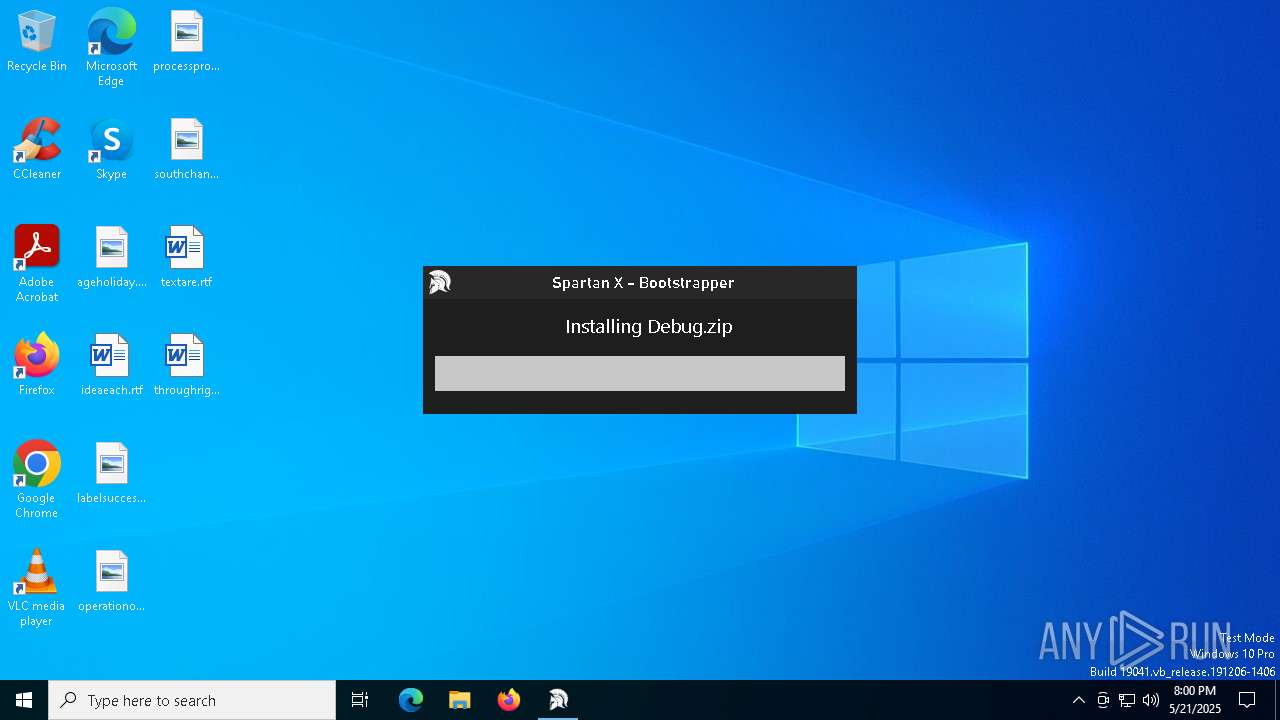
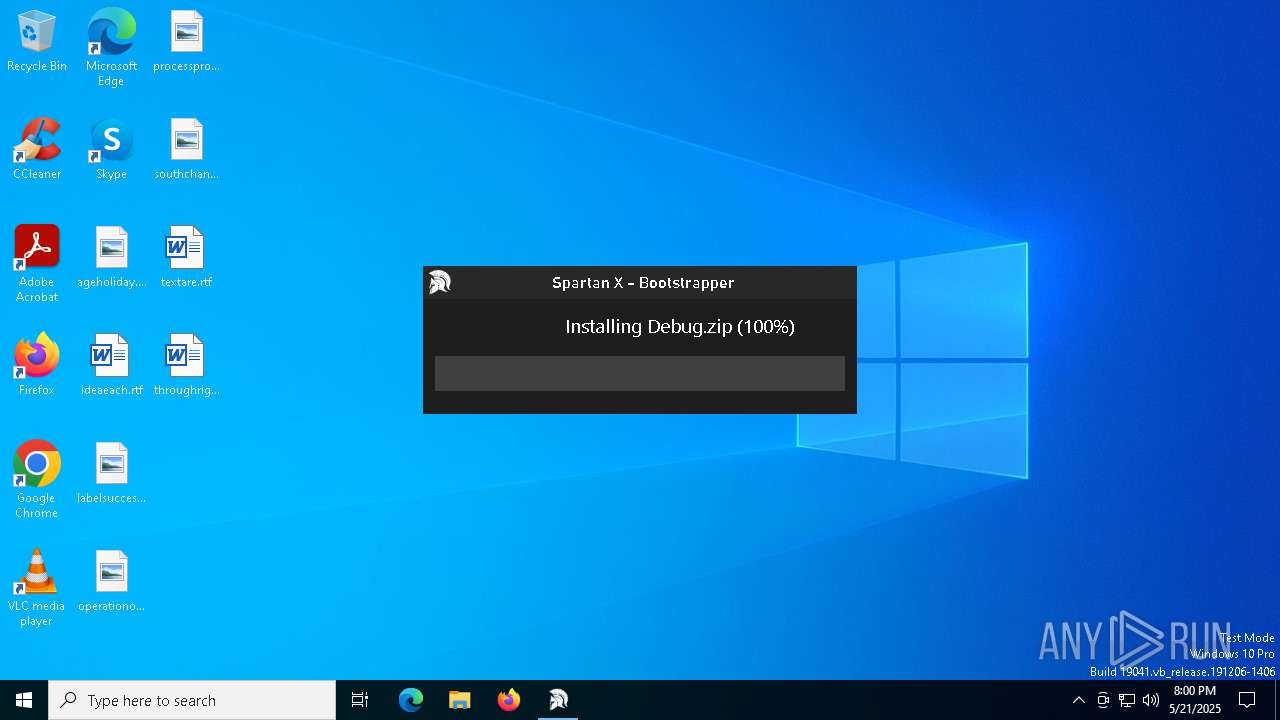
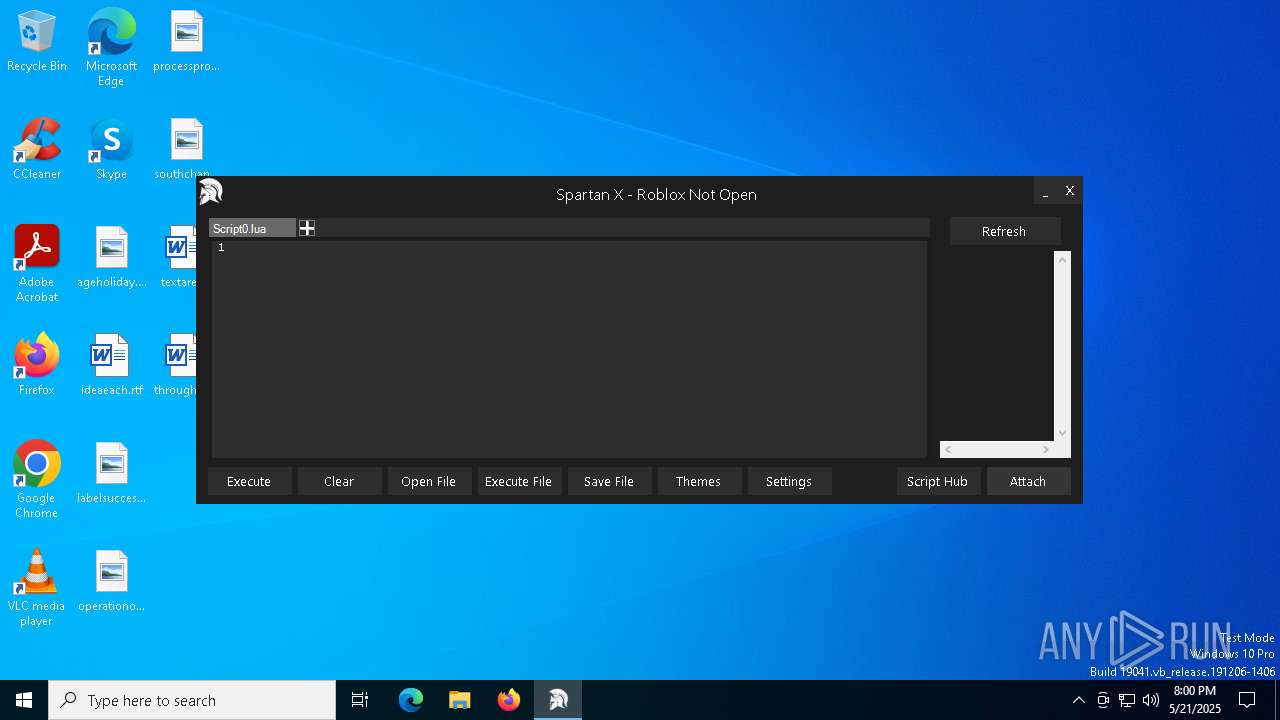
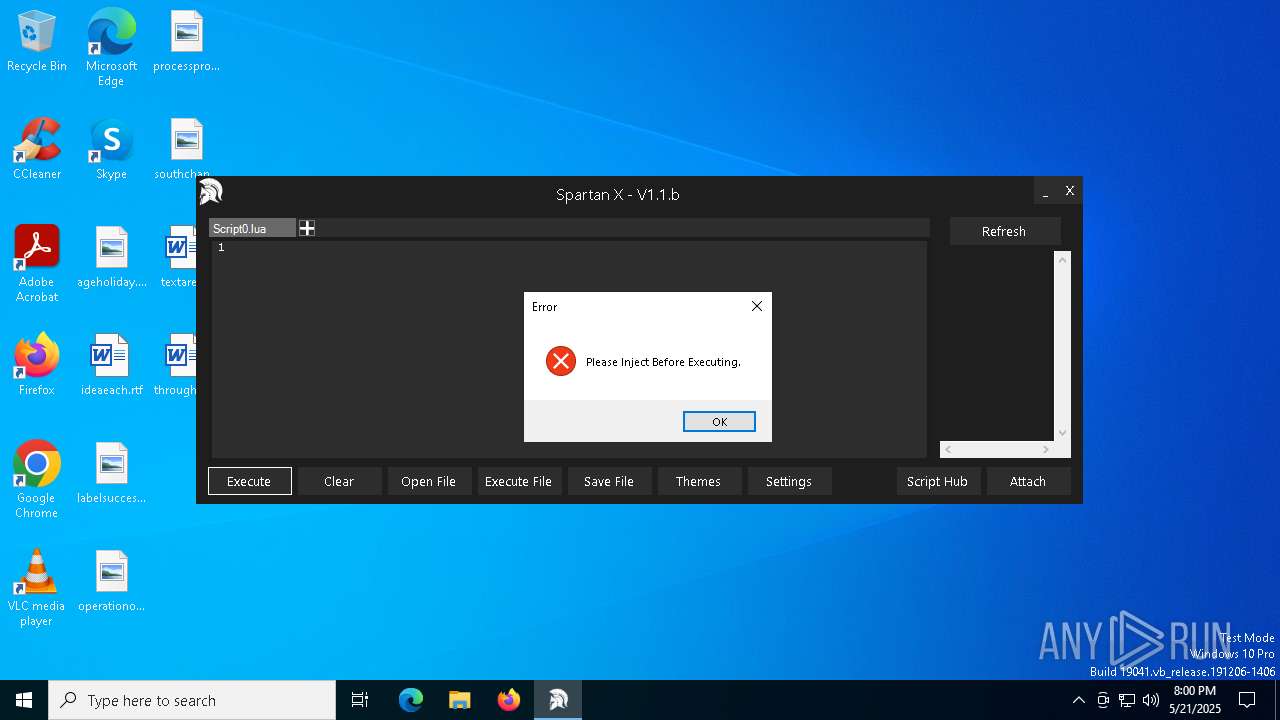
| File name: | Spartan X Bootstrapper.exe |
| Full analysis: | https://app.any.run/tasks/f5778cfb-52f1-4724-8113-20ca7e019276 |
| Verdict: | Malicious activity |
| Analysis date: | May 21, 2025, 20:00:24 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 01FB4F25181CF73D5F875A9911F4D016 |
| SHA1: | D9D6B48A1F1704DA46956CA0E25B5530EFB0CAA9 |
| SHA256: | 607763F83584B7493C5006DFE1852E787C8FE2C303150CF277ABAA43A7DE8E3B |
| SSDEEP: | 3072:+/mlcfeakZfD51f2BWwOnCwYpbXTK+neRnAOQVQZkKC0xlhSONgB:Umlc2aabzkOnClm+ne+OQqkKC0x+O |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- Spartan X Bootstrapper.exe (PID: 7396)
Process drops legitimate windows executable
- Spartan X Bootstrapper.exe (PID: 7396)
Reads security settings of Internet Explorer
- Spartan X Bootstrapper.exe (PID: 7396)
- Spartan X.exe (PID: 7980)
INFO
Reads the computer name
- Spartan X Bootstrapper.exe (PID: 7396)
- Spartan X.exe (PID: 7980)
Checks supported languages
- Spartan X Bootstrapper.exe (PID: 7396)
- Spartan X.exe (PID: 7980)
Disables trace logs
- Spartan X Bootstrapper.exe (PID: 7396)
Reads the machine GUID from the registry
- Spartan X Bootstrapper.exe (PID: 7396)
- Spartan X.exe (PID: 7980)
Checks proxy server information
- Spartan X Bootstrapper.exe (PID: 7396)
Reads the software policy settings
- Spartan X Bootstrapper.exe (PID: 7396)
Create files in a temporary directory
- Spartan X Bootstrapper.exe (PID: 7396)
The sample compiled with english language support
- Spartan X Bootstrapper.exe (PID: 7396)
Process checks computer location settings
- Spartan X Bootstrapper.exe (PID: 7396)
Creates files or folders in the user directory
- Spartan X.exe (PID: 7980)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (63.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (23.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
| .exe | | | Generic Win/DOS Executable (1.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2088:06:26 18:57:05+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 137728 |
| InitializedDataSize: | 3584 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x23896 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | Spartan X Bootstrapper |
| FileVersion: | 1.0.0.0 |
| InternalName: | Spartan X Bootstrapper.exe |
| LegalCopyright: | Copyright © 2025 |
| LegalTrademarks: | - |
| OriginalFileName: | Spartan X Bootstrapper.exe |
| ProductName: | Spartan X Bootstrapper |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
132
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 7396 | "C:\Users\admin\AppData\Local\Temp\Spartan X Bootstrapper.exe" | C:\Users\admin\AppData\Local\Temp\Spartan X Bootstrapper.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Spartan X Bootstrapper Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 7508 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7540 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7980 | "C:\Users\admin\AppData\Local\Temp\Debug\Spartan X.exe" | C:\Users\admin\AppData\Local\Temp\Debug\Spartan X.exe | — | Spartan X Bootstrapper.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Cipher Executor Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
1 318
Read events
1 304
Write events
14
Delete events
0
Modification events
| (PID) Process: | (7396) Spartan X Bootstrapper.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Spartan X Bootstrapper_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (7396) Spartan X Bootstrapper.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Spartan X Bootstrapper_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (7396) Spartan X Bootstrapper.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Spartan X Bootstrapper_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (7396) Spartan X Bootstrapper.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Spartan X Bootstrapper_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (7396) Spartan X Bootstrapper.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Spartan X Bootstrapper_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (7396) Spartan X Bootstrapper.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Spartan X Bootstrapper_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (7396) Spartan X Bootstrapper.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Spartan X Bootstrapper_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (7396) Spartan X Bootstrapper.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Spartan X Bootstrapper_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (7396) Spartan X Bootstrapper.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Spartan X Bootstrapper_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (7396) Spartan X Bootstrapper.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Spartan X Bootstrapper_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
23
Suspicious files
26
Text files
90
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7396 | Spartan X Bootstrapper.exe | C:\Users\admin\AppData\Local\Temp\TempExtract\Debug\bin\libssl-3-x64.dll | executable | |
MD5:6839DF3D3D6276093F69FFDCD474E54B | SHA256:2094C8D0EFBD30438B8A8BEF662FE407A0DFF754DA3E7708424CD0A4CD4A260A | |||
| 7396 | Spartan X Bootstrapper.exe | C:\Users\admin\AppData\Local\Temp\TempExtract\Debug\ExecutorData\ScriptHub\BladeBall\Name.txt | text | |
MD5:52019ACDEE3BE2A2F3149D9237848ABF | SHA256:BE7DBE5D04D49320EDF7FB7C254BBB7601A2FBB82FF45D5D2E3BD53F44955A64 | |||
| 7396 | Spartan X Bootstrapper.exe | C:\Users\admin\AppData\Local\Temp\TempExtract\Debug\bin\libcrypto-3-x64.dll | executable | |
MD5:688DFC4C76490BC82858D623E5E136BF | SHA256:6B5760BAFE0EEE9A4268C619516E11ACD0AE30046EC59F0C3AD8E58B1D7A6BBA | |||
| 7396 | Spartan X Bootstrapper.exe | C:\Users\admin\AppData\Local\Temp\TempExtract\Debug\ExecutorData\ScriptHub\Arsenal\Name.txt | text | |
MD5:602D5714F298CCD9219C96937C7CA804 | SHA256:A0892922586032458A0D7ECF5396332BFE02740DA5E7EE861C33084460C86B31 | |||
| 7396 | Spartan X Bootstrapper.exe | C:\Users\admin\AppData\Local\Temp\TempExtract\Debug\ExecutorData\CurrentSettings\TopMost.txt | text | |
MD5:68934A3E9455FA72420237EB05902327 | SHA256:FCBCF165908DD18A9E49F7FF27810176DB8E9F63B4352213741664245224F8AA | |||
| 7396 | Spartan X Bootstrapper.exe | C:\Users\admin\AppData\Local\Temp\TempExtract\Debug\ExecutorData\ScriptHub\Aimlock\Name.txt | text | |
MD5:589183D63569C34D4F8938FD37851231 | SHA256:E7BF73FFB4332C39569B65089F7E2F0BCDE9935744B6CF562239CEF0FDF11322 | |||
| 7396 | Spartan X Bootstrapper.exe | C:\Users\admin\AppData\Local\Temp\TempExtract\Debug\ExecutorData\ScriptHub\Aimlock\Code.txt | binary | |
MD5:1C6847508902E336185D53A22103EDCF | SHA256:86ABF3D3A312529D76507E4C5C04949D864C64B541A08A9EE757FFD7B57C11E9 | |||
| 7396 | Spartan X Bootstrapper.exe | C:\Users\admin\AppData\Local\Temp\TempExtract\Debug\Cipher.pdb | binary | |
MD5:F5D889E79B4C00FC909460FFDC23EBB7 | SHA256:4B56A0ECFEF4193459E546E943DC8813FB6D0713C38AA46710A69F6A822E42FD | |||
| 7396 | Spartan X Bootstrapper.exe | C:\Users\admin\AppData\Local\Temp\TempExtract\Debug\ExecutorData\CurrentSettings\AutoInject.txt | text | |
MD5:68934A3E9455FA72420237EB05902327 | SHA256:FCBCF165908DD18A9E49F7FF27810176DB8E9F63B4352213741664245224F8AA | |||
| 7396 | Spartan X Bootstrapper.exe | C:\Users\admin\AppData\Local\Temp\TempExtract\Debug\ExecutorData\ScriptHub\BladeBall\Code.txt | binary | |
MD5:2535D8C7EA383C4FAE84181F6BA50A51 | SHA256:123BC9B1EF3F9B6A9310D9CA8BCABD39289ED53AA0FE7D07D2F6389557787E45 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
20
DNS requests
15
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.153:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
8168 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8168 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.153:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7396 | Spartan X Bootstrapper.exe | 140.82.121.3:443 | github.com | GITHUB | US | whitelisted |
7396 | Spartan X Bootstrapper.exe | 185.199.108.133:443 | raw.githubusercontent.com | FASTLY | US | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
github.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |