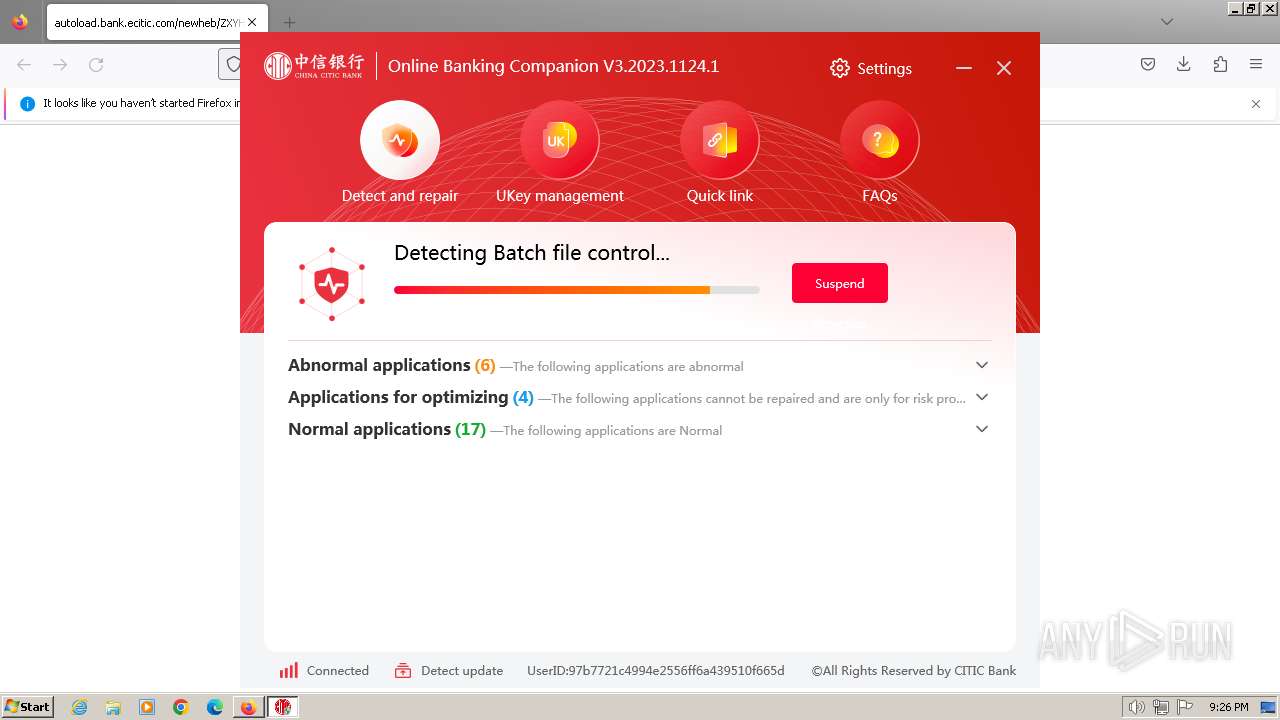
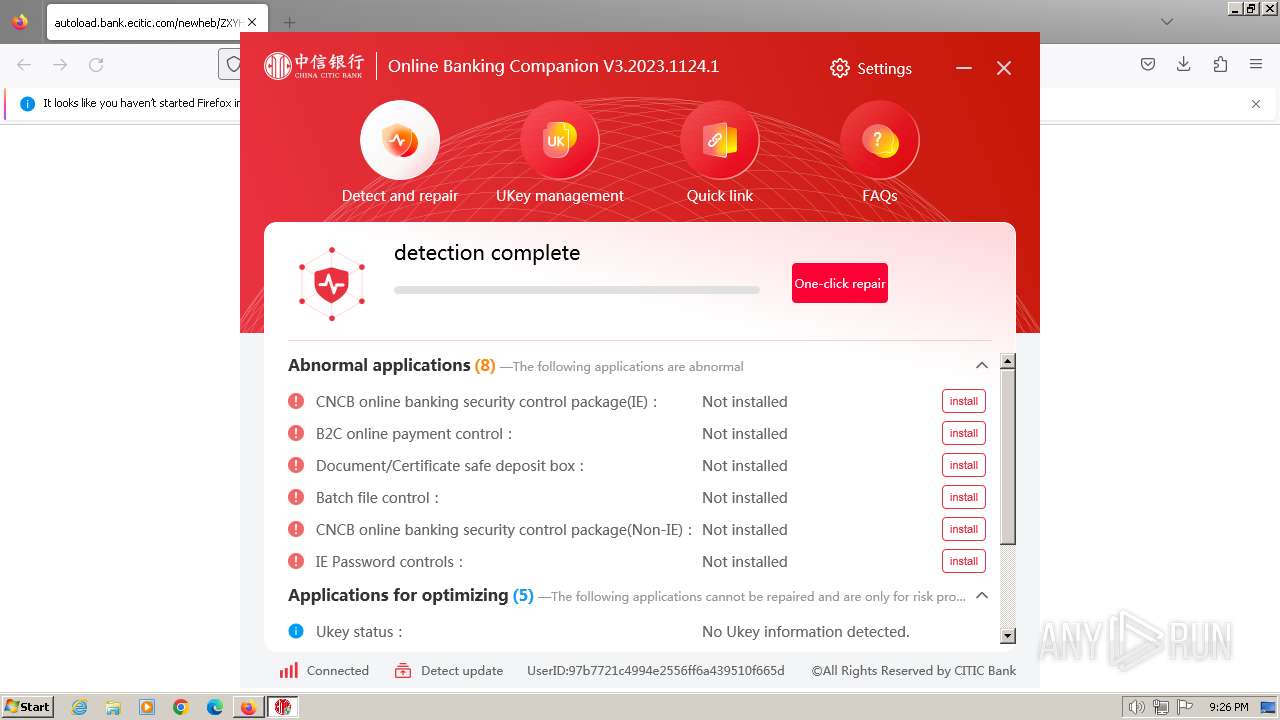
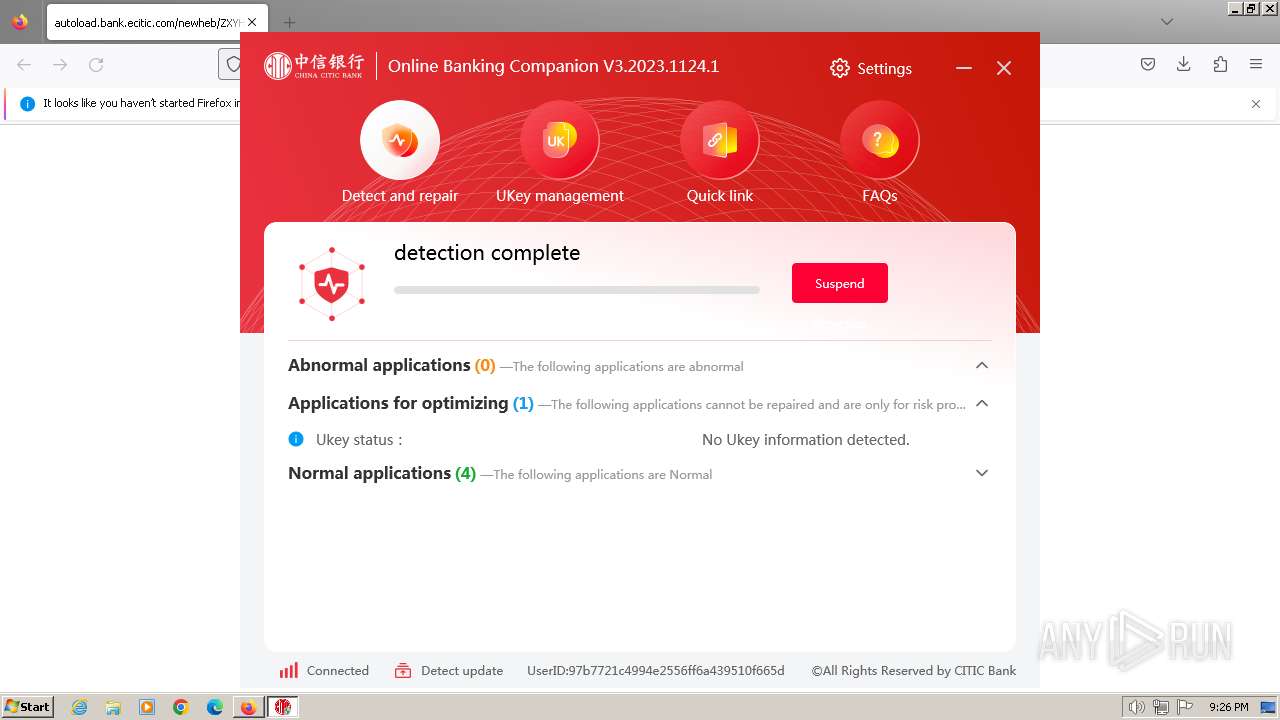
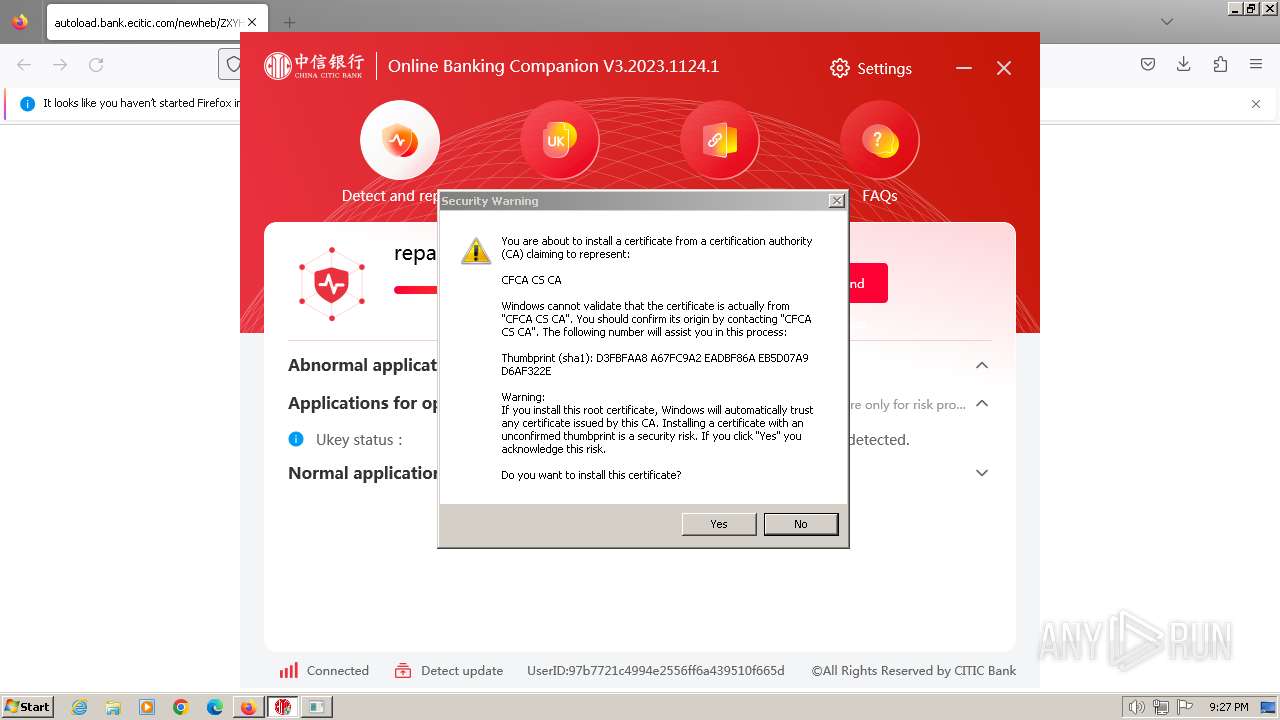
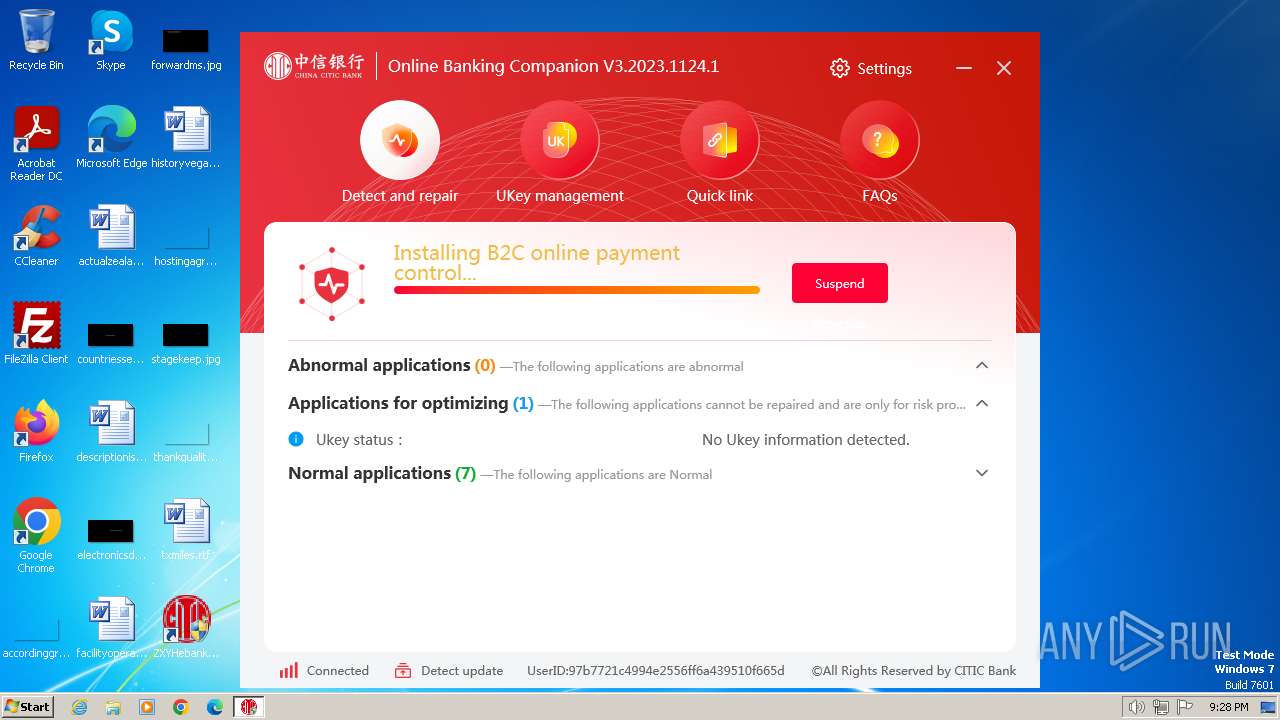
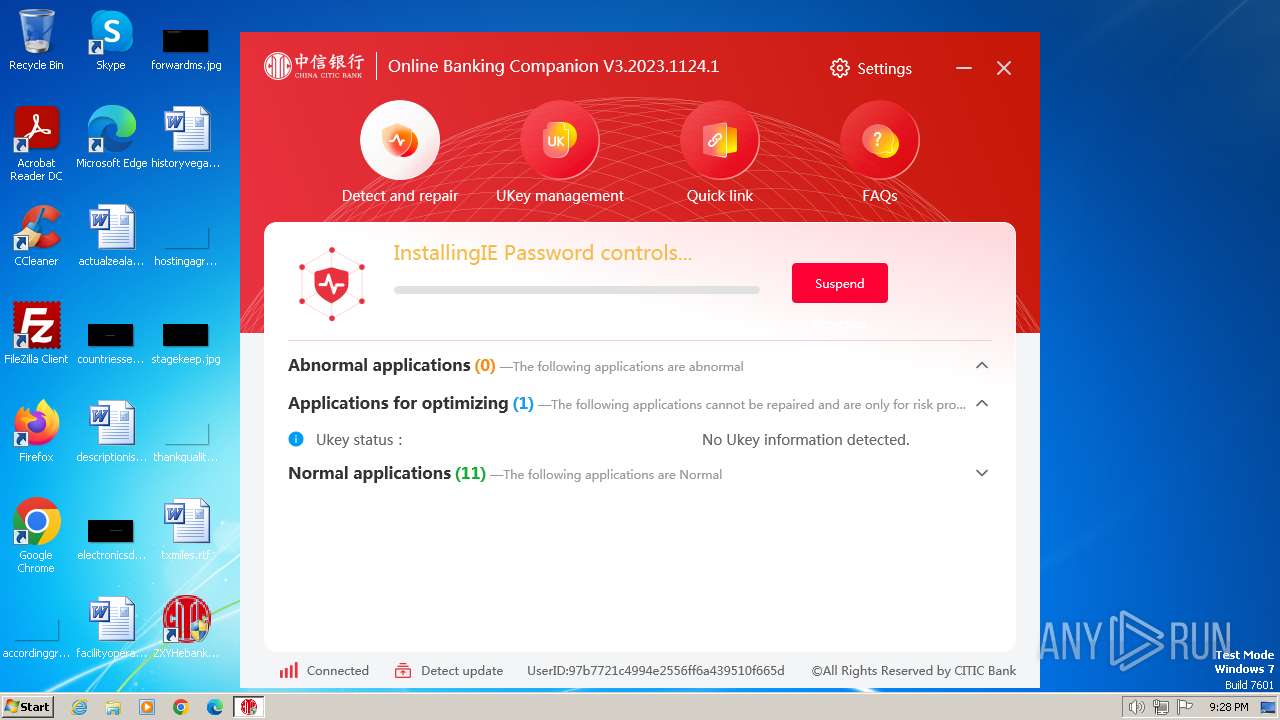
| URL: | https://autoload.bank.ecitic.com/newheb/ZXYHSetup.exe |
| Full analysis: | https://app.any.run/tasks/0fc33512-8b22-49dc-a872-2bb422360661 |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | January 01, 2024, 21:24:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | E766A2A5D6612653E8E17AFA97A68791 |
| SHA1: | EF23248236923D817FCF80EBA62787F2682F545C |
| SHA256: | 602BB38EF3B3B81525E8DC39B2B99AC1D9F6B194772D5E6070BB27A59D772221 |
| SSDEEP: | 3:N8bozELkFENAHK1ARQVkA:2EzBXRQaA |
MALICIOUS
Creates a writable file in the system directory
- CNCBGuardReg.exe (PID: 3816)
- CNCBSecPkg.tmp (PID: 3316)
- CNCBPayCtl.tmp (PID: 3616)
- regsvr32.exe (PID: 1936)
Registers / Runs the DLL via REGSVR32.EXE
- CNCBPayCtl.tmp (PID: 3616)
- CNCBSecPkg.tmp (PID: 3316)
Runs injected code in another process
- CNCBPayCtl.tmp (PID: 3616)
- ZXYHebankassit.exe (PID: 2452)
Actions looks like stealing of personal data
- ZXYHebankassit.exe (PID: 2452)
SUSPICIOUS
Detected use of alternative data streams (AltDS)
- ZXYHSetup.exe (PID: 752)
Reads the Internet Settings
- ZXYHebankassit.exe (PID: 2452)
Reads Microsoft Outlook installation path
- ZXYHebankassit.exe (PID: 2452)
Searches for installed software
- ZXYHebankassit.exe (PID: 2452)
- CNCBPayCtl.tmp (PID: 3616)
Reads settings of System Certificates
- ZXYHebankassit.exe (PID: 2452)
Uses TASKKILL.EXE to kill Browsers
- ZXYHebankassit.exe (PID: 2452)
Uses TASKKILL.EXE to kill process
- ZXYHebankassit.exe (PID: 2452)
Checks Windows Trust Settings
- ZXYHebankassit.exe (PID: 2452)
Reads the Windows owner or organization settings
- CNCBSecPkg.tmp (PID: 3316)
- CNCBPayCtl.tmp (PID: 3616)
Drops a system driver (possible attempt to evade defenses)
- CNCBSecPkg.tmp (PID: 3316)
- regsvr32.exe (PID: 1936)
The process creates files with name similar to system file names
- ZXYHSetup.exe (PID: 752)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 3428)
- regsvr32.exe (PID: 2988)
Changes internet zones settings
- ZXYHebankassit.exe (PID: 2452)
Reads Internet Explorer settings
- ZXYHebankassit.exe (PID: 2452)
INFO
Application launched itself
- firefox.exe (PID: 2184)
- firefox.exe (PID: 1692)
Checks supported languages
- ZXYHSetup.exe (PID: 752)
- ZXYHebankassit.exe (PID: 2452)
- CNCBSecPkg.exe (PID: 3404)
- CNCBSecPkg.tmp (PID: 3316)
- CNCBGuardReg.exe (PID: 3816)
- CNCBPayCtl.exe (PID: 3612)
- CNCBPayCtl.tmp (PID: 3616)
- CITICpibankcersafebox.exe (PID: 2572)
- CNCBWebBatchTool.exe (PID: 2480)
- CNCBSafeComponent_20231208.exe (PID: 2384)
- CITICEditIE_20220816.exe (PID: 1192)
Drops the executable file immediately after the start
- firefox.exe (PID: 2184)
- ZXYHSetup.exe (PID: 752)
- ZXYHebankassit.exe (PID: 2452)
- CNCBSecPkg.exe (PID: 3404)
- CNCBSecPkg.tmp (PID: 3316)
- CNCBPayCtl.exe (PID: 3612)
- CNCBPayCtl.tmp (PID: 3616)
- regsvr32.exe (PID: 1936)
- CITICpibankcersafebox.exe (PID: 2572)
- CNCBWebBatchTool.exe (PID: 2480)
- CNCBSafeComponent_20231208.exe (PID: 2384)
- CITICEditIE_20220816.exe (PID: 1192)
Reads the computer name
- ZXYHebankassit.exe (PID: 2452)
- ZXYHSetup.exe (PID: 752)
- CNCBGuardReg.exe (PID: 3816)
- CNCBSecPkg.tmp (PID: 3316)
- CNCBPayCtl.tmp (PID: 3616)
- CNCBSafeComponent_20231208.exe (PID: 2384)
- CITICEditIE_20220816.exe (PID: 1192)
Create files in a temporary directory
- ZXYHSetup.exe (PID: 752)
- CNCBSecPkg.exe (PID: 3404)
- CNCBSecPkg.tmp (PID: 3316)
- CNCBPayCtl.exe (PID: 3612)
- CNCBPayCtl.tmp (PID: 3616)
- CITICpibankcersafebox.exe (PID: 2572)
- CNCBWebBatchTool.exe (PID: 2480)
- CNCBSafeComponent_20231208.exe (PID: 2384)
- CITICEditIE_20220816.exe (PID: 1192)
Creates files in the program directory
- ZXYHSetup.exe (PID: 752)
- ZXYHebankassit.exe (PID: 2452)
- CNCBSecPkg.tmp (PID: 3316)
- CNCBPayCtl.tmp (PID: 3616)
- CNCBSafeComponent_20231208.exe (PID: 2384)
- CITICEditIE_20220816.exe (PID: 1192)
Creates files or folders in the user directory
- ZXYHSetup.exe (PID: 752)
- ZXYHebankassit.exe (PID: 2452)
The process uses the downloaded file
- firefox.exe (PID: 2184)
Reads the machine GUID from the registry
- ZXYHebankassit.exe (PID: 2452)
- CNCBGuardReg.exe (PID: 3816)
- CNCBPayCtl.tmp (PID: 3616)
Reads Environment values
- ZXYHebankassit.exe (PID: 2452)
Connects to unusual port
- ZXYHebankassit.exe (PID: 2452)
- ZXYHSetup.exe (PID: 752)
Checks proxy server information
- ZXYHebankassit.exe (PID: 2452)
Process drops legitimate windows executable
- CNCBSecPkg.tmp (PID: 3316)
- CNCBPayCtl.tmp (PID: 3616)
Process requests binary or script from the Internet
- ZXYHebankassit.exe (PID: 2452)
Malware-specific behavior (creating "System.dll" in Temp)
- ZXYHSetup.exe (PID: 752)
- CNCBSafeComponent_20231208.exe (PID: 2384)
- CITICEditIE_20220816.exe (PID: 1192)
Application was injected by another process
- regsvr32.exe (PID: 1848)
- regsvr32.exe (PID: 1544)
- CNCBWebBatchTool.exe (PID: 2480)
- CITICpibankcersafebox.exe (PID: 2572)
- CNCBSafeComponent_20231208.exe (PID: 2384)
- CITICEditIE_20220816.exe (PID: 1192)
Creates files in the driver directory
- regsvr32.exe (PID: 1936)
Creates a software uninstall entry
- CNCBPayCtl.tmp (PID: 3616)
Reads product name
- ZXYHebankassit.exe (PID: 2452)
The process creates files with name similar to system file names
- CNCBSafeComponent_20231208.exe (PID: 2384)
- CITICEditIE_20220816.exe (PID: 1192)
Process drops legitimate windows executable (CertUtil.exe)
- CNCBSafeComponent_20231208.exe (PID: 2384)
Reads the Internet Settings
- CNCBSafeComponent_20231208.exe (PID: 2384)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
198
Monitored processes
58
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 548 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="2184.1.1588393253\818686372" -parentBuildID 20230710165010 -prefsHandle 1424 -prefMapHandle 1420 -prefsLen 28600 -prefMapSize 244195 -appDir "C:\Program Files\Mozilla Firefox\browser" - {1d285538-c3c1-4b91-b038-e7077f2fd9f5} 2184 "\\.\pipe\gecko-crash-server-pipe.2184" 1436 f269200 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 1 Version: 115.0.2 Modules
| |||||||||||||||
| 568 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="2184.5.220510161\1824220629" -childID 4 -isForBrowser -prefsHandle 3888 -prefMapHandle 3796 -prefsLen 29209 -prefMapSize 244195 -jsInitHandle 880 -jsInitLen 240908 -parentBuildID 20230710165010 -appDir "C:\Program Files\Mozilla Firefox\browser" - {b48b5068-237f-4554-ad00-b2f57ed46394} 2184 "\\.\pipe\gecko-crash-server-pipe.2184" 3892 18f039b0 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 1 Version: 115.0.2 Modules
| |||||||||||||||
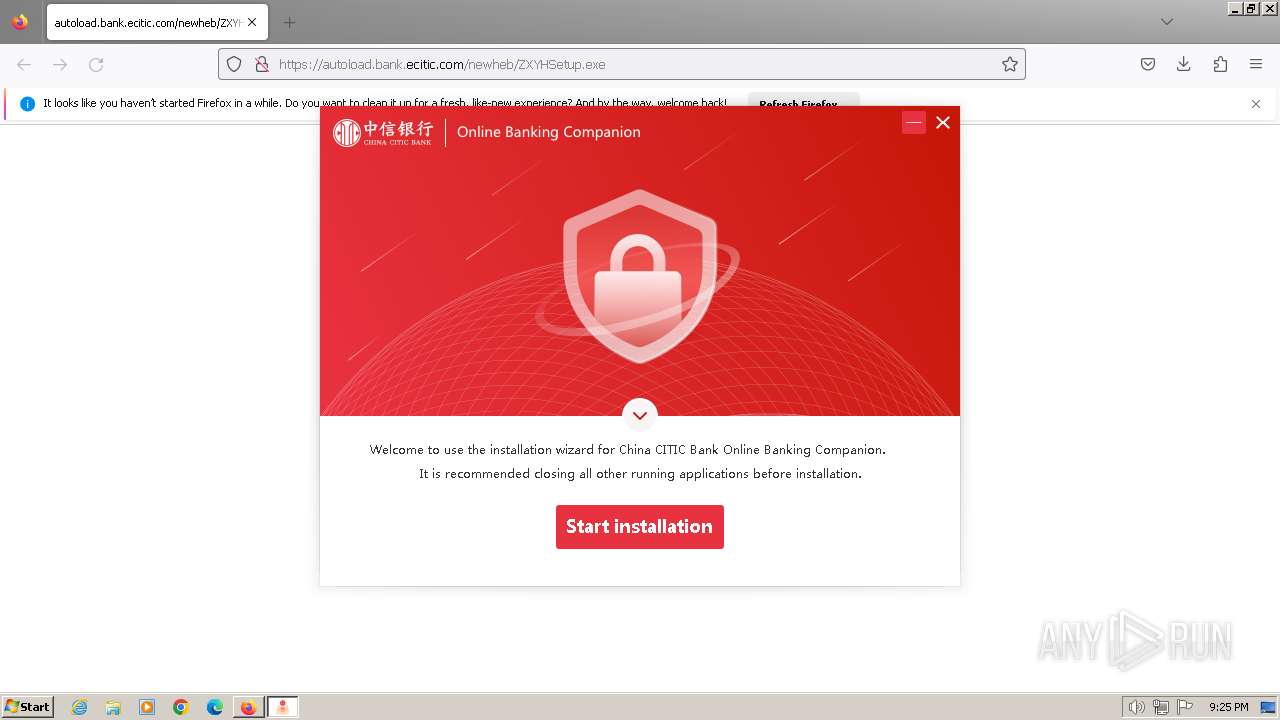
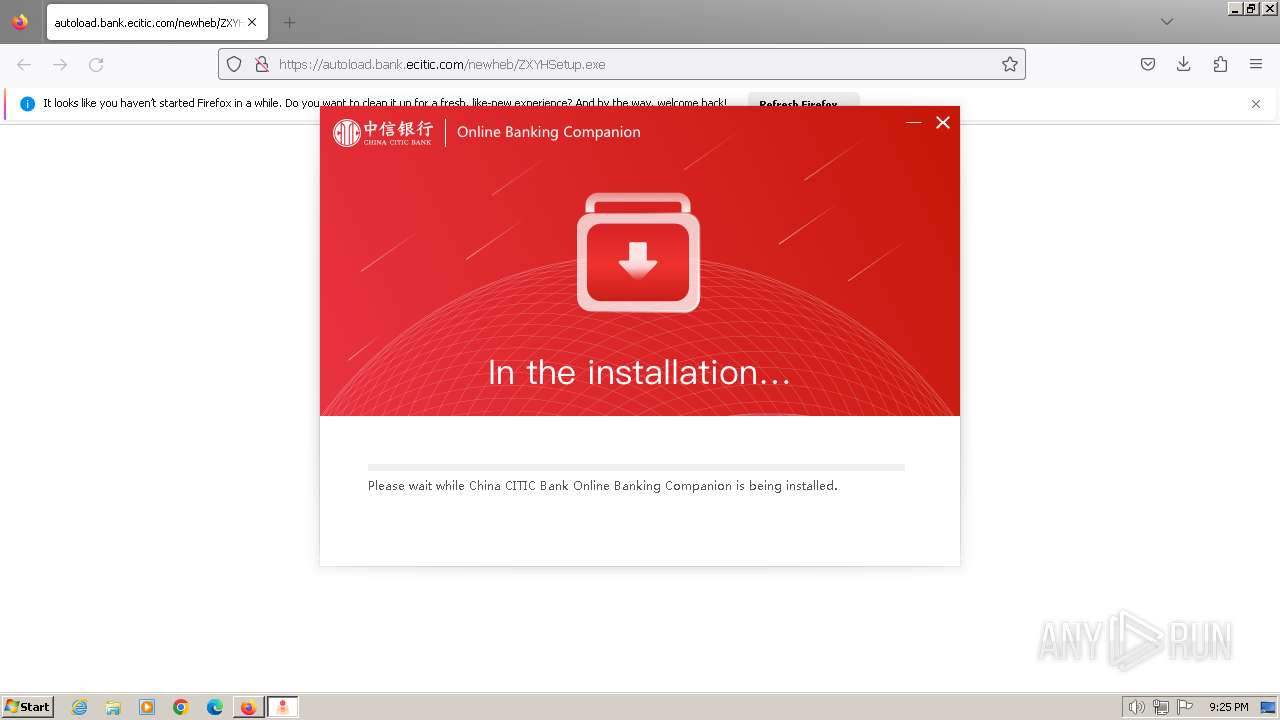
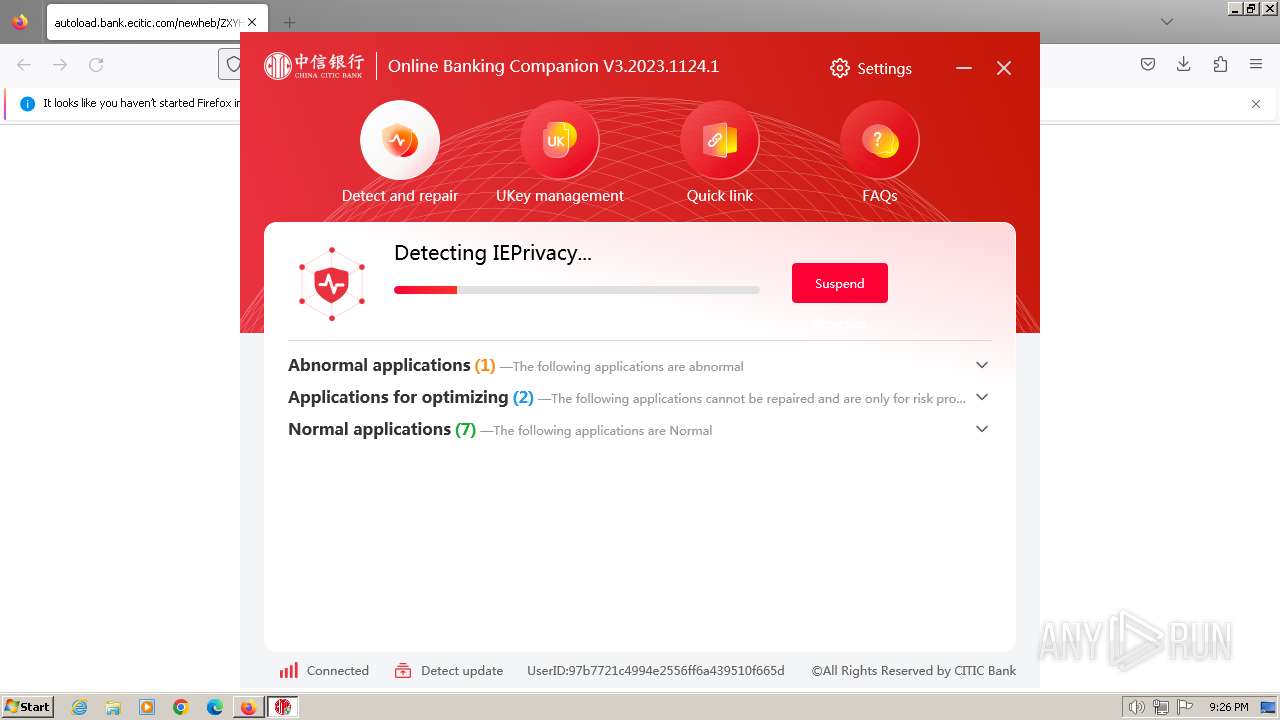
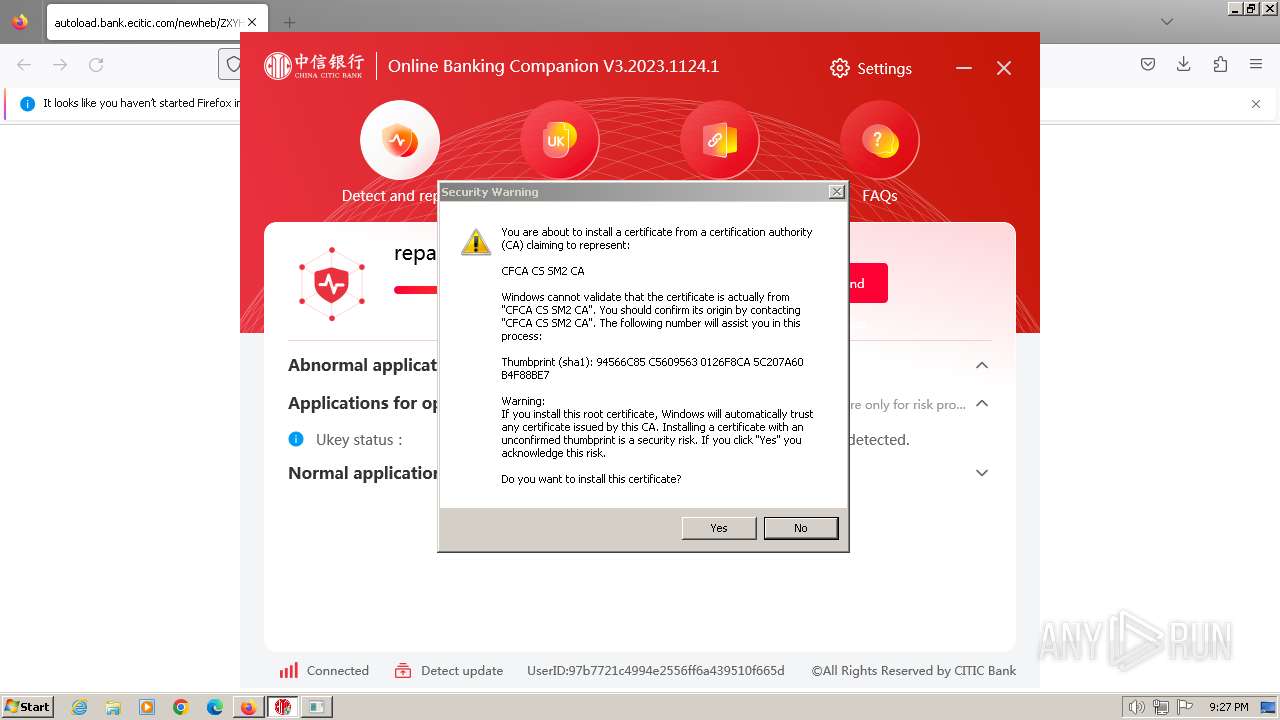
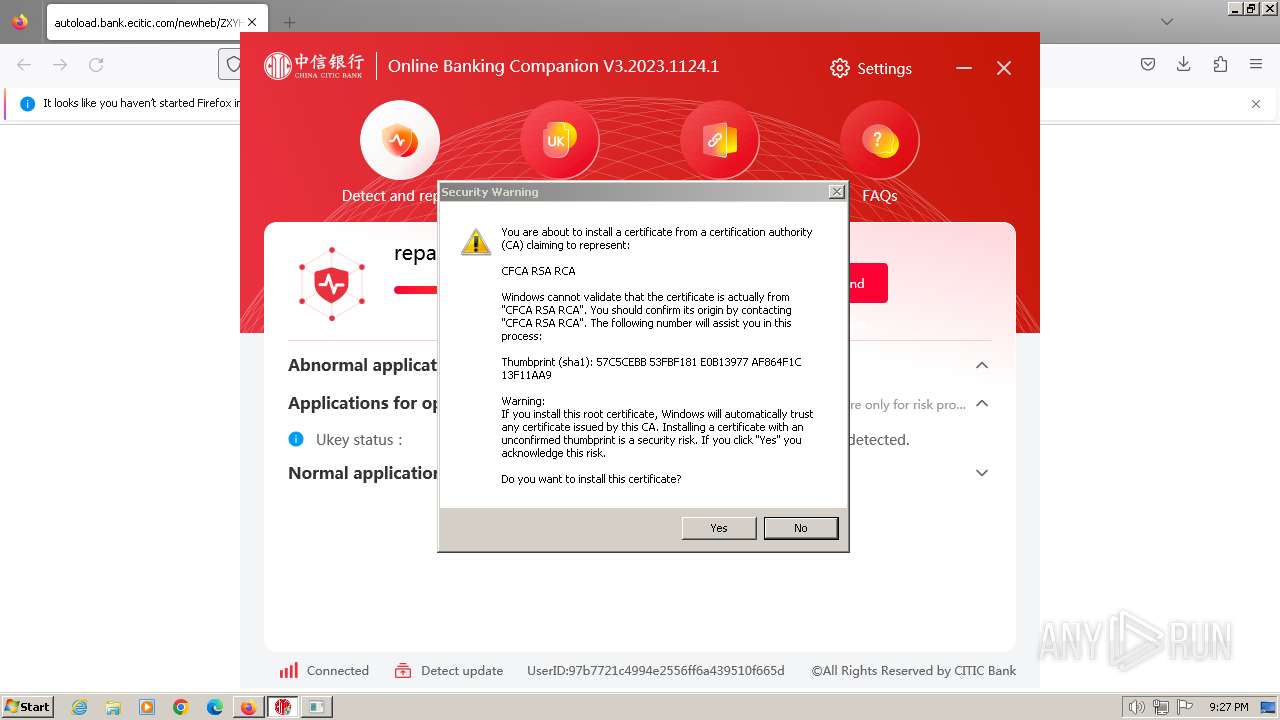
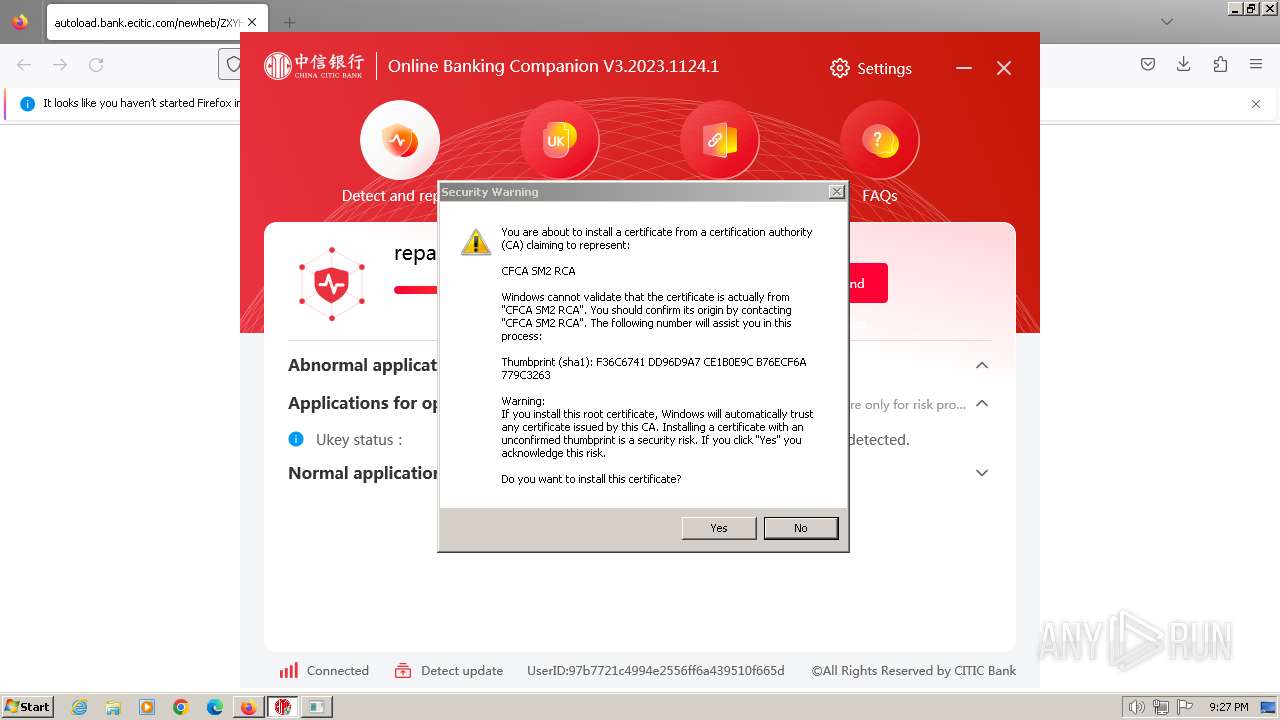
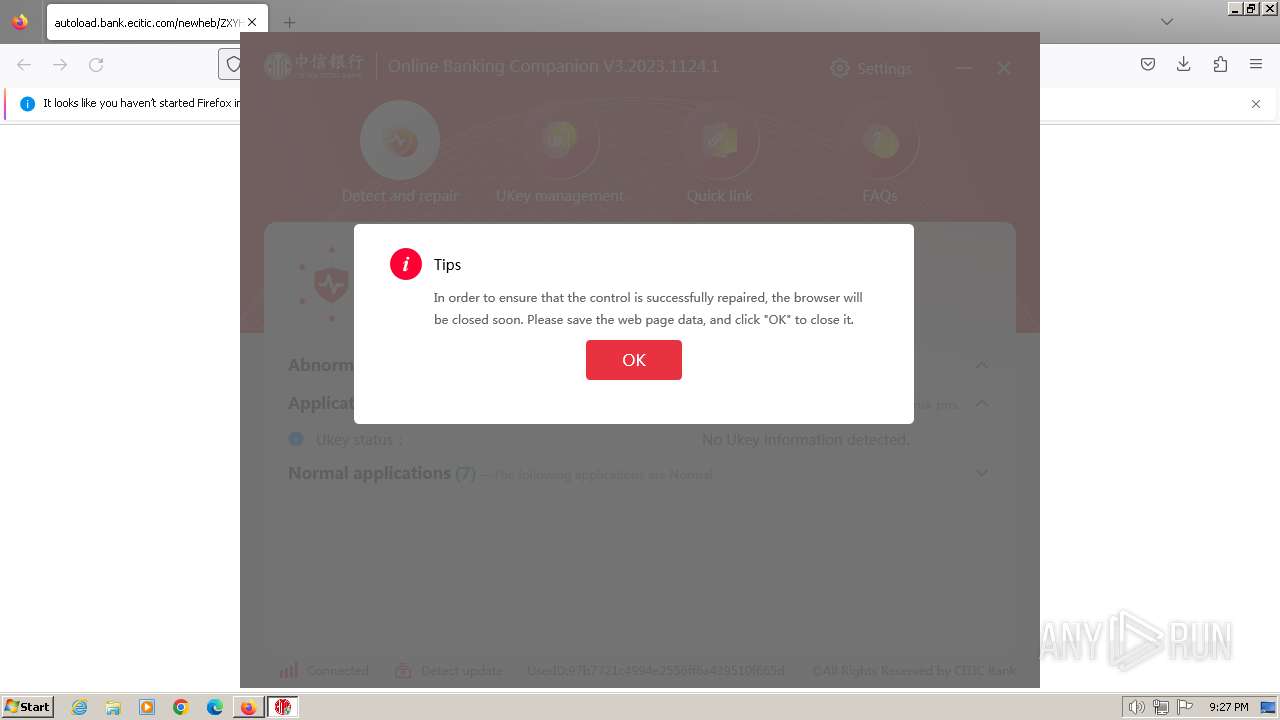
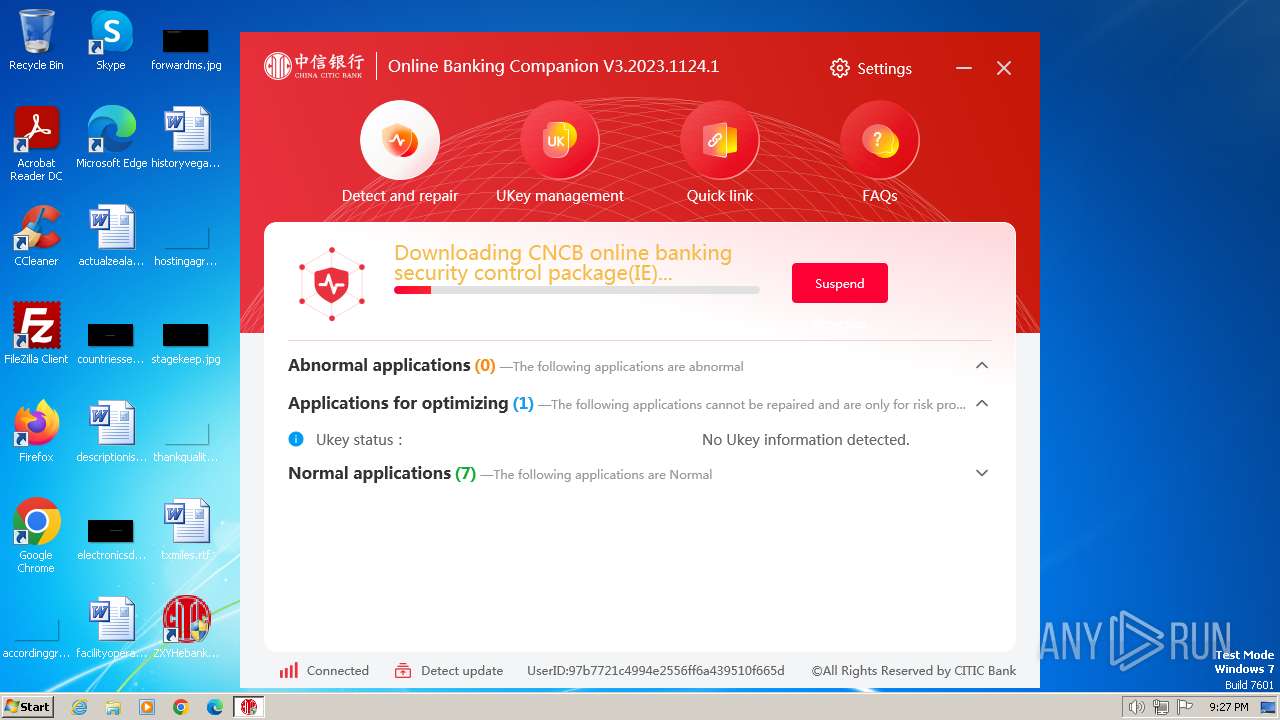
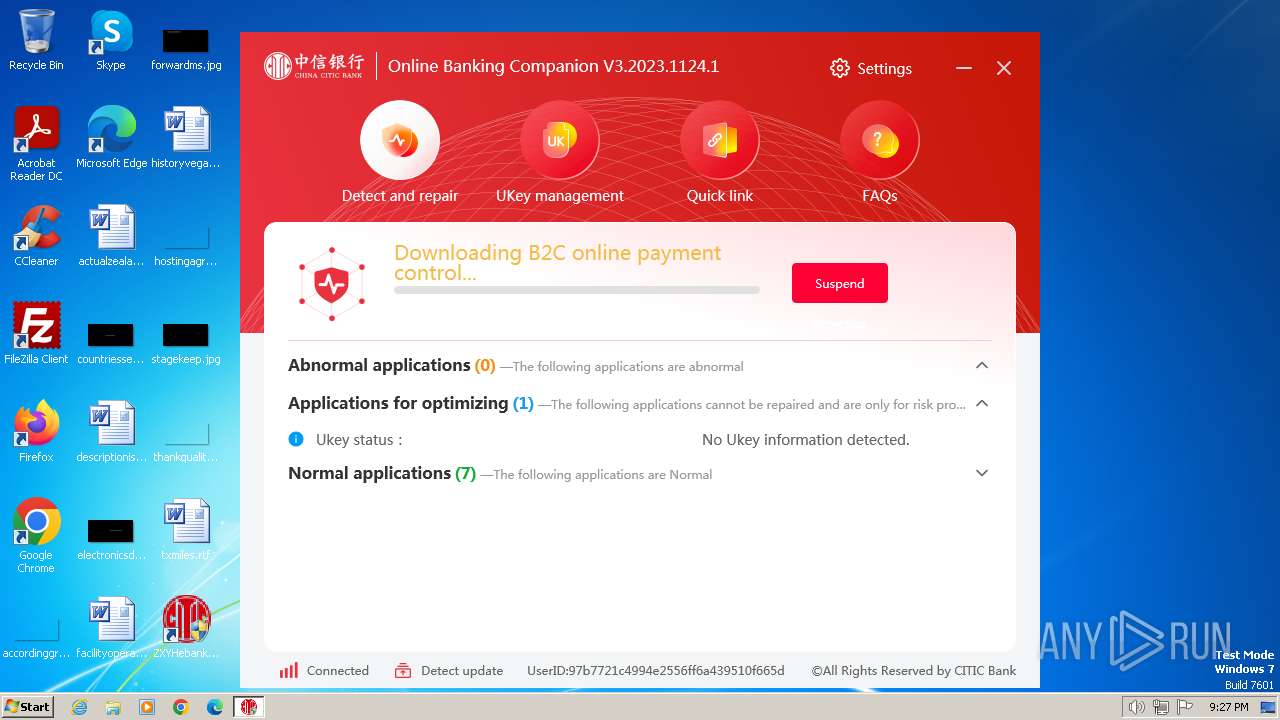
| 752 | "C:\Users\admin\Downloads\ZXYHSetup.exe" | C:\Users\admin\Downloads\ZXYHSetup.exe | firefox.exe | ||||||||||||
User: admin Company: 中信银行股份有限公司 Integrity Level: HIGH Description: 中信银行网银伴侣 Exit code: 0 Version: 3.2023.1124.1 Modules
| |||||||||||||||
| 784 | "C:\Windows\system32\regsvr32.exe" /s "C:\Windows\system32\SecCtl.dll" | C:\Windows\System32\regsvr32.exe | — | CNCBPayCtl.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 840 | "C:\Windows\system32\regsvr32.exe" /s "C:\Windows\system32\Init_Tool_ft.ocx" | C:\Windows\System32\regsvr32.exe | — | CNCBSecPkg.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1192 | "C:\Program Files\ZXYHebankassit\Download\CITICEditIE_20220816.exe" /S | C:\Program Files\ZXYHebankassit\Download\CITICEditIE_20220816.exe | — | ||||||||||||
User: admin Company: CHINA CITIC BANK Integrity Level: HIGH Description: 中信银行网银密码保护控件 Exit code: 0 Version: 1.0.22.0705 Modules
| |||||||||||||||
| 1544 | "C:\Windows\system32\regsvr32.exe" /s "C:\Program Files\CNCB\PayGate_B2C\Bin\CNCBChecker.dll" | C:\Windows\System32\regsvr32.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1556 | "C:\Windows\system32\regsvr32.exe" /s "C:\Windows\system32\CITICAP.dll" | C:\Windows\System32\regsvr32.exe | — | CNCBSecPkg.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1596 | "C:\Windows\system32\regsvr32.exe" /s "C:\Windows\system32\CITICEdit.dll" | C:\Windows\System32\regsvr32.exe | — | CNCBPayCtl.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1692 | "C:\Program Files\Mozilla Firefox\firefox.exe" "https://autoload.bank.ecitic.com/newheb/ZXYHSetup.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
Total events
60 606
Read events
59 279
Write events
1 228
Delete events
99
Modification events
| (PID) Process: | (1692) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Launcher |
Value: 2166C0A101000000 | |||
| (PID) Process: | (2184) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: 044CC1A101000000 | |||
| (PID) Process: | (2184) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Telemetry |
Value: 0 | |||
| (PID) Process: | (2184) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (2184) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Theme |
Value: 1 | |||
| (PID) Process: | (2184) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Enabled |
Value: 1 | |||
| (PID) Process: | (2184) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableTelemetry |
Value: 1 | |||
| (PID) Process: | (2184) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableDefaultBrowserAgent |
Value: 0 | |||
| (PID) Process: | (2184) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|SetDefaultBrowserUserChoice |
Value: 1 | |||
| (PID) Process: | (2184) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|AppLastRunTime |
Value: D14E5F3C23B0D901 | |||
Executable files
124
Suspicious files
163
Text files
64
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2184 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs.js | text | |
MD5:60E0DE9E05EC76C749D80F0D15A81B21 | SHA256:08252FA62CCCCD316474E20CC7317A6B5C932B2C972234318E8CCDA39EC2EF48 | |||
| 2184 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\urlCache-current.bin | binary | |
MD5:B7A3C61D0C144CC5E166B1E769CA8F8C | SHA256:7FADCB77FFACA6B9E9F15C6F1CD3AAD4C20DCD90FA92429A627A3A7110CA2644 | |||
| 2184 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2184 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2184 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 2184 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3561288849sdhlie.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2184 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\datareporting\glean\db\data.safe.tmp | binary | |
MD5:1C3C58F7838DDE7F753614D170F110FC | SHA256:81C14432135B2A50DC505904E87781864CA561EFEF9E94BAECA3704D04E6DB3D | |||
| 2184 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\2918063365piupsah.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2184 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\datareporting\glean\db\data.safe.bin | binary | |
MD5:1C3C58F7838DDE7F753614D170F110FC | SHA256:81C14432135B2A50DC505904E87781864CA561EFEF9E94BAECA3704D04E6DB3D | |||
| 2184 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
36
TCP/UDP connections
95
DNS requests
146
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2184 | firefox.exe | POST | 200 | 18.245.65.219:80 | http://ocsp.r2m02.amazontrust.com/ | unknown | binary | 471 b | unknown |
2184 | firefox.exe | POST | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3 | unknown | binary | 471 b | unknown |
2184 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | text | 90 b | unknown |
2184 | firefox.exe | POST | 200 | 184.24.77.54:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
2184 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | text | 8 b | unknown |
2184 | firefox.exe | POST | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3 | unknown | binary | 472 b | unknown |
2184 | firefox.exe | POST | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3 | unknown | binary | 471 b | unknown |
2184 | firefox.exe | POST | 200 | 184.24.77.54:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
2184 | firefox.exe | POST | 200 | 163.181.56.212:80 | http://ocsp.dcocsp.cn/ | unknown | binary | 471 b | unknown |
2184 | firefox.exe | POST | 200 | 184.24.77.54:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2184 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
2184 | firefox.exe | 142.250.184.234:443 | safebrowsing.googleapis.com | — | — | whitelisted |
2184 | firefox.exe | 142.250.186.131:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
2184 | firefox.exe | 34.107.243.93:443 | push.services.mozilla.com | GOOGLE | US | unknown |
2184 | firefox.exe | 34.117.237.239:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | unknown |
2184 | firefox.exe | 34.149.100.209:443 | firefox.settings.services.mozilla.com | GOOGLE | US | unknown |
2184 | firefox.exe | 52.4.22.105:443 | spocs.getpocket.com | AMAZON-AES | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
autoload.bank.ecitic.com |
| unknown |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
spocs.getpocket.com |
| shared |
proxyserverecs-1736642167.us-east-1.elb.amazonaws.com |
| shared |
firefox.settings.services.mozilla.com |
| whitelisted |
r3.o.lencr.org |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2452 | ZXYHebankassit.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2452 | ZXYHebankassit.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2452 | ZXYHebankassit.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2452 | ZXYHebankassit.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2452 | ZXYHebankassit.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2452 | ZXYHebankassit.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
Process | Message |
|---|---|
ZXYHSetup.exe | Window, size, 640,480
|
ZXYHSetup.exe | Window, shadowcorner, 14,14,14,14
|
ZXYHSetup.exe | Window, shadowimage, bk_shadow.png
|
ZXYHSetup.exe | Window, showshadow, true
|
ZXYHSetup.exe | Window, caption, 0,0,0,480
|
ZXYHSetup.exe | Window, sizebox, 0,0,0,0
|
ZXYHSetup.exe | Window, shadowsize, 14
|
ZXYHSetup.exe | ImageShow, images, pic1.png
|
ZXYHSetup.exe | ImageShow, imagecount, 1
|
ZXYHSetup.exe | ImageShow, width, 640
|