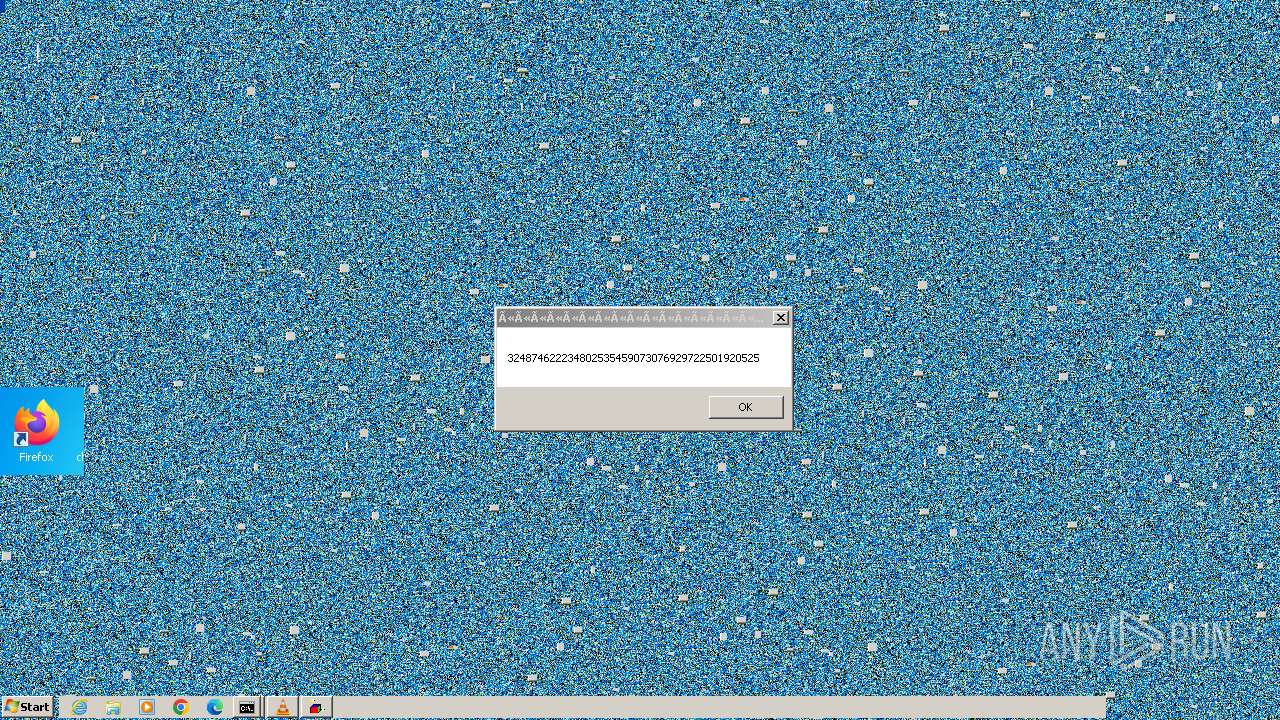
| File name: | ë.exe |
| Full analysis: | https://app.any.run/tasks/4dd00d70-75c0-49c6-8a7e-375eb2576ede |
| Verdict: | Malicious activity |
| Analysis date: | April 20, 2024, 21:19:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | FA1FBE391E1D35CC0860D5D04720FA95 |
| SHA1: | FE4FB440BCDAFFAEAA8A55CEA25AEC6A1CED6223 |
| SHA256: | 6035B7BA4A66BDA87BFDDB22E6F182C0D2F3479CAD5A36DD37ABC55EC3833D6C |
| SSDEEP: | 24576:pryvLA0c21FJnBfkw+ZclYnmPoRc9QmwQ9RvfVY7:p2vLzVh+ZclYnmPoK9ZVvO |
MALICIOUS
Disables Windows Defender
- reg.exe (PID: 452)
Drops the executable file immediately after the start
- ë.exe (PID: 548)
Changes the autorun value in the registry
- MBRDestroy.exe (PID: 3244)
UAC/LUA settings modification
- reg.exe (PID: 3808)
SUSPICIOUS
Executable content was dropped or overwritten
- ë.exe (PID: 548)
Reads security settings of Internet Explorer
- ë.exe (PID: 548)
Reads the Internet Settings
- ë.exe (PID: 548)
- cmd.exe (PID: 2416)
- cmd.exe (PID: 3080)
Executing commands from a ".bat" file
- ë.exe (PID: 548)
- cmd.exe (PID: 2416)
Starts CMD.EXE for commands execution
- ë.exe (PID: 548)
- cmd.exe (PID: 2416)
Application launched itself
- cmd.exe (PID: 2416)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2416)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 2416)
- cmd.exe (PID: 2784)
- cmd.exe (PID: 3080)
The executable file from the user directory is run by the CMD process
- eeee.exe (PID: 2856)
- MBRDestroy.exe (PID: 3244)
- lines.exe (PID: 1576)
- melter.exe (PID: 2036)
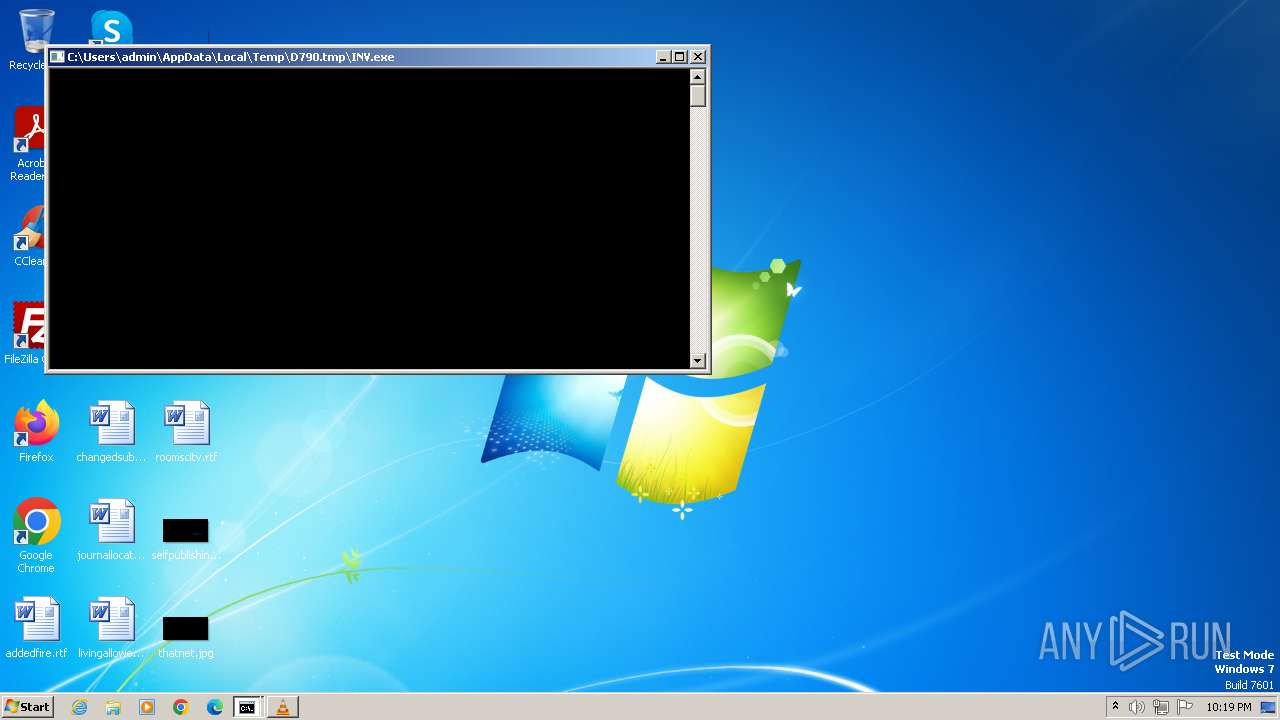
- INV.exe (PID: 3072)
- glitch.exe (PID: 2432)
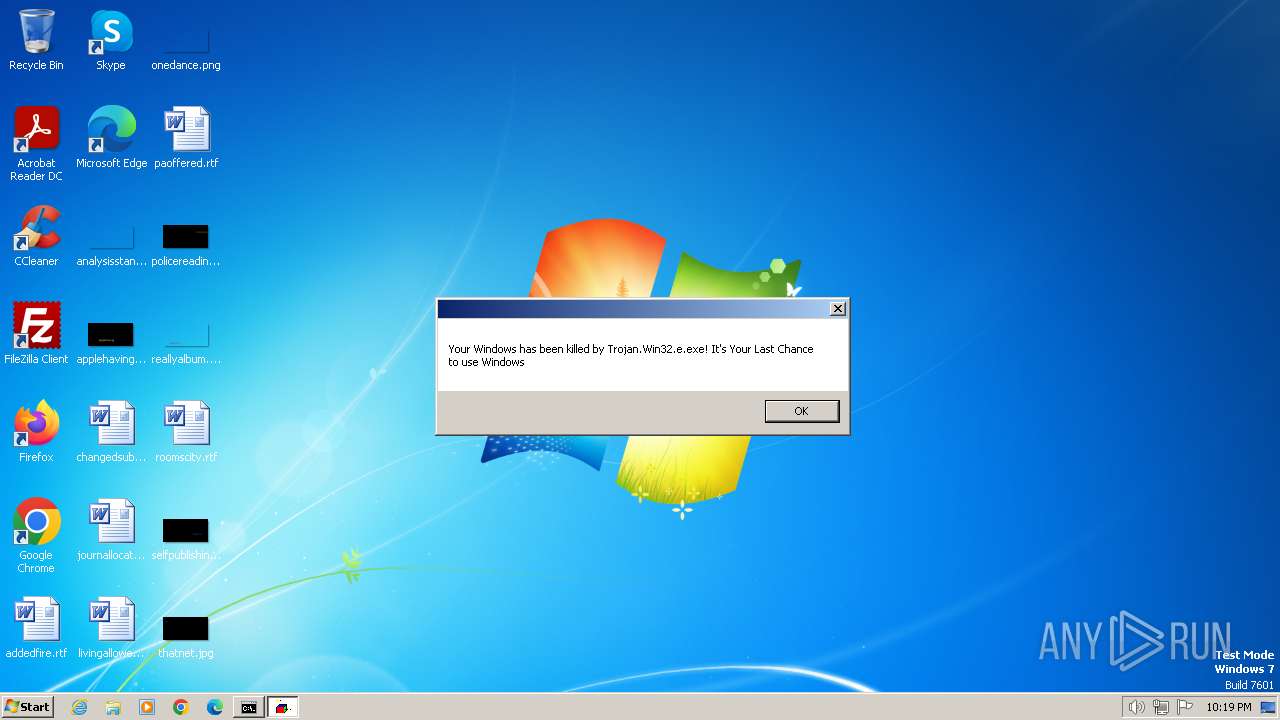
Probably fake Windows Update
- schtasks.exe (PID: 3084)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2416)
The process executes VB scripts
- cmd.exe (PID: 3080)
- cmd.exe (PID: 2416)
INFO
Create files in a temporary directory
- ë.exe (PID: 548)
Checks supported languages
- MBRDestroy.exe (PID: 3244)
- ë.exe (PID: 548)
- glitch.exe (PID: 2432)
- melter.exe (PID: 2036)
- vlc.exe (PID: 2908)
- lines.exe (PID: 1576)
- INV.exe (PID: 3072)
- vlc.exe (PID: 2156)
- eeee.exe (PID: 2856)
Reads the computer name
- ë.exe (PID: 548)
- vlc.exe (PID: 2156)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (39.3) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (38.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (9.5) |
| .exe | | | Win32 Executable (generic) (6.5) |
| .exe | | | Generic Win/DOS Executable (2.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2010:11:08 13:12:07+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 823296 |
| InitializedDataSize: | 4096 |
| UninitializedDataSize: | 393216 |
| EntryPoint: | 0x1292a0 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Debug, Pre-release, Private build |
| FileOS: | Windows 16-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | ë |
| FileDescription: | ë |
| FileVersion: | 1,0,0,0 |
| ProductName: | ë |
| InternalName: | ë |
| ProductVersion: | 1,0,0,0 |
| LegalCopyright: | 2021 |
Total processes
97
Monitored processes
46
Malicious processes
3
Suspicious processes
2
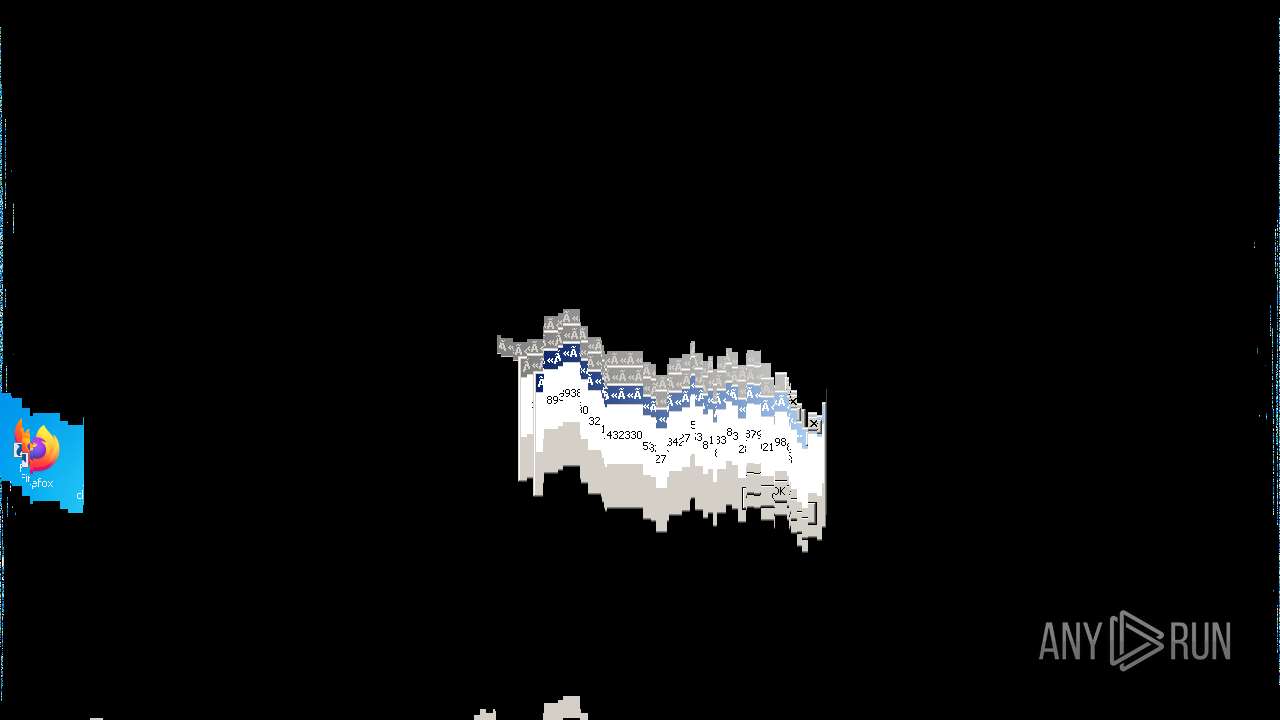
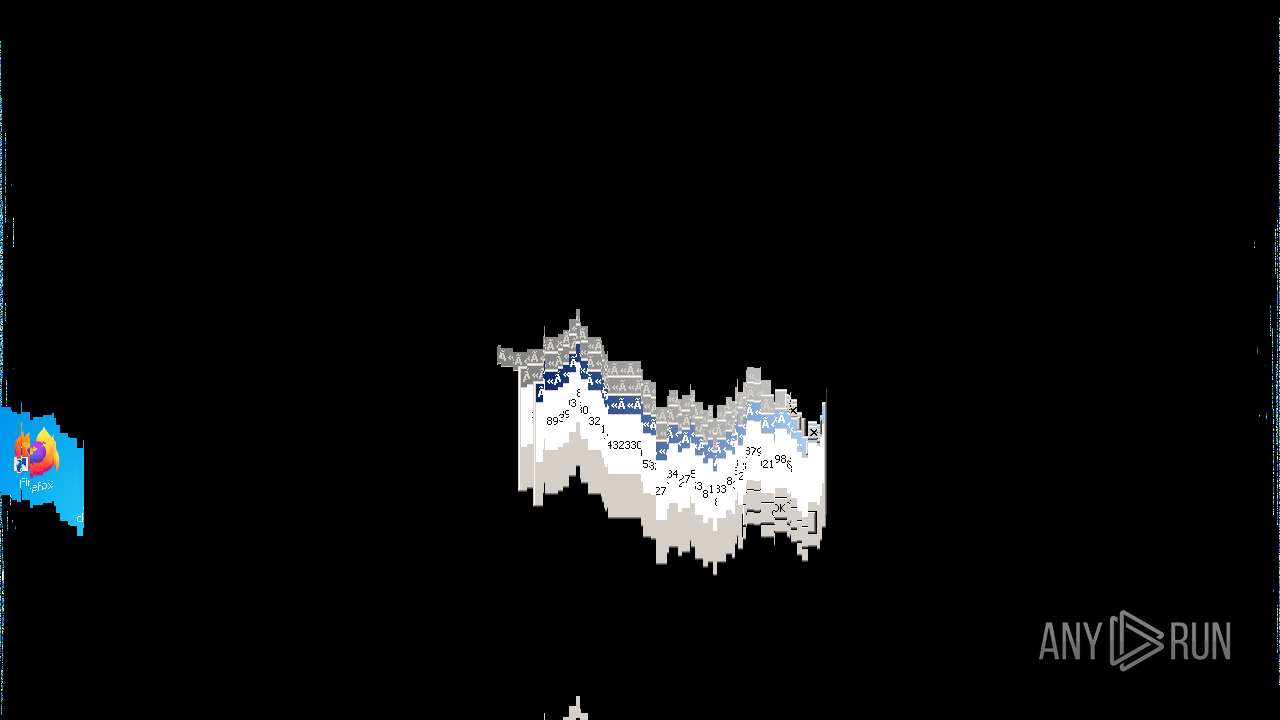
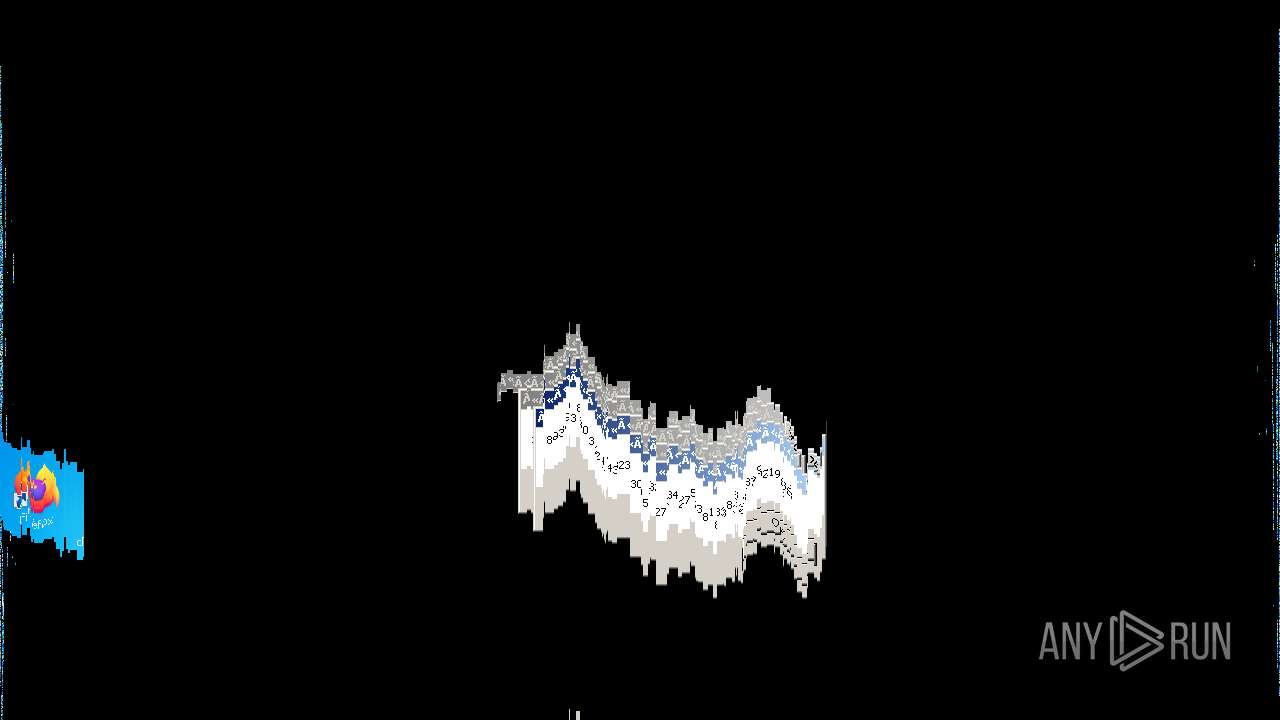
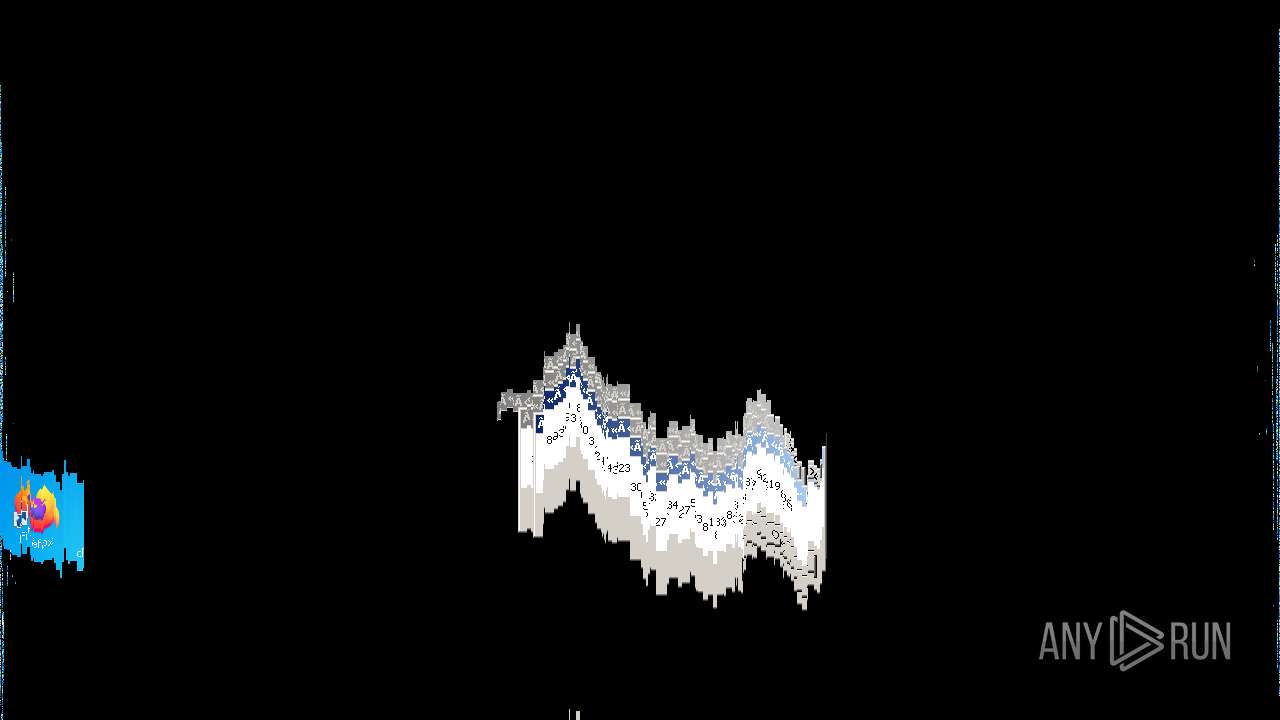
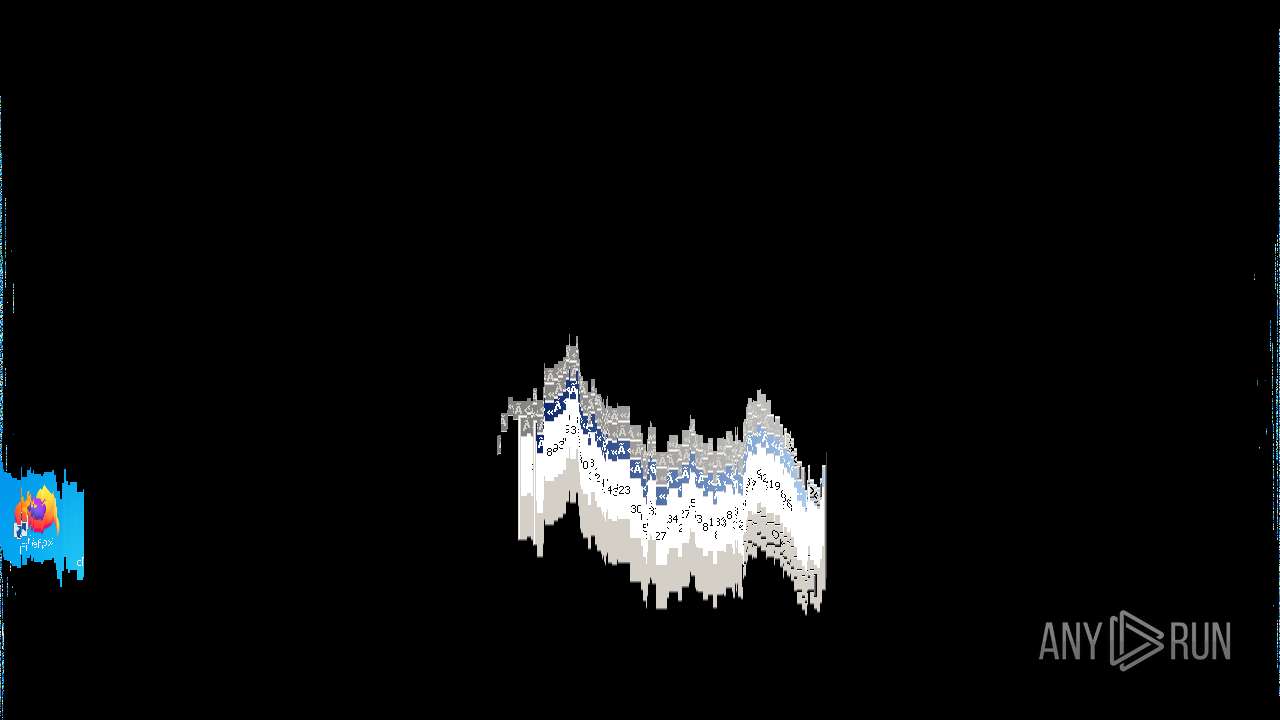
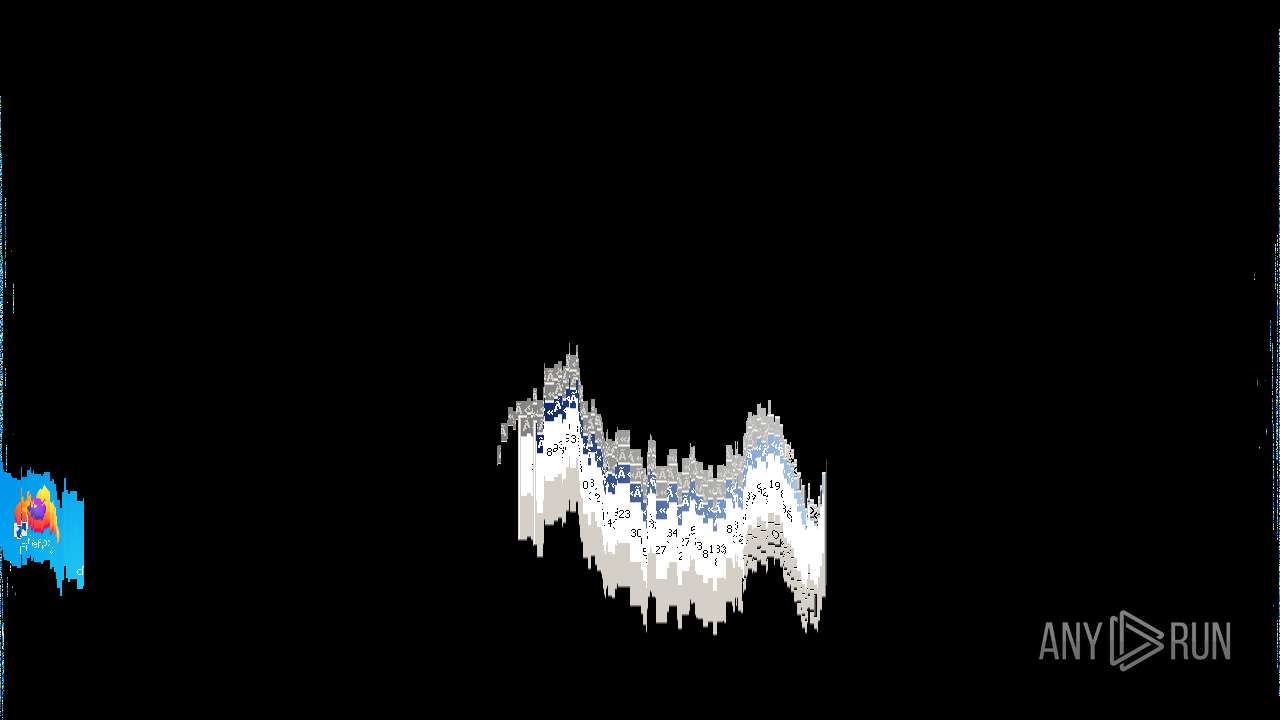
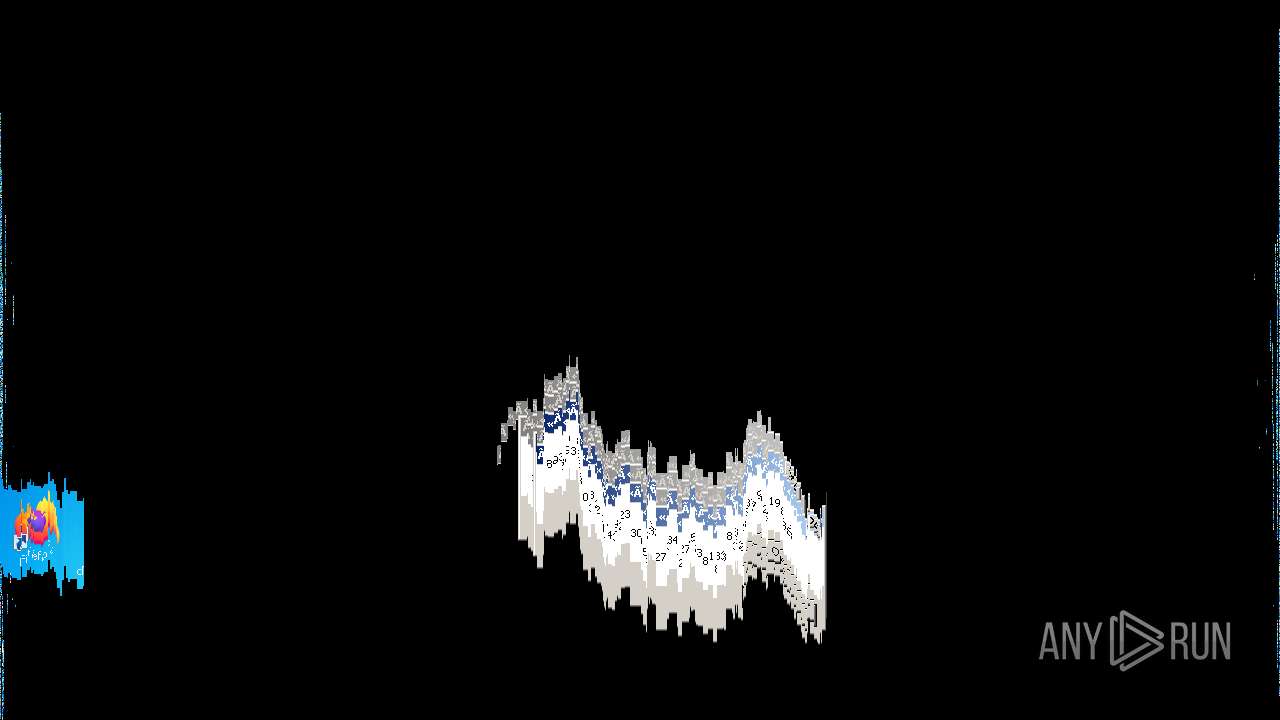
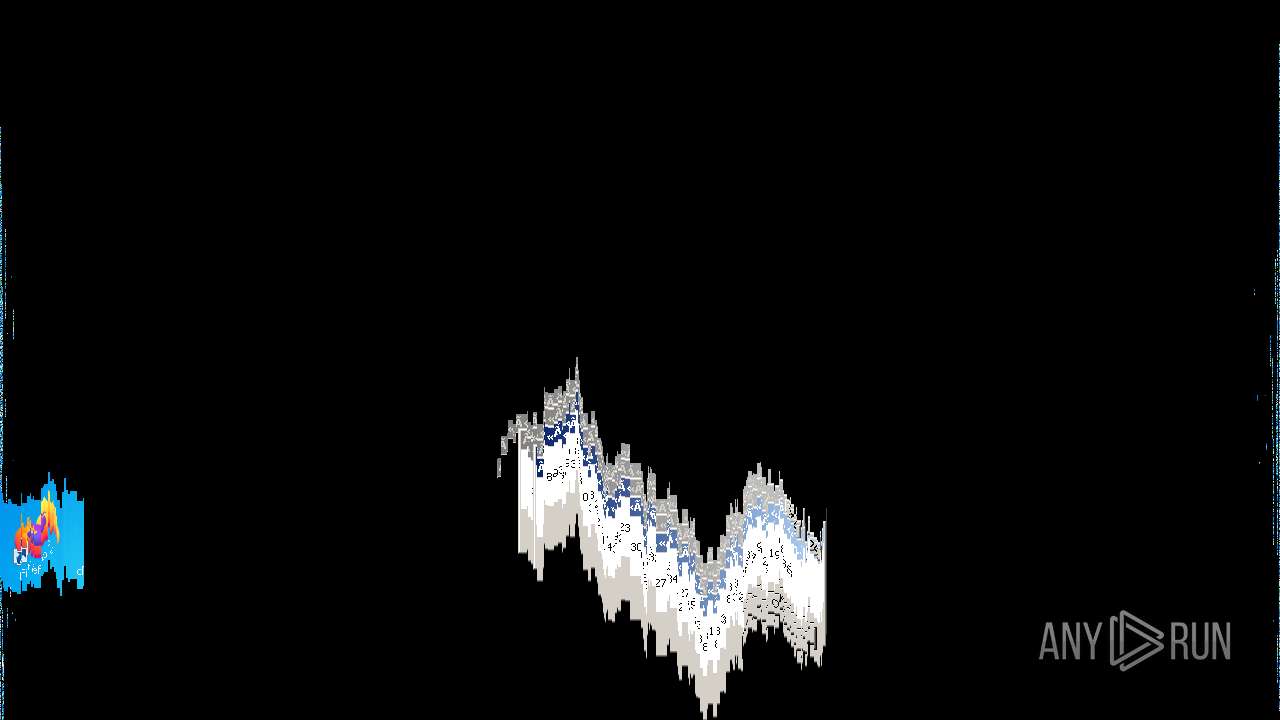
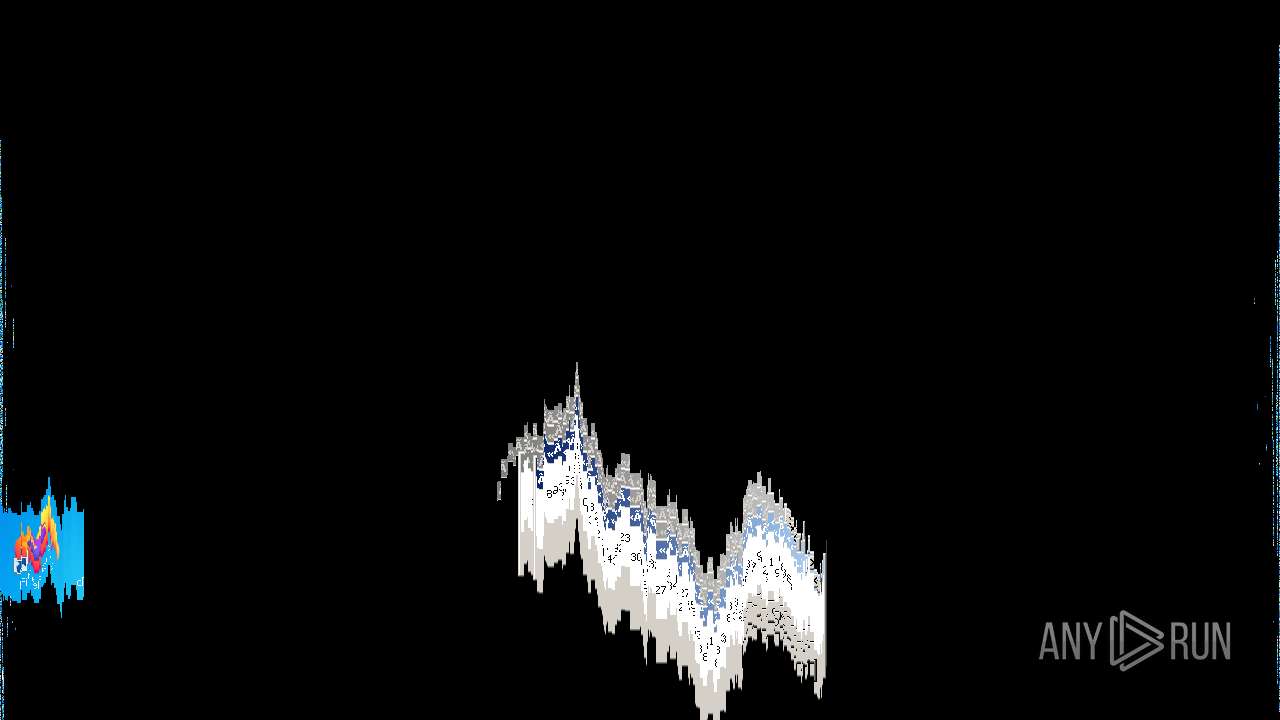
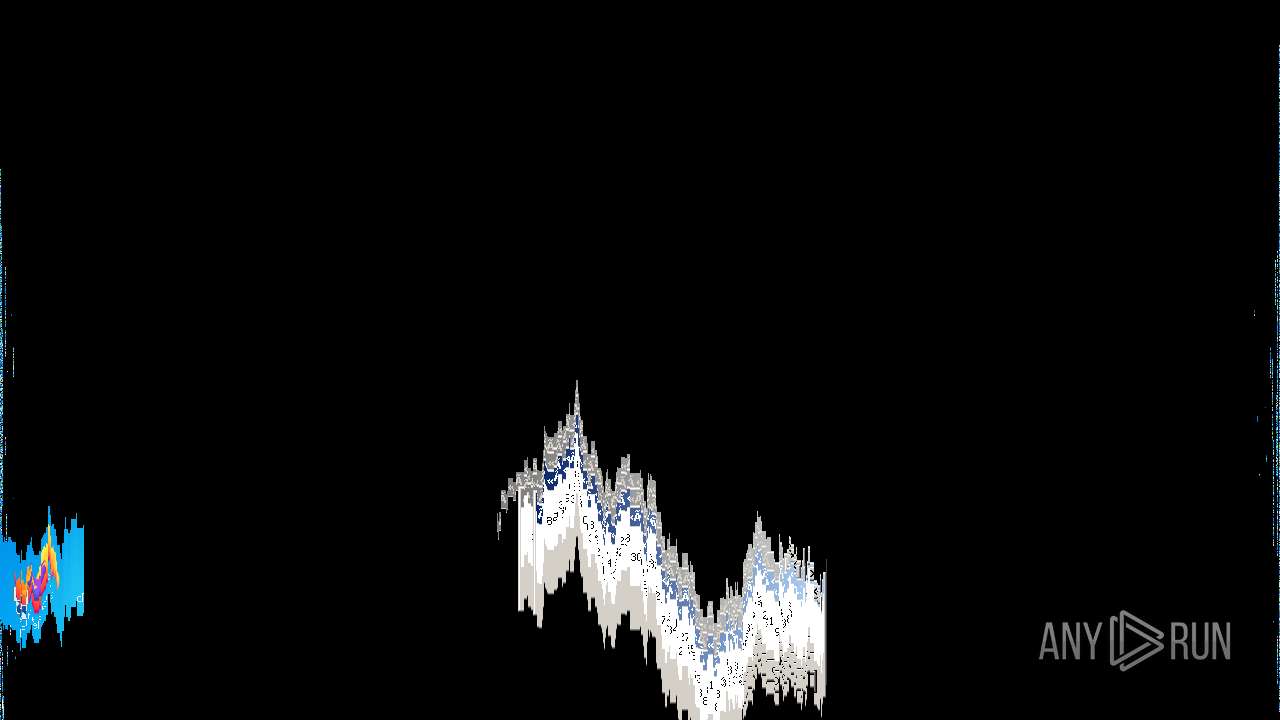
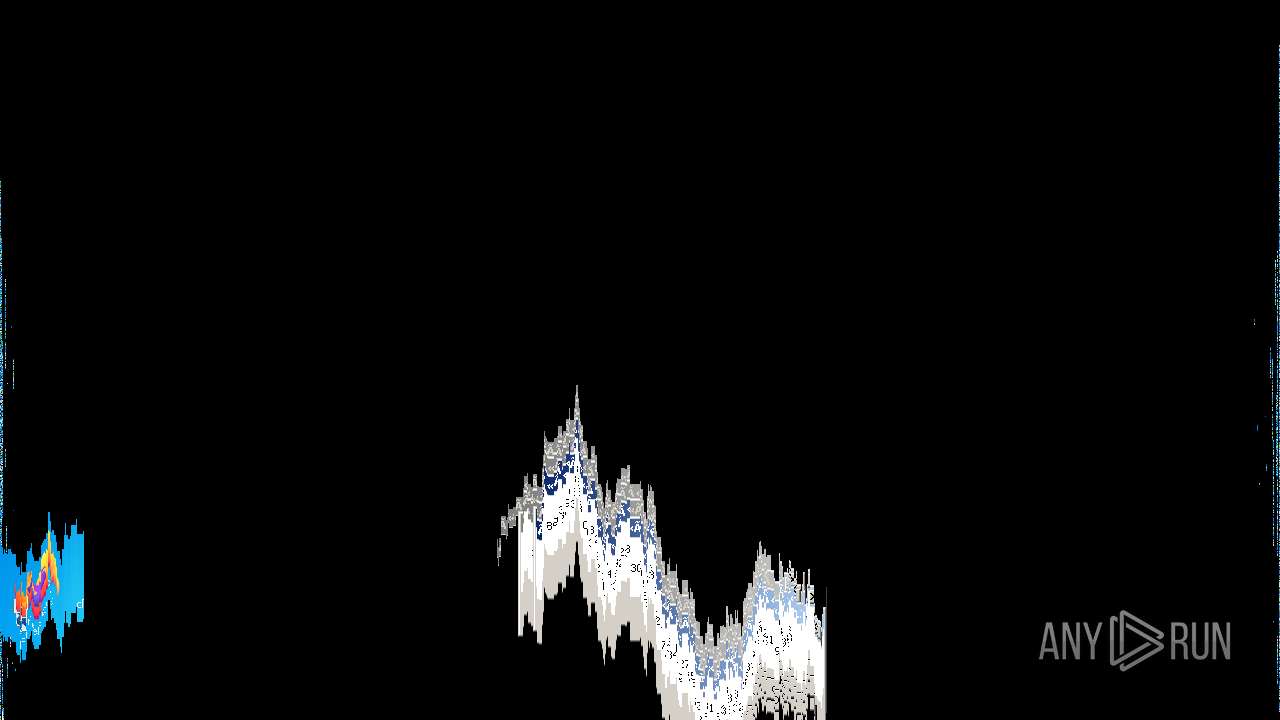
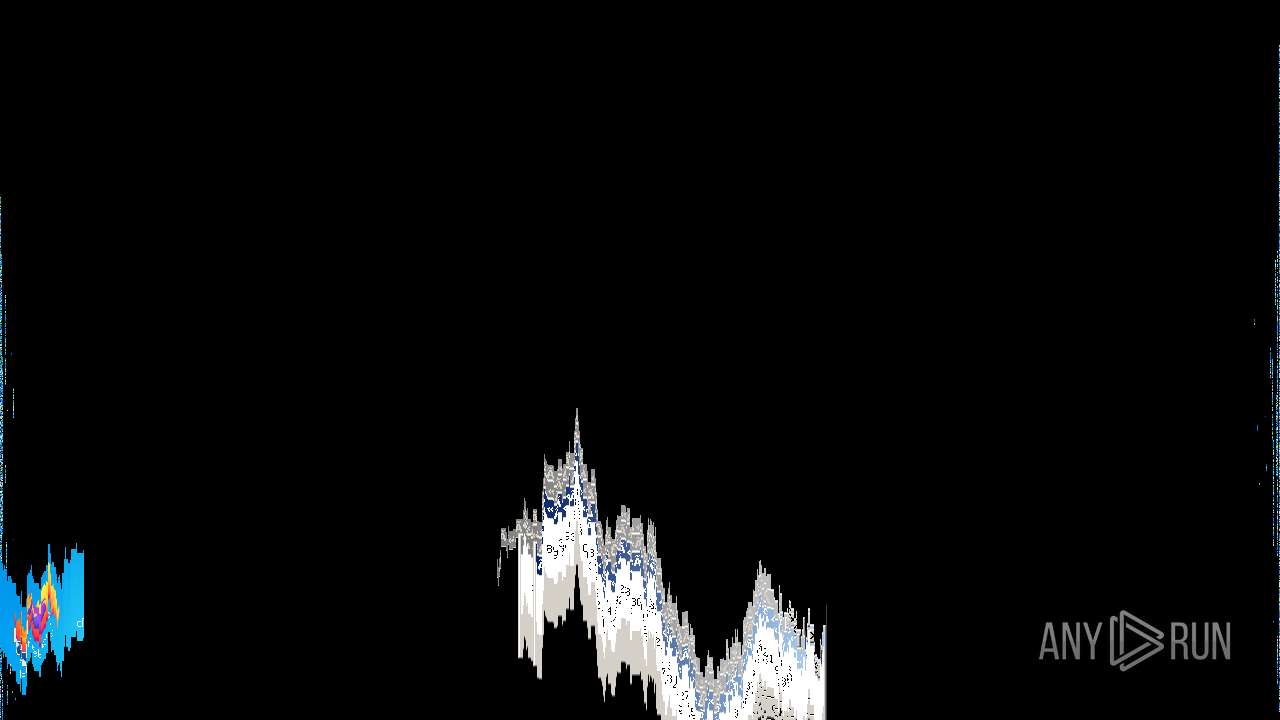
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 452 | Reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender" /v DisableAntiSpyware /t REG_DWORD /d 1 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 548 | "C:\Users\admin\AppData\Local\Temp\ë.exe" | C:\Users\admin\AppData\Local\Temp\ë.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 924 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\D790.tmp\m.vbs" | C:\Windows\System32\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1028 | bcdedit /delete {current} | C:\Windows\System32\bcdedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Boot Configuration Data Editor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1172 | timeout 5 /nobreak | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1576 | lines.exe | C:\Users\admin\AppData\Local\Temp\D790.tmp\lines.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 1584 | timeout 6 /nobreak | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1796 | timeout 6 /nobreak | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1852 | timeout 6 /nobreak | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2036 | melter.exe | C:\Users\admin\AppData\Local\Temp\D790.tmp\melter.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
Total events
24 319
Read events
24 197
Write events
92
Delete events
30
Modification events
| (PID) Process: | (548) ë.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (548) ë.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (548) ë.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (548) ë.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3988) reg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | DisableTaskMgr |
Value: 1 | |||
| (PID) Process: | (3808) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | EnableLUA |
Value: 0 | |||
| (PID) Process: | (452) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender |
| Operation: | write | Name: | DisableAntiSpyware |
Value: 1 | |||
| (PID) Process: | (3244) MBRDestroy.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Windows Update |
Value: | |||
| (PID) Process: | (3244) MBRDestroy.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Windows Update |
Value: C:\Users\admin\AppData\Local\Temp\D790.tmp\MBRDestroy.exe | |||
| (PID) Process: | (3244) MBRDestroy.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Windows Update |
Value: C:\Users\admin\AppData\Local\Temp\D790.tmp\MBRDestroy.exe | |||
Executable files
6
Suspicious files
1
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3244 | MBRDestroy.exe | \Device\Harddisk0\DR0 | — | |
MD5:— | SHA256:— | |||
| 2156 | vlc.exe | C:\Users\admin\AppData\Roaming\vlc\vlc-qt-interface.ini | — | |
MD5:— | SHA256:— | |||
| 2156 | vlc.exe | C:\Users\admin\AppData\Roaming\vlc\vlc-qt-interface.ini.gq2156 | — | |
MD5:— | SHA256:— | |||
| 548 | ë.exe | C:\Users\admin\AppData\Local\Temp\D790.tmp\sound.bat | text | |
MD5:331BC90D9EBE8282D7BF1B9092CEEE9F | SHA256:38B87D711637C9D1DF4FAD3146EBE52799E27C2B41A16608058F11F4966AFC85 | |||
| 548 | ë.exe | C:\Users\admin\AppData\Local\Temp\D790.tmp\e.bat | text | |
MD5:236707EF3C046A0867770F0522504CC0 | SHA256:7EFD9B5B48715D79A30A5EC783CC111FA794C92FDE8365F34CEEA5759FB4C5CF | |||
| 548 | ë.exe | C:\Users\admin\AppData\Local\Temp\D790.tmp\INV.exe | executable | |
MD5:E079C468C9CAED494623DBF95E9CE5E8 | SHA256:8E217CE5670AC1021FDB6101372F9322F7FF82481ECD9BADC104FF542E46128C | |||
| 548 | ë.exe | C:\Users\admin\AppData\Local\Temp\D790.tmp\glitch.exe | executable | |
MD5:47801F0CF73D320054676A56D0264EDB | SHA256:F25853B17EE25C1DF537CD39BA15A338B92B0812833E3A523AA2F90EFBF766E8 | |||
| 548 | ë.exe | C:\Users\admin\AppData\Local\Temp\D790.tmp\eeee.exe | executable | |
MD5:F12DD13F2BF50E60BECAD81660E8DD49 | SHA256:9648153AB799E13E2531B53FA44722EB677A3AC770DF9BA8641F1ACFCED678DB | |||
| 2156 | vlc.exe | C:\Users\admin\AppData\Roaming\vlc\vlc-qt-interface.ini.Hp2156 | ini | |
MD5:81E8396F21B806BC804A3696627AF7E1 | SHA256:283A3DA5D46F06802D70BC49437BFEFD5BF608CB867788CA5E08323C683F8133 | |||
| 2156 | vlc.exe | C:\Users\admin\AppData\Roaming\vlc\vlc-qt-interface.ini.lock | text | |
MD5:D1A2DFCB3D9A012F77AC204E15DD679F | SHA256:EF0ECE3104C8596D0FA4DF6FA02853BDD3F127859FADB3143D676F73B7A8F997 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
DNS requests
Threats
Process | Message |
|---|---|
vlc.exe | main libvlc debug: revision 3.0.11-0-gdc0c5ced72
|
vlc.exe | main libvlc debug: configured with ../extras/package/win32/../../../configure '--enable-update-check' '--enable-lua' '--enable-faad' '--enable-flac' '--enable-theora' '--enable-avcodec' '--enable-merge-ffmpeg' '--enable-dca' '--enable-mpc' '--enable-libass' '--enable-schroedinger' '--enable-realrtsp' '--enable-live555' '--enable-dvdread' '--enable-shout' '--enable-goom' '--enable-caca' '--enable-qt' '--enable-skins2' '--enable-sse' '--enable-mmx' '--enable-libcddb' '--enable-zvbi' '--disable-telx' '--enable-nls' '--host=i686-w64-mingw32' '--with-breakpad=https://win.crashes.videolan.org' 'host_alias=i686-w64-mingw32' 'PKG_CONFIG_LIBDIR=/home/jenkins/workspace/vlc-release/windows/vlc-release-win32-x86/contrib/i686-w64-mingw32/lib/pkgconfig'
|
vlc.exe | main libvlc debug: searching plug-in modules
|
vlc.exe | main libvlc debug: using multimedia timers as clock source
|
vlc.exe | main libvlc debug: min period: 1 ms, max period: 1000000 ms
|
vlc.exe | main libvlc debug: Copyright © 1996-2020 the VideoLAN team
|
vlc.exe | main libvlc debug: loading plugins cache file C:\Program Files\VideoLAN\VLC\plugins\plugins.dat
|
vlc.exe | main libvlc debug: VLC media player - 3.0.11 Vetinari
|
vlc.exe | main libvlc debug: recursively browsing `C:\Program Files\VideoLAN\VLC\plugins'
|
vlc.exe | main libvlc error: stale plugins cache: modified C:\Program Files\VideoLAN\VLC\plugins\access\libaccess_imem_plugin.dll
|