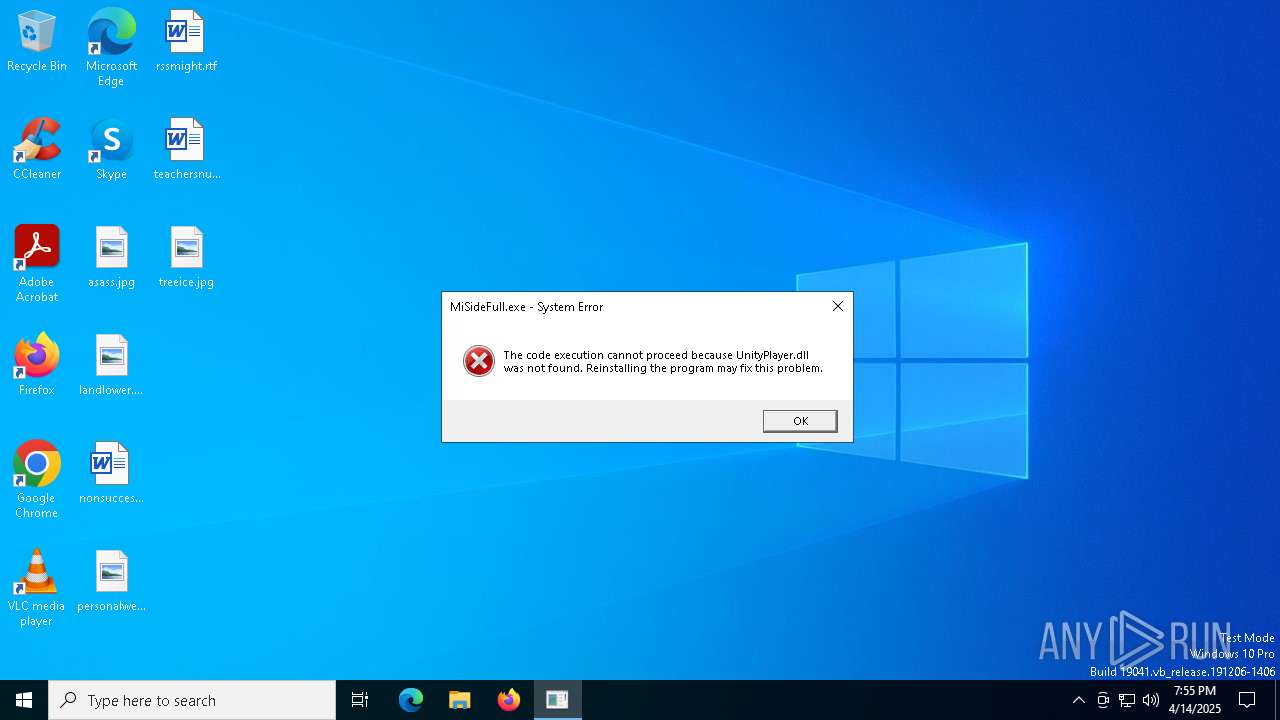
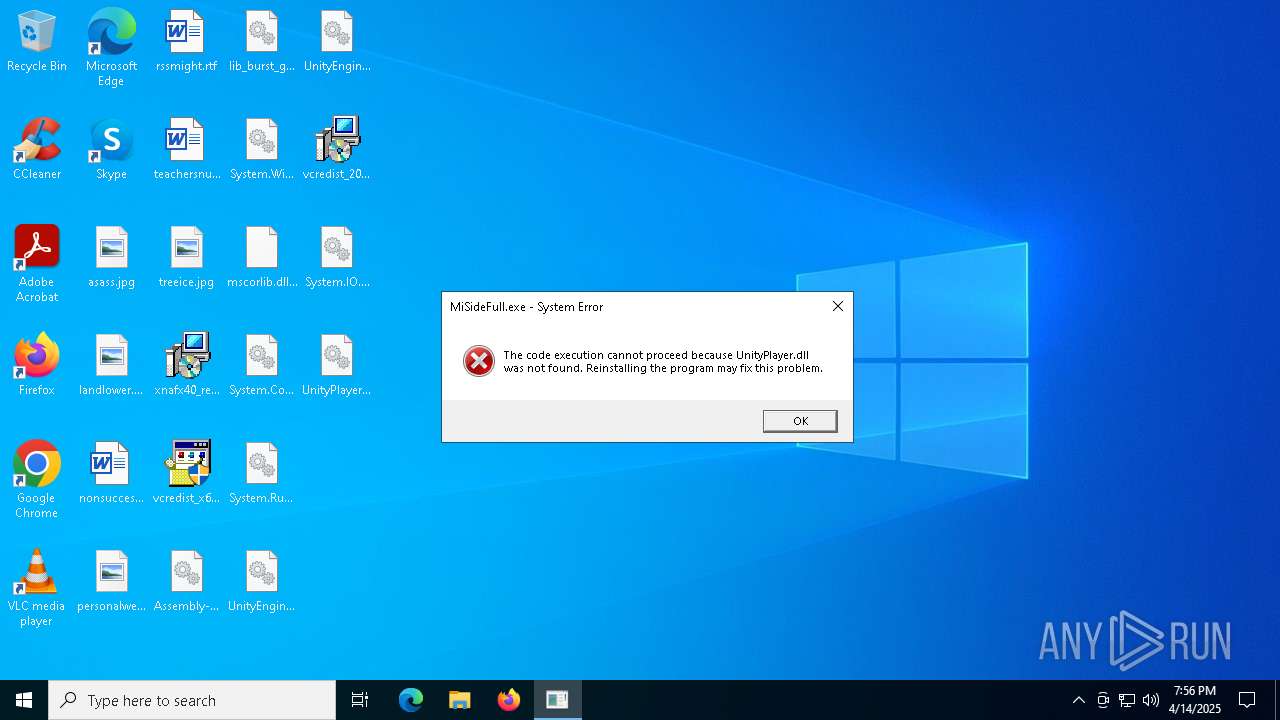
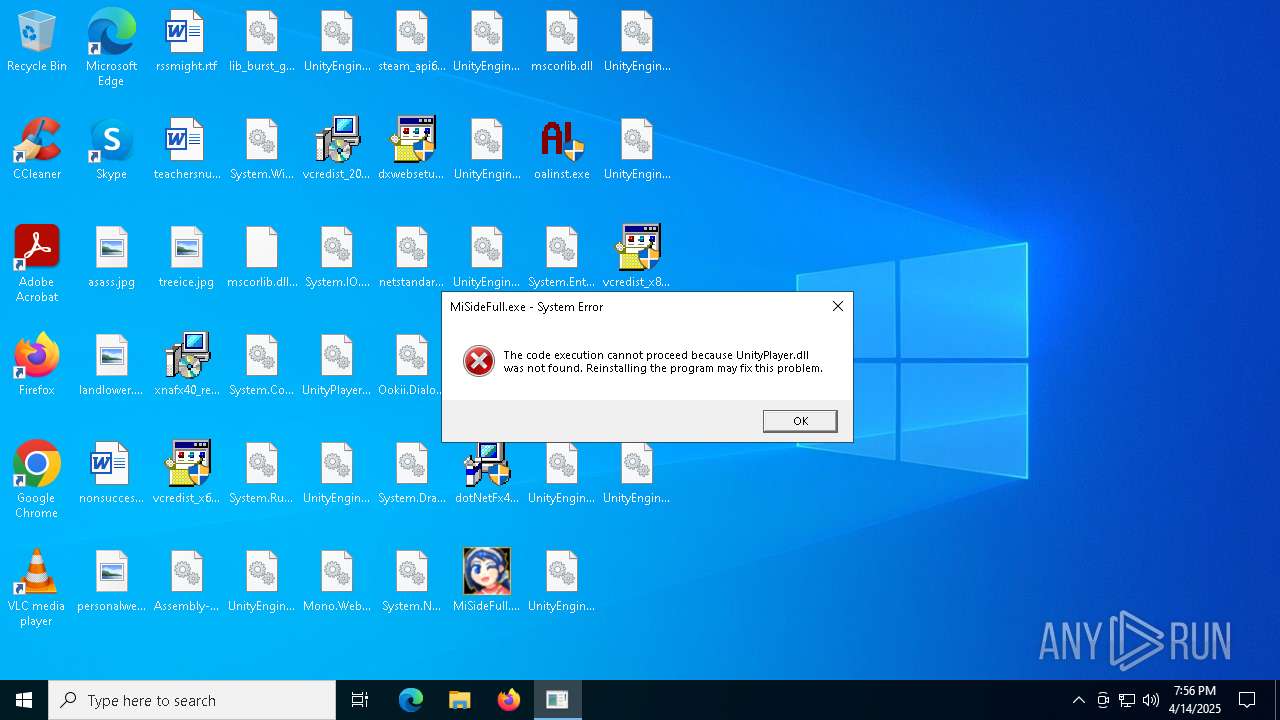
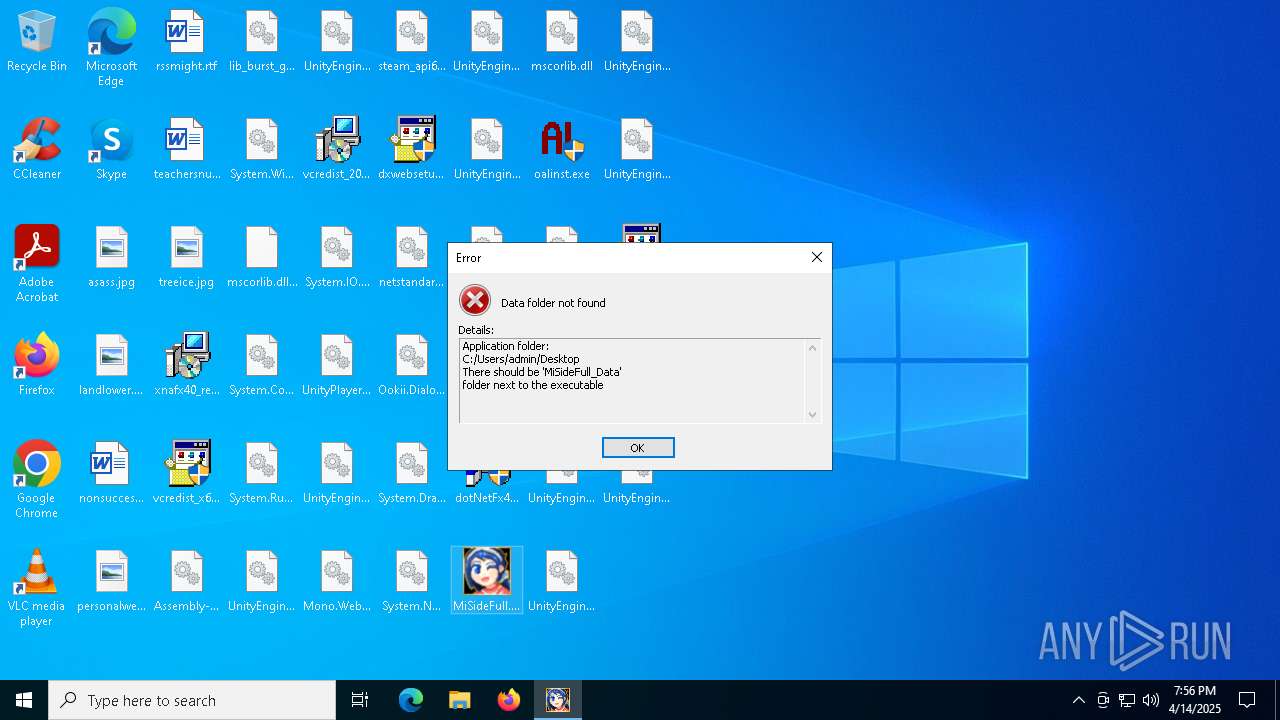
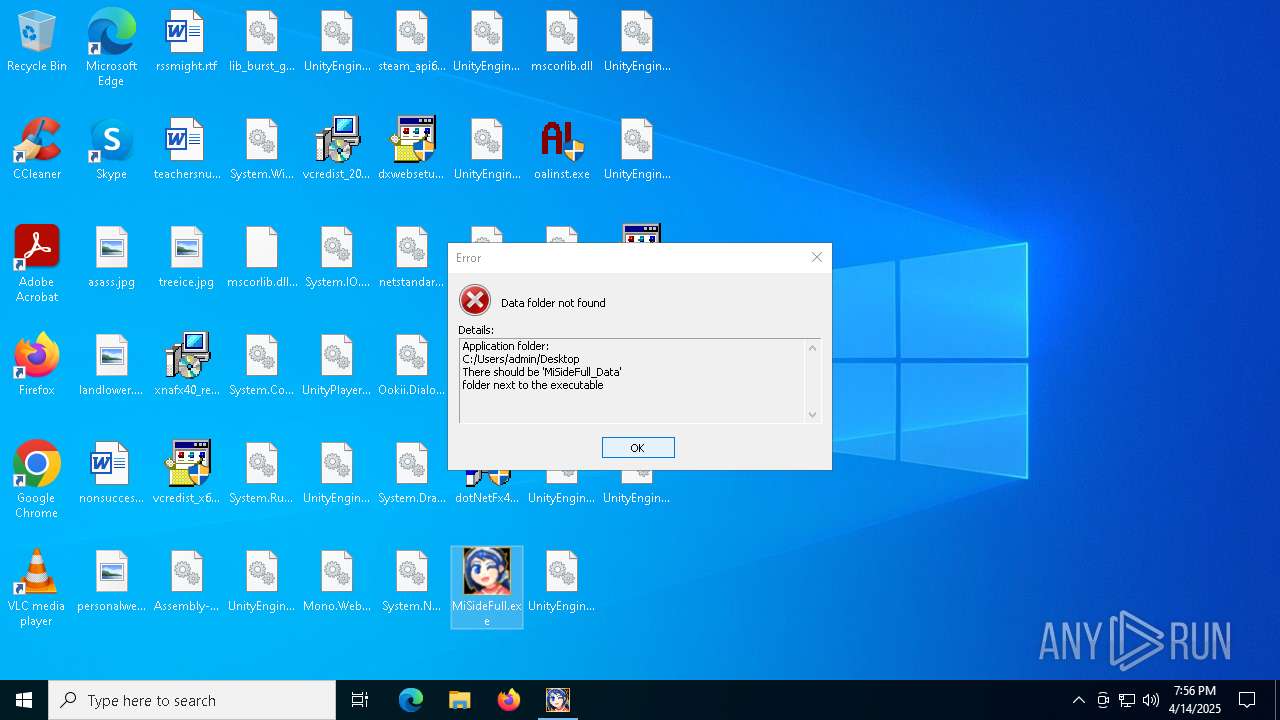
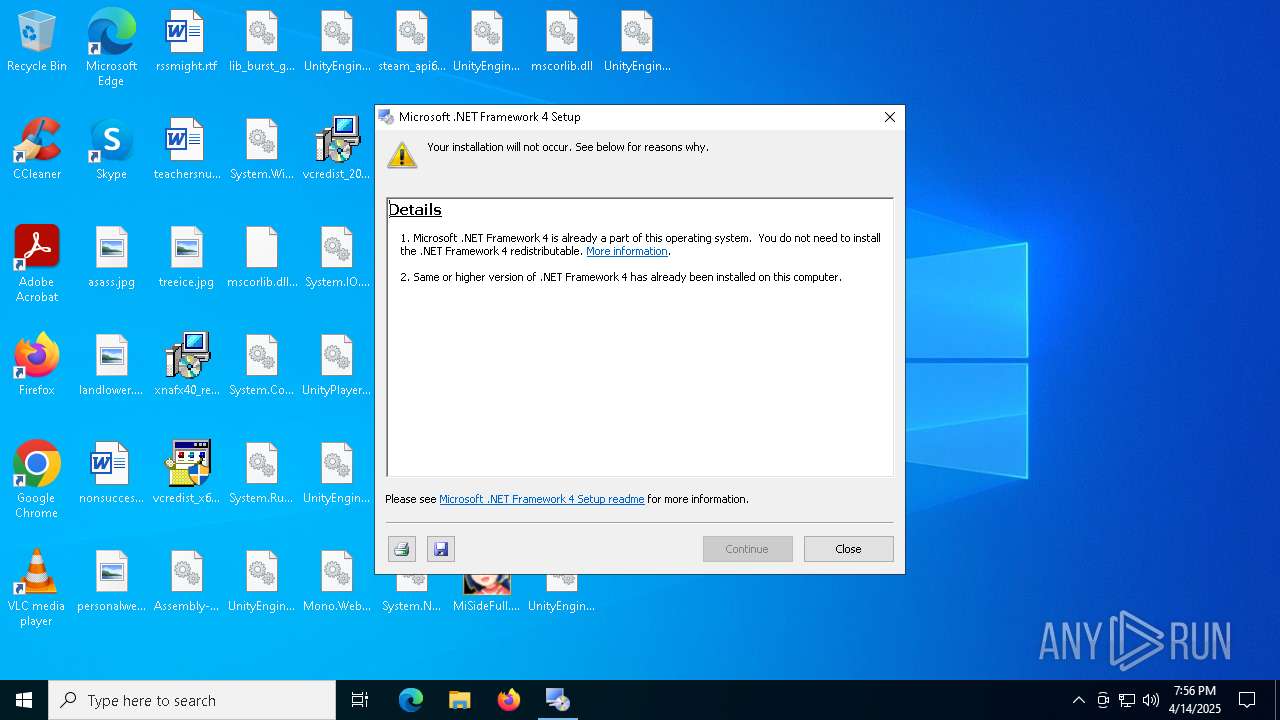
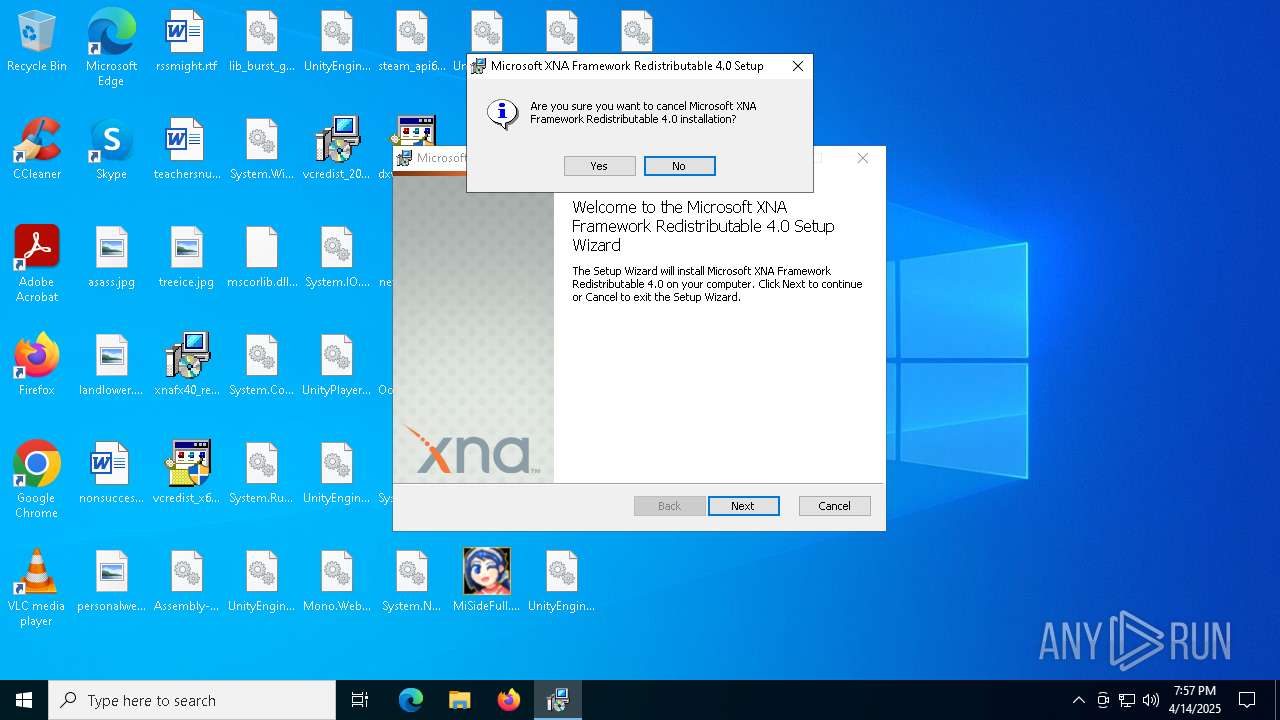
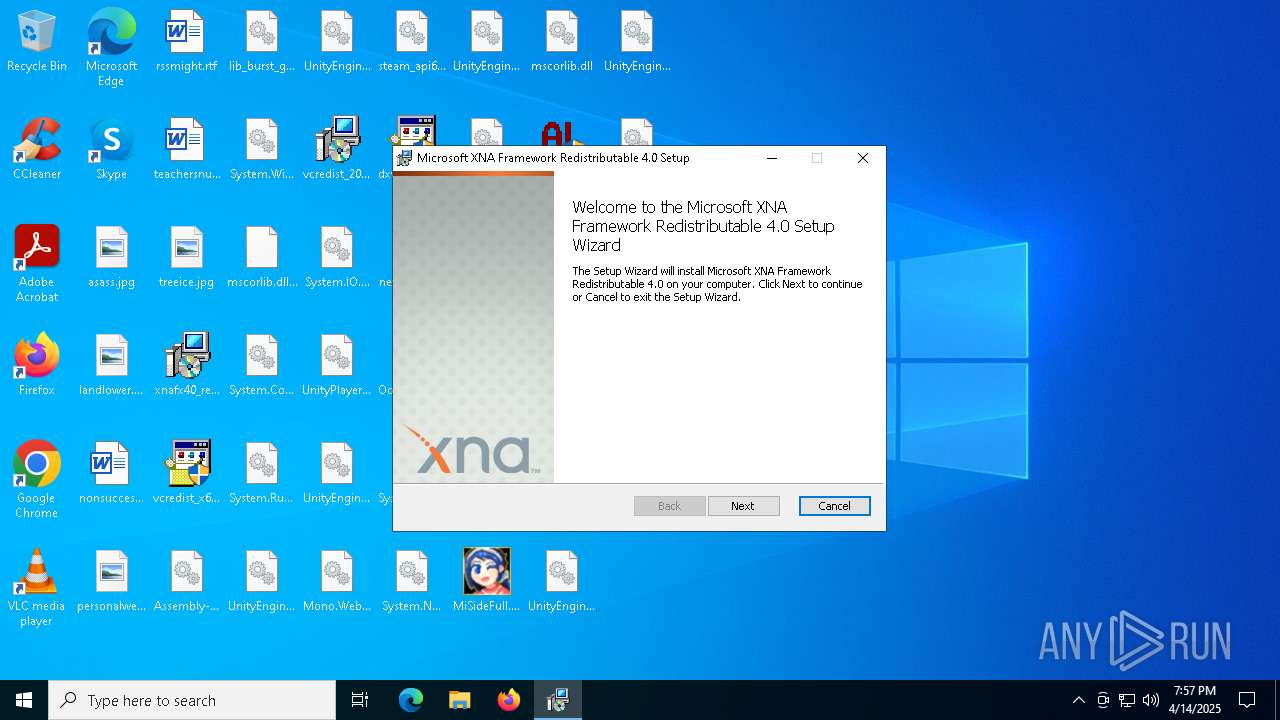
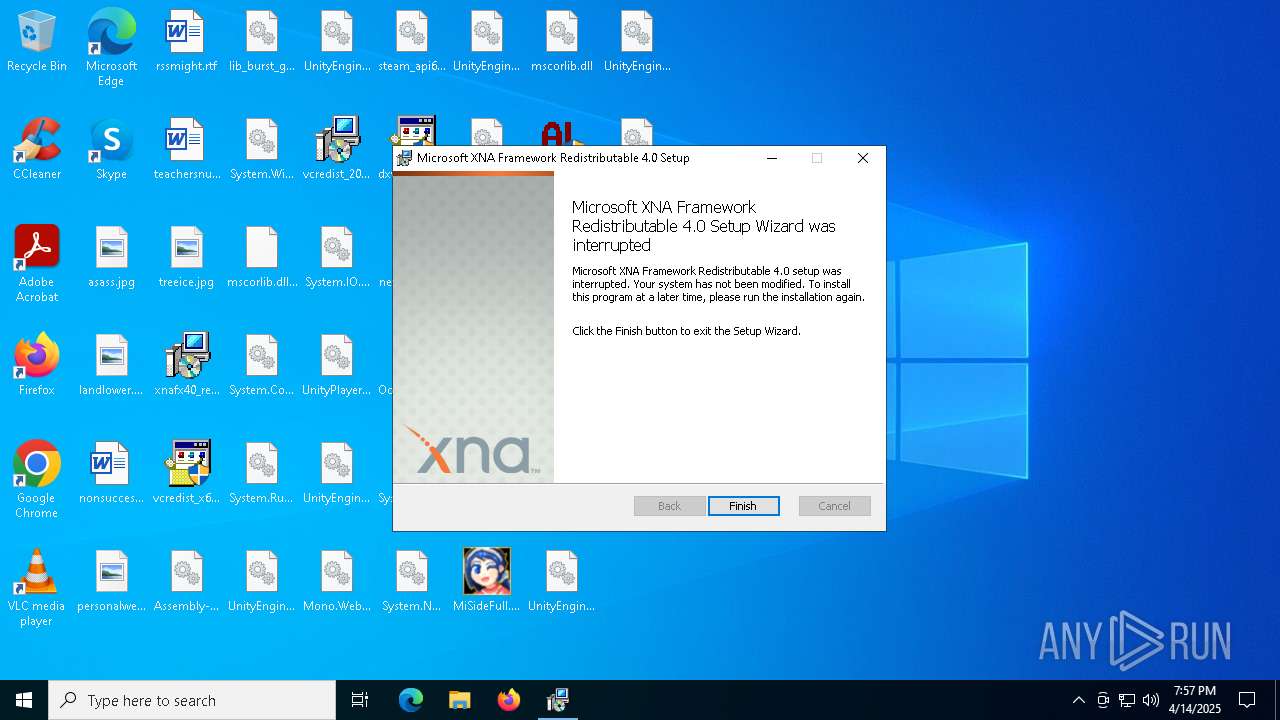
| File name: | MiSideFull.exe |
| Full analysis: | https://app.any.run/tasks/baf4b8e2-719c-486d-9f61-5a69b39069fb |
| Verdict: | Malicious activity |
| Analysis date: | April 14, 2025, 19:55:10 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 8 sections |
| MD5: | ED30491331307BC484F794608A568C37 |
| SHA1: | D97FF6C498E52D35B2F69398D0A5900068DD8074 |
| SHA256: | 602C7ED2EA1A56469806D6F7ED413E6BD45BD211B3D4EAF0C41CC2ABD34B2129 |
| SSDEEP: | 49152:6SmkVwbBbFqSUa5gskaf4E4nZw+59YK7/IitkyPDR:rmkeFbYSUab4nZz9r/IedP |
MALICIOUS
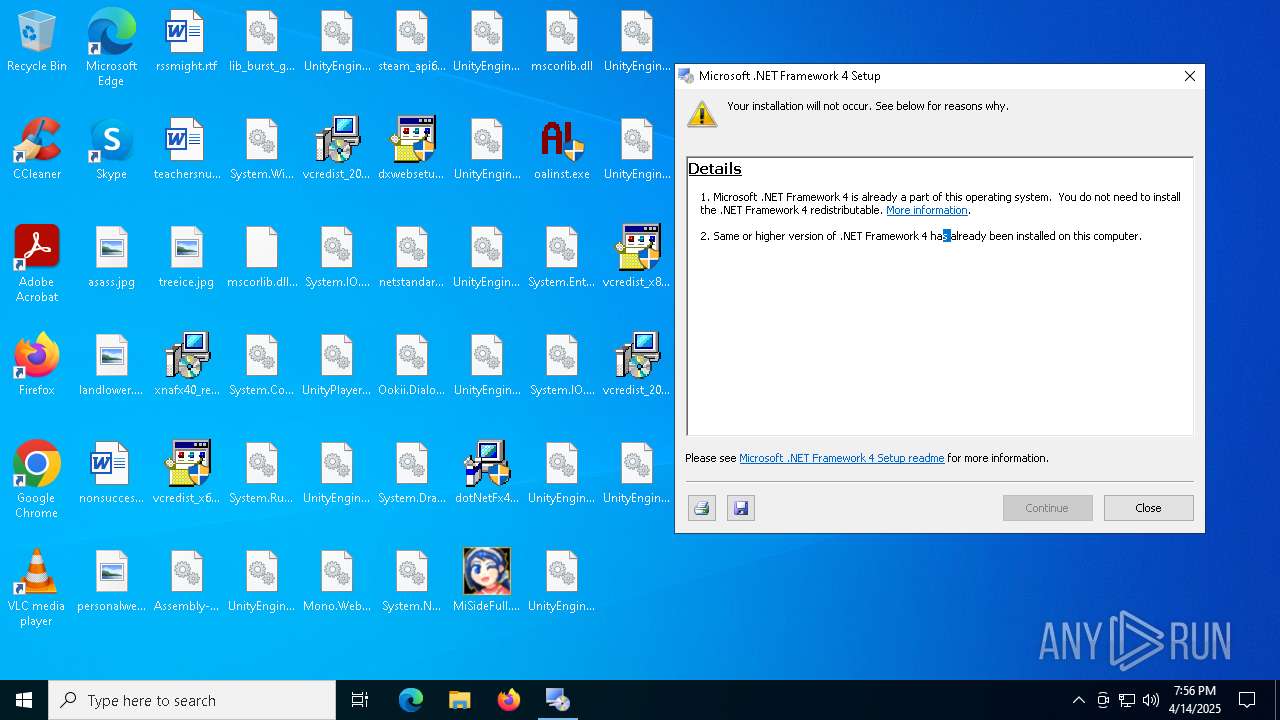
Executing a file with an untrusted certificate
- dotNetFx40_Full_setup.exe (PID: 5228)
- dotNetFx40_Full_setup.exe (PID: 4120)
- Setup.exe (PID: 6972)
- vcredist_x86.exe (PID: 6192)
- vcredist_x86.exe (PID: 4728)
- Setup.exe (PID: 4380)
- oalinst.exe (PID: 5740)
- oalinst.exe (PID: 5124)
- dxwebsetup.exe (PID: 2568)
- dxwebsetup.exe (PID: 3016)
- vcredist_x64.exe (PID: 4068)
- vcredist_x64.exe (PID: 2908)
- Setup.exe (PID: 4620)
Changes the autorun value in the registry
- dxwebsetup.exe (PID: 3016)
SUSPICIOUS
Starts a Microsoft application from unusual location
- dotNetFx40_Full_setup.exe (PID: 5228)
- dotNetFx40_Full_setup.exe (PID: 4120)
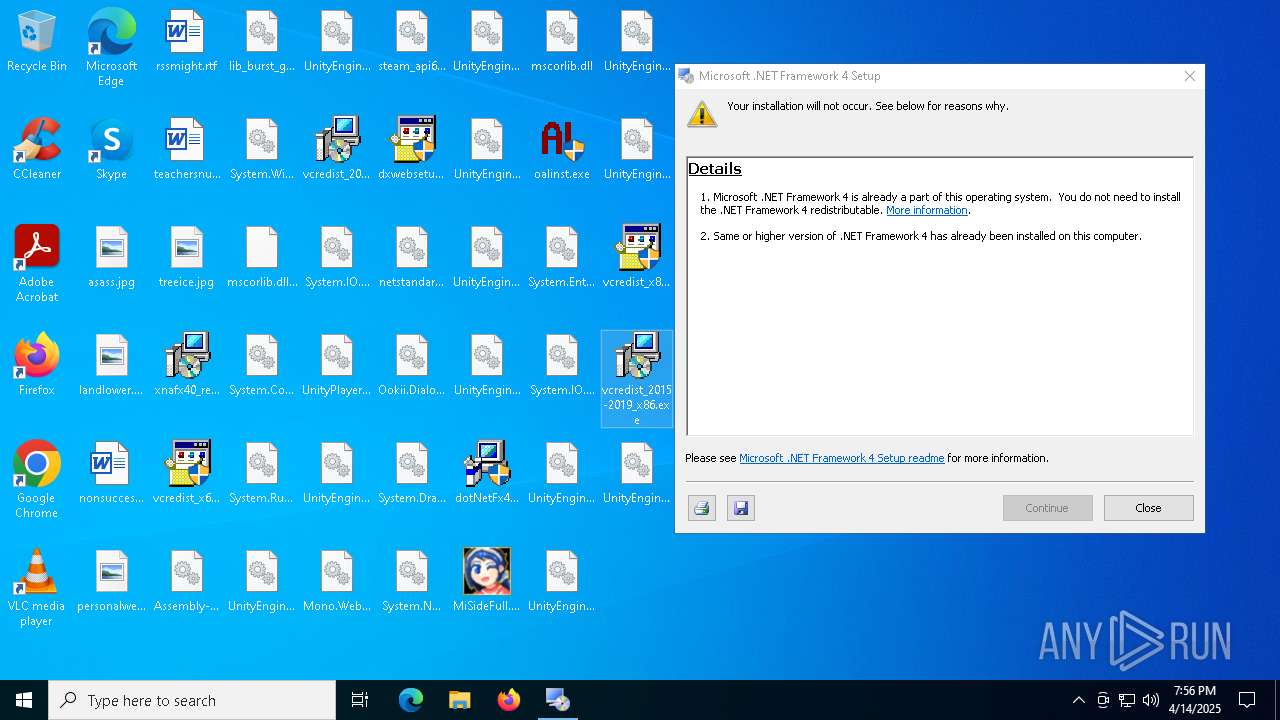
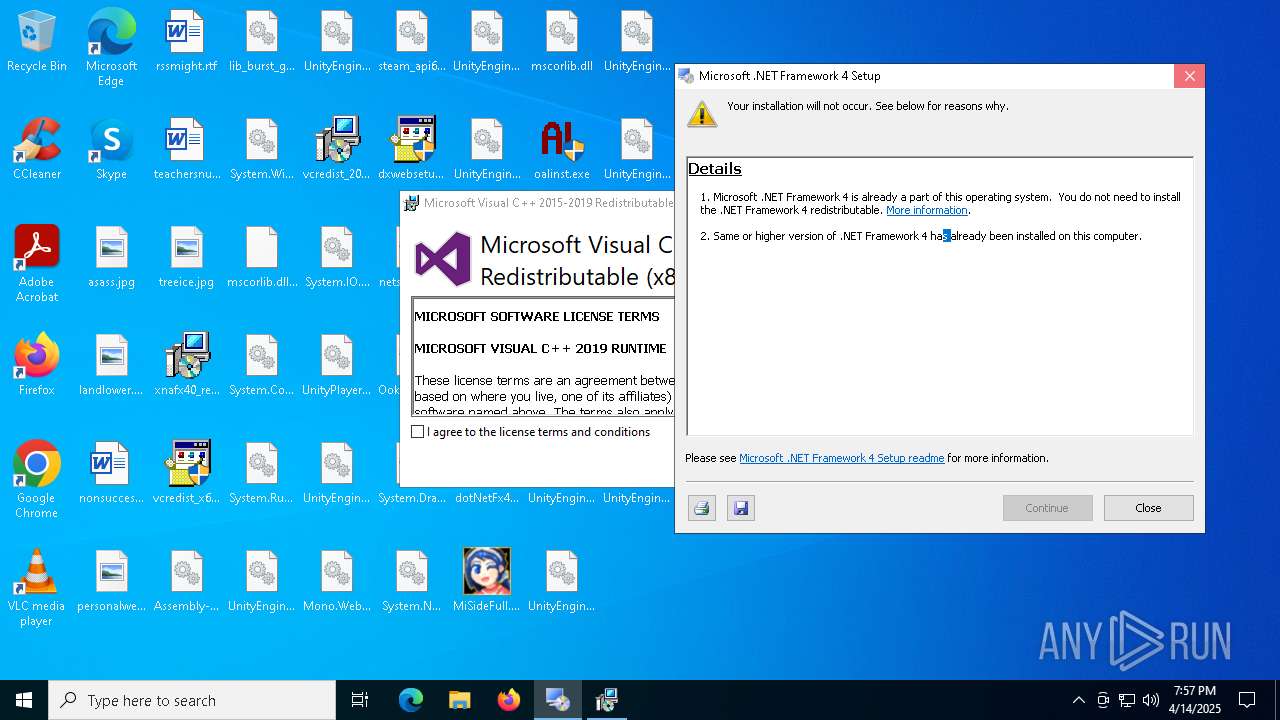
- vcredist_2015-2019_x86.exe (PID: 2516)
- vcredist_2015-2019_x86.exe (PID: 4560)
- vcredist_x86.exe (PID: 6192)
- vcredist_x86.exe (PID: 4728)
- dxwsetup.exe (PID: 3992)
- dxwebsetup.exe (PID: 2568)
- dxwebsetup.exe (PID: 3016)
- vcredist_2015-2019_x64.exe (PID: 132)
- vcredist_2015-2019_x64.exe (PID: 236)
- vcredist_x64.exe (PID: 2908)
- vcredist_x64.exe (PID: 4068)
Executable content was dropped or overwritten
- dotNetFx40_Full_setup.exe (PID: 4120)
- vcredist_2015-2019_x86.exe (PID: 2516)
- vcredist_2015-2019_x86.exe (PID: 4560)
- vcredist_x86.exe (PID: 4728)
- oalinst.exe (PID: 5740)
- dxwebsetup.exe (PID: 3016)
- vcredist_2015-2019_x64.exe (PID: 132)
- vcredist_2015-2019_x64.exe (PID: 236)
- dxwsetup.exe (PID: 3992)
- vcredist_x64.exe (PID: 4068)
Process drops legitimate windows executable
- dotNetFx40_Full_setup.exe (PID: 4120)
- vcredist_2015-2019_x86.exe (PID: 2516)
- vcredist_x86.exe (PID: 4728)
- msiexec.exe (PID: 6108)
- dxwebsetup.exe (PID: 3016)
- dxwsetup.exe (PID: 3992)
- vcredist_2015-2019_x64.exe (PID: 132)
- vcredist_x64.exe (PID: 4068)
Creates file in the systems drive root
- dotNetFx40_Full_setup.exe (PID: 4120)
- vcredist_x86.exe (PID: 4728)
- vcredist_x64.exe (PID: 4068)
Searches for installed software
- vcredist_2015-2019_x86.exe (PID: 4560)
- vcredist_2015-2019_x64.exe (PID: 236)
Reads security settings of Internet Explorer
- Setup.exe (PID: 4380)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 6108)
The process drops C-runtime libraries
- msiexec.exe (PID: 6108)
Creates a software uninstall entry
- oalinst.exe (PID: 5740)
INFO
The sample compiled with english language support
- MiSideFull.exe (PID: 4000)
- dotNetFx40_Full_setup.exe (PID: 4120)
- vcredist_2015-2019_x86.exe (PID: 2516)
- vcredist_2015-2019_x86.exe (PID: 4560)
- vcredist_x86.exe (PID: 4728)
- msiexec.exe (PID: 6108)
- oalinst.exe (PID: 5740)
- dxwebsetup.exe (PID: 3016)
- dxwsetup.exe (PID: 3992)
- vcredist_2015-2019_x64.exe (PID: 132)
- vcredist_2015-2019_x64.exe (PID: 236)
- vcredist_x64.exe (PID: 4068)
Creates files or folders in the user directory
- MiSideFull.exe (PID: 6036)
- msiexec.exe (PID: 6108)
- msiexec.exe (PID: 4464)
Reads the software policy settings
- slui.exe (PID: 5216)
- Setup.exe (PID: 4380)
- msiexec.exe (PID: 6108)
- slui.exe (PID: 976)
- msiexec.exe (PID: 4464)
Manual execution by a user
- MiSideFull.exe (PID: 6036)
- dotNetFx40_Full_setup.exe (PID: 5228)
- dotNetFx40_Full_setup.exe (PID: 4120)
- vcredist_2015-2019_x86.exe (PID: 2516)
- vcredist_x86.exe (PID: 6192)
- vcredist_x86.exe (PID: 4728)
- oalinst.exe (PID: 5124)
- oalinst.exe (PID: 5740)
- dxwebsetup.exe (PID: 2568)
- dxwebsetup.exe (PID: 3016)
- msiexec.exe (PID: 4464)
- vcredist_2015-2019_x64.exe (PID: 132)
- vcredist_x64.exe (PID: 2908)
- vcredist_x64.exe (PID: 4068)
Checks supported languages
- MiSideFull.exe (PID: 6036)
- dotNetFx40_Full_setup.exe (PID: 4120)
- Setup.exe (PID: 6972)
- vcredist_2015-2019_x86.exe (PID: 4560)
- vcredist_2015-2019_x86.exe (PID: 2516)
- Setup.exe (PID: 4380)
- vcredist_x86.exe (PID: 4728)
- msiexec.exe (PID: 6108)
- oalinst.exe (PID: 5740)
- dxwsetup.exe (PID: 3992)
- dxwebsetup.exe (PID: 3016)
- vcredist_2015-2019_x64.exe (PID: 236)
- vcredist_2015-2019_x64.exe (PID: 132)
- msiexec.exe (PID: 2596)
- vcredist_x64.exe (PID: 4068)
- Setup.exe (PID: 4620)
Reads the computer name
- MiSideFull.exe (PID: 6036)
- dotNetFx40_Full_setup.exe (PID: 4120)
- Setup.exe (PID: 6972)
- vcredist_2015-2019_x86.exe (PID: 4560)
- vcredist_x86.exe (PID: 4728)
- Setup.exe (PID: 4380)
- msiexec.exe (PID: 6108)
- oalinst.exe (PID: 5740)
- vcredist_2015-2019_x64.exe (PID: 236)
- dxwsetup.exe (PID: 3992)
- msiexec.exe (PID: 2596)
- vcredist_x64.exe (PID: 4068)
- Setup.exe (PID: 4620)
Create files in a temporary directory
- dotNetFx40_Full_setup.exe (PID: 4120)
- Setup.exe (PID: 6972)
- vcredist_2015-2019_x86.exe (PID: 2516)
- vcredist_2015-2019_x86.exe (PID: 4560)
- Setup.exe (PID: 4380)
- dxwebsetup.exe (PID: 3016)
- vcredist_2015-2019_x64.exe (PID: 132)
- vcredist_2015-2019_x64.exe (PID: 236)
- Setup.exe (PID: 4620)
Reads the machine GUID from the registry
- dotNetFx40_Full_setup.exe (PID: 4120)
- vcredist_x86.exe (PID: 4728)
- msiexec.exe (PID: 6108)
- Setup.exe (PID: 4380)
- vcredist_x64.exe (PID: 4068)
The sample compiled with czech language support
- dotNetFx40_Full_setup.exe (PID: 4120)
The sample compiled with arabic language support
- dotNetFx40_Full_setup.exe (PID: 4120)
The sample compiled with turkish language support
- dotNetFx40_Full_setup.exe (PID: 4120)
The sample compiled with french language support
- dotNetFx40_Full_setup.exe (PID: 4120)
- vcredist_x86.exe (PID: 4728)
- msiexec.exe (PID: 6108)
- vcredist_x64.exe (PID: 4068)
The sample compiled with chinese language support
- dotNetFx40_Full_setup.exe (PID: 4120)
- vcredist_x86.exe (PID: 4728)
- msiexec.exe (PID: 6108)
- vcredist_x64.exe (PID: 4068)
The sample compiled with korean language support
- dotNetFx40_Full_setup.exe (PID: 4120)
- vcredist_x86.exe (PID: 4728)
- msiexec.exe (PID: 6108)
- vcredist_x64.exe (PID: 4068)
The sample compiled with japanese language support
- dotNetFx40_Full_setup.exe (PID: 4120)
- vcredist_x86.exe (PID: 4728)
- msiexec.exe (PID: 6108)
- vcredist_x64.exe (PID: 4068)
The sample compiled with swedish language support
- dotNetFx40_Full_setup.exe (PID: 4120)
The sample compiled with spanish language support
- dotNetFx40_Full_setup.exe (PID: 4120)
- vcredist_x86.exe (PID: 4728)
- msiexec.exe (PID: 6108)
- vcredist_x64.exe (PID: 4068)
The sample compiled with Italian language support
- dotNetFx40_Full_setup.exe (PID: 4120)
- vcredist_x86.exe (PID: 4728)
- msiexec.exe (PID: 6108)
- vcredist_x64.exe (PID: 4068)
Reads CPU info
- Setup.exe (PID: 6972)
- Setup.exe (PID: 4380)
- Setup.exe (PID: 4620)
The sample compiled with portuguese language support
- dotNetFx40_Full_setup.exe (PID: 4120)
The sample compiled with polish language support
- dotNetFx40_Full_setup.exe (PID: 4120)
The sample compiled with russian language support
- dotNetFx40_Full_setup.exe (PID: 4120)
- vcredist_x86.exe (PID: 4728)
- msiexec.exe (PID: 6108)
- vcredist_x64.exe (PID: 4068)
The sample compiled with german language support
- dotNetFx40_Full_setup.exe (PID: 4120)
- vcredist_x86.exe (PID: 4728)
- msiexec.exe (PID: 6108)
- vcredist_x64.exe (PID: 4068)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6108)
Checks proxy server information
- slui.exe (PID: 976)
- Setup.exe (PID: 4380)
- msiexec.exe (PID: 4464)
Creates a software uninstall entry
- msiexec.exe (PID: 6108)
Creates files in the program directory
- oalinst.exe (PID: 5740)
Failed to create an executable file in Windows directory
- msiexec.exe (PID: 4464)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 4464)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 2516)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:01:31 10:09:22+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.28 |
| CodeSize: | 41472 |
| InitializedDataSize: | 615936 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1260 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2021.3.35.31558 |
| ProductVersionNumber: | 2021.3.35.31558 |
| FileFlagsMask: | 0x0017 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| FileVersion: | 2021.3.35.1407814 |
| LegalCopyright: | (c) 2005-2024 Unity Technologies. All rights reserved. |
| ProductVersion: | 2021.3.35f1 (157b46ce122a) |
Total processes
166
Monitored processes
27
Malicious processes
6
Suspicious processes
10
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
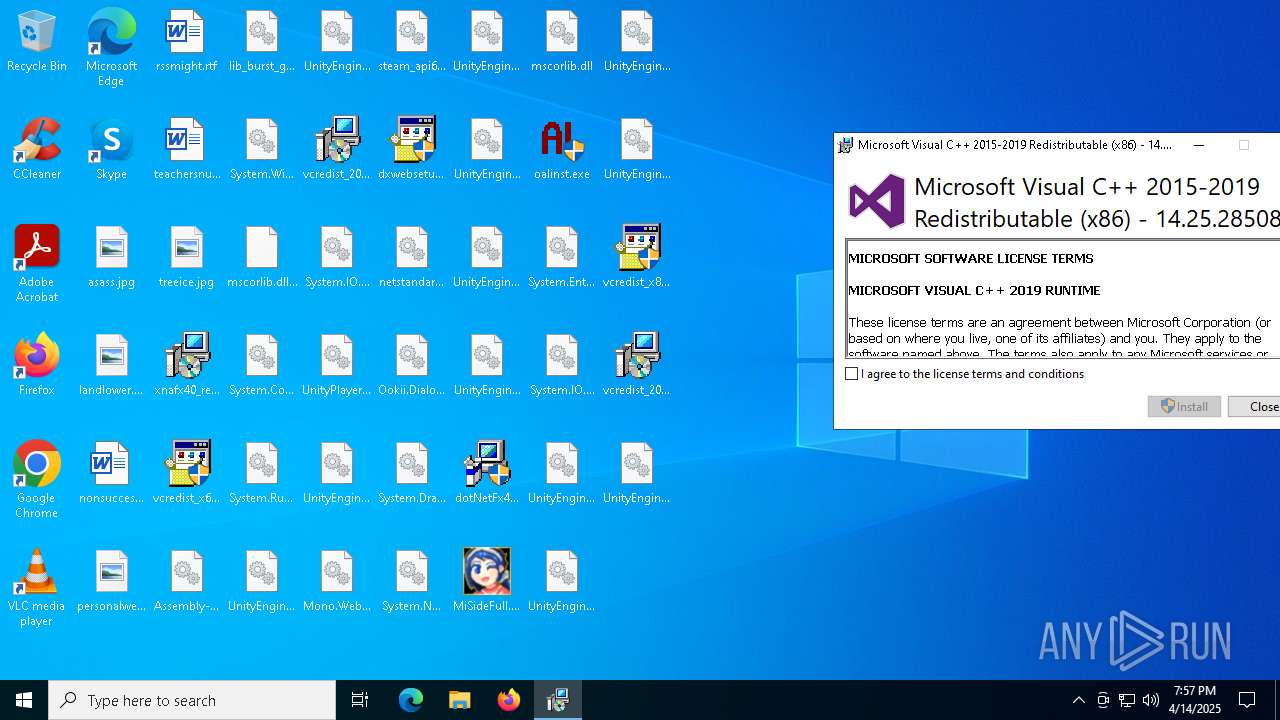
| 132 | "C:\Users\admin\Desktop\vcredist_2015-2019_x64.exe" | C:\Users\admin\Desktop\vcredist_2015-2019_x64.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Visual C++ 2015-2019 Redistributable (x64) - 14.25.28508 Exit code: 1602 Version: 14.25.28508.3 Modules
| |||||||||||||||
| 236 | "C:\Users\admin\AppData\Local\Temp\{64244B8D-F787-459B-9E75-E9C1B1539EE8}\.cr\vcredist_2015-2019_x64.exe" -burn.clean.room="C:\Users\admin\Desktop\vcredist_2015-2019_x64.exe" -burn.filehandle.attached=632 -burn.filehandle.self=636 | C:\Users\admin\AppData\Local\Temp\{64244B8D-F787-459B-9E75-E9C1B1539EE8}\.cr\vcredist_2015-2019_x64.exe | vcredist_2015-2019_x64.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Visual C++ 2015-2019 Redistributable (x64) - 14.25.28508 Exit code: 1602 Version: 14.25.28508.3 Modules
| |||||||||||||||
| 976 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1852 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2516 | "C:\Users\admin\Desktop\vcredist_2015-2019_x86.exe" | C:\Users\admin\Desktop\vcredist_2015-2019_x86.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Visual C++ 2015-2019 Redistributable (x86) - 14.25.28508 Exit code: 1602 Version: 14.25.28508.3 Modules
| |||||||||||||||
| 2516 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2568 | "C:\Users\admin\Desktop\dxwebsetup.exe" | C:\Users\admin\Desktop\dxwebsetup.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: DirectX 9.0 Web setup Exit code: 3221226540 Version: 9.29.1962.0 Modules
| |||||||||||||||
| 2596 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2908 | "C:\Users\admin\Desktop\vcredist_x64.exe" | C:\Users\admin\Desktop\vcredist_x64.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Visual C++ 2010 x64 Redistributable Setup Exit code: 3221226540 Version: 10.0.30319.01 Modules
| |||||||||||||||
| 3016 | "C:\Users\admin\Desktop\dxwebsetup.exe" | C:\Users\admin\Desktop\dxwebsetup.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DirectX 9.0 Web setup Exit code: 2852126720 Version: 9.29.1962.0 Modules
| |||||||||||||||
Total events
14 319
Read events
14 114
Write events
195
Delete events
10
Modification events
| (PID) Process: | (6108) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: DC170000AD1C1E6E77ADDB01 | |||
| (PID) Process: | (6108) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 5513D85DAD8F36E3928A718FE829B467D4431C8C6A59F1F15E4F25EE67A1C159 | |||
| (PID) Process: | (6108) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (6108) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Folders |
| Operation: | write | Name: | c:\Config.Msi\ |
Value: | |||
| (PID) Process: | (6108) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Rollback\Scripts |
| Operation: | write | Name: | c:\Config.Msi\12b485.rbs |
Value: 31174007 | |||
| (PID) Process: | (6108) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Rollback\Scripts |
| Operation: | write | Name: | c:\Config.Msi\12b485.rbsLow |
Value: | |||
| (PID) Process: | (6108) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\7E4C35488E6280433B4A9504AC59CB06 |
| Operation: | write | Name: | D04BB691875110D32B98EBCF771AA1E1 |
Value: 02:\SOFTWARE\Microsoft\VisualStudio\10.0\VC\VCRedist\x86\Version | |||
| (PID) Process: | (6108) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\SharedDlls |
| Operation: | write | Name: | C:\WINDOWS\system32\mfc100.dll |
Value: 1 | |||
| (PID) Process: | (6108) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\8EBEE9DB288E3EA36B66B61AD16E6844 |
| Operation: | write | Name: | D04BB691875110D32B98EBCF771AA1E1 |
Value: c:\?WINDOWS\SysWOW64\mfc100.dll | |||
| (PID) Process: | (6108) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\SharedDlls |
| Operation: | write | Name: | C:\WINDOWS\system32\mfc100u.dll |
Value: 1 | |||
Executable files
107
Suspicious files
29
Text files
243
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4120 | dotNetFx40_Full_setup.exe | C:\889bcb60582f01a128\Graphics\Rotate2.ico | image | |
MD5:8419CAA81F2377E09B7F2F6218E505AE | SHA256:DB89D8A45C369303C04988322B2774D2C7888DA5250B4DAB2846DEEF58A7DE22 | |||
| 4120 | dotNetFx40_Full_setup.exe | C:\889bcb60582f01a128\watermark.bmp | image | |
MD5:B0075CEE80173D764C0237E840BA5879 | SHA256:AB18374B3AAB10E5979E080D0410579F9771DB888BA1B80A5D81BA8896E2D33A | |||
| 4120 | dotNetFx40_Full_setup.exe | C:\889bcb60582f01a128\header.bmp | image | |
MD5:514BFCD8DA66722A9639EB41ED3988B7 | SHA256:6B8201ED10CE18FFADE072B77C6D1FCACCF1D29ACB47D86F553D9BEEBD991290 | |||
| 4120 | dotNetFx40_Full_setup.exe | C:\889bcb60582f01a128\DisplayIcon.ico | image | |
MD5:F9657D290048E169FFABBBB9C7412BE0 | SHA256:B74AD253B9B8F9FCADE725336509143828EE739CC2B24782BE3ECFF26F229160 | |||
| 6036 | MiSideFull.exe | C:\Users\admin\AppData\LocalLow\Unknown Vendor\Unknown Unity Application\Player.log | text | |
MD5:0FB3E4B18D358EF575A236CD8C4FEADE | SHA256:809630D5F27B13B7F5A1764FE74C47406F027E8CFB276AC4AC77BCA7D3EB114D | |||
| 4120 | dotNetFx40_Full_setup.exe | C:\889bcb60582f01a128\Graphics\stop.ico | image | |
MD5:5DFA8D3ABCF4962D9EC41CFC7C0F75E3 | SHA256:B499E1B21091B539D4906E45B6FDF490D5445256B72871AECE2F5B2562C11793 | |||
| 4120 | dotNetFx40_Full_setup.exe | C:\889bcb60582f01a128\Graphics\Setup.ico | image | |
MD5:3D25D679E0FF0B8C94273DCD8B07049D | SHA256:288E9AD8F0201E45BC187839F15ACA79D6B9F76A7D3C9274C80F5D4A4C219C0F | |||
| 4120 | dotNetFx40_Full_setup.exe | C:\889bcb60582f01a128\Graphics\Rotate1.ico | image | |
MD5:26A00597735C5F504CF8B3E7E9A7A4C1 | SHA256:37026C4EA2182D7908B3CF0CEF8A6F72BDDCA5F1CFBC702F35B569AD689CF0AF | |||
| 4120 | dotNetFx40_Full_setup.exe | C:\889bcb60582f01a128\Graphics\Print.ico | image | |
MD5:7E55DDC6D611176E697D01C90A1212CF | SHA256:FF542E32330B123486797B410621E19EAFB39DF3997E14701AFA4C22096520ED | |||
| 4120 | dotNetFx40_Full_setup.exe | C:\889bcb60582f01a128\Graphics\Rotate3.ico | image | |
MD5:924FD539523541D42DAD43290E6C0DB5 | SHA256:02A7FE932029C6FA24D1C7CC06D08A27E84F43A0CBC47B7C43CAC59424B3D1F6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
22
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6564 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6564 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4464 | msiexec.exe | GET | 200 | 23.48.23.164:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6108 | msiexec.exe | GET | 200 | 23.48.23.144:80 | http://crl.microsoft.com/pki/crl/products/CSPCA.crl | unknown | — | — | whitelisted |
4464 | msiexec.exe | GET | 200 | 23.48.23.164:80 | http://crl.microsoft.com/pki/crl/products/CodeSigPCA.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6564 | SIHClient.exe | 20.109.210.53:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6564 | SIHClient.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
6564 | SIHClient.exe | 52.165.164.15:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5216 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |