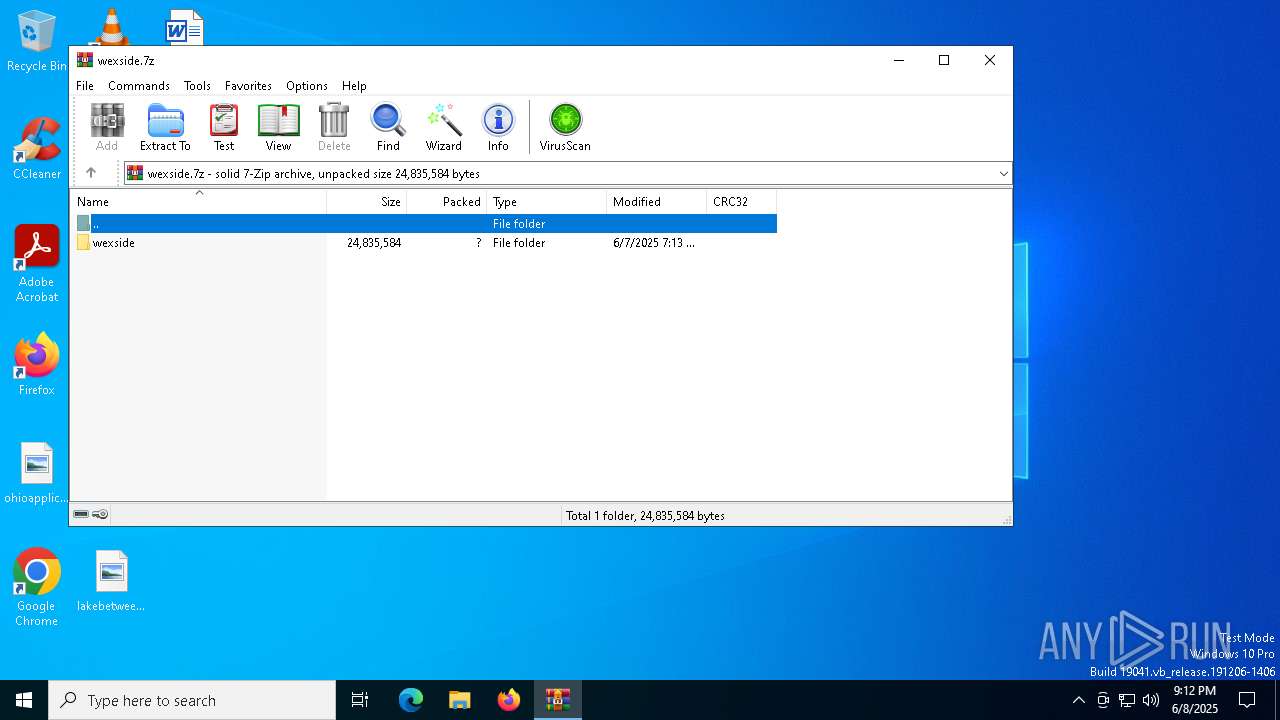
| File name: | wexside.7z |
| Full analysis: | https://app.any.run/tasks/fd5aeb39-553f-4ee0-b498-8c4ca155746c |
| Verdict: | Malicious activity |
| Analysis date: | June 08, 2025, 21:12:01 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 8088769807AEFF388BDA19A6EBBD01ED |
| SHA1: | 34C262059F403B71047AFD9ABBEA3011E46606E0 |
| SHA256: | 617C5C6636536AECC37054205687A4044F9BD17345A71C558A42218609C74CCA |
| SSDEEP: | 196608:p9OmpIsnhcHO4XPuPRNgrZ5qsGcV9Ga/jRqnzXWHTfoIR8M:vGouOWPQzgrmmd9qzX2N2M |
MALICIOUS
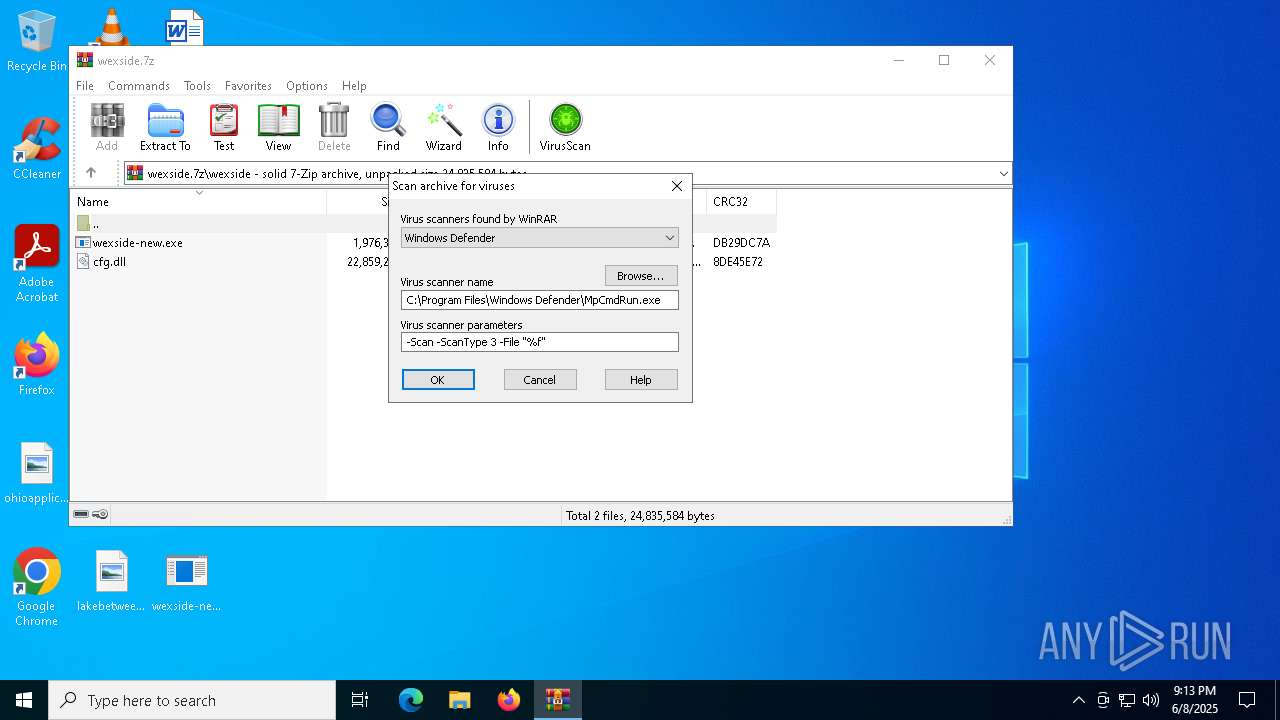
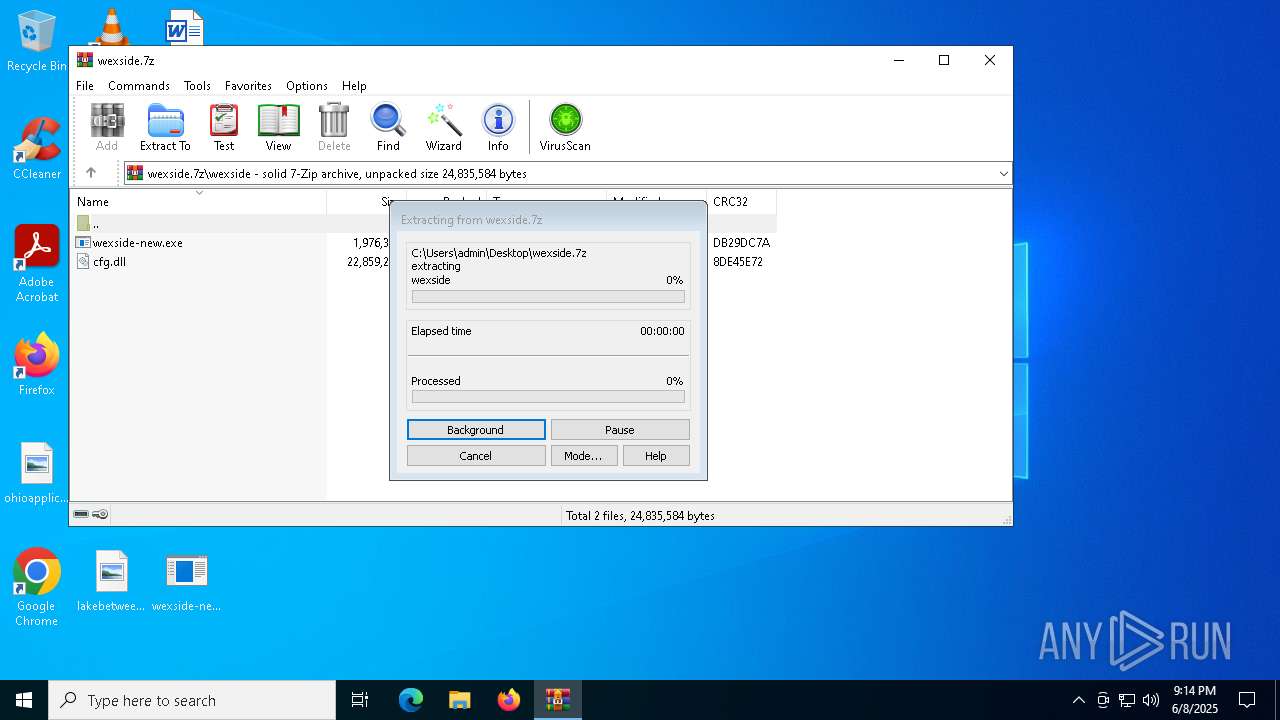
Generic archive extractor
- WinRAR.exe (PID: 7048)
SUSPICIOUS
Executes application which crashes
- MSBuild.exe (PID: 7000)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 7048)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7048)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 7048)
INFO
Reads the computer name
- MSBuild.exe (PID: 7000)
- MpCmdRun.exe (PID: 8044)
Checks supported languages
- MSBuild.exe (PID: 7000)
- wexside-new.exe (PID: 6248)
- MpCmdRun.exe (PID: 8044)
Reads the machine GUID from the registry
- MSBuild.exe (PID: 7000)
Manual execution by a user
- wexside-new.exe (PID: 6248)
Creates files or folders in the user directory
- WerFault.exe (PID: 1852)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7048)
Create files in a temporary directory
- MpCmdRun.exe (PID: 8044)
Reads the software policy settings
- slui.exe (PID: 5624)
Checks proxy server information
- slui.exe (PID: 5624)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2025:06:07 07:13:40+00:00 |
| ArchivedFileName: | wexside |
Total processes
129
Monitored processes
9
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1852 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 7000 -s 856 | C:\Windows\SysWOW64\WerFault.exe | — | MSBuild.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5124 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | wexside-new.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5624 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6248 | "C:\Users\admin\Desktop\wexside-new.exe" | C:\Users\admin\Desktop\wexside-new.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6876 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR7048.5688\Rar$Scan110766.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7000 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | wexside-new.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Exit code: 3221225477 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 7048 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\wexside.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7224 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8044 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR7048.5688" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
6 797
Read events
6 787
Write events
10
Delete events
0
Modification events
| (PID) Process: | (7048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\wexside.7z | |||
| (PID) Process: | (7048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList |
| Operation: | write | Name: | ArcSort |
Value: 32 | |||
| (PID) Process: | (7048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\VirusScan |
| Operation: | write | Name: | DefScanner |
Value: Windows Defender | |||
Executable files
2
Suspicious files
1
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1852 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_MSBuild.exe_d6d361fb51dc191b263f33ce496b8bf9d4dec4_59a9f4ae_d9ba8949-9838-4213-b912-f714e3b43468\Report.wer | — | |
MD5:— | SHA256:— | |||
| 1852 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\MSBuild.exe.7000.dmp | — | |
MD5:— | SHA256:— | |||
| 7048 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7048.5688\wexside.7z\wexside\wexside-new.exe | executable | |
MD5:8F26514A5E46FD9AEB0E3762C2BA5198 | SHA256:116053DDEE75E67C04DA90BD19202DA3D2A47F189C47A4126E248A5E3F6A6B91 | |||
| 1852 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER3C17.tmp.dmp | binary | |
MD5:2B322019675C62F79210FFEBC77E5C09 | SHA256:9134E1D9D7D47C2075D3A95D2AD296CB85D089BF912A77162DAC0009CADF3756 | |||
| 1852 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER3D02.tmp.WERInternalMetadata.xml | xml | |
MD5:A337226EC84551BC31E9ABE3E5EB8A0D | SHA256:F789D14BD9C18B423EF9A05334F1F92FD49359BFA03326FE6B1CBB6CC22353A5 | |||
| 7048 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7048.5688\wexside.7z\wexside\cfg.dll | executable | |
MD5:92D8E195ADDD7C6AE9589311D9DDFE46 | SHA256:95E62B3EE2A56D9661E5401148B9A7617E1AF252A5F20915A527ECB9698DE510 | |||
| 8044 | MpCmdRun.exe | C:\Users\admin\AppData\Local\Temp\MpCmdRun.log | text | |
MD5:947E7A2624D063CD59CD15C84DA02926 | SHA256:9F204095C930937B2E794C04D65349097B57B7E74C4A533953356FA5628BB32D | |||
| 1852 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER3D22.tmp.xml | xml | |
MD5:58853AD9F4D795C0717257DB5D38CD09 | SHA256:63B296294A88037A61EF5984F2E07D47FF522D39EBAE01435C5D8BC616306191 | |||
| 7048 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7048.5688\Rar$Scan110766.bat | text | |
MD5:6AFA3E5334D25768A804AA236FBB3385 | SHA256:CB21E458F414F4B51D7239562EC75999CB8246F4E379A1D606323E031052FD82 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
20
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.38:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 23.216.77.38:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
7320 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5624 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |