| download: | /bin/mimikatz.exe |
| Full analysis: | https://app.any.run/tasks/887a03a0-8026-4b67-8d30-110a7d886d8c |
| Verdict: | Malicious activity |
| Analysis date: | July 24, 2024, 09:57:40 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (console) x86-64, for MS Windows |
| MD5: | 29EFD64DD3C7FE1E2B022B7AD73A1BA5 |
| SHA1: | E3B6EA8C46FA831CEC6F235A5CF48B38A4AE8D69 |
| SHA256: | 61C0810A23580CF492A6BA4F7654566108331E7A4134C968C2D6A05261B2D8A1 |
| SSDEEP: | 24576:0CgjBAeu8iuUHGzkuBhzy2F+yVICFPC27rIlve3NuacODvsGA:0CI7XBE2IuF64rIlmdiis |
MALICIOUS
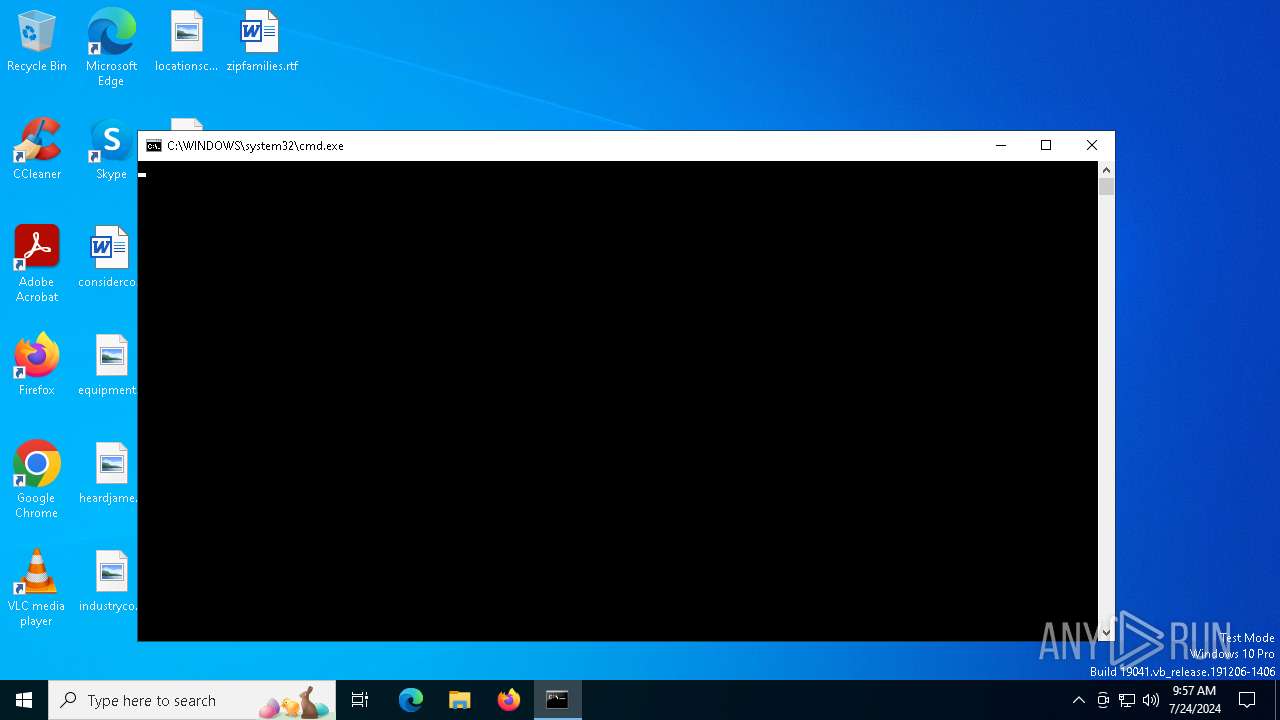
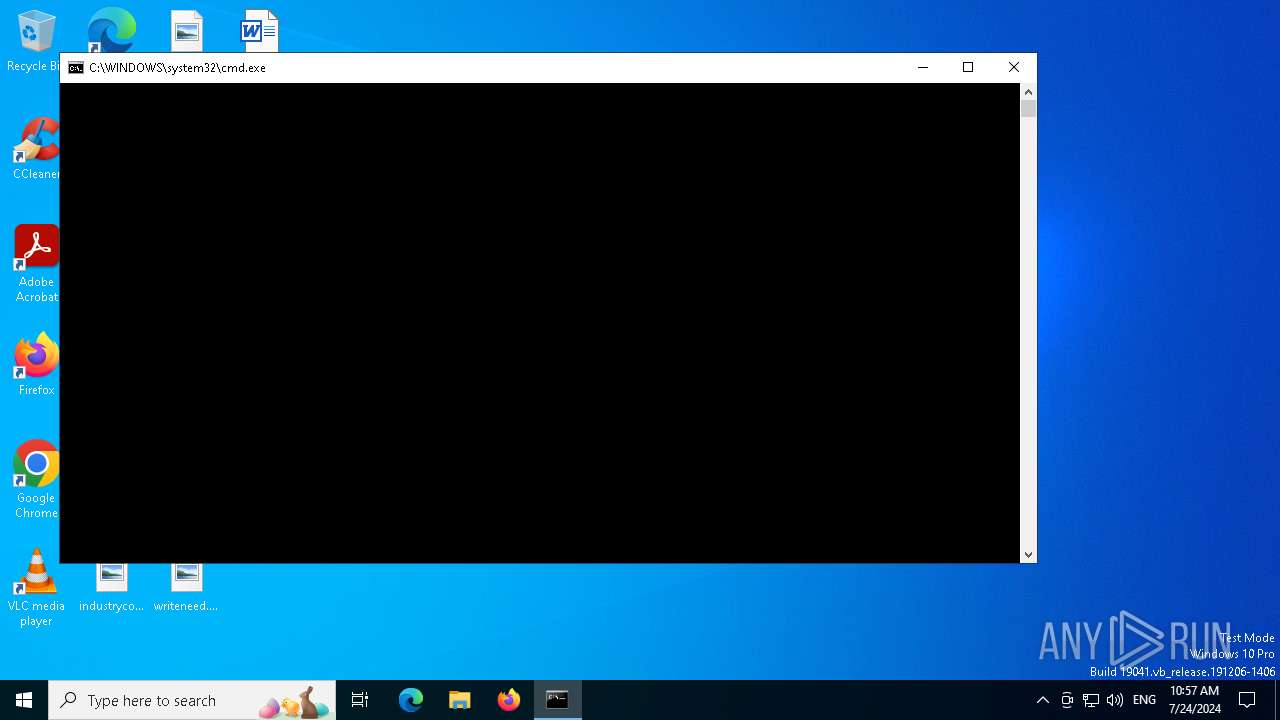
Drops the executable file immediately after the start
- mimikatz.exe (PID: 920)
MIMIKATZ has been detected (YARA)
- mimikatz.exe (PID: 920)
SUSPICIOUS
No suspicious indicators.INFO
Checks supported languages
- mimikatz.exe (PID: 920)
Reads the computer name
- mimikatz.exe (PID: 920)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2022:09:19 15:44:39+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 9 |
| CodeSize: | 849920 |
| InitializedDataSize: | 508416 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xc98e8 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 2.2.0.0 |
| ProductVersionNumber: | 2.2.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Pre-release, Private build, Special build |
| FileOS: | Windows NT |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| ProductName: | mimikatz |
| ProductVersion: | 2.2.0.0 |
| CompanyName: | gentilkiwi (Benjamin DELPY) |
| FileDescription: | mimikatz for Windows |
| FileVersion: | 2.2.0.0 |
| InternalName: | mimikatz |
| LegalCopyright: | Copyright (c) 2007 - 2021 gentilkiwi (Benjamin DELPY) |
| OriginalFileName: | mimikatz.exe |
| PrivateBuild: | Build with love for POC only |
| SpecialBuild: | :) |
Total processes
131
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 612 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | mimikatz.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 920 | "C:\Users\admin\Desktop\mimikatz.exe" | C:\Users\admin\Desktop\mimikatz.exe | explorer.exe | ||||||||||||
User: admin Company: gentilkiwi (Benjamin DELPY) Integrity Level: MEDIUM Description: mimikatz for Windows Version: 2.2.0.0 Modules
| |||||||||||||||
| 2152 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | UCPDMgr.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 5304 | "C:\WINDOWS\system32\UCPDMgr.exe" | C:\Windows\System32\UCPDMgr.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: User Choice Protection Manager Exit code: 0 Version: 1.0.0.414301 | |||||||||||||||
Total events
180
Read events
180
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
31
DNS requests
17
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 304 | 20.12.23.50:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 200 | 13.85.23.86:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 304 | 13.85.23.86:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 200 | 13.85.23.206:443 | https://fe3cr.delivery.mp.microsoft.com/clientwebservice/ping | unknown | — | — | unknown |
— | — | GET | 200 | 13.85.23.86:443 | https://slscr.update.microsoft.com/sls/ping | unknown | — | — | unknown |
— | — | GET | 304 | 13.85.23.86:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 304 | 13.85.23.86:443 | https://slscr.update.microsoft.com/SLS/%7BE7A50285-D08D-499D-9FF8-180FDC2332BC%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 304 | 52.165.165.26:443 | https://slscr.update.microsoft.com/SLS/%7BE7A50285-D08D-499D-9FF8-180FDC2332BC%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 304 | 40.68.123.157:443 | https://slscr.update.microsoft.com/SLS/%7BE7A50285-D08D-499D-9FF8-180FDC2332BC%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.209.33.156:443 | licensing.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4012 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1324 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
— | — | 20.42.65.84:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 20.12.23.50:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
licensing.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Generic Protocol Command Decode | SURICATA HTTP Request unrecognized authorization method |