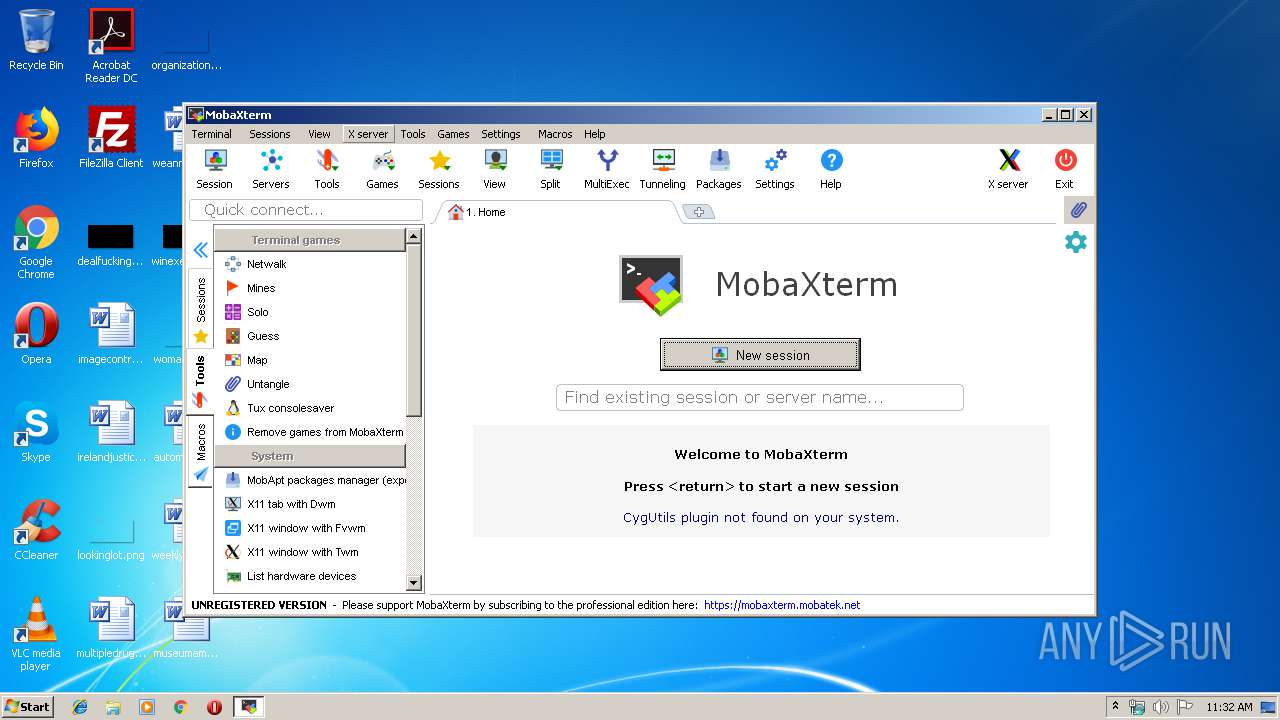
| File name: | MobaXterm_Personal_12.1.exe |
| Full analysis: | https://app.any.run/tasks/7d09ea1e-12f5-4806-8ad3-fbb7f626c700 |
| Verdict: | Malicious activity |
| Analysis date: | September 25, 2019, 10:31:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 61E08A8762BEFC0B9DA02DA50BE0C12C |
| SHA1: | 62EB10A4E3C37A40706D3134DC4A1583FCFE7FDC |
| SHA256: | 6125E12A7EC55988AFF3C2C860A47B0DCE2597B289518F3A06249119A4CA16C8 |
| SSDEEP: | 196608:J69VCTb4h8NrPf3ReXLDbpJ4q2DZQF35Fr/GUWSik8R9FIshnM6jcG2oQ+iH:JpbPGD3l8OrrTWSikqVfjao2 |
MALICIOUS
Loads dropped or rewritten executable
- XWin_MobaX.exe (PID: 3720)
- xkbcomp_w32.exe (PID: 2468)
Application was dropped or rewritten from another process
- MobaRTE.exe (PID: 2872)
- XWin_MobaX.exe (PID: 3720)
- MobaRTE.exe (PID: 2844)
- MobaRTE.exe (PID: 2464)
- xkbcomp_w32.exe (PID: 2468)
SUSPICIOUS
Executable content was dropped or overwritten
- MobaXterm_Personal_12.1.exe (PID: 3744)
Changes IE settings (feature browser emulation)
- MobaRTE.exe (PID: 2464)
- MobaRTE.exe (PID: 2872)
Creates files in the user directory
- MobaRTE.exe (PID: 2872)
Reads internet explorer settings
- MobaRTE.exe (PID: 2464)
- MobaRTE.exe (PID: 2872)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (53.2) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (17.5) |
| .scr | | | Windows screen saver (16.1) |
| .exe | | | Win32 Executable (generic) (5.5) |
| .exe | | | Win16/32 Executable Delphi generic (2.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:08:02 02:00:00+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 6191104 |
| InitializedDataSize: | 8418816 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x5e6764 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 12.1.0.4156 |
| ProductVersionNumber: | 12.1.0.4156 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | Mobatek |
| FileDescription: | MobaXterm |
| FileVersion: | 12.1.0.4156 |
| InternalName: | MobaXterm |
| LegalCopyright: | Mobatek - https://mobaxterm.mobatek.net |
| LegalTrademarks: | Mobatek - https://mobaxterm.mobatek.net |
| OriginalFileName: | MobaXterm |
| ProductName: | MobaXterm |
| ProductVersion: | 12.1 |
| Comments: | https://mobaxterm.mobatek.net |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 02-Aug-2019 00:00:00 |
| Detected languages: |
|
| CompanyName: | Mobatek |
| FileDescription: | MobaXterm |
| FileVersion: | 12.1.0.4156 |
| InternalName: | MobaXterm |
| LegalCopyright: | Mobatek - https://mobaxterm.mobatek.net |
| LegalTrademarks: | Mobatek - https://mobaxterm.mobatek.net |
| OriginalFilename: | MobaXterm |
| ProductName: | MobaXterm |
| ProductVersion: | 12.1 |
| Comments: | https://mobaxterm.mobatek.net |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0050 |
| Pages in file: | 0x0002 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x000F |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x001A |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 8 |
| Time date stamp: | 02-Aug-2019 00:00:00 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
CODE | 0x00001000 | 0x005E762C | 0x005E7800 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.58996 |
DATA | 0x005E9000 | 0x000860A4 | 0x00086200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.17731 |
BSS | 0x00670000 | 0x00028909 | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.idata | 0x00699000 | 0x00004AAE | 0x00004C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.97218 |
.tls | 0x0069E000 | 0x00000034 | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rdata | 0x0069F000 | 0x00000018 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 0.210826 |
.reloc | 0x006A0000 | 0x00055BA4 | 0x00000000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 0 |
.rsrc | 0x006F6000 | 0x00726A00 | 0x00726A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 7.96219 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.03446 | 1738 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 3.27987 | 9640 | UNKNOWN | French - France | RT_ICON |
3 | 3.60944 | 4264 | UNKNOWN | French - France | RT_ICON |
4 | 3.77446 | 2440 | UNKNOWN | French - France | RT_ICON |
5 | 4.01242 | 1128 | UNKNOWN | French - France | RT_ICON |
6 | 2.62527 | 308 | UNKNOWN | UNKNOWN | RT_CURSOR |
7 | 2.91604 | 308 | UNKNOWN | UNKNOWN | RT_CURSOR |
8 | 1.0999 | 4268 | UNKNOWN | English - United States | RT_CURSOR |
9 | 1.95679 | 4268 | UNKNOWN | English - United States | RT_CURSOR |
10 | 1.07477 | 4268 | UNKNOWN | English - United States | RT_CURSOR |
Imports
IPHLPAPI.DLL |
advapi32.dll |
comctl32.dll |
comdlg32.dll |
crypt32.dll |
gdi32.dll |
gdiplus.dll |
imm32.dll |
kernel32.dll |
netapi32.dll |
Total processes
39
Monitored processes
6
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
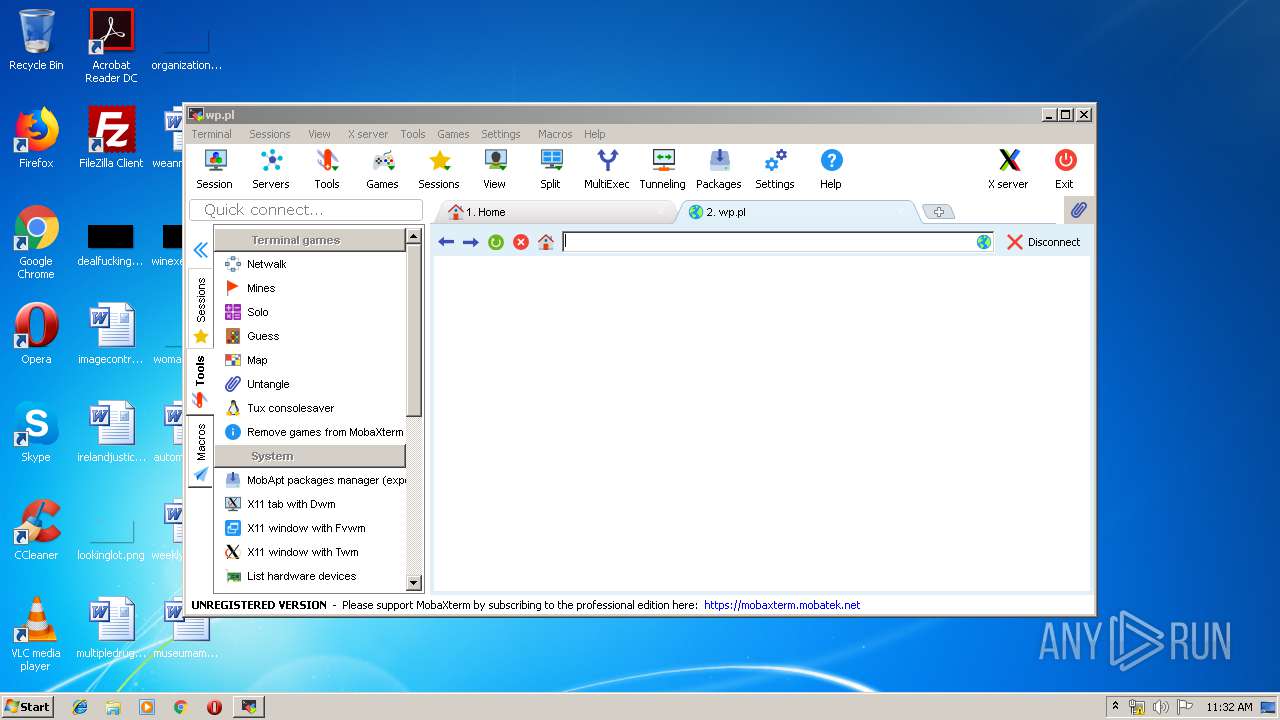
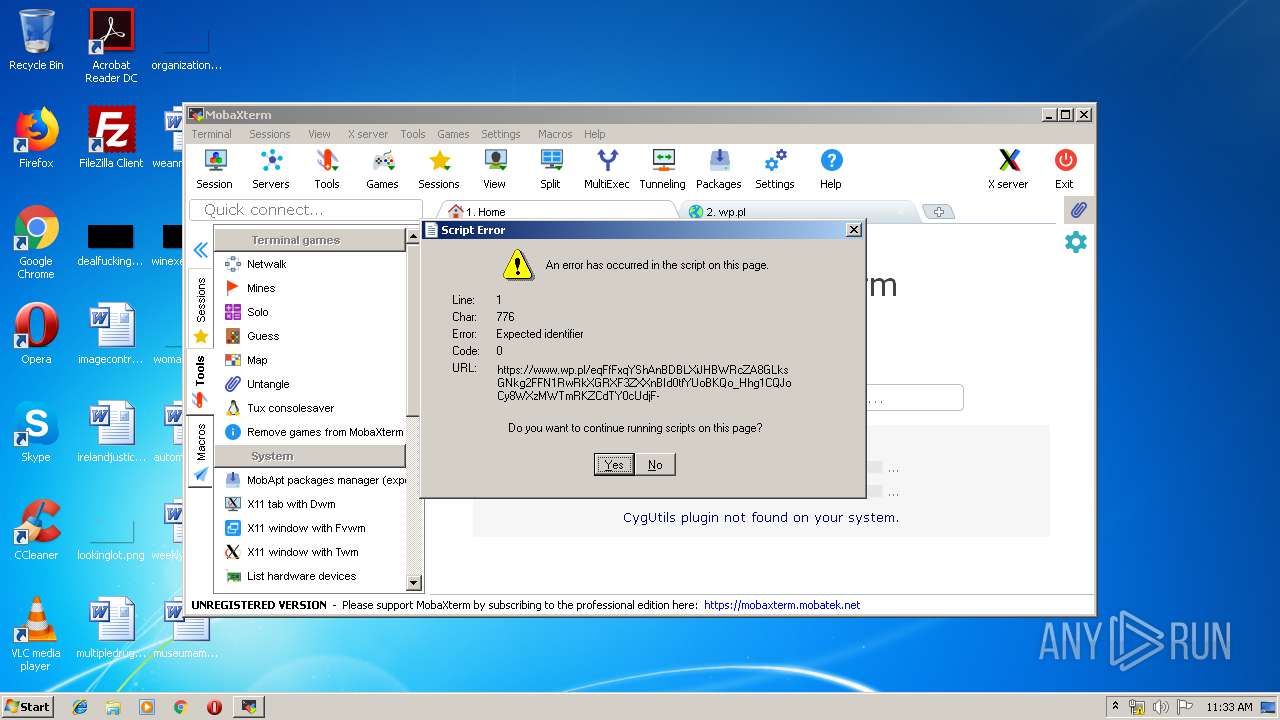
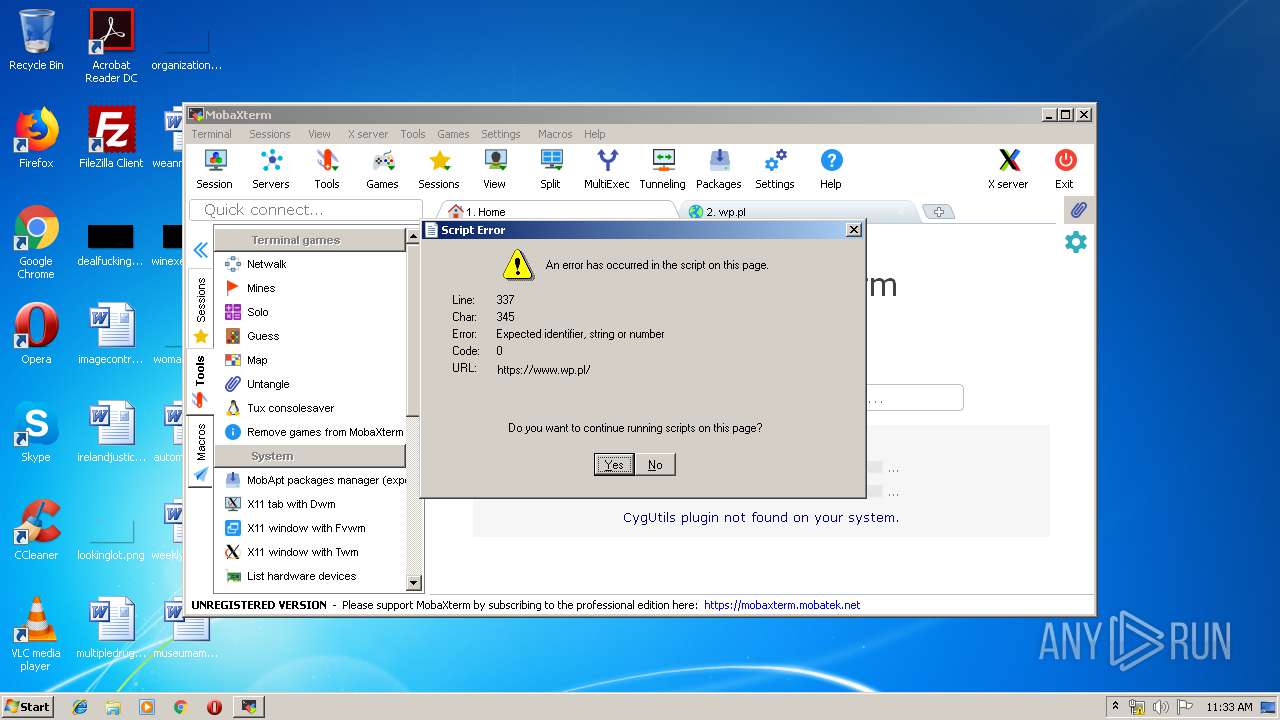
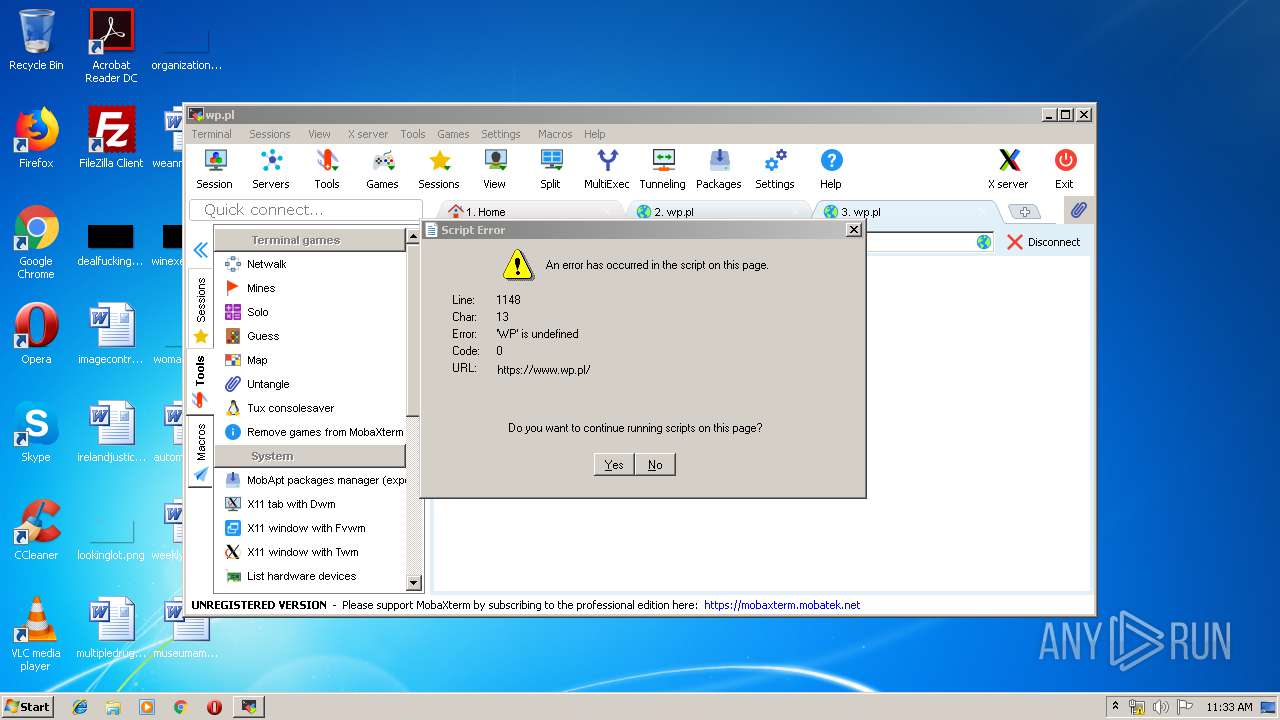
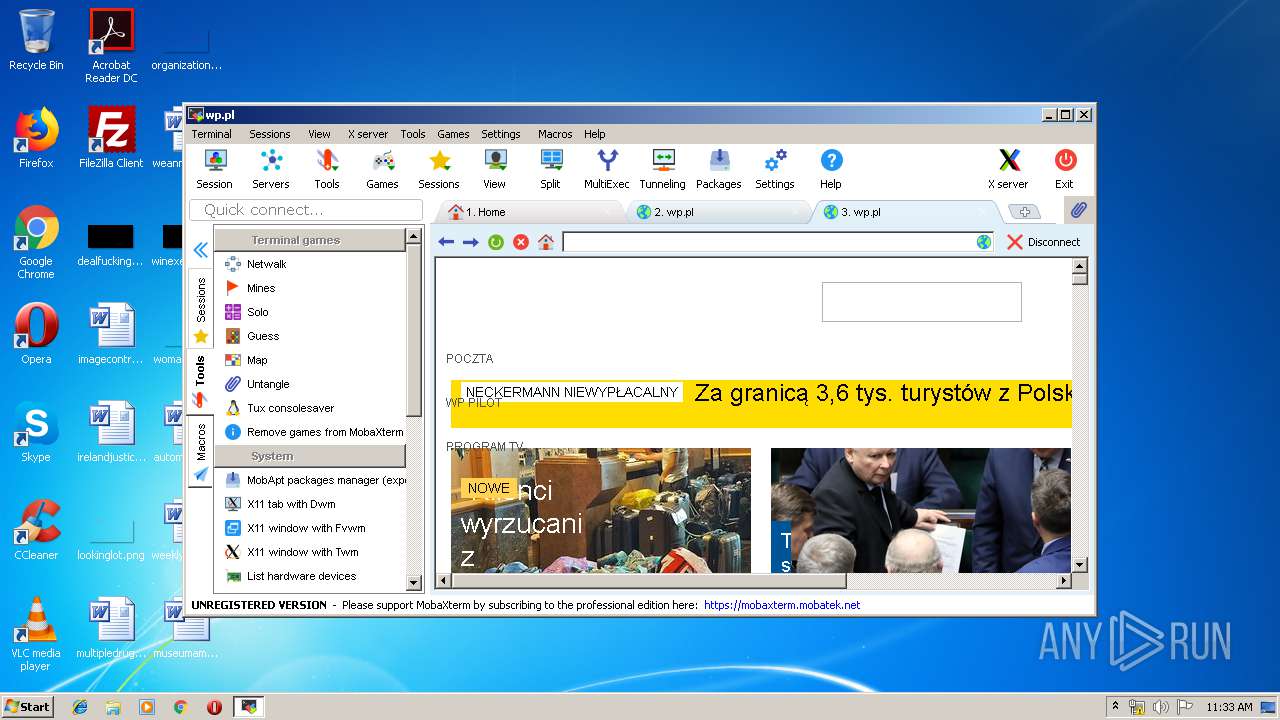
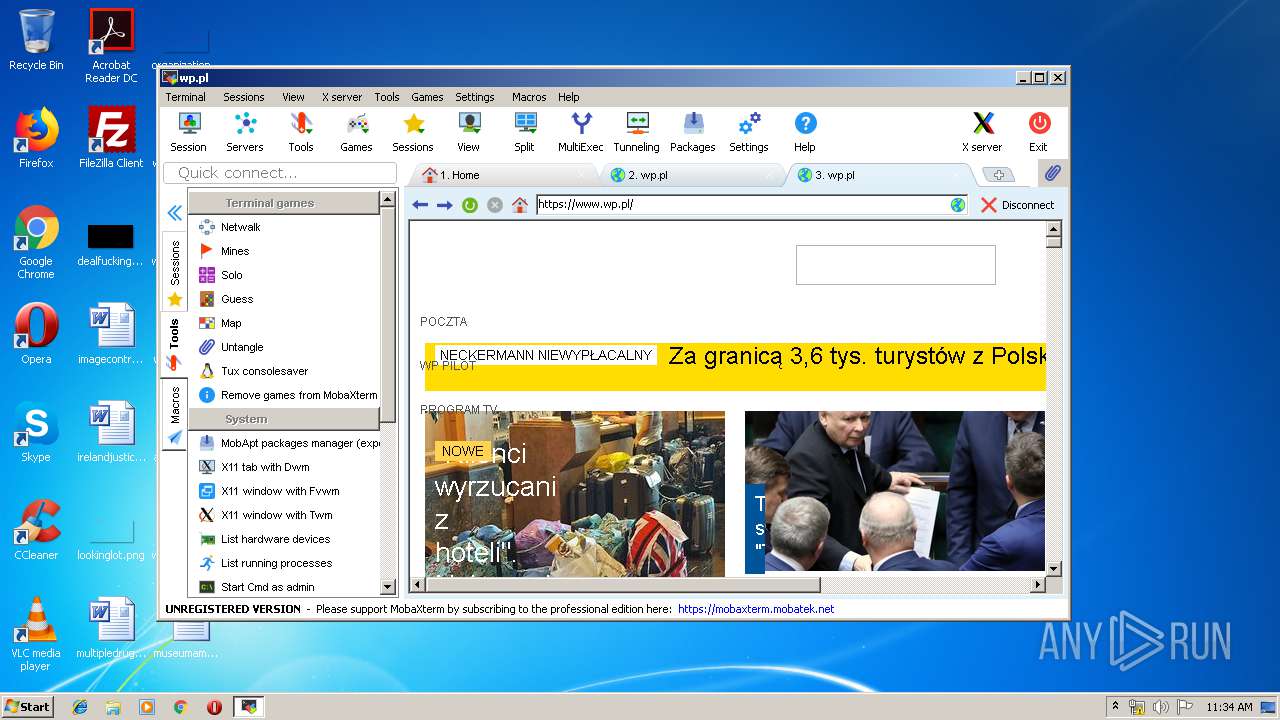
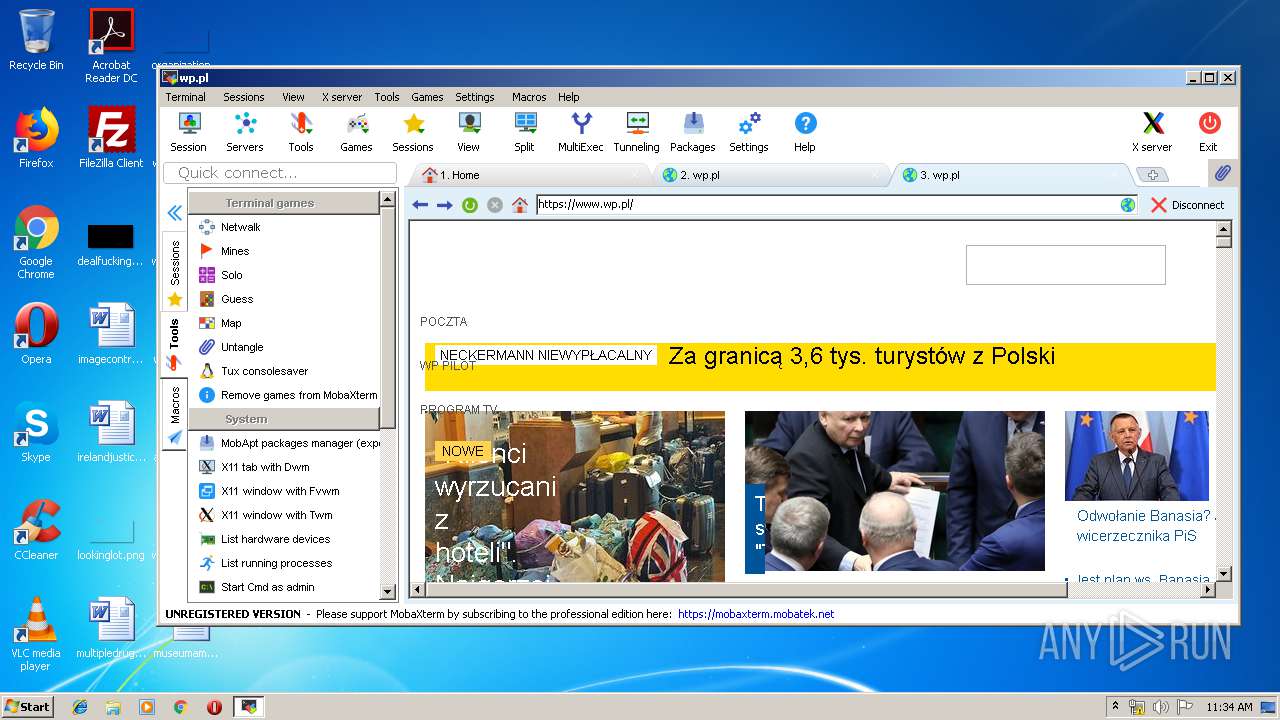
| 2464 | "C:\Users\admin\AppData\Local\Temp\Mxt121\bin\MobaRTE.exe" -browser "wp.pl" -numtab 3 | C:\Users\admin\AppData\Local\Temp\Mxt121\bin\MobaRTE.exe | MobaXterm_Personal_12.1.exe | ||||||||||||
User: admin Company: Mobatek Integrity Level: MEDIUM Description: MobaRTE Exit code: 0 Version: 1.2.4.0 Modules
| |||||||||||||||
| 2468 | "C:\Users\admin\AppData\Local\Temp\Mxt121\bin\xkbcomp_w32.exe" -w 1 "-RC:\Users\admin\AppData\Local\Temp\Mxt121\usr\share\X11\xkb" -xkm "C:\Users\admin\AppData\Local\Temp\Mxt121\var\log\xwin\xkb_a03668" -em1 "The XKEYBOARD keymap compiler (xkbcomp) reports:" -emp "> " -eml "Errors from xkbcomp are not fatal to the X server" "C:\Users\admin\AppData\Local\Temp\Mxt121\var\log\xwin\server-0.xkm" | C:\Users\admin\AppData\Local\Temp\Mxt121\bin\xkbcomp_w32.exe | — | XWin_MobaX.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
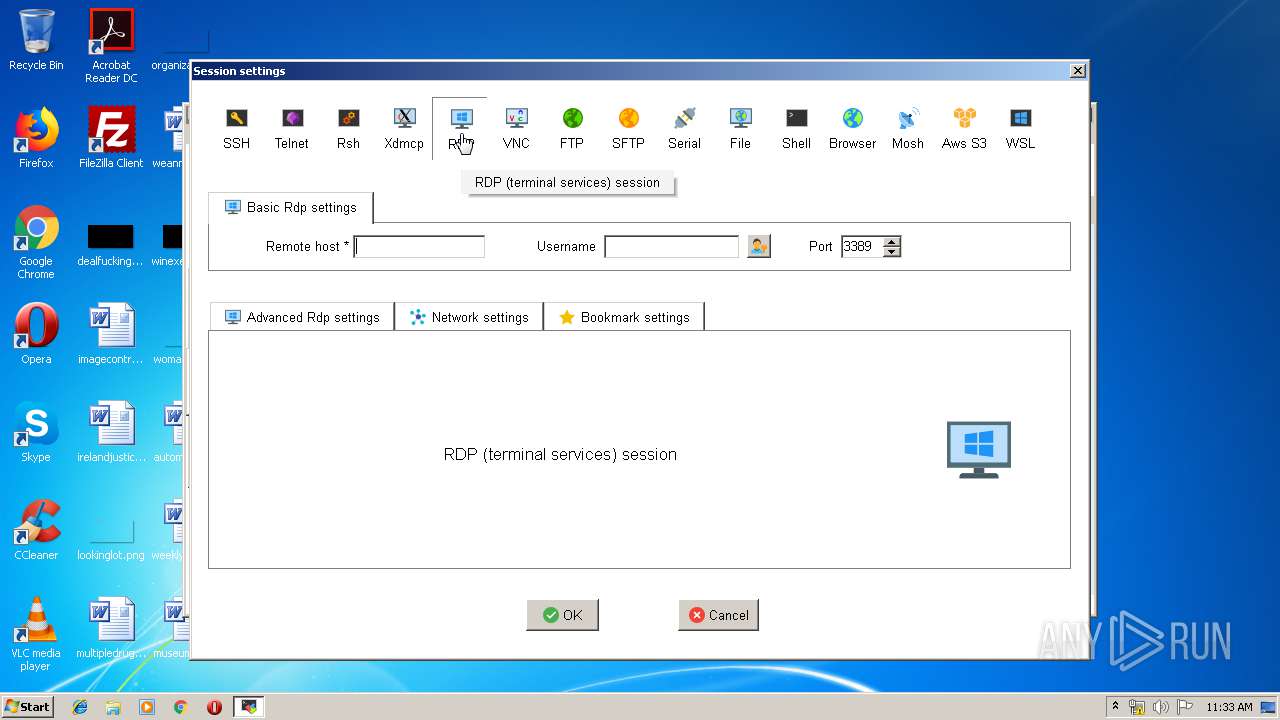
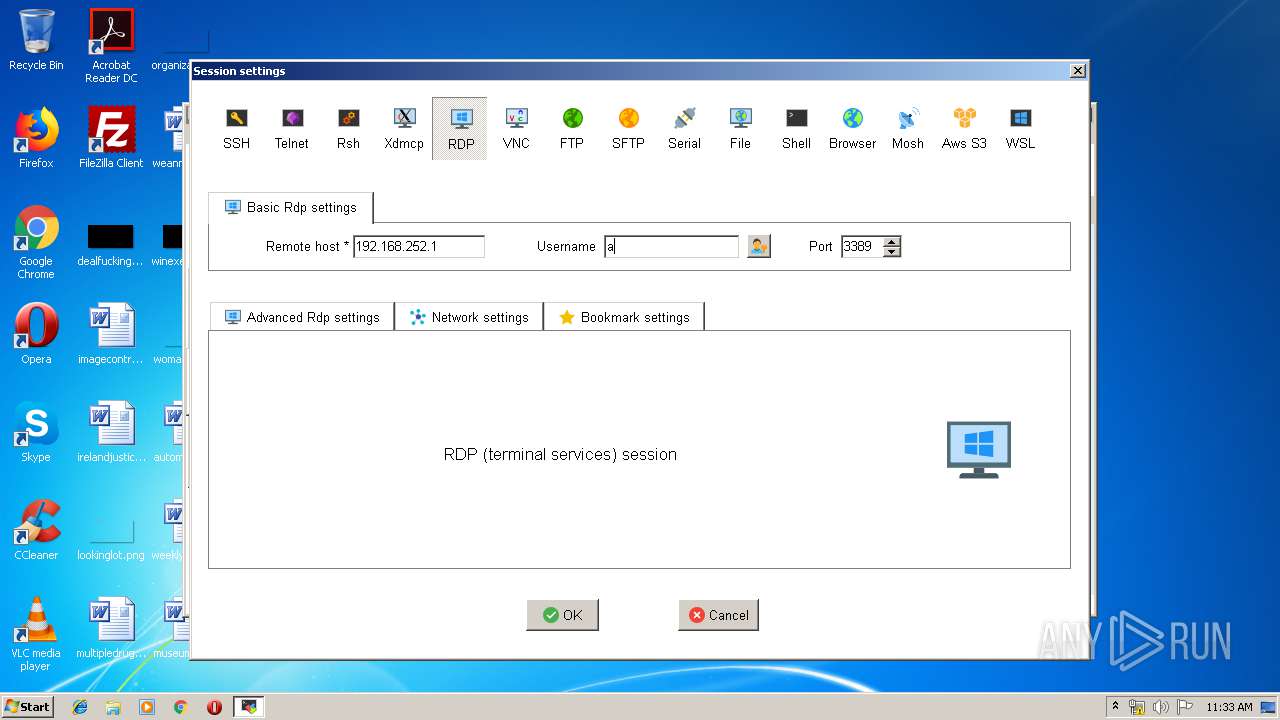
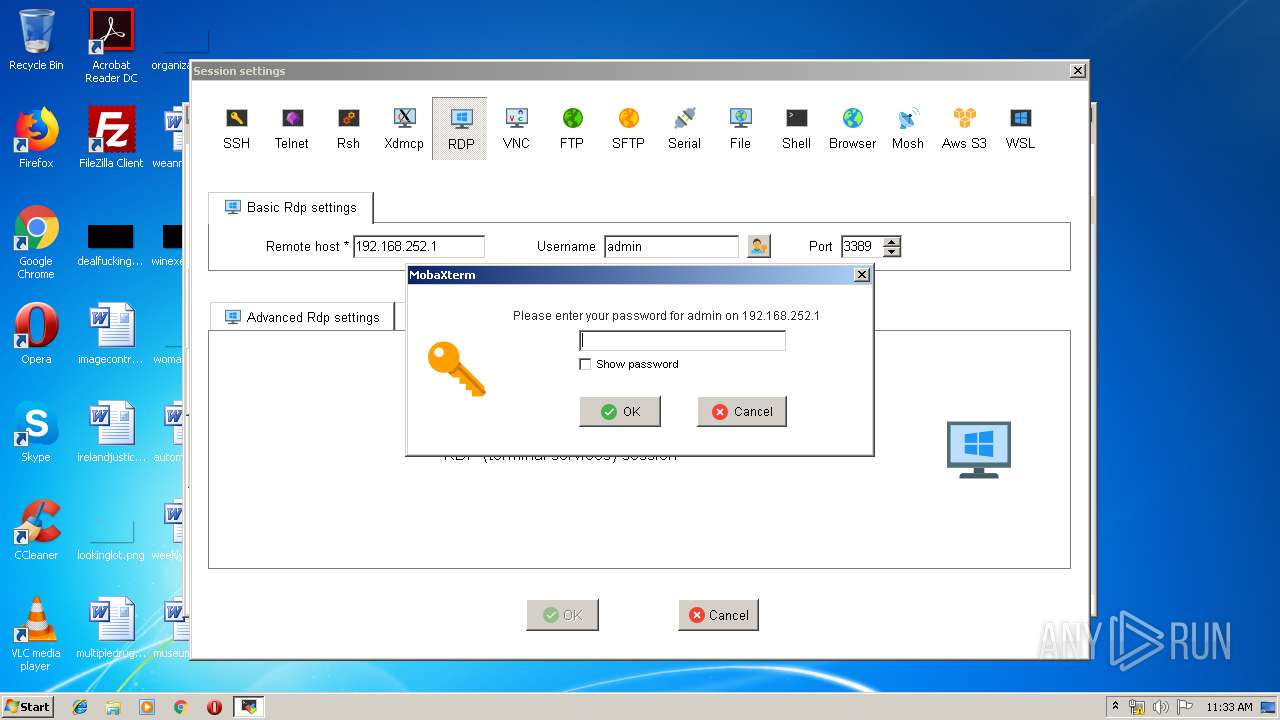
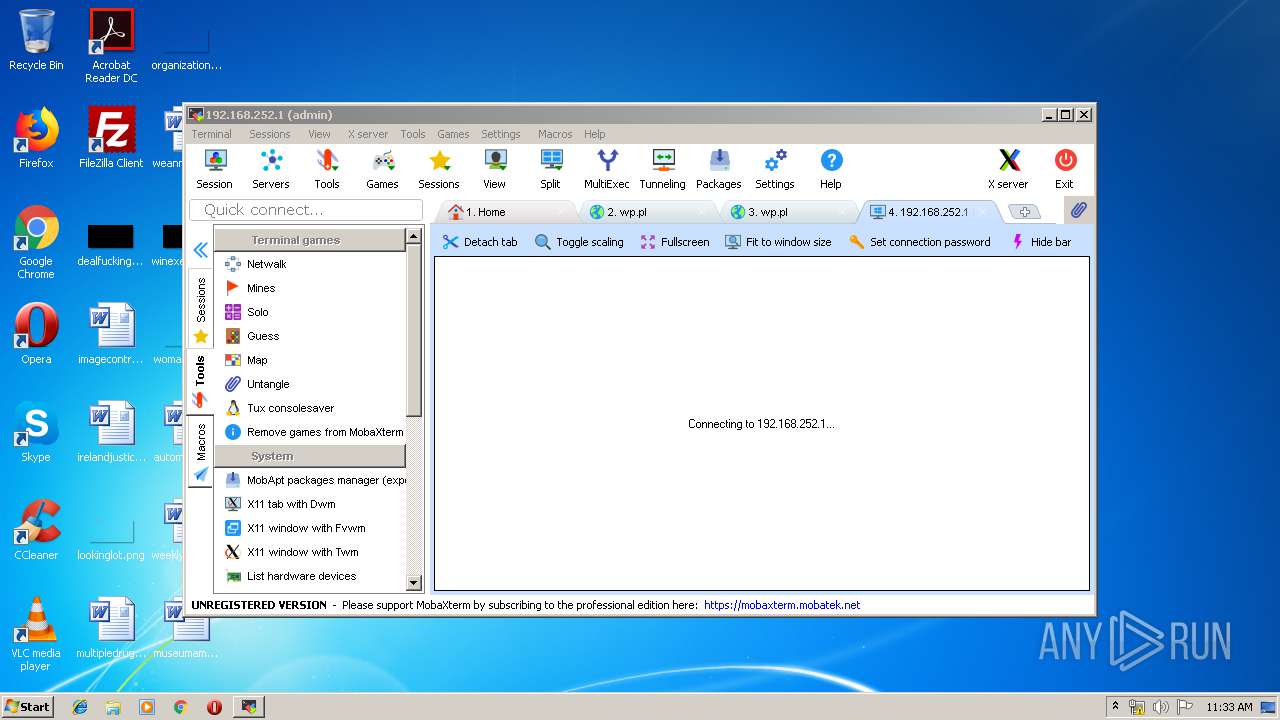
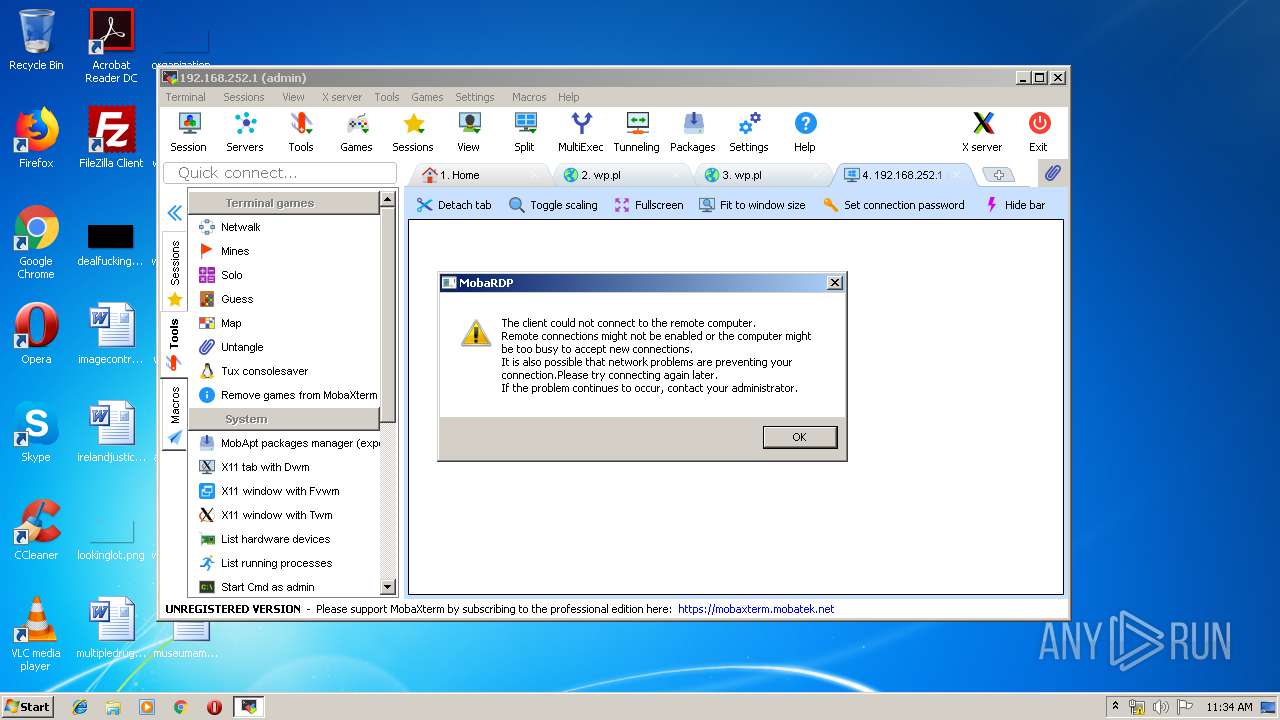
| 2844 | "C:\Users\admin\AppData\Local\Temp\Mxt121\bin\MobaRTE.exe" -rdp mobardp -host "192.168.252.1" -port 3389 -user "admin" -displayres "656x335" -mobahwnd "262484" -remcmd "" -rdpgateway "" -redirdrives -redirprinters -redirports -audiomode 0 -comp -RedirectClipboard -forwardkeys -autoscale -numtab 4 | C:\Users\admin\AppData\Local\Temp\Mxt121\bin\MobaRTE.exe | MobaXterm_Personal_12.1.exe | ||||||||||||
User: admin Company: Mobatek Integrity Level: MEDIUM Description: MobaRTE Exit code: 0 Version: 1.2.4.0 Modules
| |||||||||||||||
| 2872 | "C:\Users\admin\AppData\Local\Temp\Mxt121\bin\MobaRTE.exe" -browser "wp.pl" -numtab 2 | C:\Users\admin\AppData\Local\Temp\Mxt121\bin\MobaRTE.exe | MobaXterm_Personal_12.1.exe | ||||||||||||
User: admin Company: Mobatek Integrity Level: MEDIUM Description: MobaRTE Exit code: 0 Version: 1.2.4.0 Modules
| |||||||||||||||
| 3720 | "C:\Users\admin\AppData\Local\Temp\Mxt121\bin\XWin_MobaX.exe" -silent-dup-error -notrayicon -nolisten inet6 -hostintitle +bs -clipboard -nowgl -multiwindow -noreset :0 | C:\Users\admin\AppData\Local\Temp\Mxt121\bin\XWin_MobaX.exe | MobaXterm_Personal_12.1.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3744 | "C:\Users\admin\AppData\Local\Temp\MobaXterm_Personal_12.1.exe" | C:\Users\admin\AppData\Local\Temp\MobaXterm_Personal_12.1.exe | explorer.exe | ||||||||||||
User: admin Company: Mobatek Integrity Level: MEDIUM Description: MobaXterm Exit code: 0 Version: 12.1.0.4156 Modules
| |||||||||||||||
Total events
2 433
Read events
1 765
Write events
668
Delete events
0
Modification events
| (PID) Process: | (3744) MobaXterm_Personal_12.1.exe | Key: | HKEY_CURRENT_USER\Software\MobaXterm\MoTTY\Sessions\TERM2624841 |
| Operation: | write | Name: | WindowClass |
Value: CMoTTY | |||
| (PID) Process: | (3744) MobaXterm_Personal_12.1.exe | Key: | HKEY_CURRENT_USER\Software\MobaXterm\MoTTY\Sessions\TERM2624841 |
| Operation: | write | Name: | LogguerDansMobaXterm |
Value: 0 | |||
| (PID) Process: | (3744) MobaXterm_Personal_12.1.exe | Key: | HKEY_CURRENT_USER\Software\MobaXterm\MoTTY\Sessions\TERM2624841 |
| Operation: | write | Name: | utf8linedraw |
Value: 1 | |||
| (PID) Process: | (3744) MobaXterm_Personal_12.1.exe | Key: | HKEY_CURRENT_USER\Software\MobaXterm\MoTTY\Sessions\TERM2624841 |
| Operation: | write | Name: | NoRemoteResize |
Value: 1 | |||
| (PID) Process: | (3744) MobaXterm_Personal_12.1.exe | Key: | HKEY_CURRENT_USER\Software\MobaXterm\MoTTY\Sessions\TERM2624841 |
| Operation: | write | Name: | ScrollbarOnLeft |
Value: 0 | |||
| (PID) Process: | (3744) MobaXterm_Personal_12.1.exe | Key: | HKEY_CURRENT_USER\Software\MobaXterm\MoTTY\Sessions\TERM2624841 |
| Operation: | write | Name: | EraseToScrollback |
Value: 1 | |||
| (PID) Process: | (3744) MobaXterm_Personal_12.1.exe | Key: | HKEY_CURRENT_USER\Software\MobaXterm\MoTTY\Sessions\TERM2624841 |
| Operation: | write | Name: | ScrollOnDisp |
Value: 0 | |||
| (PID) Process: | (3744) MobaXterm_Personal_12.1.exe | Key: | HKEY_CURRENT_USER\Software\MobaXterm\MoTTY\Sessions\TERM2624841 |
| Operation: | write | Name: | ScrollOnKey |
Value: 1 | |||
| (PID) Process: | (3744) MobaXterm_Personal_12.1.exe | Key: | HKEY_CURRENT_USER\Software\MobaXterm\MoTTY\Sessions\TERM2624841 |
| Operation: | write | Name: | ScrollBarFullScreen |
Value: 1 | |||
| (PID) Process: | (3744) MobaXterm_Personal_12.1.exe | Key: | HKEY_CURRENT_USER\Software\MobaXterm\MoTTY\Sessions\TERM2624841 |
| Operation: | write | Name: | ScrollBar |
Value: 1 | |||
Executable files
41
Suspicious files
60
Text files
705
Unknown types
117
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3744 | MobaXterm_Personal_12.1.exe | C:\Users\admin\AppData\Local\Temp\Mxt121\etc\nsswitch.conf | text | |
MD5:5A76145CB2E0BD7CABAC55C6E941F3F7 | SHA256:C83DC30523FEDB6298ABE4A492EC03CE74B3EDF1679A69F23B6B901620925B1B | |||
| 3744 | MobaXterm_Personal_12.1.exe | C:\Users\admin\AppData\Local\Temp\Mxt121\etc\profile | text | |
MD5:— | SHA256:— | |||
| 3744 | MobaXterm_Personal_12.1.exe | C:\Users\admin\AppData\Local\Temp\Mxt121\mnt | binary | |
MD5:2064A8DFFC77A2130D9F64018604769E | SHA256:D7F3656E9078257BD9B7558EE2D01E94D3C30B81F035FA3417B745139C9ECCB8 | |||
| 3744 | MobaXterm_Personal_12.1.exe | C:\Users\admin\AppData\Local\Temp\Mxt121\media | binary | |
MD5:2064A8DFFC77A2130D9F64018604769E | SHA256:D7F3656E9078257BD9B7558EE2D01E94D3C30B81F035FA3417B745139C9ECCB8 | |||
| 3744 | MobaXterm_Personal_12.1.exe | C:\Users\admin\AppData\Local\Temp\Mxt121\mx86_64b\media | binary | |
MD5:2064A8DFFC77A2130D9F64018604769E | SHA256:D7F3656E9078257BD9B7558EE2D01E94D3C30B81F035FA3417B745139C9ECCB8 | |||
| 3744 | MobaXterm_Personal_12.1.exe | C:\Users\admin\AppData\Local\Temp\Mxt121\cygdrive | binary | |
MD5:2064A8DFFC77A2130D9F64018604769E | SHA256:D7F3656E9078257BD9B7558EE2D01E94D3C30B81F035FA3417B745139C9ECCB8 | |||
| 3744 | MobaXterm_Personal_12.1.exe | C:\Users\admin\AppData\Local\Temp\Mxt121\etc\ssh_config | text | |
MD5:7CEB8529CB9FBE96FA321424D4C2681B | SHA256:8F1265583B3480A2F0D3F2FA6AFE347E26FDD5C975CB3285F4C74FB2335F9C49 | |||
| 3744 | MobaXterm_Personal_12.1.exe | C:\Users\admin\AppData\Local\Temp\Mxt121\etc\init.d\ssh | binary | |
MD5:2A2FCE224C91755D043CFD460CB7EBC2 | SHA256:CAABB53C134A5727836D7669AB5063AFAECD37E1225F5F3A6810AEF441BAFF20 | |||
| 3744 | MobaXterm_Personal_12.1.exe | C:\Users\admin\AppData\Local\Temp\Mxt121\etc\init.d\http | binary | |
MD5:2A2FCE224C91755D043CFD460CB7EBC2 | SHA256:CAABB53C134A5727836D7669AB5063AFAECD37E1225F5F3A6810AEF441BAFF20 | |||
| 3744 | MobaXterm_Personal_12.1.exe | C:\Users\admin\AppData\Local\Temp\Mxt121\etc\init.d\tftp | binary | |
MD5:2A2FCE224C91755D043CFD460CB7EBC2 | SHA256:CAABB53C134A5727836D7669AB5063AFAECD37E1225F5F3A6810AEF441BAFF20 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
155
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
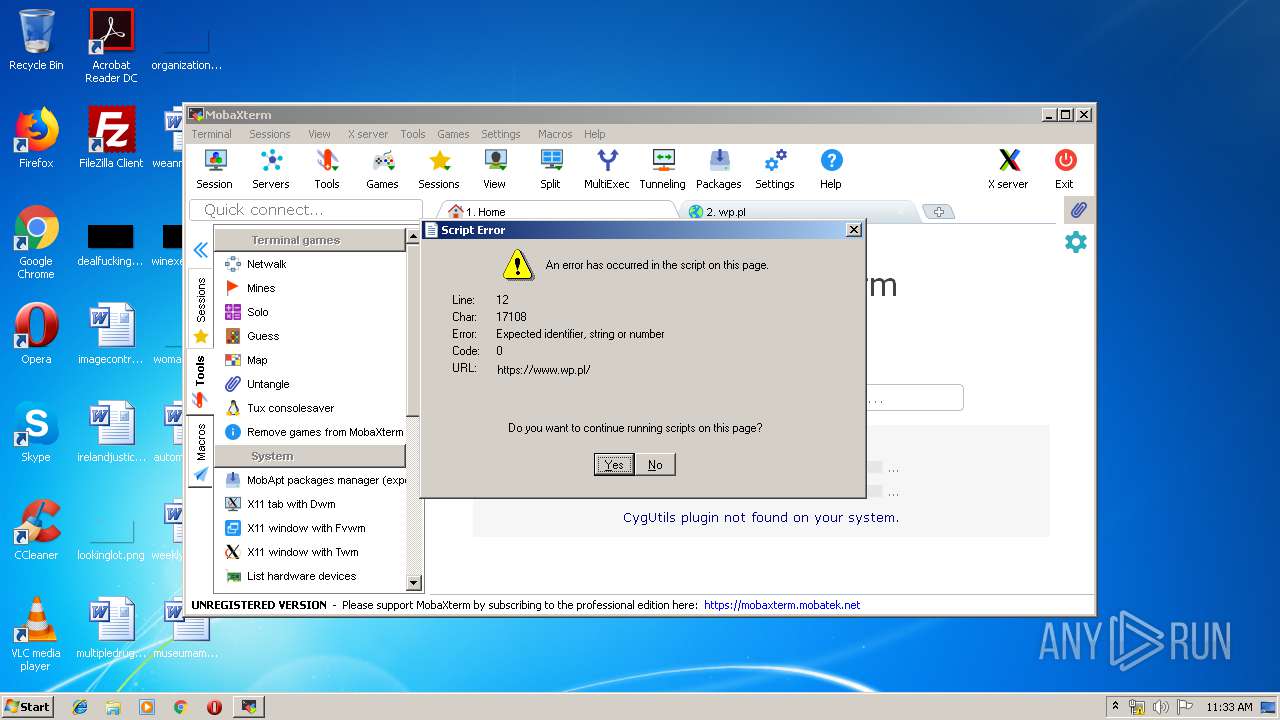
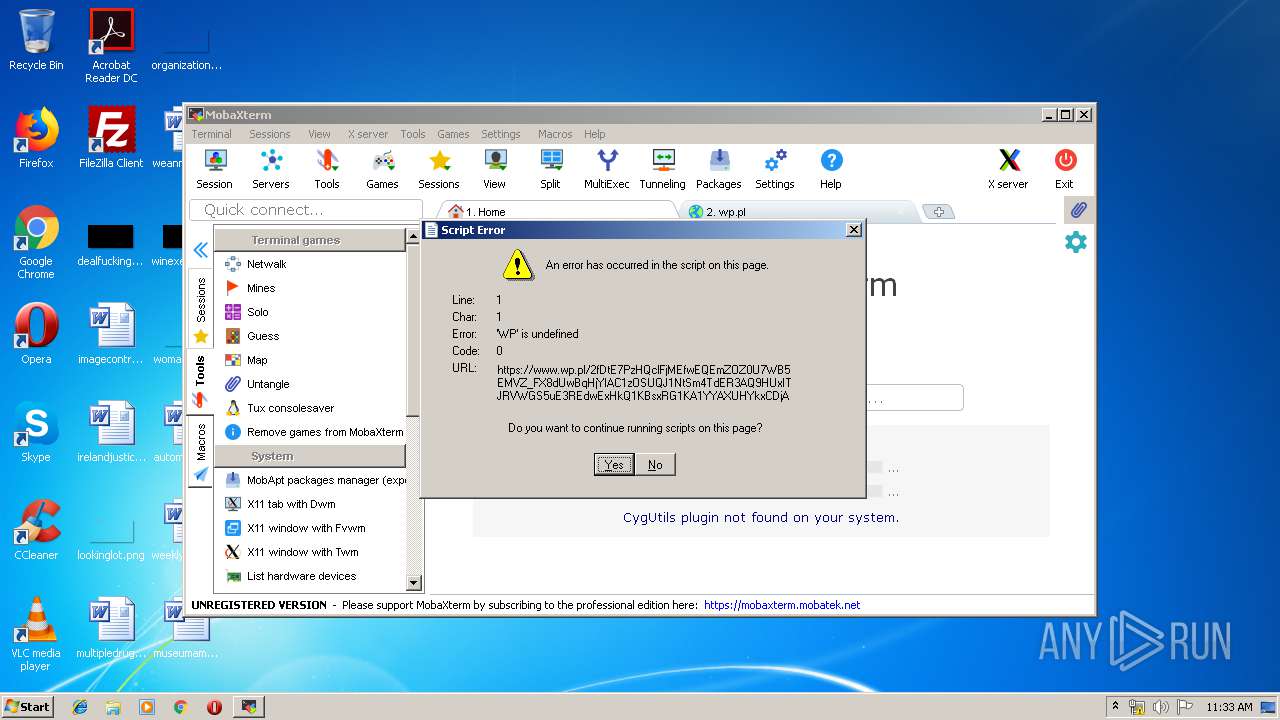
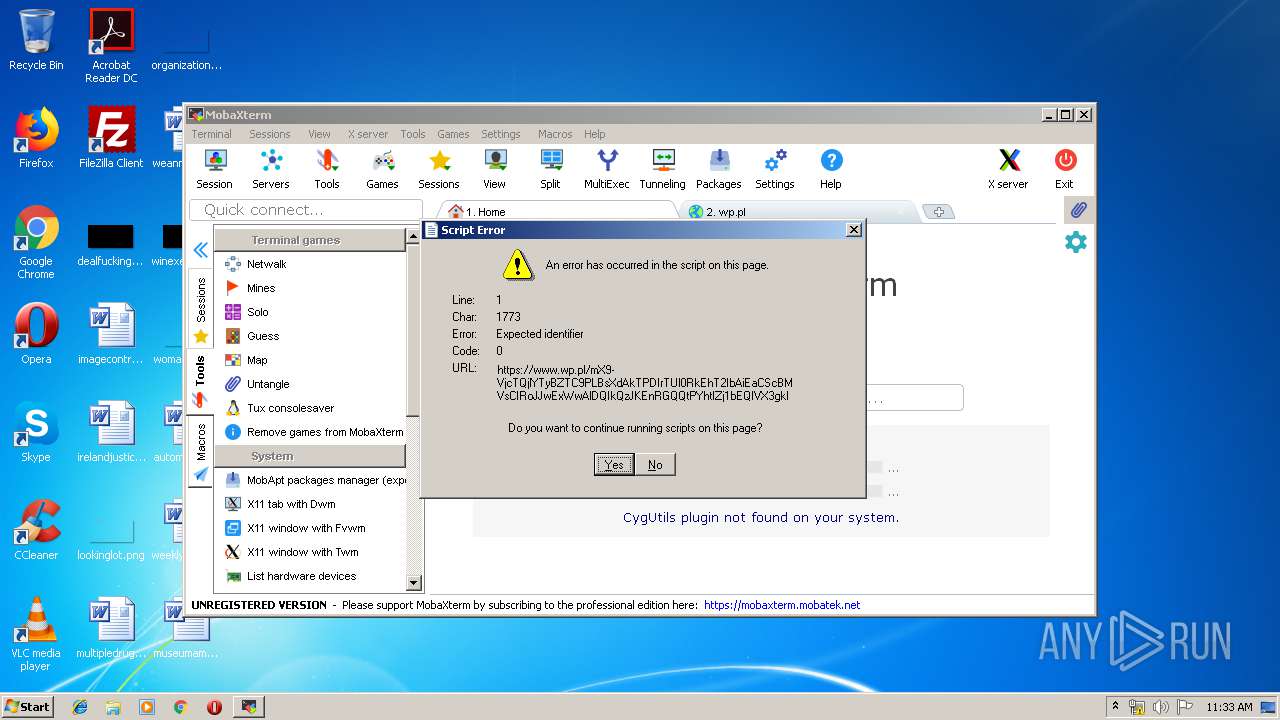
2872 | MobaRTE.exe | GET | 301 | 212.77.98.9:80 | http://wp.pl/ | PL | html | 162 b | shared |
2872 | MobaRTE.exe | GET | 301 | 212.77.98.9:80 | http://www.wp.pl/ | PL | html | 162 b | whitelisted |
2464 | MobaRTE.exe | GET | 301 | 212.77.98.9:80 | http://www.wp.pl/ | PL | html | 162 b | whitelisted |
2464 | MobaRTE.exe | GET | 301 | 212.77.98.9:80 | http://wp.pl/ | PL | html | 162 b | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2872 | MobaRTE.exe | 212.77.98.9:80 | wp.pl | Wirtualna Polska S.A. | PL | suspicious |
2872 | MobaRTE.exe | 51.83.241.203:443 | s-eu-1.pushpushgo.com | — | GB | unknown |
2872 | MobaRTE.exe | 212.77.98.9:443 | wp.pl | Wirtualna Polska S.A. | PL | suspicious |
2872 | MobaRTE.exe | 212.77.98.6:443 | d.wpimg.pl | Wirtualna Polska S.A. | PL | unknown |
2464 | MobaRTE.exe | 212.77.98.9:80 | wp.pl | Wirtualna Polska S.A. | PL | suspicious |
2464 | MobaRTE.exe | 51.83.241.203:443 | s-eu-1.pushpushgo.com | — | GB | unknown |
2872 | MobaRTE.exe | 212.77.99.26:443 | v.wpimg.pl | Wirtualna Polska S.A. | PL | suspicious |
2464 | MobaRTE.exe | 212.77.98.9:443 | wp.pl | Wirtualna Polska S.A. | PL | suspicious |
2464 | MobaRTE.exe | 212.77.98.32:443 | fonts.wpcdn.pl | Wirtualna Polska S.A. | PL | suspicious |
2872 | MobaRTE.exe | 212.77.98.32:443 | fonts.wpcdn.pl | Wirtualna Polska S.A. | PL | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
wp.pl |
| shared |
www.wp.pl |
| whitelisted |
s-eu-1.pushpushgo.com |
| whitelisted |
fonts.wpcdn.pl |
| suspicious |
v.wpimg.pl |
| suspicious |
d.wpimg.pl |
| unknown |