analyze malware
- Huge database of samples and IOCs
- Custom VM setup
- Unlimited submissions
- Interactive approach
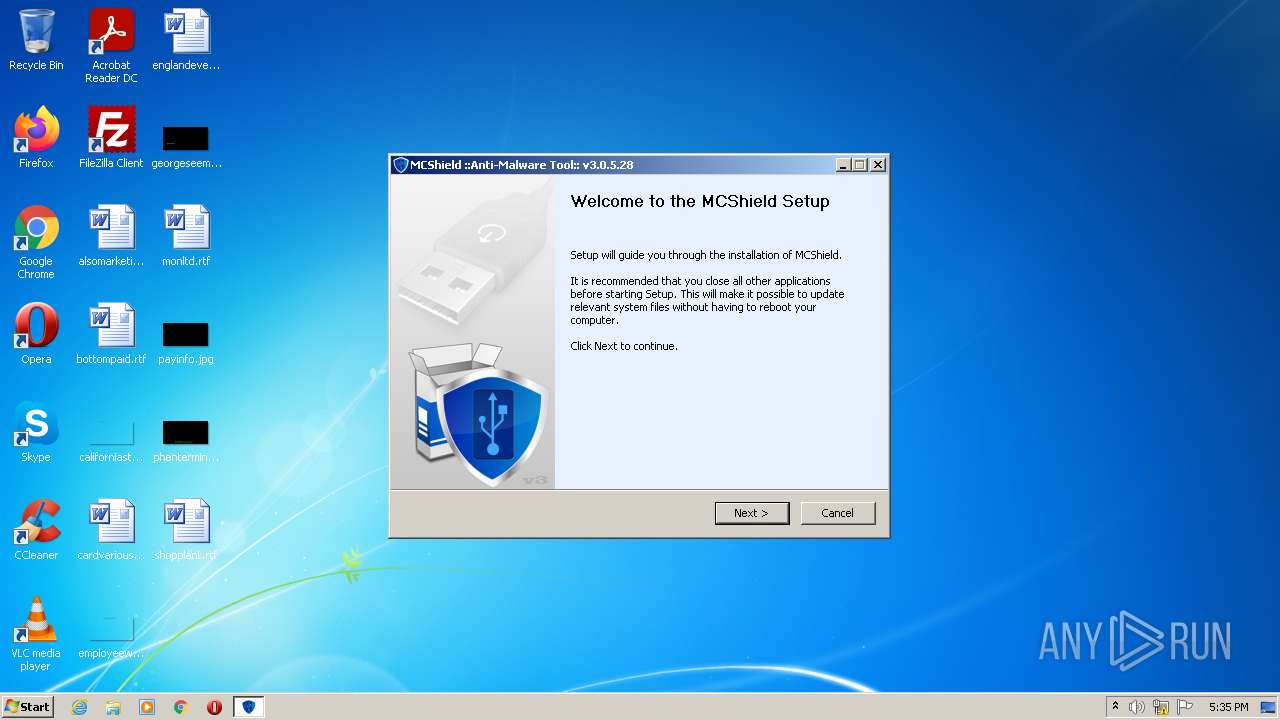
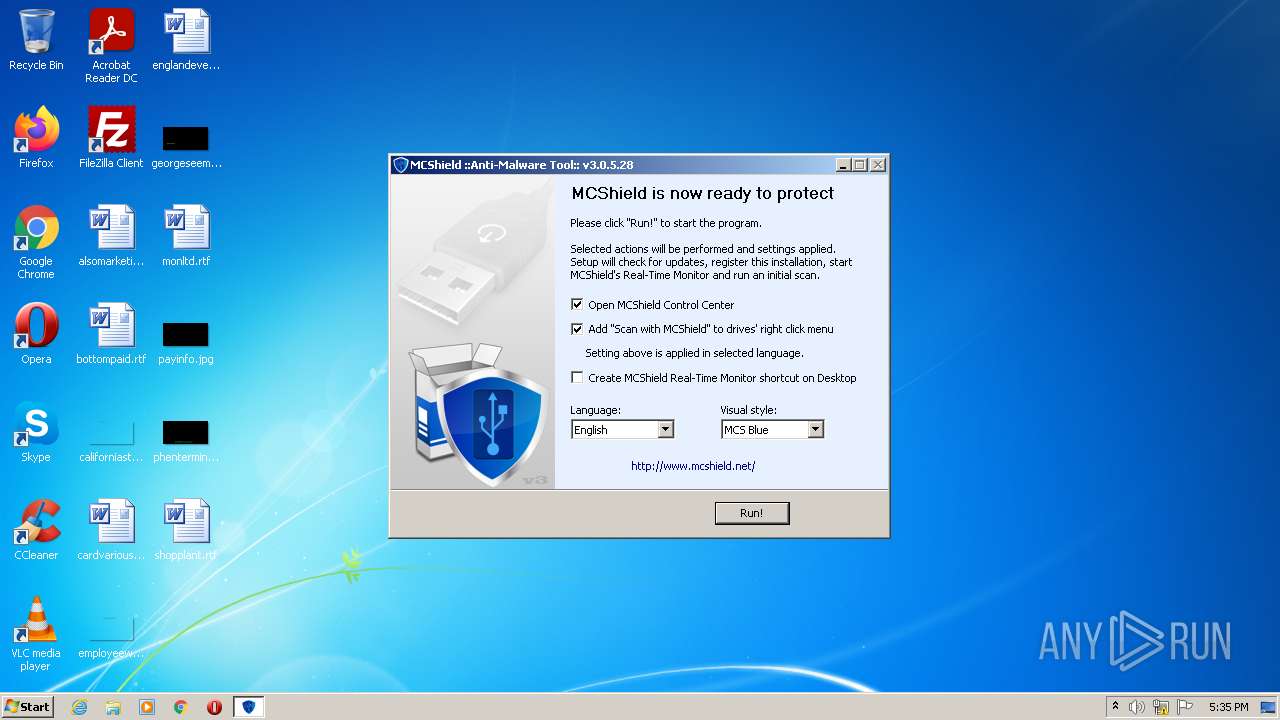
| File name: | MCShield-Setup.exe |
| Full analysis: | https://app.any.run/tasks/3996efdd-044e-44fb-963b-988d0fe0e4bc |
| Verdict: | Malicious activity |
| Analysis date: | May 20, 2022, 16:35:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 6E44C49039E696991D2DB54B5C81E2F5 |
| SHA1: | 894AF728E188305DE6588B40CEE9B33E023938BF |
| SHA256: | 61AEB8EAB73041503849EAFEC5F56103D79E82D80288A4210A8637F225917DC1 |
| SSDEEP: | 49152:++mCDy/KHacNFu2FhacuQMpRHGt9XPGQtdmP0S2iEl7IEg/:++mCDyyHah2fPutRE5PGvcl7I5/ |
MALICIOUS
Drops executable file immediately after starts
- MCShield-Setup.exe (PID: 2976)
- MCShield-Setup.exe (PID: 1792)
Loads dropped or rewritten executable
- MCShield-Setup.exe (PID: 2976)
- MCShield-Setup.exe (PID: 1792)
Changes the autorun value in the registry
- MCShield-Setup.exe (PID: 1792)
SUSPICIOUS
Drops a file with a compile date too recent
- MCShield-Setup.exe (PID: 2976)
- MCShield-Setup.exe (PID: 1792)
Executable content was dropped or overwritten
- MCShield-Setup.exe (PID: 2976)
- MCShield-Setup.exe (PID: 1792)
Checks supported languages
- MCShield-Setup.exe (PID: 2976)
- MCShield-Setup.exe (PID: 1792)
Reads the computer name
- MCShield-Setup.exe (PID: 2976)
- MCShield-Setup.exe (PID: 1792)
Application launched itself
- MCShield-Setup.exe (PID: 2976)
Creates a directory in Program Files
- MCShield-Setup.exe (PID: 1792)
Creates/Modifies COM task schedule object
- MCShield-Setup.exe (PID: 1792)
Creates files in the program directory
- MCShield-Setup.exe (PID: 1792)
Changes default file association
- MCShield-Setup.exe (PID: 1792)
Creates a software uninstall entry
- MCShield-Setup.exe (PID: 1792)
Creates files in the user directory
- MCShield-Setup.exe (PID: 1792)
INFO
Dropped object may contain Bitcoin addresses
- MCShield-Setup.exe (PID: 1792)
Checks supported languages
- explorer.exe (PID: 3280)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| ProductVersion: | 3.0.5.28 |
|---|---|
| ProductName: | MCShield ::Anti-Malware Tool:: |
| LegalCopyright: | © MyCity |
| FileVersion: | 3.0.5.28 |
| FileDescription: | MCShield ::Anti-Malware Tool:: |
| CompanyName: | MyCity |
| Comments: | MCShield: http://www.mcshield.net/ |
| CharacterSet: | Unicode |
| LanguageCode: | Neutral |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Win32 |
| FileFlags: | (none) |
| FileFlagsMask: | 0x0000 |
| ProductVersionNumber: | 3.0.5.28 |
| FileVersionNumber: | 3.0.5.28 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 5 |
| ImageVersion: | 6 |
| OSVersion: | 5 |
| EntryPoint: | 0x354b |
| UninitializedDataSize: | 16896 |
| InitializedDataSize: | 431104 |
| CodeSize: | 25600 |
| LinkerVersion: | 9 |
| PEType: | PE32 |
| TimeStamp: | 2010:04:10 14:19:31+02:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 10-Apr-2010 12:19:31 |
| Detected languages: |
|
| Comments: | MCShield: http://www.mcshield.net/ |
| CompanyName: | MyCity |
| FileDescription: | MCShield ::Anti-Malware Tool:: |
| FileVersion: | 3.0.5.28 |
| LegalCopyright: | © MyCity |
| ProductName: | MCShield ::Anti-Malware Tool:: |
| ProductVersion: | 3.0.5.28 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000E0 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 10-Apr-2010 12:19:31 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x000063A2 | 0x00006400 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.48045 |
.rdata | 0x00008000 | 0x000018F2 | 0x00001A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.88829 |
.data | 0x0000A000 | 0x0006669C | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 1.42988 |
.ndata | 0x00071000 | 0x000B5000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rsrc | 0x00126000 | 0x000248E8 | 0x00024A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.29056 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.22444 | 955 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 2.78093 | 38056 | UNKNOWN | English - United States | RT_ICON |
3 | 6.53566 | 16936 | UNKNOWN | English - United States | RT_ICON |
4 | 5.31473 | 9640 | UNKNOWN | English - United States | RT_ICON |
5 | 3.40747 | 7962 | UNKNOWN | English - United States | RT_ICON |
6 | 1.88906 | 4264 | UNKNOWN | English - United States | RT_ICON |
7 | 0 | 1128 | UNKNOWN | English - United States | RT_ICON |
102 | 2.71813 | 180 | UNKNOWN | English - United States | RT_DIALOG |
103 | 2.78436 | 104 | UNKNOWN | English - United States | RT_GROUP_ICON |
105 | 2.67385 | 512 | UNKNOWN | English - United States | RT_DIALOG |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
VERSION.dll |
ole32.dll |
Total processes
39
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
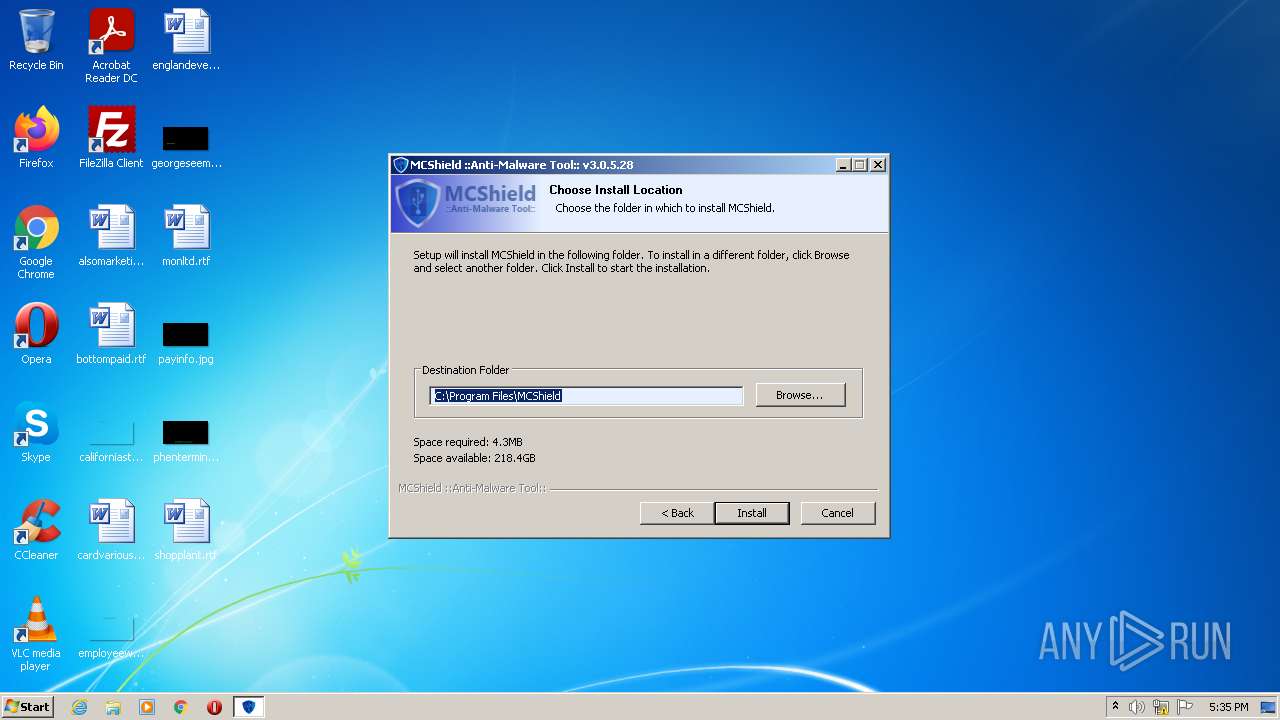
| 2976 | "C:\Users\admin\AppData\Local\Temp\MCShield-Setup.exe" | C:\Users\admin\AppData\Local\Temp\MCShield-Setup.exe | Explorer.EXE | |
User: admin Company: MyCity Integrity Level: MEDIUM Description: MCShield ::Anti-Malware Tool:: Version: 3.0.5.28 | ||||
| 1792 | "C:\Users\admin\AppData\Local\Temp\MCShield-Setup.exe" /UAC:2012C /NCRC | C:\Users\admin\AppData\Local\Temp\MCShield-Setup.exe | MCShield-Setup.exe | |
User: admin Company: MyCity Integrity Level: HIGH Description: MCShield ::Anti-Malware Tool:: Version: 3.0.5.28 | ||||
| 3280 | C:\Windows\explorer.exe | C:\Windows\explorer.exe | — | MCShield-Setup.exe |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
Total events
1 939
Read events
1 846
Write events
0
Delete events
0
Modification events
Executable files
22
Suspicious files
3
Text files
44
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1792 | MCShield-Setup.exe | C:\Users\admin\AppData\Local\Temp\nsi97FE.tmp\Aero.dll | executable | |
MD5:4A431317F236C9C77FD0D60FD86160E7 | SHA256:9F203844E8BA8B566FE4C613294BF329E9CF4E6E618882479E4E2672AD55FC05 | |||
| 1792 | MCShield-Setup.exe | C:\Users\admin\AppData\Local\Temp\spltmp.jpg | image | |
MD5:11CB9FCBD254B9A2A209B8D8D53EB98B | SHA256:A3092E4A52D44837E5641A433D9C30292CE8568EE959C8E72772AE2C4FE76A35 | |||
| 1792 | MCShield-Setup.exe | C:\Program Files\MCShield\_Translator.exe | executable | |
MD5:2537BEC725060DCBB10258122CBA3368 | SHA256:F919A20603C7109394C52FC560F3FA9004EA345E7824D0941FAE3ECB7C875101 | |||
| 1792 | MCShield-Setup.exe | C:\Users\admin\AppData\Local\Temp\nsi97FE.tmp\modern-header.bmp | image | |
MD5:37665CCFB10BCE8322C78A6E696E9992 | SHA256:275086F793C62C86894F938E3C9FA1F18BDCAAFD884779E421A6ACF1B4FA2494 | |||
| 1792 | MCShield-Setup.exe | C:\Program Files\MCShield\_MCShieldCC.exe | executable | |
MD5:433E000C5E873A084F2F10A9CE9C42FE | SHA256:C78A4B83387807DADDF7AA5258367612754360AD322CCAF5E825D057A654436B | |||
| 1792 | MCShield-Setup.exe | C:\Program Files\MCShield\_LastScan.txt | text | |
MD5:4FE0A47305F99C53F9F33AF1B0E9BA5A | SHA256:0D54EF41A67936C83EAEEA38CC1F299037E81F63240EC78CCDE3406A6D7C14A7 | |||
| 1792 | MCShield-Setup.exe | C:\Users\admin\AppData\Local\Temp\nsi97FE.tmp\modern-wizard.bmp | image | |
MD5:77D35DA598C31BE461D3EB7BCF411AF2 | SHA256:B2302B3F38E92B9A55503888247A1BBF79C76FF74412E4B43D0FD2518EBBAEDE | |||
| 1792 | MCShield-Setup.exe | C:\Program Files\MCShield\_MCShieldRTM.exe | executable | |
MD5:E5703839EE9DD7FACE721CF56E3F9963 | SHA256:4B020EAA0B9F47D61F2C77A8755C43D34C72C8D4132FD17BC011A6316250E66E | |||
| 1792 | MCShield-Setup.exe | C:\Program Files\MCShield\_AllScans.txt | text | |
MD5:A81791CBEE45EFA066AF718EF6160DA0 | SHA256:0273B4222C3BAAA5D9B023B2D48256B68CBF508EFE67C48C74F475CDF5E6DDA7 | |||
| 1792 | MCShield-Setup.exe | C:\Program Files\MCShield\_news.txt | text | |
MD5:F326998B88F1D382BA1130832A0CE8CF | SHA256:F55BF57755B8AF973E07934D546D0A2A1D5DD5264A01F4976D39C653E998F0BC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
7
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1792 | MCShield-Setup.exe | GET | 302 | 103.224.182.208:80 | http://www.mcshield.net/download/version-info.txt | AU | — | — | malicious |
1792 | MCShield-Setup.exe | GET | 302 | 103.224.182.208:80 | http://www.mcshield.net/download/version-info.txt | AU | — | — | malicious |
1792 | MCShield-Setup.exe | GET | 302 | 103.224.182.208:80 | http://www.mcshield.net/download/MCSDB.bin | AU | — | — | malicious |
1792 | MCShield-Setup.exe | GET | 200 | 199.59.243.200:80 | http://ww25.mcshield.net/download/version-info.txt?subid1=20220521-0235-5684-9d12-bcf8ab72a466 | US | html | 1.36 Kb | malicious |
1792 | MCShield-Setup.exe | GET | 200 | 199.59.243.200:80 | http://ww25.mcshield.net/download/version-info.txt?subid1=20220521-0236-1588-8390-80dcb8eefa6b | US | html | 1.45 Kb | malicious |
1792 | MCShield-Setup.exe | GET | 404 | 94.130.164.54:80 | http://www2.mycity.rs/mcshield/install.php?ver=3.0.5.28 | DE | html | 1.39 Kb | suspicious |
1792 | MCShield-Setup.exe | GET | 200 | 199.59.243.200:80 | http://ww25.mcshield.net/download/MCSDB.bin?subid1=20220521-0236-30ce-9ddd-556688e0ea47 | US | html | 1.44 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1792 | MCShield-Setup.exe | 94.130.164.54:80 | www2.mycity.rs | Hetzner Online GmbH | DE | suspicious |
1792 | MCShield-Setup.exe | 103.224.182.208:80 | www.mcshield.net | Trellian Pty. Limited | AU | suspicious |
— | — | 103.224.182.208:80 | www.mcshield.net | Trellian Pty. Limited | AU | suspicious |
1792 | MCShield-Setup.exe | 199.59.243.200:80 | ww25.mcshield.net | — | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.mcshield.net |
| malicious |
ww25.mcshield.net |
| malicious |
www2.mycity.rs |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1792 | MCShield-Setup.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
1792 | MCShield-Setup.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
1792 | MCShield-Setup.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
1792 | MCShield-Setup.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
1792 | MCShield-Setup.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
1792 | MCShield-Setup.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
1792 | MCShield-Setup.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
1792 | MCShield-Setup.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
1792 | MCShield-Setup.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
1792 | MCShield-Setup.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |