| File name: | ActivationAcronisTI(H).exe |
| Full analysis: | https://app.any.run/tasks/95f34dea-c24a-4e1c-be15-f456427c9f89 |
| Verdict: | Malicious activity |
| Analysis date: | March 26, 2019, 12:13:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 7CB5B869FCD68B223E98F84041E960F2 |
| SHA1: | A1113A140F2A20E557B0CD864BB7AE21DC5391CF |
| SHA256: | 60A0BFE0EBBB77E0412002AEAB59CA042D9114BD2D670C651AC498FBA42345AB |
| SSDEEP: | 98304:rOkDWFRToJ1n7r4LSqipo9mf1x6U0am0vLk:rOUWHgx7OSHKAf1E5Oo |
MALICIOUS
No malicious indicators.SUSPICIOUS
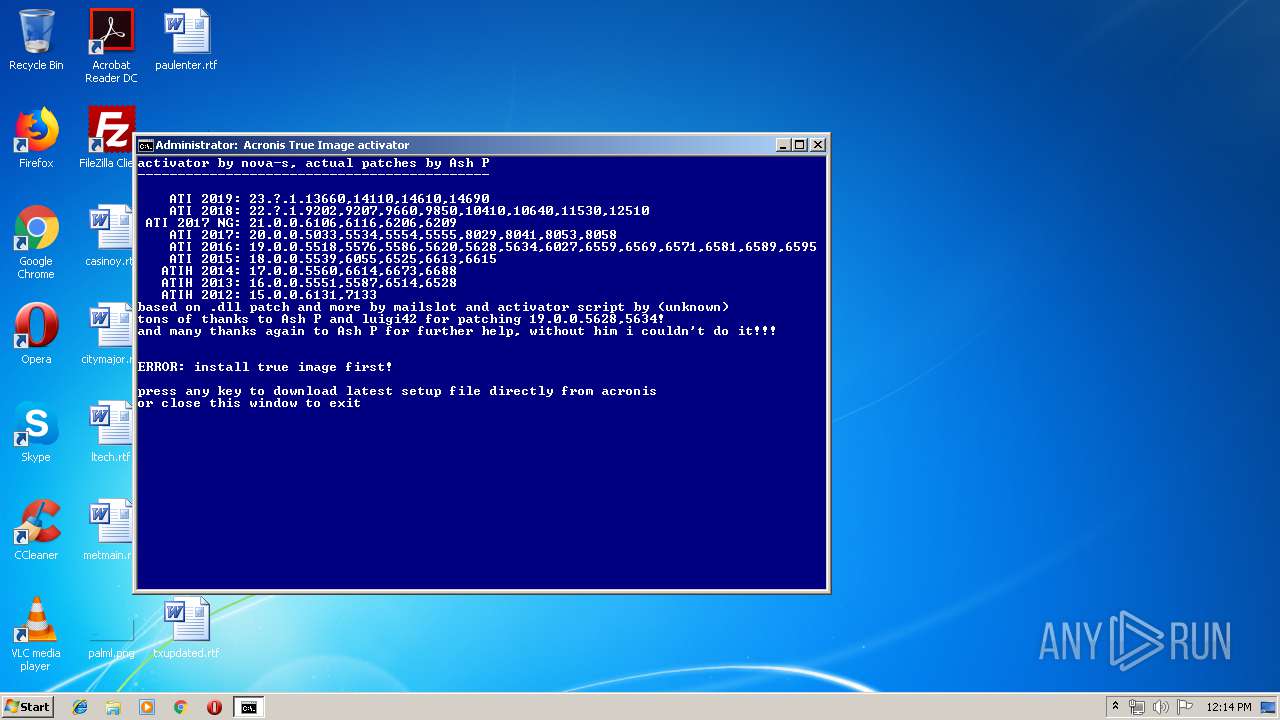
Starts CMD.EXE for commands execution
- ActivationAcronisTI(H).exe (PID: 1892)
- cmd.exe (PID: 2348)
Checks Windows language
- reg.exe (PID: 1524)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 2248)
- cmd.exe (PID: 2632)
Checks supported languages
- reg.exe (PID: 1524)
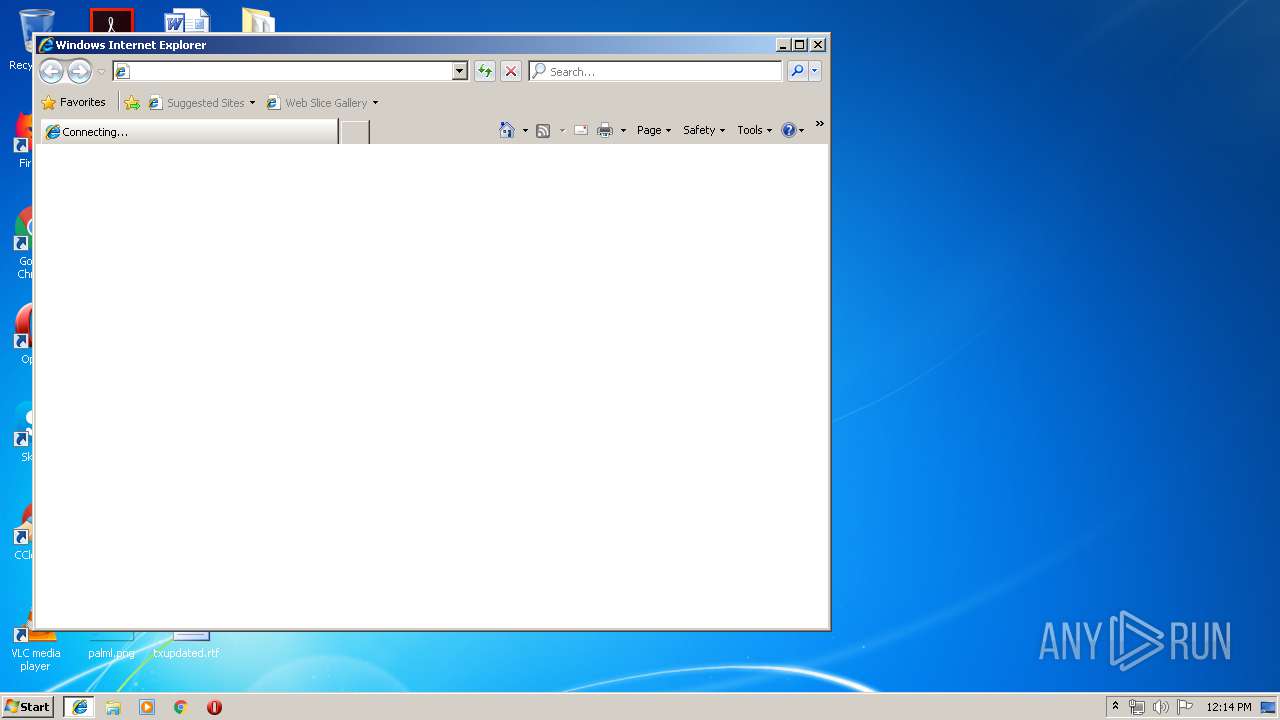
Starts Internet Explorer
- cmd.exe (PID: 2348)
Executable content was dropped or overwritten
- ActivationAcronisTI(H).exe (PID: 1892)
INFO
Changes internet zones settings
- iexplore.exe (PID: 2448)
Application launched itself
- iexplore.exe (PID: 2448)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:12:31 01:38:32+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 87040 |
| InitializedDataSize: | 20480 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1596f |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 23.4.1.14690 |
| ProductVersionNumber: | 23.4.1.14690 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| CompanyName: | not by Acronis |
| FileDescription: | activates build 23.4.1.14690 and previous |
| FileVersion: | 1, 0, 0, 0 |
| InternalName: | Acronis True Image 2019 Activator |
| LegalCopyright: | not by Acronis |
| OriginalFileName: | Acronis True Image 2019 Activator |
| PrivateBuild: | - |
| ProductName: | Acronis True Image 2019 Activator |
| ProductVersion: | 23, 4, 1,14690 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 31-Dec-2012 00:38:32 |
| Detected languages: |
|
| CompanyName: | not by Acronis |
| FileDescription: | activates build 23.4.1.14690 and previous |
| FileVersion: | 1, 0, 0, 0 |
| InternalName: | Acronis True Image 2019 Activator |
| LegalCopyright: | not by Acronis |
| OriginalFilename: | Acronis True Image 2019 Activator |
| PrivateBuild: | - |
| ProductName: | Acronis True Image 2019 Activator |
| ProductVersion: | 23, 4, 1,14690 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0060 |
| Pages in file: | 0x0001 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000060 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 4 |
| Time date stamp: | 31-Dec-2012 00:38:32 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x000152CE | 0x00015400 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.64322 |
.rdata | 0x00017000 | 0x0000393A | 0x00003A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.68963 |
.data | 0x0001B000 | 0x00004C6C | 0x00000A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.31456 |
.rsrc | 0x00020000 | 0x00000B2D | 0x00000C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.22823 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.21692 | 849 | Latin 1 / Western European | English - United States | RT_MANIFEST |
101 | 2.16096 | 20 | Latin 1 / Western European | Russian - Russia | RT_GROUP_ICON |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
MSVCRT.dll |
OLEAUT32.dll |
SHELL32.dll |
USER32.dll |
ole32.dll |
Total processes
46
Monitored processes
11
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1476 | xcopy /y TrueImageReadme "C:\Users\admin\Desktop\TrueImageReadme" | C:\Windows\system32\xcopy.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Extended Copy Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1524 | REG QUERY "HKLM\SYSTEM\CurrentControlSet\Control\Nls\Language" /v InstallLanguage | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1892 | "C:\Users\admin\AppData\Local\Temp\ActivationAcronisTI(H).exe" | C:\Users\admin\AppData\Local\Temp\ActivationAcronisTI(H).exe | explorer.exe | ||||||||||||
User: admin Company: not by Acronis Integrity Level: HIGH Description: activates build 23.4.1.14690 and previous Exit code: 0 Version: 1, 0, 0, 0 Modules
| |||||||||||||||
| 2248 | C:\Windows\system32\cmd.exe /c REG QUERY "HKLM\SOFTWARE\Acronis\TrueImageHome\Settings" /v LicenseActivatorExePath 2>NUL | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2320 | mode con:cols=86 lines=36 | C:\Windows\system32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DOS Device MODE Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2348 | cmd /c ""C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\Activation.cmd" " | C:\Windows\system32\cmd.exe | — | ActivationAcronisTI(H).exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2448 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2536 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2448 CREDAT:79873 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2632 | C:\Windows\system32\cmd.exe /c REG QUERY "HKLM\SYSTEM\CurrentControlSet\Control\Nls\Language" /v InstallLanguage | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2736 | REG QUERY "HKLM\SOFTWARE\Acronis\TrueImageHome\Settings" /v LicenseActivatorExePath | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
658
Read events
612
Write events
46
Delete events
0
Modification events
| (PID) Process: | (1892) ActivationAcronisTI(H).exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (1892) ActivationAcronisTI(H).exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2448) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2448) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2448) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2448) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (2448) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2448) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000071000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2448) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\AdminActive |
| Operation: | write | Name: | {AFA14931-4FC0-11E9-B63D-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (2448) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
Executable files
47
Suspicious files
29
Text files
129
Unknown types
12
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1892 | ActivationAcronisTI(H).exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\20.0.0.5534\PropertyStorage | sqlite | |
MD5:ACD18ACE4DE26708427EE072CCA61288 | SHA256:E37AC79387FBA082D5823E5E1E4A00577A9827837EC91B10DB7B0EF14BA1B3F3 | |||
| 1892 | ActivationAcronisTI(H).exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\20.0.0.8058\PropertyStorage | sqlite | |
MD5:E3F7D85D2C23389C2EBD495C7F086DA7 | SHA256:9C23198D8128FD70BBEDF6CCB155C0A56F18F21D1291F8EA19F1DBA2FFE08D7B | |||
| 1892 | ActivationAcronisTI(H).exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\20.0.0.8053\PropertyStorage | sqlite | |
MD5:E3F7D85D2C23389C2EBD495C7F086DA7 | SHA256:9C23198D8128FD70BBEDF6CCB155C0A56F18F21D1291F8EA19F1DBA2FFE08D7B | |||
| 1892 | ActivationAcronisTI(H).exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\20.0.0.5554\PropertyStorage | sqlite | |
MD5:E3F7D85D2C23389C2EBD495C7F086DA7 | SHA256:9C23198D8128FD70BBEDF6CCB155C0A56F18F21D1291F8EA19F1DBA2FFE08D7B | |||
| 1892 | ActivationAcronisTI(H).exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\20.0.0.8029\PropertyStorage | sqlite | |
MD5:E3F7D85D2C23389C2EBD495C7F086DA7 | SHA256:9C23198D8128FD70BBEDF6CCB155C0A56F18F21D1291F8EA19F1DBA2FFE08D7B | |||
| 1892 | ActivationAcronisTI(H).exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\21.0.0.6106\PropertyStorage | sqlite | |
MD5:E3F7D85D2C23389C2EBD495C7F086DA7 | SHA256:9C23198D8128FD70BBEDF6CCB155C0A56F18F21D1291F8EA19F1DBA2FFE08D7B | |||
| 1892 | ActivationAcronisTI(H).exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\21.0.0.6206\PropertyStorage | sqlite | |
MD5:E3F7D85D2C23389C2EBD495C7F086DA7 | SHA256:9C23198D8128FD70BBEDF6CCB155C0A56F18F21D1291F8EA19F1DBA2FFE08D7B | |||
| 1892 | ActivationAcronisTI(H).exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\20.0.0.5555\PropertyStorage | sqlite | |
MD5:E3F7D85D2C23389C2EBD495C7F086DA7 | SHA256:9C23198D8128FD70BBEDF6CCB155C0A56F18F21D1291F8EA19F1DBA2FFE08D7B | |||
| 1892 | ActivationAcronisTI(H).exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\20.0.0.8041\PropertyStorage | sqlite | |
MD5:E3F7D85D2C23389C2EBD495C7F086DA7 | SHA256:9C23198D8128FD70BBEDF6CCB155C0A56F18F21D1291F8EA19F1DBA2FFE08D7B | |||
| 1892 | ActivationAcronisTI(H).exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\21.0.0.6209\PropertyStorage | sqlite | |
MD5:E3F7D85D2C23389C2EBD495C7F086DA7 | SHA256:9C23198D8128FD70BBEDF6CCB155C0A56F18F21D1291F8EA19F1DBA2FFE08D7B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
2
DNS requests
2
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
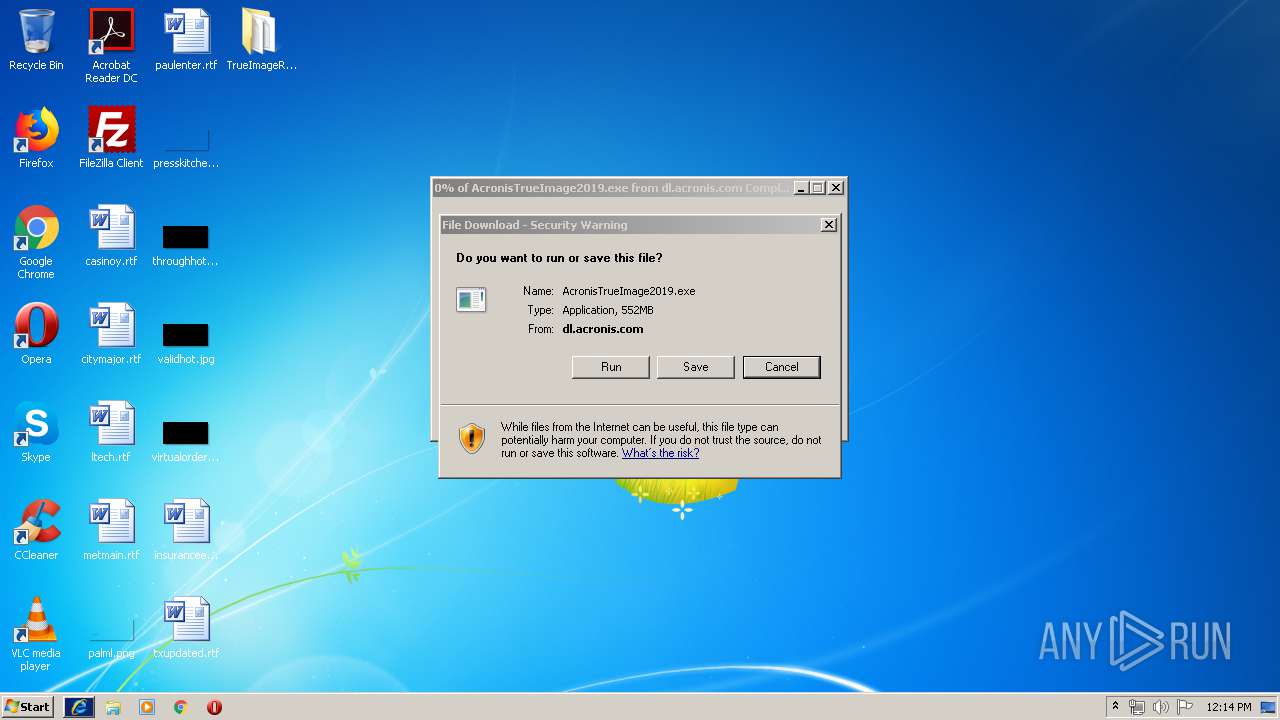
2536 | iexplore.exe | GET | — | 2.16.186.73:80 | http://dl.acronis.com/s/AcronisTrueImage2019.exe | unknown | — | — | whitelisted |
2448 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2536 | iexplore.exe | 2.16.186.73:80 | dl.acronis.com | Akamai International B.V. | — | whitelisted |
2448 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dl.acronis.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2536 | iexplore.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |