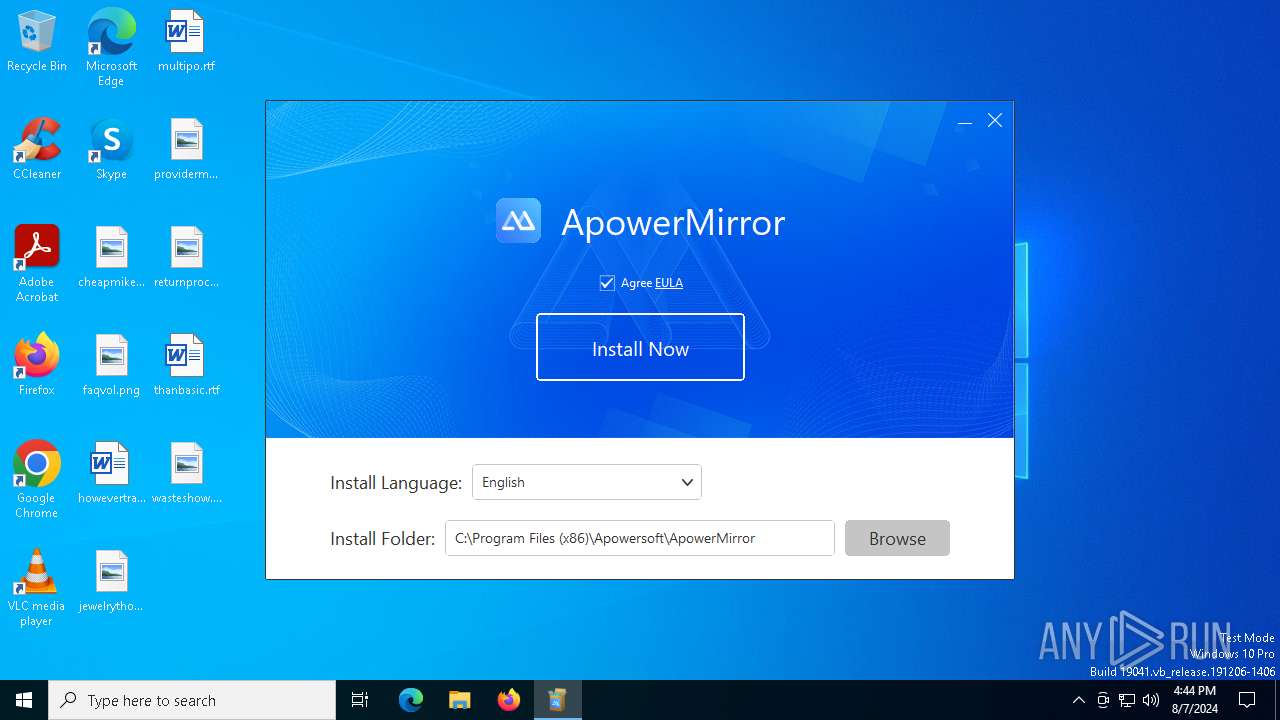
| File name: | power.exe |
| Full analysis: | https://app.any.run/tasks/428d6f3f-d805-450c-aa23-edfe76b85857 |
| Verdict: | Malicious activity |
| Analysis date: | August 07, 2024, 16:44:12 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 53E8D1C8B51A16C183CF3C448D9669D4 |
| SHA1: | 2A83265CD724F1C9A60F4391136F97FA9D25502D |
| SHA256: | 61BBD85A0DCA5A80D214BD0B57E81C22107594B680C899D039CB8F075C65416A |
| SSDEEP: | 98304:mB0I5/udvsufk3LJzhLd3rZKL43YQK+blKYn: |
MALICIOUS
Drops the executable file immediately after the start
- installer.exe (PID: 6260)
- power.exe (PID: 6836)
- installer.tmp (PID: 3276)
- msiexec.exe (PID: 6644)
SUSPICIOUS
Reads security settings of Internet Explorer
- power.exe (PID: 6836)
- ApowerMirror.exe (PID: 6796)
Reads the date of Windows installation
- power.exe (PID: 6836)
Executable content was dropped or overwritten
- installer.tmp (PID: 3276)
- installer.exe (PID: 6260)
Starts CMD.EXE for commands execution
- installer.tmp (PID: 3276)
- cmd.exe (PID: 4824)
- cmd.exe (PID: 6600)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 7100)
- installer.tmp (PID: 3276)
Executing commands from a ".bat" file
- installer.tmp (PID: 3276)
Reads the Windows owner or organization settings
- installer.tmp (PID: 3276)
- msiexec.exe (PID: 6644)
Get information on the list of running processes
- cmd.exe (PID: 4824)
- cmd.exe (PID: 6684)
- cmd.exe (PID: 420)
- cmd.exe (PID: 6600)
Application launched itself
- cmd.exe (PID: 6600)
- cmd.exe (PID: 4824)
Searches for installed software
- installer.tmp (PID: 3276)
Drops 7-zip archiver for unpacking
- installer.tmp (PID: 3276)
Process drops legitimate windows executable
- installer.tmp (PID: 3276)
- msiexec.exe (PID: 6644)
The process drops C-runtime libraries
- installer.tmp (PID: 3276)
Checks Windows Trust Settings
- msiexec.exe (PID: 6644)
Checks for Java to be installed
- msiexec.exe (PID: 6908)
Executes as Windows Service
- mDNSResponder.exe (PID: 6344)
Changes Internet Explorer settings (feature browser emulation)
- installer.tmp (PID: 3276)
Uses NETSH.EXE to add a firewall rule or allowed programs
- installer.tmp (PID: 3276)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- installer.tmp (PID: 3276)
Reads Microsoft Outlook installation path
- ApowerMirror.exe (PID: 6796)
Reads Internet Explorer settings
- ApowerMirror.exe (PID: 6796)
There is functionality for taking screenshot (YARA)
- ApowerMirror.exe (PID: 6796)
Creates/Modifies COM task schedule object
- msiexec.exe (PID: 6644)
INFO
Create files in a temporary directory
- power.exe (PID: 6836)
- installer.exe (PID: 6260)
- installer.tmp (PID: 3276)
Creates files in the program directory
- power.exe (PID: 6836)
- installer.tmp (PID: 3276)
- ApowerMirror.exe (PID: 6796)
Checks supported languages
- installer.exe (PID: 6260)
- installer.tmp (PID: 3276)
- power.exe (PID: 6836)
- msiexec.exe (PID: 6644)
- msiexec.exe (PID: 6908)
- msiexec.exe (PID: 6560)
- mDNSResponder.exe (PID: 6344)
- ApowerMirror.exe (PID: 6796)
- identity_helper.exe (PID: 4296)
- adb.exe (PID: 3972)
- msiexec.exe (PID: 2088)
Reads the computer name
- installer.tmp (PID: 3276)
- power.exe (PID: 6836)
- msiexec.exe (PID: 6644)
- msiexec.exe (PID: 6908)
- msiexec.exe (PID: 6560)
- mDNSResponder.exe (PID: 6344)
- ApowerMirror.exe (PID: 6796)
- identity_helper.exe (PID: 4296)
- msiexec.exe (PID: 2088)
Checks proxy server information
- power.exe (PID: 6836)
- msiexec.exe (PID: 6908)
- ApowerMirror.exe (PID: 6796)
Process checks computer location settings
- power.exe (PID: 6836)
- ApowerMirror.exe (PID: 6796)
Creates files or folders in the user directory
- installer.tmp (PID: 3276)
- msiexec.exe (PID: 6644)
- ApowerMirror.exe (PID: 6796)
Reads the software policy settings
- msiexec.exe (PID: 6644)
- ApowerMirror.exe (PID: 6796)
Application launched itself
- msiexec.exe (PID: 6644)
- msedge.exe (PID: 904)
- msedge.exe (PID: 5956)
Reads the machine GUID from the registry
- msiexec.exe (PID: 6644)
- ApowerMirror.exe (PID: 6796)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6644)
Creates a software uninstall entry
- installer.tmp (PID: 3276)
- msiexec.exe (PID: 6644)
Reads Microsoft Office registry keys
- msedge.exe (PID: 904)
- power.exe (PID: 6836)
- msedge.exe (PID: 5956)
Manual execution by a user
- msedge.exe (PID: 5956)
- ApowerMirror.exe (PID: 6796)
Reads Environment values
- ApowerMirror.exe (PID: 6796)
- identity_helper.exe (PID: 4296)
Process checks Internet Explorer phishing filters
- ApowerMirror.exe (PID: 6796)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (18) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (2.9) |
| .exe | | | Generic Win/DOS Executable (1.3) |
| .exe | | | DOS Executable Generic (1.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:11:28 08:54:50+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.29 |
| CodeSize: | 1233920 |
| InitializedDataSize: | 773632 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xeb545 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.1.1.6 |
| ProductVersionNumber: | 1.1.1.6 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| CompanyName: | Apowersoft |
| FileDescription: | Apowersoft Installer |
| FileVersion: | 1.1.1.6 |
| InternalName: | Apowersoft Installer.exe |
| LegalCopyright: | Copyright (C) 2023 WANGXU TECHNOLOGY CO. Ltd. |
| OriginalFileName: | Apowersoft Installer.exe |
| ProductName: | Apowersoft Installer |
| ProductVersion: | 1.1.1.6 |
Total processes
211
Monitored processes
76
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_xpay_wallet.mojom.EdgeXPayWalletService --lang=en-US --service-sandbox-type=utility --no-appcompat-clear --mojo-platform-channel-handle=3816 --field-trial-handle=2300,i,15118011706718618280,15574840203955234252,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 320 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=6112 --field-trial-handle=2300,i,15118011706718618280,15574840203955234252,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 420 | C:\WINDOWS\system32\cmd.exe /c tasklist | find "ApowerMirror.exe" | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 608 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2512 --field-trial-handle=2300,i,15118011706718618280,15574840203955234252,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 752 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 904 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --single-argument http://r.aoscdn.com/jumper?type=install&product_id=113&language=en&unique_id=39e30d720e18376278a9be61a436df98&apptype=saas-pro&appver=1.8.9.2&first_install_ts=1723049223&ts=1723049223&wxga=&ct=1723049060&mt=1723049060&h=53e8d1c8b51a16c183cf3c448d9669d4&hash=1d32323750f8bcff5151a0d4a18a0e8b | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | power.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 1 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1132 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6480 --field-trial-handle=2300,i,15118011706718618280,15574840203955234252,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1664 | find "ApowerMirror.exe" | C:\Windows\SysWOW64\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1748 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=3848 --field-trial-handle=2300,i,15118011706718618280,15574840203955234252,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2088 | C:\Windows\syswow64\MsiExec.exe -Embedding 8EE91B2C80CB4CE69B30C7D1A6763E90 E Global\MSI0000 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
82 678
Read events
82 163
Write events
483
Delete events
32
Modification events
| (PID) Process: | (6836) power.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6836) power.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6836) power.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6836) power.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3276) installer.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: CC0C000071B3733EE9E8DA01 | |||
| (PID) Process: | (3276) installer.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: E57DCDE2904550FB0F000E00F9A83BEC56139B011256526B98A70A35261E8C3B | |||
| (PID) Process: | (3276) installer.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (3276) installer.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Program Files (x86)\Apowersoft\ApowerMirror\7z.dll | |||
| (PID) Process: | (3276) installer.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: 5CDEBB6DD1D9C1DFABAE2590AFE53E4888AAE2725AD0CFEE8DD59E124E272CF1 | |||
| (PID) Process: | (6644) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Folders |
| Operation: | write | Name: | C:\Config.Msi\ |
Value: | |||
Executable files
239
Suspicious files
119
Text files
845
Unknown types
26
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6836 | power.exe | C:\Users\admin\AppData\Local\Temp\installer.exe | — | |
MD5:— | SHA256:— | |||
| 6836 | power.exe | C:\Users\admin\AppData\Local\Temp\installer.exe.err.log | text | |
MD5:001867DE516905464263C1E83429FD64 | SHA256:2AD4BEC2D90E36A245309D2A22308959F7D8C23FF42639451BA67D8F8CDCB4D5 | |||
| 3276 | installer.tmp | C:\Users\admin\AppData\Local\Temp\is-P0GUF.tmp\isxdl.dll | executable | |
MD5:F7B445A6CB2064D7B459451E86CA6B0E | SHA256:BD03543C37FEB48432E166FE3898ABC2A7FE854B1113EE4D5D284633B4605377 | |||
| 3276 | installer.tmp | C:\Users\admin\AppData\Local\Temp\is-P0GUF.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 3276 | installer.tmp | C:\Users\admin\AppData\Local\Temp\is-P0GUF.tmp\KillProcessWithName.bat | text | |
MD5:12320B56FAD8A52D1FC409D7977637DB | SHA256:DAA5B50A7973DD0C49F0CD5F90C2351617146CDC0408E99CF7FCB219D0703299 | |||
| 3276 | installer.tmp | C:\Program Files (x86)\Apowersoft\ApowerMirror\is-TKLIO.tmp | executable | |
MD5:08E1946ECF8670A3CEF6C2A28CF42380 | SHA256:5AE057FF19D5AC5EB36FBA26CFACFF7AE5D2D2D1A3BE4F684B94ADED15FE6477 | |||
| 3276 | installer.tmp | C:\Program Files (x86)\Apowersoft\ApowerMirror\adb.exe | executable | |
MD5:E0473372B98E481F0FC6C5395402F2B5 | SHA256:1DD18B061A5926107812D71905D957E8865B08F6E7D71D3A4D041CACC29D33E6 | |||
| 3276 | installer.tmp | C:\Program Files (x86)\Apowersoft\ApowerMirror\is-6METD.tmp | executable | |
MD5:ED5A809DC0024D83CBAB4FB9933D598D | SHA256:D60103A5E99BC9888F786EE916F5D6E45493C3247972CB053833803DE7E95CF9 | |||
| 3276 | installer.tmp | C:\Program Files (x86)\Apowersoft\ApowerMirror\AdbWinApi.dll | executable | |
MD5:ED5A809DC0024D83CBAB4FB9933D598D | SHA256:D60103A5E99BC9888F786EE916F5D6E45493C3247972CB053833803DE7E95CF9 | |||
| 6260 | installer.exe | C:\Users\admin\AppData\Local\Temp\is-44G8A.tmp\installer.tmp | executable | |
MD5:08E1946ECF8670A3CEF6C2A28CF42380 | SHA256:5AE057FF19D5AC5EB36FBA26CFACFF7AE5D2D2D1A3BE4F684B94ADED15FE6477 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
62
TCP/UDP connections
166
DNS requests
108
Threats
49
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1360 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6836 | power.exe | GET | 200 | 47.244.67.191:80 | http://wx-user-behavior.cn-hongkong.log.aliyuncs.com/logstores/webtrack/track?APIVersion=0.6.0&__topic__=win-launcher&unique_id=39e30d720e18376278a9be61a436df98&session_id=1723049064&app=ApowerMirror&appid=113&ga_error=&ga_ok=0&ga_response=%7B%22status%22%3A404%2C%22message%22%3A%22Not%20found%22%7D&gaid=&step=1 | unknown | — | — | unknown |
6836 | power.exe | GET | 200 | 47.244.67.191:80 | http://wx-user-behavior.cn-hongkong.log.aliyuncs.com/logstores/webtrack/track?APIVersion=0.6.0&__topic__=win-launcher&unique_id=39e30d720e18376278a9be61a436df98&session_id=1723049064&app=ApowerMirror&app_install_path=C%3A%5CProgram%20Files%20%28x86%29%5CApowersoft%5CApowerMirror&app_lang=English&appid=113&apptype=saas-pro&last_step_duration=3&step=2 | unknown | — | — | unknown |
1360 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6836 | power.exe | GET | 200 | 47.244.67.191:80 | http://wx-user-behavior.cn-hongkong.log.aliyuncs.com/logstores/webtrack/track?APIVersion=0.6.0&__topic__=win-launcher&unique_id=39e30d720e18376278a9be61a436df98&session_id=1723049064&app=ApowerMirror&appid=113&apptype=saas-pro&installer_version=1.1.1.6&is_old_user=-1&last_step_duration=1&os_available_memory=2699504000&os_culture=0409&os_dpi=100&os_fullname=Microsoft%20Windows%2010%20Pro&os_lang=en-US&os_resolution=1280x720&os_total_memory=4188620000&os_version=10.0.19045&step=1 | unknown | — | — | unknown |
6836 | power.exe | GET | 404 | 163.181.92.228:80 | http://cdn.aoscdn.com/img/contact-group/installer-113-qq.png?19942 | unknown | — | — | whitelisted |
6644 | msiexec.exe | GET | 200 | 152.199.19.74:80 | http://sf.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTSqZMG5M8TA9rdzkbCnNwuMAd5VgQUz5mp6nsm9EvJjo%2FX8AUm7%2BPSp50CECsg6zOAeSqwEfZiwGT9tHM%3D | unknown | — | — | whitelisted |
6440 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6836 | power.exe | GET | 302 | 47.243.121.132:80 | http://download.aoscdn.com/down.php?softid=apowermirrorinstall-saas-pro | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5588 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5336 | SearchApp.exe | 2.23.209.140:443 | www.bing.com | Akamai International B.V. | GB | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 40.126.32.138:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1360 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
wx-user-behavior.cn-hongkong.log.aliyuncs.com |
| unknown |
download.aoscdn.com |
| unknown |
fd.api.iris.microsoft.com |
| whitelisted |
th.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Misc activity | ET INFO DNS Query to Alibaba Cloud CDN Domain (aliyuncs .com) |
2256 | svchost.exe | Misc activity | ET INFO DNS Query to Alibaba Cloud CDN Domain (aliyuncs .com) |
608 | msedge.exe | Misc activity | ET INFO DNS Query to Alibaba Cloud CDN Domain (aliyuncs .com) |
608 | msedge.exe | Misc activity | ET INFO DNS Query to Alibaba Cloud CDN Domain (aliyuncs .com) |
608 | msedge.exe | Misc activity | ET INFO Observed Alibaba Cloud CDN Domain (aliyuncs .com in TLS SNI) |
6796 | ApowerMirror.exe | Generic Protocol Command Decode | SURICATA HTTP Request unrecognized authorization method |
6796 | ApowerMirror.exe | Generic Protocol Command Decode | SURICATA HTTP Request unrecognized authorization method |
6796 | ApowerMirror.exe | Generic Protocol Command Decode | SURICATA HTTP Request unrecognized authorization method |
6796 | ApowerMirror.exe | Generic Protocol Command Decode | SURICATA HTTP Request unrecognized authorization method |
6796 | ApowerMirror.exe | Generic Protocol Command Decode | SURICATA HTTP Request unrecognized authorization method |