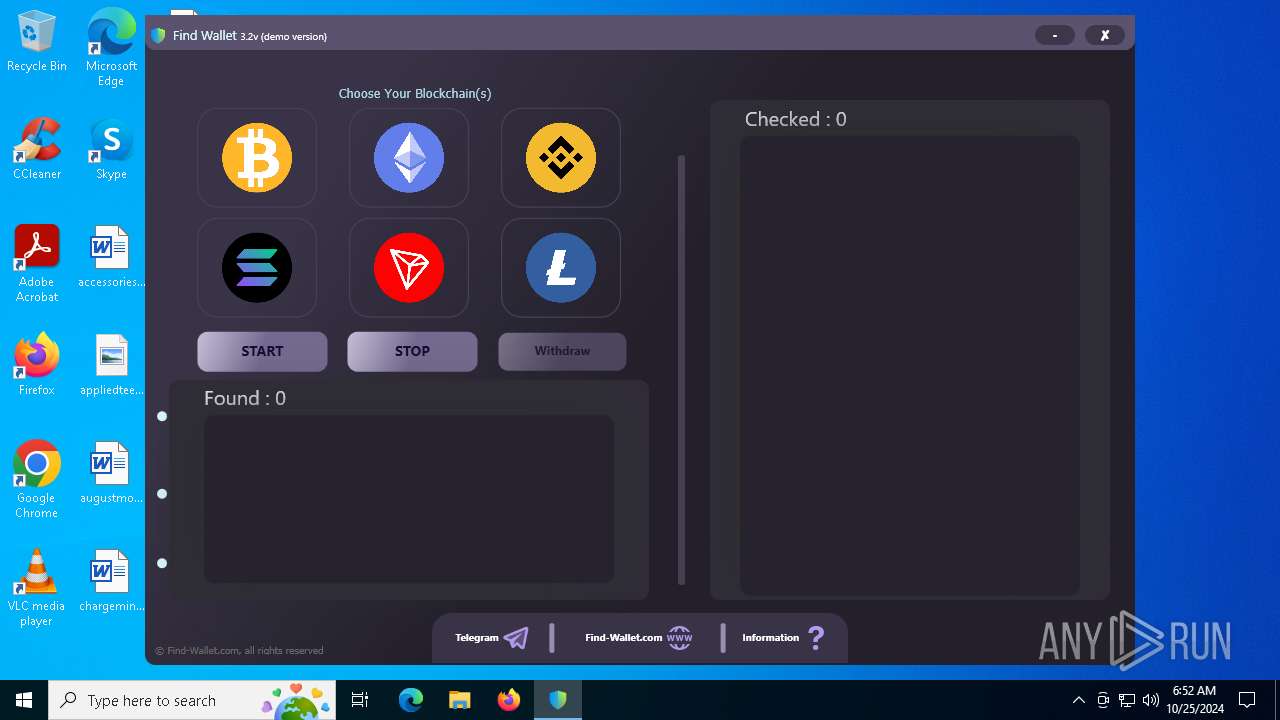
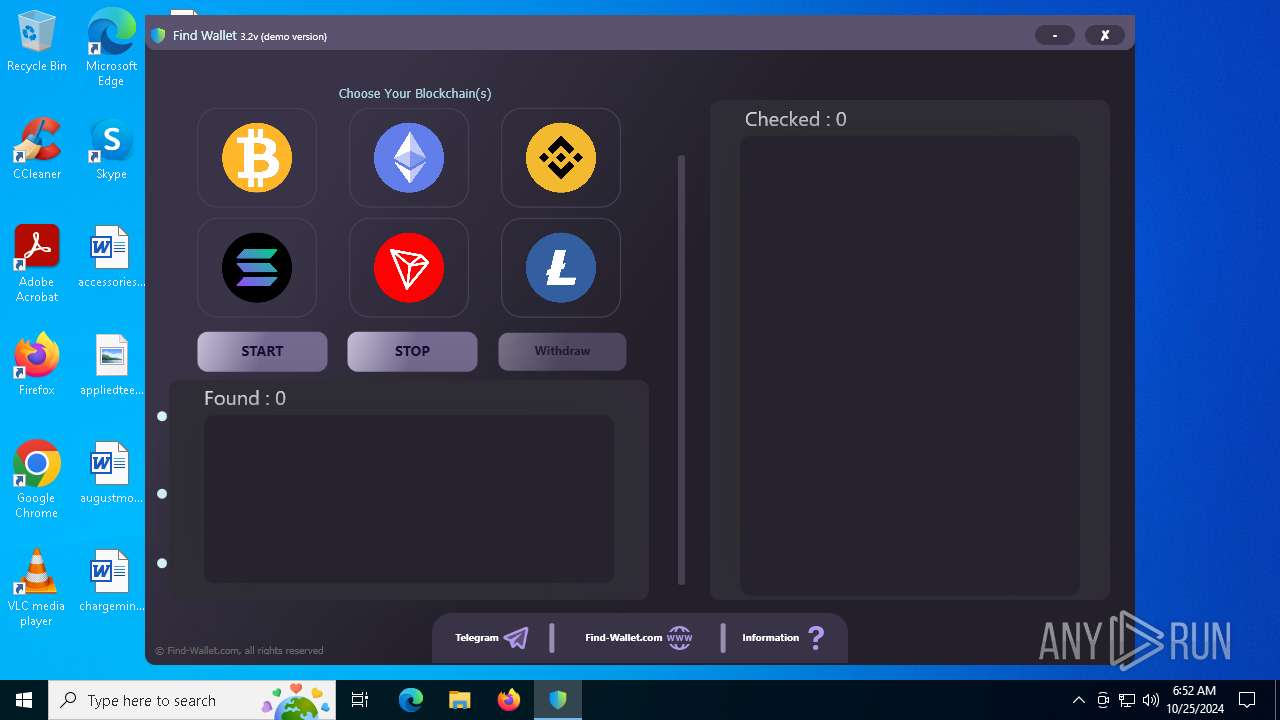
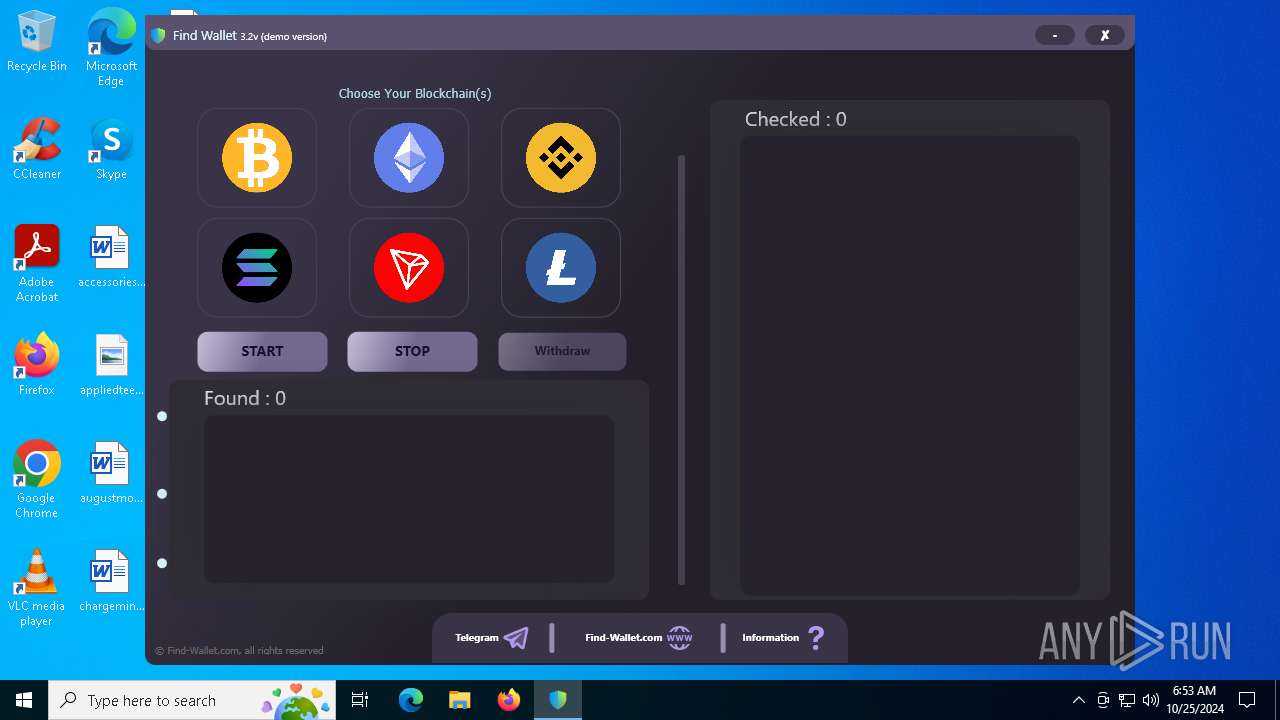
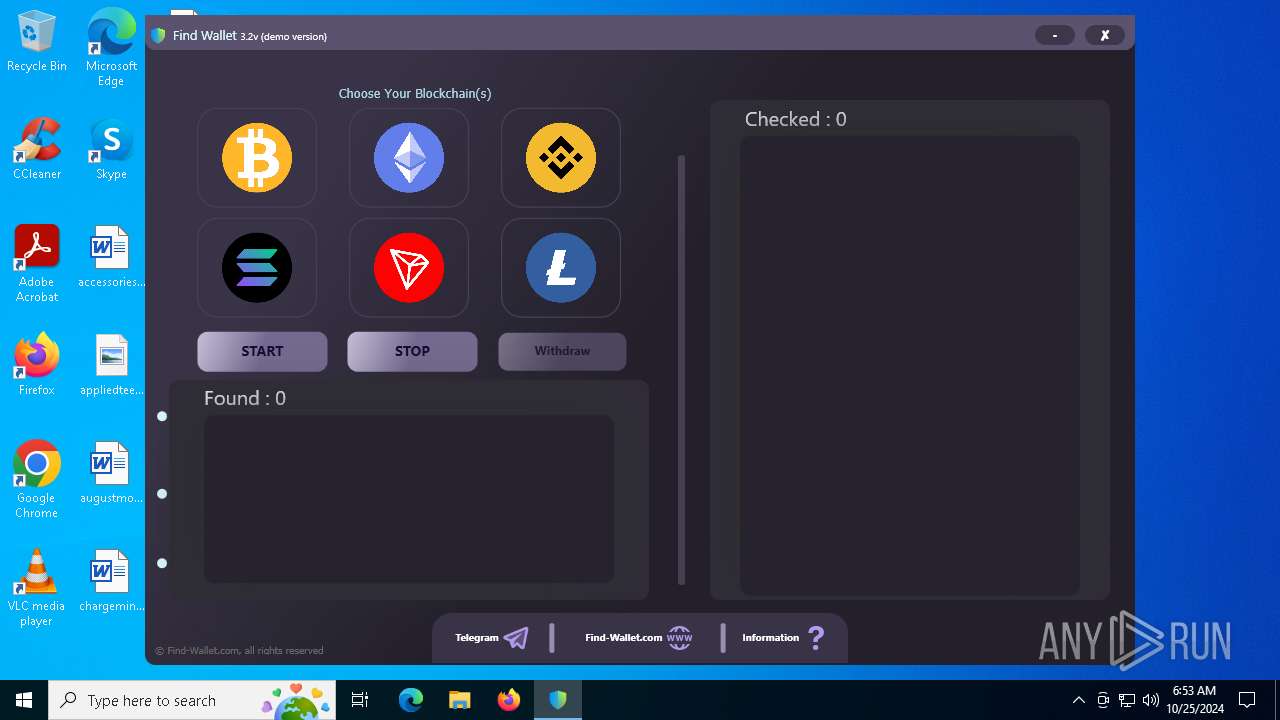
| File name: | FindWalletv3.2-Crack.exe |
| Full analysis: | https://app.any.run/tasks/95d552d3-fe0b-4b81-992b-c435716e0ca6 |
| Verdict: | Malicious activity |
| Analysis date: | October 25, 2024, 06:51:50 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 8 sections |
| MD5: | A5AAD19F2467992040DCE284A1D34016 |
| SHA1: | 9BF000680F2870272BA9F0403CA4DC526FB7C16C |
| SHA256: | 6131F59ADE95F5AAF4F78C1CBD31F033AE508BAE3418D30AD9B7E35E3F96BEB6 |
| SSDEEP: | 49152:9TwBSjTSeRF5peaNgnqwLO8bZWPfehRJ3RJ3vM/oPVy+aZ2qMlXAjmEDGk0DYr6R:xwBSvSeBfgqwrJvMoPdZN9ixy |
MALICIOUS
NESHTA mutex has been found
- FindWalletv3.2-Crack.exe (PID: 6464)
SUSPICIOUS
Reads security settings of Internet Explorer
- FindWalletv3.2-Crack.exe (PID: 6464)
Mutex name with non-standard characters
- FindWalletv3.2-Crack.exe (PID: 6464)
Executable content was dropped or overwritten
- FindWalletv3.2-Crack.exe (PID: 612)
- FindWalletv3.2-Crack.exe (PID: 6464)
Possible usage of Discord/Telegram API has been detected (YARA)
- Client.exe (PID: 6256)
Checks for external IP
- svchost.exe (PID: 2172)
- Client.exe (PID: 6256)
Potential Corporate Privacy Violation
- Client.exe (PID: 6256)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- Client.exe (PID: 6256)
Starts a Microsoft application from unusual location
- FileCoAuth.exe (PID: 6024)
INFO
Checks supported languages
- FindWalletv3.2-Crack.exe (PID: 6464)
- FindWalletv3.2-Crack.exe (PID: 612)
Process checks computer location settings
- FindWalletv3.2-Crack.exe (PID: 6464)
Create files in a temporary directory
- FindWalletv3.2-Crack.exe (PID: 6464)
Reads the computer name
- FindWalletv3.2-Crack.exe (PID: 6464)
The process uses the downloaded file
- FindWalletv3.2-Crack.exe (PID: 6464)
Attempting to use instant messaging service
- svchost.exe (PID: 2172)
- Client.exe (PID: 6256)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Borland Delphi 6 (85.5) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (4.6) |
| .scr | | | Windows screen saver (4.2) |
| .dll | | | Win32 Dynamic Link Library (generic) (2.1) |
| .exe | | | Win32 Executable (generic) (1.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 29696 |
| InitializedDataSize: | 10752 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x80e4 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
128
Monitored processes
6
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 612 | "C:\Users\admin\AppData\Local\Temp\3582-490\FindWalletv3.2-Crack.exe" | C:\Users\admin\AppData\Local\Temp\3582-490\FindWalletv3.2-Crack.exe | FindWalletv3.2-Crack.exe | ||||||||||||
User: admin Company: bitter Integrity Level: MEDIUM Description: sissyaccomplice Exit code: 0 Version: 4.6.11.32 Modules
| |||||||||||||||
| 2172 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6024 | "C:\Users\admin\AppData\Local\Temp\3582-490\FileCoAuth.exe" -Embedding | C:\Users\admin\AppData\Local\Temp\3582-490\FileCoAuth.exe | — | FileCoAuth.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft OneDriveFile Co-Authoring Executable Exit code: 0 Version: 19.043.0304.0013 Modules
| |||||||||||||||
| 6256 | "C:\Users\admin\AppData\Roaming\Client.exe" | C:\Users\admin\AppData\Roaming\Client.exe | FindWalletv3.2-Crack.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: RL Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 6464 | "C:\Users\admin\Desktop\FindWalletv3.2-Crack.exe" | C:\Users\admin\Desktop\FindWalletv3.2-Crack.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6692 | "C:\Users\admin\AppData\Roaming\Find Wallet v3.2-Crack.exe" | C:\Users\admin\AppData\Roaming\Find Wallet v3.2-Crack.exe | — | FindWalletv3.2-Crack.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Find-Wallet Version: 3.2 Modules
| |||||||||||||||
Total events
7 496
Read events
7 481
Write events
15
Delete events
0
Modification events
| (PID) Process: | (6256) Client.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Client_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6256) Client.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Client_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6256) Client.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Client_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (6256) Client.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Client_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (6256) Client.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Client_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (6256) Client.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Client_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (6256) Client.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Client_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (6256) Client.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Client_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6256) Client.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Client_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6256) Client.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Client_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
10
Suspicious files
15
Text files
36
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6256 | Client.exe | C:\Users\admin\AppData\Local\Temp\places.raw | — | |
MD5:— | SHA256:— | |||
| 612 | FindWalletv3.2-Crack.exe | C:\Users\admin\AppData\Roaming\Client.exe | executable | |
MD5:BC5DA83795B587FB1DFCE2D6BEF2D176 | SHA256:D8539AEC2E01D20B840F4C35AE675ECA7F85DE828282D03C4AABAD6034CD8FFB | |||
| 6256 | Client.exe | C:\Users\admin\AppData\Roaming\DESKTOP-JGLLJLD\FileGrabber\Desktop\accessoriessub.rtf | text | |
MD5:CC8BD8A06952B6489CC127DB34592750 | SHA256:DF32F7B33258846C719B826C587C958E6012DD709D4ED68FFBDEFFEF95E967AF | |||
| 612 | FindWalletv3.2-Crack.exe | C:\Users\admin\AppData\Roaming\Find Wallet v3.2-Crack.exe | executable | |
MD5:C309CB9865DFC6DBB7F977F4C0F722C0 | SHA256:51472E512316807270D85560BF6E3030355007C36A4F74D59A286411BB5378B5 | |||
| 6256 | Client.exe | C:\Users\admin\AppData\Roaming\DESKTOP-JGLLJLD\FileGrabber\Desktop\augustmonth.rtf | text | |
MD5:559613DD338FD064C950FCD8BD8B3D0A | SHA256:7CDB1CF6302DAA5AACA30BFCBF087EBCB19BDB25DCAEC319C64447DCF21A6BCA | |||
| 6464 | FindWalletv3.2-Crack.exe | C:\Users\admin\AppData\Local\Temp\3582-490\FindWalletv3.2-Crack.exe | executable | |
MD5:68F929DC1286BF7AF65BF056845F9B42 | SHA256:0D20648267D3004BA95B04F9EF01F3F6E40644B46773990807C2741ADBDD3D82 | |||
| 6256 | Client.exe | C:\Users\admin\AppData\Roaming\DESKTOP-JGLLJLD\Browsers\Outlook\Outlook.txt | text | |
MD5:81051BCC2CF1BEDF378224B0A93E2877 | SHA256:7EB70257593DA06F682A3DDDA54A9D260D4FC514F645237F5CA74B08F8DA61A6 | |||
| 6256 | Client.exe | C:\Users\admin\AppData\Roaming\DESKTOP-JGLLJLD\FileGrabber\Desktop\appliedteens.png | image | |
MD5:46B45DEA3AE4DE54B6D8D1267E6FD038 | SHA256:96CC4C3E17EF4E6C8A76EDDD0E755550DC2D77BE5F2A16AEBCF9E7B6AE48D1E5 | |||
| 6256 | Client.exe | C:\Users\admin\AppData\Roaming\DESKTOP-JGLLJLD\FileGrabber\Desktop\desktop.ini | text | |
MD5:9E36CC3537EE9EE1E3B10FA4E761045B | SHA256:4B9D687AC625690FD026ED4B236DAD1CAC90EF69E7AD256CC42766A065B50026 | |||
| 6256 | Client.exe | C:\Users\admin\AppData\Roaming\DESKTOP-JGLLJLD\FileGrabber\Documents\azmonths.rtf | text | |
MD5:45C78100499E2EECD6DCA93747F551FC | SHA256:7EF0DDE4BB2BB883450489B3F3CD73B9A9F0ABD3AE7AB1D4ED0A174D12030F56 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
27
TCP/UDP connections
37
DNS requests
13
Threats
55
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6944 | svchost.exe | GET | 200 | 2.16.164.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1248 | RUXIMICS.exe | GET | 200 | 2.16.164.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1248 | RUXIMICS.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6256 | Client.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/xml | unknown | — | — | shared |
6256 | Client.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/xml | unknown | — | — | shared |
6256 | Client.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/xml | unknown | — | — | shared |
6256 | Client.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/xml | unknown | — | — | shared |
— | — | GET | 403 | 162.125.72.15:443 | https://dl.dropboxusercontent.com/s/n41axwfwvc7fb8d/image.png?dl=1 | unknown | html | 925 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1248 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | 2.16.164.9:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
6944 | svchost.exe | 2.16.164.9:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
1248 | RUXIMICS.exe | 2.16.164.9:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
1248 | RUXIMICS.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
dl.dropboxusercontent.com |
| shared |
freegeoip.app |
| whitelisted |
ipbase.com |
| unknown |
api.ipify.org |
| shared |
ip-api.com |
| shared |
api.telegram.org |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6256 | Client.exe | Misc activity | ET INFO DropBox User Content Domain (dl .dropboxusercontent .com in TLS SNI) |
6256 | Client.exe | Misc activity | ET INFO DropBox User Content Domain (dl .dropboxusercontent .com in TLS SNI) |
2172 | svchost.exe | Potentially Bad Traffic | ET INFO External IP Lookup Domain Domain in DNS Lookup (ipbase .com) |
6256 | Client.exe | Potentially Bad Traffic | ET INFO Observed External IP Lookup Domain (ipbase .com in TLS SNI) |
6256 | Client.exe | Misc activity | ET INFO DropBox User Content Domain (dl .dropboxusercontent .com in TLS SNI) |
6256 | Client.exe | Misc activity | ET INFO DropBox User Content Domain (dl .dropboxusercontent .com in TLS SNI) |
6256 | Client.exe | Misc activity | ET INFO DropBox User Content Domain (dl .dropboxusercontent .com in TLS SNI) |
6256 | Client.exe | Misc activity | ET INFO DropBox User Content Domain (dl .dropboxusercontent .com in TLS SNI) |
6256 | Client.exe | Misc activity | ET INFO DropBox User Content Domain (dl .dropboxusercontent .com in TLS SNI) |
6256 | Client.exe | Misc activity | ET INFO DropBox User Content Domain (dl .dropboxusercontent .com in TLS SNI) |
17 ETPRO signatures available at the full report