUID from the registry
- oxygen.exe (PID: 7224)
Checks proxy server information
- oxygen.exe (PID: 7224)
Creates files or folders in the user directory
- oxygen.exe (PID: 7224)
Create files in a temporary directory
- oxygen.exe (PID: 7224)
- Steam.exe (PID: 7964)
- Steam.exe (PID: 7988)
The sample compiled with bulgarian language support
- oxygen.exe (PID: 7224)
Process checks computer location settings
- oxygen.exe (PID: 7224)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:10:18 17:00:18+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.22 |
| CodeSize: | 4353024 |
| InitializedDataSize: | 1675776 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x398c98 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Unknown (0) |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| FileDescription: | Download Manager |
| FileVersion: | 1 |
| InternalName: | Download Manager |
| LegalCopyright: | Download Manager |
| OriginalFileName: | Download Manager |
| ProductName: | Download Manager |
| ProductVersion: | 1 |
Total processes
138
Monitored processes
6
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6620 | "C:\Users\admin\AppData\Local\Temp\oxygen.exe" | C:\Users\admin\AppData\Local\Temp\oxygen.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Download Manager Exit code: 3221226540 Version: 1 Modules
| |||||||||||||||
| 7224 | "C:\Users\admin\AppData\Local\Temp\oxygen.exe" | C:\Users\admin\AppData\Local\Temp\oxygen.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Download Manager Exit code: 0 Version: 1 Modules
| |||||||||||||||
| 7376 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7408 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7964 | "C:\Users\admin\AppData\Local\Temp\Steam.exe" | C:\Users\admin\AppData\Local\Temp\Steam.exe | oxygen.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Steam Exit code: 0 Version: 2.10.91.91 Modules
| |||||||||||||||
| 7988 | "C:\Users\admin\AppData\Local\Temp\Steam.exe" | C:\Users\admin\AppData\Local\Temp\Steam.exe | oxygen.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Steam Exit code: 2 Version: 2.10.91.91 Modules
| |||||||||||||||
Total events
2 544
Read events
2 541
Write events
3
Delete events
0
Modification events
| (PID) Process: | (7224) oxygen.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7224) oxygen.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7224) oxygen.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
7
Suspicious files
20
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7224 | oxygen.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:997251DE84B6694BB272B782CD27C8B8 | SHA256:6DC5CCA3FEA0F30782EE2924E6907EF1909EE835AB9FE51700E59F2ABAED7E40 | |||
| 7224 | oxygen.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B77FAD61EB4A40E3443FA60D1451BEB4_5F55BE09F9262B37AA5427711092D3D4 | binary | |
MD5:38E1626041FF65D8324A496792431667 | SHA256:B94FAEB9E26AD4B0800C5F2AAF55EB2573B377A84630AD38D242F32D96354D77 | |||
| 7224 | oxygen.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:87A906CABD2C2ADC64BA543488D5CFCC | SHA256:C6FD2F8F57BBD5B23CC6F81AA91FCCAE545FC24EFF870849397A45E345C63F0C | |||
| 7224 | oxygen.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\05DDC6AA91765AACACDB0A5F96DF8199 | binary | |
MD5:4BC124BB9297021785DDF986E0145317 | SHA256:5ACD4B28D434627940E59196DD3728DFF74D1FA053B9E8A5E4692821A2DCCEE8 | |||
| 7224 | oxygen.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B77FAD61EB4A40E3443FA60D1451BEB4_5F55BE09F9262B37AA5427711092D3D4 | binary | |
MD5:5B8698D0B41470295B36135C882F8FF1 | SHA256:51D96AFB0B893A8FB165C14B190B15570261070CC8DB7C9633EFD129E05FA722 | |||
| 7224 | oxygen.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\DD2A7AB6E9F505401E82E727A63C7450_B73C7F9C4217B96C2B9DB7FC54C11C60 | binary | |
MD5:DEC3832F5036DF2E8342952D252A0B73 | SHA256:5C74CC276BA30DAFE6DAB3735A5F87D30E49B69B5D3E801A06FE2CCFC30DCADB | |||
| 7224 | oxygen.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\geo[1].htm | text | |
MD5:B6712DF220BB6E54644B6A6F0E513F3D | SHA256:2F9F55FB94AB806FA2EC499BECBF7B1D948BC4275686A7D004F593CA834B9078 | |||
| 7224 | oxygen.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\service[1].htm | text | |
MD5:CB5E100E5A9A3E7F6D1FD97512215282 | SHA256:CA00FCCFB408989EDDC401062C4D1219A6ACEB6B9B55412357F1790862E8F178 | |||
| 7224 | oxygen.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\83D863F495E7D991917B3ABB3E1EB382_4D9C2C5E642FAF6FA3B8098AB3241EF2 | binary | |
MD5:6358227982E385B95D461FFCC542F6EB | SHA256:FB12DE901C981CADF927EEC50269FDCA52261F5F9125ECE4D826A8D5029BEC0F | |||
| 7224 | oxygen.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\DD2A7AB6E9F505401E82E727A63C7450_B73C7F9C4217B96C2B9DB7FC54C11C60 | binary | |
MD5:205FF20A41C775E09515B1F3684D034F | SHA256:EDA699FA1939AD8576D7F991BBB5CC1D45C0C400CAB2E442880910E5CB294DDA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
31
DNS requests
24
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.31:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7224 | oxygen.exe | GET | 200 | 142.250.185.99:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | whitelisted |
7224 | oxygen.exe | GET | 200 | 216.58.206.35:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | whitelisted |
7224 | oxygen.exe | GET | 200 | 216.58.206.35:80 | http://o.pki.goog/s/wr3/mV0/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBQSq0i5t2Pafi2Gw9uzwnc7KTctWgQUx4H1%2FY6I2QA8TWOiUDEkoM4j%2FiMCEQCZXRxDEgK4oBBPRElcaU8c | unknown | — | — | whitelisted |
7224 | oxygen.exe | GET | 200 | 216.58.206.35:80 | http://o.pki.goog/s/wr3/Vdw/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQSq0i5t2Pafi2Gw9uzwnc7KTctWgQUx4H1%2FY6I2QA8TWOiUDEkoM4j%2FiMCEFXcf42tINpLCbnQS8S2feE%3D | unknown | — | — | whitelisted |
7224 | oxygen.exe | GET | 200 | 142.250.185.99:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
7224 | oxygen.exe | GET | 200 | 142.250.185.99:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7224 | oxygen.exe | GET | 200 | 18.245.38.41:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEkzUBtJnwJkc3SmanzgxeYU%3D | unknown | — | — | whitelisted |
7224 | oxygen.exe | GET | 200 | 18.245.65.219:80 | http://ocsp.r2m03.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQqHI%2BsdmapawQncL1rpCEZZ8gTSAQUVdkYX9IczAHhWLS%2Bq9lVQgHXLgICEAsG7SjIJKGIOV3vwg87c8M%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5176 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.31:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7224 | oxygen.exe | 35.190.60.70:443 | www.dlsft.com | GOOGLE | US | whitelisted |
7224 | oxygen.exe | 216.58.206.35:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
7224 | oxygen.exe | 142.250.185.99:80 | c.pki.goog | GOOGLE | US | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.dlsft.com |
| unknown |
ocsp.pki.goog |
| whitelisted |
c.pki.goog |
| whitelisted |
o.pki.goog |
| whitelisted |
client.wns.windows.com |
| whitelisted |
dlsft.com |
| unknown |
filedm.com |
| malicious |