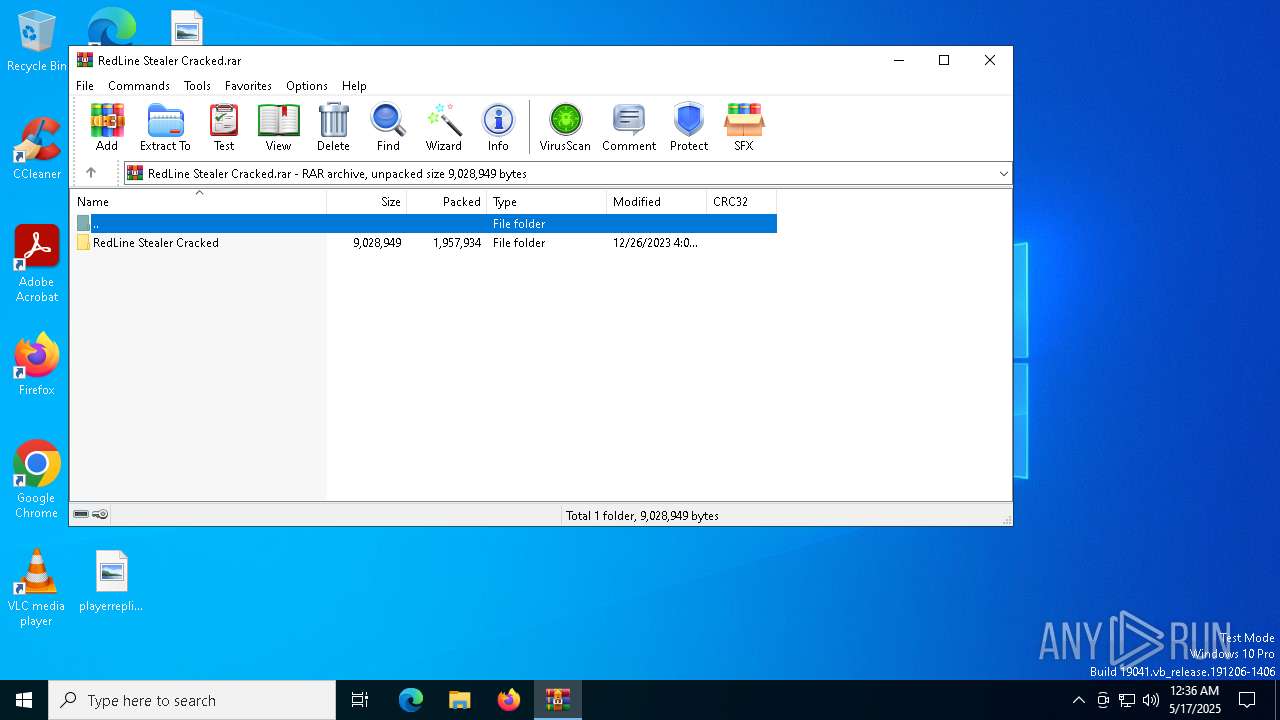
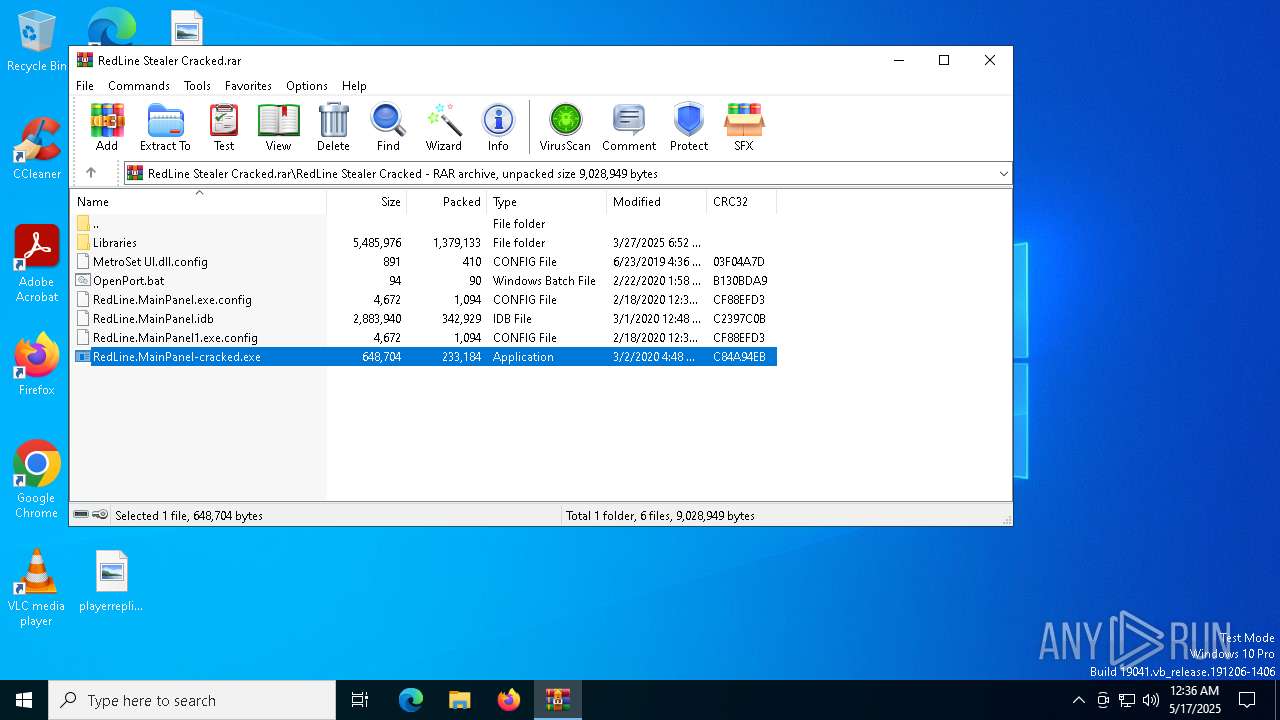
| File name: | RedLine Stealer Cracked.rar |
| Full analysis: | https://app.any.run/tasks/17476558-f8b0-44f2-a445-4cc35ff77ae0 |
| Verdict: | Malicious activity |
| Analysis date: | May 17, 2025, 00:36:36 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 4F0205E869CD5E12CD102A210443938C |
| SHA1: | 0FB7A0EA87E66D067BA159743B9363CB55F27118 |
| SHA256: | 61974B843AE371E0472ABF494817311E209D1AD9D01505537B7A58A330E19DDA |
| SSDEEP: | 98304:MEAAGglfBZhyA8jI2yFlM3cOy01MUnLD5QeBSN0Fs4FdpS4It/APNsRG9dXJJuH8:Nap |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7368)
XORed URL has been found (YARA)
- RedLine.MainPanel-cracked.exe (PID: 7668)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7368)
- RedLine.MainPanel-cracked.exe (PID: 7668)
There is functionality for taking screenshot (YARA)
- RedLine.MainPanel-cracked.exe (PID: 7668)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7368)
Checks supported languages
- RedLine.MainPanel-cracked.exe (PID: 7668)
Reads the computer name
- RedLine.MainPanel-cracked.exe (PID: 7668)
Reads the machine GUID from the registry
- RedLine.MainPanel-cracked.exe (PID: 7668)
.NET Reactor protector has been detected
- RedLine.MainPanel-cracked.exe (PID: 7668)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
xor-url
(PID) Process(7668) RedLine.MainPanel-cracked.exe
Decrypted-URLs (1)http://ip-api.com/line/?fields=hostingM~
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 24609 |
| UncompressedSize: | 34304 |
| OperatingSystem: | Win32 |
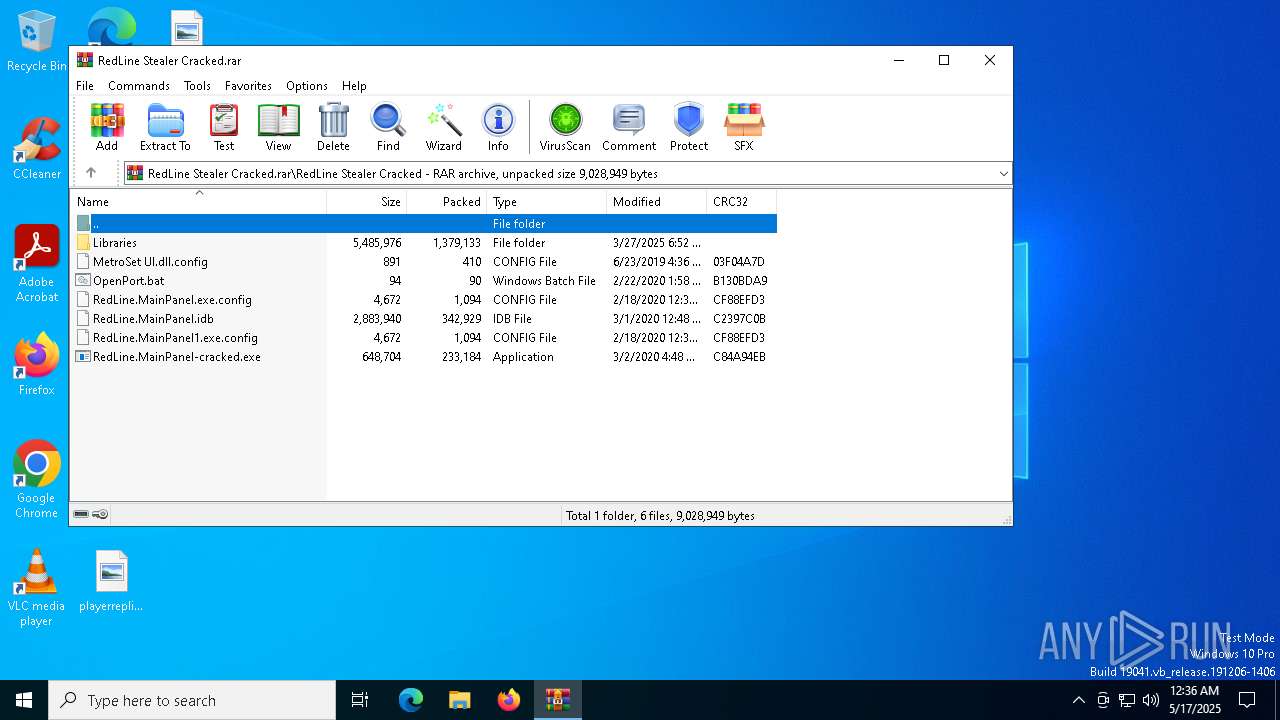
| ArchivedFileName: | RedLine Stealer Cracked/Libraries/builder.exe |
Total processes
129
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 7368 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\RedLine Stealer Cracked.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7668 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa7368.2180\RedLine Stealer Cracked\RedLine.MainPanel-cracked.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa7368.2180\RedLine Stealer Cracked\RedLine.MainPanel-cracked.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: RedLinePanel Version: 1.0.0.0 Modules
xor-url(PID) Process(7668) RedLine.MainPanel-cracked.exe Decrypted-URLs (1)http://ip-api.com/line/?fields=hostingM~ | |||||||||||||||
| 8092 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 887
Read events
3 879
Write events
8
Delete events
0
Modification events
| (PID) Process: | (7368) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7368) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7368) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7368) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\RedLine Stealer Cracked.rar | |||
| (PID) Process: | (7368) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7368) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7368) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7368) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
14
Suspicious files
7
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7368 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7368.2180\RedLine Stealer Cracked\Libraries\GuiLib.dll | executable | |
MD5:EAF9C55793CD26F133708714ED3A5397 | SHA256:87CFC70BEC2D2A37BCD5D46F9E6F0051F82E015FF96E8F2BC2D81B85F2632F15 | |||
| 7368 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7368.2180\RedLine Stealer Cracked\Libraries\links.txt | text | |
MD5:7E0B0F449C419BC5DCE0A9AE1920C00C | SHA256:2CA989920E2CD5C250BE6FB5E0EF82EE45A77F2147E91D736562C110B5EC372E | |||
| 7368 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7368.2180\RedLine Stealer Cracked\Libraries\Mono.Cecil.Mdb.pdb | binary | |
MD5:0BA762B6B5FBDA000E51D66722A3BB2C | SHA256:D18EB89421D50F079291B78783408CEE4BAB6810E4C5A4B191849265BDD5BA7C | |||
| 7368 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7368.2180\RedLine Stealer Cracked\Libraries\Bunifu_UI_v1.52.dll | executable | |
MD5:5ECA94D909F1BA4C5F3E35AC65A49076 | SHA256:DE0E530D46C803D85B8AEB6D18816F1B09CB3DAFEFB5E19FDFA15C9F41E0F474 | |||
| 7368 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7368.2180\RedLine Stealer Cracked\Libraries\Mono.Cecil.Pdb.pdb | binary | |
MD5:8E07476DB3813903E596B669D3744855 | SHA256:AA6469974D04CBA872F86E6598771663BB8721D43A4A0A2A44CF3E2CD2F1E646 | |||
| 7368 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7368.2180\RedLine Stealer Cracked\Libraries\Mono.Cecil.pdb | binary | |
MD5:C0A69F1B0C50D4F133CD0B278AC2A531 | SHA256:A4F79C99D8923BD6C30EFAFA39363C18BABE95F6609BBAD242BCA44342CCC7BB | |||
| 7368 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7368.2180\RedLine Stealer Cracked\Libraries\Mono.Cecil.Pdb.dll | executable | |
MD5:6CD3ED3DB95D4671B866411DB4950853 | SHA256:D67EBD49241041E6B6191703A90D89E68D4465ADCE02C595218B867DF34581A3 | |||
| 7368 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7368.2180\RedLine Stealer Cracked\Libraries\builder.pdb | binary | |
MD5:418DC008EF956465E179EC29D3C3C245 | SHA256:8C7E21B37540211D56C5FDBB7E731655A96945AA83F2988E33D5ADB8AA7C8DF1 | |||
| 7368 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7368.2180\RedLine Stealer Cracked\Libraries\Mono.Cecil.dll | executable | |
MD5:7546ACEBC5A5213DEE2A5ED18D7EBC6C | SHA256:7744C9C84C28033BC3606F4DFCE2ADCD6F632E2BE7827893C3E2257100F1CF9E | |||
| 7368 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7368.2180\RedLine Stealer Cracked\Libraries\stub.exe | executable | |
MD5:C2F7222E591A9D587C20486FE97AE551 | SHA256:3F63F47C4D764D332F13FAF328F73F7A205E3422D89AFA8ACD4514912A556037 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
19
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7920 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7920 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4024 | RUXIMICS.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |