| File name: | 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe |
| Full analysis: | https://app.any.run/tasks/b58f4e61-ce73-45c3-addb-1cbc2706e868 |
| Verdict: | Malicious activity |
| Analysis date: | March 08, 2024, 02:28:47 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | 92EAA2C4ED748E199065628B704A93A0 |
| SHA1: | E2EB95B0B8F408A8022AB1ED872E3FC5E73B5F34 |
| SHA256: | 61A0BA630479946F811A17478115FD4CB4D56A3FB5A26E69473A8EA4FB4E029C |
| SSDEEP: | 24576:5errpLXtQKQzJ2jcAGIy838YvFPy/Dq6s5Ojoj:5irpdQNgjcAGIy8sYvFPx6oOk |
MALICIOUS
Drops the executable file immediately after the start
- 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe (PID: 2724)
- 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe (PID: 4092)
SUSPICIOUS
Reads the date of Windows installation
- 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe (PID: 2724)
Application launched itself
- 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe (PID: 2724)
Reads security settings of Internet Explorer
- 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe (PID: 2724)
- 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe (PID: 4092)
Process drops legitimate windows executable
- 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe (PID: 4092)
Executable content was dropped or overwritten
- 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe (PID: 4092)
The process drops C-runtime libraries
- 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe (PID: 4092)
Process requests binary or script from the Internet
- 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe (PID: 4092)
INFO
Checks supported languages
- 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe (PID: 2724)
- 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe (PID: 4092)
- java.exe (PID: 3944)
- javaw.exe (PID: 4360)
Reads the computer name
- 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe (PID: 2724)
- 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe (PID: 4092)
Process checks computer location settings
- 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe (PID: 2724)
Create files in a temporary directory
- 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe (PID: 2724)
- 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe (PID: 4092)
- java.exe (PID: 3944)
- javaw.exe (PID: 4360)
Creates files in the program directory
- 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe (PID: 4092)
Checks proxy server information
- 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe (PID: 4092)
- slui.exe (PID: 6648)
Creates files or folders in the user directory
- 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe (PID: 4092)
Reads CPU info
- java.exe (PID: 3944)
- javaw.exe (PID: 4360)
Reads the software policy settings
- slui.exe (PID: 6648)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2022:12:29 07:43:36+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 10 |
| CodeSize: | 531456 |
| InitializedDataSize: | 392192 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x5c304 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.0.0.0 |
| ProductVersionNumber: | 3.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Unknown (0019) |
| CharacterSet: | Unicode |
| CompanyName: | INSTREM |
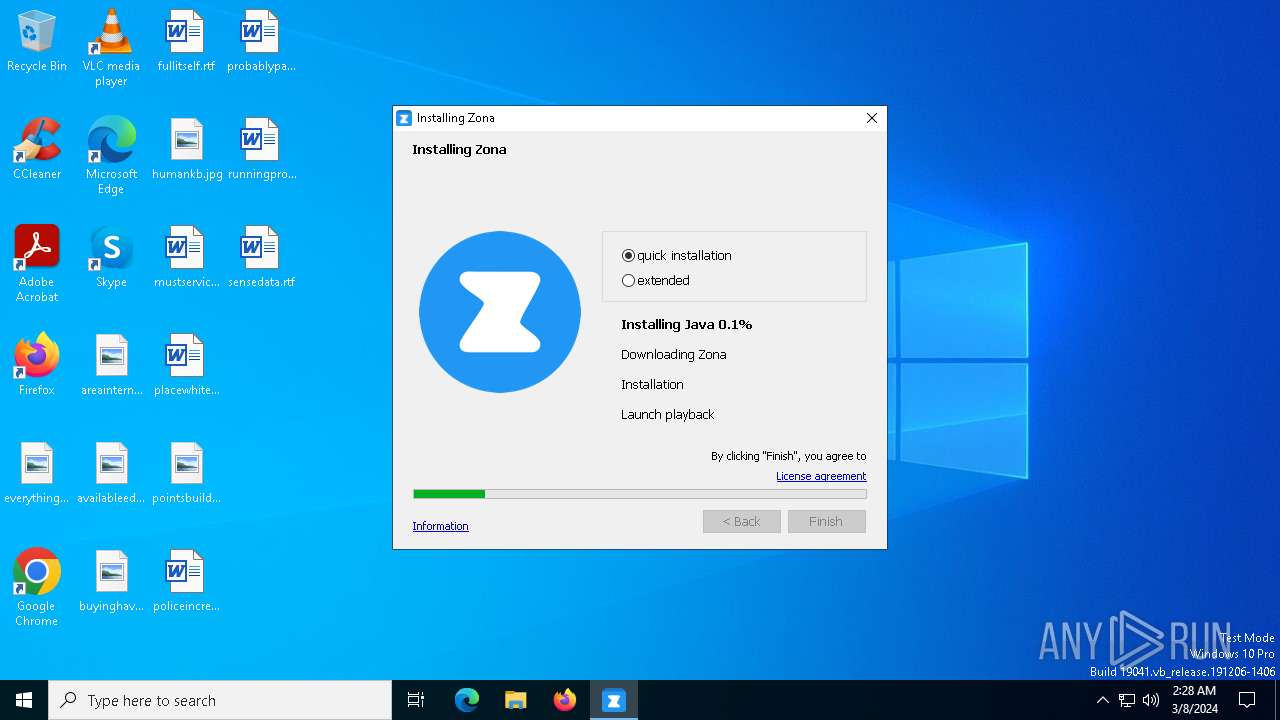
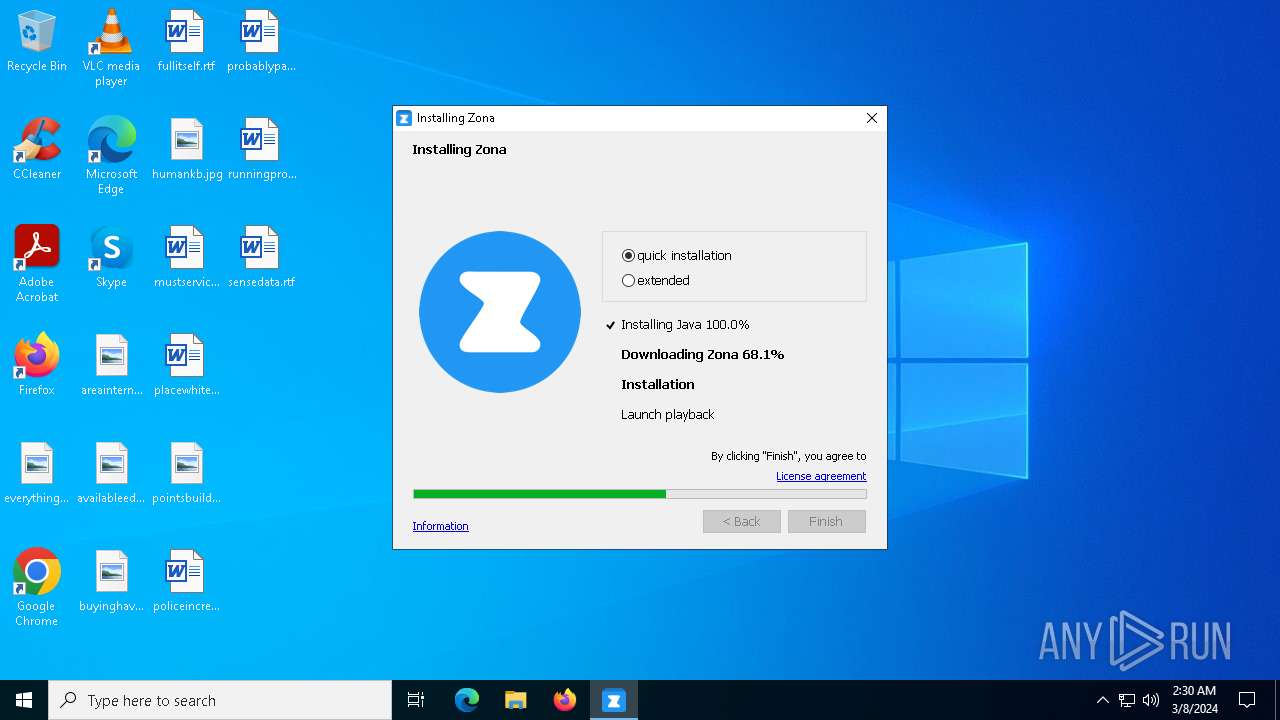
| FileDescription: | Zona installer |
| FileVersion: | 3.0.0.0 |
| InternalName: | ZonaInstaller.exe |
| LegalCopyright: | Copyright (C) 2022 |
| ProductName: | Zona installer |
| ProductVersion: | 3.0.0.0 |
Total processes
121
Monitored processes
6
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2724 | "C:\Users\admin\AppData\Local\Temp\61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe" | C:\Users\admin\AppData\Local\Temp\61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe | — | explorer.exe | |||||||||||
User: admin Company: INSTREM Integrity Level: MEDIUM Description: Zona installer Exit code: 0 Version: 3.0.0.0 Modules
| |||||||||||||||
| 3944 | "C:\PROGRA~1\Zona\jre\bin\java.exe" -version | C:\Program Files\Zona\jre\bin\java.exe | — | 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe | |||||||||||
User: admin Company: Eclipse Adoptium Integrity Level: HIGH Description: OpenJDK Platform binary Exit code: 0 Version: 11.0.15 Modules
| |||||||||||||||
| 4092 | "C:\Users\admin\AppData\Local\Temp\61A0BA~1.EXE" /secondInstance /logPath "C:\Users\admin\AppData\Local\Temp\ZonaInstall.log" | C:\Users\admin\AppData\Local\Temp\61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe | 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe | ||||||||||||
User: admin Company: INSTREM Integrity Level: HIGH Description: Zona installer Exit code: 0 Version: 3.0.0.0 Modules
| |||||||||||||||
| 4360 | "C:\PROGRA~1\Zona\jre\bin\javaw.exe" -classpath "C:\PROGRA~1\Zona\utils.jar" ru.megamakc.core.JavaArch | C:\Program Files\Zona\jre\bin\javaw.exe | — | 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe | |||||||||||
User: admin Company: Eclipse Adoptium Integrity Level: HIGH Description: OpenJDK Platform binary Exit code: 64 Version: 11.0.15 Modules
| |||||||||||||||
| 4700 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | java.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6648 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 597
Read events
5 575
Write events
22
Delete events
0
Modification events
| (PID) Process: | (2724) 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Pinstall |
| Operation: | write | Name: | i_user_id |
Value: 078F4E3C-8794-4AFF-BC5D-01C1ADCFBC63 | |||
| (PID) Process: | (2724) 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2724) 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2724) 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2724) 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (4092) 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Zona |
| Operation: | write | Name: | exec |
Value: C:\Program Files\Zona\Zona.exe | |||
| (PID) Process: | (4092) 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Zona |
| Operation: | write | Name: | DownloadsDir |
Value: C:\Users\admin\Documents\Zona Downloads | |||
| (PID) Process: | (4092) 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (4092) 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4092) 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
98
Suspicious files
5
Text files
229
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4092 | 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe | C:\Users\admin\AppData\Local\Temp\jre8BD5.tmp | — | |
MD5:— | SHA256:— | |||
| 2724 | 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe | C:\Users\admin\AppData\Local\Temp\ZonaInstall.log | text | |
MD5:E8C2993B7B60C9DBEF9A89D9ECA411FF | SHA256:427C5288B3BD8B647D2BD4B3ED65B124818CCBF4814EFC0290FBFA3DFB55B66F | |||
| 4092 | 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe | C:\PROGRA~1\Zona\License_uk.rtf | text | |
MD5:80606AD23E78C34ECD419864FDBFF137 | SHA256:0E651FB683476D17336E11D1152225416C8E3089C25593F4EED3D61B2A43A262 | |||
| 4092 | 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe | C:\PROGRA~1\Zona\utils.jar | compressed | |
MD5:96A5CE1F1E403294FB341250537A1370 | SHA256:2EAB829FF82F6510F2D08083042C34951EBBFB0EB389F22C7B1654EA21040CC0 | |||
| 4092 | 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe | C:\PROGRA~1\Zona\jre\bin\api-ms-win-core-heap-l1-1-0.dll | executable | |
MD5:9918F3AB081D9677725A42BB9404C30C | SHA256:3269C02BF596610105129A130A09DC1AF6D5AADC7963BA89EC2F94E6272280BA | |||
| 4092 | 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe | C:\PROGRA~1\Zona\jre\bin\api-ms-win-core-memory-l1-1-0.dll | executable | |
MD5:584CCC0B7CBFCBAE5A42DE9F1AB8DDEF | SHA256:5F134268D8357DF48E63B7B54F9F8524D00464F576BF962743194F279A63F35E | |||
| 4092 | 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe | C:\PROGRA~1\Zona\jre\bin\api-ms-win-core-libraryloader-l1-1-0.dll | executable | |
MD5:72699261554BF79AFFC4E83644743FA8 | SHA256:6D2B53CB396F9E844B6F16F7C02AC736C65B02B37925179A2D06A416049DFD5A | |||
| 4092 | 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe | C:\PROGRA~1\Zona\jre\bin\api-ms-win-core-debug-l1-1-0.dll | executable | |
MD5:034D6F4513448E68D82A2FD9695E9055 | SHA256:F81E655291DCCA48B7EF37ABC4E23CA101261FD9955D862EB4DF9317C398965E | |||
| 4092 | 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe | C:\PROGRA~1\Zona\jre\bin\api-ms-win-core-file-l1-2-0.dll | executable | |
MD5:1CBA516107ED68857615DE261E8EA332 | SHA256:EA7241A2973FBFC79263134F9799116BAFC6762F02C979C8CA0E5FE5D789E2DF | |||
| 4092 | 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe | C:\PROGRA~1\Zona\jre\bin\api-ms-win-core-interlocked-l1-1-0.dll | executable | |
MD5:BCEE0500B67D7D58A18C60386B935988 | SHA256:20BEBEFC10B9C64008432FCCF960D93B869BCBF5B65C59A8B1625B4E489ACC7D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
26
TCP/UDP connections
25
DNS requests
7
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4092 | 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe | GET | 206 | 46.254.18.90:80 | http://dl2.zonainst.com/Zona.ebz | unknown | binary | 3.17 Mb | unknown |
4092 | 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe | GET | 200 | 185.22.235.93:80 | http://install.zonastat.com/installer2.html?param=d03dd27af7e25c83272e737ffe5caba2c7089a7bfd3dd76db4a6f9cbe8924f88e50af37761d3cbf1047527ea6018831ccf5ed775167483b5b10e531908f87e58c20ebebbcc485ebed56f43a88f542e5b4544534cf22038dfb202dfab432b27281d84703828b5a7a71bd9ad7ab4ce86ee9bb9fb365cb9e2111fed34a6c150cad247815184603cd4c4454595f9cac851dbbcedc459b44ac78b2257022a9888c837a376aef19c0448ae6737f31910adea00a0176130621272881e3a4b02cc87a45fff1c166869d4d727db2d097c0db575ff680bef90a6727a69ea70f8061c791ecc5d89b7b9e8977f8a14661d11696dbecb2bd3ed2aaaa91dfe9de14bdb2781f1042f5681447e76c6a4db6e92539ccec238698a90dc9613c641727d154f9d635994018088a6fe86ad2a9540eee860188d5368f4092c3bc161f02443265580447c02f395bbe59047ff022940df28d76f1445300f933768c93567ac1ba6ac13a20055acd47efecfb812e02ecf790bc7ac4b26ceff228db98825797f269ef52a2f10b140bceef0e419c34442595bbac40790977adcbb5fa9f921185e1fe72e6f7f04c1 | unknown | binary | 82 b | unknown |
4092 | 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe | GET | 200 | 185.22.235.16:80 | http://dl.upzona.net/java2.json | unknown | binary | 81 b | unknown |
4092 | 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe | GET | — | 46.254.18.90:80 | http://dl2.zonainst.com/Zona.ebz | unknown | — | — | unknown |
4092 | 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe | GET | — | 46.254.18.90:80 | http://dl2.zonainst.com/appdata.ebz | unknown | — | — | unknown |
4092 | 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe | GET | 206 | 185.22.235.16:80 | http://dl.upzona.net/jre2_packed.ebz | unknown | binary | 6.29 Mb | unknown |
4092 | 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe | GET | 206 | 185.22.235.16:80 | http://dl.upzona.net/jre2_packed.ebz | unknown | binary | 6.29 Mb | unknown |
4092 | 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe | GET | — | 46.254.18.90:80 | http://dl2.zonainst.com/appdata.ebz | unknown | — | — | unknown |
4092 | 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe | GET | — | 46.254.18.90:80 | http://dl2.zonainst.com/appdata.ebz | unknown | — | — | unknown |
4092 | 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe | GET | 206 | 185.22.235.16:80 | http://dl.upzona.net/jre2_packed.ebz | unknown | binary | 6.29 Mb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3624 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4092 | 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe | 185.22.235.93:80 | install.zonastat.com | EuroByte LLC | RU | unknown |
4092 | 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe | 185.22.235.16:80 | dl.upzona.net | EuroByte LLC | RU | unknown |
4092 | 61a0ba630479946f811a17478115fd4cb4d56a3fb5a26e69473a8ea4fb4e029c.exe | 46.254.18.90:80 | dl2.zonainst.com | EuroByte LLC | RU | unknown |
3308 | svchost.exe | 40.115.3.253:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5000 | backgroundTaskHost.exe | 95.101.133.80:443 | — | Telia Company AB | SE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6692 | svchost.exe | 2.18.97.227:80 | go.microsoft.com | Akamai International B.V. | FR | unknown |
6692 | svchost.exe | 138.91.171.81:80 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
install.zonastat.com |
| unknown |
dl.upzona.net |
| unknown |
dl2.zonainst.com |
| unknown |
go.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
dmd.metaservices.microsoft.com |
| whitelisted |
Threats
1 ETPRO signatures available at the full report