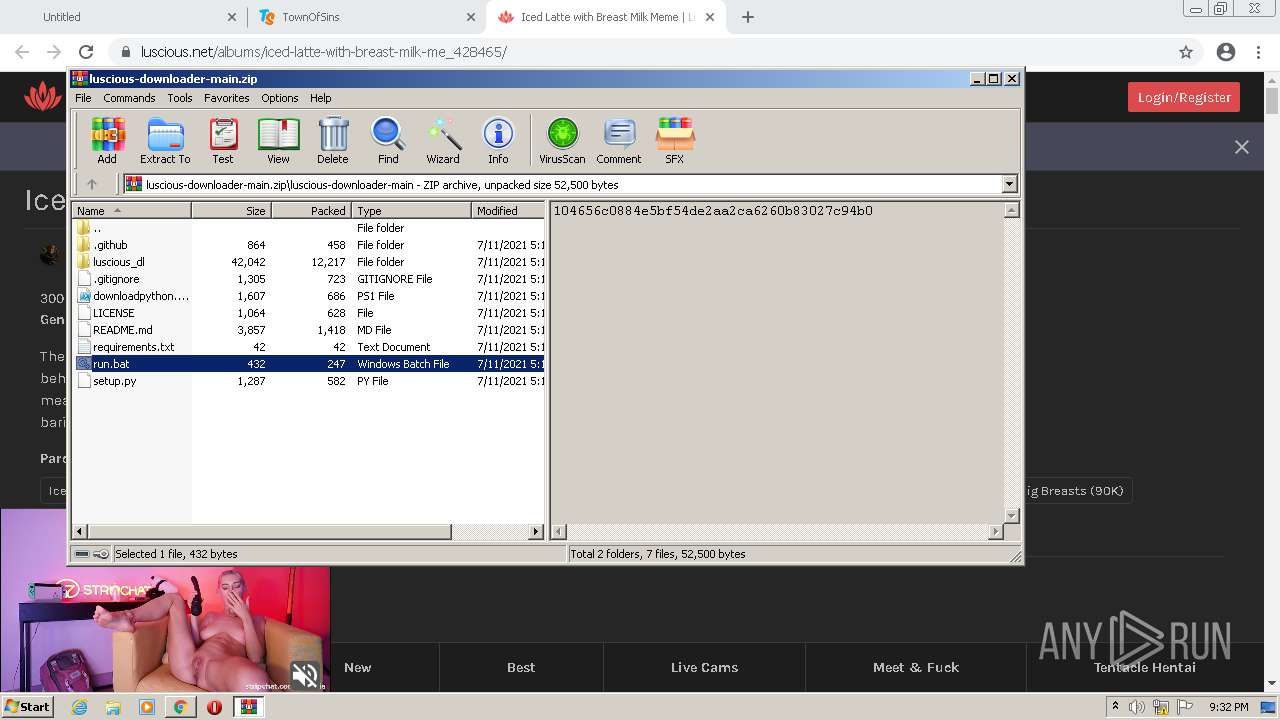
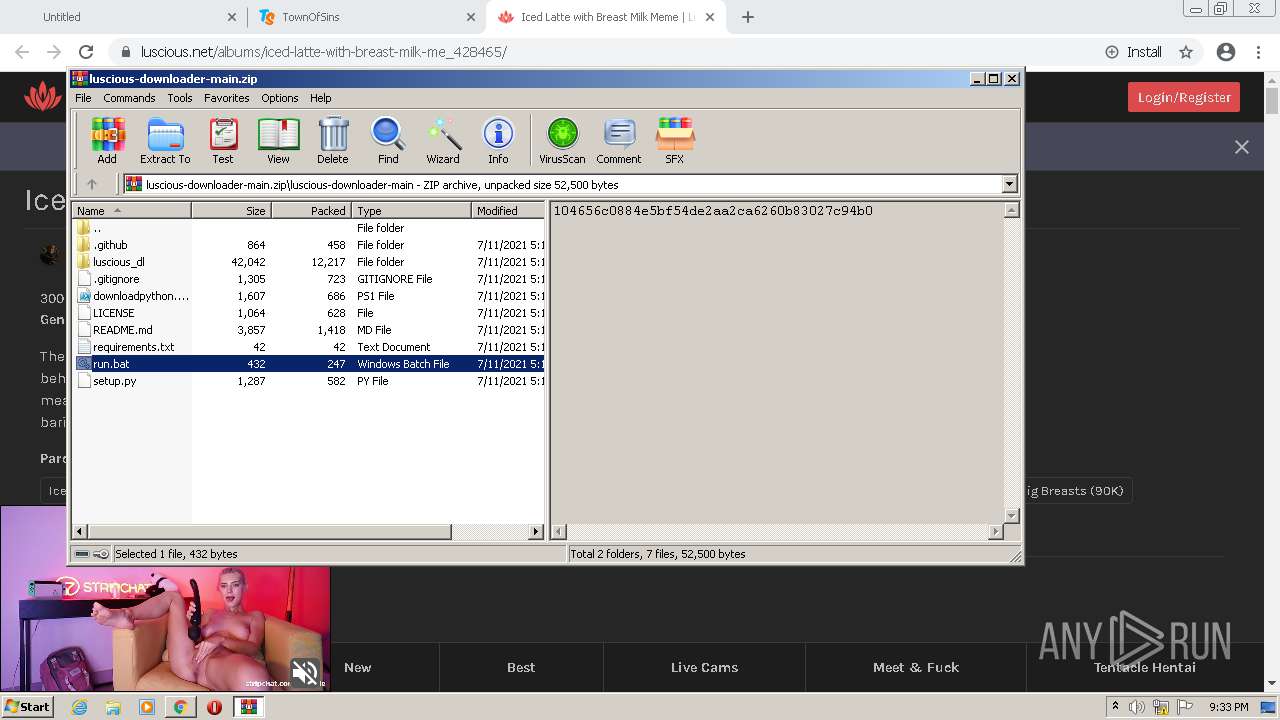
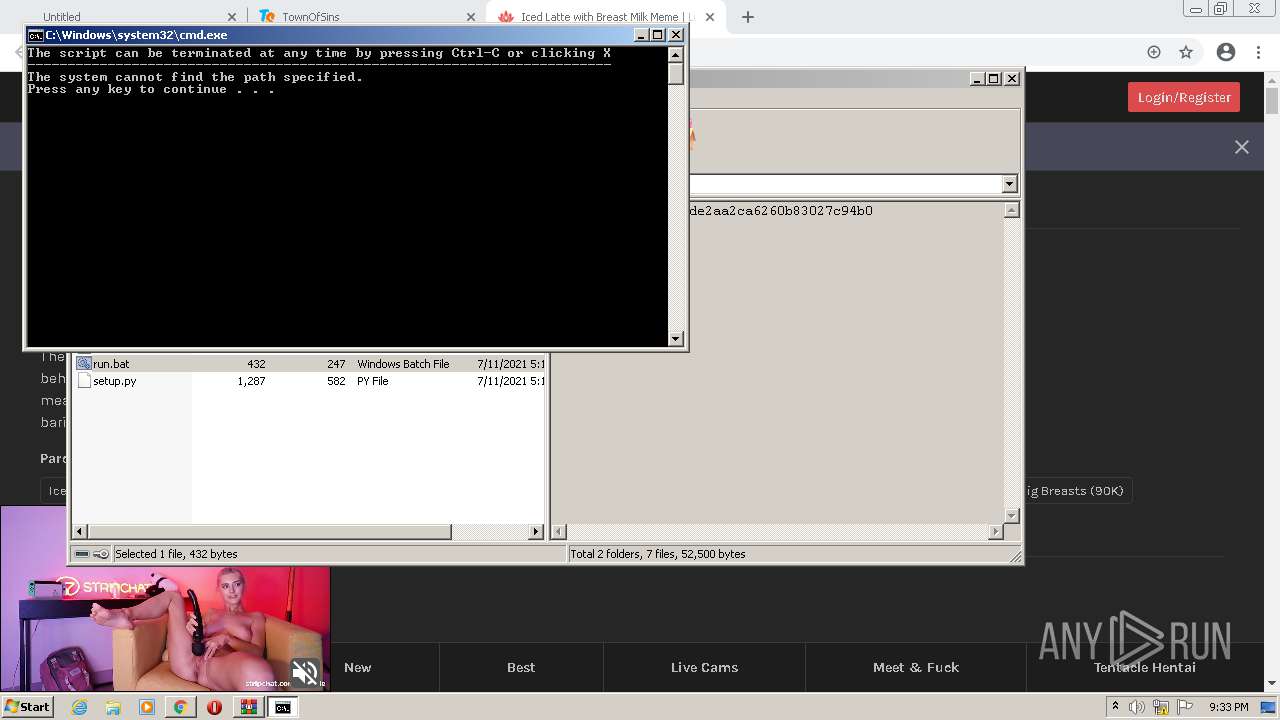
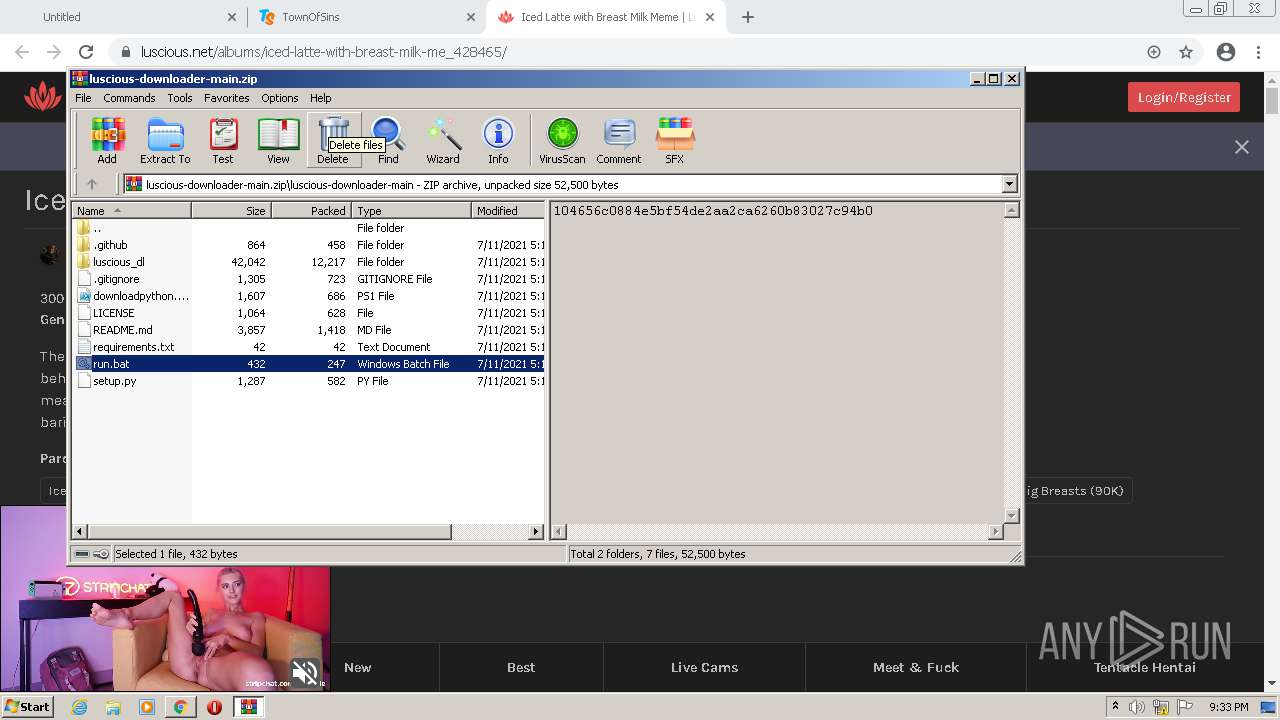
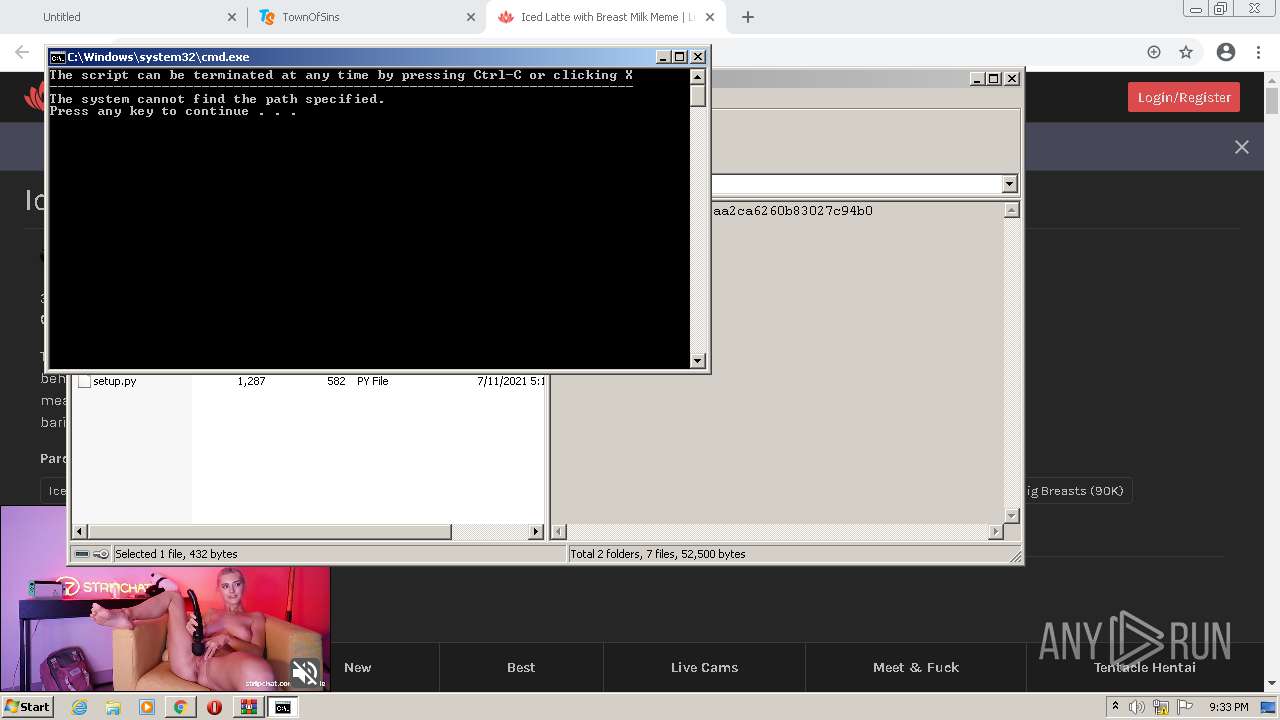
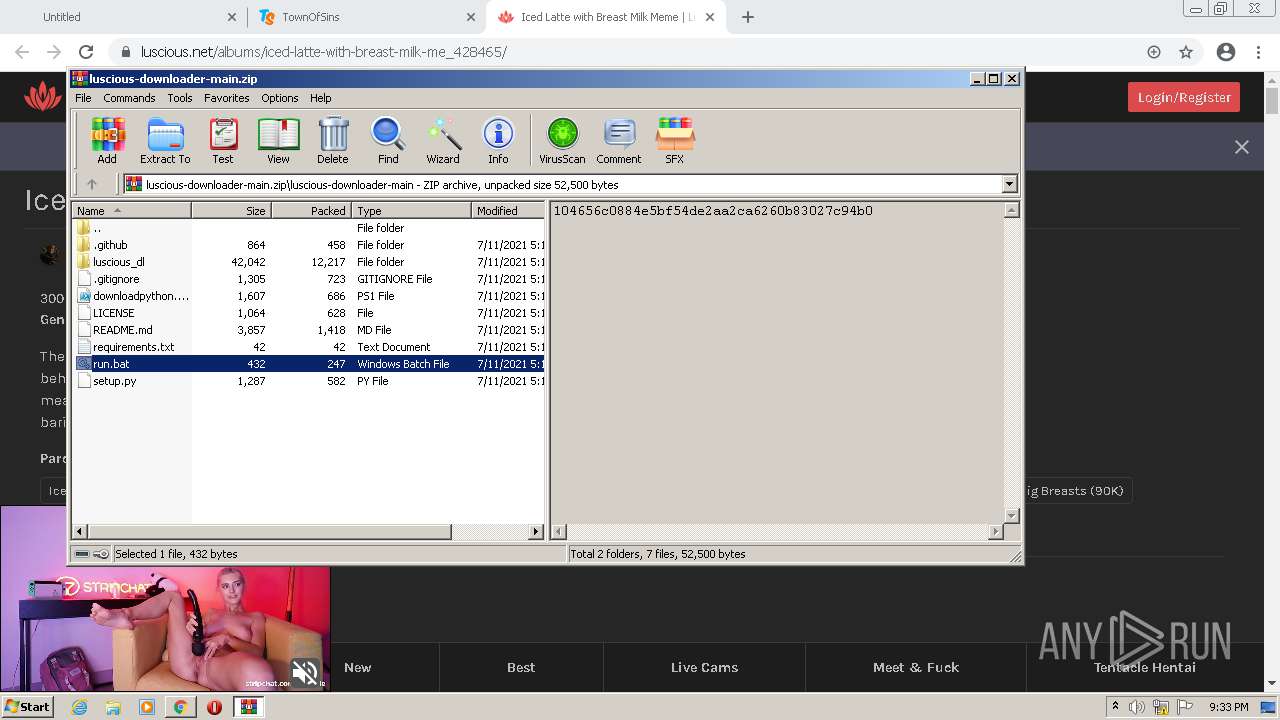
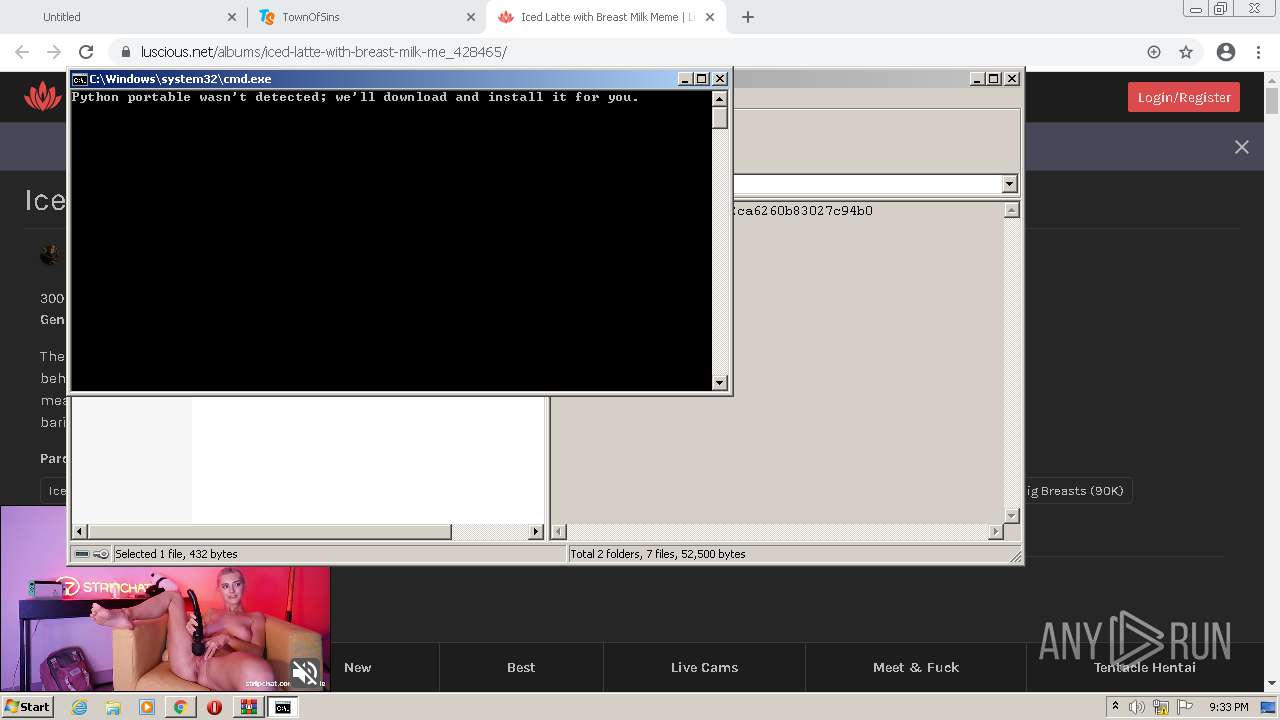
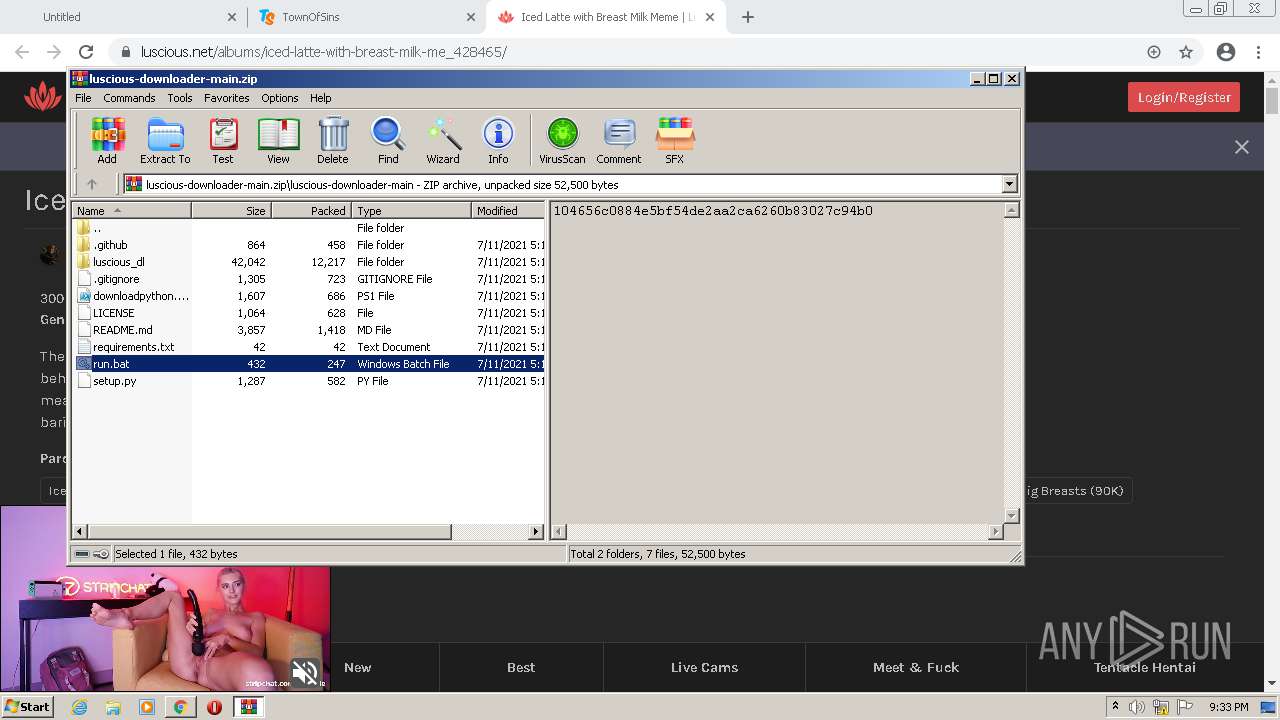
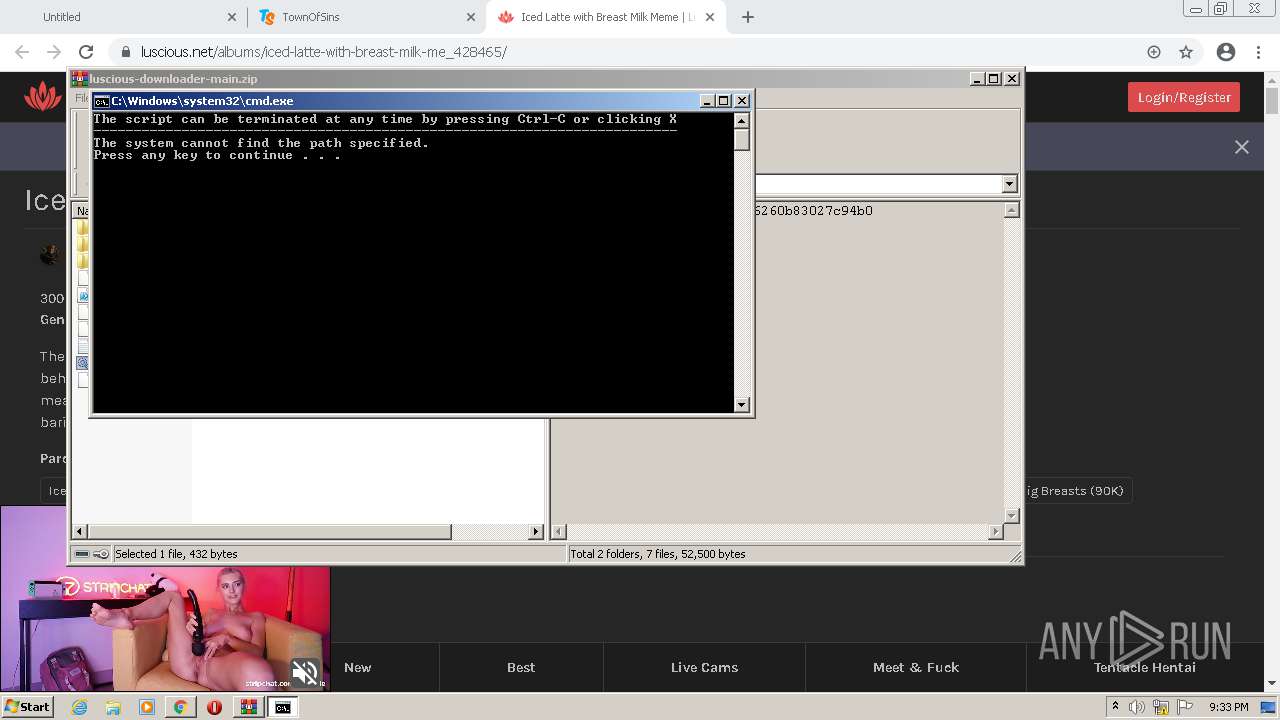
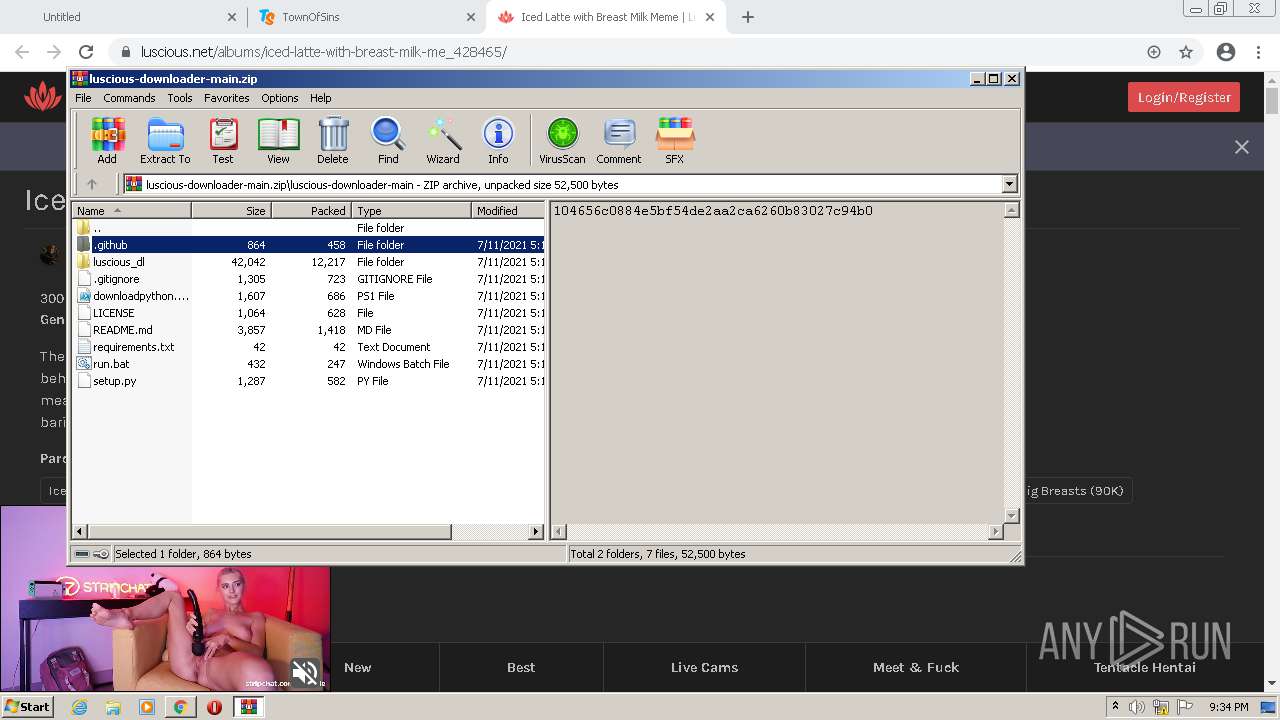
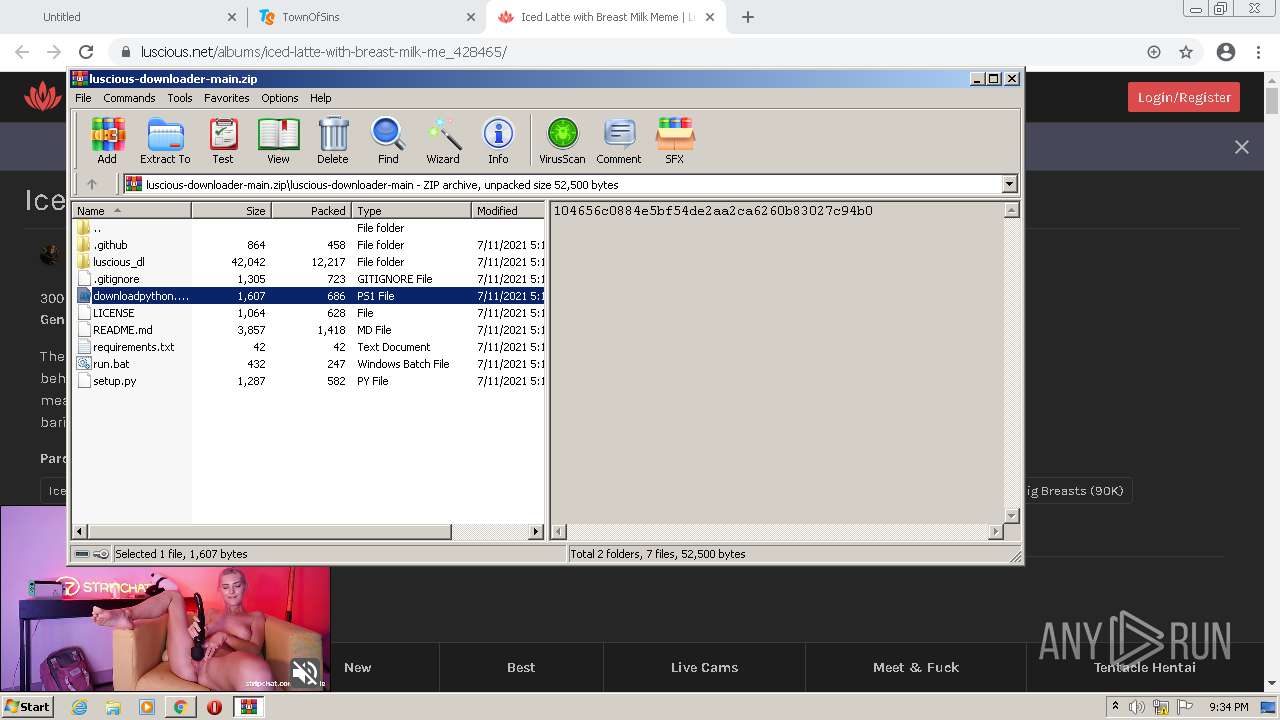
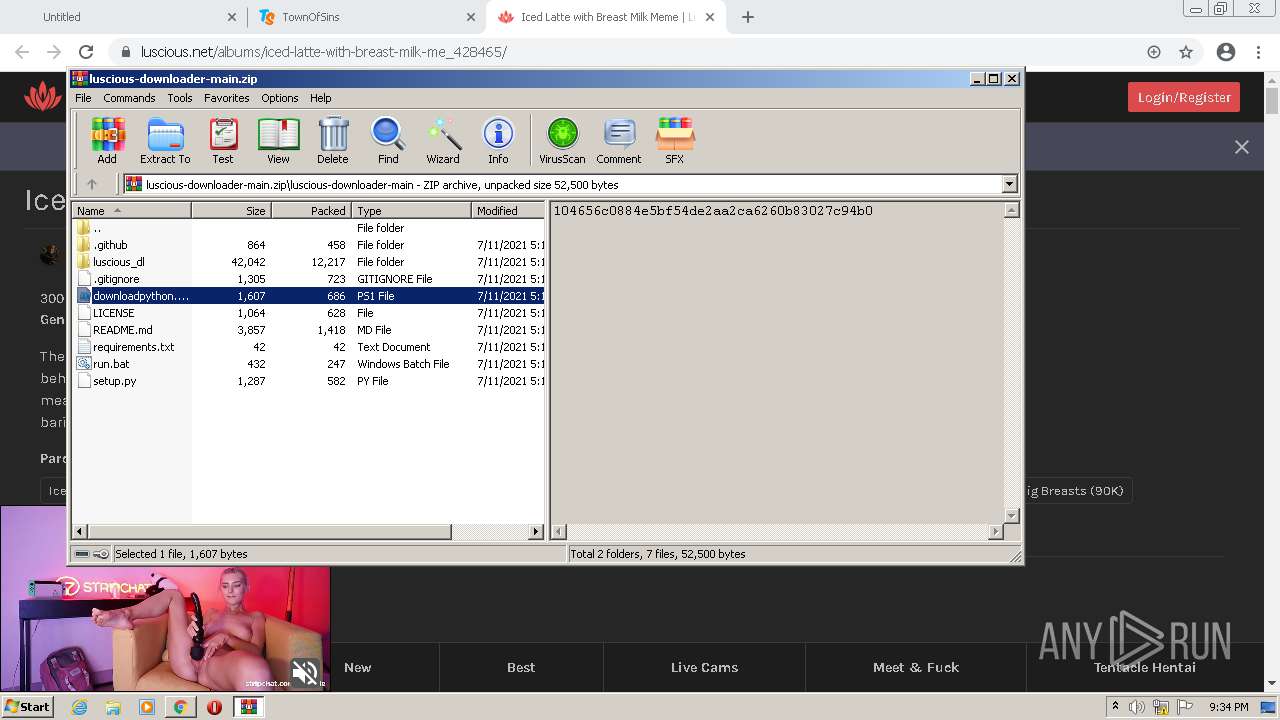
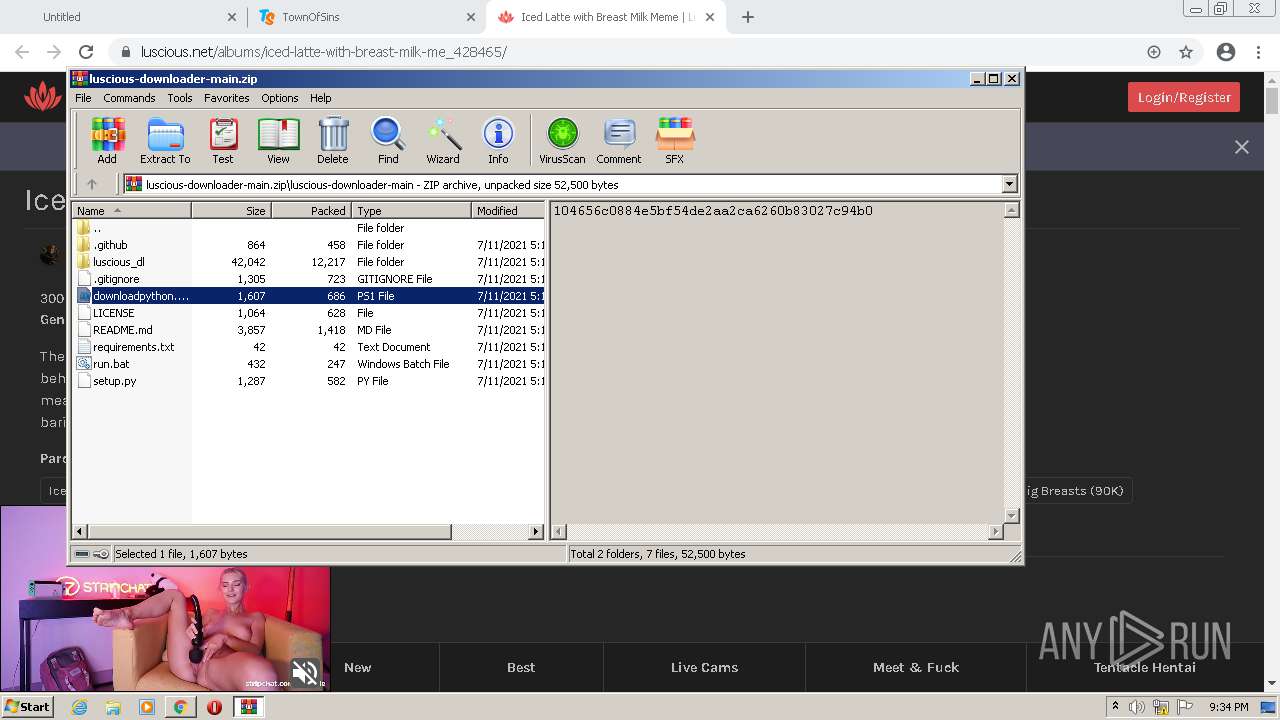
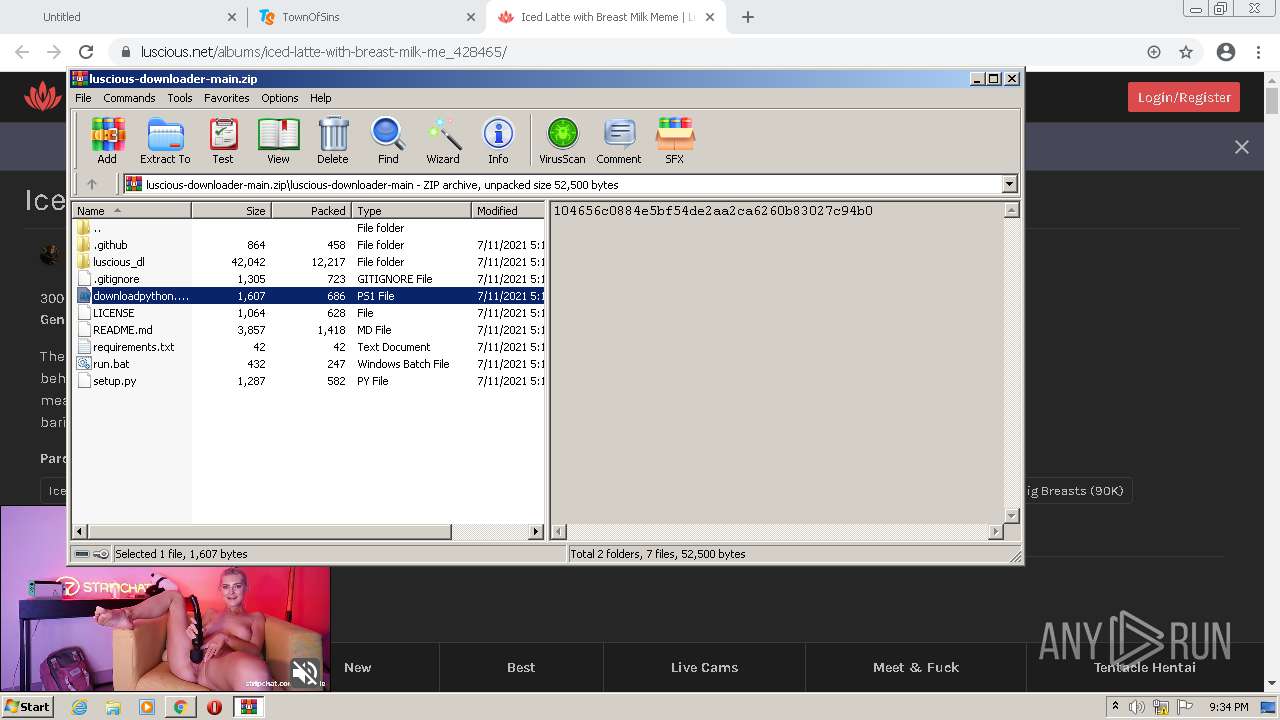
| URL: | https://github.com/Lucas8x/luscious-downloader/archive/main.zip |
| Full analysis: | https://app.any.run/tasks/1652161f-b66b-43ca-b922-49891c7ecdb0 |
| Verdict: | Malicious activity |
| Analysis date: | October 14, 2021, 20:31:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 3D6064155F8BB6D48006BAB44CF2B453 |
| SHA1: | 2B4E570B9198853EEBA953B57B5F981A8086088F |
| SHA256: | 60BC719C3CAB213001F4A00FA2674740DAEA7AEFA6C7157643A5F1C1730314D8 |
| SSDEEP: | 3:N8tEdhWuQW8JLsXLwLc:2uWuYaw4 |
MALICIOUS
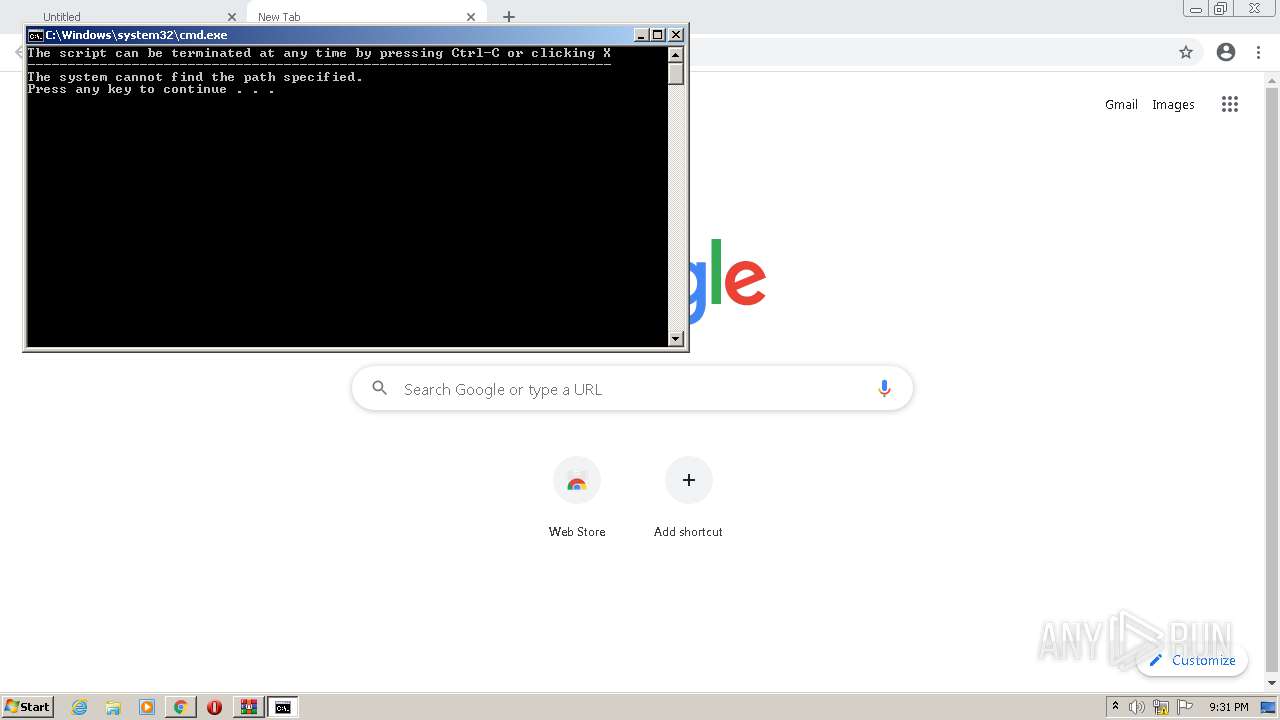
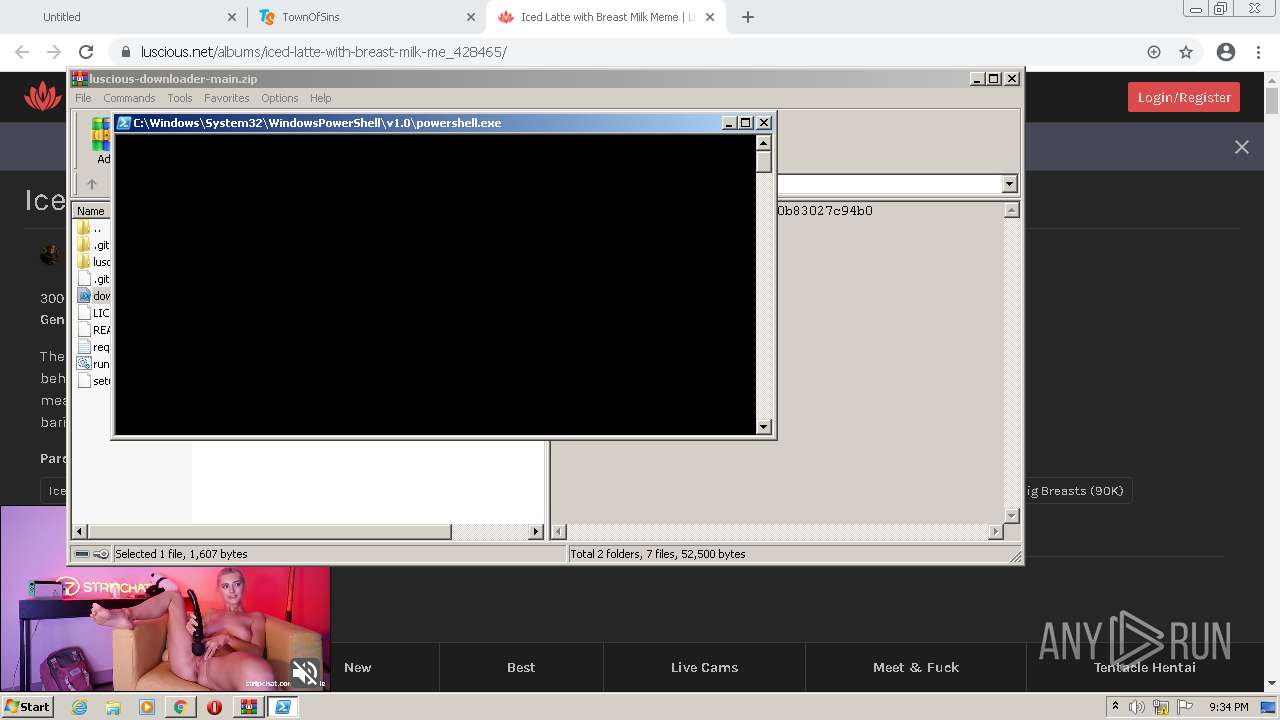
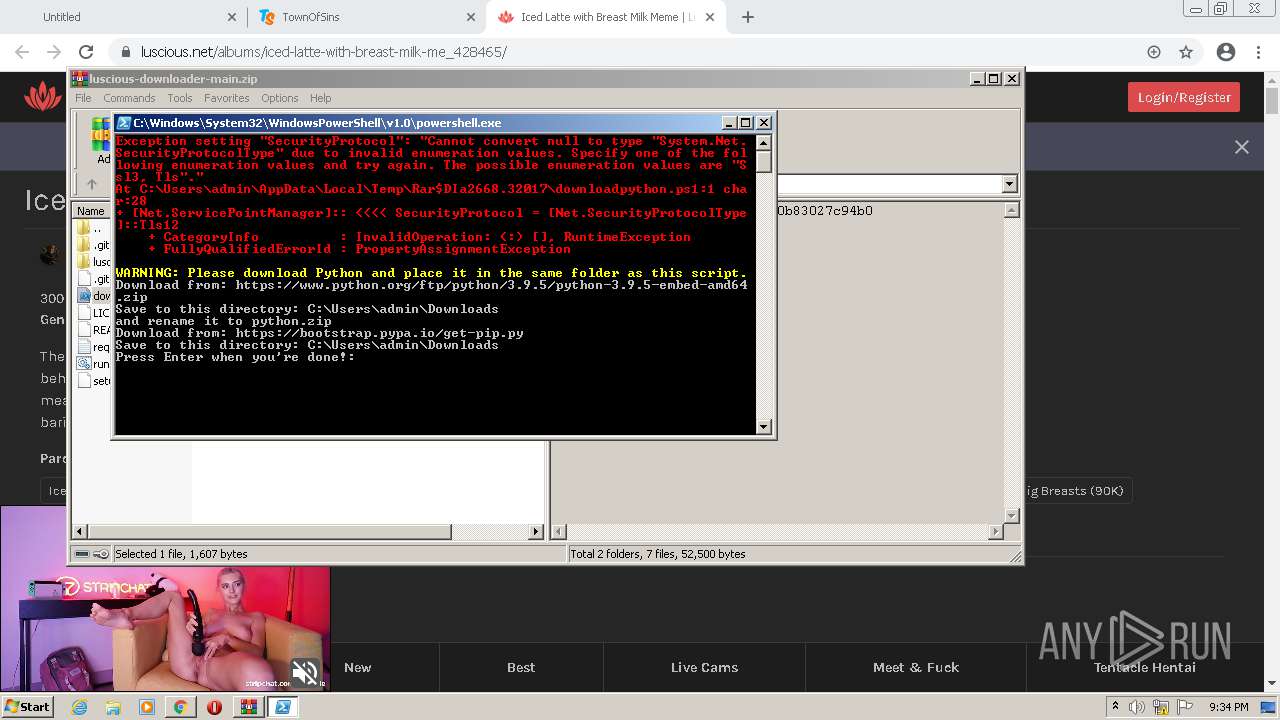
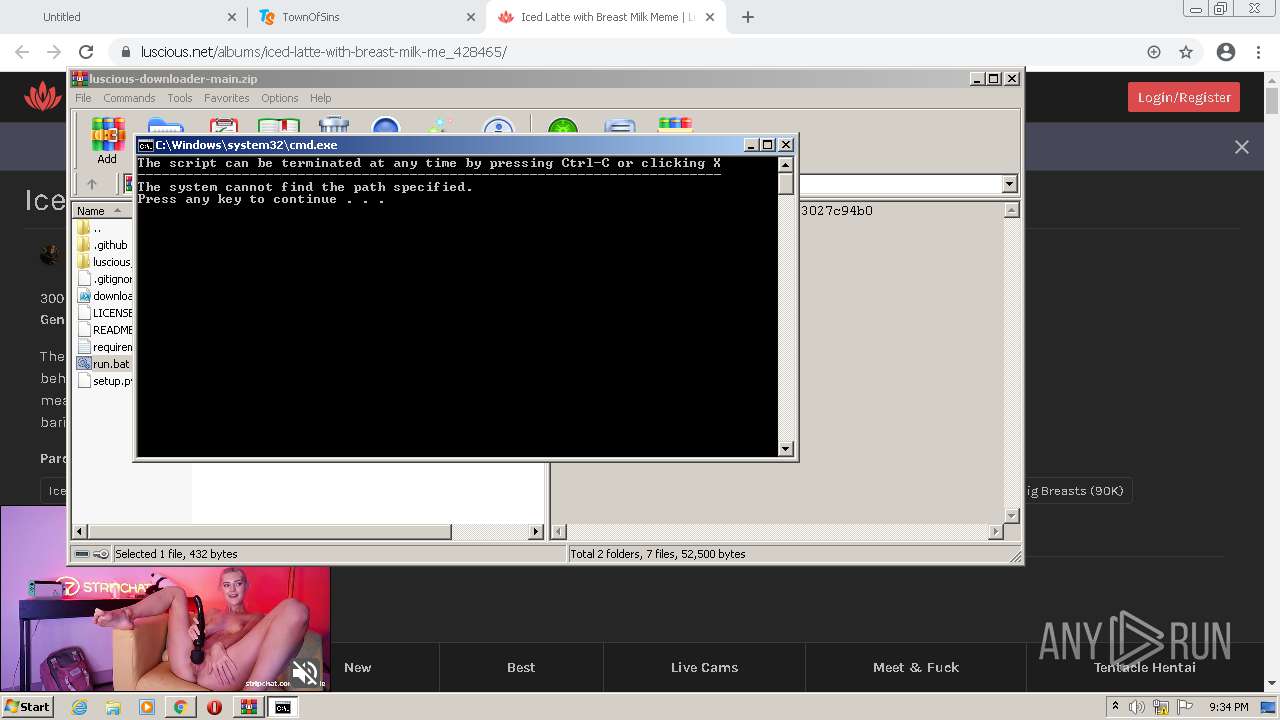
Executes PowerShell scripts
- cmd.exe (PID: 3076)
- cmd.exe (PID: 1336)
- cmd.exe (PID: 3060)
- cmd.exe (PID: 716)
- cmd.exe (PID: 1380)
- cmd.exe (PID: 2492)
SUSPICIOUS
Reads the computer name
- WinRAR.exe (PID: 2668)
- powershell.exe (PID: 3368)
- powershell.exe (PID: 3744)
- powershell.exe (PID: 3804)
- powershell.exe (PID: 4068)
- powershell.exe (PID: 3124)
- powershell.exe (PID: 272)
- powershell.exe (PID: 3588)
Checks supported languages
- cmd.exe (PID: 3076)
- powershell.exe (PID: 3368)
- WinRAR.exe (PID: 2668)
- cmd.exe (PID: 1336)
- powershell.exe (PID: 4068)
- powershell.exe (PID: 3804)
- powershell.exe (PID: 3744)
- cmd.exe (PID: 3060)
- cmd.exe (PID: 716)
- cmd.exe (PID: 1380)
- powershell.exe (PID: 3124)
- powershell.exe (PID: 272)
- cmd.exe (PID: 2492)
- powershell.exe (PID: 3588)
Reads the date of Windows installation
- powershell.exe (PID: 3368)
- powershell.exe (PID: 4068)
- powershell.exe (PID: 3744)
- powershell.exe (PID: 3804)
- powershell.exe (PID: 3124)
- powershell.exe (PID: 272)
- powershell.exe (PID: 3588)
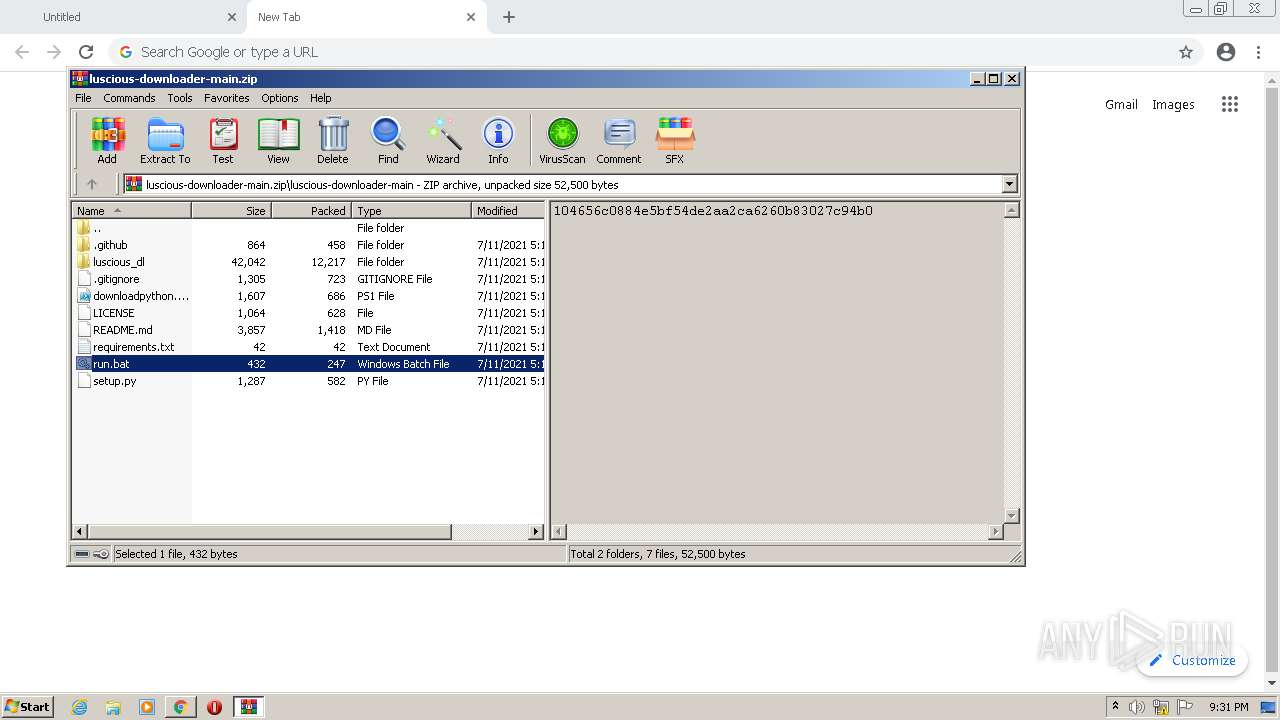
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 2668)
Creates files in the user directory
- powershell.exe (PID: 3368)
- powershell.exe (PID: 4068)
- powershell.exe (PID: 3744)
- powershell.exe (PID: 3804)
- powershell.exe (PID: 3124)
- powershell.exe (PID: 272)
- powershell.exe (PID: 3588)
Executes PowerShell scripts
- WinRAR.exe (PID: 2668)
INFO
Reads the computer name
- chrome.exe (PID: 1268)
- chrome.exe (PID: 3612)
- chrome.exe (PID: 188)
- chrome.exe (PID: 3824)
- chrome.exe (PID: 4004)
- chrome.exe (PID: 4092)
- chrome.exe (PID: 3084)
- chrome.exe (PID: 3536)
- chrome.exe (PID: 3092)
- chrome.exe (PID: 3992)
Checks supported languages
- chrome.exe (PID: 4036)
- chrome.exe (PID: 1268)
- chrome.exe (PID: 3184)
- chrome.exe (PID: 188)
- chrome.exe (PID: 3612)
- chrome.exe (PID: 2980)
- chrome.exe (PID: 4004)
- chrome.exe (PID: 3392)
- chrome.exe (PID: 4092)
- chrome.exe (PID: 3988)
- chrome.exe (PID: 3824)
- chrome.exe (PID: 1292)
- chrome.exe (PID: 576)
- chrome.exe (PID: 3084)
- chrome.exe (PID: 3536)
- chrome.exe (PID: 3412)
- chrome.exe (PID: 2820)
- chrome.exe (PID: 3912)
- chrome.exe (PID: 3704)
- chrome.exe (PID: 2436)
- chrome.exe (PID: 1352)
- chrome.exe (PID: 3092)
- chrome.exe (PID: 1244)
- chrome.exe (PID: 3412)
- chrome.exe (PID: 1184)
- chrome.exe (PID: 3264)
- chrome.exe (PID: 3080)
- chrome.exe (PID: 2508)
- chrome.exe (PID: 2248)
- chrome.exe (PID: 636)
- chrome.exe (PID: 3992)
- chrome.exe (PID: 964)
- NOTEPAD.EXE (PID: 880)
Application launched itself
- chrome.exe (PID: 1268)
Reads the hosts file
- chrome.exe (PID: 1268)
- chrome.exe (PID: 3612)
Reads settings of System Certificates
- chrome.exe (PID: 3612)
Reads the date of Windows installation
- chrome.exe (PID: 3536)
Dropped object may contain Bitcoin addresses
- chrome.exe (PID: 1268)
Checks Windows Trust Settings
- powershell.exe (PID: 272)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
91
Monitored processes
47
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1048,8207355896192838427,11164587123431621803,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgACAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --mojo-platform-channel-handle=1044 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
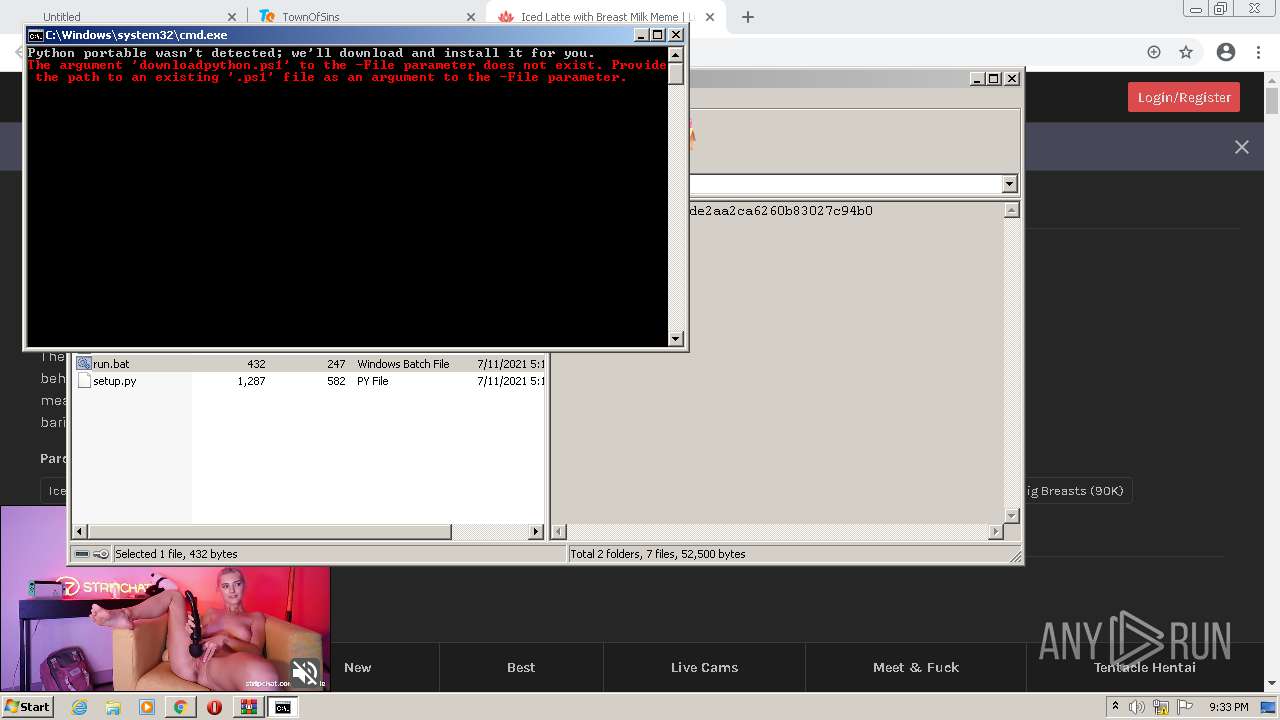
| 272 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "-file" "C:\Users\admin\AppData\Local\Temp\Rar$DIa2668.32017\downloadpython.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 3221225786 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 576 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1048,8207355896192838427,11164587123431621803,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2604 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 636 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1048,8207355896192838427,11164587123431621803,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=27 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2284 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
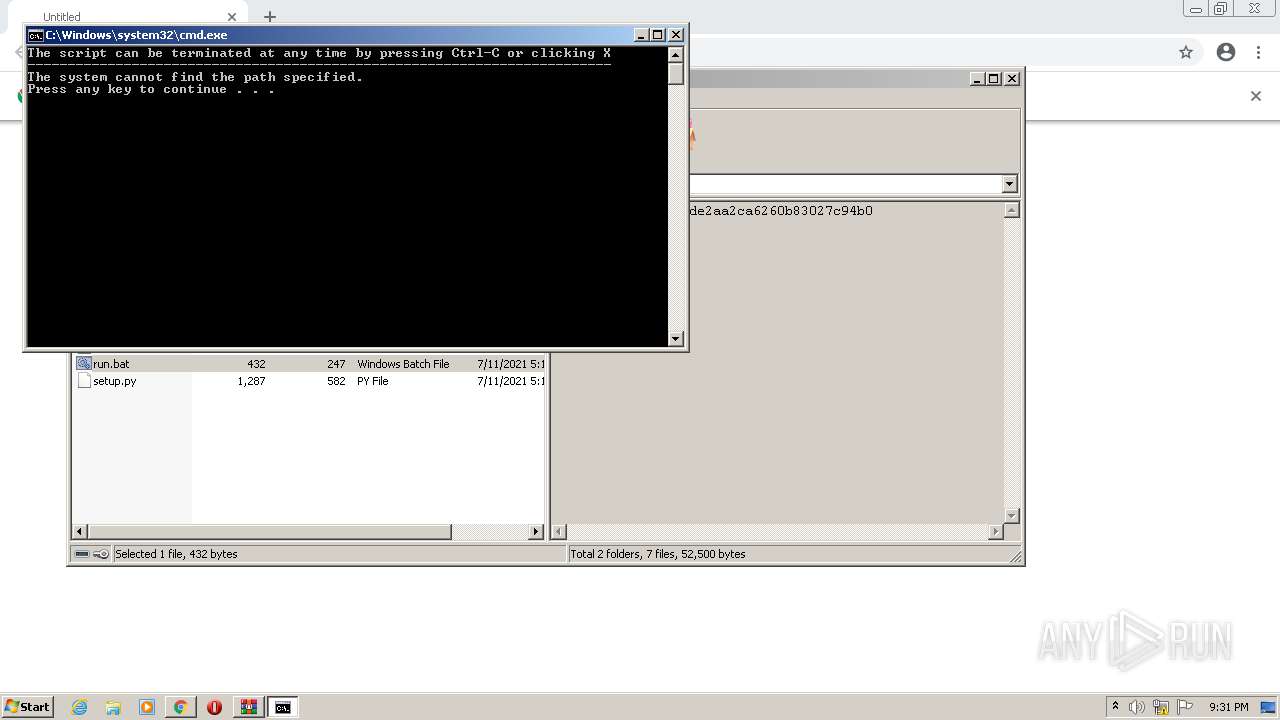
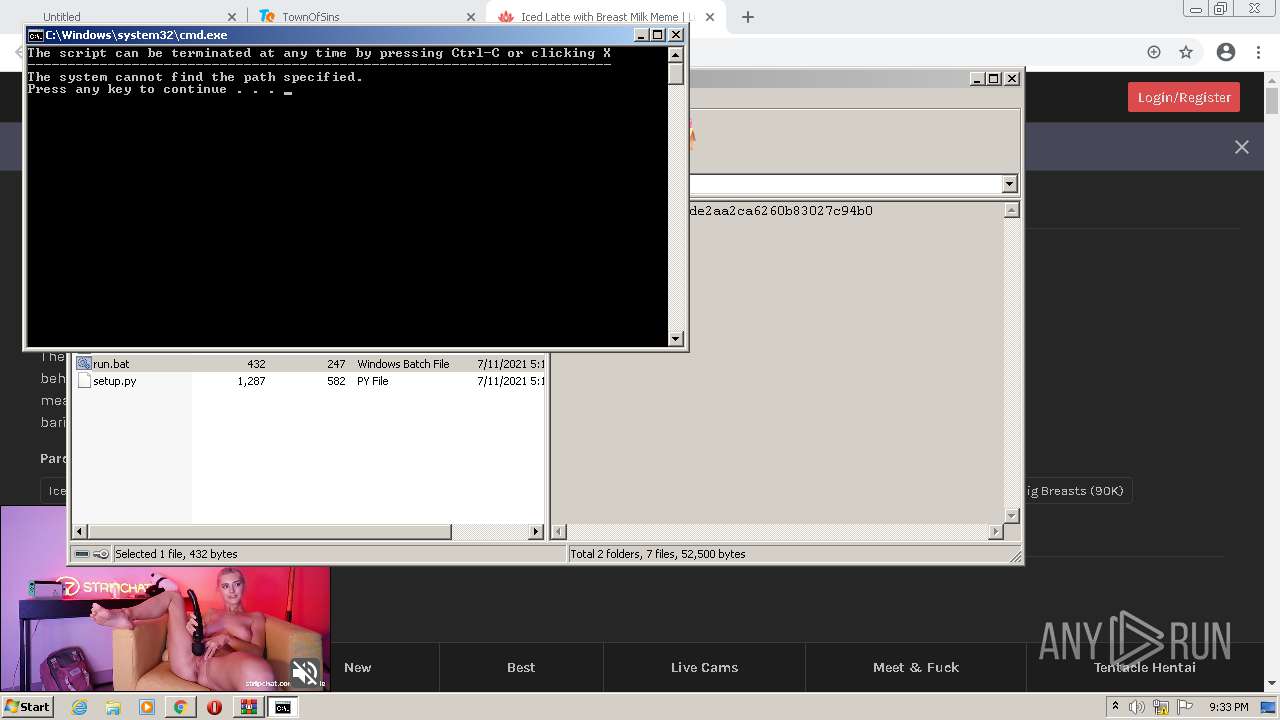
| 716 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$DIa2668.26410\run.bat" " | C:\Windows\system32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
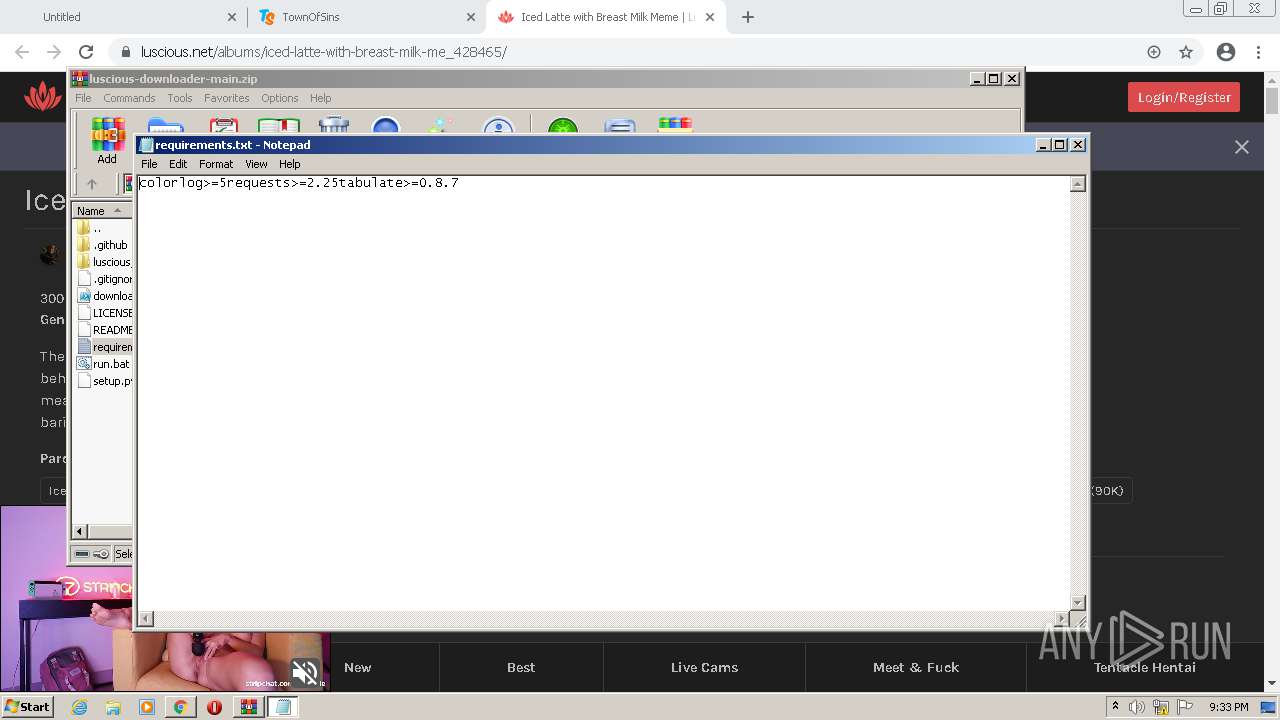
| 880 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIa2668.28824\requirements.txt | C:\Windows\system32\NOTEPAD.EXE | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 964 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1048,8207355896192838427,11164587123431621803,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=29 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2808 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1184 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1048,8207355896192838427,11164587123431621803,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=26 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3176 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1244 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1048,8207355896192838427,11164587123431621803,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3032 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1268 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --disk-cache-dir=null --disk-cache-size=1 --media-cache-size=1 --disable-gpu-shader-disk-cache --disable-background-networking "https://github.com/Lucas8x/luscious-downloader/archive/main.zip" | C:\Program Files\Google\Chrome\Application\chrome.exe | Explorer.EXE | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
25 960
Read events
25 433
Write events
521
Delete events
6
Modification events
| (PID) Process: | (1268) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1268) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1268) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (1268) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (1268) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1268) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (1268) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (1268) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (1268) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
| (PID) Process: | (1268) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_installdate |
Value: 0 | |||
Executable files
0
Suspicious files
213
Text files
141
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1268 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-6168938A-4F4.pma | — | |
MD5:— | SHA256:— | |||
| 1268 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Preferences | text | |
MD5:— | SHA256:— | |||
| 1268 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\659b4d5c-b2f0-4b39-ab4c-86607dd590e8.tmp | text | |
MD5:— | SHA256:— | |||
| 4036 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\CrashpadMetrics.pma | binary | |
MD5:03C4F648043A88675A920425D824E1B3 | SHA256:F91DBB7C64B4582F529C968C480D2DCE1C8727390482F31E4355A27BB3D9B450 | |||
| 1268 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF93d1c.TMP | text | |
MD5:936EB7280DA791E6DD28EF3A9B46D39C | SHA256:CBAF2AFD831B32F6D1C12337EE5D2F090D6AE1F4DCB40B08BEF49BF52AD9721F | |||
| 1268 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:5BD3C311F2136A7A88D3E197E55CF902 | SHA256:FA331915E1797E59979A3E4BCC2BD0D3DEAA039B94D4DB992BE251FD02A224B9 | |||
| 1268 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:00046F773EFDD3C8F8F6D0F87A2B93DC | SHA256:593EDE11D17AF7F016828068BCA2E93CF240417563FB06DC8A579110AEF81731 | |||
| 1268 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF93d1c.TMP | text | |
MD5:64AD8ED3E666540337BA541C549F72F7 | SHA256:BECBDB08B5B37D203A85F2E974407334053BB1D2270F0B3C9A4DB963896F2206 | |||
| 1268 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:8FF312A95D60ED89857FEB720D80D4E1 | SHA256:946A57FAFDD28C3164D5AB8AB4971B21BD5EC5BFFF7554DBF832CB58CC37700B | |||
| 1268 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:9C016064A1F864C8140915D77CF3389A | SHA256:0E7265D4A8C16223538EDD8CD620B8820611C74538E420A88E333BE7F62AC787 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
134
DNS requests
72
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
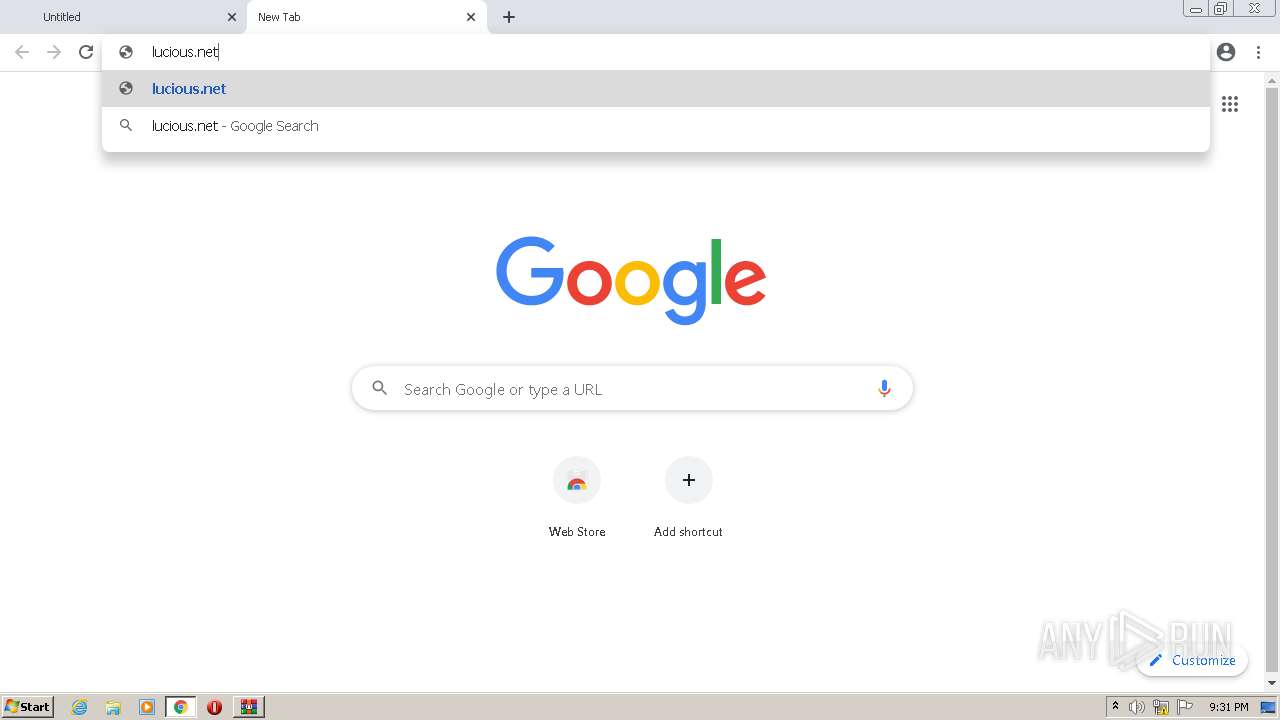
3612 | chrome.exe | GET | 302 | 104.219.168.162:80 | http://lucious.net/ | US | — | — | suspicious |
852 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvODZmQUFYS2VOaGowdjdSeVBvWFBSTDIxdw/1.0.0.9_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | US | — | — | whitelisted |
3612 | chrome.exe | GET | 301 | 104.26.2.49:80 | http://luscious.net/ | US | — | — | whitelisted |
3612 | chrome.exe | GET | 200 | 199.59.242.153:80 | http://ww6.lucious.net/js/parking.2.72.0.js | US | html | 18.9 Kb | malicious |
852 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adtxiggt2hkfqk7tbrhpj3pefoya_2021.9.27.1142/ggkkehgbnfjpeggfpleeakpidbkibbmn_2021.9.27.1142_all_acb6aquodb2erwqb72y757llqyza.crx3 | US | crx | 2.81 Kb | whitelisted |
3612 | chrome.exe | POST | 200 | 199.59.242.153:80 | http://ww6.lucious.net/_fd | US | text | 2.63 Kb | malicious |
3612 | chrome.exe | GET | 200 | 199.59.242.153:80 | http://ww6.lucious.net/ | US | html | 1.08 Kb | malicious |
852 | svchost.exe | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvODZmQUFYS2VOaGowdjdSeVBvWFBSTDIxdw/1.0.0.9_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | US | crx | 2.81 Kb | whitelisted |
3612 | chrome.exe | GET | 200 | 199.59.242.153:80 | http://ww6.lucious.net/px.gif?ch=2&rn=0.6200269423470322 | US | image | 42 b | malicious |
3612 | chrome.exe | GET | 200 | 199.59.242.153:80 | http://ww6.lucious.net/px.gif?ch=1&rn=0.6200269423470322 | US | image | 42 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3612 | chrome.exe | 142.250.185.110:443 | sb-ssl.google.com | Google Inc. | US | whitelisted |
3612 | chrome.exe | 172.217.23.99:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
1936 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | — | US | whitelisted |
3612 | chrome.exe | 142.250.185.106:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3612 | chrome.exe | 216.58.212.131:443 | www.gstatic.com | Google Inc. | US | whitelisted |
3612 | chrome.exe | 142.250.185.132:443 | www.google.com | Google Inc. | US | whitelisted |
— | — | 216.58.212.131:443 | www.gstatic.com | Google Inc. | US | whitelisted |
— | — | 142.250.185.106:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3612 | chrome.exe | 142.250.185.142:443 | apis.google.com | Google Inc. | US | whitelisted |
3612 | chrome.exe | 142.250.184.195:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clients2.google.com |
| whitelisted |
github.com |
| malicious |
accounts.google.com |
| shared |
codeload.github.com |
| whitelisted |
sb-ssl.google.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.google.com |
| malicious |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3612 | chrome.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |
3612 | chrome.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |