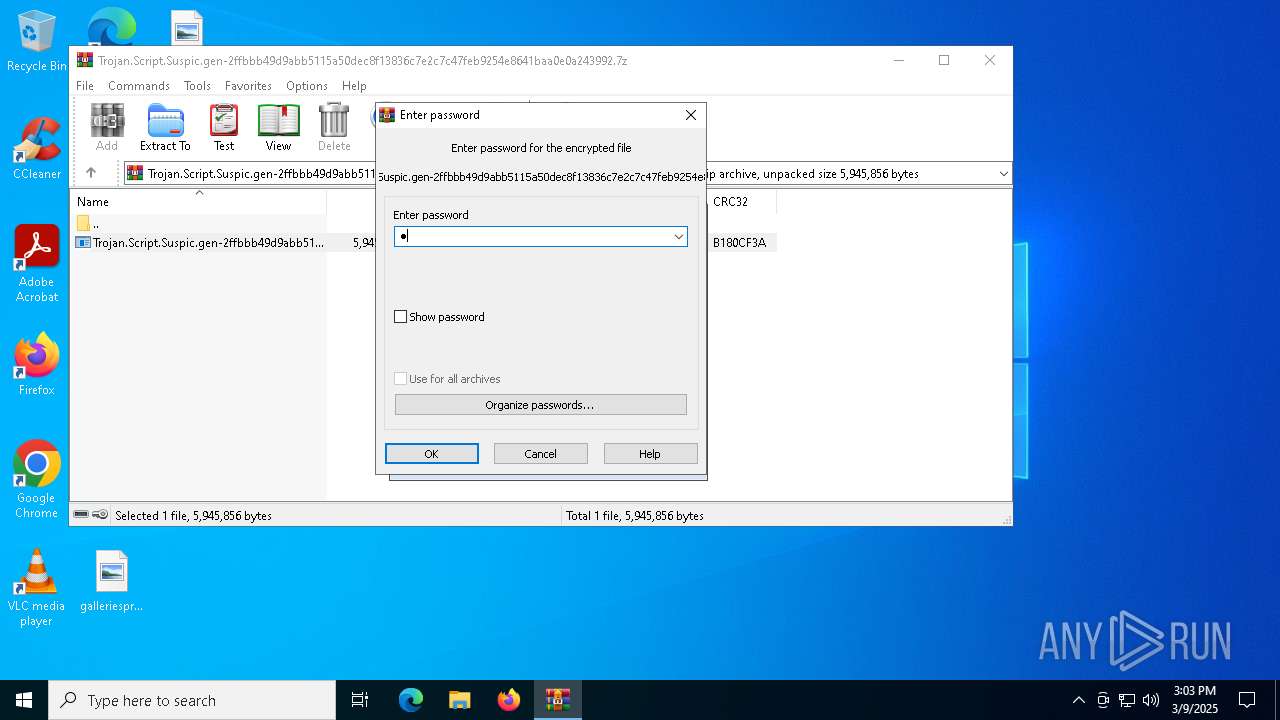
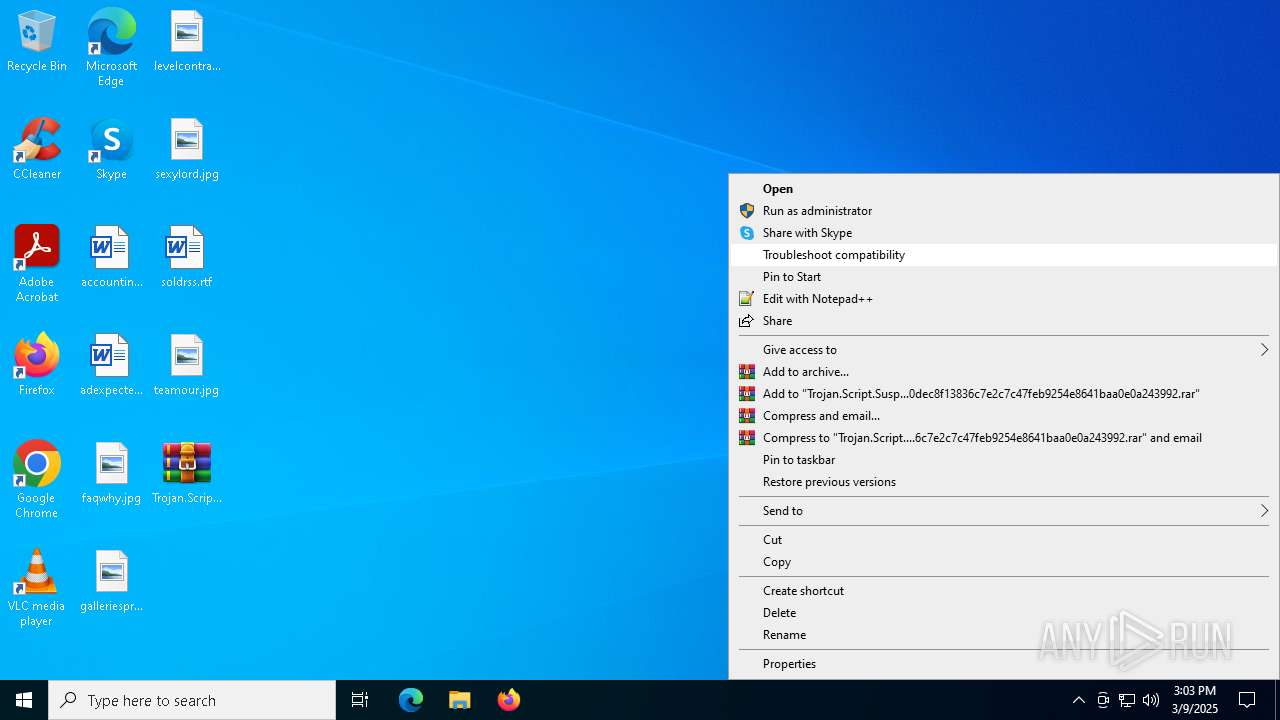
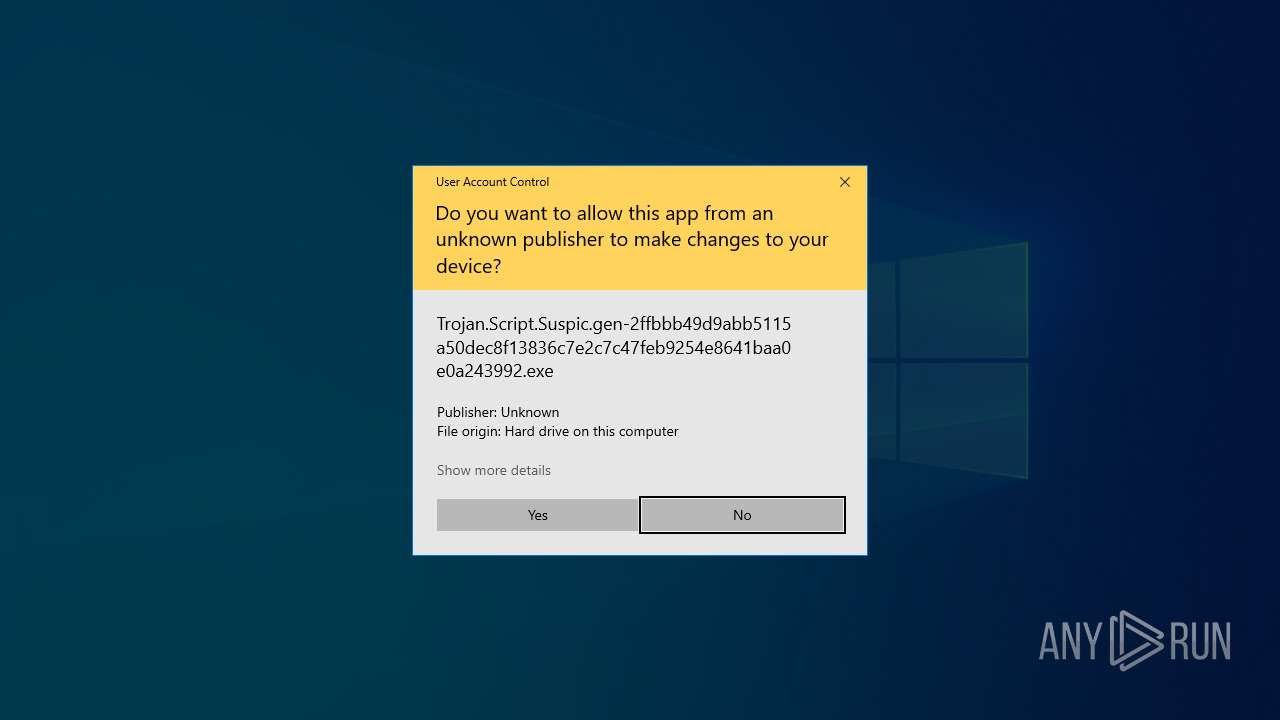
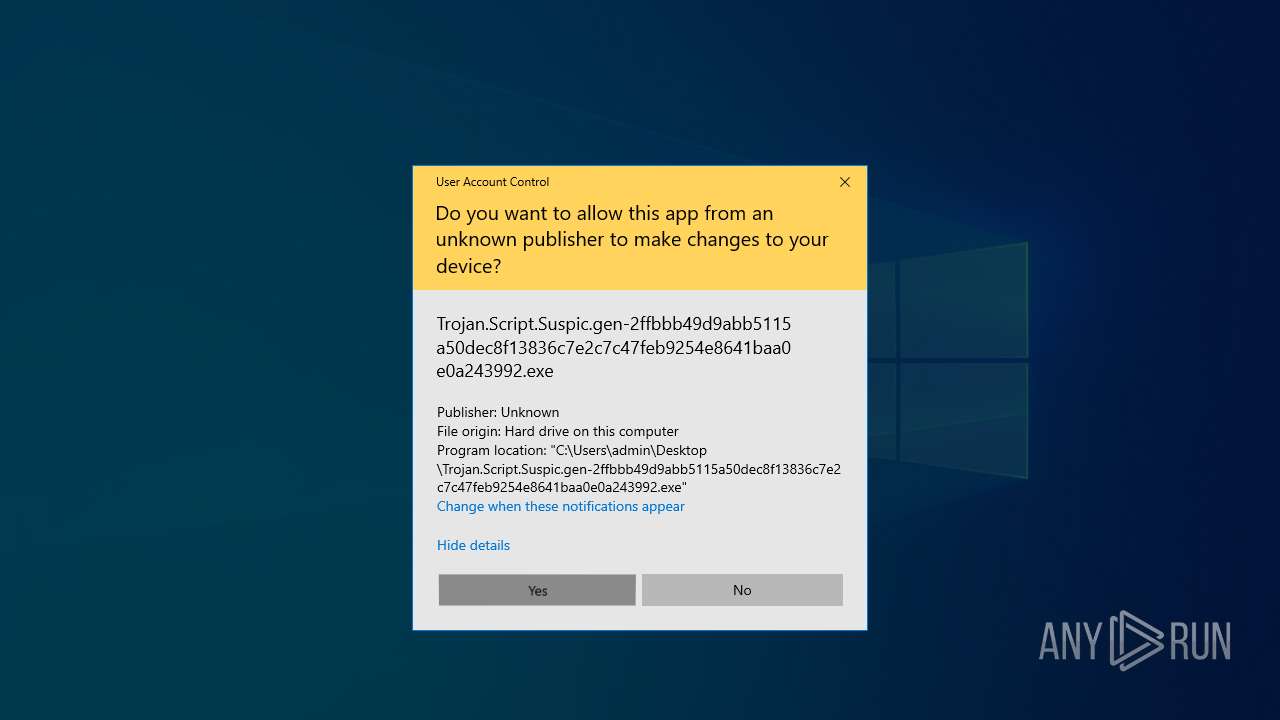
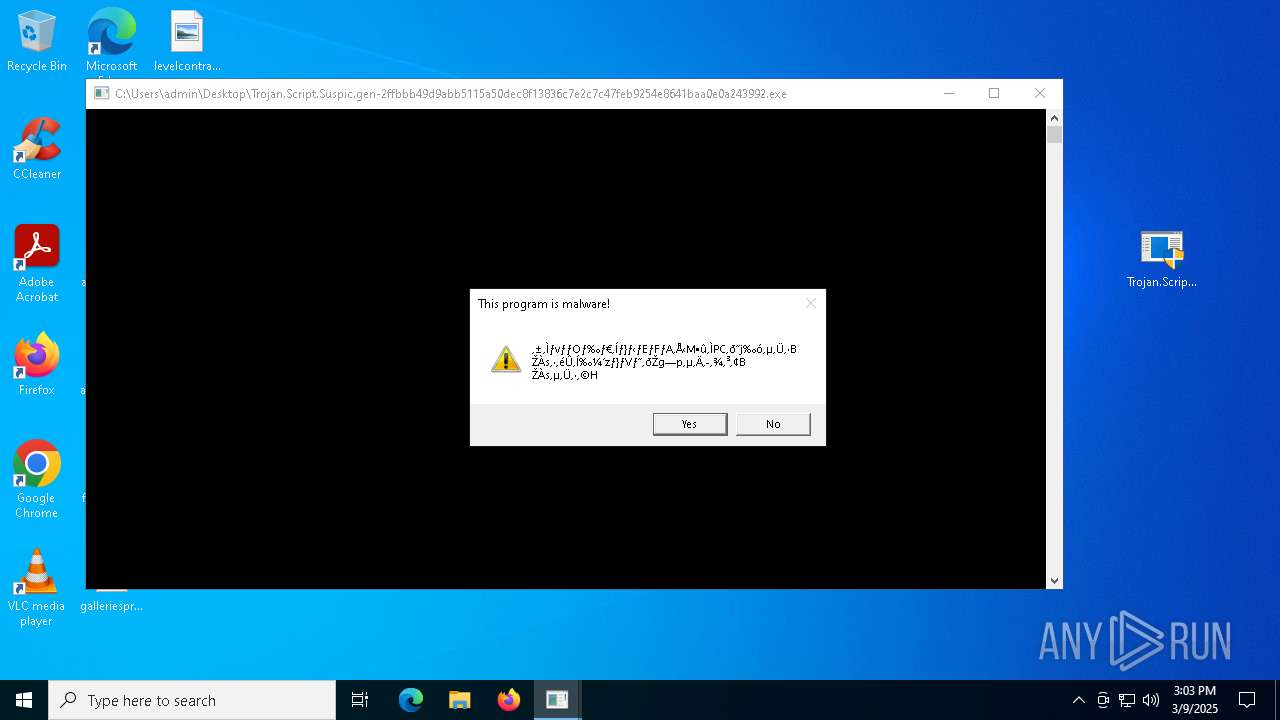
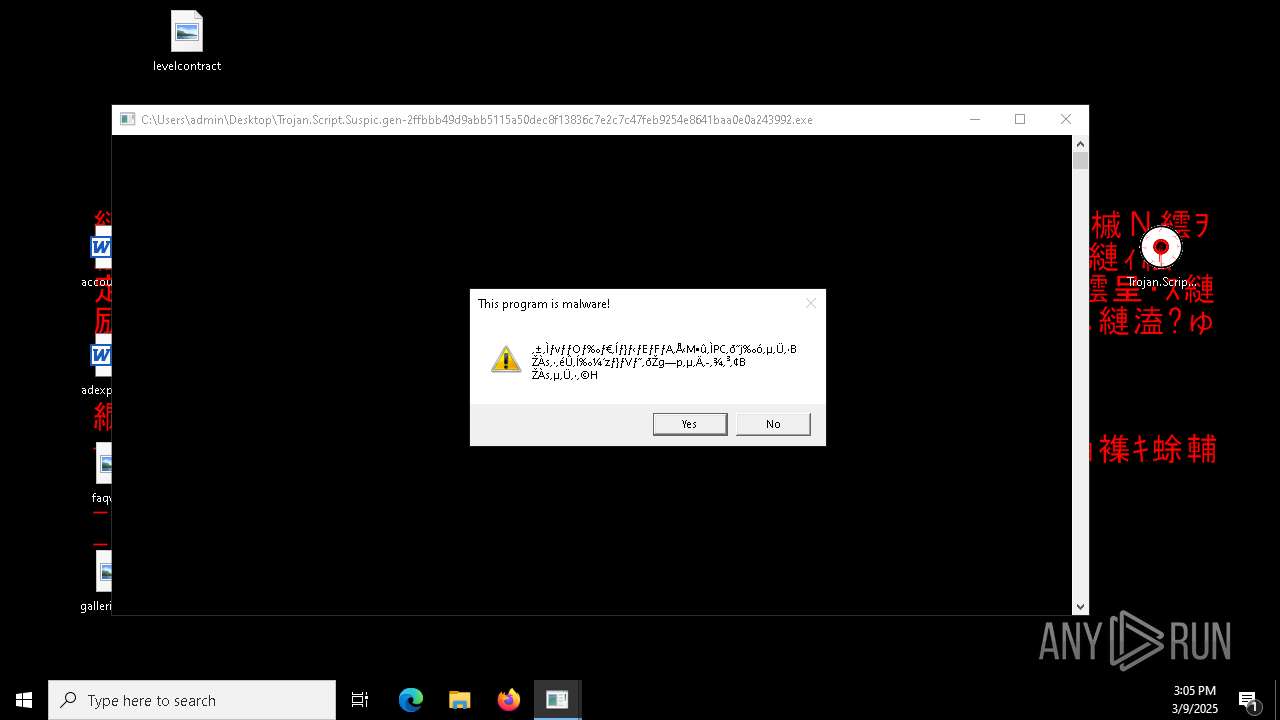
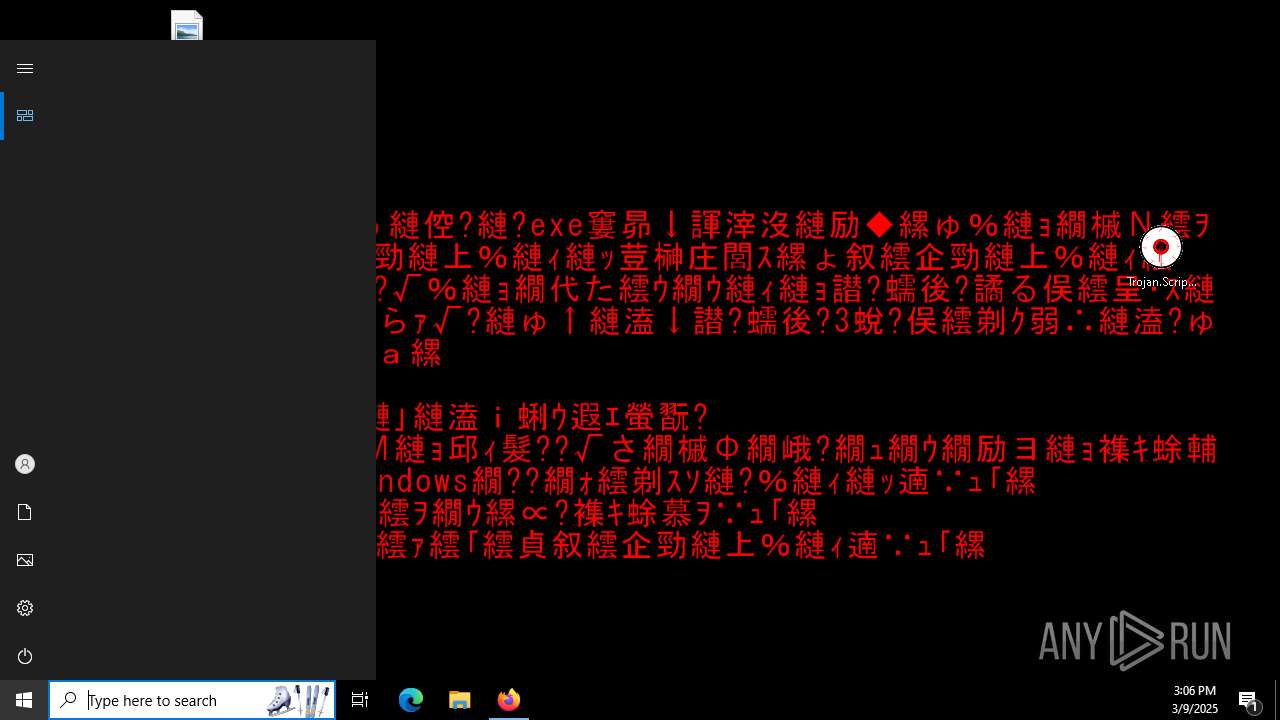
| File name: | Trojan.Script.Suspic.gen-2ffbbb49d9abb5115a50dec8f13836c7e2c7c47feb9254e8641baa0e0a243992.7z |
| Full analysis: | https://app.any.run/tasks/7b4e9010-0d92-40e3-a034-aed92724e19d |
| Verdict: | Malicious activity |
| Analysis date: | March 09, 2025, 15:03:38 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | A0396911CA029034DBBCA508AC35F98E |
| SHA1: | 403E0D66295D16E209167BD55F51066397889DD1 |
| SHA256: | 615580558EBD65AF9257FACE92474E78A0B3BF5EA0F1725DED5A0EB239FBAF4C |
| SSDEEP: | 49152:ePG/VORsm5/SaxezAWyuQtNjJj7q0u1bMrsc8l9WpydCre1LCJZxKUQEhpoDqfuJ:ePGsOmZScezAZ17YyQcc9W8dCre9Cn9Q |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 720)
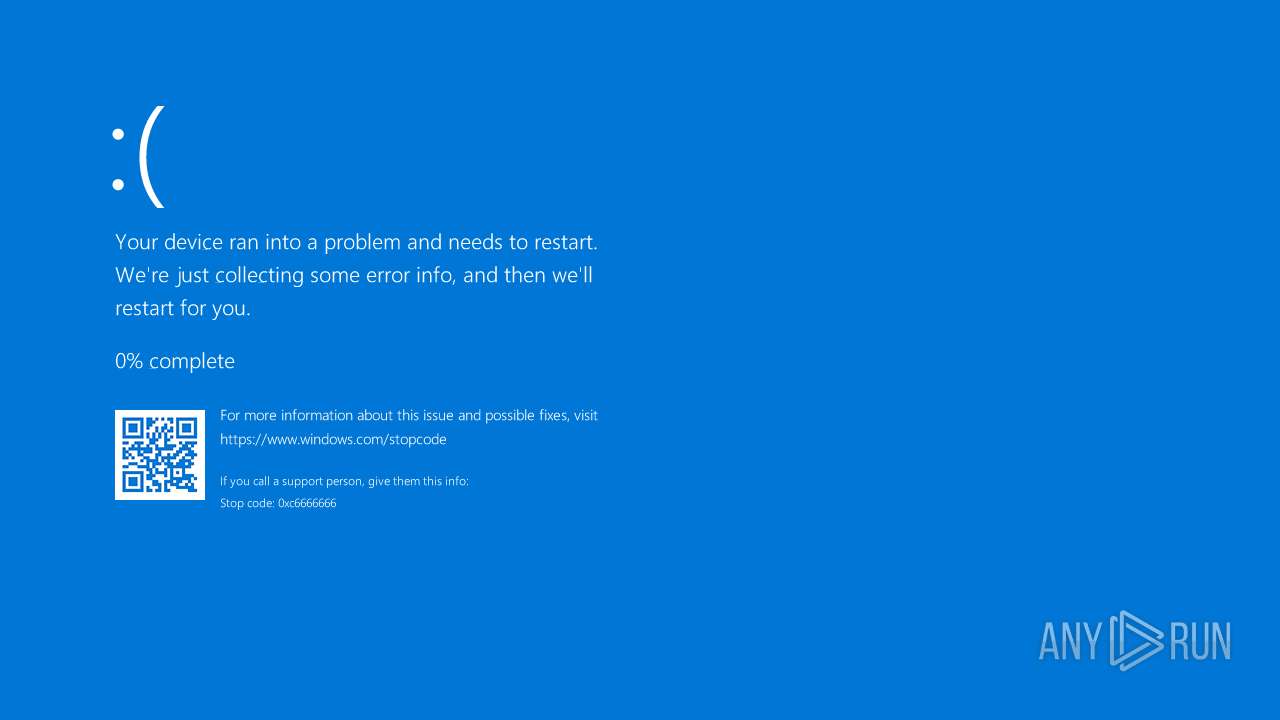
Starts REAGENTC.EXE to disable the Windows Recovery Environment
- ReAgentc.exe (PID: 2108)
Changes powershell execution policy (Unrestricted)
- cmd.exe (PID: 4268)
Uses TASKKILL.EXE to kill security tools
- cmd.exe (PID: 4268)
Disables the Run the Start menu
- checker.exe (PID: 5740)
Disables the LogOff the Start menu
- checker.exe (PID: 5740)
Disables the Shutdown in the Start menu
- checker.exe (PID: 5740)
Disables Windows Defender
- checker.exe (PID: 5740)
Modify registry editing tools (regedit)
- checker.exe (PID: 5740)
Changes appearance of the Explorer extensions
- checker.exe (PID: 5740)
Disables task manager
- checker.exe (PID: 5740)
Disables the Find the Start menu
- checker.exe (PID: 5740)
Task Manager has been disabled (taskmgr)
- checker.exe (PID: 5740)
UAC/LUA settings modification
- checker.exe (PID: 5740)
Changes the autorun value in the registry
- checker.exe (PID: 5740)
- ie4uinit.exe (PID: 7540)
SUSPICIOUS
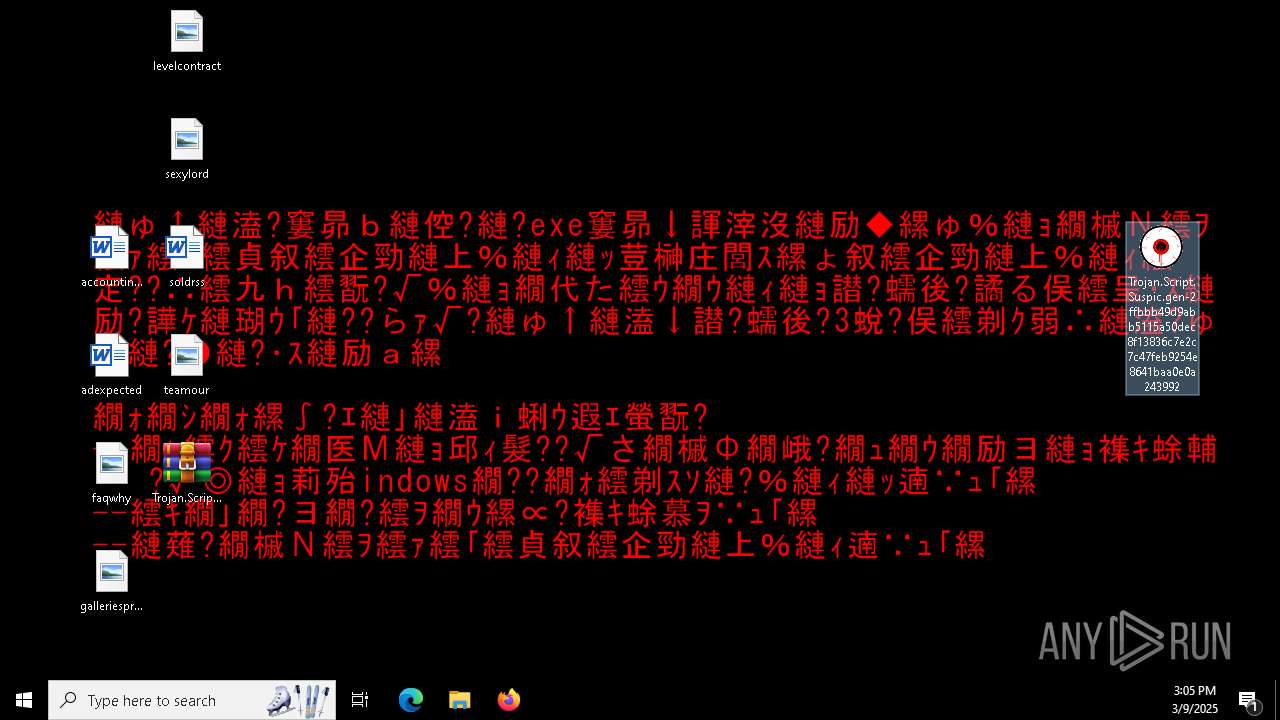
Write to the desktop.ini file (may be used to cloak folders)
- Trojan.Script.Suspic.gen-2ffbbb49d9abb5115a50dec8f13836c7e2c7c47feb9254e8641baa0e0a243992.exe (PID: 2552)
- ie4uinit.exe (PID: 7540)
Reads security settings of Internet Explorer
- Trojan.Script.Suspic.gen-2ffbbb49d9abb5115a50dec8f13836c7e2c7c47feb9254e8641baa0e0a243992.exe (PID: 2552)
- ShellExperienceHost.exe (PID: 5112)
Starts CMD.EXE for commands execution
- checker.exe (PID: 5740)
Executing commands from a ".bat" file
- checker.exe (PID: 5740)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 4268)
Executing commands from ".cmd" file
- checker.exe (PID: 5740)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 4268)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 4268)
Uses WMIC.EXE to obtain user accounts information
- cmd.exe (PID: 4268)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 4268)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 4268)
The process executes Powershell scripts
- cmd.exe (PID: 4268)
Uses TASKKILL.EXE to kill Browsers
- cmd.exe (PID: 4268)
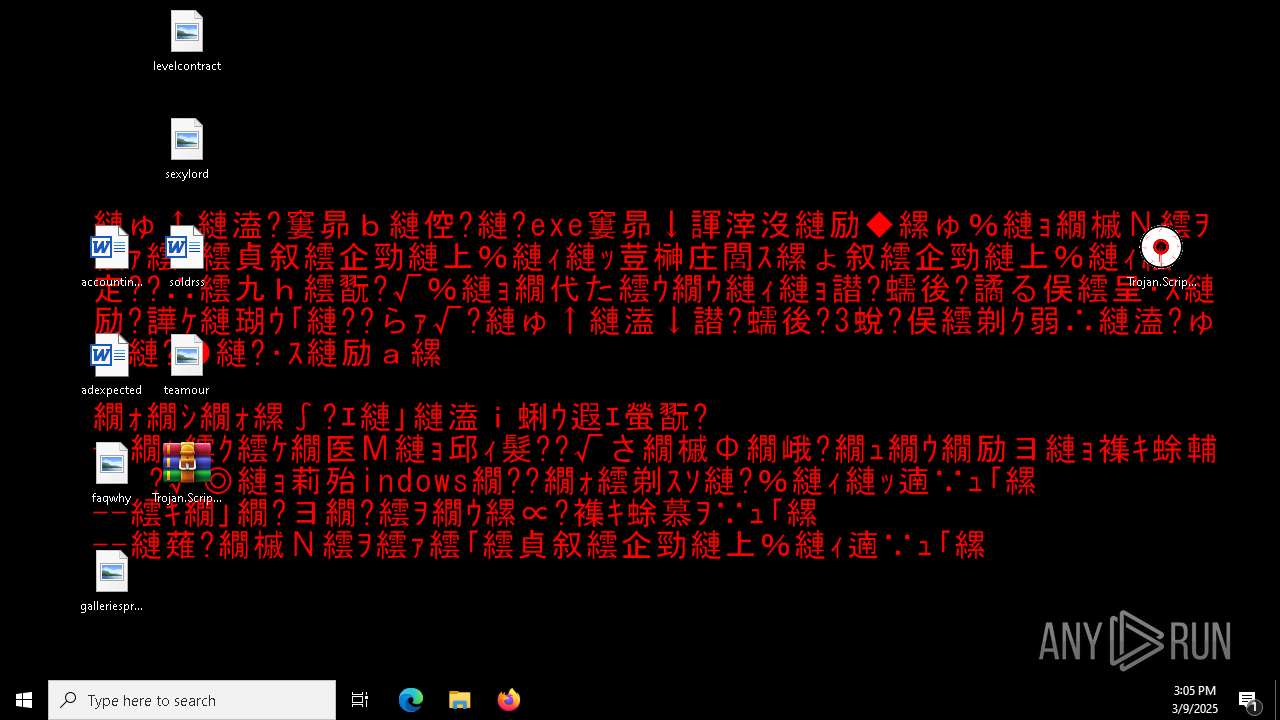
Changes the desktop background image
- checker.exe (PID: 5740)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 2732)
- PLUGScheduler.exe (PID: 680)
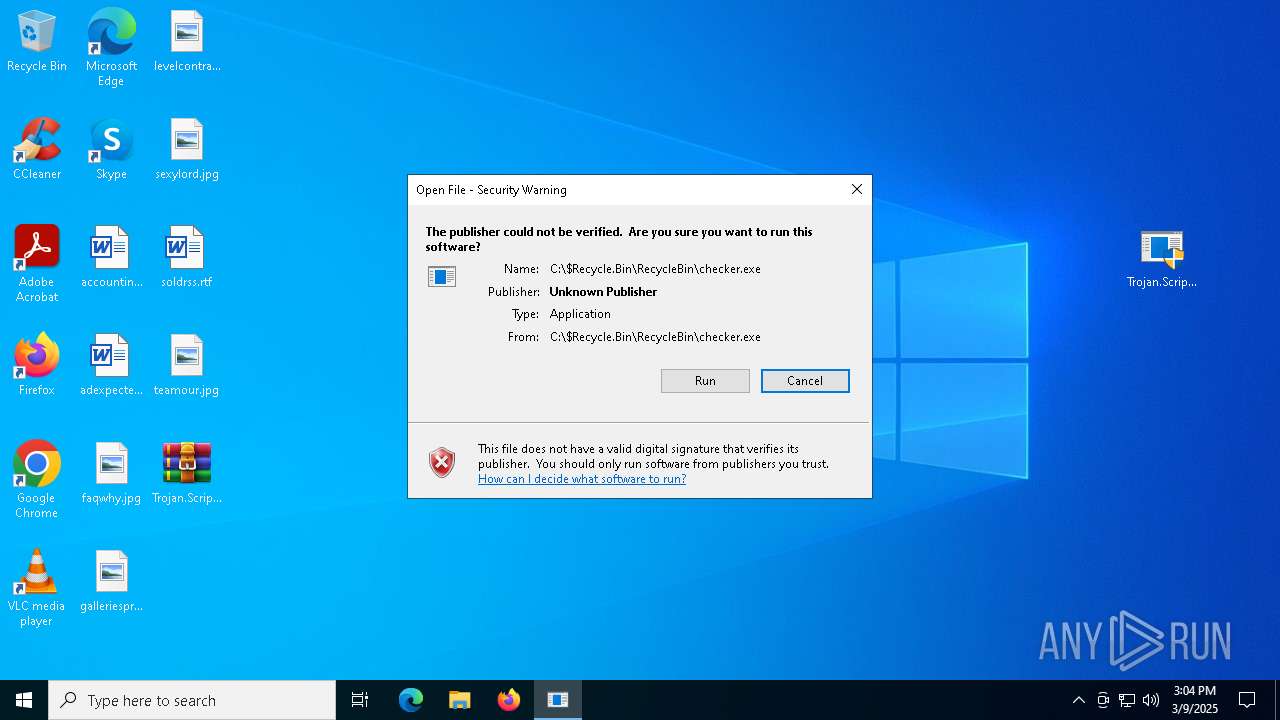
Executable content was dropped or overwritten
- Trojan.Script.Suspic.gen-2ffbbb49d9abb5115a50dec8f13836c7e2c7c47feb9254e8641baa0e0a243992.exe (PID: 2552)
Reads Microsoft Outlook installation path
- FirstLogonAnim.exe (PID: 7308)
Application launched itself
- ie4uinit.exe (PID: 7540)
Changes internet zones settings
- ie4uinit.exe (PID: 7540)
Uses RUNDLL32.EXE to load library
- ie4uinit.exe (PID: 7604)
Reads Internet Explorer settings
- FirstLogonAnim.exe (PID: 7308)
INFO
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 6028)
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 6028)
- BackgroundTransferHost.exe (PID: 6392)
- BackgroundTransferHost.exe (PID: 4024)
- BackgroundTransferHost.exe (PID: 4408)
- WMIC.exe (PID: 6512)
- BackgroundTransferHost.exe (PID: 6644)
- FirstLogonAnim.exe (PID: 7308)
- ie4uinit.exe (PID: 7540)
- ie4uinit.exe (PID: 7604)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 720)
- firefox.exe (PID: 6608)
Manual execution by a user
- Trojan.Script.Suspic.gen-2ffbbb49d9abb5115a50dec8f13836c7e2c7c47feb9254e8641baa0e0a243992.exe (PID: 2552)
- firefox.exe (PID: 6588)
- Trojan.Script.Suspic.gen-2ffbbb49d9abb5115a50dec8f13836c7e2c7c47feb9254e8641baa0e0a243992.exe (PID: 6120)
- FirstLogonAnim.exe (PID: 7308)
- unregmp2.exe (PID: 7496)
- ie4uinit.exe (PID: 7540)
Reads the machine GUID from the registry
- Trojan.Script.Suspic.gen-2ffbbb49d9abb5115a50dec8f13836c7e2c7c47feb9254e8641baa0e0a243992.exe (PID: 2552)
Process checks computer location settings
- Trojan.Script.Suspic.gen-2ffbbb49d9abb5115a50dec8f13836c7e2c7c47feb9254e8641baa0e0a243992.exe (PID: 2552)
Reads the computer name
- Trojan.Script.Suspic.gen-2ffbbb49d9abb5115a50dec8f13836c7e2c7c47feb9254e8641baa0e0a243992.exe (PID: 2552)
- checker.exe (PID: 5740)
- ShellExperienceHost.exe (PID: 5112)
- PLUGScheduler.exe (PID: 2732)
- Trojan.Script.Suspic.gen-2ffbbb49d9abb5115a50dec8f13836c7e2c7c47feb9254e8641baa0e0a243992.exe (PID: 6120)
- PLUGScheduler.exe (PID: 680)
Checks supported languages
- checker.exe (PID: 5740)
- Trojan.Script.Suspic.gen-2ffbbb49d9abb5115a50dec8f13836c7e2c7c47feb9254e8641baa0e0a243992.exe (PID: 2552)
- ShellExperienceHost.exe (PID: 5112)
- PLUGScheduler.exe (PID: 2732)
- Trojan.Script.Suspic.gen-2ffbbb49d9abb5115a50dec8f13836c7e2c7c47feb9254e8641baa0e0a243992.exe (PID: 6120)
- PLUGScheduler.exe (PID: 680)
Changes file name
- cmd.exe (PID: 4268)
Checks proxy server information
- BackgroundTransferHost.exe (PID: 6028)
Reads the software policy settings
- BackgroundTransferHost.exe (PID: 6028)
Application launched itself
- firefox.exe (PID: 6608)
- firefox.exe (PID: 6588)
Local mutex for internet shortcut management
- ie4uinit.exe (PID: 7540)
Creates files in the program directory
- ie4uinit.exe (PID: 7540)
- PLUGScheduler.exe (PID: 680)
- PLUGScheduler.exe (PID: 2732)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2021:10:26 12:11:30+00:00 |
| ArchivedFileName: | Trojan.Script.Suspic.gen-2ffbbb49d9abb5115a50dec8f13836c7e2c7c47feb9254e8641baa0e0a243992.exe |
Total processes
371
Monitored processes
50
Malicious processes
6
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 536 | taskkill /f /im processhacker.exe | C:\Windows\SysWOW64\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 668 | taskkill /f /im edge.exe | C:\Windows\SysWOW64\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 680 | "C:\Program Files\RUXIM\PLUGscheduler.exe" | C:\Program Files\RUXIM\PLUGScheduler.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Update LifeCycle Component Scheduler Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 720 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Trojan.Script.Suspic.gen-2ffbbb49d9abb5115a50dec8f13836c7e2c7c47feb9254e8641baa0e0a243992.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 728 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 988 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5852 -childID 5 -isForBrowser -prefsHandle 5608 -prefMapHandle 5612 -prefsLen 31144 -prefMapSize 244583 -jsInitHandle 1492 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {059e618c-c636-4347-bddf-dea1cdb3dc9e} 6608 "\\.\pipe\gecko-crash-server-pipe.6608" 224e21f6150 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 1124 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5184 -parentBuildID 20240213221259 -sandboxingKind 0 -prefsHandle 4492 -prefMapHandle 5248 -prefsLen 36588 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {ff101594-444e-4138-a4c0-605cfbb95295} 6608 "\\.\pipe\gecko-crash-server-pipe.6608" 224e0442110 utility | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 1568 | reg add HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\PowerShell /v EnableScripts /t REG_DWORD /d 1 | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2108 | reagentc /disable | C:\Windows\SysWOW64\ReAgentc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Windows Recovery Agent Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2236 | taskkill /f /im taskmgr.exe | C:\Windows\SysWOW64\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
22 524
Read events
20 694
Write events
1 751
Delete events
79
Modification events
| (PID) Process: | (720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Trojan.Script.Suspic.gen-2ffbbb49d9abb5115a50dec8f13836c7e2c7c47feb9254e8641baa0e0a243992.7z | |||
| (PID) Process: | (720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6644) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
Executable files
18
Suspicious files
253
Text files
51
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6028 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\4d78eacd-aced-45fc-b47c-95b069f991a0.down_data | — | |
MD5:— | SHA256:— | |||
| 2108 | ReAgentc.exe | C:\Windows\SysWOW64\Recovery\Winre.wim | — | |
MD5:— | SHA256:— | |||
| 6028 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\MetaData\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:201CD3D6B71BE2C61A6F661C2966166A | SHA256:DACCC1D30D043353B45AEB640E5FEA372001EE4BF1624FBD01048714A816753B | |||
| 6028 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\Content\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:AD65BBA990E9A146C8789184B44B3332 | SHA256:C57BBFD31CE81C873E766C5DEEE854B02BFF08020DF9BE1A3B4562BD67CC932D | |||
| 720 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb720.43563\Trojan.Script.Suspic.gen-2ffbbb49d9abb5115a50dec8f13836c7e2c7c47feb9254e8641baa0e0a243992.exe | executable | |
MD5:BA7BFCE093BEB93702BBC7270D90E9AB | SHA256:2FFBBB49D9ABB5115A50DEC8F13836C7E2C7C47FEB9254E8641BAA0E0A243992 | |||
| 2552 | Trojan.Script.Suspic.gen-2ffbbb49d9abb5115a50dec8f13836c7e2c7c47feb9254e8641baa0e0a243992.exe | C:\Windows\Windows10UpgradeComponents\bsod666.exe | executable | |
MD5:48DA298539D917790100DC75DB1873D6 | SHA256:FC7EDF0E4234974BB84D3075AA853C4F4950CA916888F467130D929F275CFF22 | |||
| 2552 | Trojan.Script.Suspic.gen-2ffbbb49d9abb5115a50dec8f13836c7e2c7c47feb9254e8641baa0e0a243992.exe | C:\Windows\Windows10UpgradeComponents\activemelt.exe | executable | |
MD5:6DDE2D5D965D69D6E3C955EA4A6603B8 | SHA256:15A37D4178113A830237DFA1206C3E98A9DBFF8A5F9ED61917A3BAA92EC4AF9B | |||
| 2552 | Trojan.Script.Suspic.gen-2ffbbb49d9abb5115a50dec8f13836c7e2c7c47feb9254e8641baa0e0a243992.exe | C:\Windows\Windows10UpgradeComponents\popup.exe | executable | |
MD5:B2DDA34BDC2B413796C7C275B2595DAB | SHA256:5E9DA3B067BFD512A654706AD2CF1B649CE1F847246552DAE3C66ADEF5C9C2FA | |||
| 6028 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\4c6e95a5-3d92-4b4b-a5f3-6966f131ddcc.97655a97-6990-401a-8f05-0421eea8bbaa.down_meta | binary | |
MD5:6946EAD3D97DF5569AFE82005E95D185 | SHA256:F3C98615BFB95957D48F9B20B37C3AA90739125A23704F580769D6C89326A595 | |||
| 2552 | Trojan.Script.Suspic.gen-2ffbbb49d9abb5115a50dec8f13836c7e2c7c47feb9254e8641baa0e0a243992.exe | C:\Windows\Windows10UpgradeComponents\maineffect.exe | executable | |
MD5:9B28DE0F948E5FC24098D87878EEB5DF | SHA256:7E74EA3E17E47CFC1671F30564CCA8B113C8E2A2E665A654EF8939A5B4337564 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
30
TCP/UDP connections
110
DNS requests
120
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6028 | BackgroundTransferHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2908 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5680 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2908 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5200 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6608 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
— | — | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
6608 | firefox.exe | POST | 200 | 142.250.185.195:80 | http://o.pki.goog/s/wr3/cgo | unknown | — | — | whitelisted |
6608 | firefox.exe | POST | 200 | 184.24.77.52:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 20.190.160.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5680 | backgroundTaskHost.exe | 20.199.58.43:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
5680 | backgroundTaskHost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
6028 | BackgroundTransferHost.exe | 104.126.37.145:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |