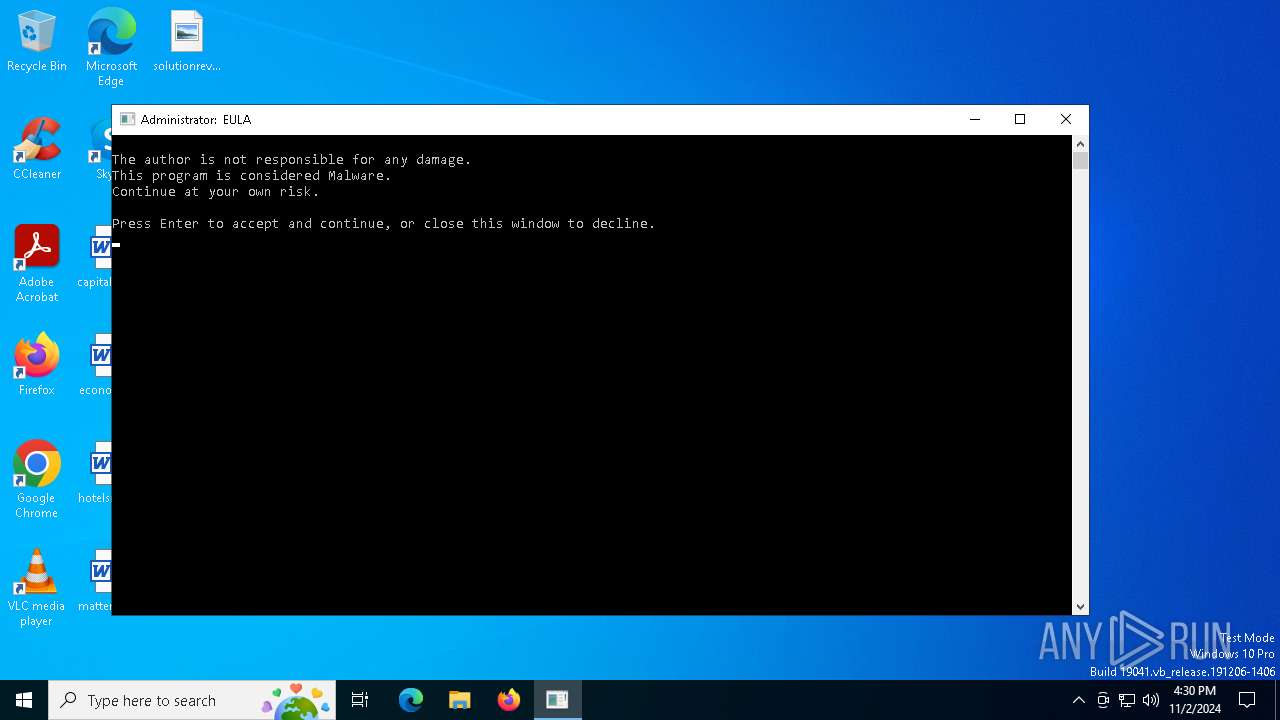
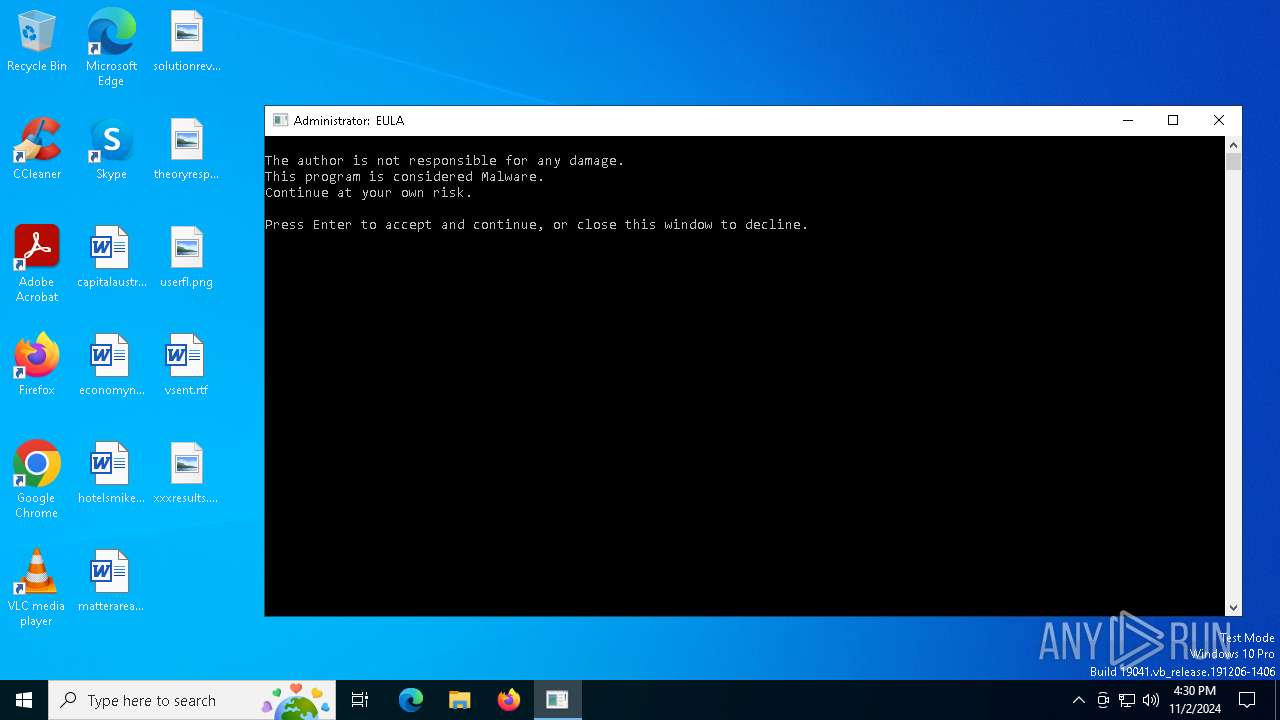
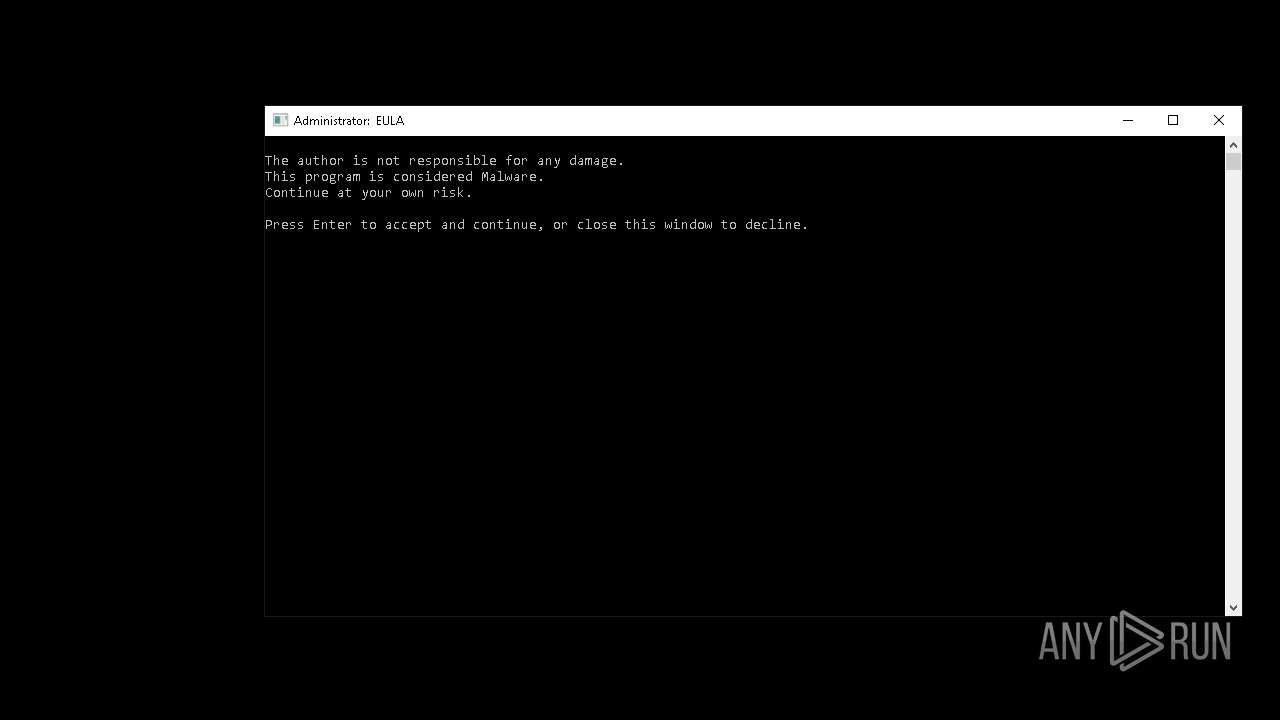
| File name: | 666.exe |
| Full analysis: | https://app.any.run/tasks/a2b0211a-aff9-4c1b-be64-08914790b9df |
| Verdict: | Malicious activity |
| Analysis date: | November 02, 2024, 16:30:41 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386, for MS Windows, 5 sections |
| MD5: | E8335C96A6D84AE303D2908E79EBA24B |
| SHA1: | D2D1FFCDC96CC7AD4F6C13B36A10B11A512EC77A |
| SHA256: | 60352F191D73298DA994108F5940C4811B1AFE7F7F9244367BE4F1EDE0E6C2D7 |
| SSDEEP: | 3072:rCYa+0Nu6vQAkQ5S7JmyxCbBKhiTbMoIL:YQLi8NiTbXk |
MALICIOUS
Starts NET.EXE to view/add/change user profiles
- net.exe (PID: 6400)
- net.exe (PID: 6328)
- net.exe (PID: 3844)
- cmd.exe (PID: 6704)
- net.exe (PID: 6728)
Starts NET.EXE to view/change users localgroup
- net.exe (PID: 6804)
- net.exe (PID: 2000)
- cmd.exe (PID: 6704)
SUSPICIOUS
Uses RUNDLL32.EXE to load library
- cmd.exe (PID: 6704)
Uses TASKKILL.EXE to kill Browsers
- cmd.exe (PID: 6704)
Executing commands from a ".bat" file
- 666.exe (PID: 4548)
Starts application with an unusual extension
- cmd.exe (PID: 6704)
Starts CMD.EXE for commands execution
- 666.exe (PID: 4548)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 6704)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6704)
The process executes VB scripts
- cmd.exe (PID: 6704)
The process executes via Task Scheduler
- explorer.exe (PID: 6560)
INFO
Changes the display of characters in the console
- cmd.exe (PID: 6704)
Checks supported languages
- chcp.com (PID: 6256)
- 666.exe (PID: 4548)
Create files in a temporary directory
- 666.exe (PID: 4548)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (41) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.6) |
| .exe | | | Win32 Executable (generic) (5.9) |
| .exe | | | Win16/32 Executable Delphi generic (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:07:30 08:52:45+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 70656 |
| InitializedDataSize: | 26624 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows command line |
Total processes
180
Monitored processes
42
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1168 | C:\WINDOWS\system32\net1 user "無路可走" | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1336 | reg add "HKEY_CURRENT_USER\Control Panel\Desktop" /v TileWallpaper /t REG_SZ /d "0" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
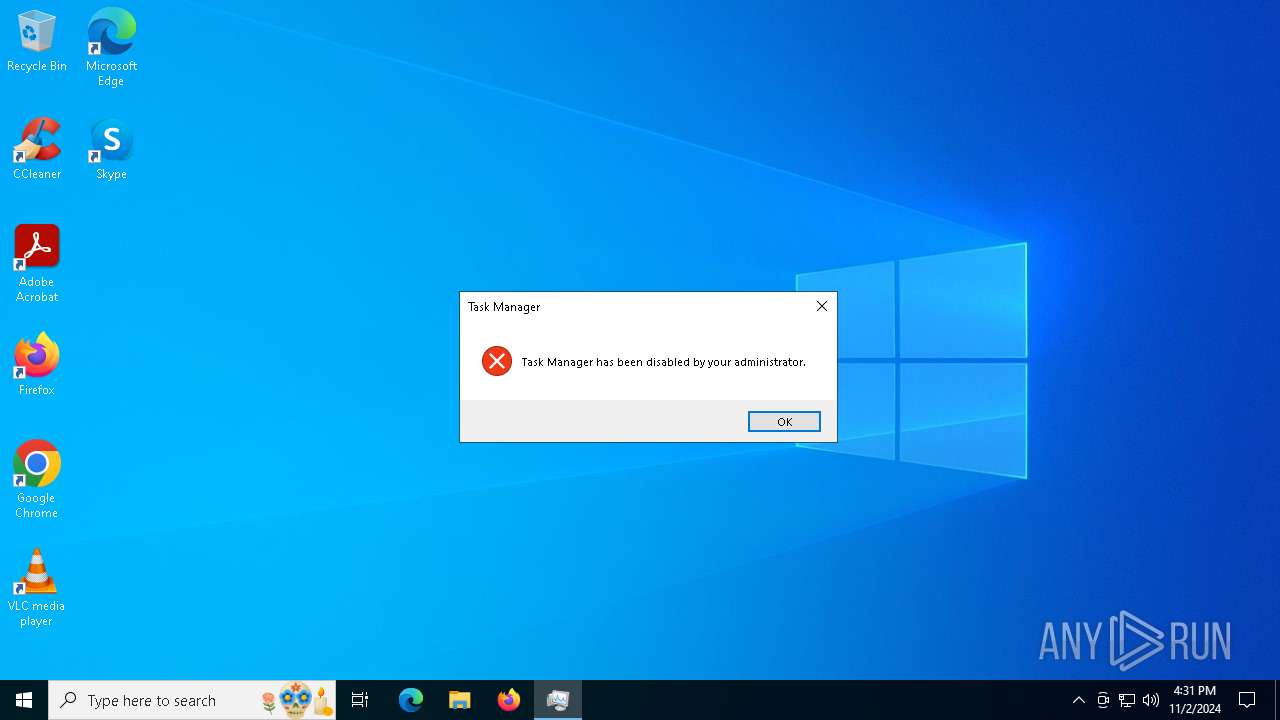
| 1452 | taskkill /f /im taskmgr.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1500 | taskkill /f /im discord.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1952 | taskkill /f /im powershell.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2000 | net localgroup "Benutzer" "無路可走" /add | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2708 | C:\WINDOWS\system32\net1 localgroup "Benutzer" "你是下一個" /add | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2796 | "C:\WINDOWS\system32\taskmgr.exe" /7 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Exit code: 2147500037 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3156 | reg add "HKEY_CURRENT_USER\Control Panel\Desktop" /v WallpaperStyle /t REG_SZ /d "2" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3604 | taskkill /f /im explorer.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
31 322
Read events
30 875
Write events
411
Delete events
36
Modification events
| (PID) Process: | (4304) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | DisableTaskMgr |
Value: 1 | |||
| (PID) Process: | (7136) reg.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | Wallpaper |
Value: C:\Users\admin\Desktop\666.jpg | |||
| (PID) Process: | (3156) reg.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | WallpaperStyle |
Value: 2 | |||
| (PID) Process: | (1336) reg.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | TileWallpaper |
Value: 0 | |||
| (PID) Process: | (6148) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2\CPC\Volume\{eaf65672-68c3-4f99-8d5c-104b5f4d8fff} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6148) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2\CPC\Volume\{2f5c5e73-85a9-11eb-90a8-9a9b76358421} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6148) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2\CPC\Volume\{2f5c5e72-85a9-11eb-90a8-9a9b76358421} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6148) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2\CPC\Volume\{2f5c5e71-85a9-11eb-90a8-9a9b76358421} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6148) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2\CPC\Volume |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6560) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2\CPC\Volume\{2f5c5e72-85a9-11eb-90a8-9a9b76358421} |
| Operation: | write | Name: | Data |
Value: D60D00000DF0ADBA41000000080000000000008000000000000000300000000000000000FF06E703FF00000016000000FA99B7261F00000004400000030000000000000000000000000000000000000000005C005C003F005C00530054004F005200410047004500230056006F006C0075006D00650023007B00390030006300660033006400640036002D0030006100660037002D0031003100650063002D0062003400380030002D003800300036006500360066003600650036003900360033007D002300300030003000300030003000300030003100460035003000300030003000300023007B00350033006600350036003300300064002D0062003600620066002D0031003100640030002D0039003400660032002D003000300061003000630039003100650066006200380062007D000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000005C005C003F005C0056006F006C0075006D0065007B00320066003500630035006500370032002D0038003500610039002D0031003100650062002D0039003000610038002D003900610039006200370036003300350038003400320031007D005C0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000004E005400460053000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF0000 | |||
Executable files
1
Suspicious files
287
Text files
185
Unknown types
14
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7156 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\DeviceSearchCache\AppCache133750386619041189.txt~RF8f1db.TMP | — | |
MD5:— | SHA256:— | |||
| 6704 | cmd.exe | C:\Users\admin\AppData\Local\Temp\msg.vbs | text | |
MD5:A622F171409E52016A6E87068DDF04F9 | SHA256:C5A1E783B627884942F110313C780A2FE140C2C5A77E261A07ACFE97A9479C9B | |||
| 4548 | 666.exe | C:\Users\admin\AppData\Local\Temp\BE19.tmp\BE1A.tmp\BE1B.bat | text | |
MD5:F2650F2B7CD26B6042303D74D8CB9560 | SHA256:E6A31BAF0726C64A08E2D5E7AC4C28D56B43C3343BE0FB758230229D92584530 | |||
| 7156 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\MetaData\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:3F20D86A62C38AF80F8EADA71261762B | SHA256:66E51A33204B05CA51CFFD098E74368E249065AEFDCCE2CC8233326F8EED0604 | |||
| 4548 | 666.exe | C:\Users\admin\AppData\Local\Temp\666.jpg | image | |
MD5:B0058B62EEF8F75CC5817C2727581049 | SHA256:7A437FEDC2CF3AC7CE6C6004A77C8D76745E92E5820FB2C3334AE21576EB1FFB | |||
| 7156 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\Content\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | der | |
MD5:309C222F85BCA69AF3BF3301770614A4 | SHA256:8A6AC095CD1CCF7E3AEC06632AAFE71FBC7FC2E12BE0D2E98A58E17CCB43067D | |||
| 7156 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\63\f4st08wpuYBQ5KWRJ3MqAsJB8zg[1].css | text | |
MD5:3D24779C6014BCFEFB3D9A80B8F3567B | SHA256:A7EF8FAA37710D7E90C9C8950C203C8DA82410780F872E4F217EE636250D831F | |||
| 7156 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\INetCache\Q84V0JUH\-UAIppANYxiGpRWJy2NDph4qOEw.gz[1].js | binary | |
MD5:9E527B91C2D8B31B0017B76049B5E4E3 | SHA256:38EDF0F961C1CCB287880B88F12F370775FC65B2E28227EEE215E849CDBE9BBC | |||
| 7156 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\TokenBroker\Cache\fbaf94e759052658216786bfbabcdced1b67a5c2.tbres | binary | |
MD5:321B060A20D692CF6202CDA4DE3DEE82 | SHA256:72F2E86A6FD9D05103E197E3D4D2D5EB6343F255F58AB33506D4932E646F0A73 | |||
| 7156 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\ConstraintIndex\Apps_{bff2d3dd-a1e0-41f3-8656-379b2aa5cedc}\0.0.filtertrie.intermediate.txt | text | |
MD5:313FB75B427790D01342FE144D9C3C06 | SHA256:50DBBA1A26C02E1C1B831C474708E68C9B11E3FCF6B254AE908A2C3007D88100 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
41
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2776 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7156 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4292 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4292 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7156 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
7156 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7156 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3524 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6944 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
7156 | SearchApp.exe | 92.123.104.17:443 | r.bing.com | Akamai International B.V. | DE | whitelisted |
7156 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
7156 | SearchApp.exe | 92.123.104.15:443 | r.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
r.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |