| File name: | Free Exm Tweaking Utility 2.2.bat |
| Full analysis: | https://app.any.run/tasks/32aa53dc-d6b3-4b7e-956e-24b90e8fe1d4 |
| Verdict: | Malicious activity |
| Analysis date: | January 27, 2024, 17:17:06 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, UTF-8 Unicode text, with very long lines, with CRLF line terminators, with escape sequences |
| MD5: | BF7CB2306FD90460E2E31E6C6C2E575A |
| SHA1: | 4E248D3565AE99D8E6E664AF500C051410F329BA |
| SHA256: | 61703295DBDFCF01C617B21FA71655A950F6F3E481DE04B3AFEA81C261E4FC40 |
| SSDEEP: | 768:33rEb6K/v9zqsaIZz+Q+FW5/PJzUhNVAC51qpfUqPqoYXpM:U/v5rzUhNVn1qypM |
MALICIOUS
Changes powershell execution policy (Unrestricted)
- cmd.exe (PID: 2640)
- cmd.exe (PID: 2176)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 2640)
- cmd.exe (PID: 2176)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 2640)
- cmd.exe (PID: 2176)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2640)
- cmd.exe (PID: 2176)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 2640)
- cmd.exe (PID: 2176)
Starts application with an unusual extension
- cmd.exe (PID: 2640)
- cmd.exe (PID: 2176)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 1824)
Executing commands from a ".bat" file
- powershell.exe (PID: 1824)
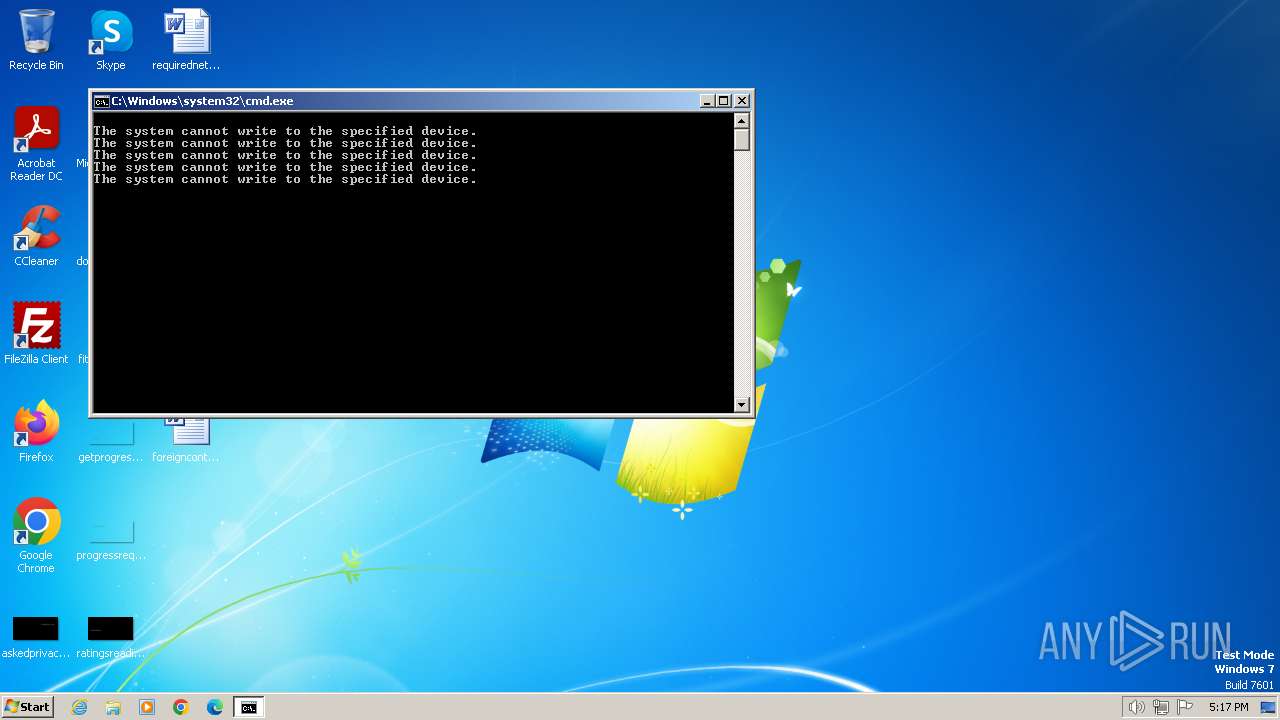
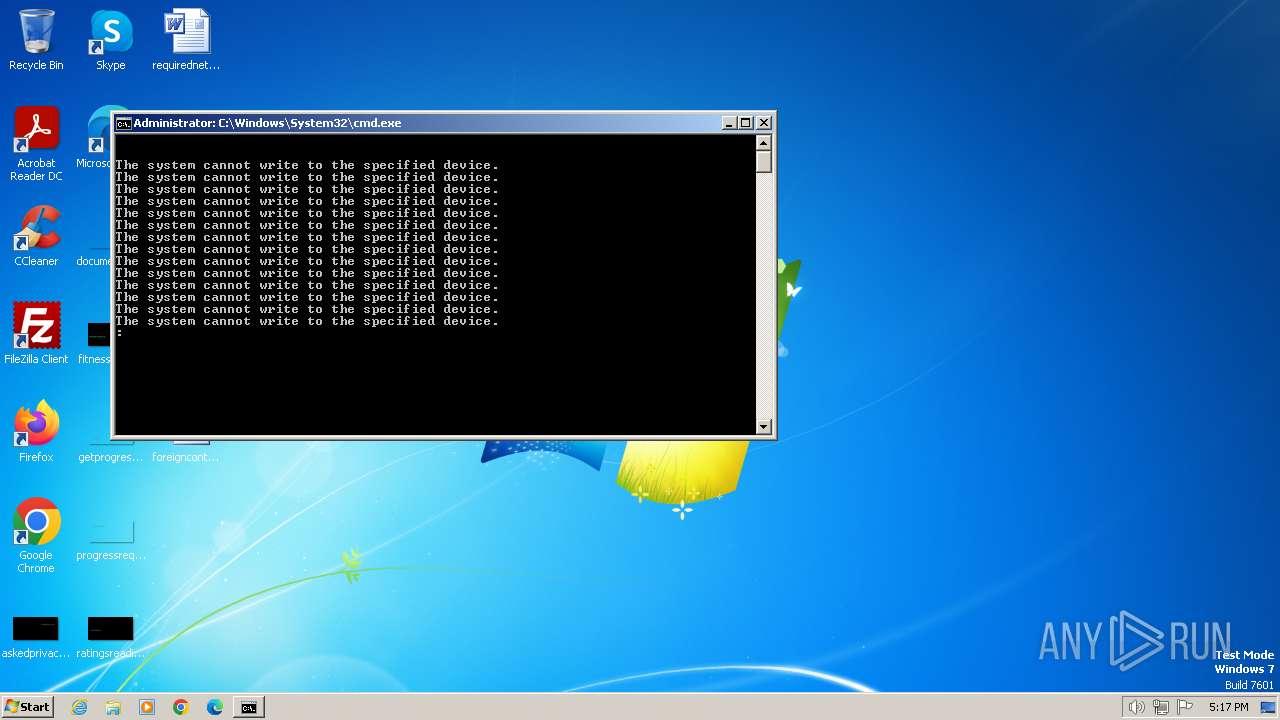
The process hide an interactive prompt from the user
- cmd.exe (PID: 2640)
Reads the Internet Settings
- powershell.exe (PID: 1824)
INFO
Checks supported languages
- chcp.com (PID: 2316)
- chcp.com (PID: 3076)
- chcp.com (PID: 2380)
- chcp.com (PID: 2784)
- chcp.com (PID: 2728)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
63
Monitored processes
22
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 884 | powershell -ExecutionPolicy Unrestricted -NoProfile Enable-ComputerRestore -Drive 'C:\' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1268 | Reg.exe delete "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRestore" /v "DisableConfig" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1556 | Reg.exe add "HKCU\CONSOLE" /v "VirtualTerminalLevel" /t REG_DWORD /d "1" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1824 | powershell -NoProfile -NonInteractive -Command start -verb runas "'C:\Users\admin\AppData\Local\Temp\FREEEX~1.BAT'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2060 | timeout /t 1 /nobreak | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2176 | "C:\Windows\System32\cmd.exe" /C "C:\Users\admin\AppData\Local\Temp\FREEEX~1.BAT" | C:\Windows\System32\cmd.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2240 | Reg.exe add "HKLM\Software\Microsoft\Windows NT\CurrentVersion\SystemRestore" /v "SystemRestorePointCreationFrequency" /t REG_DWORD /d 0 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2316 | chcp 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2376 | Reg.exe delete "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRestore" /v "RPSessionInterval" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2380 | chcp 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Change CodePage Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 464
Read events
2 452
Write events
11
Delete events
1
Modification events
| (PID) Process: | (1824) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1824) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1824) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1824) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3040) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP\Clients |
| Operation: | write | Name: | {09F7EDC5-294E-4180-AF6A-FB0E6A0E9513} |
Value: \\?\Volume{e1a82db4-a9f0-11e7-b142-806e6f6e6963}\:(C%3A) | |||
| (PID) Process: | (2376) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRestore |
| Operation: | delete value | Name: | RPSessionInterval |
Value: 1 | |||
| (PID) Process: | (2508) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRestore |
| Operation: | write | Name: | SystemRestorePointCreationFrequency |
Value: 0 | |||
| (PID) Process: | (3136) reg.exe | Key: | HKEY_CURRENT_USER\Console |
| Operation: | write | Name: | VirtualTerminalLevel |
Value: 1 | |||
Executable files
0
Suspicious files
7
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 884 | powershell.exe | C:\Users\admin\AppData\Local\Temp\gvmlstbu.fhn.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2396 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | dbf | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
| 2396 | powershell.exe | C:\Users\admin\AppData\Local\Temp\kndtmgri.3ov.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1824 | powershell.exe | C:\Users\admin\AppData\Local\Temp\t5wvuxxk.uzq.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2396 | powershell.exe | C:\Users\admin\AppData\Local\Temp\b1fhstok.nka.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 884 | powershell.exe | C:\Users\admin\AppData\Local\Temp\qancyieq.bbb.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1824 | powershell.exe | C:\Users\admin\AppData\Local\Temp\j4eq3vzh.hr0.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |