| File name: | DiskInternals VMFS Recovery 4.8.zip |
| Full analysis: | https://app.any.run/tasks/d939f1b8-ac09-440d-9e07-6e84edb12e4d |
| Verdict: | Malicious activity |
| Analysis date: | January 29, 2021, 19:58:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 9F9CBA698B1E2F672B7520E7E74932C5 |
| SHA1: | 8756F22BF28ED91B8F8C63FC242CF0C54620DC6A |
| SHA256: | 60CBD5D77C9F57A867613801CC77C03B97EA5B3373EEEE2DD8FB700D4C406A38 |
| SSDEEP: | 12288:PjAjXK5tlHYsa9+yiMgp6wzZZ4rJjtu2w4Xem5m4BMDVl6JmwADA6pT:Pk0/4VIyiMXw9Z4rJjInk2Vl6JmwAjT |
MALICIOUS
Drops executable file immediately after starts
- DiskInternals VMFS Recovery 4.8.exe (PID: 3084)
- 7za.exe (PID: 2524)
- DiskInternals VMFS Recovery 4.8.exe (PID: 3036)
Application was dropped or rewritten from another process
- DiskInternals VMFS Recovery 4.8.exe (PID: 3036)
- DiskInternals VMFS Recovery 4.8.exe (PID: 3084)
- sihost.exe (PID: 3480)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 444)
- schtasks.exe (PID: 3392)
Uses Task Scheduler to run other applications
- sihost.exe (PID: 3480)
SUSPICIOUS
Executable content was dropped or overwritten
- DiskInternals VMFS Recovery 4.8.exe (PID: 3084)
- 7za.exe (PID: 2524)
- DiskInternals VMFS Recovery 4.8.tmp (PID: 2444)
- DiskInternals VMFS Recovery 4.8.exe (PID: 3036)
Reads Windows owner or organization settings
- DiskInternals VMFS Recovery 4.8.tmp (PID: 2444)
Reads the Windows organization settings
- DiskInternals VMFS Recovery 4.8.tmp (PID: 2444)
Creates files in the user directory
- DiskInternals VMFS Recovery 4.8.tmp (PID: 2444)
- sihost.exe (PID: 3480)
Drops a file with a compile date too recent
- 7za.exe (PID: 2524)
- DiskInternals VMFS Recovery 4.8.tmp (PID: 2444)
Executed via COM
- explorer.exe (PID: 3548)
Drops a file with too old compile date
- DiskInternals VMFS Recovery 4.8.tmp (PID: 2444)
INFO
Manual execution by user
- DiskInternals VMFS Recovery 4.8.exe (PID: 3084)
Application was dropped or rewritten from another process
- DiskInternals VMFS Recovery 4.8.tmp (PID: 184)
- 7za.exe (PID: 944)
- 7za.exe (PID: 2524)
- 7za.exe (PID: 3372)
- DiskInternals VMFS Recovery 4.8.tmp (PID: 2444)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2021:01:29 22:42:03 |
| ZipCRC: | 0xdc416bfb |
| ZipCompressedSize: | 686419 |
| ZipUncompressedSize: | 760290 |
| ZipFileName: | DiskInternals VMFS Recovery 4.8.exe |
Total processes
56
Monitored processes
14
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 184 | "C:\Users\admin\AppData\Local\Temp\is-Q868N.tmp\DiskInternals VMFS Recovery 4.8.tmp" /SL5="$40162,369896,121344,C:\Users\admin\Desktop\DiskInternals VMFS Recovery 4.8.exe" | C:\Users\admin\AppData\Local\Temp\is-Q868N.tmp\DiskInternals VMFS Recovery 4.8.tmp | — | DiskInternals VMFS Recovery 4.8.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 444 | "C:\Windows\system32\schtasks.exe" /Delete /tn "Microsoft\Windows\Windows Error Reporting\SysInfo" /f | C:\Windows\system32\schtasks.exe | — | sihost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 944 | "C:\Users\admin\AppData\Local\Temp\is-FGRJN.tmp\7za.exe" x "C:\Users\admin\AppData\Local\Temp\is-FGRJN.tmp\sub.res" -p"b1lig@n_vl" | C:\Users\admin\AppData\Local\Temp\is-FGRJN.tmp\7za.exe | — | DiskInternals VMFS Recovery 4.8.tmp | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7-Zip Standalone Console Exit code: 0 Version: 4.65 Modules
| |||||||||||||||
| 1596 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\DiskInternals VMFS Recovery 4.8.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2444 | "C:\Users\admin\AppData\Local\Temp\is-I89T9.tmp\DiskInternals VMFS Recovery 4.8.tmp" /SL5="$3017A,369896,121344,C:\Users\admin\Desktop\DiskInternals VMFS Recovery 4.8.exe" /SPAWNWND=$3017C /NOTIFYWND=$40162 | C:\Users\admin\AppData\Local\Temp\is-I89T9.tmp\DiskInternals VMFS Recovery 4.8.tmp | DiskInternals VMFS Recovery 4.8.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
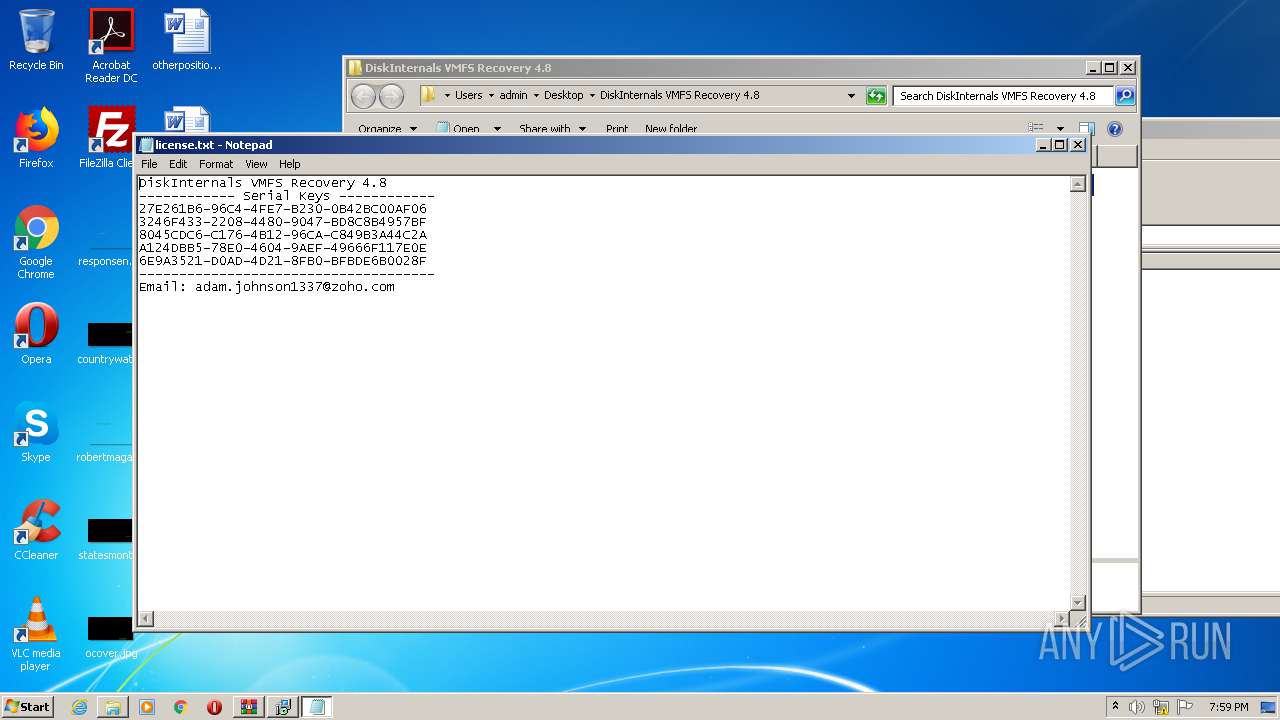
| 2456 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\DiskInternals VMFS Recovery 4.8\license.txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2524 | "C:\Users\admin\AppData\Local\Temp\is-FGRJN.tmp\7za.exe" x "C:\Users\admin\AppData\Local\Temp\is-FGRJN.tmp\form.res" -p"b1lig@n_vl" | C:\Users\admin\AppData\Local\Temp\is-FGRJN.tmp\7za.exe | DiskInternals VMFS Recovery 4.8.tmp | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7-Zip Standalone Console Exit code: 0 Version: 4.65 Modules
| |||||||||||||||
| 2684 | "explorer.exe" "C:\Users\admin\Desktop\DiskInternals VMFS Recovery 4.8" | C:\Windows\explorer.exe | — | DiskInternals VMFS Recovery 4.8.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3036 | "C:\Users\admin\Desktop\DiskInternals VMFS Recovery 4.8.exe" /SPAWNWND=$3017C /NOTIFYWND=$40162 | C:\Users\admin\Desktop\DiskInternals VMFS Recovery 4.8.exe | DiskInternals VMFS Recovery 4.8.tmp | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: Exit code: 0 Version: 29.64 Modules
| |||||||||||||||
| 3084 | "C:\Users\admin\Desktop\DiskInternals VMFS Recovery 4.8.exe" | C:\Users\admin\Desktop\DiskInternals VMFS Recovery 4.8.exe | explorer.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Exit code: 0 Version: 29.64 Modules
| |||||||||||||||
Total events
1 306
Read events
1 198
Write events
108
Delete events
0
Modification events
| (PID) Process: | (1596) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1596) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1596) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1596) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\DiskInternals VMFS Recovery 4.8.zip | |||
| (PID) Process: | (1596) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1596) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1596) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1596) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1596) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2444) DiskInternals VMFS Recovery 4.8.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 8C0900007407F33979F6D601 | |||
Executable files
5
Suspicious files
3
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1596 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1596.16690\DiskInternals VMFS Recovery 4.8.exe | — | |
MD5:— | SHA256:— | |||
| 2444 | DiskInternals VMFS Recovery 4.8.tmp | C:\Users\admin\AppData\Local\Temp\{F3BD1FDB-4CCD-4181-BF75-29E0599791C9}\is-06162.tmp | — | |
MD5:— | SHA256:— | |||
| 2444 | DiskInternals VMFS Recovery 4.8.tmp | C:\Users\admin\AppData\Local\Temp\{F3BD1FDB-4CCD-4181-BF75-29E0599791C9}\license.txt | — | |
MD5:— | SHA256:— | |||
| 3480 | sihost.exe | C:\Users\admin\AppData\Roaming\ToolSysHost\data.xml | — | |
MD5:— | SHA256:— | |||
| 2444 | DiskInternals VMFS Recovery 4.8.tmp | C:\Users\admin\AppData\Local\Temp\is-FGRJN.tmp\form.res | compressed | |
MD5:— | SHA256:— | |||
| 2444 | DiskInternals VMFS Recovery 4.8.tmp | C:\Users\admin\AppData\Local\Temp\is-FGRJN.tmp\7za.exe | executable | |
MD5:E92604E043F51C604B6D1AC3BCD3A202 | SHA256:FA252E501332B7486A972E7E471CF6915DAA681AF35C6AA102213921093EB2A3 | |||
| 944 | 7za.exe | C:\Users\admin\AppData\Local\Temp\is-FGRJN.tmp\sub.xml | xml | |
MD5:C047508A4A1F583B7ED31EC7B0DF9695 | SHA256:CD999BAA036D44D442FE43A541D69F04BA206C58938F3C22EC0F226493C63E35 | |||
| 2444 | DiskInternals VMFS Recovery 4.8.tmp | C:\Users\admin\AppData\Local\Temp\is-FGRJN.tmp\misc.res | compressed | |
MD5:4276E4182A04700263891F395FD74B65 | SHA256:436DB65389AFD9020211E47F28A090AB12A5D0E2AF5961BB6C491074F73E30D6 | |||
| 2444 | DiskInternals VMFS Recovery 4.8.tmp | C:\Users\admin\AppData\Roaming\ToolSysHost\sihost.exe.config | xml | |
MD5:C047508A4A1F583B7ED31EC7B0DF9695 | SHA256:CD999BAA036D44D442FE43A541D69F04BA206C58938F3C22EC0F226493C63E35 | |||
| 2444 | DiskInternals VMFS Recovery 4.8.tmp | C:\Users\admin\AppData\Local\Temp\is-FGRJN.tmp\sub.res | compressed | |
MD5:AE50AD46B7EF3517F5DF5EDF2B96443E | SHA256:F4A2B3FA7460606D58AD078D320AFCEAD400285304DC49E8F2BA3FA9800854DC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
2
DNS requests
2
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2444 | DiskInternals VMFS Recovery 4.8.tmp | POST | 200 | 142.250.186.174:80 | http://www.google-analytics.com/collect | US | image | 35 b | whitelisted |
2444 | DiskInternals VMFS Recovery 4.8.tmp | POST | 200 | 142.250.186.174:80 | http://www.google-analytics.com/collect | US | image | 35 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2444 | DiskInternals VMFS Recovery 4.8.tmp | 172.67.152.72:80 | avkit.org | — | US | suspicious |
2444 | DiskInternals VMFS Recovery 4.8.tmp | 142.250.186.174:80 | www.google-analytics.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.google-analytics.com |
| whitelisted |
avkit.org |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2444 | DiskInternals VMFS Recovery 4.8.tmp | Unknown Traffic | ET INFO Suspicious User-Agent (1 space) |
1 ETPRO signatures available at the full report