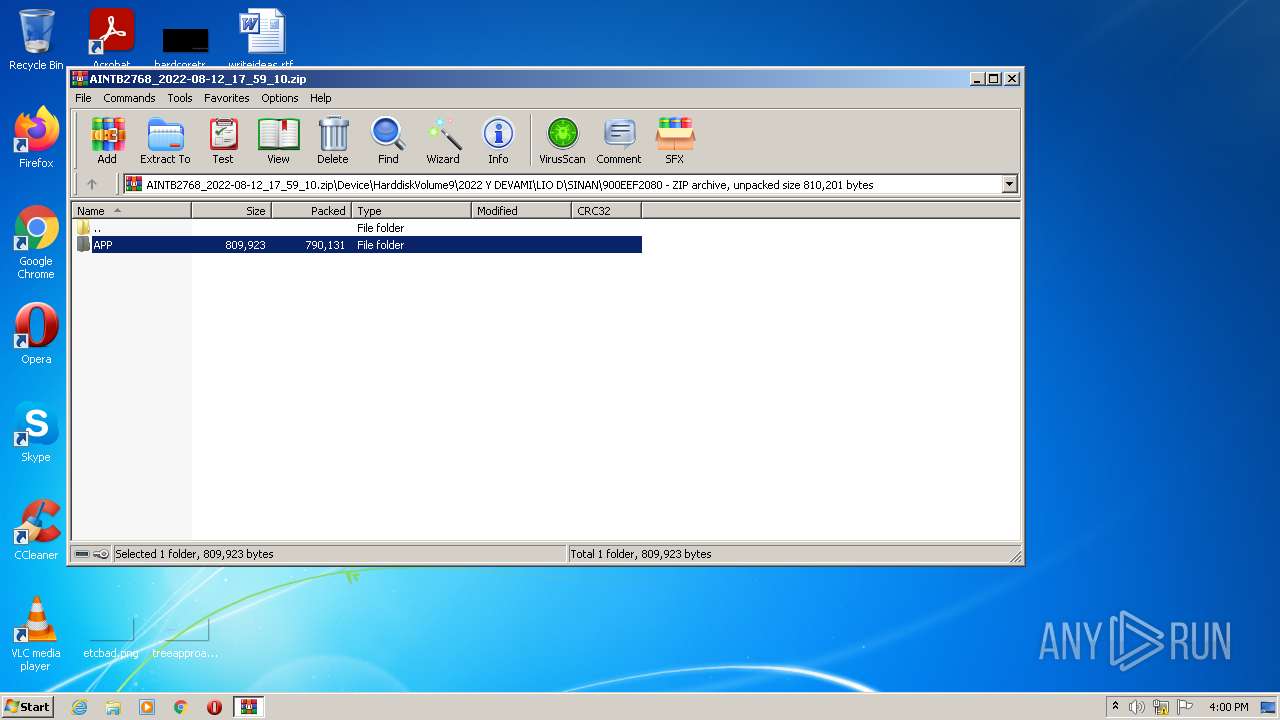
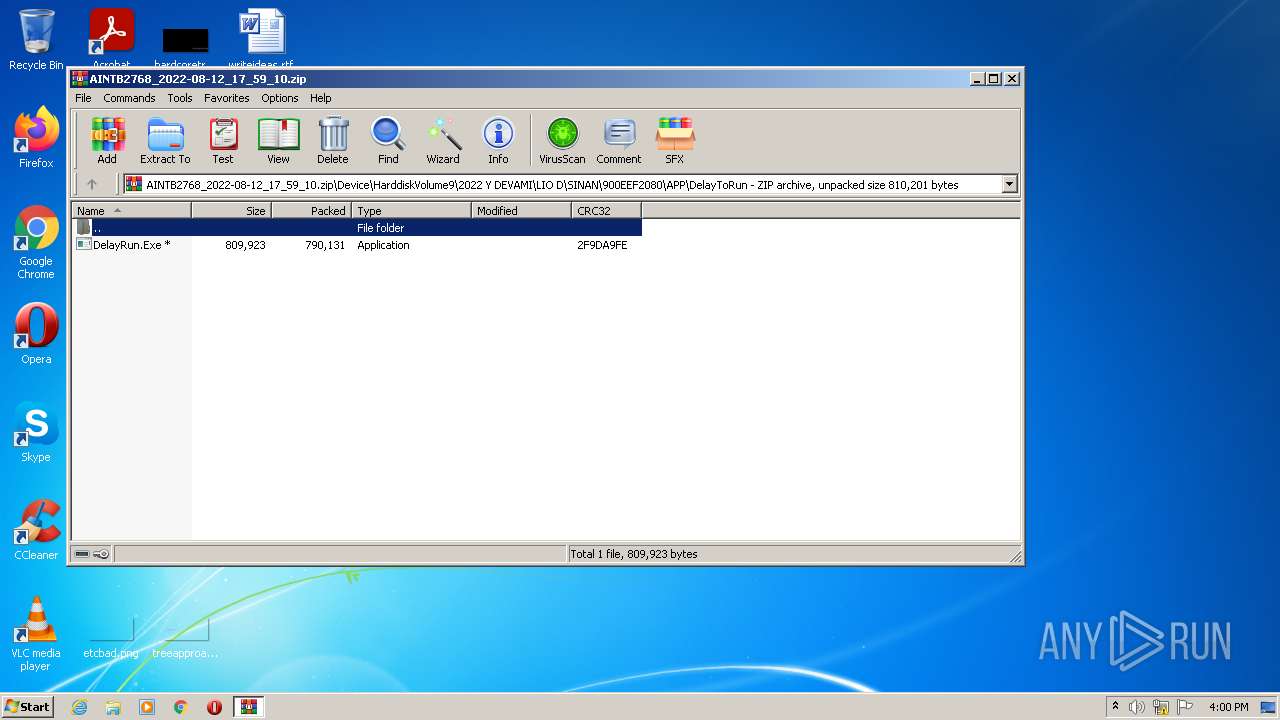
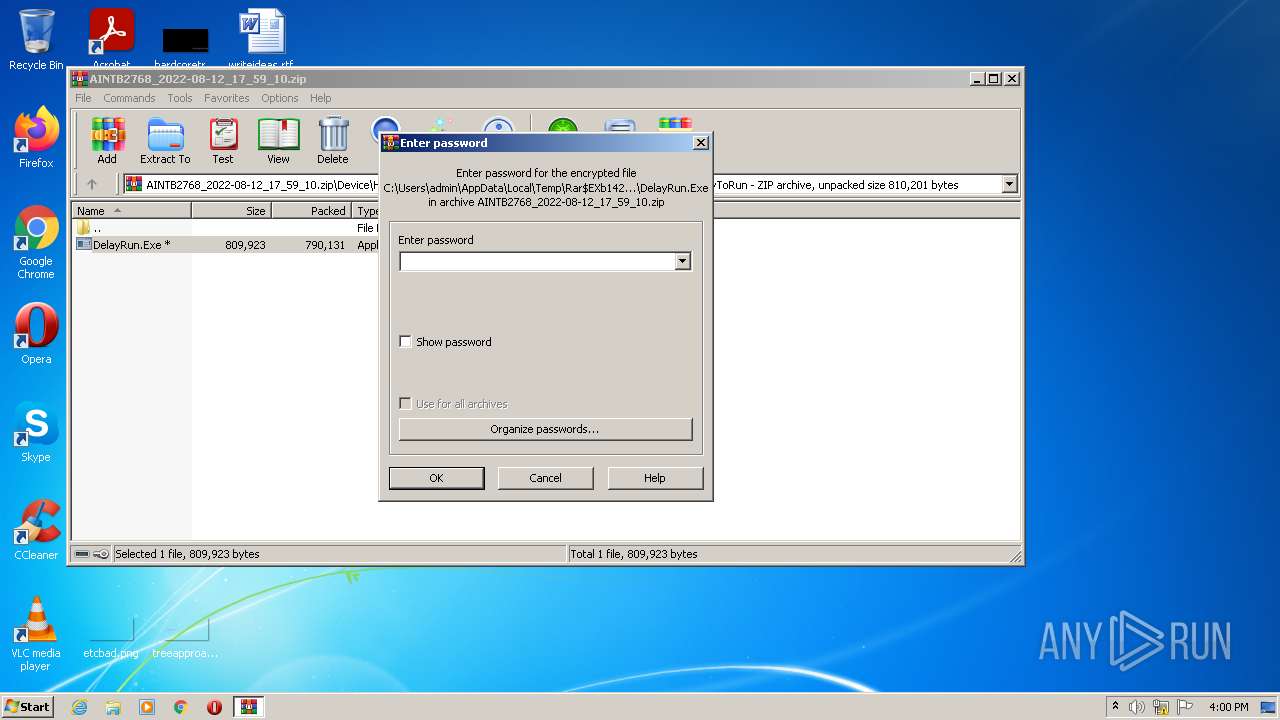
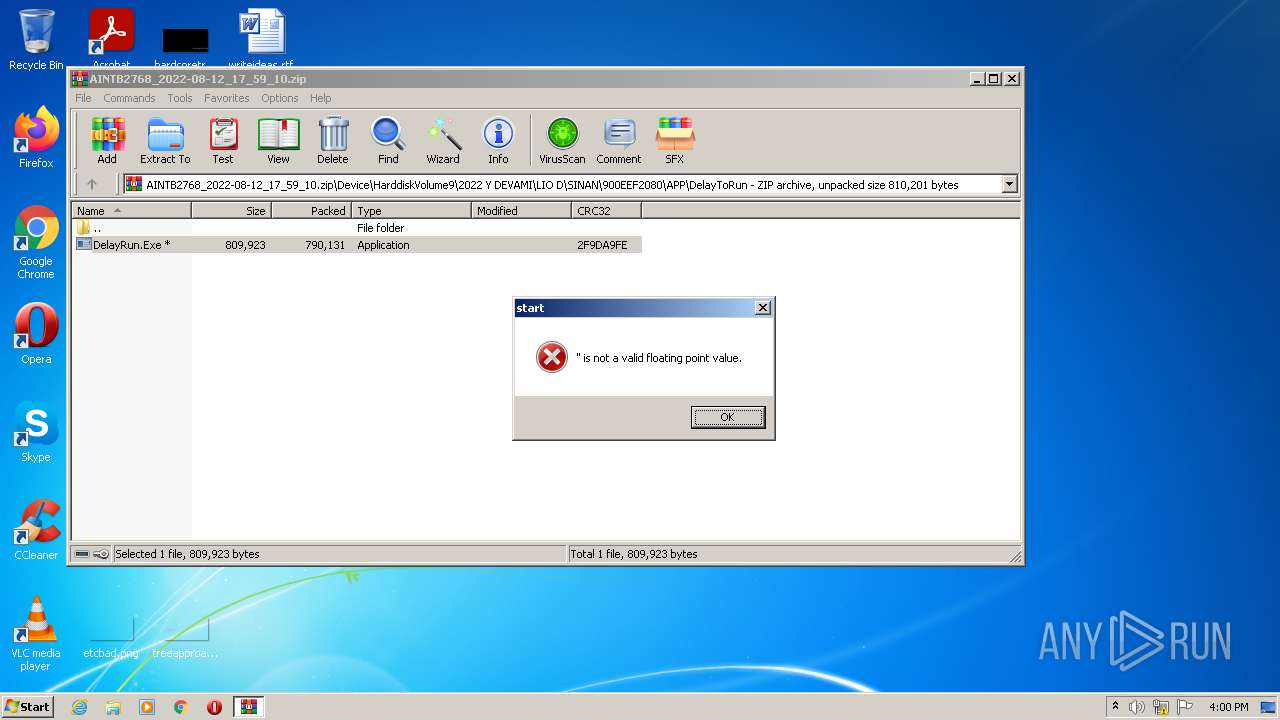
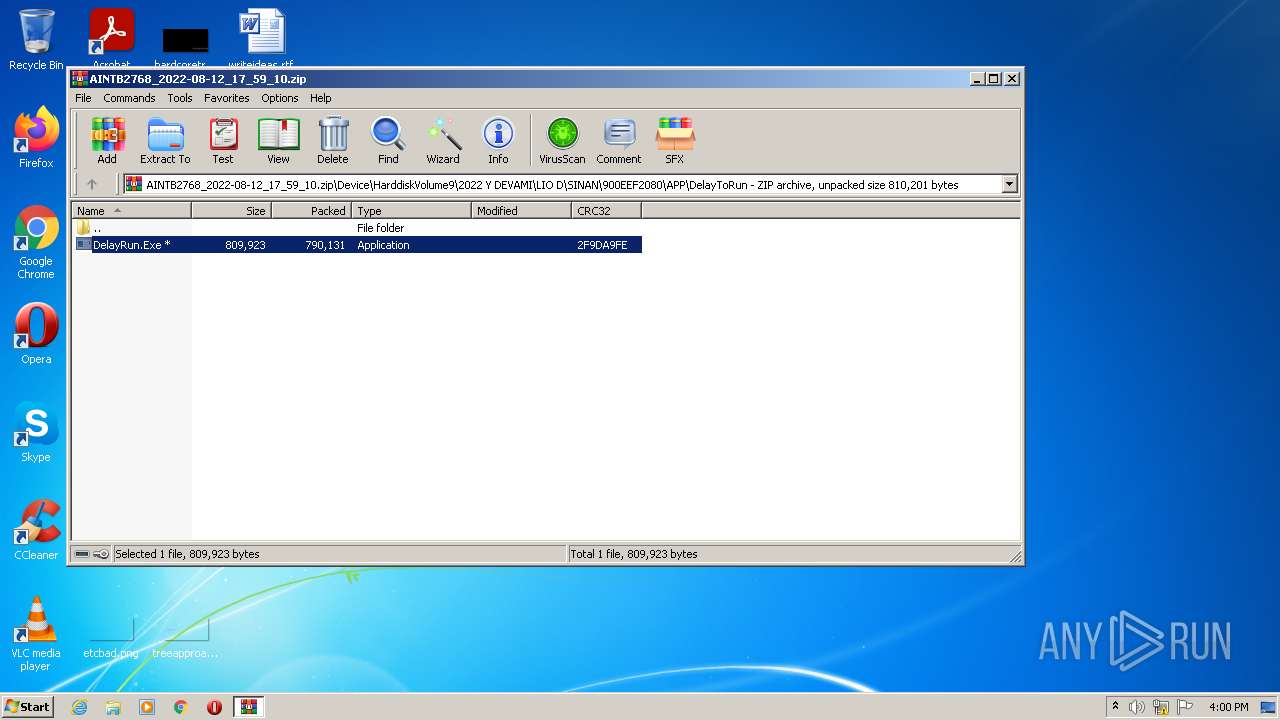
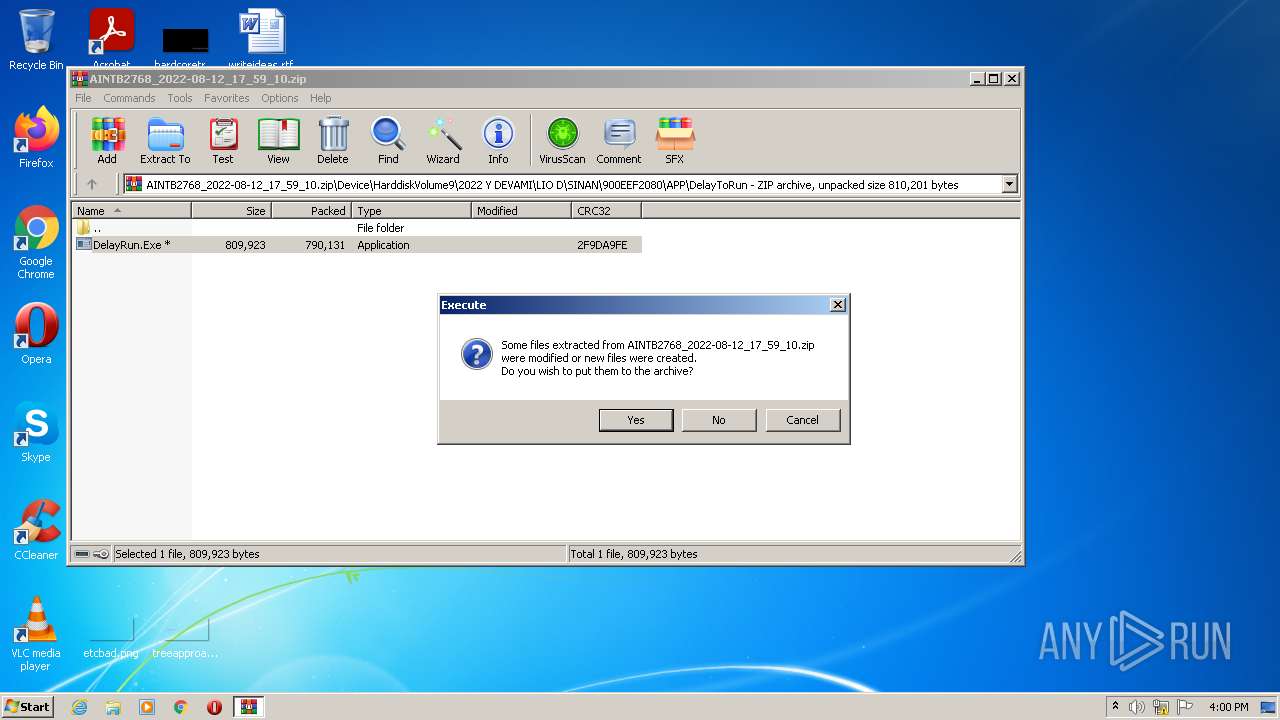
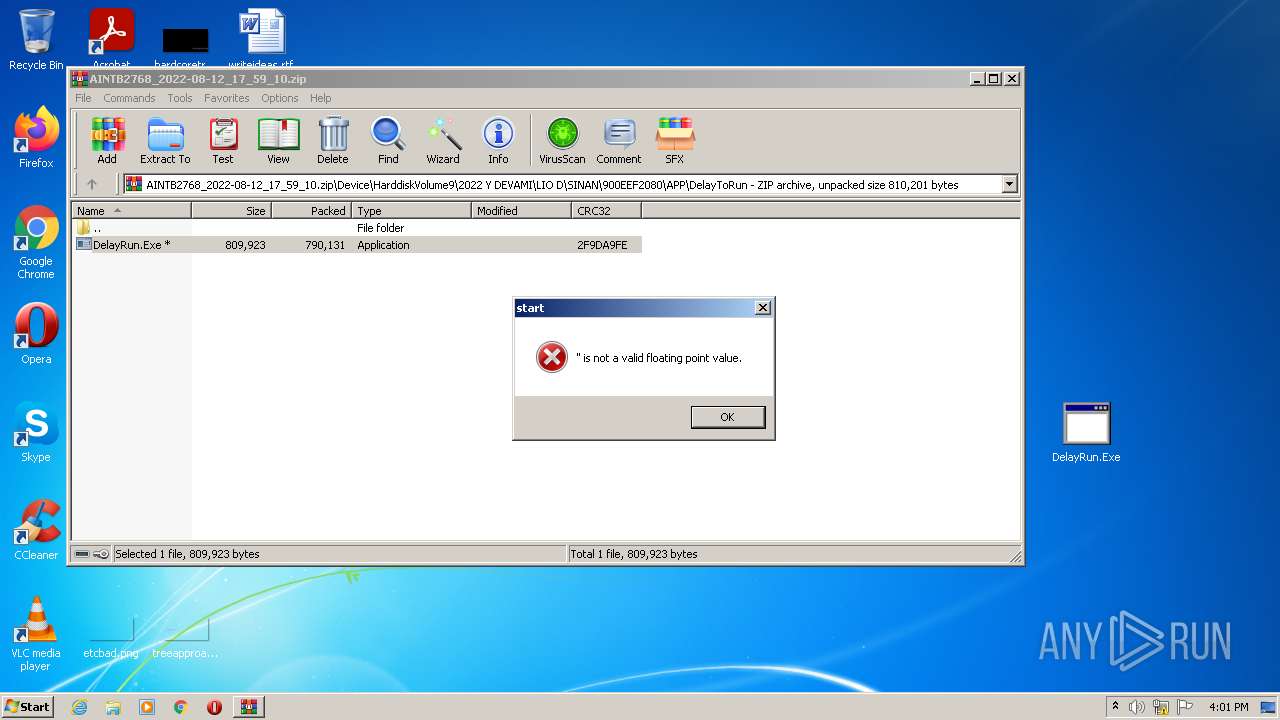
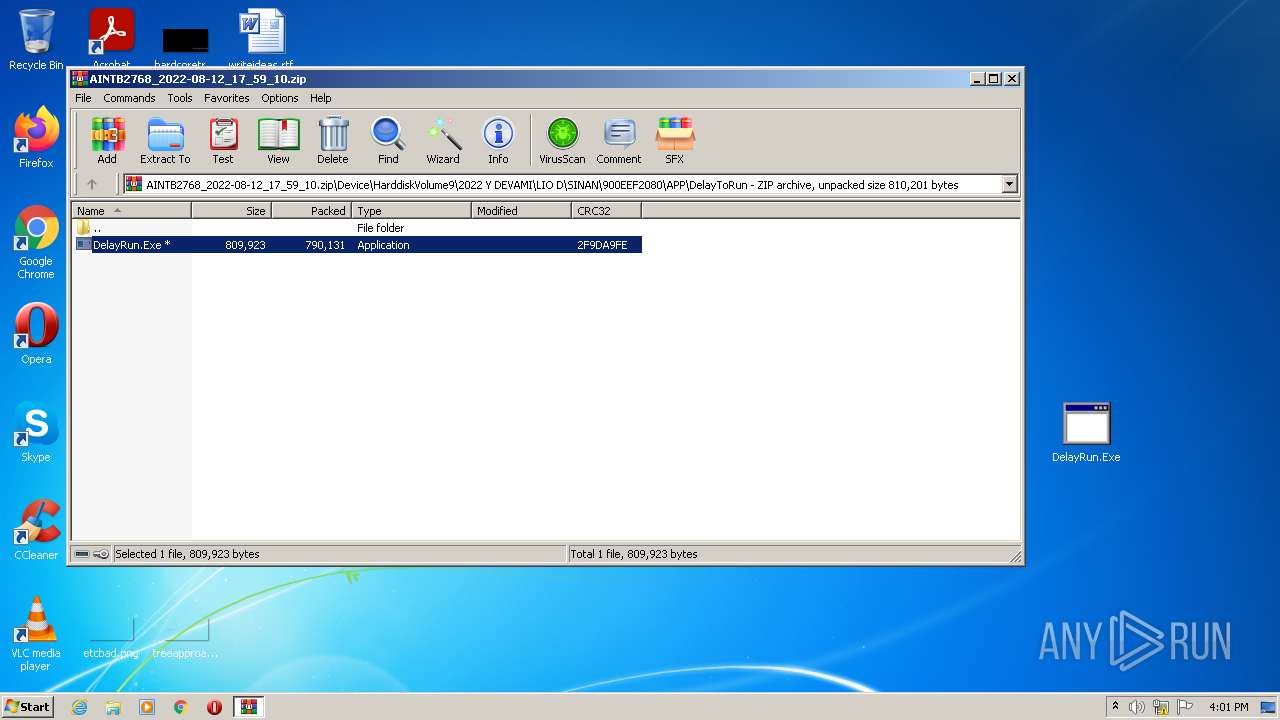
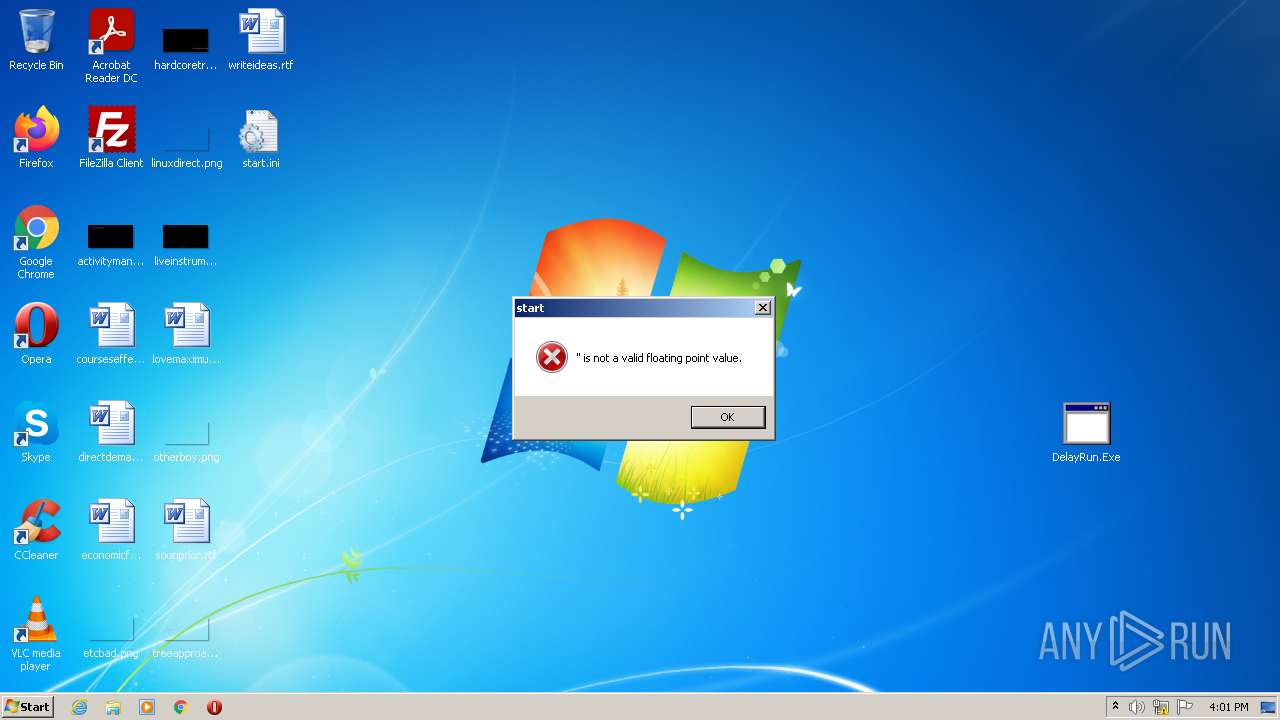
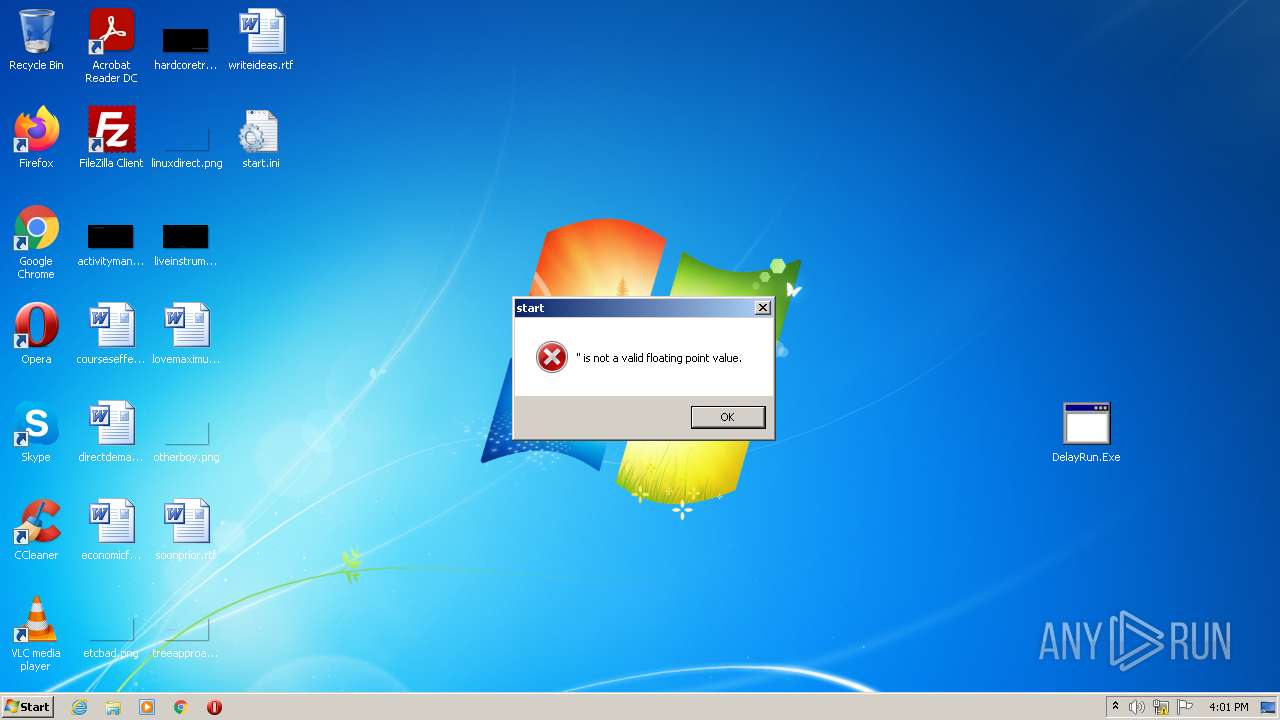
| File name: | AINTB2768_2022-08-12_17_59_10.zip |
| Full analysis: | https://app.any.run/tasks/1c4739dc-3cd6-4473-a543-bd229092c6d3 |
| Verdict: | Malicious activity |
| Analysis date: | August 12, 2022, 14:59:45 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v4.5 to extract |
| MD5: | D825582B6CE6A64489D1921554E9F70F |
| SHA1: | F86E45D52A769C49F8E772130BD098D9556D736A |
| SHA256: | 61B6A2A5D7D9C7B9D797C10433633E9A45E1F9DC726C7E33B5616C24FDCBBF3B |
| SSDEEP: | 24576:S+4wz7ghW03QaTkmwNcM9hte9nsLPWuXobHuk:lcwaTIaQ7epkWuYZ |
MALICIOUS
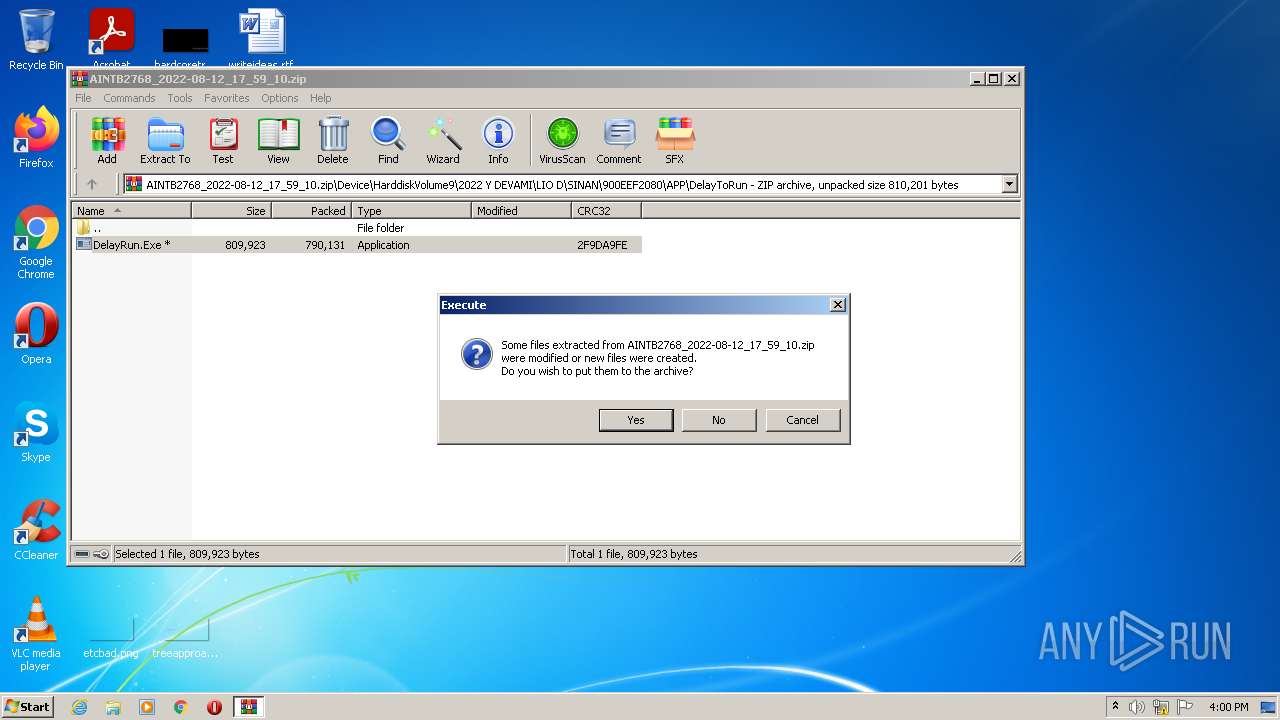
Application was dropped or rewritten from another process
- DelayRun.Exe (PID: 188)
- DelayRun.Exe (PID: 2848)
- DelayRun.Exe (PID: 1064)
- DelayRun.Exe (PID: 3000)
- DelayRun.Exe (PID: 3524)
- DelayRun.Exe (PID: 3564)
- DelayRun.Exe (PID: 1736)
Drops executable file immediately after starts
- WinRAR.exe (PID: 1420)
SUSPICIOUS
Drops a file with a compile date too recent
- WinRAR.exe (PID: 1420)
Checks supported languages
- WinRAR.exe (PID: 1420)
- DelayRun.Exe (PID: 188)
- DelayRun.Exe (PID: 2848)
- DelayRun.Exe (PID: 1064)
- DelayRun.Exe (PID: 3000)
- DelayRun.Exe (PID: 3524)
- DelayRun.Exe (PID: 3564)
- DelayRun.Exe (PID: 1736)
Reads the computer name
- WinRAR.exe (PID: 1420)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1420)
INFO
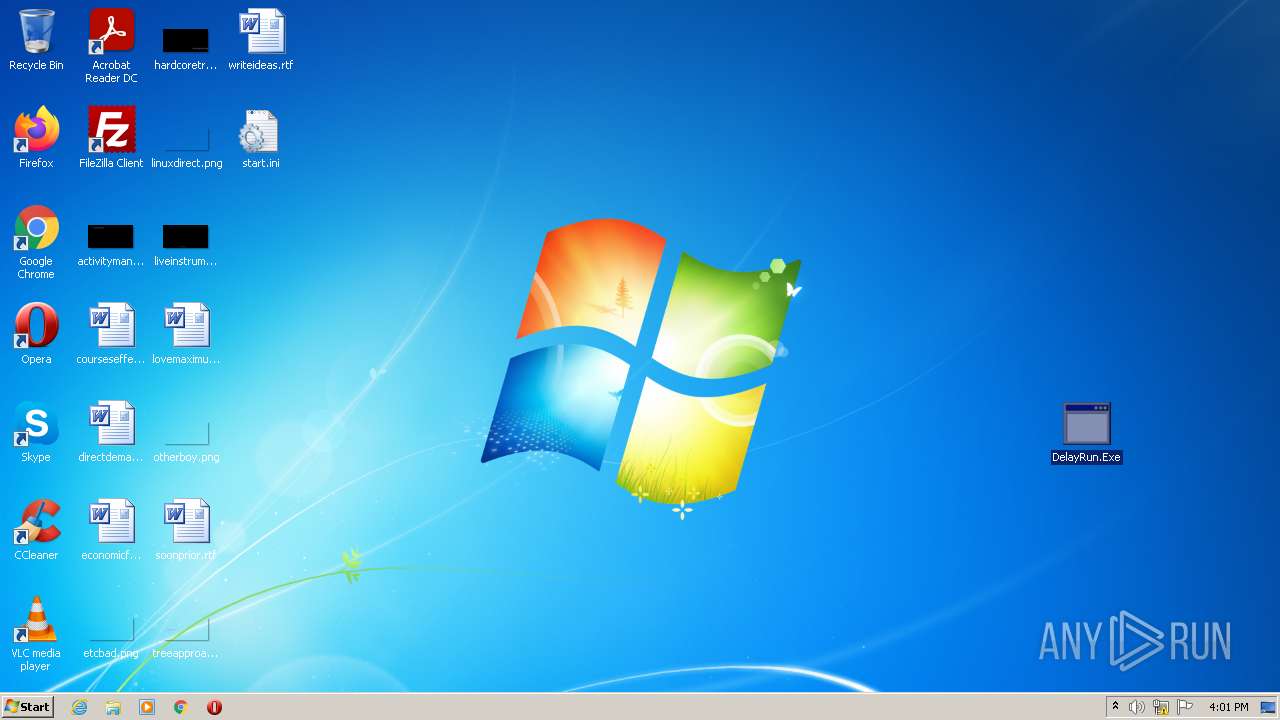
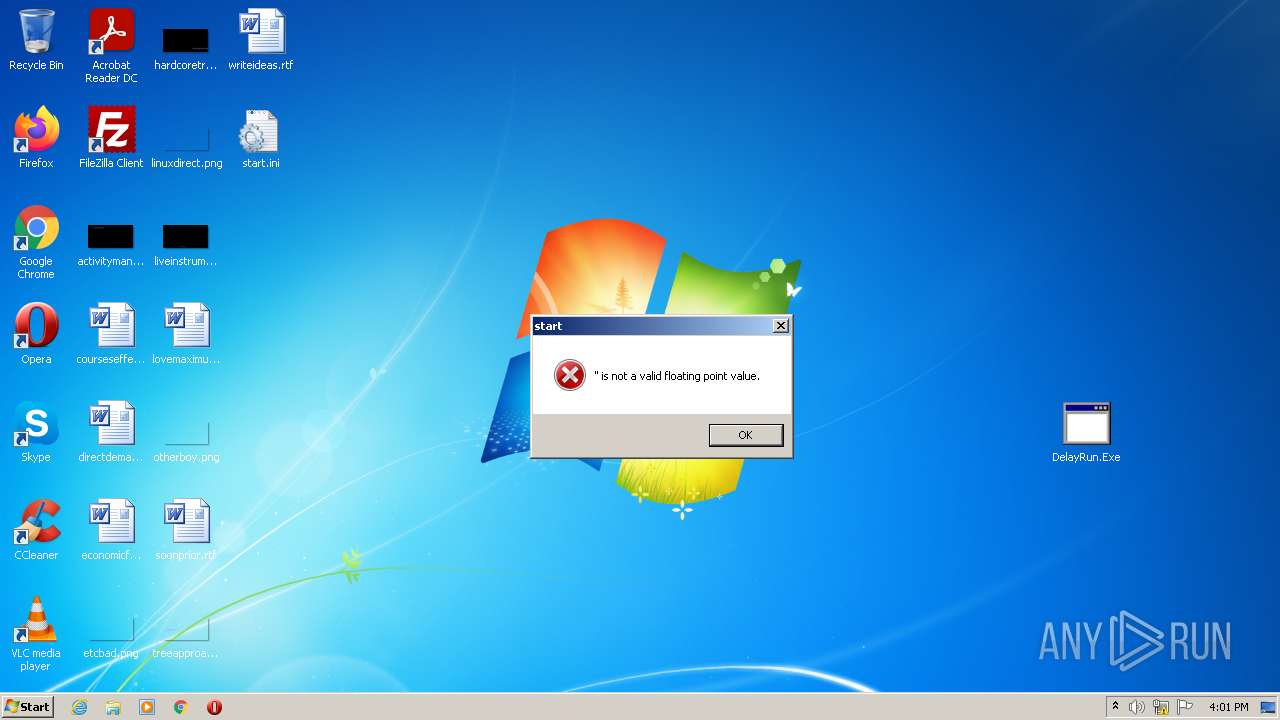
Manual execution by user
- DelayRun.Exe (PID: 2848)
- DelayRun.Exe (PID: 1064)
- DelayRun.Exe (PID: 3000)
- DelayRun.Exe (PID: 3524)
- DelayRun.Exe (PID: 3564)
- DelayRun.Exe (PID: 1736)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
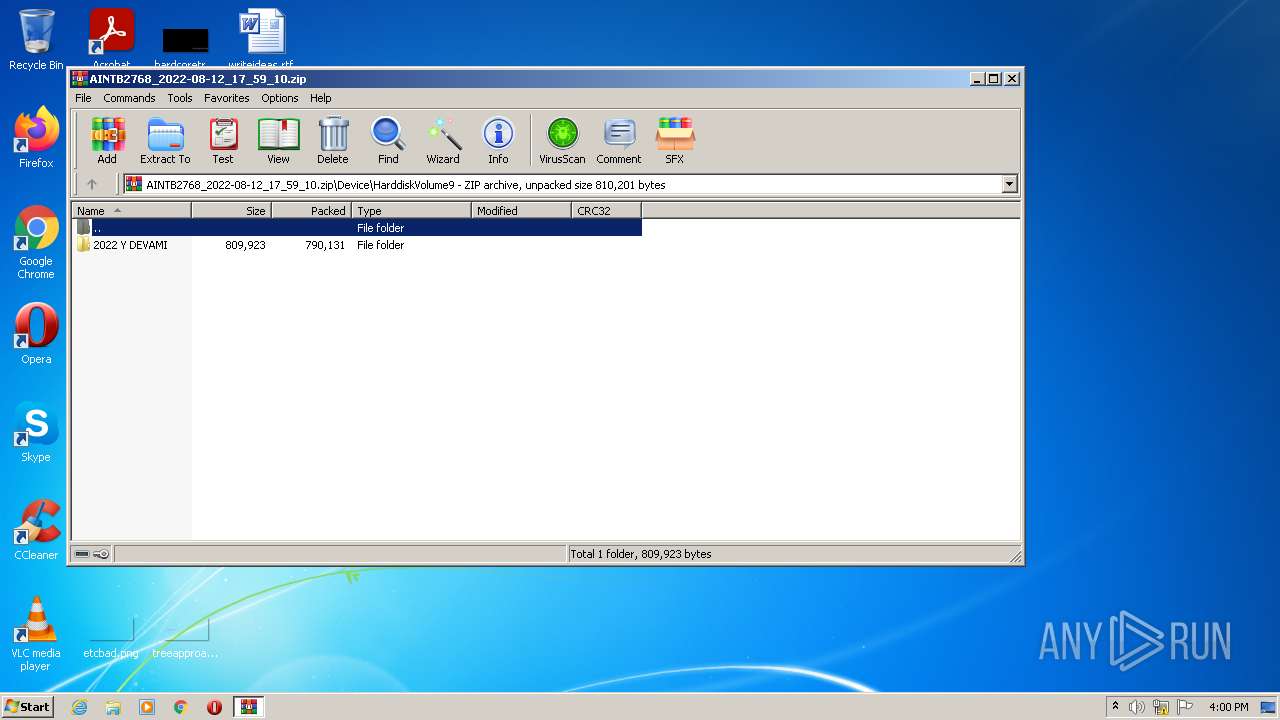
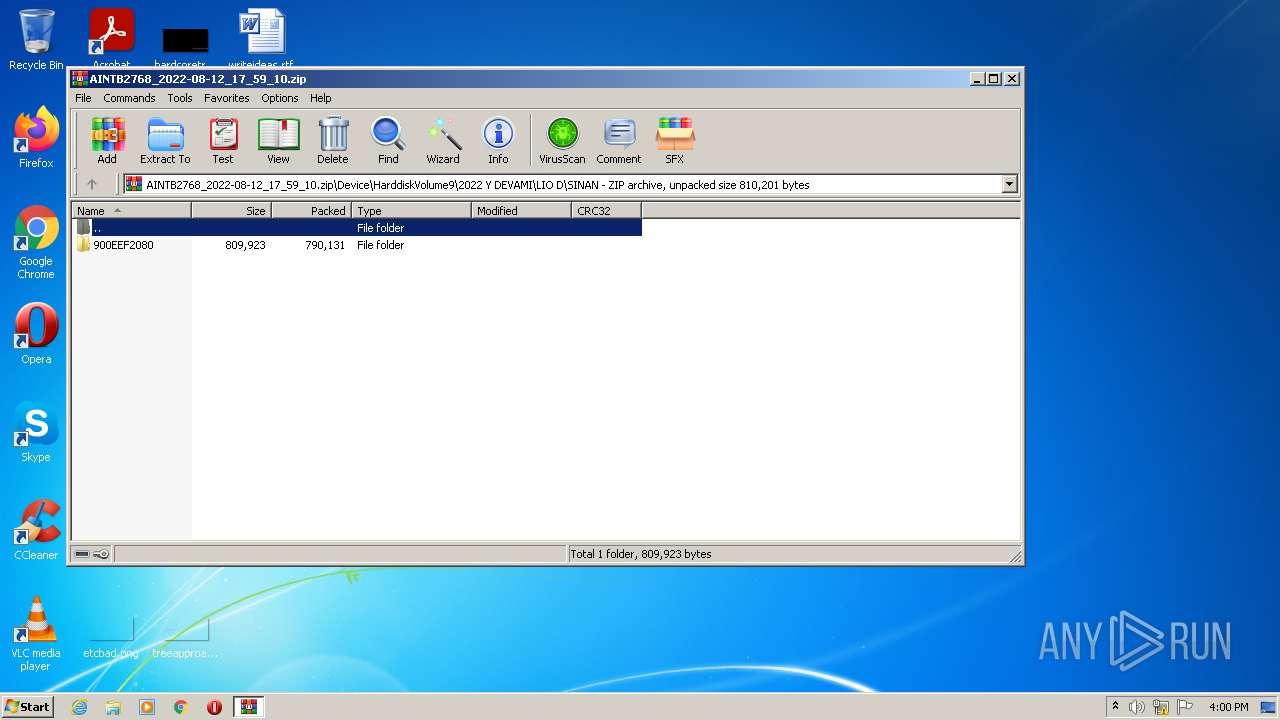
| ZipFileName: | Device/HarddiskVolume9/2022 Y DEVAMI/LIO D/SINAN/900EEF2080/APP/DelayToRun/DelayRun.Exe |
|---|---|
| ZipUncompressedSize: | 809923 |
| ZipCompressedSize: | 790131 |
| ZipCRC: | 0x2f9da9fe |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCompression: | Deflated |
| ZipBitFlag: | 0x0801 |
| ZipRequiredVersion: | 20 |
Total processes
43
Monitored processes
8
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb1420.9026\Device\HarddiskVolume9\2022 Y DEVAMI\LIO D\SINAN\900EEF2080\APP\DelayToRun\DelayRun.Exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb1420.9026\Device\HarddiskVolume9\2022 Y DEVAMI\LIO D\SINAN\900EEF2080\APP\DelayToRun\DelayRun.Exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1064 | "C:\Users\admin\Desktop\DelayRun.Exe" | C:\Users\admin\Desktop\DelayRun.Exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1420 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\AINTB2768_2022-08-12_17_59_10.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1736 | "C:\Users\admin\Desktop\DelayRun.Exe" | C:\Users\admin\Desktop\DelayRun.Exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2848 | "C:\Users\admin\Desktop\DelayRun.Exe" | C:\Users\admin\Desktop\DelayRun.Exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3000 | "C:\Users\admin\Desktop\DelayRun.Exe" | C:\Users\admin\Desktop\DelayRun.Exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3524 | "C:\Users\admin\Desktop\DelayRun.Exe" | C:\Users\admin\Desktop\DelayRun.Exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3564 | "C:\Users\admin\Desktop\DelayRun.Exe" | C:\Users\admin\Desktop\DelayRun.Exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
1 973
Read events
1 942
Write events
31
Delete events
0
Modification events
| (PID) Process: | (1420) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1420) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1420) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1420) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1420) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1420) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\AINTB2768_2022-08-12_17_59_10.zip | |||
| (PID) Process: | (1420) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1420) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1420) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1420) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
2
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1420 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb1420.9026\manifest.json | ini | |
MD5:— | SHA256:— | |||
| 1420 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb1420.9026\Device\HarddiskVolume9\2022 Y DEVAMI\LIO D\SINAN\900EEF2080\APP\DelayToRun\DelayRun.Exe | executable | |
MD5:— | SHA256:— | |||
| 1420 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1420.10995\Device\HarddiskVolume9\2022 Y DEVAMI\LIO D\SINAN\900EEF2080\APP\DelayToRun\DelayRun.Exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report