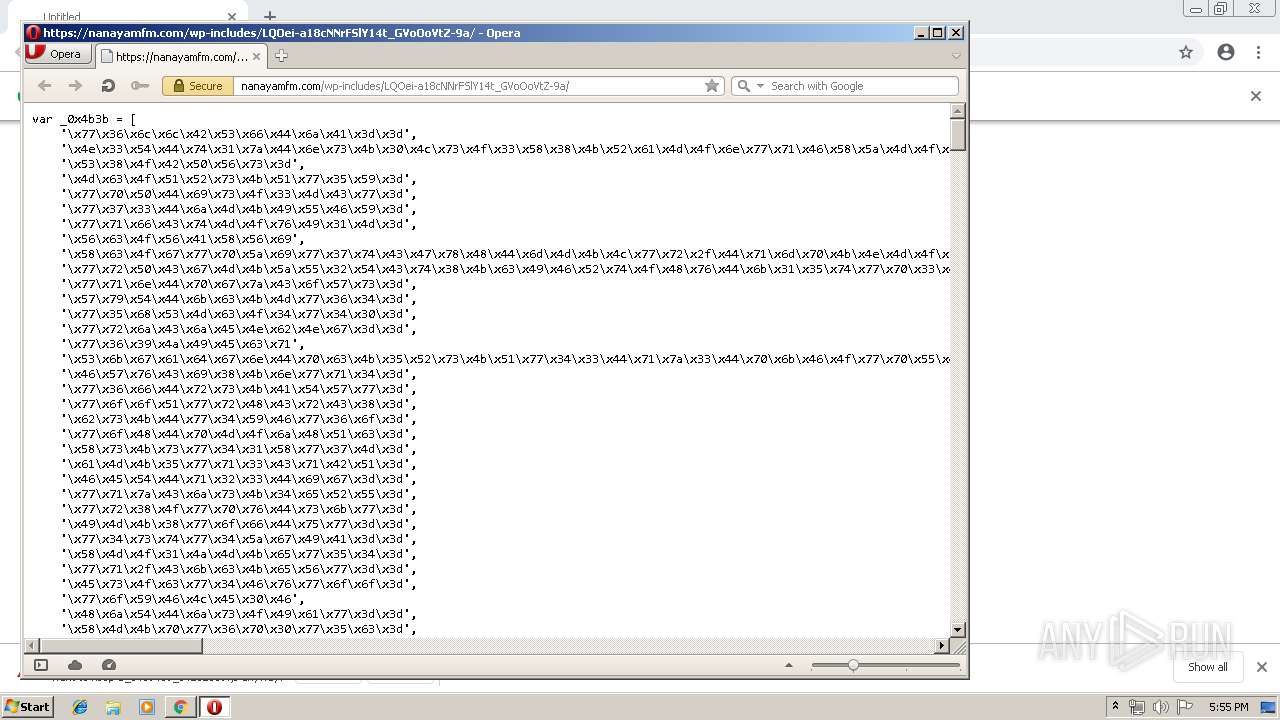
| URL: | https://nanayamfm.com/wp-includes/LQOei-a18cNNrFSlY14t_GVoOoVtZ-9a/ |
| Full analysis: | https://app.any.run/tasks/59e87da4-7d4b-4a7d-870d-1d8134697bdf |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | April 23, 2019, 16:54:26 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 4480419D03D8297ED474725F73053799 |
| SHA1: | 30EFED9AD1F9BCCBEC4C7FC17FAED87747218114 |
| SHA256: | 60F32A28644367C7D1B07139F5C5DB104D9BFA4FB9FBD36C6441A55B332774BE |
| SSDEEP: | 3:N8d3mUe27MJEv/z2y2KzRA1Kn:20Uf7MJO//2KzRBn |
MALICIOUS
Application was dropped or rewritten from another process
- p6dgnrbzl.exe (PID: 3348)
- p6dgnrbzl.exe (PID: 2724)
- soundser.exe (PID: 2732)
- soundser.exe (PID: 2648)
- kBB0ofA9tz.exe (PID: 3080)
- kBB0ofA9tz.exe (PID: 3844)
- soundser.exe (PID: 2960)
- soundser.exe (PID: 2868)
Emotet process was detected
- soundser.exe (PID: 2732)
- soundser.exe (PID: 2868)
Downloads executable files from the Internet
- WScript.exe (PID: 3384)
Connects to CnC server
- soundser.exe (PID: 2648)
- soundser.exe (PID: 2960)
EMOTET was detected
- soundser.exe (PID: 2648)
- soundser.exe (PID: 2960)
Changes the autorun value in the registry
- soundser.exe (PID: 2648)
SUSPICIOUS
Executable content was dropped or overwritten
- p6dgnrbzl.exe (PID: 2724)
- soundser.exe (PID: 2648)
- WScript.exe (PID: 3384)
- kBB0ofA9tz.exe (PID: 3080)
Creates files in the user directory
- WScript.exe (PID: 3384)
Starts itself from another location
- p6dgnrbzl.exe (PID: 2724)
- kBB0ofA9tz.exe (PID: 3080)
Application launched itself
- kBB0ofA9tz.exe (PID: 3844)
- soundser.exe (PID: 2868)
Connects to server without host name
- soundser.exe (PID: 2648)
- soundser.exe (PID: 2960)
INFO
Application launched itself
- chrome.exe (PID: 2644)
Creates files in the user directory
- opera.exe (PID: 2564)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
54
Monitored processes
22
Malicious processes
9
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2388 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=960,5059443428091262702,2540024473480929749,131072 --enable-features=PasswordImport --service-pipe-token=10570409212713995402 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=10570409212713995402 --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1952 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2444 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=960,5059443428091262702,2540024473480929749,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=13977050167515680542 --mojo-platform-channel-handle=888 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2464 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=960,5059443428091262702,2540024473480929749,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAACAAwAAAQAAAAAAAAAAAGAAAAAAAAEAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=12853412596651629655 --mojo-platform-channel-handle=3660 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2564 | "C:\Program Files\Opera\opera.exe" | C:\Program Files\Opera\opera.exe | explorer.exe | ||||||||||||
User: admin Company: Opera Software Integrity Level: MEDIUM Description: Opera Internet Browser Exit code: 0 Version: 1748 Modules
| |||||||||||||||
| 2644 | "C:\Program Files\Google\Chrome\Application\chrome.exe" https://nanayamfm.com/wp-includes/LQOei-a18cNNrFSlY14t_GVoOoVtZ-9a/ | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 3221225547 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2648 | --3ab57678 | C:\Users\admin\AppData\Local\soundser\soundser.exe | soundser.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2656 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=960,5059443428091262702,2540024473480929749,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=9433343437352029430 --mojo-platform-channel-handle=1844 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2672 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2724 | --c0ed12ab | C:\Users\admin\AppData\Local\Temp\p6dgnrbzl.exe | p6dgnrbzl.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2732 | "C:\Users\admin\AppData\Local\soundser\soundser.exe" | C:\Users\admin\AppData\Local\soundser\soundser.exe | p6dgnrbzl.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
1 869
Read events
1 580
Write events
283
Delete events
6
Modification events
| (PID) Process: | (2644) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2644) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2644) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2644) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2644) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2800) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2644-13200512081022375 |
Value: 259 | |||
| (PID) Process: | (2644) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2644) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2644) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3488-13197474229333984 |
Value: 0 | |||
| (PID) Process: | (2644) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
4
Suspicious files
63
Text files
103
Unknown types
14
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2644 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\index | — | |
MD5:— | SHA256:— | |||
| 2644 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_0 | — | |
MD5:— | SHA256:— | |||
| 2644 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_1 | — | |
MD5:— | SHA256:— | |||
| 2644 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_2 | — | |
MD5:— | SHA256:— | |||
| 2644 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_3 | — | |
MD5:— | SHA256:— | |||
| 2644 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\185a83c7-ea86-422b-8529-a0cbfb7a39aa.tmp | — | |
MD5:— | SHA256:— | |||
| 2644 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000018.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2644 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\GPUCache\index | — | |
MD5:— | SHA256:— | |||
| 2644 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\GPUCache\data_0 | — | |
MD5:— | SHA256:— | |||
| 2644 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\GPUCache\data_1 | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
37
DNS requests
20
Threats
15
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2644 | chrome.exe | GET | — | 87.245.198.13:80 | http://r2---sn-gxuog0-axqe.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvMjJlQUFXRC12Ny1ldUFnMXF3SDlXZDlFZw/7319.128.0.1_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mip=91.221.66.140&mm=28&mn=sn-gxuog0-axqe&ms=nvh&mt=1556038021&mv=u&pl=23&shardbypass=yes | RU | — | — | whitelisted |
2564 | opera.exe | GET | 200 | 66.225.197.197:80 | http://crl4.digicert.com/DigiCertHighAssuranceEVRootCA.crl | US | der | 543 b | whitelisted |
3384 | WScript.exe | GET | 200 | 164.52.146.13:80 | http://potterspots.com/cgi-bin/8MnY/ | US | executable | 77.5 Kb | suspicious |
2564 | opera.exe | GET | 200 | 192.35.177.64:80 | http://crl.identrust.com/DSTROOTCAX3CRL.crl | US | der | 896 b | whitelisted |
2960 | soundser.exe | POST | — | 177.225.175.199:80 | http://177.225.175.199/chunk/loadan/ | MX | — | — | malicious |
2564 | opera.exe | GET | 200 | 2.16.186.11:80 | http://ocsp.int-x3.letsencrypt.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBR%2B5mrncpqz%2FPiiIGRsFqEtYHEIXQQUqEpqYwR93brm0Tm3pkVl7%2FOo7KECEgSZ%2BYrdG3n%2BgdBgu9ysKfpA6w%3D%3D | unknown | der | 527 b | whitelisted |
2960 | soundser.exe | POST | — | 181.142.29.90:80 | http://181.142.29.90/cone/ | CO | — | — | malicious |
2564 | opera.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPJvUY%2Bsl%2Bj4yzQuAcL2oQno5fCgQUUWj%2FkK8CB3U8zNllZGKiErhZcjsCEAOXQPQlVpLtFek%2BmcpabOk%3D | US | der | 471 b | whitelisted |
2648 | soundser.exe | POST | 200 | 24.150.44.53:80 | http://24.150.44.53/enabled/ | CA | binary | 141 Kb | malicious |
2960 | soundser.exe | POST | — | 24.150.44.53:80 | http://24.150.44.53/guids/arizona/ringin/merge/ | CA | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2644 | chrome.exe | 172.217.22.78:443 | sb-ssl.google.com | Google Inc. | US | whitelisted |
2644 | chrome.exe | 172.217.22.68:443 | www.google.com | Google Inc. | US | whitelisted |
2564 | opera.exe | 82.145.215.40:443 | certs.opera.com | Opera Software AS | — | whitelisted |
2644 | chrome.exe | 216.58.206.3:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
2564 | opera.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2564 | opera.exe | 66.225.197.197:80 | crl4.digicert.com | CacheNetworks, Inc. | US | whitelisted |
2644 | chrome.exe | 172.217.18.3:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2644 | chrome.exe | 178.128.22.201:443 | nanayamfm.com | Forthnet | GR | unknown |
2644 | chrome.exe | 172.217.21.237:443 | accounts.google.com | Google Inc. | US | whitelisted |
2564 | opera.exe | 185.26.182.94:443 | sitecheck2.opera.com | Opera Software AS | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
nanayamfm.com |
| unknown |
accounts.google.com |
| shared |
sb-ssl.google.com |
| whitelisted |
www.google.com |
| malicious |
ssl.gstatic.com |
| whitelisted |
certs.opera.com |
| whitelisted |
crl4.digicert.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
sitecheck2.opera.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3384 | WScript.exe | Misc activity | SUSPICIOUS [PTsecurity] Cmd.Powershell.Download HTTP UserAgent (Win7) |
3384 | WScript.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3384 | WScript.exe | A Network Trojan was detected | ET CURRENT_EVENTS Likely Evil EXE download from MSXMLHTTP non-exe extension M2 |
3384 | WScript.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
2648 | soundser.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
2960 | soundser.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
2960 | soundser.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
8 ETPRO signatures available at the full report