| File name: | in6.ps1 |
| Full analysis: | https://app.any.run/tasks/044cb3b4-6d70-49b2-942c-3c5b796ff8df |
| Verdict: | Malicious activity |
| Analysis date: | December 30, 2020, 16:33:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines, with CRLF line terminators |
| MD5: | B2C55A01DF509D91D23B8354CE8F3291 |
| SHA1: | 211AE34C1FF3449730A476B9383A84805A43E99C |
| SHA256: | 61B5934940E218F942AAEF0C7EFDAD99B4A210A1D9C3CCC01B276CDEE04C5AA3 |
| SSDEEP: | 49152:rWGMCm9Q9C6EvY/bOAc8EAK6AWB/X/hsE29RIpJKK5KhVcKNBH7jCZEDTE2fpGbV:p |
MALICIOUS
No malicious indicators.SUSPICIOUS
Uses NETSTAT.EXE to discover network connections
- powershell.exe (PID: 2744)
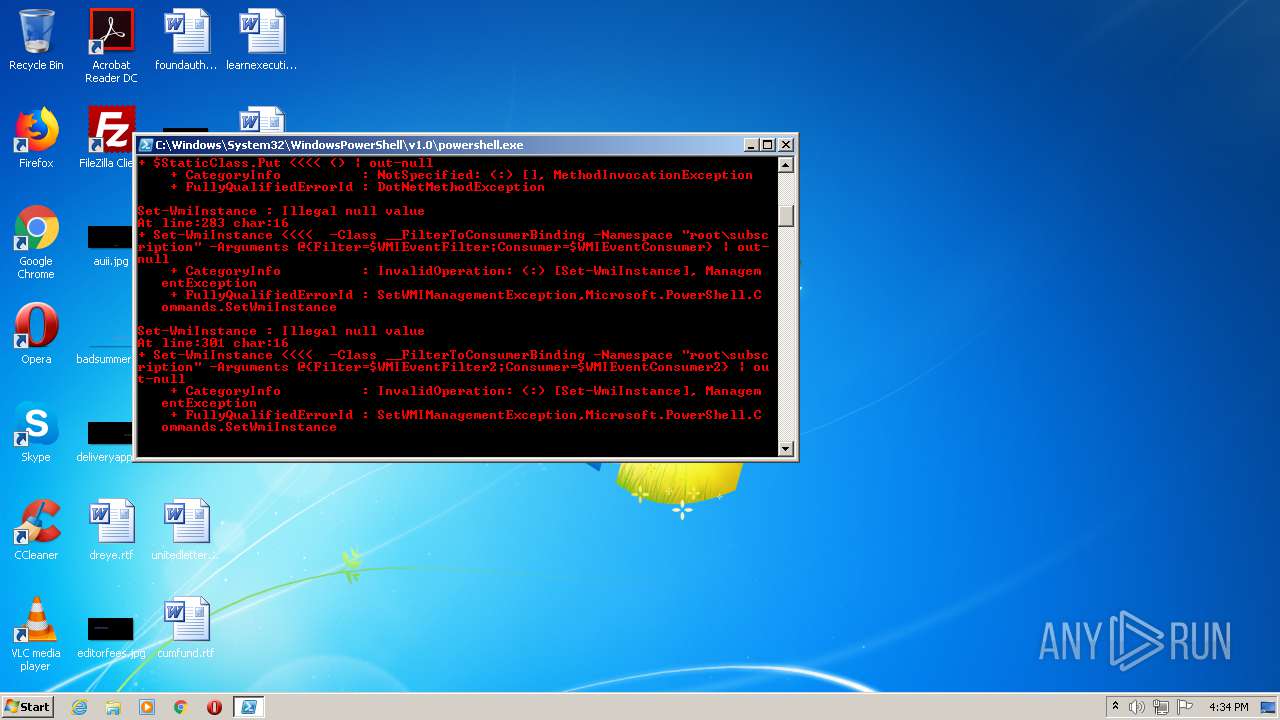
PowerShell script executed
- powershell.exe (PID: 2744)
Creates files in the user directory
- powershell.exe (PID: 2744)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
40
Monitored processes
5
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | "C:\Windows\system32\NETSTAT.EXE" -anop tcp | C:\Windows\system32\NETSTAT.EXE | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Netstat Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1980 | "C:\Windows\system32\powercfg.exe" /CHANGE -standby-timeout-ac 0 | C:\Windows\system32\powercfg.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Power Settings Command-Line Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2504 | "C:\Windows\system32\powercfg.exe" /CHANGE -hibernate-timeout-ac 0 | C:\Windows\system32\powercfg.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Power Settings Command-Line Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2744 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "-file" "C:\Users\admin\AppData\Local\Temp\in6.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3496 | "C:\Windows\system32\powercfg.exe" -SetAcValueIndex 381b4222-f694-41f0-9685-ff5bb260df2e 4f971e89-eebd-4455-a8de-9e59040e7347 5ca83367-6e45-459f-a27b-476b1d01c936 000 | C:\Windows\system32\powercfg.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Power Settings Command-Line Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
329
Read events
258
Write events
71
Delete events
0
Modification events
| (PID) Process: | (2744) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2744) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2744) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2744) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2744) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2744) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2744) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2744) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (2744) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (2744) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
Executable files
0
Suspicious files
2
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2744 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\MWCU87L4O9GS1MTESDT6.temp | — | |
MD5:— | SHA256:— | |||
| 2744 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF154a03.TMP | binary | |
MD5:— | SHA256:— | |||
| 2744 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
1
DNS requests
2
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
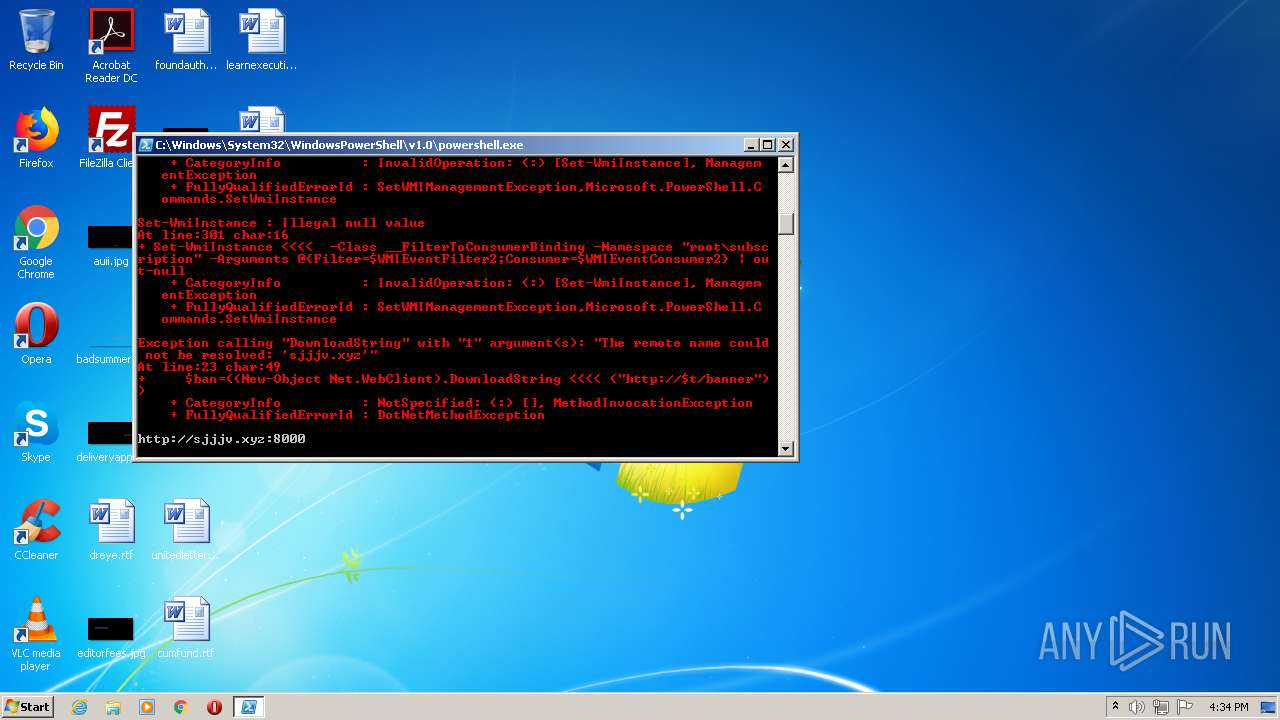
2744 | powershell.exe | GET | 200 | 45.10.69.141:8000 | http://profetestruec.net:8000/banner | unknown | text | 14 b | malicious |
2744 | powershell.exe | GET | 200 | 45.10.69.141:8000 | http://profetestruec.net:8000/in3.ps1 | unknown | text | 1.00 Mb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2744 | powershell.exe | 45.10.69.141:8000 | profetestruec.net | — | — | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
sjjjv.xyz |
| malicious |
profetestruec.net |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2744 | powershell.exe | A Network Trojan was detected | ET POLICY Win32/Ymacco.AA2F Checking (Multiple OS) |
2744 | powershell.exe | A Network Trojan was detected | MALWARE [PTsecurity] PowerShell/Dropper.ED56!tr |